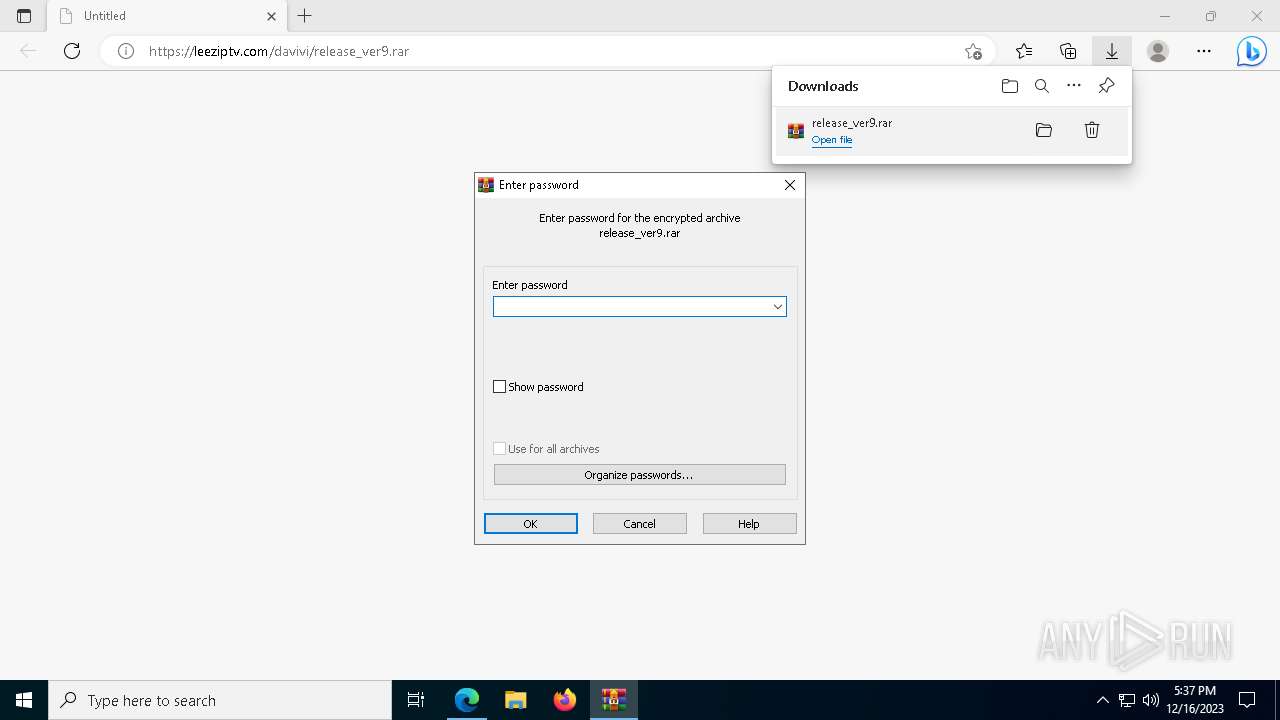
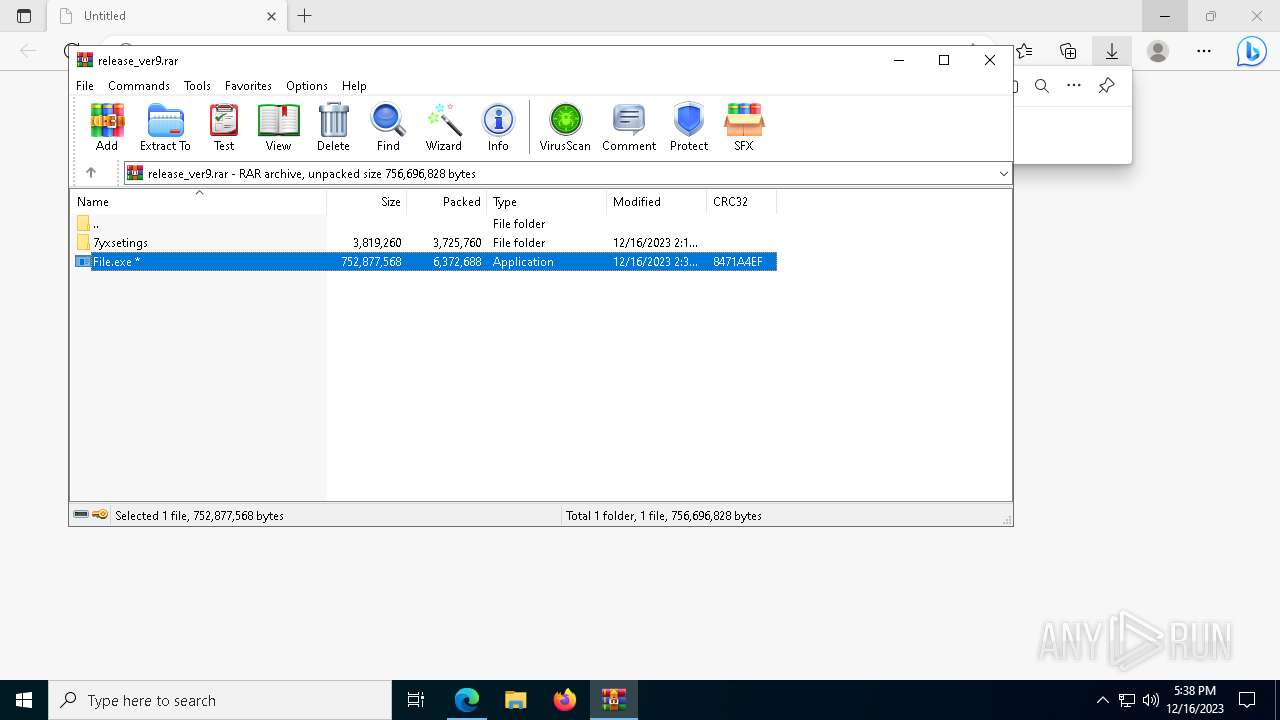
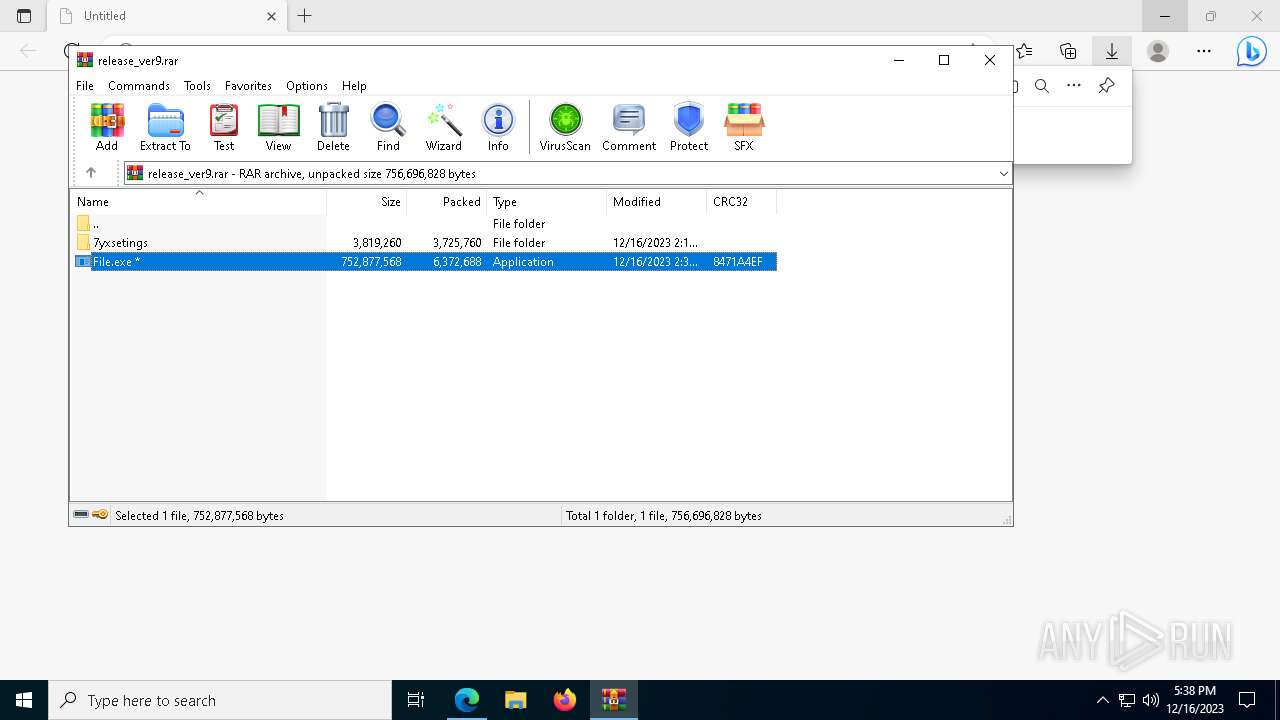
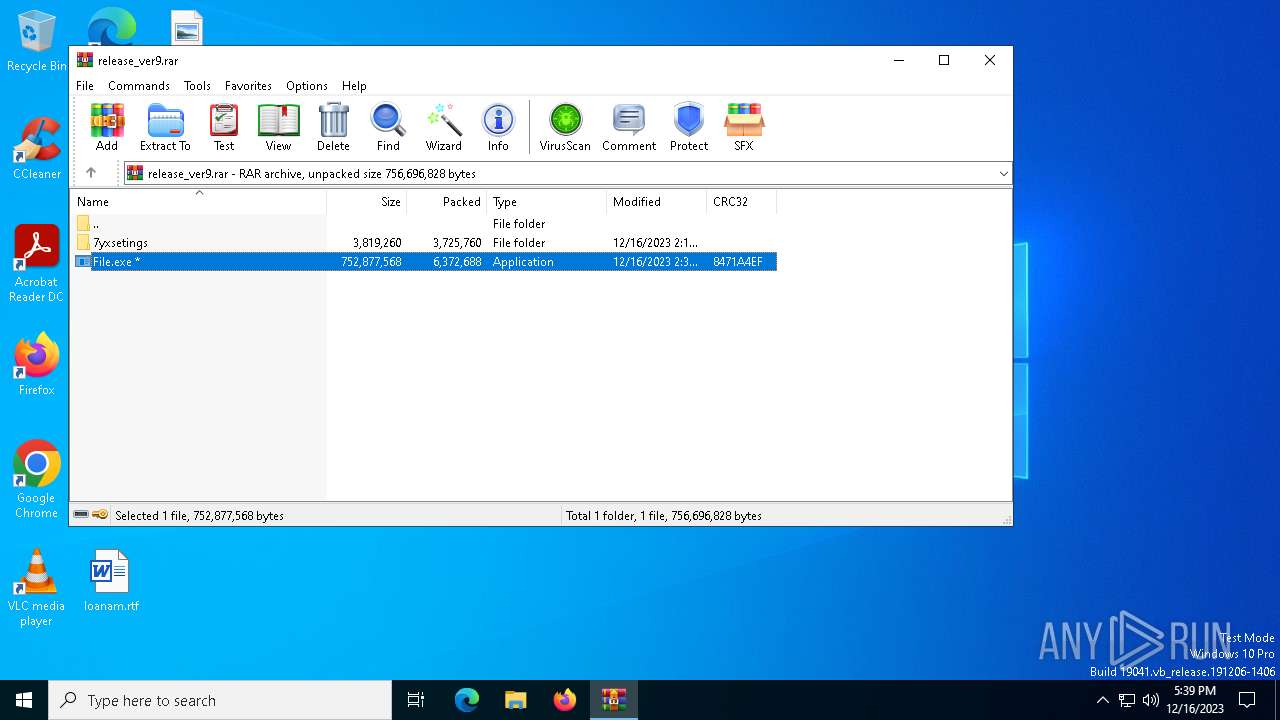
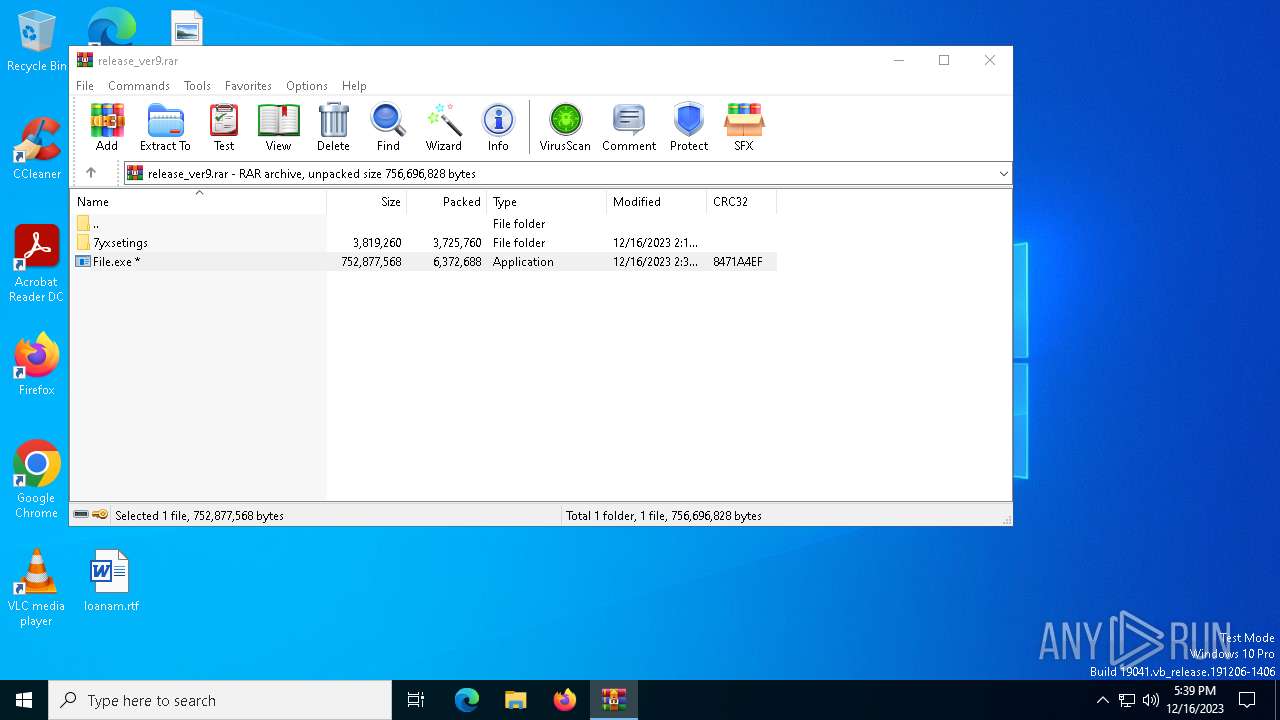
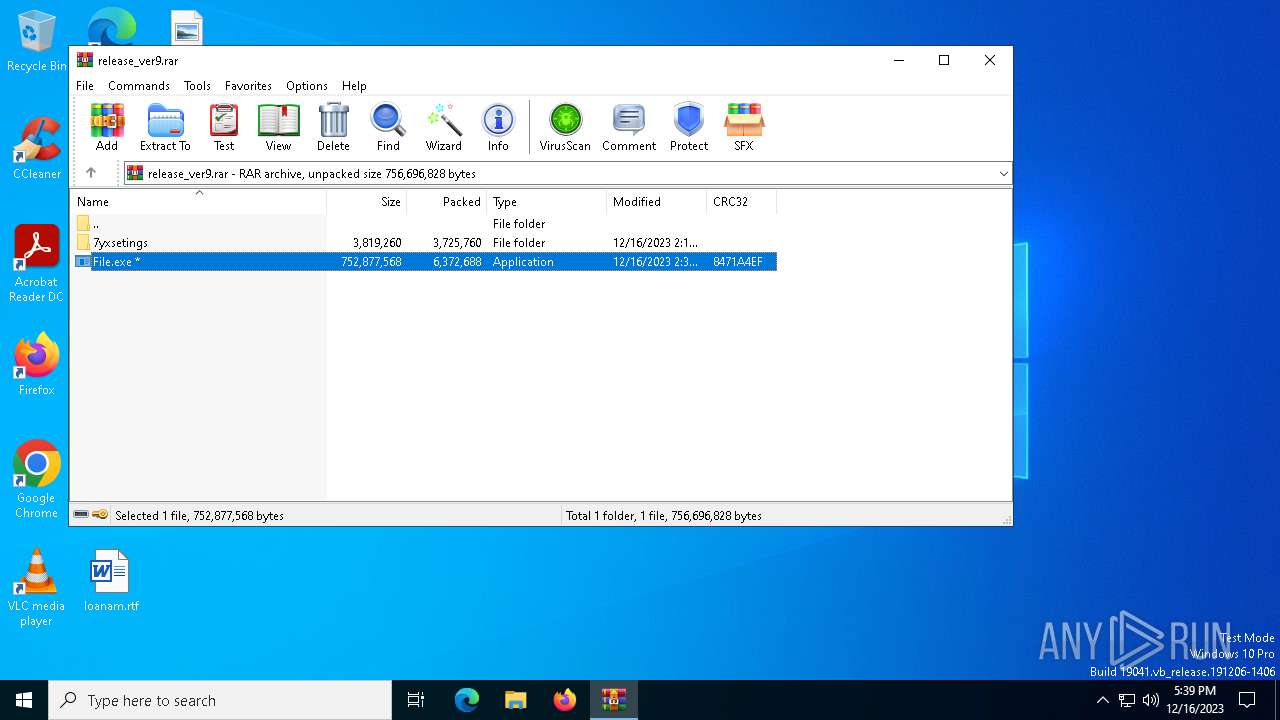
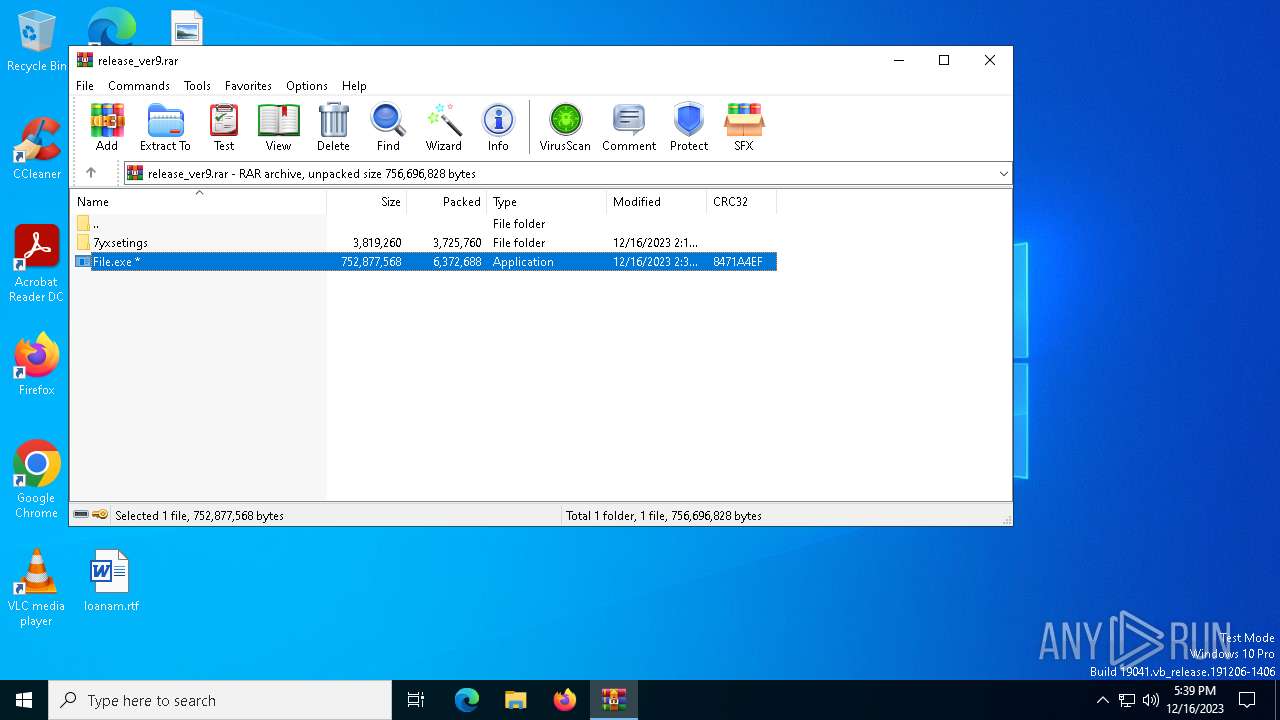
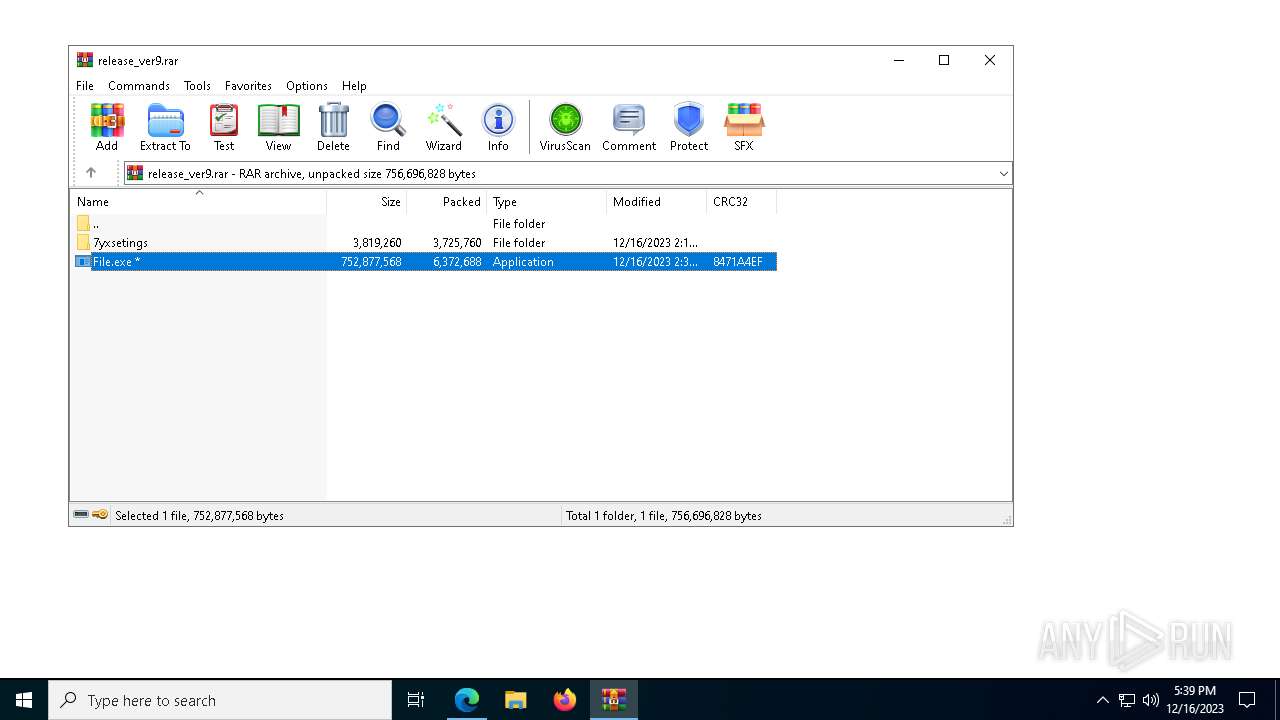
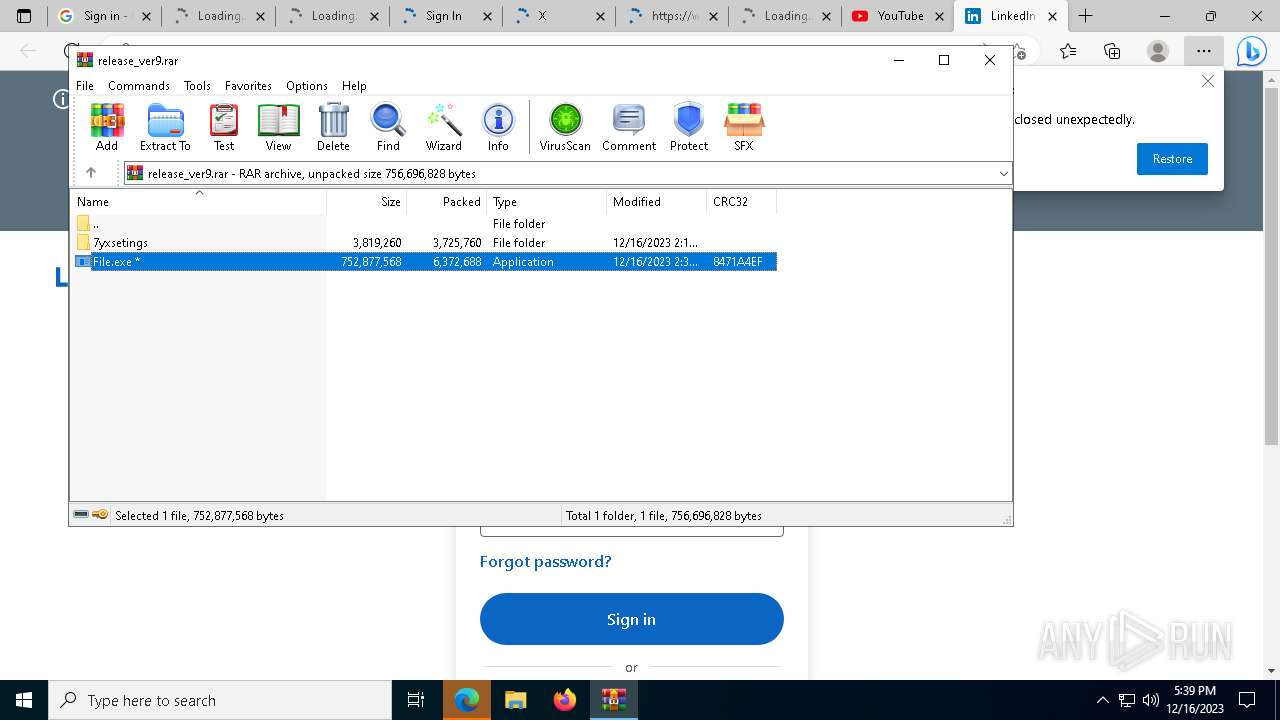
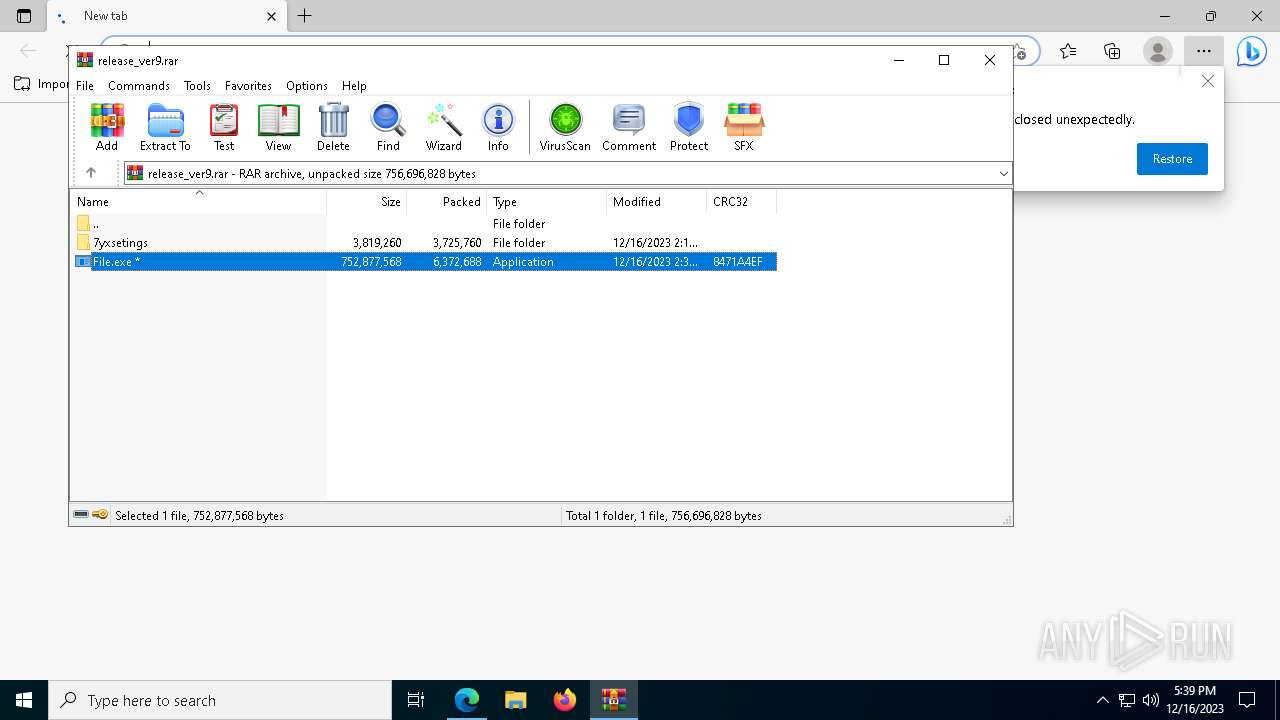
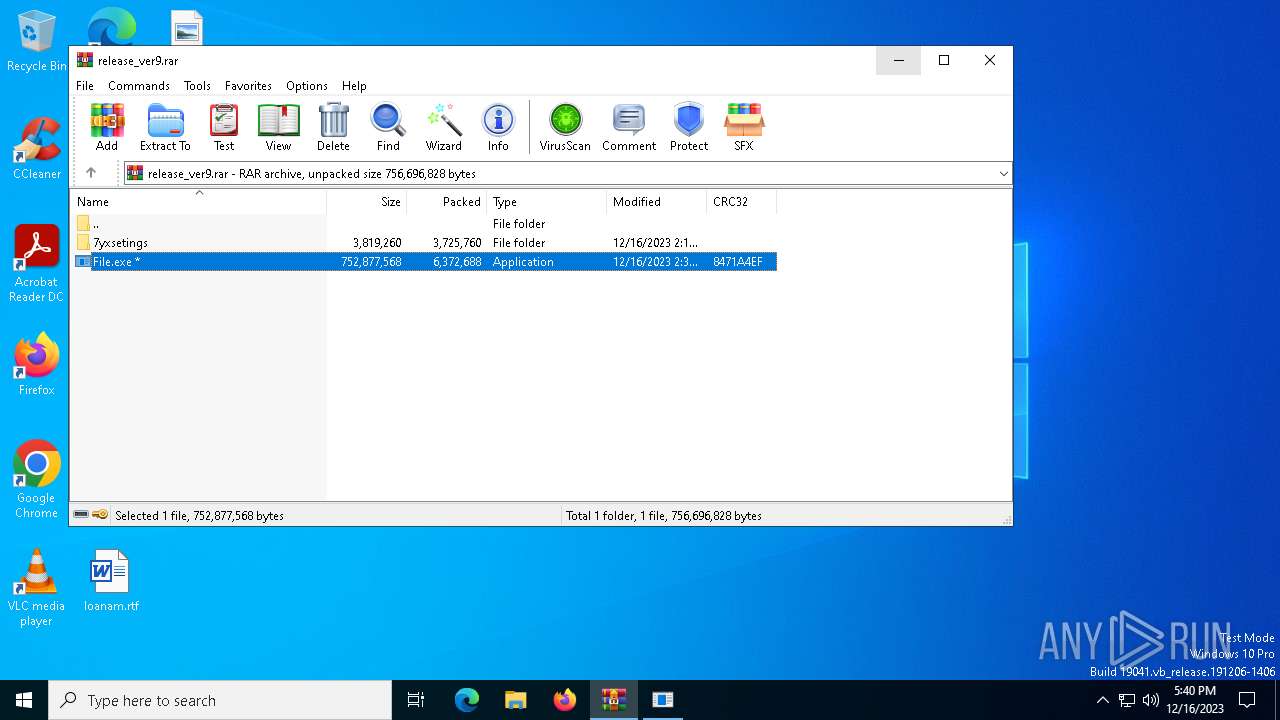
| URL: | https://leeziptv.com/davivi/release_ver9.rar |
| Full analysis: | https://app.any.run/tasks/c8867ec1-e1c8-4eb8-ab30-143c048e42a1 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 16, 2023, 17:37:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8C8EE84D2DDF6EB944A20FB27C568D8D |
| SHA1: | 1673891167797D31EB3116AA3766344234638EE2 |
| SHA256: | 89990CDE275244D3F0DDC24FC80CEEBFF939A8B5EB708EEF89DFB7E88A5AC50A |
| SSDEEP: | 3:N8AAk4TCXArtX8+:2AAk4TUAJX9 |
MALICIOUS
Drops the executable file immediately after the start
- File.exe (PID: 6568)
- v6eCSljQm8qXKqqYJjabfsk5.exe (PID: 8132)
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- cmd.exe (PID: 1480)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- ESWXc3t0z75INnovTK8I71Qt.exe (PID: 8112)
- eigh.exe (PID: 5460)
- NFgoZdOnk8g2x_4I9jXiEJGP.exe (PID: 7824)
- BC1F.exe (PID: 1824)
- Lk8WH12.exe (PID: 4680)
- 3HA73be.exe (PID: 8816)
- EC1A.exe (PID: 7296)
- EC1A.exe (PID: 5920)
- dphonelite.exe (PID: 4984)
- EC1A.tmp (PID: 2672)
- updater.exe (PID: 2980)
- 73CC.exe (PID: 1908)
- tuc3.exe (PID: 5456)
- A84C.exe (PID: 8108)
- InstallSetup9.exe (PID: 8392)
- 8AC1.exe (PID: 9312)
- tuc3.exe (PID: 7216)
- stdbutton.exe (PID: 8688)
- tuc3.tmp (PID: 8020)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
- csrss.exe (PID: 6632)
Disables Windows Defender
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
Connects to the CnC server
- dnIm9ryaZEvp0qg_RH9KKWTk.exe (PID: 7876)
- File.exe (PID: 6568)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- RegSvcs.exe (PID: 7560)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- svchost.exe (PID: 8892)
- explorer.exe (PID: 4500)
- B7A9.exe (PID: 5972)
- 3HA73be.exe (PID: 8816)
- explorer.exe (PID: 7628)
- explorer.exe (PID: 7812)
- 6D22.exe (PID: 4456)
- 6F75.exe (PID: 6780)
- File2.exe (PID: 4980)
- 77A5.exe (PID: 8080)
- nsfB3C0.tmp.exe (PID: 8188)
- RegSvcs.exe (PID: 9724)
- RegSvcs.exe (PID: 7756)
- AppLaunch.exe (PID: 8124)
- AppLaunch.exe (PID: 6132)
- csrss.exe (PID: 6632)
- dphonelite.exe (PID: 6504)
- stdbutton.exe (PID: 3176)
STEALC has been detected (SURICATA)
- dnIm9ryaZEvp0qg_RH9KKWTk.exe (PID: 7876)
- nsfB3C0.tmp.exe (PID: 8188)
RISEPRO has been detected (SURICATA)
- vsLoEVX051aerrcJOZCRzpyn.exe (PID: 8104)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- 3HA73be.exe (PID: 8816)
PRIVATELOADER has been detected (SURICATA)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- File.exe (PID: 6568)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
Actions looks like stealing of personal data
- File.exe (PID: 6568)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- eigh.exe (PID: 5460)
- RegSvcs.exe (PID: 7560)
- jsc.exe (PID: 6492)
- B7A9.exe (PID: 5972)
- explorer.exe (PID: 7628)
- 6D22.exe (PID: 4456)
- File1.exe (PID: 6204)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- 6F75.exe (PID: 6780)
- File2.exe (PID: 4980)
- 77A5.exe (PID: 8080)
- 3HA73be.exe (PID: 8816)
- RegSvcs.exe (PID: 9724)
- RegSvcs.exe (PID: 7756)
- AppLaunch.exe (PID: 6132)
- AppLaunch.exe (PID: 8124)
Runs injected code in another process
- BlvqaXLBhaJKA6eVE0lW37WL.exe (PID: 7916)
- 5wO3FW6.exe (PID: 10192)
- dbcgshj (PID: 6032)
Application was injected by another process
- explorer.exe (PID: 4500)
Create files in the Startup directory
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
Windows Defender preferences modified via 'Set-MpPreference'
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
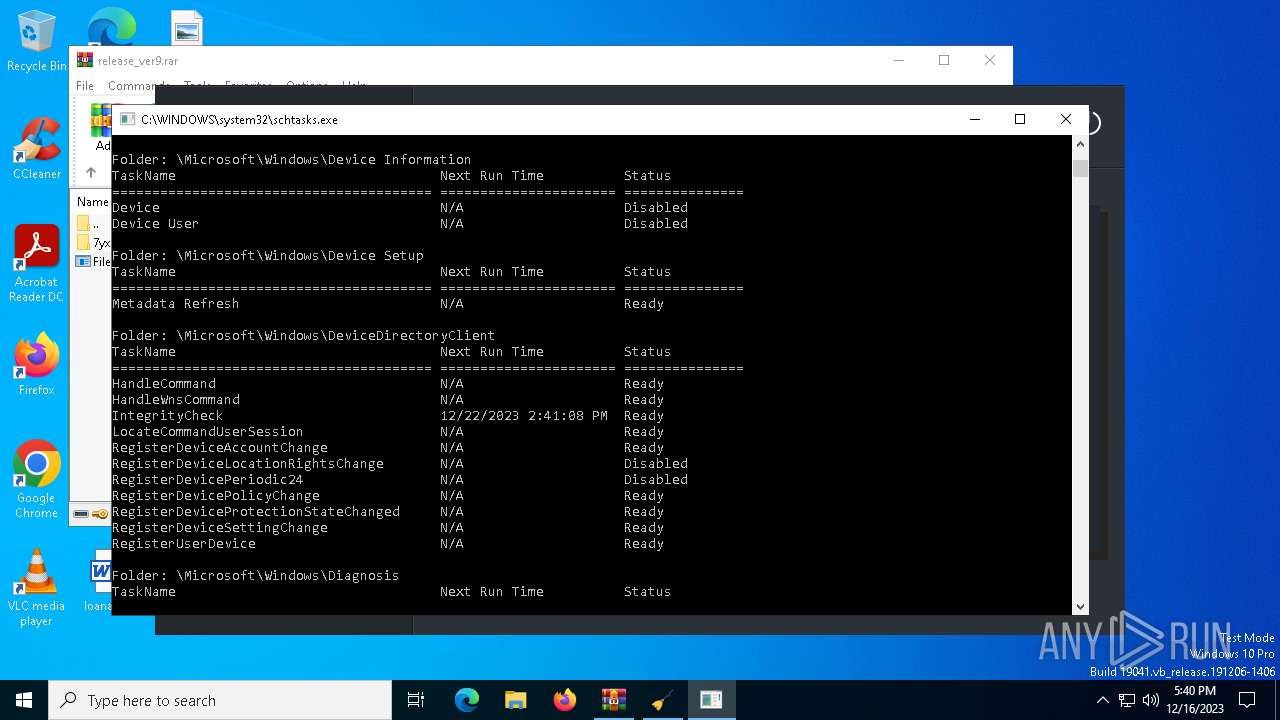
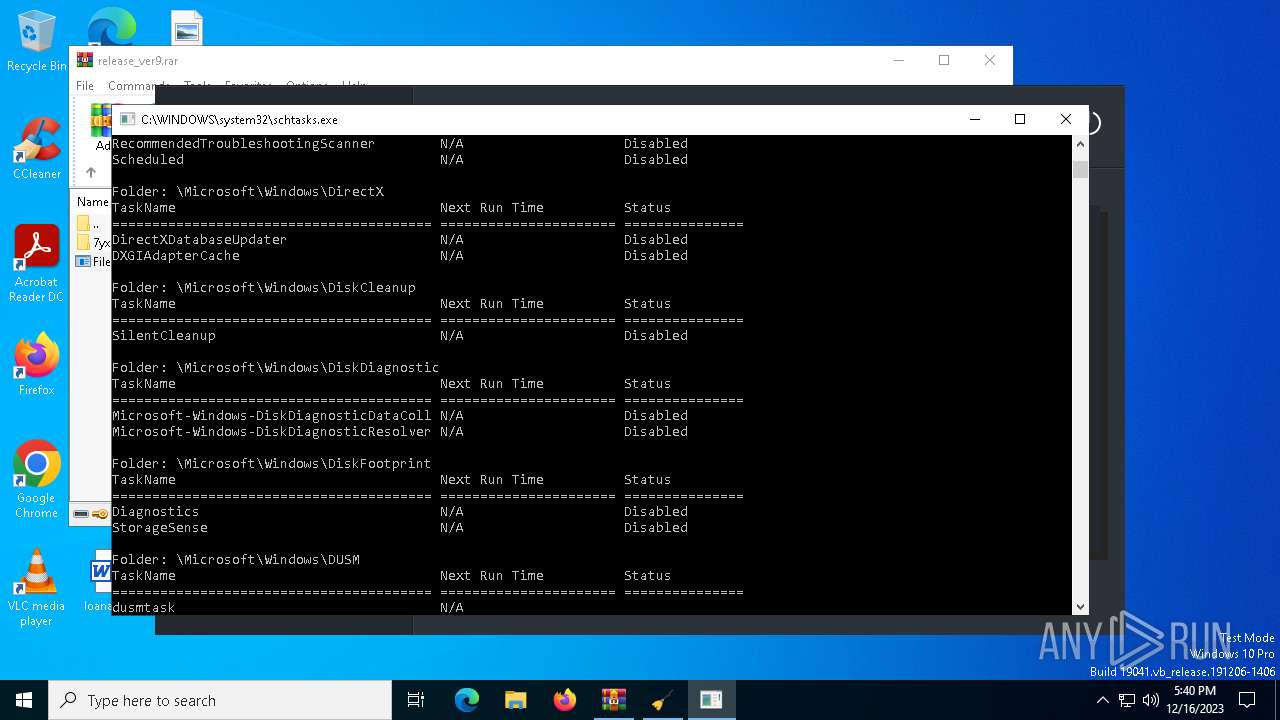
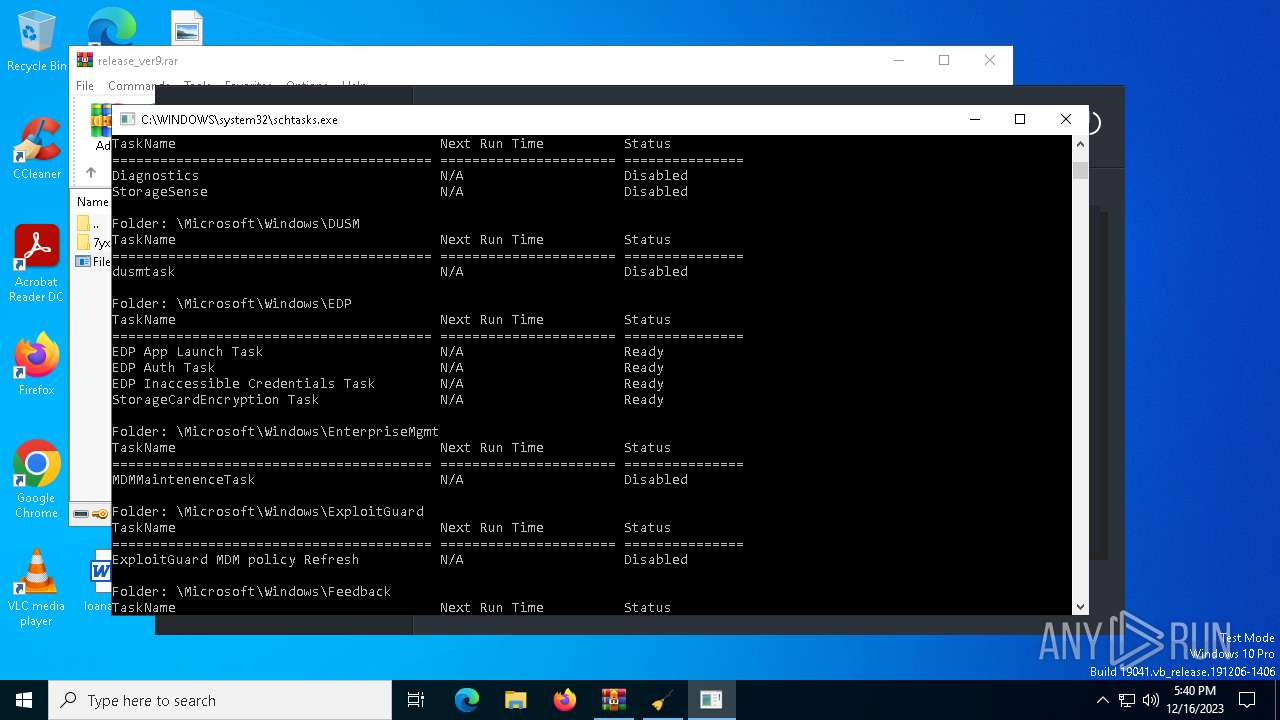
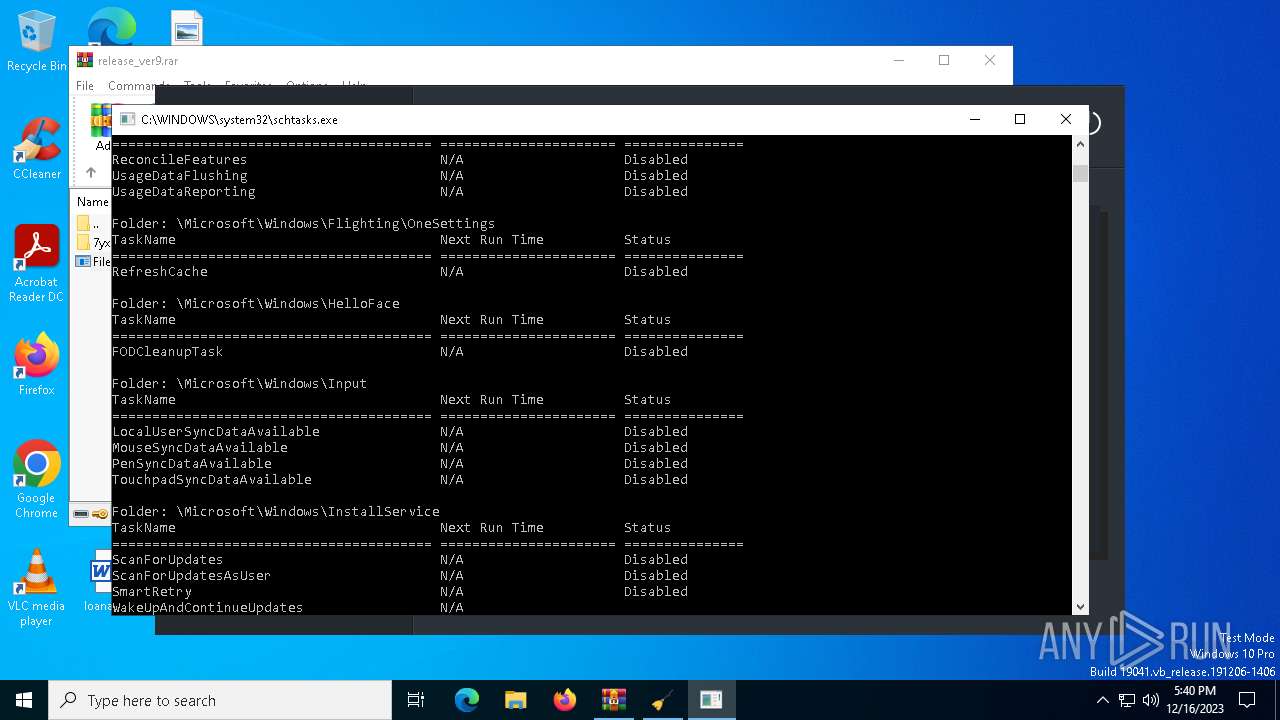
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 8512)
- csrss.exe (PID: 6632)
Changes the autorun value in the registry
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- csrss.exe (PID: 6632)
Uses Task Scheduler to run other applications
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- cmd.exe (PID: 7944)
- explorer.exe (PID: 4500)
- EC1A.tmp (PID: 2672)
- tuc3.tmp (PID: 8020)
- csrss.exe (PID: 6632)
Creates a writable file in the system directory
- svchost.exe (PID: 7188)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- powershell.exe (PID: 8732)
- powershell.exe (PID: 10020)
- csrss.exe (PID: 6632)
Starts CMD.EXE for self-deleting
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
Steals credentials from Web Browsers
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- jsc.exe (PID: 6492)
- 3HA73be.exe (PID: 8816)
- B7A9.exe (PID: 5972)
- File1.exe (PID: 6204)
- 77A5.exe (PID: 8080)
- 6F75.exe (PID: 6780)
- RegSvcs.exe (PID: 9724)
- AppLaunch.exe (PID: 8124)
- AppLaunch.exe (PID: 6132)
Modifies files in the Chrome extension folder
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
LUMMA has been detected (SURICATA)
- RegSvcs.exe (PID: 7560)
- 6D22.exe (PID: 4456)
- RegSvcs.exe (PID: 7756)
Stop is detected
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7340)
TOFSEE has been detected (SURICATA)
- svchost.exe (PID: 7188)
Adds path to the Windows Defender exclusion list
- explorer.exe (PID: 4500)
AMADEY has been detected (SURICATA)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
MINER has been detected (SURICATA)
- svchost.exe (PID: 8892)
REDLINE has been detected (SURICATA)
- jsc.exe (PID: 6492)
- B7A9.exe (PID: 5972)
- 6F75.exe (PID: 6780)
- File2.exe (PID: 4980)
- File1.exe (PID: 6204)
- 77A5.exe (PID: 8080)
- RegSvcs.exe (PID: 9724)
- AppLaunch.exe (PID: 8124)
- AppLaunch.exe (PID: 6132)
SMOKE has been detected (SURICATA)
- explorer.exe (PID: 4500)
- explorer.exe (PID: 7628)
- explorer.exe (PID: 7812)
TOFSEE has been detected (YARA)
- svchost.exe (PID: 7188)
Unusual connection from system programs
- explorer.exe (PID: 7628)
Glupteba is detected
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
GLUPTEBA has been detected (SURICATA)
- csrss.exe (PID: 6632)
SOCKS5SYSTEMZ has been detected (SURICATA)
- dphonelite.exe (PID: 6504)
- stdbutton.exe (PID: 3176)
SUSPICIOUS
Checks for external IP
- File.exe (PID: 6568)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- vsLoEVX051aerrcJOZCRzpyn.exe (PID: 8104)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- 3HA73be.exe (PID: 8816)
- InstallSetup9.exe (PID: 8392)
Connects to the server without a host name
- File.exe (PID: 6568)
- dnIm9ryaZEvp0qg_RH9KKWTk.exe (PID: 7876)
- explorer.exe (PID: 4500)
- svchost.exe (PID: 7188)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
Checks Windows Trust Settings
- File.exe (PID: 6568)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- WinProxy.exe (PID: 7396)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7340)
- InstallSetup9.exe (PID: 8392)
Reads security settings of Internet Explorer
- File.exe (PID: 6568)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- WinProxy.exe (PID: 7396)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7340)
- InstallSetup9.exe (PID: 8392)
Process requests binary or script from the Internet
- File.exe (PID: 6568)
Application launched itself
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 8160)
- svchost.exe (PID: 7188)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 8880)
- toolspub2.exe (PID: 8060)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7400)
Query Microsoft Defender preferences
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
Starts POWERSHELL.EXE for commands execution
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- explorer.exe (PID: 4500)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7400)
- csrss.exe (PID: 6632)
Process drops legitimate windows executable
- v6eCSljQm8qXKqqYJjabfsk5.exe (PID: 8132)
- ESWXc3t0z75INnovTK8I71Qt.exe (PID: 8112)
- explorer.exe (PID: 4500)
- BC1F.exe (PID: 1824)
- EC1A.tmp (PID: 2672)
- tuc3.tmp (PID: 8020)
The process drops C-runtime libraries
- v6eCSljQm8qXKqqYJjabfsk5.exe (PID: 8132)
Reads the date of Windows installation
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- EC1A.tmp (PID: 7680)
- B7A9.exe (PID: 5972)
- 73CC.exe (PID: 1908)
- A84C.exe (PID: 8108)
- tuc3.tmp (PID: 8160)
Executes application which crashes
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- dnIm9ryaZEvp0qg_RH9KKWTk.exe (PID: 7876)
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- qggdpbrp.exe (PID: 6832)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- 3HA73be.exe (PID: 8816)
- nsfB3C0.tmp.exe (PID: 8188)
- 6D22.exe (PID: 4456)
Loads Python modules
- LG.exe (PID: 6484)
Reads the BIOS version
- File.exe (PID: 6568)
- 5IjfD6RM8EHTN8lawOGGJAWe.exe (PID: 8064)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- B7A9.exe (PID: 5972)
Starts CMD.EXE for commands execution
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- explorer.exe (PID: 4500)
- 73CC.exe (PID: 1908)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6584)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
- csrss.exe (PID: 6632)
- windefender.exe (PID: 1612)
Connects to unusual port
- vsLoEVX051aerrcJOZCRzpyn.exe (PID: 8104)
- 5IjfD6RM8EHTN8lawOGGJAWe.exe (PID: 8064)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- svchost.exe (PID: 7188)
- svchost.exe (PID: 8892)
- eigh.exe (PID: 5460)
- jsc.exe (PID: 6492)
- B7A9.exe (PID: 5972)
- 3HA73be.exe (PID: 8816)
- explorer.exe (PID: 10184)
- File2.exe (PID: 4980)
- 6F75.exe (PID: 6780)
- File1.exe (PID: 6204)
- 77A5.exe (PID: 8080)
- RegSvcs.exe (PID: 9724)
- AppLaunch.exe (PID: 8124)
- AppLaunch.exe (PID: 6132)
- dphonelite.exe (PID: 6504)
Uses ICACLS.EXE to modify access control lists
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
Executes as Windows Service
- qggdpbrp.exe (PID: 6832)
- windefender.exe (PID: 9584)
The process executes via Task Scheduler
- WinProxy.exe (PID: 7396)
- updater.exe (PID: 2980)
- dbcgshj (PID: 6032)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 6716)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 2064)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8384)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 6104)
Uses NETSH.EXE to add a firewall rule or allowed programs
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- cmd.exe (PID: 8328)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 7188)
Creates or modifies Windows services
- svchost.exe (PID: 7188)
The process creates files with name similar to system file names
- powershell.exe (PID: 7512)
- powershell.exe (PID: 8732)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
- powershell.exe (PID: 10020)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 9016)
Connects to SMTP port
- svchost.exe (PID: 7188)
Searches for installed software
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- RegSvcs.exe (PID: 7560)
- jsc.exe (PID: 6492)
- B7A9.exe (PID: 5972)
- 3HA73be.exe (PID: 8816)
- File1.exe (PID: 6204)
- File2.exe (PID: 4980)
- 77A5.exe (PID: 8080)
- 6F75.exe (PID: 6780)
- 6D22.exe (PID: 4456)
- RegSvcs.exe (PID: 9724)
- RegSvcs.exe (PID: 7756)
- AppLaunch.exe (PID: 6132)
- AppLaunch.exe (PID: 8124)
The process verifies whether the antivirus software is installed
- eigh.exe (PID: 5460)
Script adds exclusion path to Windows Defender
- explorer.exe (PID: 4500)
Starts SC.EXE for service management
- cmd.exe (PID: 2328)
- cmd.exe (PID: 9924)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 8956)
- cmd.exe (PID: 10076)
Reads the Windows owner or organization settings
- EC1A.tmp (PID: 2672)
- tuc3.tmp (PID: 8020)
Process drops SQLite DLL files
- EC1A.tmp (PID: 2672)
- tuc3.tmp (PID: 8020)
Drops 7-zip archiver for unpacking
- EC1A.tmp (PID: 2672)
- tuc3.tmp (PID: 8020)
Loads DLL from Mozilla Firefox
- explorer.exe (PID: 7812)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 2980)
- csrss.exe (PID: 6632)
The process hides Powershell's copyright startup banner
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7400)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
- csrss.exe (PID: 6632)
The process bypasses the loading of PowerShell profile settings
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7400)
- csrss.exe (PID: 6632)
Starts itself from another location
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
Creates files in the driver directory
- csrss.exe (PID: 6632)
Found strings related to reading or modifying Windows Defender settings
- windefender.exe (PID: 1612)
Xmrig is detected
- csrss.exe (PID: 6632)
INFO
Application launched itself
- msedge.exe (PID: 4884)
- msedge.exe (PID: 2064)
- msedge.exe (PID: 8456)
- msedge.exe (PID: 7872)
- msedge.exe (PID: 1604)
- msedge.exe (PID: 1232)
- msedge.exe (PID: 3204)
- msedge.exe (PID: 7140)
- msedge.exe (PID: 8604)
- msedge.exe (PID: 2844)
- msedge.exe (PID: 7672)
Reads the computer name
- identity_helper.exe (PID: 6472)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- 3hPTTqc23On4BwB9YR22B6cH.exe (PID: 8124)
- dnIm9ryaZEvp0qg_RH9KKWTk.exe (PID: 7876)
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- File.exe (PID: 6568)
- vsLoEVX051aerrcJOZCRzpyn.exe (PID: 8104)
- LG.exe (PID: 6484)
- RegSvcs.exe (PID: 7560)
- qggdpbrp.exe (PID: 6832)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- VP6mkpMg5A4PM.exe (PID: 7916)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- eigh.exe (PID: 5460)
- WinProxy.exe (PID: 7396)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7340)
- jsc.exe (PID: 6492)
- B7A9.exe (PID: 5972)
- 1fp12sh6.exe (PID: 6220)
- 3HA73be.exe (PID: 8816)
- CBEF.exe (PID: 9360)
- EC1A.tmp (PID: 7680)
- EC1A.tmp (PID: 2672)
- dphonelite.exe (PID: 4984)
- 6F75.exe (PID: 6780)
- 73CC.exe (PID: 1908)
- 6D22.exe (PID: 4456)
- File1.exe (PID: 6204)
- File2.exe (PID: 4980)
- 77A5.exe (PID: 8080)
- 8AC1.exe (PID: 9312)
- A84C.exe (PID: 8108)
- BroomSetup.exe (PID: 6432)
- InstallSetup9.exe (PID: 8392)
- AC06.exe (PID: 8996)
- tuc3.tmp (PID: 8160)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6584)
- tuc3.tmp (PID: 8020)
- RegSvcs.exe (PID: 9724)
- nsfB3C0.tmp.exe (PID: 8188)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7400)
- stdbutton.exe (PID: 8688)
- RegSvcs.exe (PID: 7756)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
- csrss.exe (PID: 6632)
- windefender.exe (PID: 9584)
- windefender.exe (PID: 1612)
- AppLaunch.exe (PID: 6132)
- dphonelite.exe (PID: 6504)
- AppLaunch.exe (PID: 8124)
- stdbutton.exe (PID: 3176)
- v6eCSljQm8qXKqqYJjabfsk5.exe (PID: 8132)
Checks supported languages
- identity_helper.exe (PID: 6472)
- File.exe (PID: 6568)
- dnIm9ryaZEvp0qg_RH9KKWTk.exe (PID: 7876)
- so5wem8yXWuvYhTy_zADxFOX.exe (PID: 7884)
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- BlvqaXLBhaJKA6eVE0lW37WL.exe (PID: 7916)
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- 5IjfD6RM8EHTN8lawOGGJAWe.exe (PID: 8064)
- ESWXc3t0z75INnovTK8I71Qt.exe (PID: 8112)
- vsLoEVX051aerrcJOZCRzpyn.exe (PID: 8104)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- v6eCSljQm8qXKqqYJjabfsk5.exe (PID: 8132)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- 3hPTTqc23On4BwB9YR22B6cH.exe (PID: 8124)
- v1NGHg5s9nEMB24PfFzOC1g0.exe (PID: 8148)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 8160)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- LG.exe (PID: 6484)
- qggdpbrp.exe (PID: 6832)
- RegSvcs.exe (PID: 7560)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- VP6mkpMg5A4PM.exe (PID: 7916)
- eigh.exe (PID: 5460)
- WinProxy.exe (PID: 7396)
- NFgoZdOnk8g2x_4I9jXiEJGP.exe (PID: 7824)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 8880)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7340)
- jsc.exe (PID: 6492)
- updater.exe (PID: 2980)
- Lk8WH12.exe (PID: 4680)
- BC1F.exe (PID: 1824)
- 1fp12sh6.exe (PID: 6220)
- B7A9.exe (PID: 5972)
- 3HA73be.exe (PID: 8816)
- CBEF.exe (PID: 9360)
- EC1A.exe (PID: 7296)
- EC1A.tmp (PID: 7680)
- EC1A.exe (PID: 5920)
- EC1A.tmp (PID: 2672)
- dphonelite.exe (PID: 4984)
- dphonelite.exe (PID: 6504)
- 5wO3FW6.exe (PID: 10192)
- 6D22.exe (PID: 4456)
- 6F75.exe (PID: 6780)
- 73CC.exe (PID: 1908)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 6716)
- 77A5.exe (PID: 8080)
- dbcgshj (PID: 6032)
- File2.exe (PID: 4980)
- File1.exe (PID: 6204)
- 8AC1.exe (PID: 9312)
- A84C.exe (PID: 8108)
- InstallSetup9.exe (PID: 8392)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6584)
- AC06.exe (PID: 8996)
- toolspub2.exe (PID: 8060)
- BroomSetup.exe (PID: 6432)
- tuc3.exe (PID: 5456)
- toolspub2.exe (PID: 6332)
- tuc3.tmp (PID: 8160)
- tuc3.exe (PID: 7216)
- tuc3.tmp (PID: 8020)
- nsfB3C0.tmp.exe (PID: 8188)
- RegSvcs.exe (PID: 9724)
- stdbutton.exe (PID: 8688)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7400)
- stdbutton.exe (PID: 3176)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 7288)
- RegSvcs.exe (PID: 7756)
- csrss.exe (PID: 6632)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 2064)
- windefender.exe (PID: 1612)
- windefender.exe (PID: 9584)
- AppLaunch.exe (PID: 8124)
- AppLaunch.exe (PID: 6132)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8384)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 6104)
The process uses the downloaded file
- msedge.exe (PID: 4884)
- WinRAR.exe (PID: 6628)
- msedge.exe (PID: 6364)
Process checks are UAC notifies on
- File.exe (PID: 6568)
- 5IjfD6RM8EHTN8lawOGGJAWe.exe (PID: 8064)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
Reads the machine GUID from the registry
- File.exe (PID: 6568)
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- 3hPTTqc23On4BwB9YR22B6cH.exe (PID: 8124)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- vsLoEVX051aerrcJOZCRzpyn.exe (PID: 8104)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- WinProxy.exe (PID: 7396)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7340)
- jsc.exe (PID: 6492)
- B7A9.exe (PID: 5972)
- 3HA73be.exe (PID: 8816)
- CBEF.exe (PID: 9360)
- 6F75.exe (PID: 6780)
- File1.exe (PID: 6204)
- 77A5.exe (PID: 8080)
- File2.exe (PID: 4980)
- 8AC1.exe (PID: 9312)
- AC06.exe (PID: 8996)
- RegSvcs.exe (PID: 9724)
- InstallSetup9.exe (PID: 8392)
- windefender.exe (PID: 1612)
- windefender.exe (PID: 9584)
- AppLaunch.exe (PID: 6132)
- AppLaunch.exe (PID: 8124)
- csrss.exe (PID: 6632)
Process checks computer location settings
- File.exe (PID: 6568)
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- EC1A.tmp (PID: 7680)
- B7A9.exe (PID: 5972)
- 73CC.exe (PID: 1908)
- A84C.exe (PID: 8108)
- tuc3.tmp (PID: 8160)
- csrss.exe (PID: 6632)
Checks proxy server information
- File.exe (PID: 6568)
- dnIm9ryaZEvp0qg_RH9KKWTk.exe (PID: 7876)
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- LG.exe (PID: 6484)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- WerFault.exe (PID: 7628)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- WerFault.exe (PID: 9128)
- eigh.exe (PID: 5460)
- WinProxy.exe (PID: 7396)
