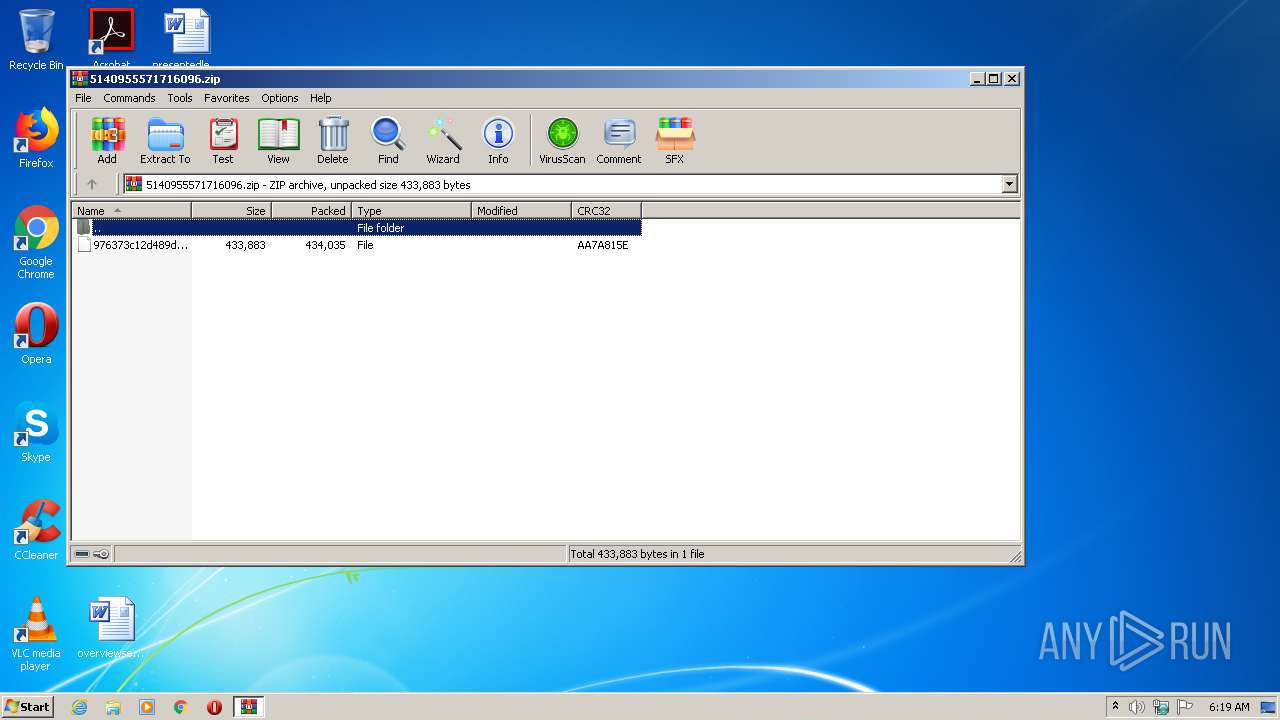
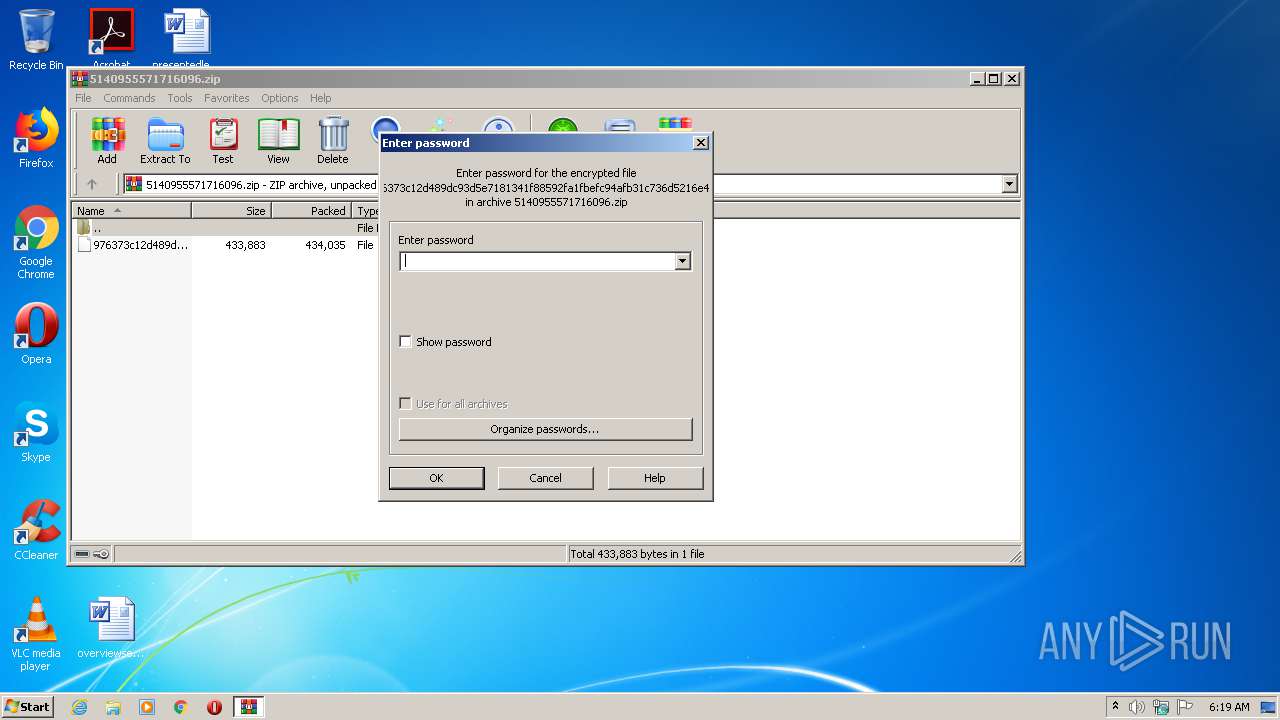
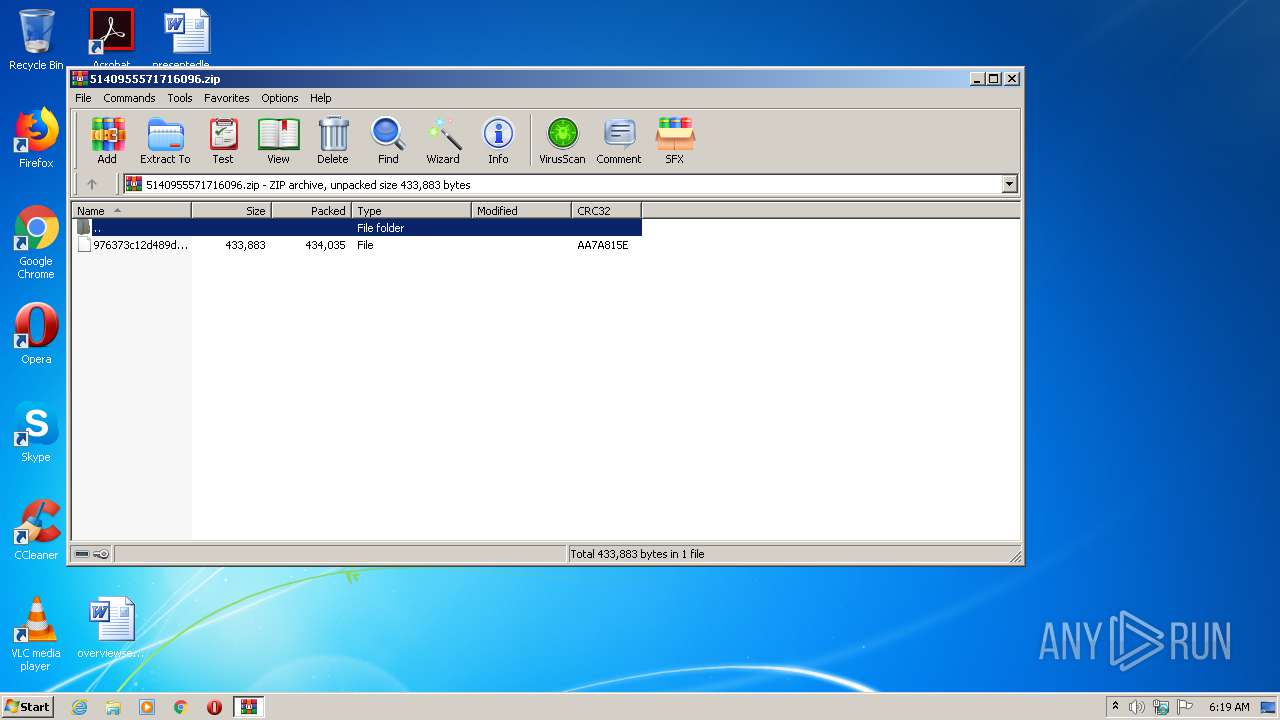
| File name: | 5140955571716096.zip |
| Full analysis: | https://app.any.run/tasks/e25f40ee-18c8-42bf-b008-852a7485b8ca |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 13, 2020, 05:19:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 588C1E9F7727708582B996D23AC0C46A |
| SHA1: | 7ABA276916EAE024266F2DB87CD8B6AD78B25042 |
| SHA256: | 89AB2FB109934256696C54D45ED078B6693A9C06859C27DB4D3D0BF355E4B8BD |
| SSDEEP: | 12288:ZrJtHDABhS1ZHbfMD1BNokLS3kKYanuGx0ptIcMlLyQ:ZrDDABhAHrUOkO3kKYa9MAGQ |
MALICIOUS
Application was dropped or rewritten from another process
- Informative Program on.exe (PID: 3008)
- Informative Program on.exe (PID: 2800)
Disables Windows Defender
- Informative Program on.exe (PID: 3008)
Changes the autorun value in the registry
- Informative Program on.exe (PID: 2800)
AGENTTESLA detected
- Informative Program on.exe (PID: 2800)
Actions looks like stealing of personal data
- Informative Program on.exe (PID: 2800)
Changes settings of System certificates
- Informative Program on.exe (PID: 2800)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3668)
- Informative Program on.exe (PID: 2800)
Executes PowerShell scripts
- Informative Program on.exe (PID: 3008)
Creates files in the user directory
- Informative Program on.exe (PID: 2800)
- powershell.exe (PID: 3196)
