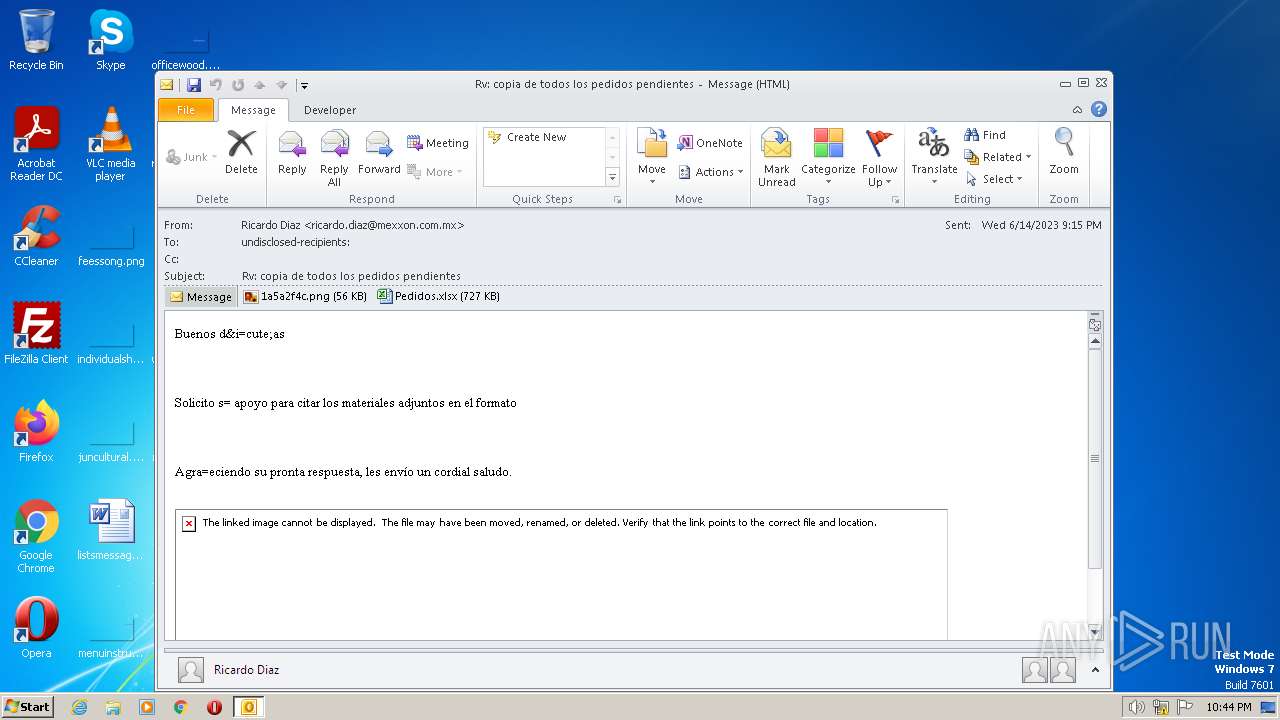
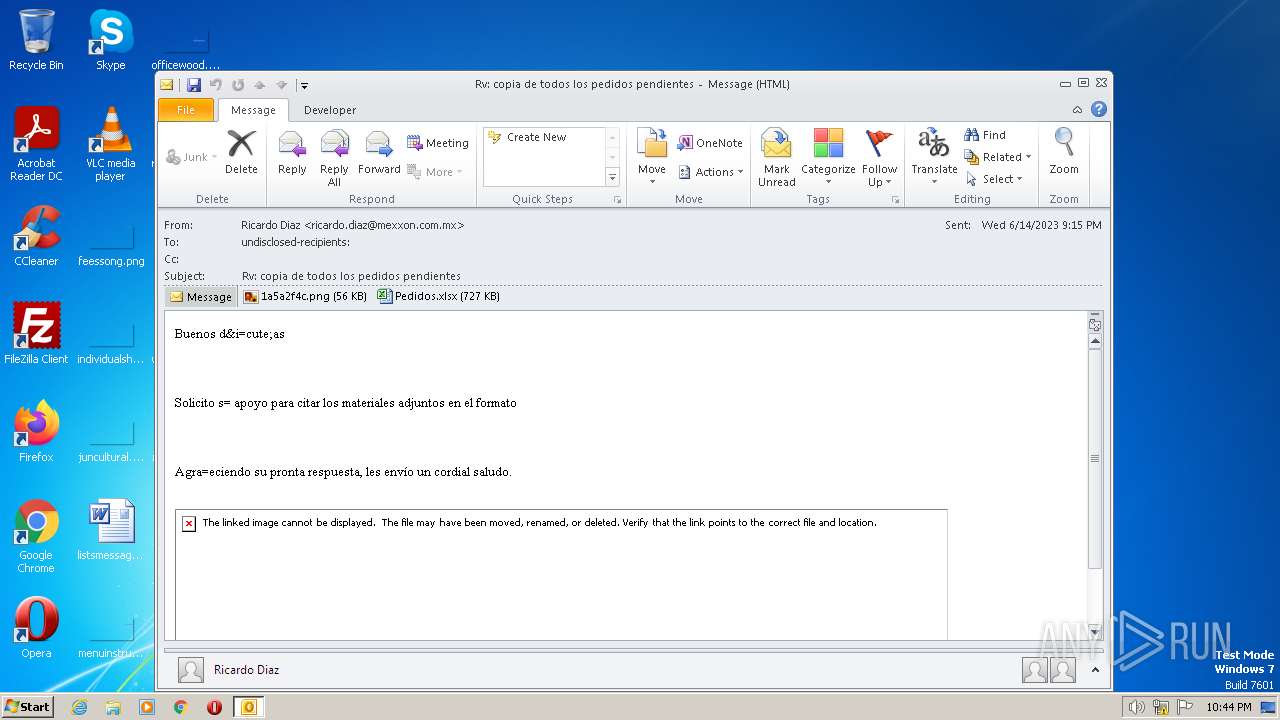
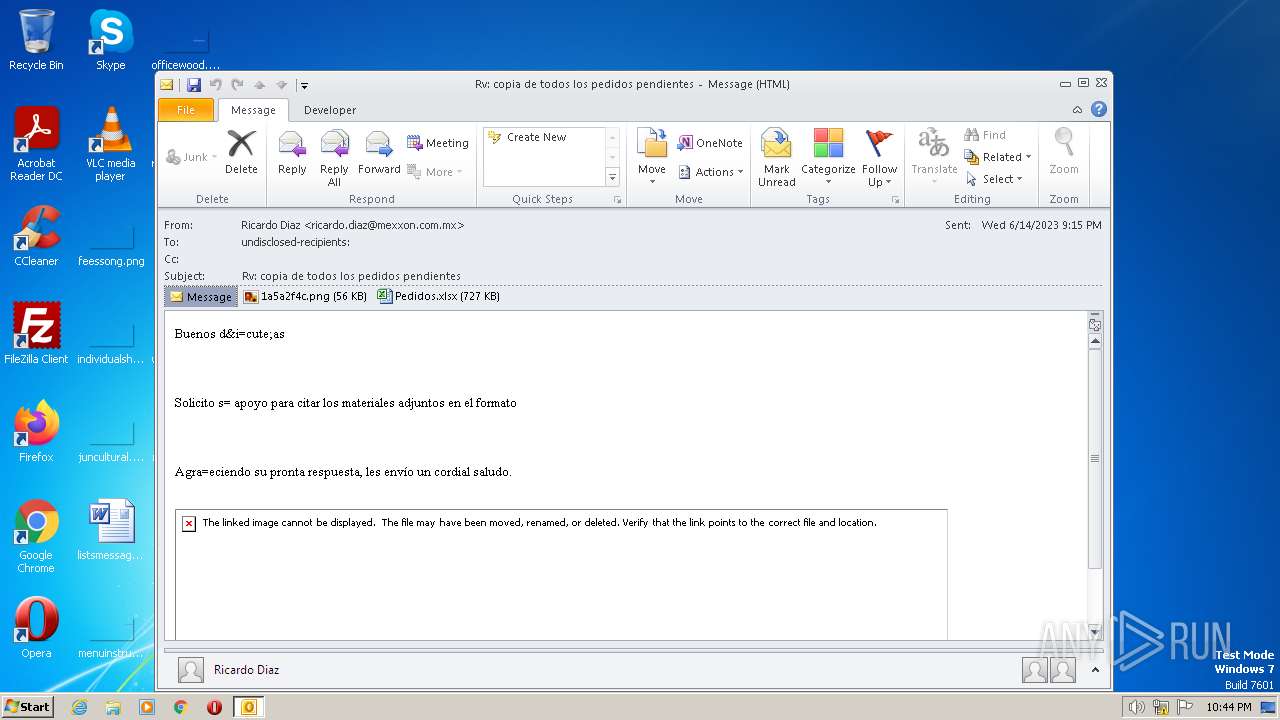
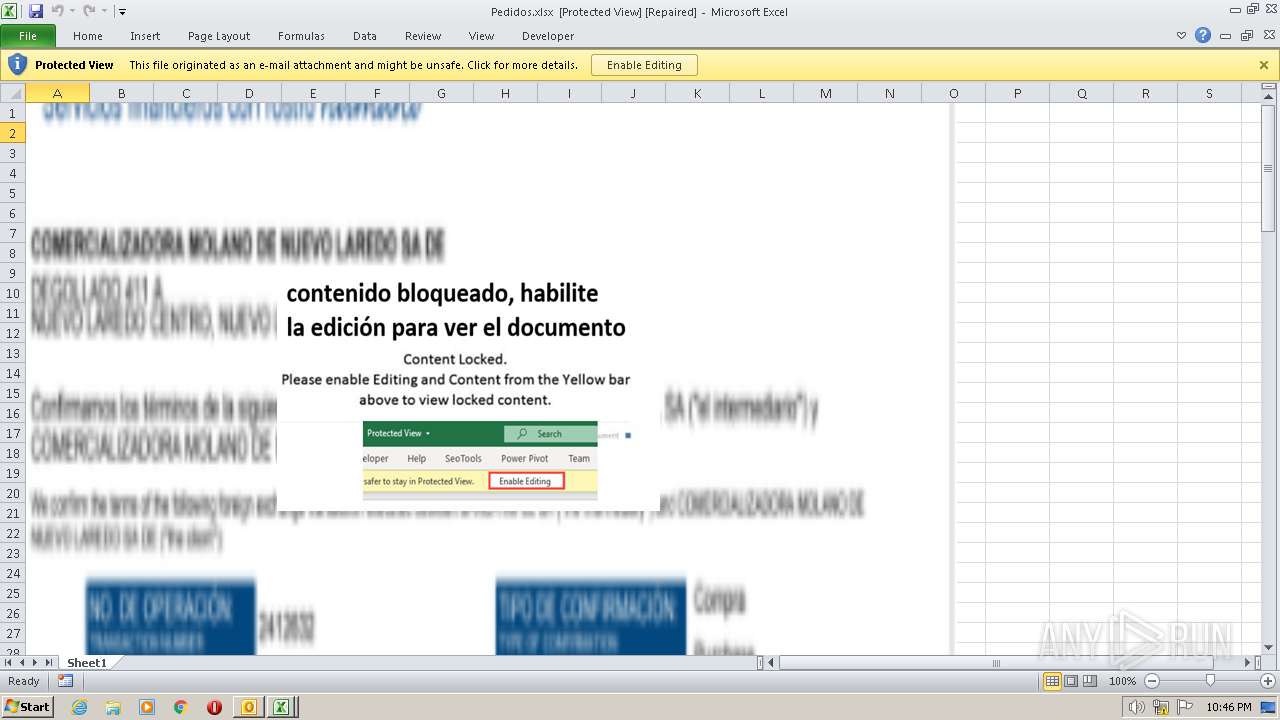
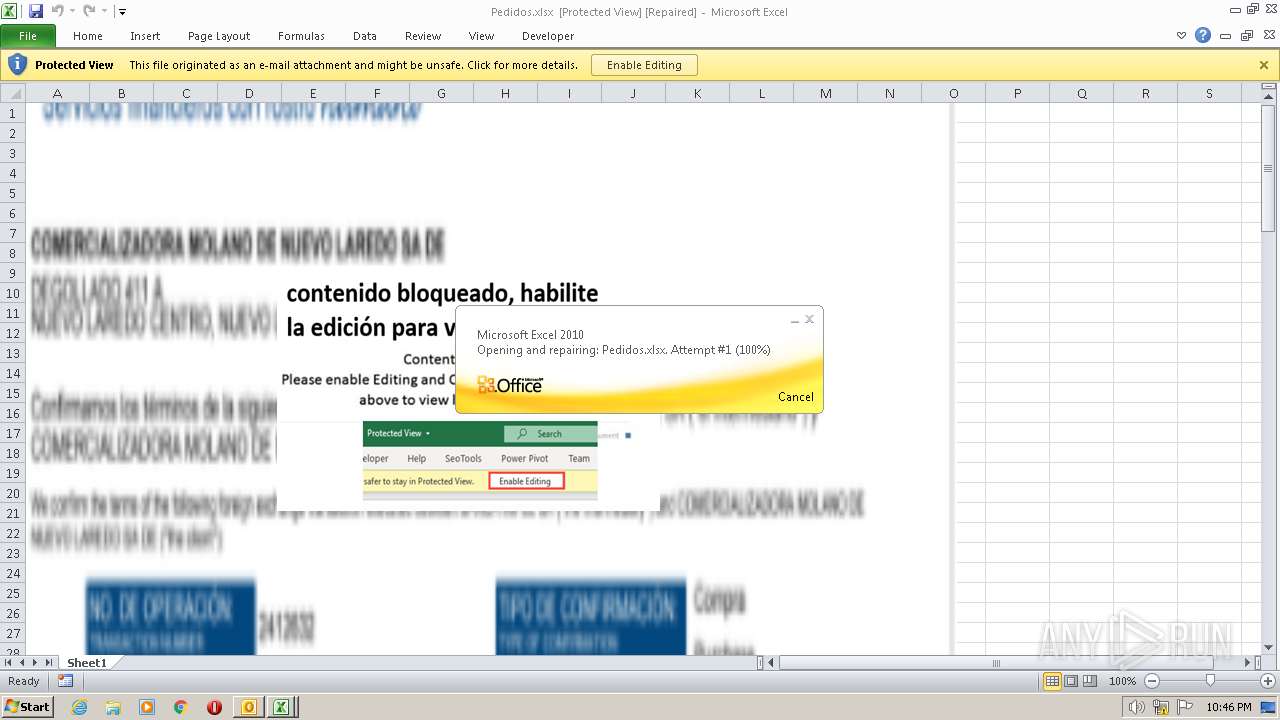
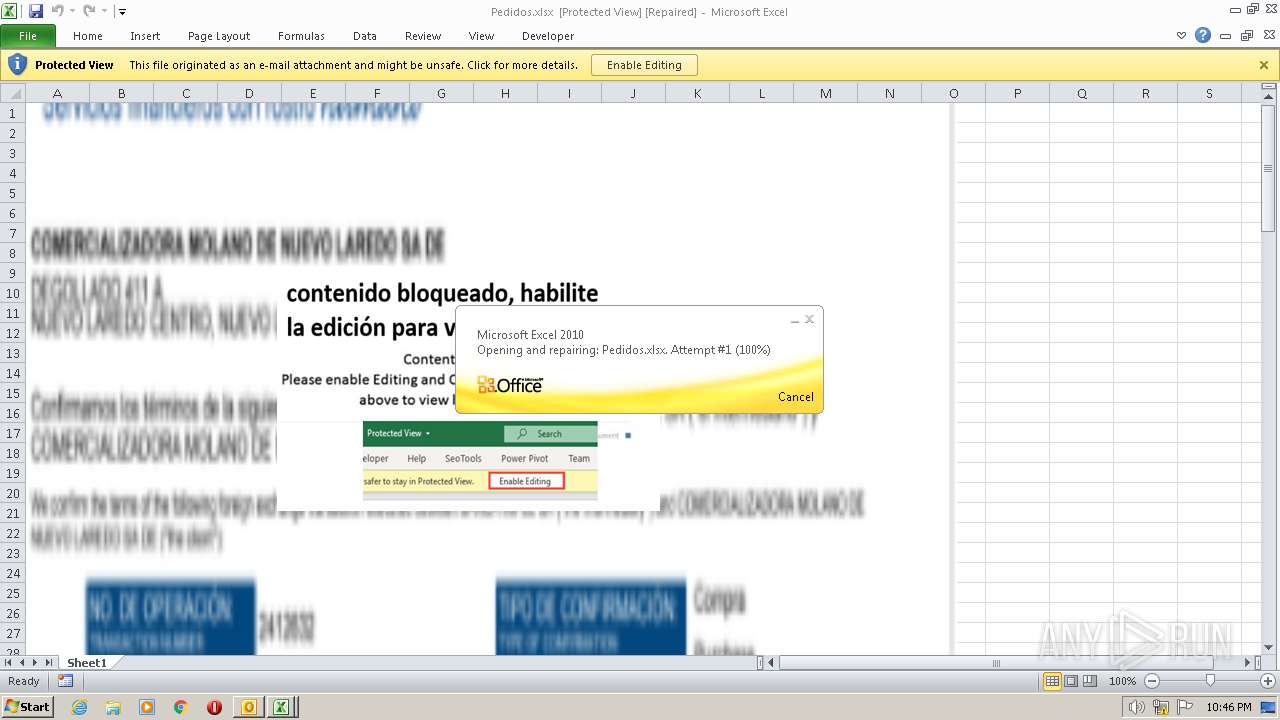
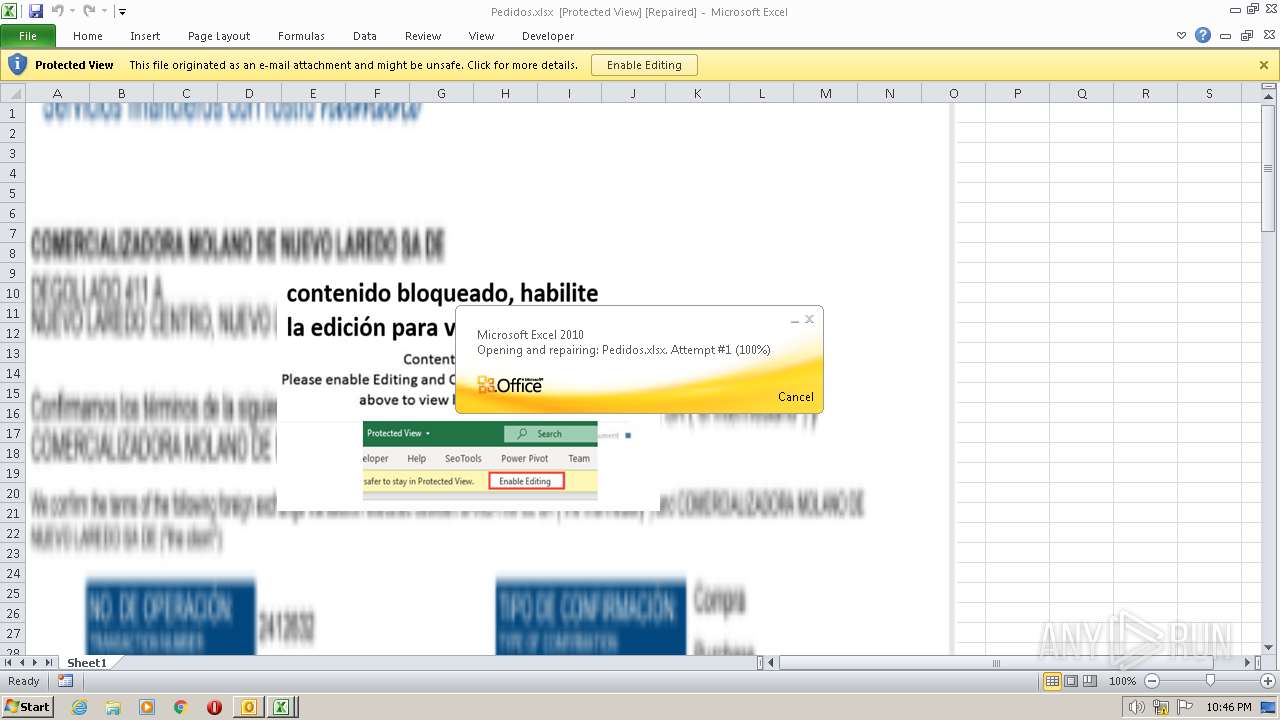
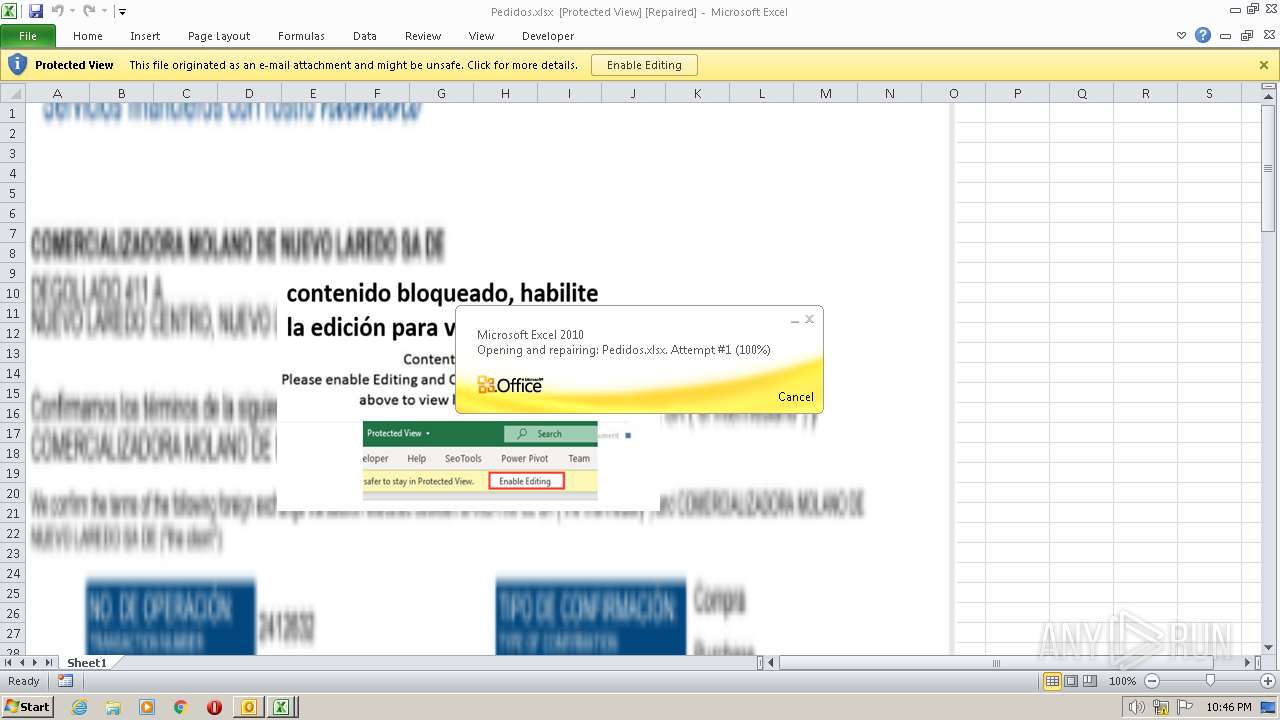
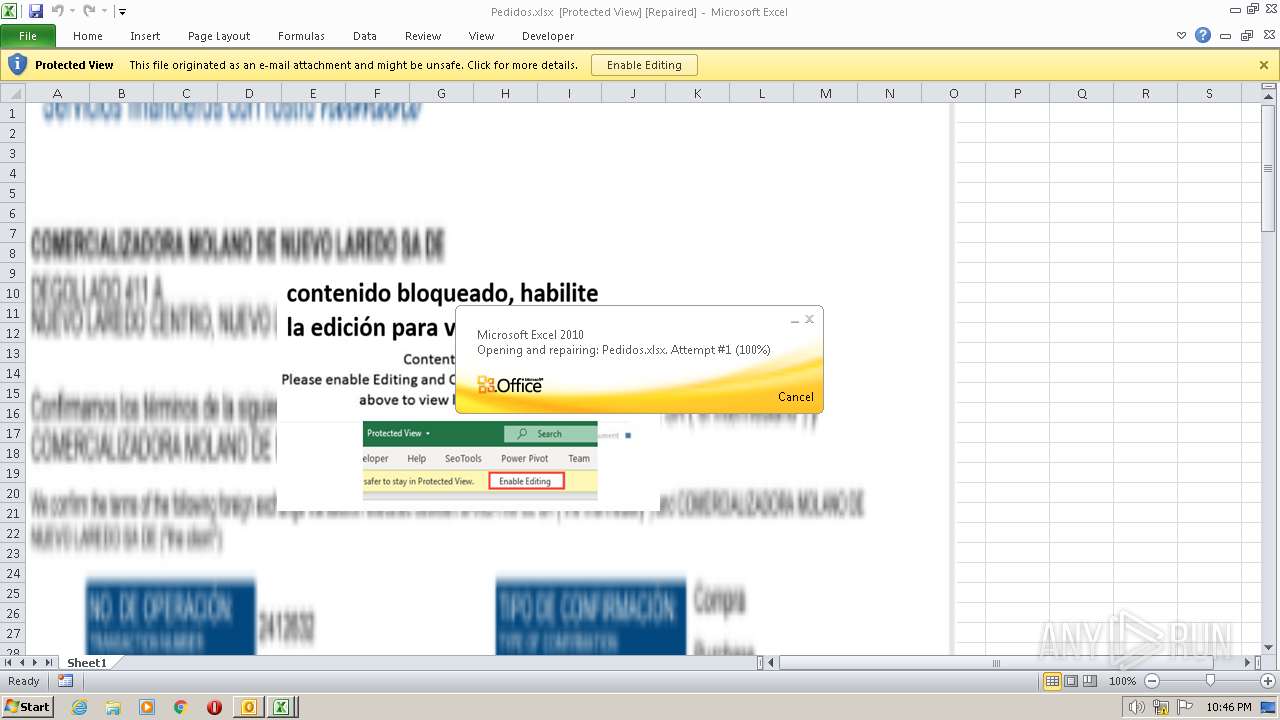
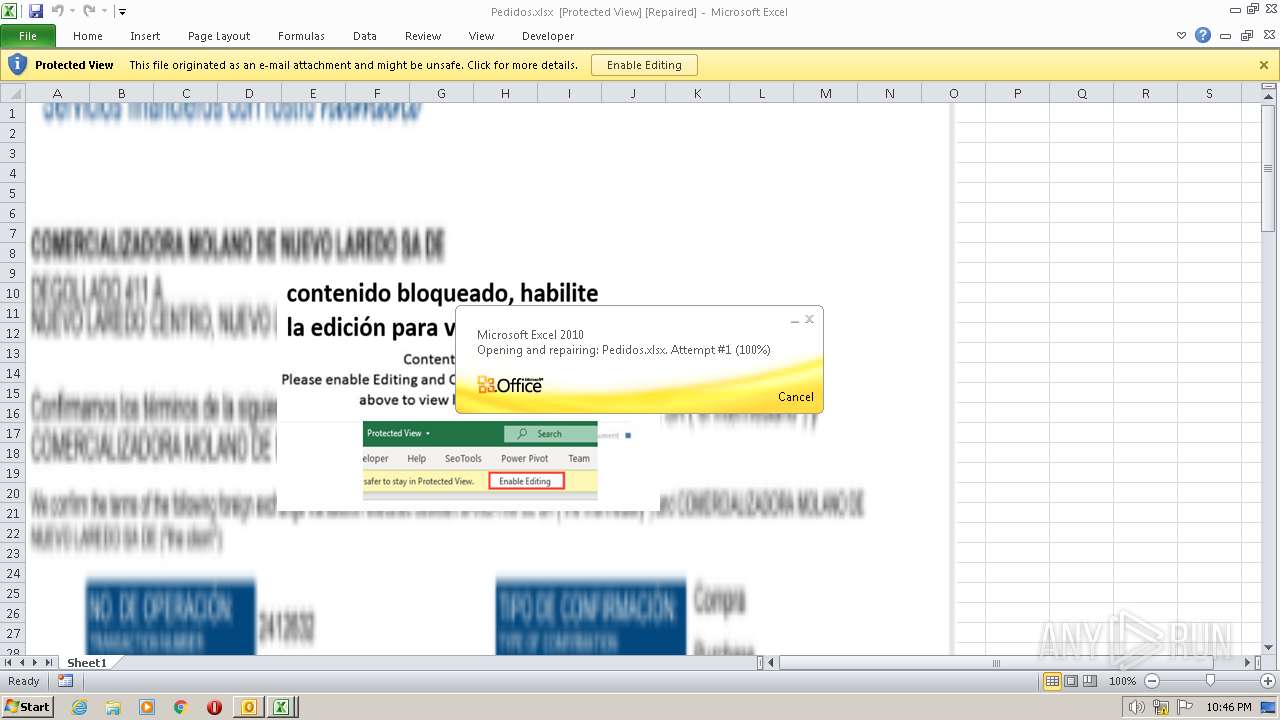
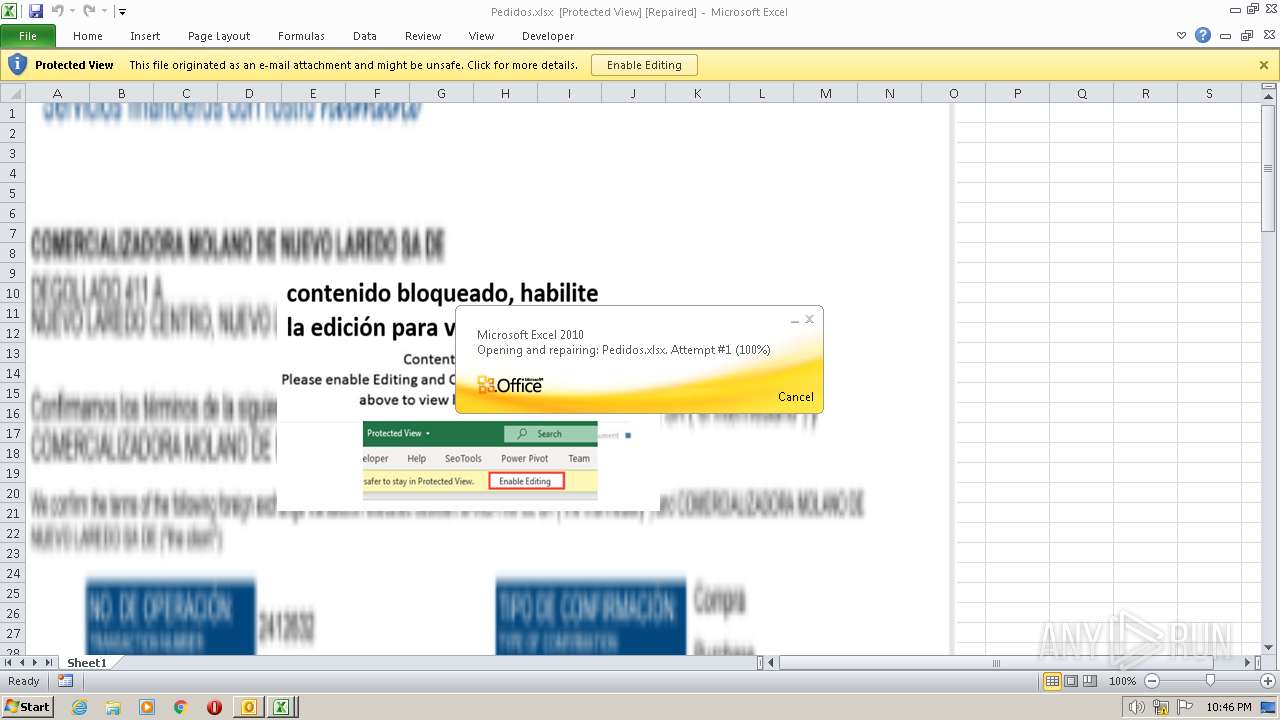
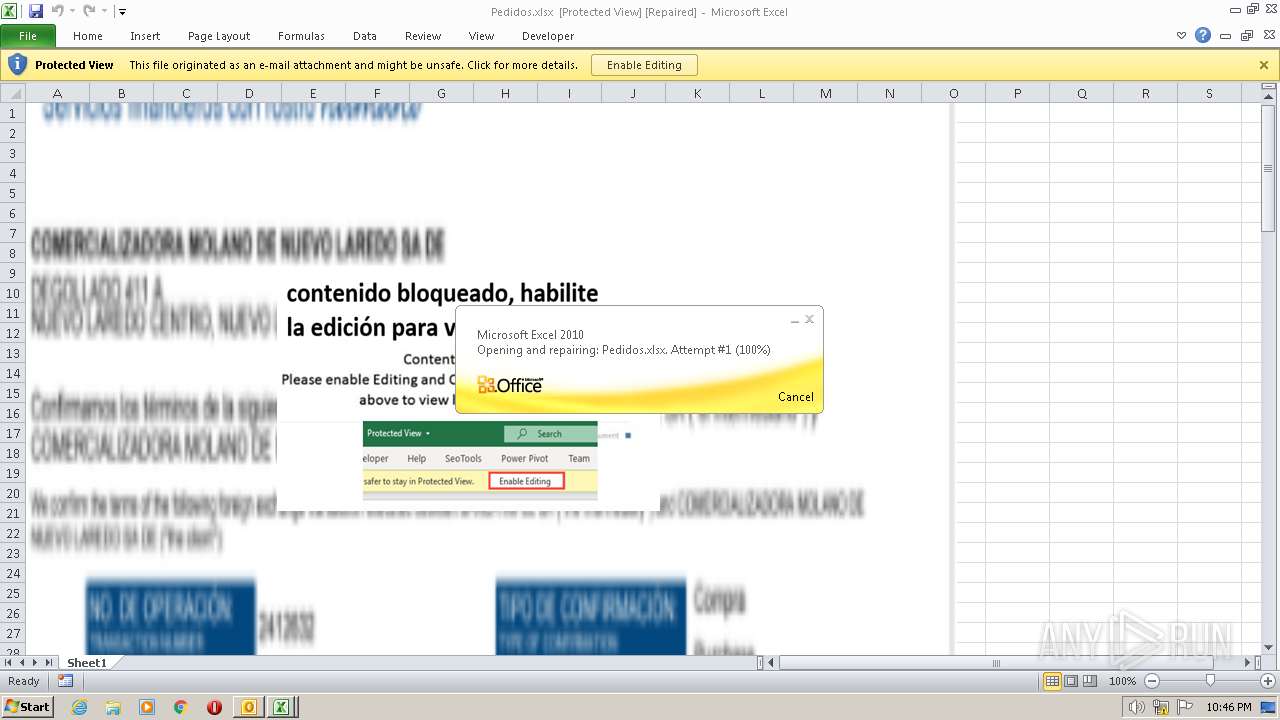
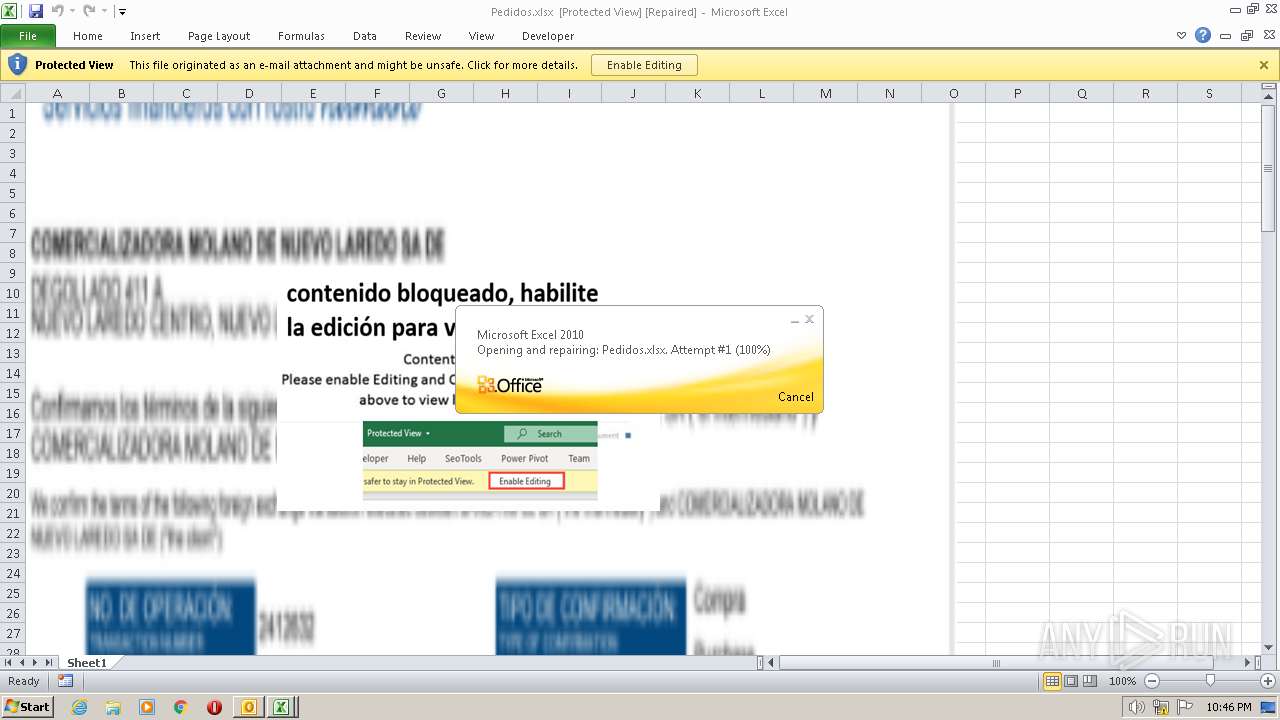
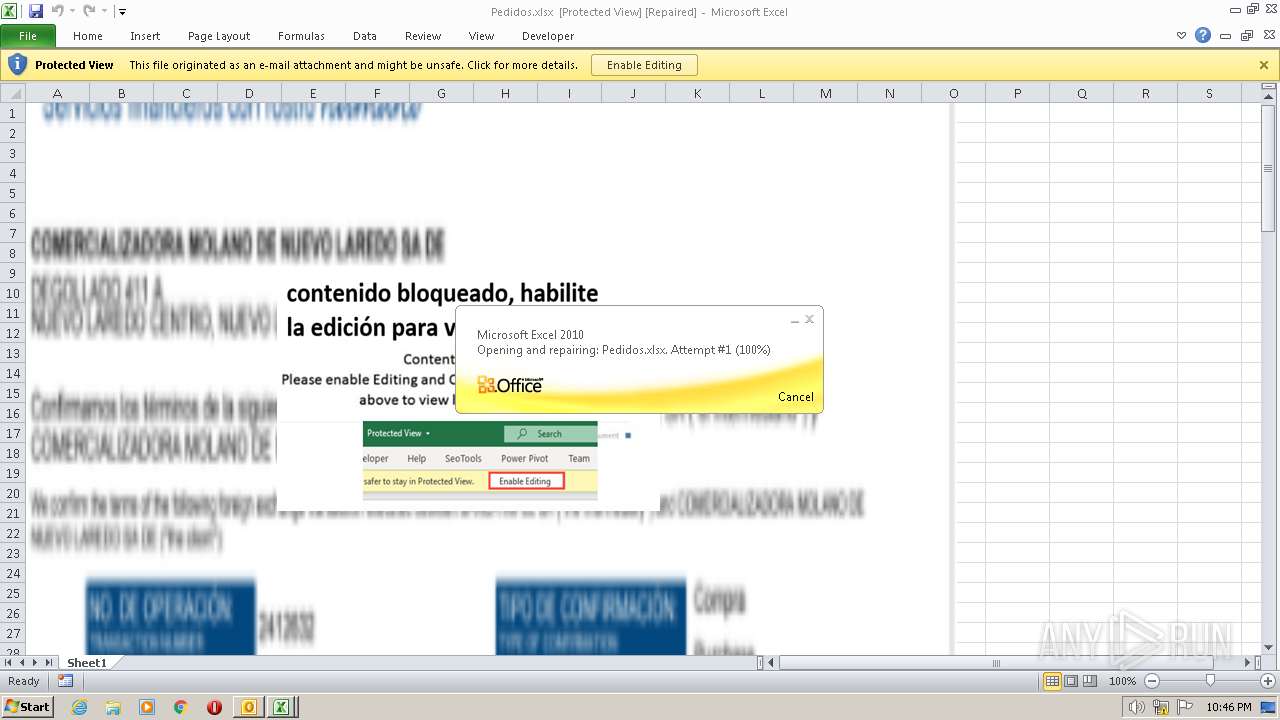
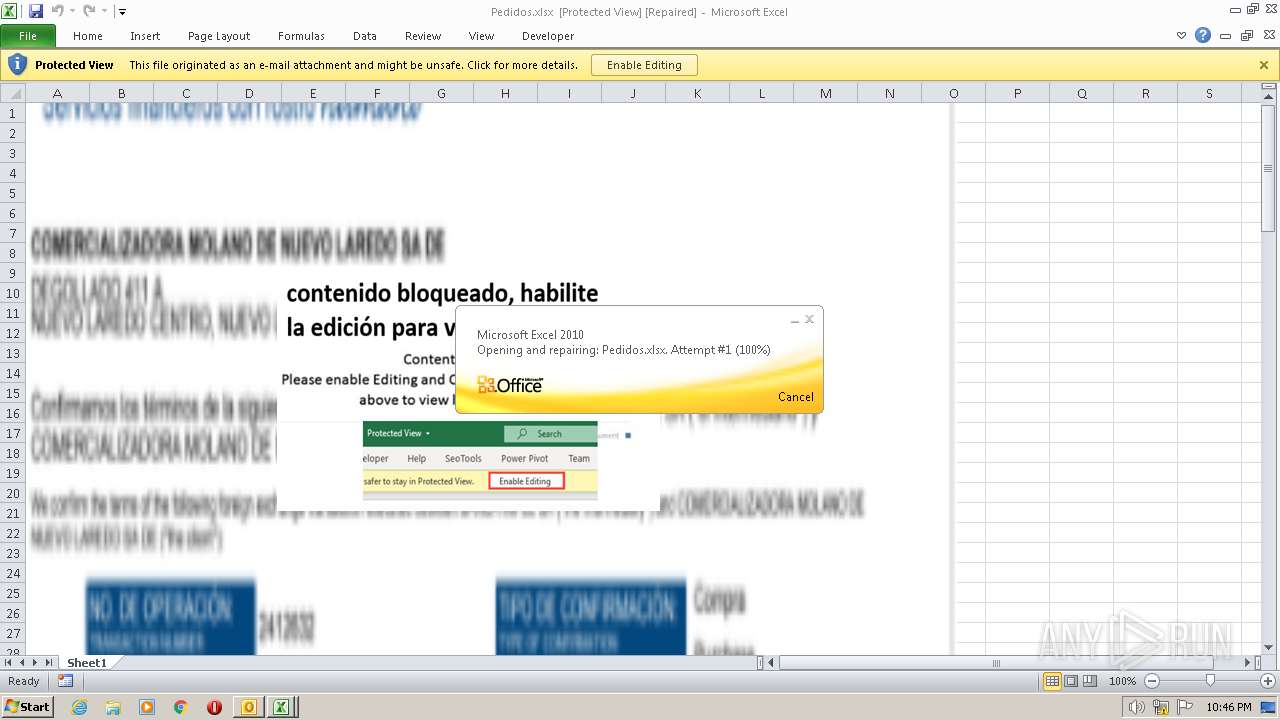
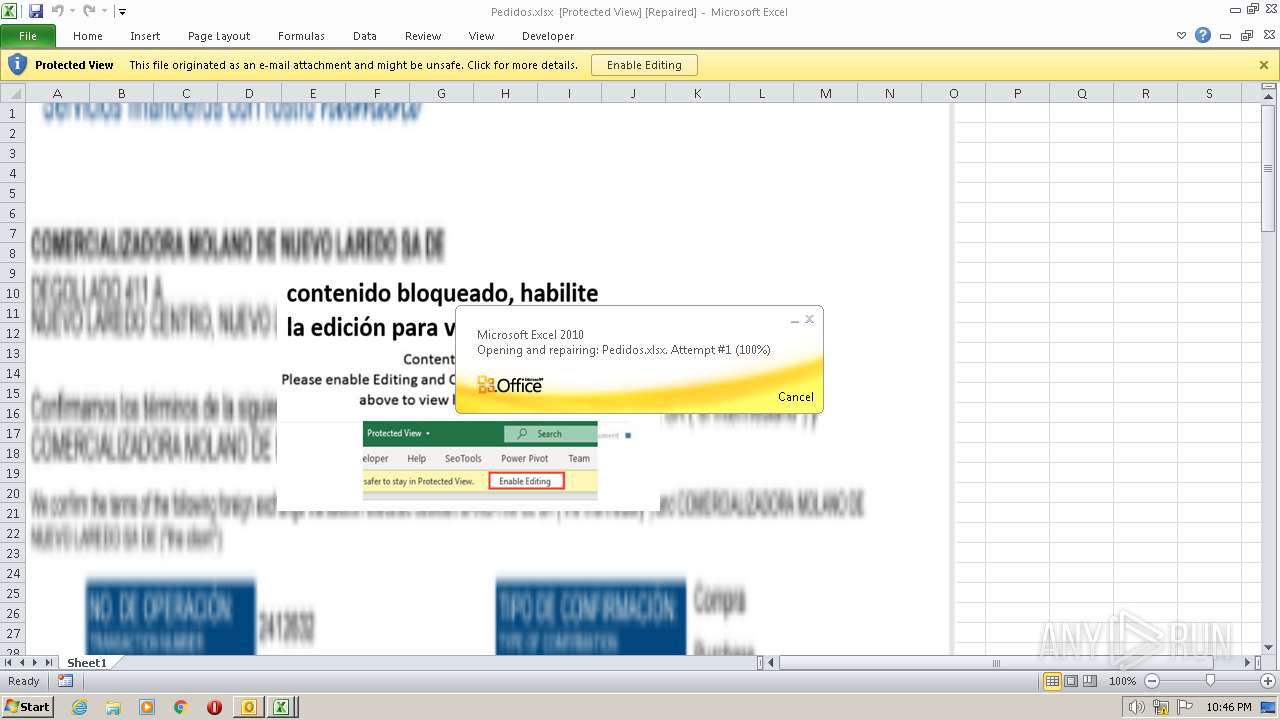
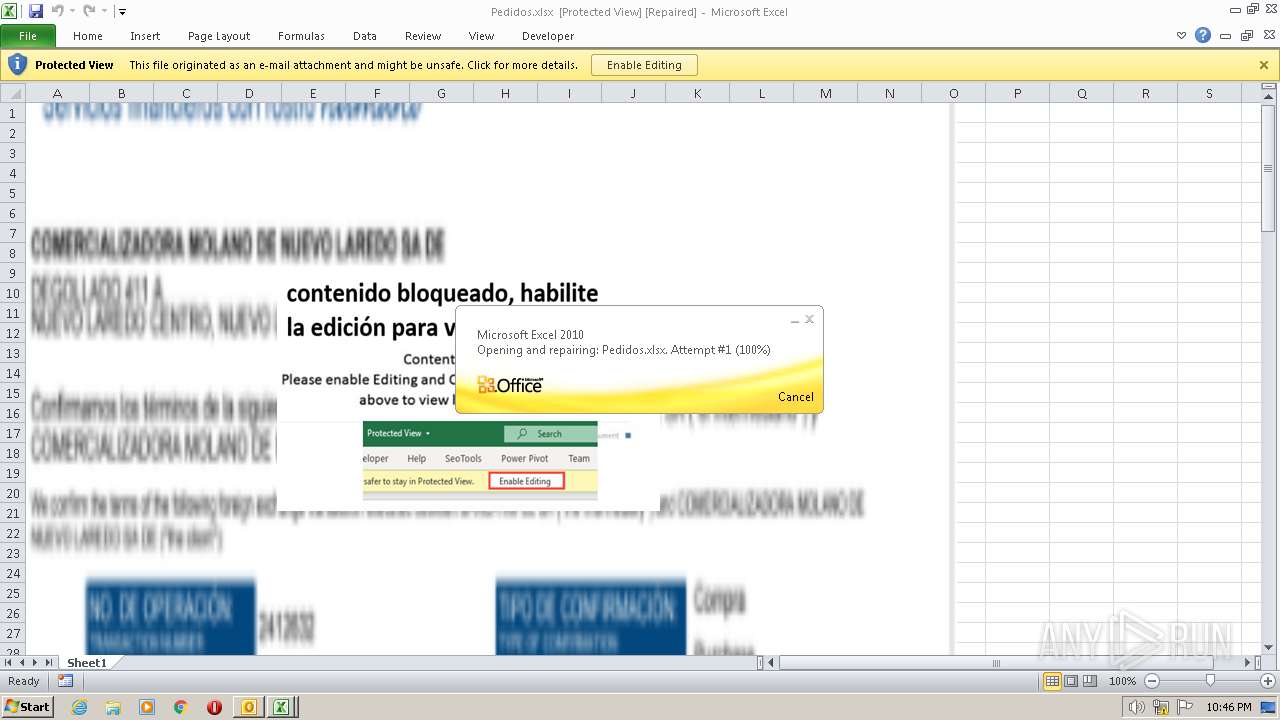
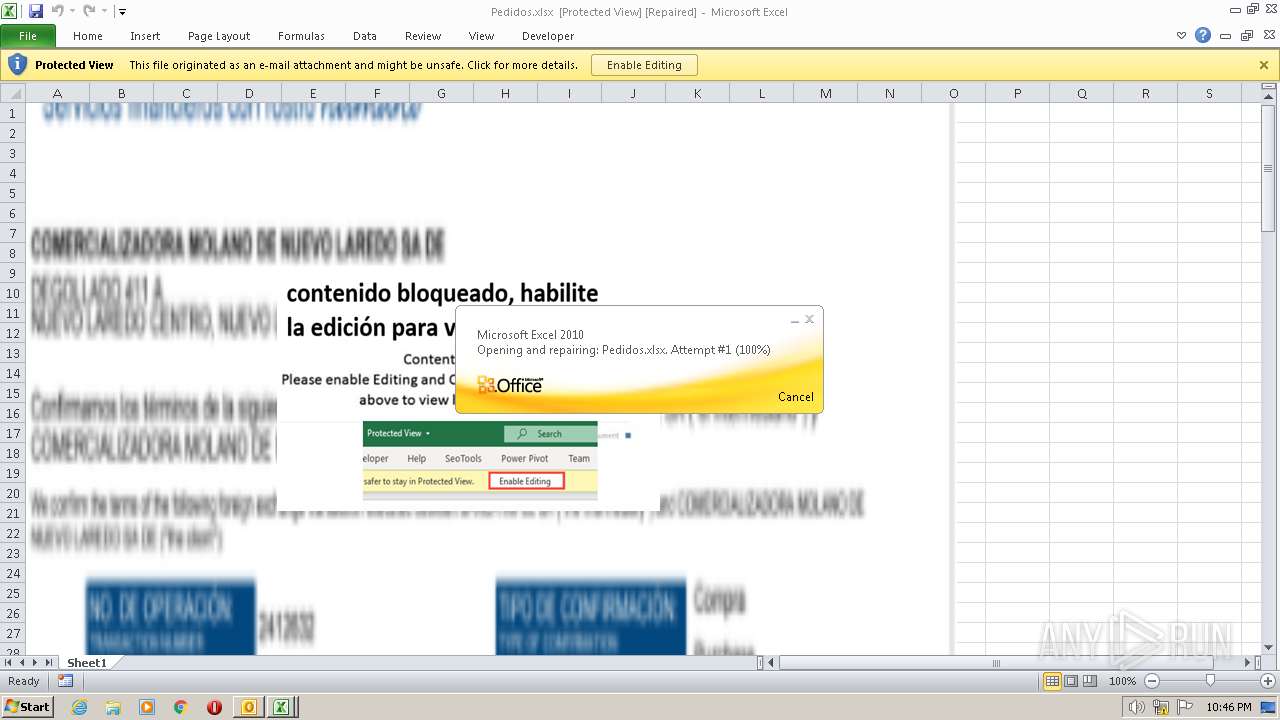
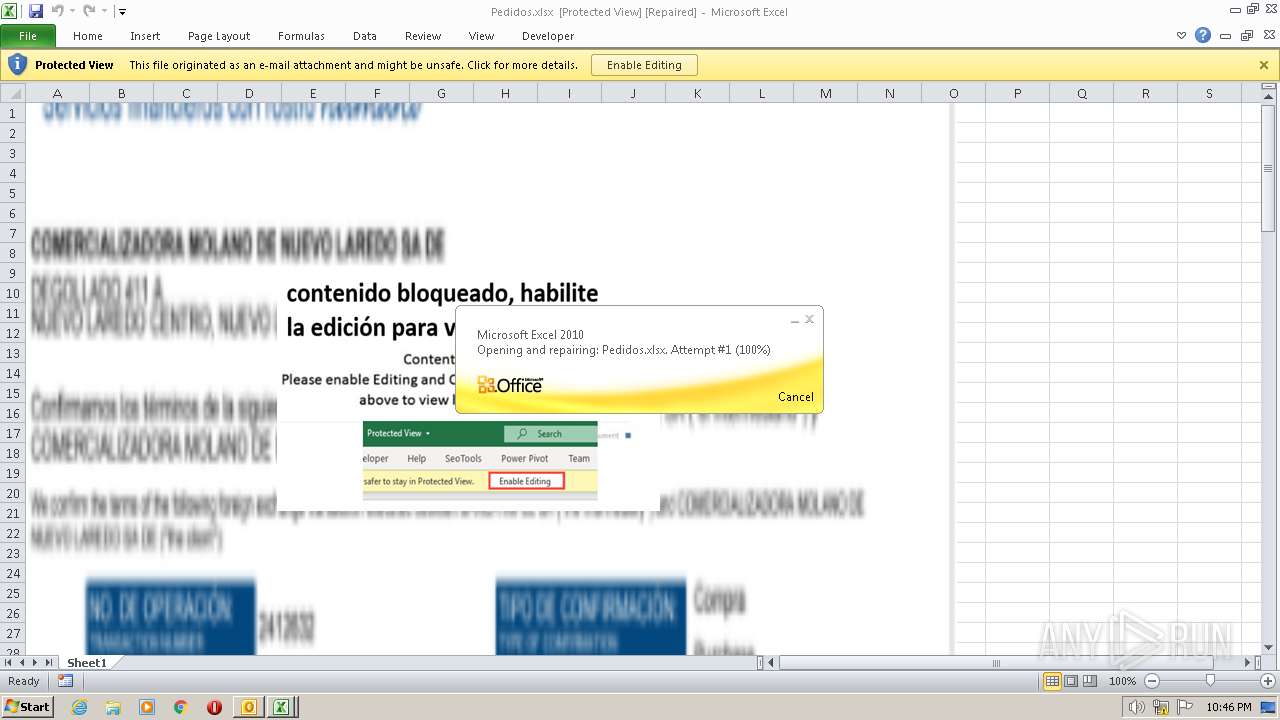
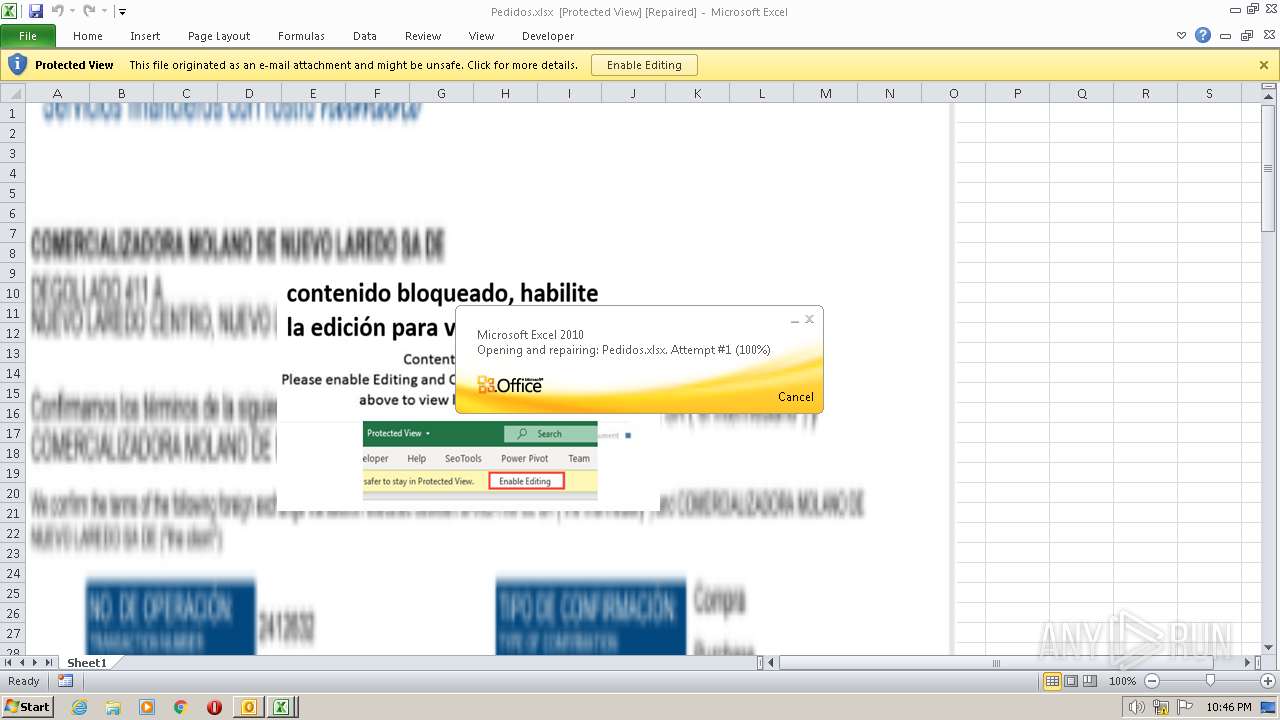
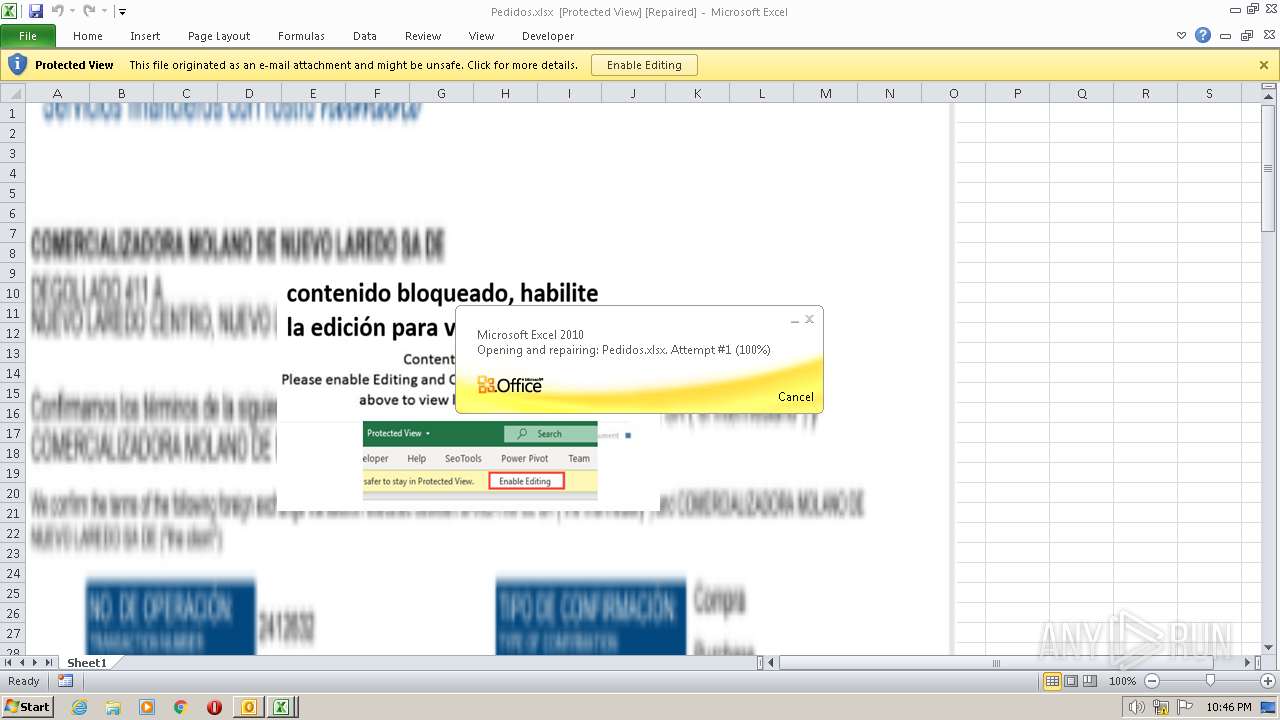
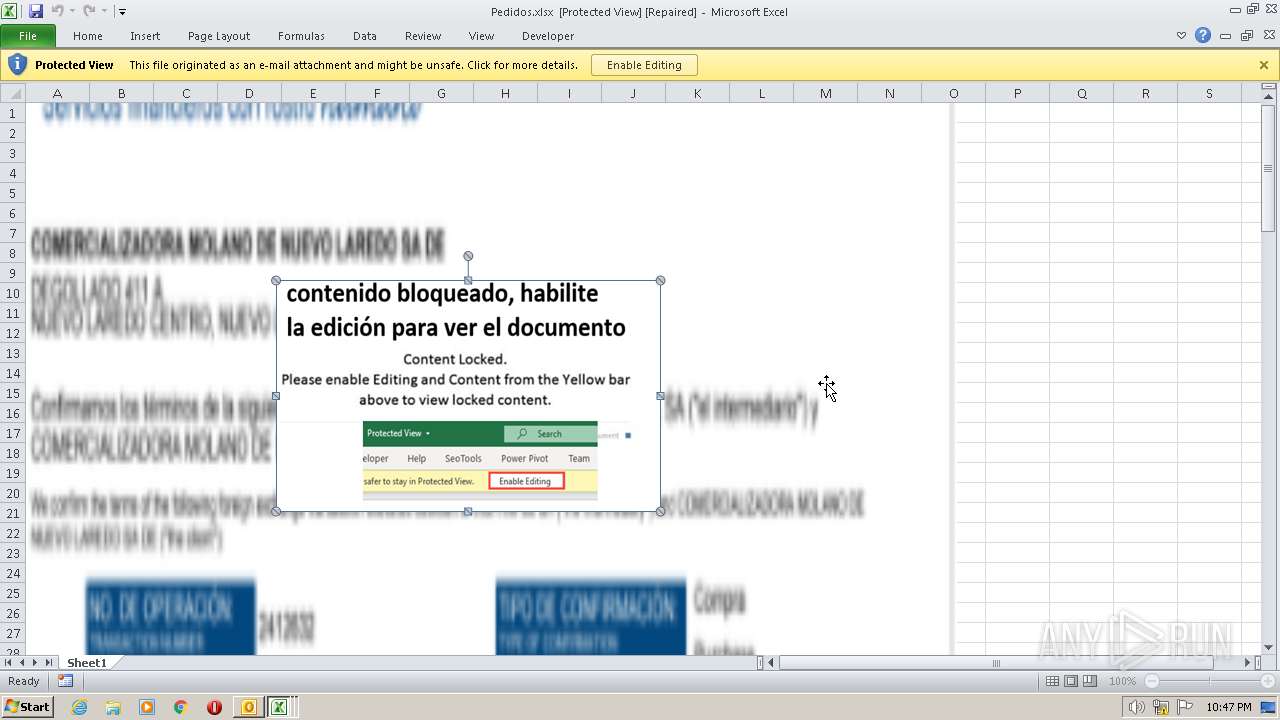
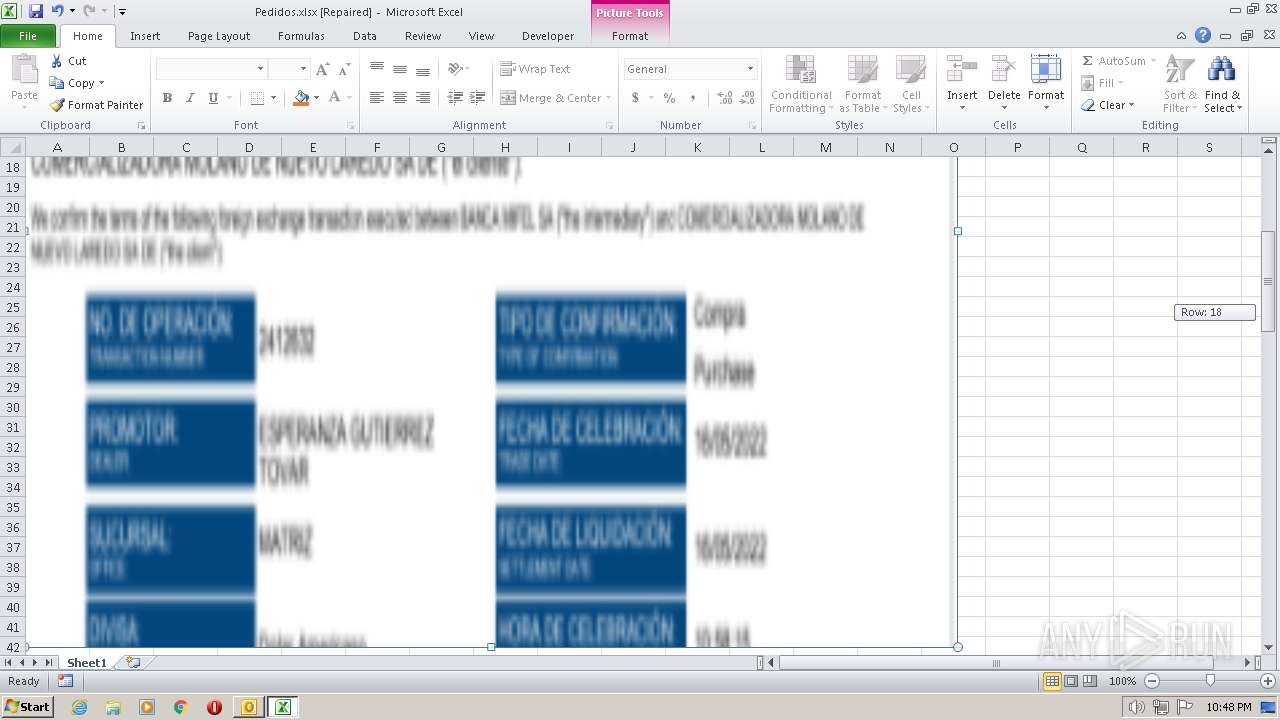
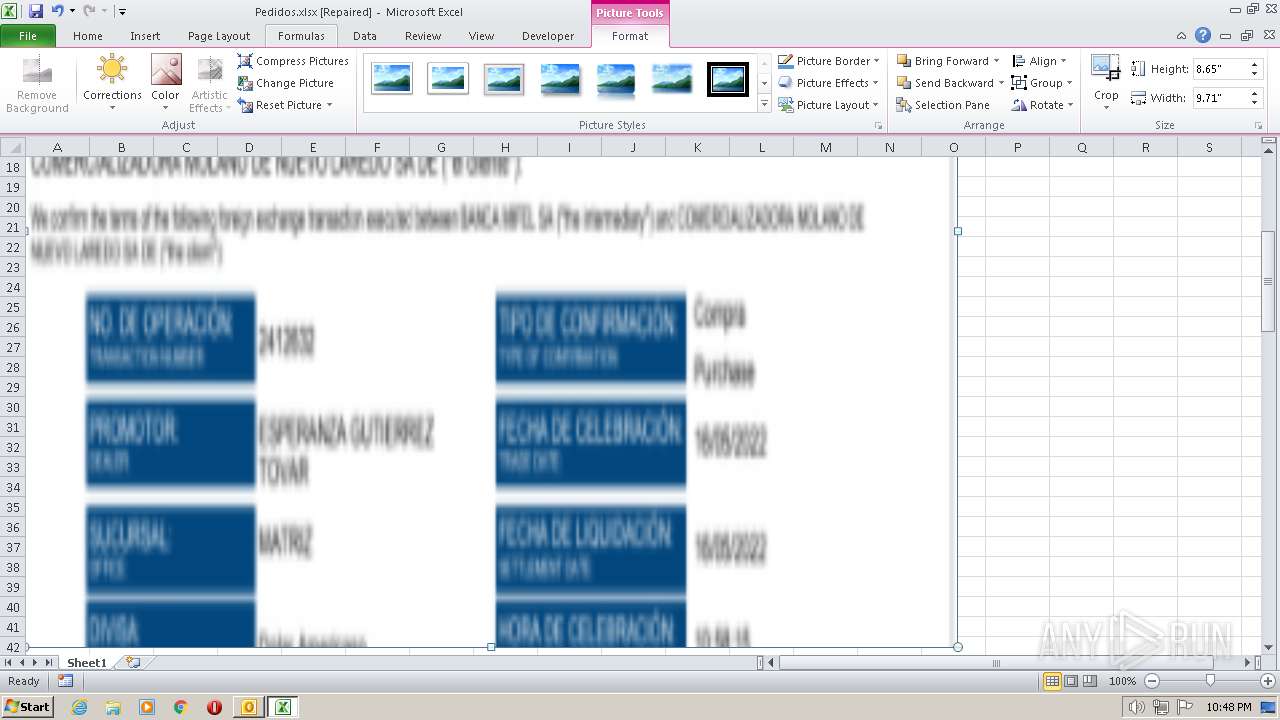
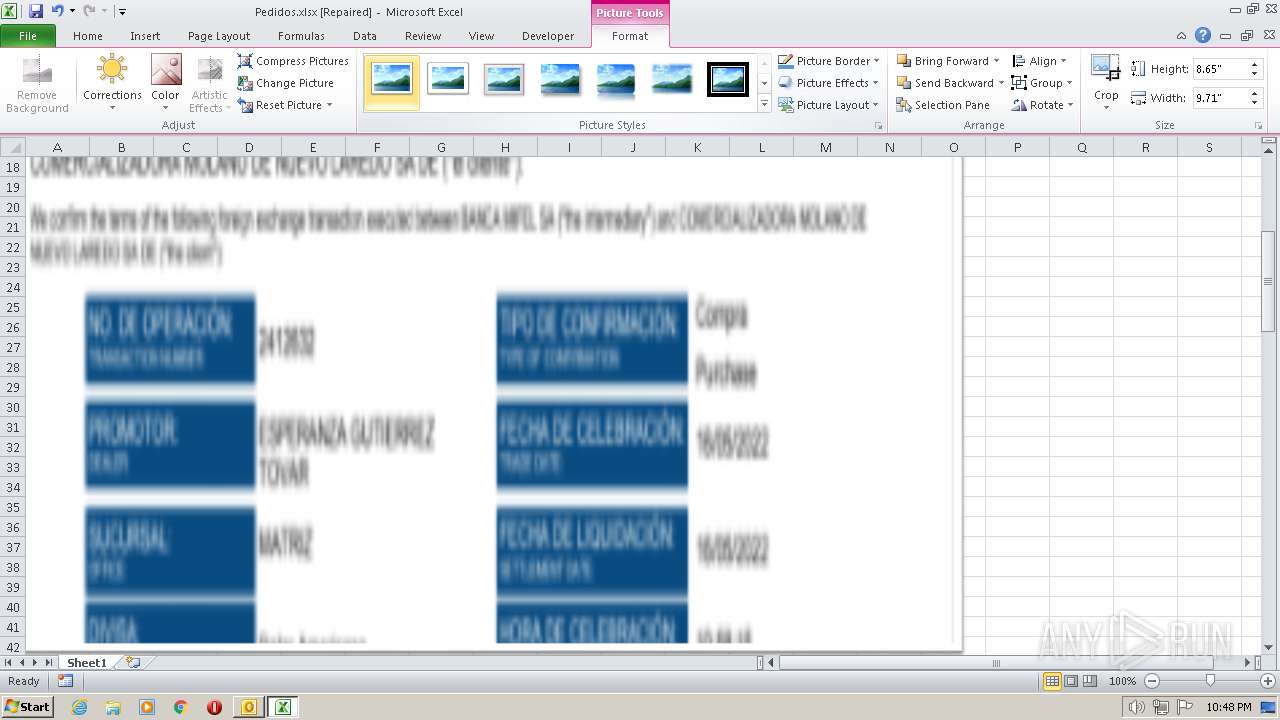
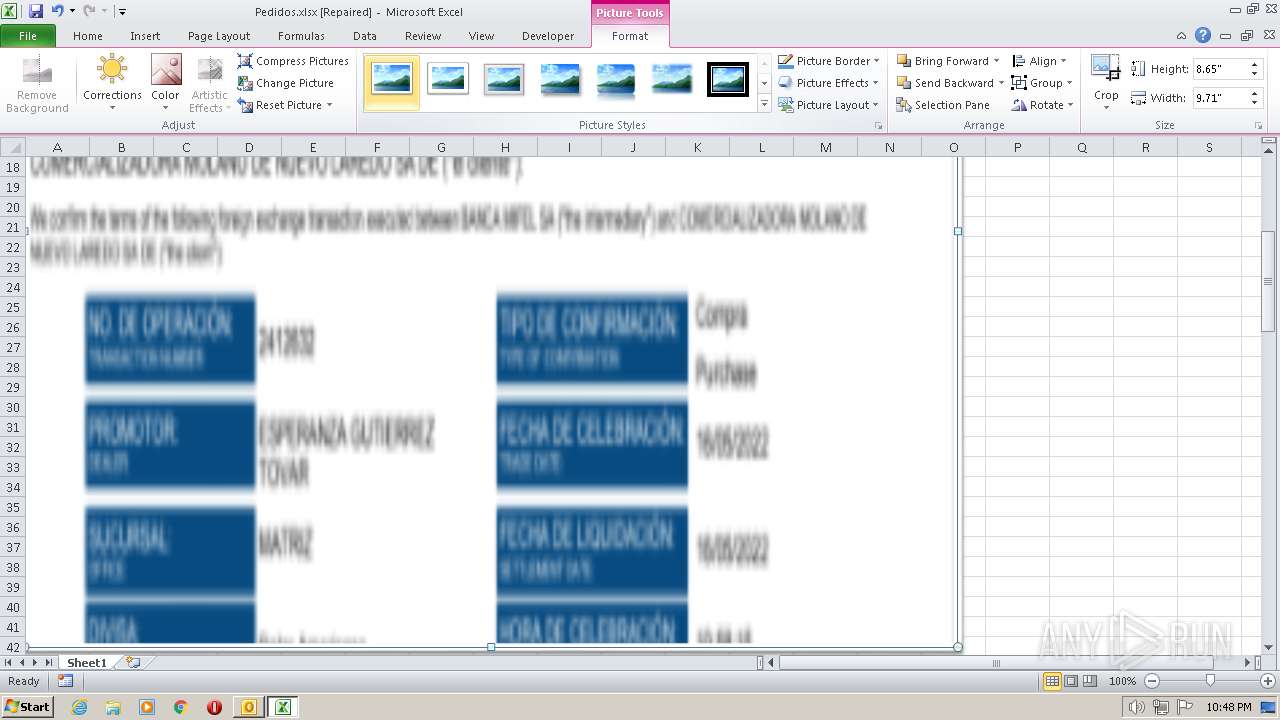
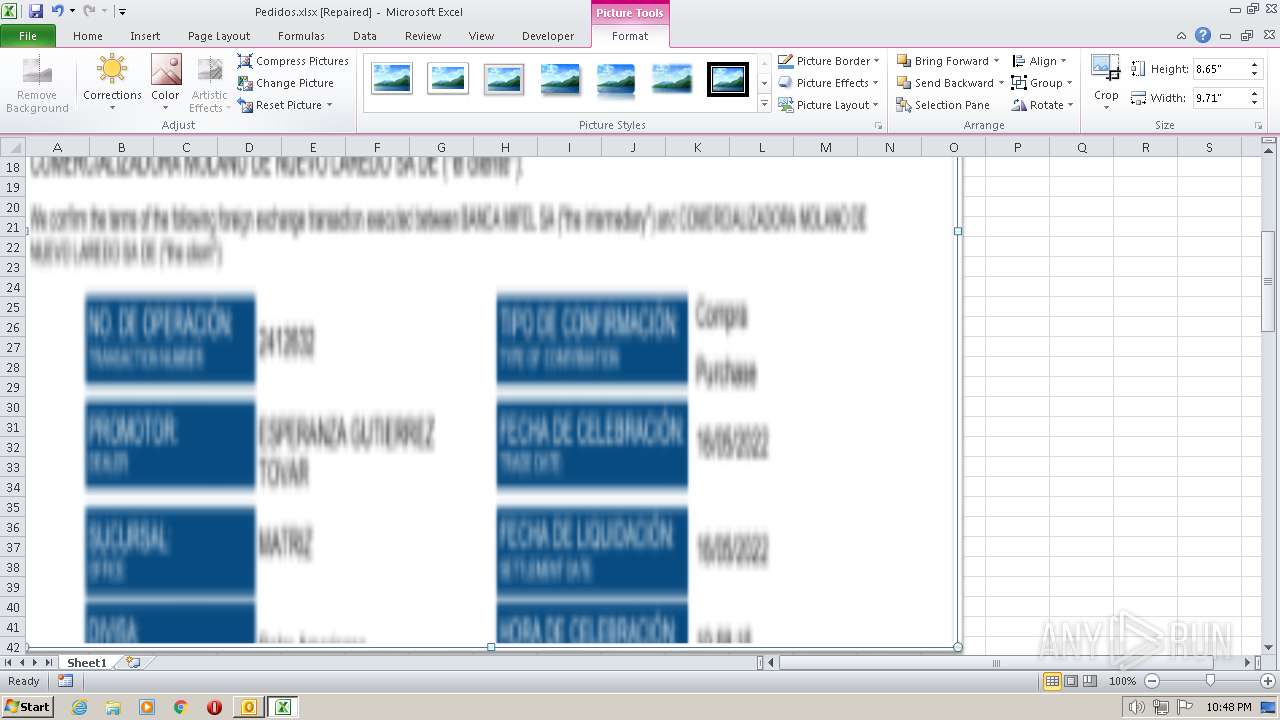
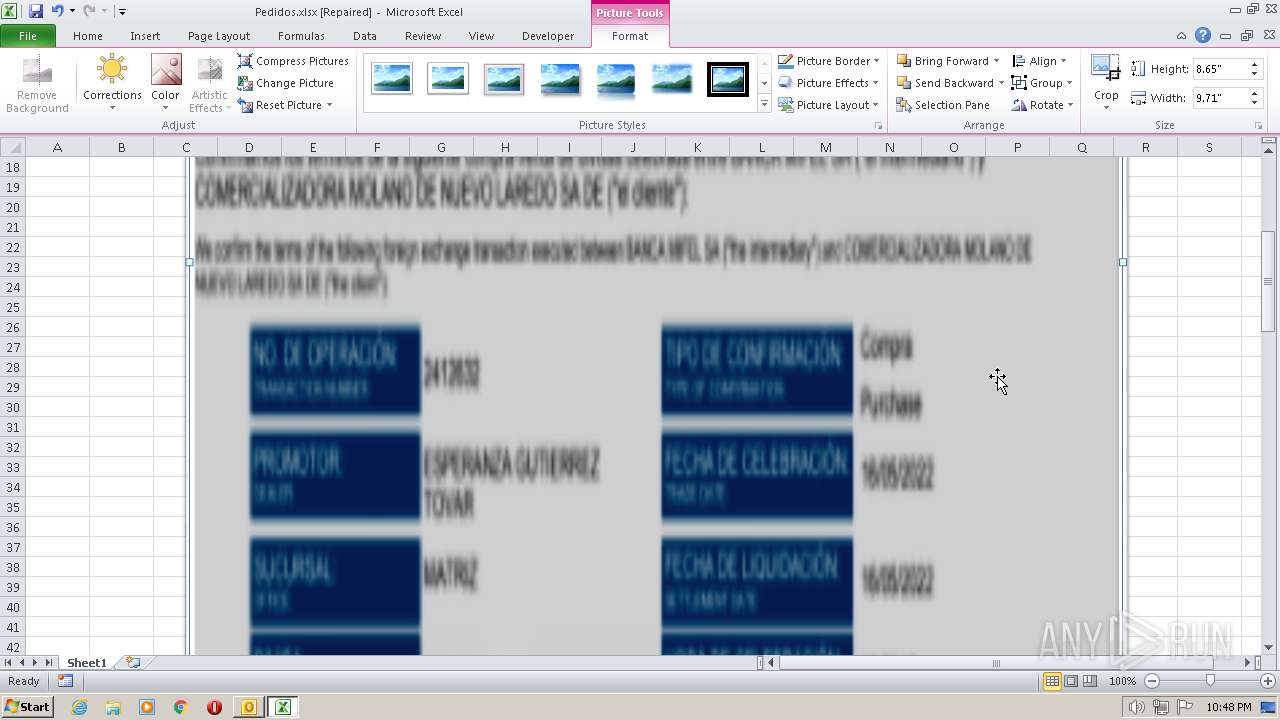
