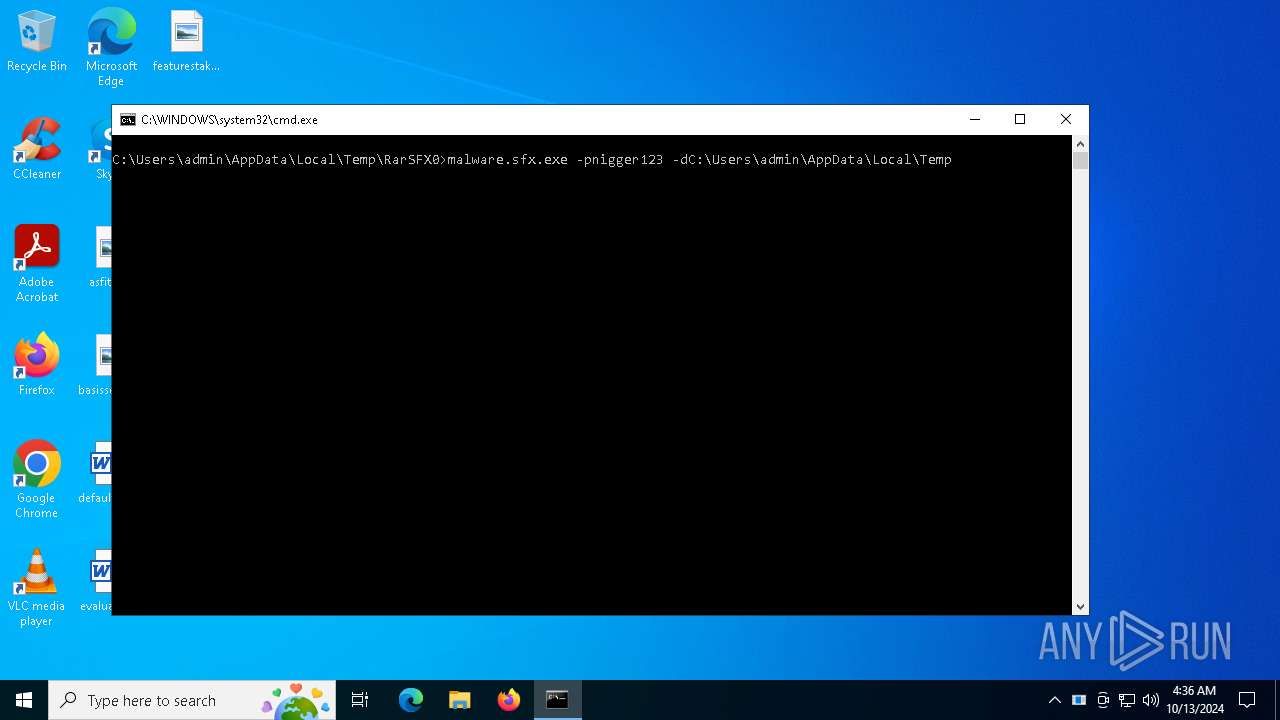
| File name: | RobuxGen.exe |
| Full analysis: | https://app.any.run/tasks/2322a5cc-af13-4cc6-a389-100d110920f6 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | October 13, 2024, 04:36:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | F8C6493BD89FFFF6F0772ACE8F2C2452 |
| SHA1: | 16F6C2F17398A7FD3F91B1C76017FE729C8F3E66 |
| SHA256: | 8A46C2B4862AD258880E56DDF82E367CEE61D0E8E198DD2EE1B7FE180AD280D2 |
| SSDEEP: | 98304:qM0F9FFwhsaYNm2hQubuN4mIDdA+ItTGOx3FpR4njt9XXZAb2W7vyGp422IoyyUf:F3 |
MALICIOUS
Connects to the CnC server
- Client.exe (PID: 6112)
QUASAR has been detected (SURICATA)
- Client.exe (PID: 6112)
ASYNCRAT has been detected (SURICATA)
- Client.exe (PID: 6112)
SUSPICIOUS
Reads security settings of Internet Explorer
- RobuxGen.exe (PID: 5892)
- malware.sfx.exe (PID: 6368)
- malware.exe (PID: 5932)
Reads the date of Windows installation
- RobuxGen.exe (PID: 5892)
- malware.sfx.exe (PID: 6368)
- malware.exe (PID: 5932)
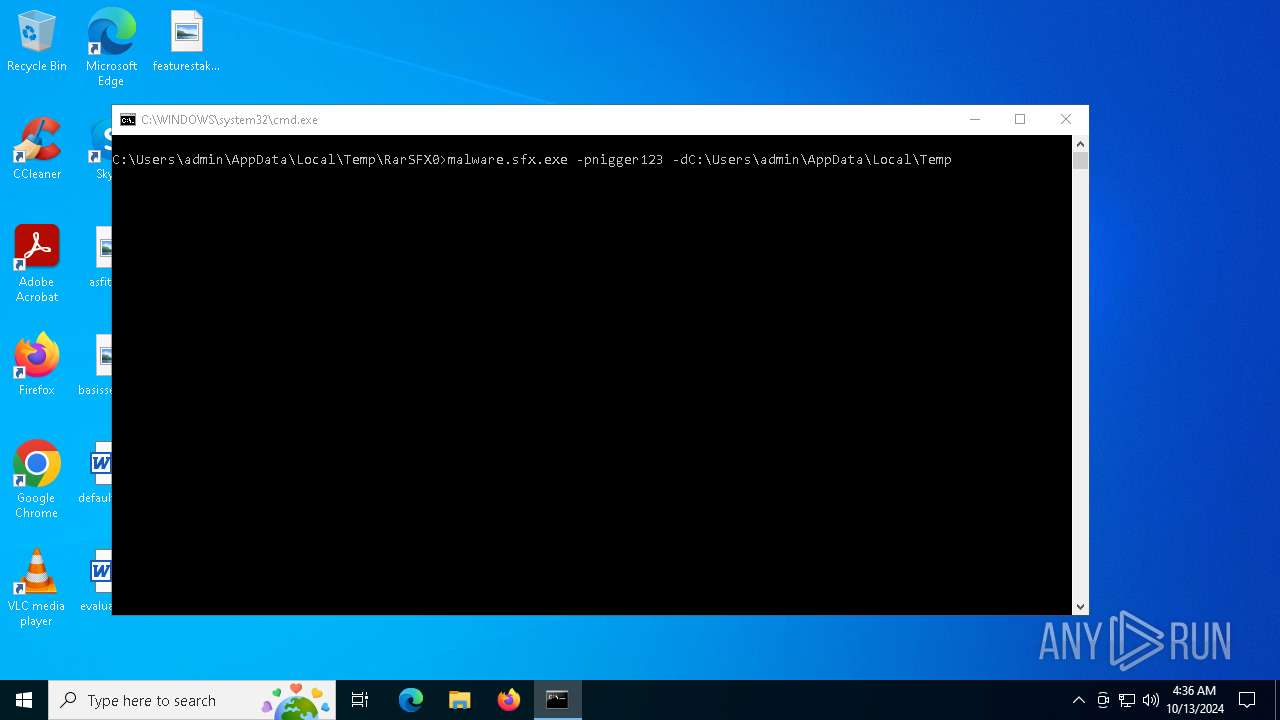
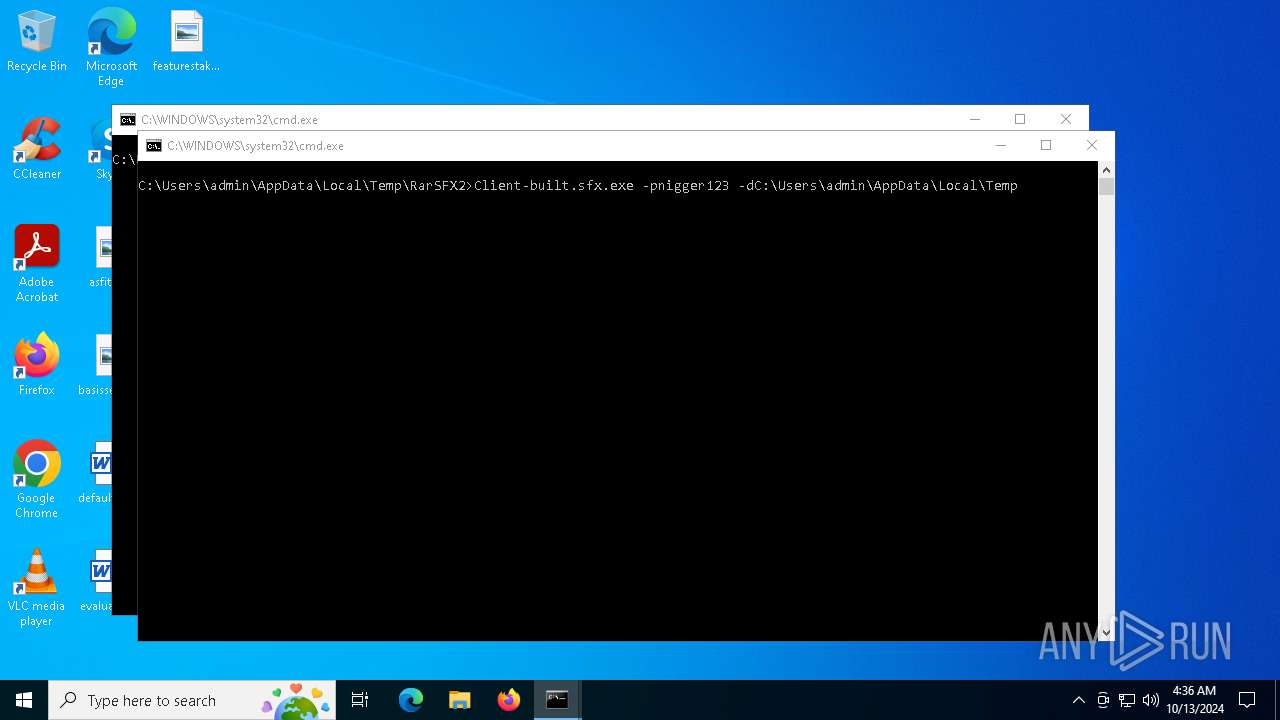
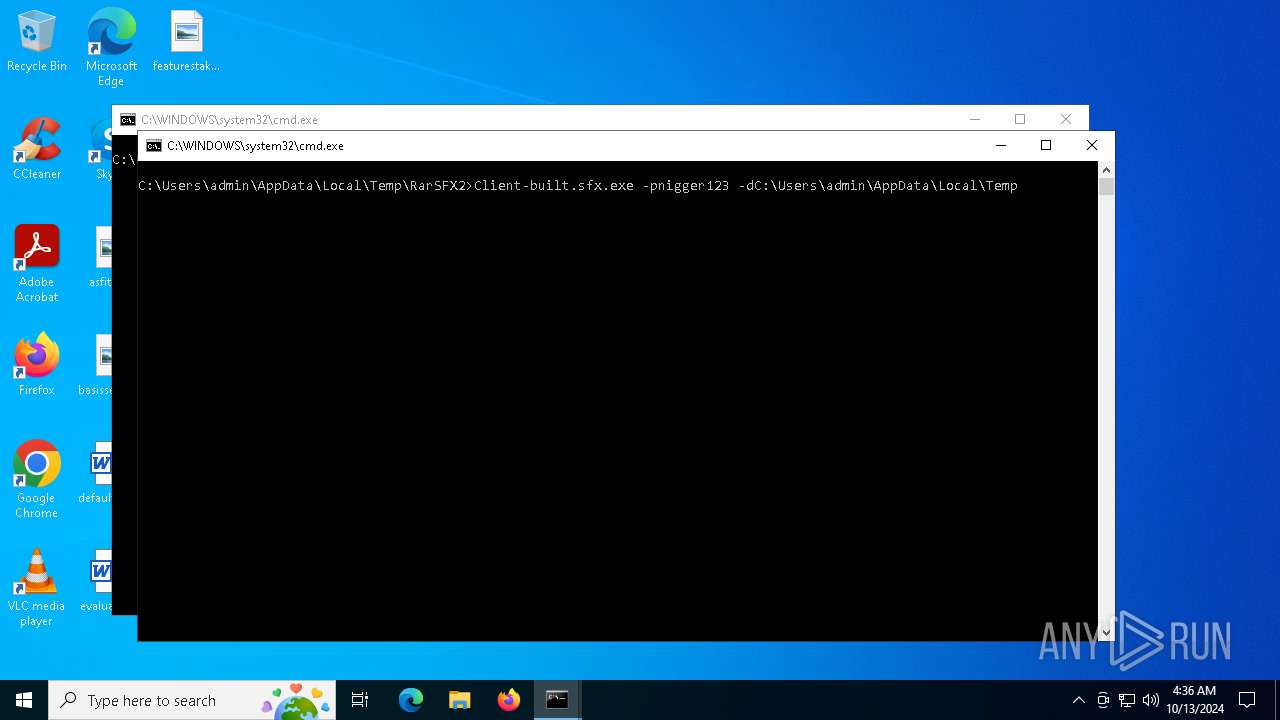
Executable content was dropped or overwritten
- RobuxGen.exe (PID: 5892)
- malware.sfx.exe (PID: 6368)
- malware.exe (PID: 5932)
- Client-built.sfx.exe (PID: 5512)
- Client-built.exe (PID: 4700)
Starts CMD.EXE for commands execution
- RobuxGen.exe (PID: 5892)
- malware.exe (PID: 5932)
The executable file from the user directory is run by the CMD process
- malware.sfx.exe (PID: 6368)
- Client-built.sfx.exe (PID: 5512)
Executing commands from a ".bat" file
- RobuxGen.exe (PID: 5892)
- malware.exe (PID: 5932)
The process checks if it is being run in the virtual environment
- malware.sfx.exe (PID: 6368)