- WerFault.exe (PID: 8948)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7340)
- explorer.exe (PID: 4500)
- 3HA73be.exe (PID: 8816)
- CBEF.exe (PID: 9360)
- explorer.exe (PID: 7628)
- explorer.exe (PID: 7812)
- WerFault.exe (PID: 7924)
- InstallSetup9.exe (PID: 8392)
- WerFault.exe (PID: 7656)
- nsfB3C0.tmp.exe (PID: 8188)
- WerFault.exe (PID: 7348)
- dphonelite.exe (PID: 6504)
- stdbutton.exe (PID: 3176)
Creates files or folders in the user directory
- File.exe (PID: 6568)
- WerFault.exe (PID: 6500)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- WerFault.exe (PID: 7684)
- WerFault.exe (PID: 7628)
- WerFault.exe (PID: 8160)
- WerFault.exe (PID: 6680)
- WerFault.exe (PID: 5568)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- WerFault.exe (PID: 6504)
- Vcl_dyK2t2TyGCuEhKDkBlah.exe (PID: 8052)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- 3hPTTqc23On4BwB9YR22B6cH.exe (PID: 8124)
- WerFault.exe (PID: 8644)
- VP6mkpMg5A4PM.exe (PID: 7916)
- WerFault.exe (PID: 8304)
- explorer.exe (PID: 4500)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- WerFault.exe (PID: 9128)
- WinProxy.exe (PID: 7396)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7340)
- WerFault.exe (PID: 8948)
- jsc.exe (PID: 6492)
- eigh.exe (PID: 5460)
- WerFault.exe (PID: 7924)
- B7A9.exe (PID: 5972)
- CBEF.exe (PID: 9360)
- 73CC.exe (PID: 1908)
- File1.exe (PID: 6204)
- 77A5.exe (PID: 8080)
- A84C.exe (PID: 8108)
- InstallSetup9.exe (PID: 8392)
- 6F75.exe (PID: 6780)
- 8AC1.exe (PID: 9312)
- WerFault.exe (PID: 7656)
- WerFault.exe (PID: 7348)
- RegSvcs.exe (PID: 9724)
- AC06.exe (PID: 8996)
Create files in a temporary directory
- v6eCSljQm8qXKqqYJjabfsk5.exe (PID: 8132)
- ClS0GFX6S0baJm18t2YbQl3R.exe (PID: 7932)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- ESWXc3t0z75INnovTK8I71Qt.exe (PID: 8112)
- eigh.exe (PID: 5460)
- explorer.exe (PID: 4500)
- BC1F.exe (PID: 1824)
- Lk8WH12.exe (PID: 4680)
- 3HA73be.exe (PID: 8816)
- EC1A.exe (PID: 7296)
- explorer.exe (PID: 7628)
- EC1A.exe (PID: 5920)
- EC1A.tmp (PID: 2672)
- A84C.exe (PID: 8108)
- InstallSetup9.exe (PID: 8392)
- tuc3.exe (PID: 5456)
- tuc3.tmp (PID: 8020)
- 8AC1.exe (PID: 9312)
- tuc3.exe (PID: 7216)
Reads Environment values
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- Thu9UvX5Ql37czoXSjEE7DNU.exe (PID: 8828)
- jsc.exe (PID: 6492)
- 3HA73be.exe (PID: 8816)
- B7A9.exe (PID: 5972)
- CBEF.exe (PID: 9360)
- File1.exe (PID: 6204)
- File2.exe (PID: 4980)
- 6F75.exe (PID: 6780)
- 77A5.exe (PID: 8080)
- RegSvcs.exe (PID: 9724)
- AppLaunch.exe (PID: 6132)
- AppLaunch.exe (PID: 8124)
Reads the software policy settings
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- File.exe (PID: 6568)
- rEdilVqCtAxcAIRONP6XScoY.exe (PID: 8096)
- Xc0ZsUWiJSGjfW2UcrkqZrQk.exe (PID: 7408)
- vsLoEVX051aerrcJOZCRzpyn.exe (PID: 8104)
- WerFault.exe (PID: 7628)
- slui.exe (PID: 3108)
- 0CSLkRsdIpz6NqfuvgqD53Iw.exe (PID: 8140)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- WerFault.exe (PID: 9128)
- WinProxy.exe (PID: 7396)
- WerFault.exe (PID: 8948)
- 3HA73be.exe (PID: 8816)
- WerFault.exe (PID: 7924)
- explorer.exe (PID: 4500)
- WerFault.exe (PID: 7348)
- InstallSetup9.exe (PID: 8392)
- WerFault.exe (PID: 7656)
Creates files in the program directory
- jcEhfUxbIYjfYrWp__mWR2ER.exe (PID: 7924)
- zQzfVDGfPYJq4_3IXtK4FhLj.exe (PID: 7972)
- eigh.exe (PID: 5460)
- NFgoZdOnk8g2x_4I9jXiEJGP.exe (PID: 7824)
- EC1A.tmp (PID: 2672)
- dphonelite.exe (PID: 4984)
- updater.exe (PID: 2980)
- tuc3.tmp (PID: 8020)
- stdbutton.exe (PID: 8688)
- dphonelite.exe (PID: 6504)
Manual execution by a user
- powershell.exe (PID: 3176)
- cmd.exe (PID: 8956)
- powershell.exe (PID: 5184)
- schtasks.exe (PID: 4984)
- B7A9.exe (PID: 5972)
- cmd.exe (PID: 2328)
- BC1F.exe (PID: 1824)
- powershell.exe (PID: 8732)
- CBEF.exe (PID: 9360)
- cmd.exe (PID: 9924)
- cmd.exe (PID: 10076)
- powershell.exe (PID: 10116)
- EC1A.exe (PID: 7296)
- explorer.exe (PID: 7628)
- explorer.exe (PID: 7812)
- conhost.exe (PID: 9956)
- explorer.exe (PID: 10184)
- 6D22.exe (PID: 4456)
- 6F75.exe (PID: 6780)
- 77A5.exe (PID: 8080)
- 73CC.exe (PID: 1908)
- 8AC1.exe (PID: 9312)
- A84C.exe (PID: 8108)
- AC06.exe (PID: 8996)
Drops the executable file immediately after the start
- explorer.exe (PID: 4500)
Reads mouse settings
- 1fp12sh6.exe (PID: 6220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Tofsee
(PID) Process(7188) svchost.exe
C2 (2)vanaheim.cn
jotunheim.name
Encrypted Strings (59)c:\Windows
\system32\
ImagePath
.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
MSConfig
/r
.exe
cmd /C move /Y "%s" %s
sc config %s binPath= "%s%s /d\"%s\""
sc start %s
svchost.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin
PromptOnSecureDesktop
MSConfig
:.repos
USERPROFILE
\Local Settings:.repos
USERPROFILE
\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat.repos
USERPROFILE
\wincookie.repos
TMP
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
SYSTEM\CurrentControlSet\services
ImagePath
SYSTEM\CurrentControlSet\services
SYSTEM\CurrentControlSet\services
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
.exe
qazwsxed
%s%i%i%i%i.bat
@echo off
:next_try
del "%s">nul
if exist "%s" (
ping 127.0.0.1 >nul
goto next_try
)
del %%0
svchost.exe
.exe
/u
USERPROFILE
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/d
/e
/d
/e
.exe
"%s" /u"%s"
USERPROFILE
.exe
USERPROFILE
USERPROFILE
ver=%d lid=%d
win=%X/%d sid=%s
rep=%s
Total processes
506
Monitored processes
337
Malicious processes
66
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Set-MpPreference -ModerateThreatDefaultAction 6 | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | zQzfVDGfPYJq4_3IXtK4FhLj.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2328 --field-trial-handle=2072,i,15362847834226006305,2897971221502885283,131072 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1100 | fodhelper | C:\Windows\System32\fodhelper.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Features On Demand Helper Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://accounts.google.com/ | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | 1fp12sh6.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 4294967295 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1480 | "C:\Windows\System32\cmd.exe" /C move /Y "C:\Users\admin\AppData\Local\Temp\qggdpbrp.exe" C:\WINDOWS\SysWOW64\nvalhmzh\ | C:\Windows\SysWOW64\cmd.exe | — | ClS0GFX6S0baJm18t2YbQl3R.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | windefender.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1536 | icacls "C:\Users\admin\AppData\Local\c906aa9e-50b8-4441-a762-4f05e1d2f566" /deny *S-1-1-0:(OI)(CI)(DE,DC) | C:\Windows\SysWOW64\icacls.exe | — | Xc0ZsUWiJSGjfW2UcrkqZrQk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1604 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://www.linkedin.com/login | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | 1fp12sh6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1612 | "C:\WINDOWS\windefender.exe" | C:\Windows\windefender.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
207 385
Read events
206 464
Write events
689
Delete events
232
Modification events
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
| (PID) Process: | (4884) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 74A98451B7602F00 | |||
Executable files
326
Suspicious files
930
Text files
491
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFf283f.TMP | — | |
MD5:— | SHA256:— | |||
| 4884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFf284f.TMP | — | |
MD5:— | SHA256:— | |||
| 4884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RFf286e.TMP | — | |
MD5:— | SHA256:— | |||
| 4884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\2e7a8add-22c2-4545-9170-e8074f74f81b.tmp | binary | |
MD5:1637026C6EC32BCE83AB2A63734B99AA | SHA256:8DDBB3CB7B10F62E6BE7AC46861DD2F9A647D53178436FEFB6921E5C72E4A150 | |||
| 4884 | msedge.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\EDGE\USER DATA\VARIATIONS | binary | |
MD5:6E1AF7D7074A6124EFDB62180565A385 | SHA256:70811DE44C337675FCFFDA381E8AB2FB66544B07FFCAE651804B75EF71C11748 | |||
| 4884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old~RFf2830.TMP | text | |
MD5:5DB127C66F688E2B285A0816EC4BDE1C | SHA256:1A490965A2E4688809FF31A5DB1971688F92700DEFA536BEF28D91512B9AA966 | |||
| 4884 | msedge.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\EDGE\USER DATA\CRASHPAD\SETTINGS.DAT | binary | |
MD5:E2757D5A5254E45CDCE4888662B214A8 | SHA256:8306EF3DCAE74D697DF4367324A026CAA9EAC9B36D7FBE49E9C381446DE0CE75 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
258
TCP/UDP connections
709
DNS requests
329
Threats
448
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4988 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1092 | svchost.exe | POST | 302 | 2.18.97.227:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1912 | svchost.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | binary | 814 b | unknown |
1912 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.11 Kb | unknown |
6932 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
6476 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
6476 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
6568 | File.exe | GET | 200 | 195.20.16.45:80 | http://195.20.16.45/api/tracemap.php | unknown | text | 15 b | unknown |
1092 | svchost.exe | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
6568 | File.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8EJH | unknown | binary | 1.41 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
1048 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1048 | msedge.exe | 188.114.97.3:443 | leeziptv.com | CLOUDFLARENET | NL | unknown |
1048 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1048 | msedge.exe | 20.31.251.109:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 51.104.176.40:443 | data-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 20.103.180.120:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3720 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1048 | msedge.exe | 13.107.213.62:443 | edgeassetservice.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4884 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
leeziptv.com |
| malicious |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
dl-edge.smartscreen.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
www2.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6568 | File.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
6568 | File.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/BeamWinHTTP CnC Activity M2 (GET) |
6568 | File.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
6568 | File.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
6568 | File.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 25 |
6568 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6568 | File.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 20 |
6568 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6568 | File.exe | Misc activity | ET INFO Packed Executable Download |
6568 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
39 ETPRO signatures available at the full report
Process | Message |
|---|---|
vsLoEVX051aerrcJOZCRzpyn.exe | 5yh45 |
vsLoEVX051aerrcJOZCRzpyn.exe | 5yh45 |
vsLoEVX051aerrcJOZCRzpyn.exe | 5yh45 |
vsLoEVX051aerrcJOZCRzpyn.exe | 5yh45 |
vsLoEVX051aerrcJOZCRzpyn.exe | 5445dfg |
vsLoEVX051aerrcJOZCRzpyn.exe | th1y5atj8 |