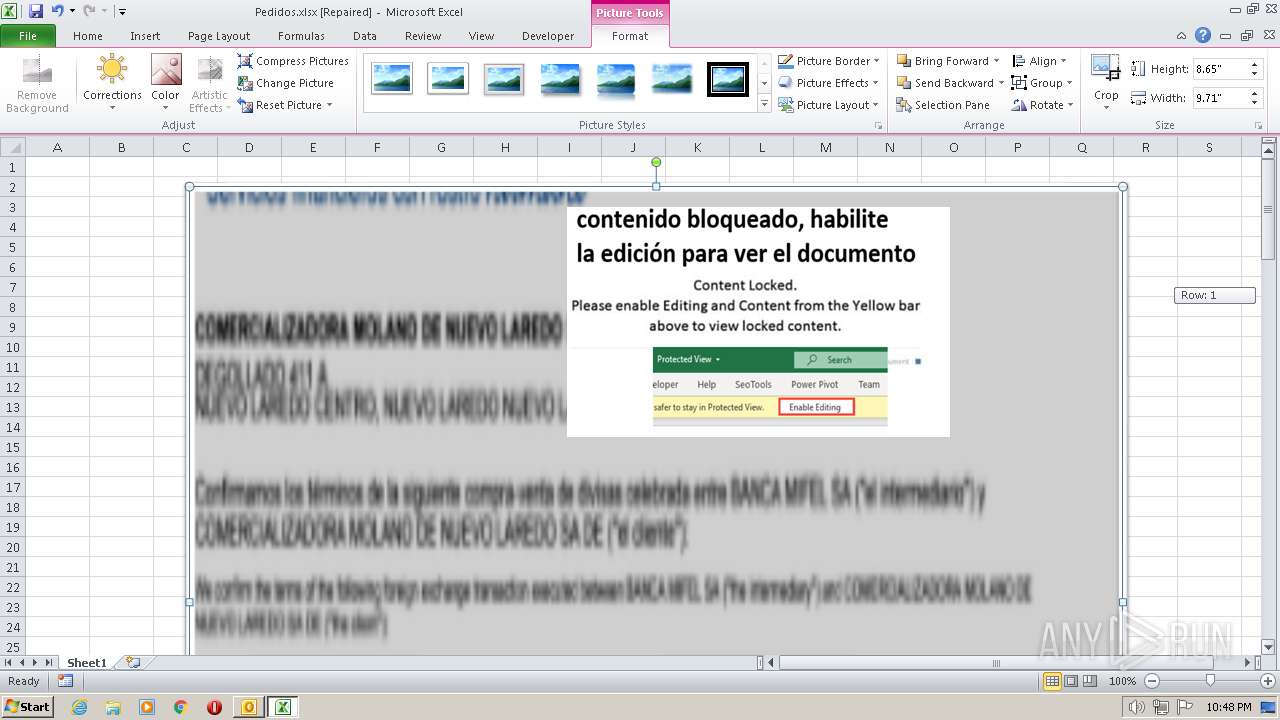
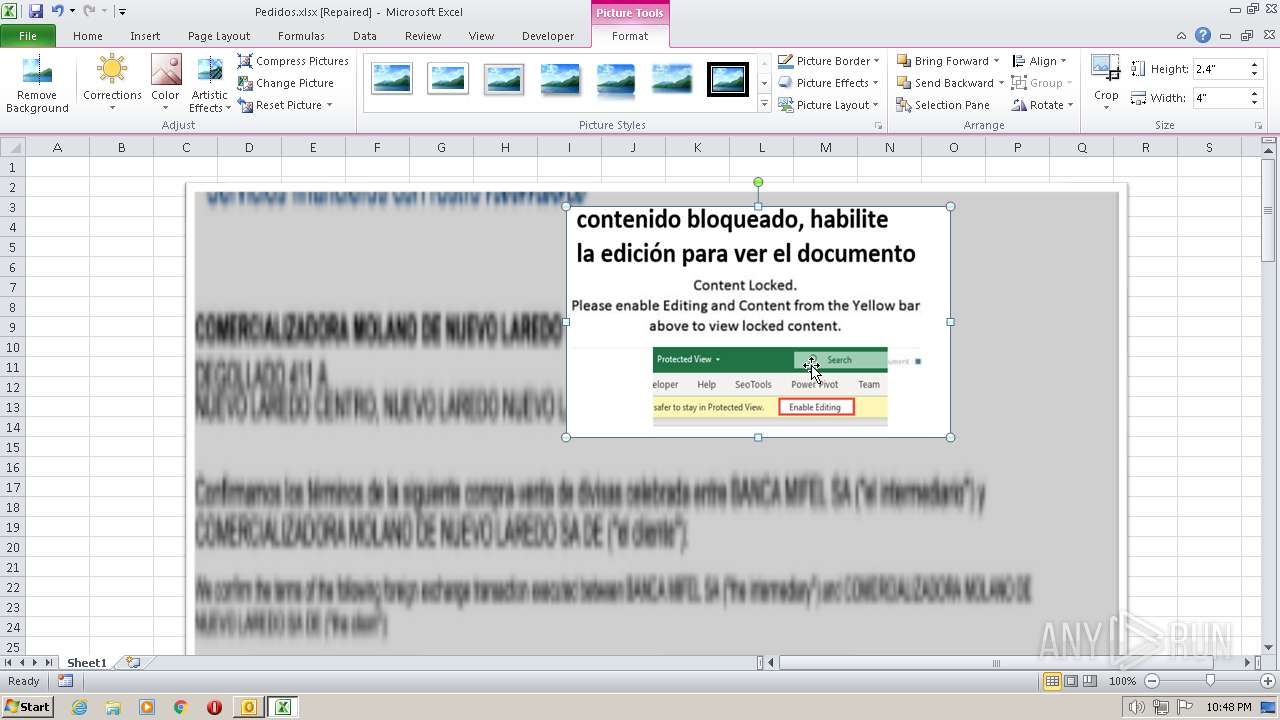
| File name: | ForwardedMessage.eml |
| Full analysis: | https://app.any.run/tasks/2a8d0d41-a928-424e-9818-19ece90c8f9e |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 14, 2023, 21:43:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text |
| MD5: | B4C8D3BC6B8B4876A861F26BFB264C67 |
| SHA1: | 11329F3DEA62180209DC441229D28561B38D1F87 |
| SHA256: | 8A5125FF2A9C2922C0823EC30384B12BA892FB6E8013FE8CB784DC54886C4F4A |
| SSDEEP: | 24576:zG5VQHb8IYI0v24GnpvNunvpYnFDKos27pN68l55LdXRxrRNc86V:KjQuTlvpYFDKaM659Pc8C |
MALICIOUS
Unusual connection from system programs
- wscript.exe (PID: 3140)
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 596)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 596)
Application was dropped or rewritten from another process
- mojooooo.exe (PID: 2016)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 3428)
AGENTTESLA was detected
- RegSvcs.exe (PID: 3428)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 3428)
SUSPICIOUS
Application launched itself
- EXCEL.EXE (PID: 2860)
Reads the Internet Settings
- EQNEDT32.EXE (PID: 596)
- wscript.exe (PID: 3140)
- RegSvcs.exe (PID: 3428)
- powershell.exe (PID: 2036)
Reads security settings of Internet Explorer
- EQNEDT32.EXE (PID: 596)
Checks Windows Trust Settings
- EQNEDT32.EXE (PID: 596)
Reads settings of System Certificates
- EQNEDT32.EXE (PID: 596)
The process executes VB scripts
- EQNEDT32.EXE (PID: 596)
Connects to the server without a host name
- wscript.exe (PID: 3140)
Process requests binary or script from the Internet
- wscript.exe (PID: 3140)
Executable content was dropped or overwritten
- wscript.exe (PID: 3140)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 3428)
Connects to FTP
- RegSvcs.exe (PID: 3428)
Connects to unusual port
- RegSvcs.exe (PID: 3428)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2036)
INFO
The process uses the downloaded file
- EXCEL.EXE (PID: 2860)
- OUTLOOK.EXE (PID: 2636)
Checks supported languages
- EQNEDT32.EXE (PID: 596)
- mojooooo.exe (PID: 2016)
- RegSvcs.exe (PID: 3428)
- wmpnscfg.exe (PID: 3324)
Reads the machine GUID from the registry
- EQNEDT32.EXE (PID: 596)
- mojooooo.exe (PID: 2016)
- RegSvcs.exe (PID: 3428)