Starts itself from another location
- malware.sfx.exe (PID: 6368)
- Client-built.exe (PID: 4700)
Checks for external IP
- svchost.exe (PID: 2172)
Contacting a server suspected of hosting an CnC
- Client.exe (PID: 6112)
Connects to unusual port
- Client.exe (PID: 6112)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2172)
INFO
Reads the computer name
- RobuxGen.exe (PID: 5892)
- malware.sfx.exe (PID: 6368)
- malware.exe (PID: 5932)
Checks supported languages
- RobuxGen.exe (PID: 5892)
- malware.sfx.exe (PID: 6368)
- malware.exe (PID: 5932)
Create files in a temporary directory
- RobuxGen.exe (PID: 5892)
- malware.sfx.exe (PID: 6368)
- malware.exe (PID: 5932)
- Client-built.sfx.exe (PID: 5512)
Process checks computer location settings
- RobuxGen.exe (PID: 5892)
- malware.sfx.exe (PID: 6368)
- malware.exe (PID: 5932)
The process uses the downloaded file
- RobuxGen.exe (PID: 5892)
- malware.sfx.exe (PID: 6368)
- malware.exe (PID: 5932)
- Client-built.sfx.exe (PID: 5512)
Manual execution by a user
- control.exe (PID: 7272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:12 10:17:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 288768 |
| InitializedDataSize: | 240128 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32ee0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
148
Monitored processes
14
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2576 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4348 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX0\nigger.bat" " | C:\Windows\System32\cmd.exe | — | RobuxGen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX2\nigger.bat" " | C:\Windows\System32\cmd.exe | — | malware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4700 | "C:\Users\admin\AppData\Local\Temp\RarSFX3\Client-built.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX3\Client-built.exe | Client-built.sfx.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 3 Version: 1.4.1 Modules
| |||||||||||||||
| 5512 | Client-built.sfx.exe -pnigger123 -dC:\Users\admin\AppData\Local\Temp | C:\Users\admin\AppData\Local\Temp\RarSFX2\Client-built.sfx.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5788 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | "C:\Users\admin\Desktop\RobuxGen.exe" | C:\Users\admin\Desktop\RobuxGen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5932 | "C:\Users\admin\AppData\Local\Temp\RarSFX1\malware.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX1\malware.exe | malware.sfx.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
8 529
Read events
8 505
Write events
24
Delete events
0
Modification events
| (PID) Process: | (5892) RobuxGen.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Users%admin%AppData%Local%Temp |
Value: C:\Users\admin\AppData\Local\Temp\RarSFX0 | |||
| (PID) Process: | (6368) malware.sfx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Users%admin%AppData%Local%Temp |
Value: C:\Users\admin\AppData\Local\Temp\RarSFX1 | |||
| (PID) Process: | (5932) malware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Users%admin%AppData%Local%Temp |
Value: C:\Users\admin\AppData\Local\Temp\RarSFX2 | |||
| (PID) Process: | (5512) Client-built.sfx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Users%admin%AppData%Local%Temp |
Value: C:\Users\admin\AppData\Local\Temp\RarSFX3 | |||
| (PID) Process: | (4700) Client-built.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Quasar Client Startup |
Value: "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" | |||
| (PID) Process: | (6112) Client.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Quasar Client Startup |
Value: "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" | |||
| (PID) Process: | (6112) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6112) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6112) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6112) Client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
5
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5892 | RobuxGen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\malware.sfx.exe | executable | |
MD5:FE021B0ABBE000D88B86120E8294ADA1 | SHA256:4CC4FAE7FCE5E20E48586A2B9241C130265191AA98289E6D3078B0FFB28748E6 | |||
| 5932 | malware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX2\Client-built.sfx.exe | executable | |
MD5:CAAA2F7465CD0743E2212A8038FB64E7 | SHA256:FC1869069FF57271E06B11C39B1330AA0C0B182510215ACD790B6DC95EF9FA55 | |||
| 4700 | Client-built.exe | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | executable | |
MD5:D150FB4AAD5ECF35963DE074D8598C72 | SHA256:08DDB469A286FB6F030E4449945329AE9AABA9A59205F9B31D2C9D8923EB7545 | |||
| 5932 | malware.exe | C:\Users\admin\AppData\Local\Temp\RarSFX2\nigger.bat | text | |
MD5:E4A7BE8D6F8CDF094D84E363BAFD0CA1 | SHA256:392596A5E8CC973D5818F481B63E4C9DAAB60AA3881AF50A312A043D2FF764C8 | |||
| 6368 | malware.sfx.exe | C:\Users\admin\AppData\Local\Temp\RarSFX1\malware.exe | executable | |
MD5:F0CA0A8C42B9CBDFA84D7C5A522E4B15 | SHA256:8422A06D128D35C64163C2763C53F7C7C57AD6E1A721C1B74325149FAAD58D37 | |||
| 5892 | RobuxGen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\nigger.bat | text | |
MD5:EDEA6BA343BDE8C086E716CF5C192C20 | SHA256:1B1F7A1C17A28C2D894CC15DDF71DCA06A01EFFA17A2F87F9CB9A658DB15E4F4 | |||
| 5512 | Client-built.sfx.exe | C:\Users\admin\AppData\Local\Temp\RarSFX3\Client-built.exe | executable | |
MD5:D150FB4AAD5ECF35963DE074D8598C72 | SHA256:08DDB469A286FB6F030E4449945329AE9AABA9A59205F9B31D2C9D8923EB7545 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
83
DNS requests
27
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5824 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6956 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4448 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4448 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2372 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4080 | RUXIMICS.exe | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6112 | Client.exe | 193.161.193.99:56944 | jarredsteven-56944.portmap.host | OOO Bitree Networks | RU | malicious |
6112 | Client.exe | 195.201.57.90:443 | ipwho.is | Hetzner Online GmbH | DE | malicious |
4360 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5824 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
jarredsteven-56944.portmap.host |
| malicious |
ipwho.is |
| malicious |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query to a Reverse Proxy Service Observed |
2172 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .host) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain in DNS Lookup (ipwho .is) |
6112 | Client.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
6112 | Client.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (Quasar CnC) |
6112 | Client.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] QuasarRAT Successful Connection (GCM_SHA384) |