| File name: | MT103paymentTransfer_pdf.exe.pellet |
| Full analysis: | https://app.any.run/tasks/b0910812-e05a-47bf-97f2-3f629263c5e7 |
| Verdict: | Malicious activity |
| Threats: | DBatLoader is a loader malware used for distributing payloads of different types, including WarzoneRAT and Formbook. It is employed in multi-stage attacks that usually start with a phishing email carrying a malicious attachment. |
| Analysis date: | May 19, 2025, 11:54:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 9 sections |
| MD5: | 2CDAC9B8BC9D7B5372BF63D301FBEEA7 |
| SHA1: | 7AF8B752012EF1A65EB5F7C987B0D098F6E1B6FF |
| SHA256: | 89AE873321570C07C0ED41B0F38DB3BA00B9EAA539AE11EDC87CD40723D44743 |
| SSDEEP: | 49152:7WMwHm/hBS00g5ijJEaoebbVGOQwKFiQMnEgn7xnGZQ96RcdDkn4nJ:7Z/70NE7IPQwKsQaEVEdDRJ |
MALICIOUS
DBATLOADER has been detected (YARA)
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
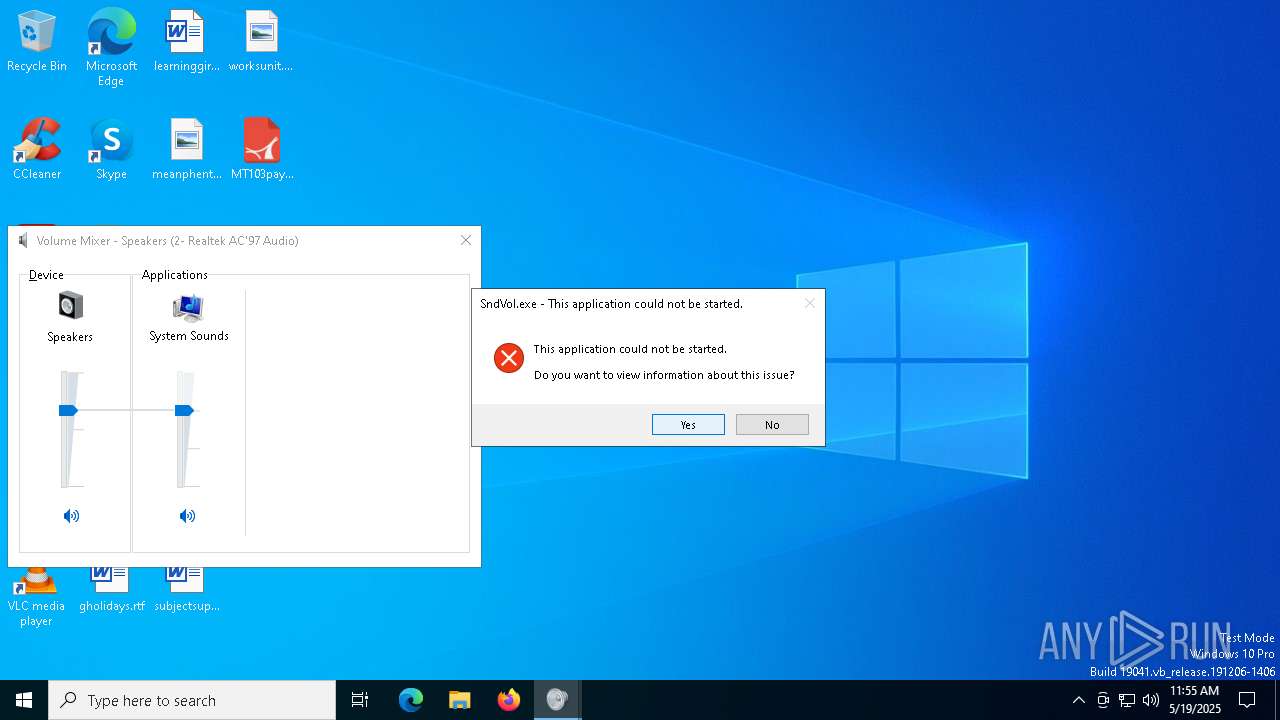
SNAKE has been detected (YARA)
- SndVol.exe (PID: 7812)
SUSPICIOUS
Executable content was dropped or overwritten
- esentutl.exe (PID: 7712)
Drops a file with a rarely used extension (PIF)
- esentutl.exe (PID: 7712)
Likely accesses (executes) a file from the Public directory
- esentutl.exe (PID: 7712)
- alpha.pif (PID: 7744)
- alpha.pif (PID: 7764)
There is functionality for taking screenshot (YARA)
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
Starts CMD.EXE for commands execution
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7588)
Executing commands from ".cmd" file
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
Reads security settings of Internet Explorer
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
Starts itself from another location
- cmd.exe (PID: 7540)
Created directory related to system
- alpha.pif (PID: 7744)
Starts a Microsoft application from unusual location
- alpha.pif (PID: 7744)
- alpha.pif (PID: 7764)
Starts application with an unusual extension
- cmd.exe (PID: 7540)
INFO
Reads the computer name
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
- identity_helper.exe (PID: 660)
The sample compiled with english language support
- esentutl.exe (PID: 7712)
Compiled with Borland Delphi (YARA)
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
Creates files in the program directory
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
Checks supported languages
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
- alpha.pif (PID: 7744)
- alpha.pif (PID: 7764)
- identity_helper.exe (PID: 660)
Checks proxy server information
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
- slui.exe (PID: 4728)
Reads the machine GUID from the registry
- MT103paymentTransfer_pdf.exe.pellet.exe (PID: 7304)
Application launched itself
- msedge.exe (PID: 7892)
Reads Environment values
- identity_helper.exe (PID: 660)
Manual execution by a user
- msedge.exe (PID: 7468)
Reads the software policy settings
- slui.exe (PID: 4728)
Reads security settings of Internet Explorer
- SndVol.exe (PID: 7812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
SnakeKeylogger
(PID) Process(7812) SndVol.exe
Keys
DES6fc98cd68a1aab8b
Options
SMTP Userreport2log@tonicables.top
SMTP Password7213575aceACE@
SMTP Hostmail.tonicables.top
SMTP SendToreport2@tonicables.top
SMTP Port587
TRiD
| .exe | | | InstallShield setup (53.2) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (17.5) |
| .scr | | | Windows screen saver (16.1) |
| .exe | | | Win32 Executable (generic) (5.5) |
| .exe | | | Win16/32 Executable Delphi generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 428544 |
| InitializedDataSize: | 1201664 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x69814 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
185
Monitored processes
63
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6572 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 664 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=6760 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=40 --mojo-platform-channel-handle=4432 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1912 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --mojo-platform-channel-handle=5400 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6836 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2104 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=41 --mojo-platform-channel-handle=5952 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2316 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7276 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2984 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3680 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3192 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=28 --mojo-platform-channel-handle=5480 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3676 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=4476 --field-trial-handle=2472,i,3188682927217043653,8694422715926588795,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
9 386
Read events
9 336
Write events
50
Delete events
0
Modification events
| (PID) Process: | (7812) SndVol.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7812) SndVol.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7812) SndVol.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7812) SndVol.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7892) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 0CB7611712942F00 | |||
| (PID) Process: | (7236) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
7
Suspicious files
213
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF11726e.TMP | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11727d.TMP | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF11729d.TMP | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF11729d.TMP | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF11729d.TMP | — | |
MD5:— | SHA256:— | |||
| 7892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
140
DNS requests
89
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1600 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747700501&P2=404&P3=2&P4=RGi7Wk%2f3hFzPf4ESrzINKr%2bcf6Vhhw6FpEH%2f3sD1D9dRdWYwvJj0RsHY88PSxpf2rAbFrv%2bMNjonjHPT20xBtQ%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747700501&P2=404&P3=2&P4=RGi7Wk%2f3hFzPf4ESrzINKr%2bcf6Vhhw6FpEH%2f3sD1D9dRdWYwvJj0RsHY88PSxpf2rAbFrv%2bMNjonjHPT20xBtQ%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747700501&P2=404&P3=2&P4=RGi7Wk%2f3hFzPf4ESrzINKr%2bcf6Vhhw6FpEH%2f3sD1D9dRdWYwvJj0RsHY88PSxpf2rAbFrv%2bMNjonjHPT20xBtQ%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747700501&P2=404&P3=2&P4=RGi7Wk%2f3hFzPf4ESrzINKr%2bcf6Vhhw6FpEH%2f3sD1D9dRdWYwvJj0RsHY88PSxpf2rAbFrv%2bMNjonjHPT20xBtQ%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747700501&P2=404&P3=2&P4=RGi7Wk%2f3hFzPf4ESrzINKr%2bcf6Vhhw6FpEH%2f3sD1D9dRdWYwvJj0RsHY88PSxpf2rAbFrv%2bMNjonjHPT20xBtQ%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747700501&P2=404&P3=2&P4=RGi7Wk%2f3hFzPf4ESrzINKr%2bcf6Vhhw6FpEH%2f3sD1D9dRdWYwvJj0RsHY88PSxpf2rAbFrv%2bMNjonjHPT20xBtQ%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747700501&P2=404&P3=2&P4=RGi7Wk%2f3hFzPf4ESrzINKr%2bcf6Vhhw6FpEH%2f3sD1D9dRdWYwvJj0RsHY88PSxpf2rAbFrv%2bMNjonjHPT20xBtQ%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747700501&P2=404&P3=2&P4=RGi7Wk%2f3hFzPf4ESrzINKr%2bcf6Vhhw6FpEH%2f3sD1D9dRdWYwvJj0RsHY88PSxpf2rAbFrv%2bMNjonjHPT20xBtQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
8132 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8132 | msedge.exe | 150.171.30.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8132 | msedge.exe | 40.90.65.40:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
go.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
learn.microsoft.com |
| whitelisted |