- wmpnscfg.exe (PID: 3324)
Checks proxy server information
- EQNEDT32.EXE (PID: 596)
Reads the computer name
- EQNEDT32.EXE (PID: 596)
- mojooooo.exe (PID: 2016)
- wmpnscfg.exe (PID: 3324)
- RegSvcs.exe (PID: 3428)
The process checks LSA protection
- EQNEDT32.EXE (PID: 596)
- mojooooo.exe (PID: 2016)
- RegSvcs.exe (PID: 3428)
- wmpnscfg.exe (PID: 3324)
Creates files or folders in the user directory
- EQNEDT32.EXE (PID: 596)
Reads Environment values
- RegSvcs.exe (PID: 3428)
Manual execution by a user
- wmpnscfg.exe (PID: 3324)
- powershell.exe (PID: 2036)
- cmd.exe (PID: 2468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
55
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 596 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 2016 | "C:\Users\Public\mojooooo.exe" | C:\Users\Public\mojooooo.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WindowsApp1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2036 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2468 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2636 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\ForwardedMessage.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2860 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3140 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\squirelllll.vbs" | C:\Windows\System32\wscript.exe | EQNEDT32.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3324 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3428 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | mojooooo.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 3768 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
16 151
Read events
15 605
Write events
501
Delete events
45
Modification events
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2636) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
1
Suspicious files
23
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2636 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRCD9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2636 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2860 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR4CD0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2636 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_684C2B1AD2E9C44C86C19B7A06F170AD.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 2636 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpE70.tmp | binary | |