Reads the BIOS version
- Informative Program on.exe (PID: 3008)
Application launched itself
- Informative Program on.exe (PID: 3008)
Adds / modifies Windows certificates
- Informative Program on.exe (PID: 2800)
INFO
Manual execution by user
- WinRAR.exe (PID: 3668)
- Informative Program on.exe (PID: 3008)
Reads settings of System Certificates
- Informative Program on.exe (PID: 2800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xaa7a815e |
| ZipCompressedSize: | 434035 |
| ZipUncompressedSize: | 433883 |
| ZipFileName: | 976373c12d489dc93d5e7181341f88592fa1fbefc94afb31c736d5216e414717 |
Total processes
46
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2800 | "{path}" | C:\Users\admin\Desktop\Informative Program on.exe | Informative Program on.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: SectorBoot Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3008 | "C:\Users\admin\Desktop\Informative Program on.exe" | C:\Users\admin\Desktop\Informative Program on.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: SectorBoot Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3160 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\5140955571716096.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3196 | "powershell" Get-MpPreference -verbose | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Informative Program on.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3668 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\a.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 976
Read events
703
Write events
1 273
Delete events
0
Modification events
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\5140955571716096.zip | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
3
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2GIH4P8ALXP2JJ7LUM28.temp | — | |
MD5:— | SHA256:— | |||
| 3160 | WinRAR.exe | C:\Users\admin\Desktop\976373c12d489dc93d5e7181341f88592fa1fbefc94afb31c736d5216e414717 | compressed | |
MD5:— | SHA256:— | |||
| 3196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2800 | Informative Program on.exe | C:\Users\admin\AppData\Local\Temp\8c93c1c9-290c-4e82-a5a2-4e3075d8078f | sqlite | |
MD5:— | SHA256:— | |||
| 2800 | Informative Program on.exe | C:\Users\admin\AppData\Roaming\mtpktKu\xkqNT.exe | executable | |
MD5:— | SHA256:— | |||
| 3196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF28854a.TMP | binary | |
MD5:— | SHA256:— | |||
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Informative Program on.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2800 | Informative Program on.exe | 85.17.28.200:587 | mail.ppe-eg.com | LeaseWeb Netherlands B.V. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mail.ppe-eg.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2800 | Informative Program on.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |