| File name: | svchost.exe |
| Full analysis: | https://app.any.run/tasks/5509bf07-0df5-42a8-ac29-be231f589066 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | August 14, 2024, 02:49:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A0003B61DE61A7D0D8B9EBFF912B0478 |
| SHA1: | 36FD6DE22DF6FC262A5571F986EA0FAFAD423CE1 |
| SHA256: | 89528742547FA683A01B9627C176BC3418BAF968E758B23A51534AFE97A395A8 |
| SSDEEP: | 24576:m3HzLnqOaNMCFJ6kPvOxrcg0i7uFymkwsE:m3HzLnqOaNMCFJ6kPvO1cg0i7xmvsE |
MALICIOUS
Changes the autorun value in the registry
- svchost.exe (PID: 6536)
- ._cache_svchost.exe (PID: 6808)
Connects to the CnC server
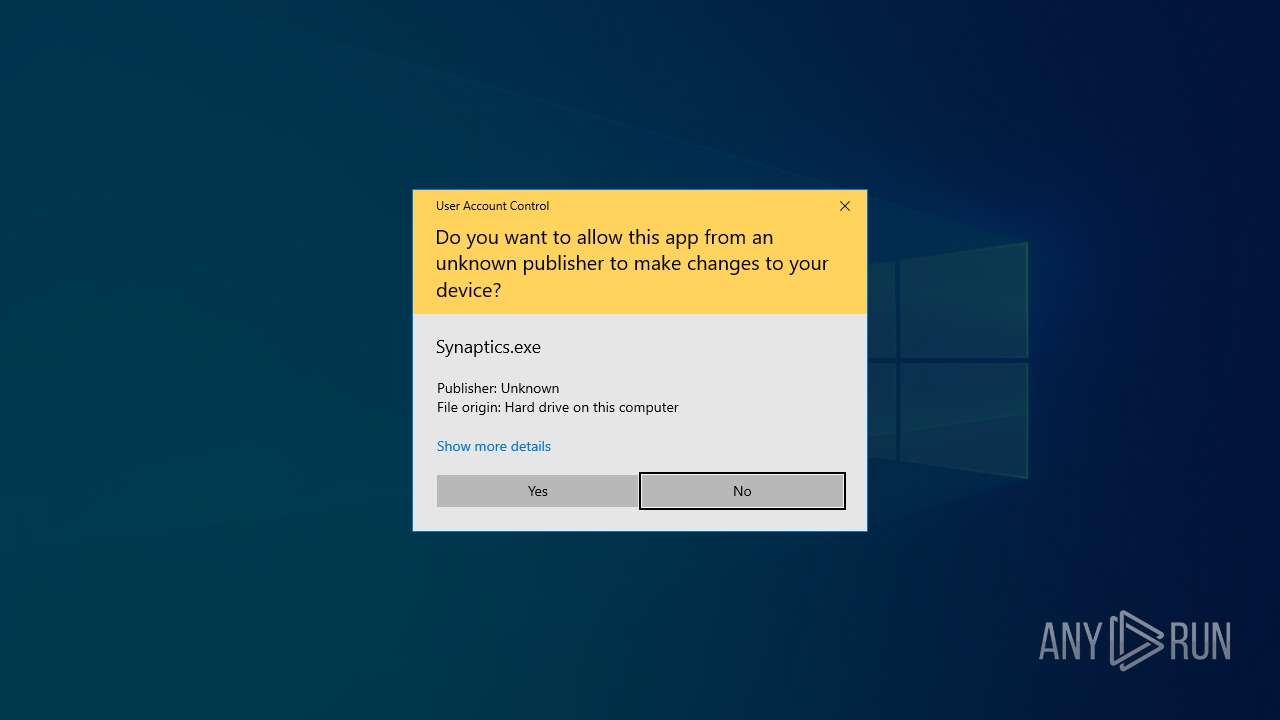
- Synaptics.exe (PID: 2476)
ASYNCRAT has been detected (YARA)
- svchost.exe (PID: 1948)
ASYNCRAT has been detected (SURICATA)
- svchost.exe (PID: 1948)
SUSPICIOUS
Drops the executable file immediately after the start
- svchost.exe (PID: 6536)
- ._cache_svchost.exe (PID: 6808)
Reads the date of Windows installation
- svchost.exe (PID: 6536)
Reads security settings of Internet Explorer
- svchost.exe (PID: 6536)
- Synaptics.exe (PID: 2476)
The process creates files with name similar to system file names
- svchost.exe (PID: 6536)
- ._cache_svchost.exe (PID: 6808)
Executing commands from a ".bat" file
- ._cache_svchost.exe (PID: 6808)
Executable content was dropped or overwritten
- svchost.exe (PID: 6536)
- ._cache_svchost.exe (PID: 6808)
Starts CMD.EXE for commands execution
- ._cache_svchost.exe (PID: 6808)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6452)
The executable file from the user directory is run by the CMD process
- svchost.exe (PID: 1948)
There is functionality for taking screenshot (YARA)
- Synaptics.exe (PID: 2476)
Contacting a server suspected of hosting an CnC
- Synaptics.exe (PID: 2476)
- svchost.exe (PID: 1948)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 2476)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 2476)
Connects to unusual port
- svchost.exe (PID: 1948)
Checks Windows Trust Settings
- Synaptics.exe (PID: 2476)
INFO
Creates files in the program directory
- svchost.exe (PID: 6536)
- Synaptics.exe (PID: 2476)
Reads the computer name
- svchost.exe (PID: 6536)
- ._cache_svchost.exe (PID: 6808)
- Synaptics.exe (PID: 2476)
- svchost.exe (PID: 1948)
Creates files or folders in the user directory
- ._cache_svchost.exe (PID: 6808)
- Synaptics.exe (PID: 2476)
Process checks computer location settings
- svchost.exe (PID: 6536)
Reads the machine GUID from the registry
- ._cache_svchost.exe (PID: 6808)
- svchost.exe (PID: 1948)
- Synaptics.exe (PID: 2476)
Checks supported languages
- svchost.exe (PID: 6536)
- ._cache_svchost.exe (PID: 6808)
- Synaptics.exe (PID: 2476)
- svchost.exe (PID: 1948)
Create files in a temporary directory
- ._cache_svchost.exe (PID: 6808)
- Synaptics.exe (PID: 2476)
Reads Environment values
- svchost.exe (PID: 1948)
Checks proxy server information
- Synaptics.exe (PID: 2476)
Reads the software policy settings
- Synaptics.exe (PID: 2476)
- svchost.exe (PID: 1948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(1948) svchost.exe
C2 (1)176.111.174.140
Ports (3)6606
7707
8808
Version0.5.8
BotnetDefault
Options
AutoRuntrue
MutexPWhSiRkcxVoa
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAJ1cCk0in0I5WMAENhHaSTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjQwNzI0MDU0OTU0WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAJorhtHGiOfUxzOI4wJsJQJqHNtwSer53LwgyLAx/J1yfZ71D/C7YtCJf4a0PiVjCb0T+UvWTjwS...
Server_SignatureIkQhvensIpRIaZSdRtes3xr+Yu8SpB4YNZGh7rK4DGIkgUsMHO6Oo0Uc9vYeXR4l22BkAG2n3X2xe9UeS5qZRwMo2b2HhtIi3rSgDCcXpYnCh1e+h2o+bAH9P4YpA1r6SD1l4hPX0NqDCW4LMGoFIZVtYRVvqBGVobBeHPg9UkCs9oYKsfuB1QO6s+b7iSUOOTSbXQ3DyYMVKib4xljLTfdy0pK75HVp4O1y9chTh4or4M5mVAmBUc7v/KsTEc+rFJIuNWs8yj59JYzpx7jXeeYdeKPasta1MMlg0MtK+6Yy...
Keys
AESbbb83b1a35e065361d945e39f6929461f637616d757966bf8d0c9da5e8dd8ca4
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (96.4) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.3) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 629760 |
| InitializedDataSize: | 189440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9ab80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Turkish |
| CharacterSet: | Windows, Turkish |
| CompanyName: | Synaptics |
| FileDescription: | Synaptics Pointing Device Driver |
| FileVersion: | 1.0.0.4 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Synaptics Pointing Device Driver |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
140
Monitored processes
7
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1948 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
AsyncRat(PID) Process(1948) svchost.exe C2 (1)176.111.174.140 Ports (3)6606 7707 8808 Version0.5.8 BotnetDefault Options AutoRuntrue MutexPWhSiRkcxVoa InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIIE8jCCAtqgAwIBAgIQAJ1cCk0in0I5WMAENhHaSTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjQwNzI0MDU0OTU0WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAJorhtHGiOfUxzOI4wJsJQJqHNtwSer53LwgyLAx/J1yfZ71D/C7YtCJf4a0PiVjCb0T+UvWTjwS... Server_SignatureIkQhvensIpRIaZSdRtes3xr+Yu8SpB4YNZGh7rK4DGIkgUsMHO6Oo0Uc9vYeXR4l22BkAG2n3X2xe9UeS5qZRwMo2b2HhtIi3rSgDCcXpYnCh1e+h2o+bAH9P4YpA1r6SD1l4hPX0NqDCW4LMGoFIZVtYRVvqBGVobBeHPg9UkCs9oYKsfuB1QO6s+b7iSUOOTSbXQ3DyYMVKib4xljLTfdy0pK75HVp4O1y9chTh4or4M5mVAmBUc7v/KsTEc+rFJIuNWs8yj59JYzpx7jXeeYdeKPasta1MMlg0MtK+6Yy... Keys AESbbb83b1a35e065361d945e39f6929461f637616d757966bf8d0c9da5e8dd8ca4 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 2476 | "C:\ProgramData\Synaptics\Synaptics.exe" InjUpdate | C:\ProgramData\Synaptics\Synaptics.exe | svchost.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: HIGH Description: Synaptics Pointing Device Driver Version: 1.0.0.4 Modules
| |||||||||||||||
| 5916 | timeout 3 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6452 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmp704A.tmp.bat"" | C:\Windows\SysWOW64\cmd.exe | — | ._cache_svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6536 | "C:\Users\admin\Desktop\svchost.exe" | C:\Users\admin\Desktop\svchost.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 6808 | "C:\Users\admin\Desktop\._cache_svchost.exe" | C:\Users\admin\Desktop\._cache_svchost.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
7 612
Read events
7 589
Write events
23
Delete events
0
Modification events
| (PID) Process: | (6536) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6536) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6536) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6536) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6536) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6536) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Synaptics Pointing Device Driver |
Value: C:\ProgramData\Synaptics\Synaptics.exe | |||
| (PID) Process: | (6536) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000060B81DB4E48ED2119906E49FADC173CA7D000000 | |||
| (PID) Process: | (6808) ._cache_svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | svchost |
Value: "C:\Users\admin\AppData\Roaming\svchost.exe" | |||
| (PID) Process: | (2476) Synaptics.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2476) Synaptics.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
8
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6536 | svchost.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:A0003B61DE61A7D0D8B9EBFF912B0478 | SHA256:89528742547FA683A01B9627C176BC3418BAF968E758B23A51534AFE97A395A8 | |||
| 2476 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:27CC9762BA0AA5F6DDD0326700B2CFE7 | SHA256:EB0CADC23EF08F1D6E2E2506F3A4CB1BB50CB5D06E6ECA1528A7CF84A34CBFB7 | |||
| 6808 | ._cache_svchost.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:670D1014EC5713D005F8DDFEFC495A9E | SHA256:70C6D555938FDC95C03F98A7A3A37B607D1DCE623663479082C5B9514CAA04FD | |||
| 2476 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:E935BC5762068CAF3E24A2683B1B8A88 | SHA256:A8ACCFCFEB51BD73DF23B91F4D89FF1A9EB7438EF5B12E8AFDA1A6FF1769E89D | |||
| 2476 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:5F65BF0EE06E5CCF027FBDD12ED39DD6 | SHA256:0FAA05F1CB37B2A0357FFACCB88F92638896A4916BFA0F1C0FFA5A57644ED261 | |||
| 2476 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:1AABA6BB0BD88C1B88B2A8F20509112B | SHA256:4D5D7629FB8E48ACA8A48F98E1D5EE5E60B4B2933437A1A574095676F39D5358 | |||
| 6536 | svchost.exe | C:\Users\admin\Desktop\._cache_svchost.exe | executable | |
MD5:670D1014EC5713D005F8DDFEFC495A9E | SHA256:70C6D555938FDC95C03F98A7A3A37B607D1DCE623663479082C5B9514CAA04FD | |||
| 6808 | ._cache_svchost.exe | C:\Users\admin\AppData\Local\Temp\tmp704A.tmp.bat | text | |
MD5:C473E1A0AA1280E74EE8327CD089563E | SHA256:B5C43B42E19FB8519A5603725EF83DA4B651F2A794DB6A039F0099E869A30F68 | |||
| 2476 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\DDE8B1B7E253A9758EC380BD648952AF_68D058512F3515153DEB95A1F4E72552 | binary | |
MD5:B89424BB626B300FF7ADFA1161C6DE25 | SHA256:C3A38C2962568975563281BB01BFAD14D2A3B2ED79CD6AD89CC37FA742F4B7C2 | |||
| 2476 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DDE8B1B7E253A9758EC380BD648952AF_68D058512F3515153DEB95A1F4E72552 | binary | |
MD5:46F8B4BEC0FB86A6A3B0BCCF42003825 | SHA256:41ED056EE2437EBD86365A4DD937DE247D6FEA6108E9DD23B47D842D55839469 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
68
DNS requests
23
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1536 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6616 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2476 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
2476 | Synaptics.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
2476 | Synaptics.exe | GET | 200 | 172.217.23.99:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCnNXjqMmu3chAgO%2BmpN88J | unknown | — | — | whitelisted |
6664 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2476 | Synaptics.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
2476 | Synaptics.exe | GET | 200 | 172.217.23.99:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEHGN%2BKTRSIp4CcztJxB9gYQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3972 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4056 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1536 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1536 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
xred.mooo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
1948 | svchost.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
1948 | svchost.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 30 |
1948 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
1948 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
14 ETPRO signatures available at the full report