MD5:6E0D4255E52309D59B1198E77CA66E1C | SHA256:9946B06F403A9D2D5EC67BEEC65231B4F22DAAC50629DC5685BBE0678F440C90 | |||
| 2636 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2636 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{540B355E-EBEE-49C6-9CF9-4328209EEBF8}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 2636 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_515D3D060C2F0240AAEC79819CC7B07F.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 2636 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_5F7FCCA2E0CFE344AF4F46B63B0A6DED.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
| 2636 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ContactPrefs_2_D3D7DA169449964FAD9DD63D84D61055.dat | xml | |
MD5:BBCF400BD7AE536EB03054021D6A6398 | SHA256:383020065C1F31F4FB09F448599A6D5E532C390AF4E5B8AF0771FE17A23222AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
15
DNS requests
8
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
596 | EQNEDT32.EXE | GET | 200 | 142.250.185.195:80 | http://crl.pki.goog/gsr1/gsr1.crl | US | binary | 1.70 Kb | whitelisted |
3140 | wscript.exe | GET | 200 | 195.178.120.24:80 | http://195.178.120.24/mojo.payload_Encrypted.exe | unknown | executable | 2.71 Mb | malicious |
596 | EQNEDT32.EXE | GET | 200 | 142.250.185.195:80 | http://crl.pki.goog/gtsr1/gtsr1.crl | US | binary | 760 b | whitelisted |
596 | EQNEDT32.EXE | GET | 200 | 142.250.185.78:80 | http://crls.pki.goog/gts1c3/moVDfISia2k.crl | US | binary | 12.4 Kb | whitelisted |
1076 | svchost.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9455179915f1fe9c | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2636 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
596 | EQNEDT32.EXE | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
596 | EQNEDT32.EXE | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
596 | EQNEDT32.EXE | 142.250.185.78:80 | crls.pki.goog | GOOGLE | US | whitelisted |
596 | EQNEDT32.EXE | 172.217.23.106:443 | firebasestorage.googleapis.com | GOOGLE | US | whitelisted |
3140 | wscript.exe | 195.178.120.24:80 | — | Delis LLC | US | malicious |
3428 | RegSvcs.exe | 190.8.176.191:21 | ftp.papeleriaveneplast.com | Colombia Hosting | CO | malicious |
1076 | svchost.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
firebasestorage.googleapis.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
crl.pki.goog |
| whitelisted |
crls.pki.goog |
| whitelisted |
ftp.papeleriaveneplast.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3140 | wscript.exe | A Network Trojan was detected | ET HUNTING Download Request Containing Suspicious Filename - Crypted |
3140 | wscript.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3140 | wscript.exe | Potentially Bad Traffic | ET HUNTING Request for EXE via WinHTTP M1 |
3140 | wscript.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3140 | wscript.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3140 | wscript.exe | Misc activity | ET INFO WinHttpRequest Downloading EXE |
3428 | RegSvcs.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3428 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
3428 | RegSvcs.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
3428 | RegSvcs.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |