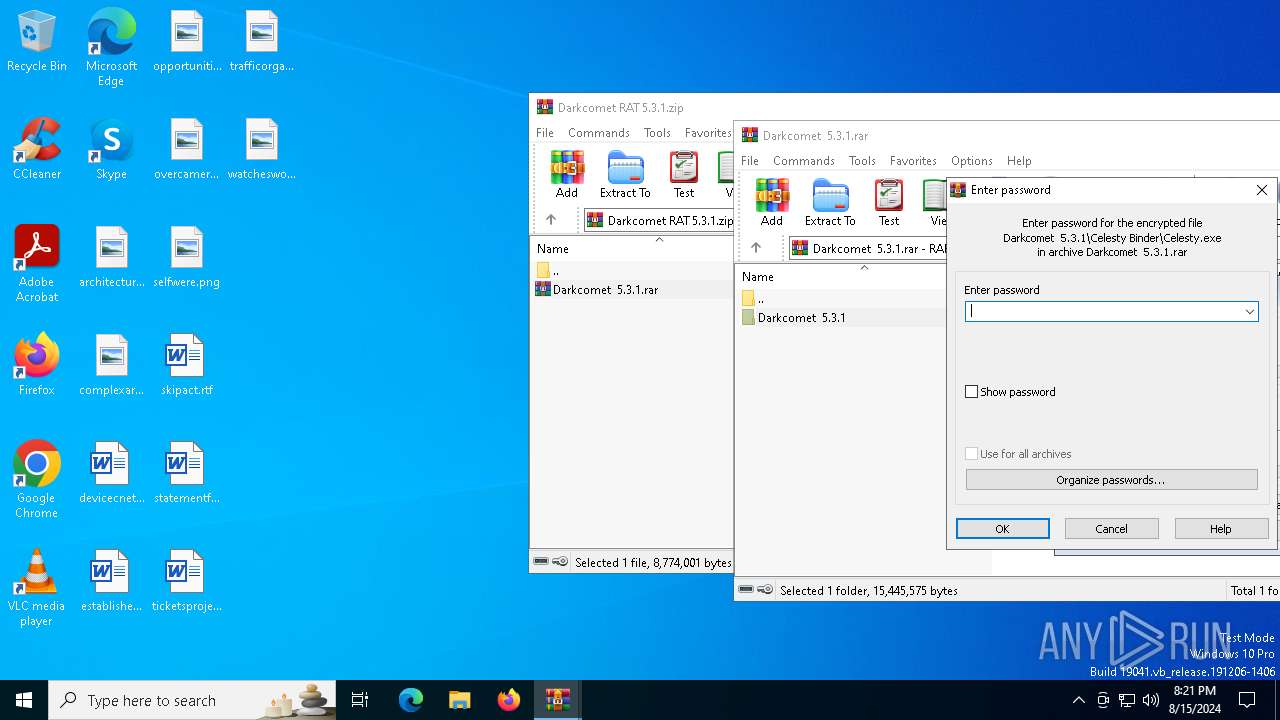
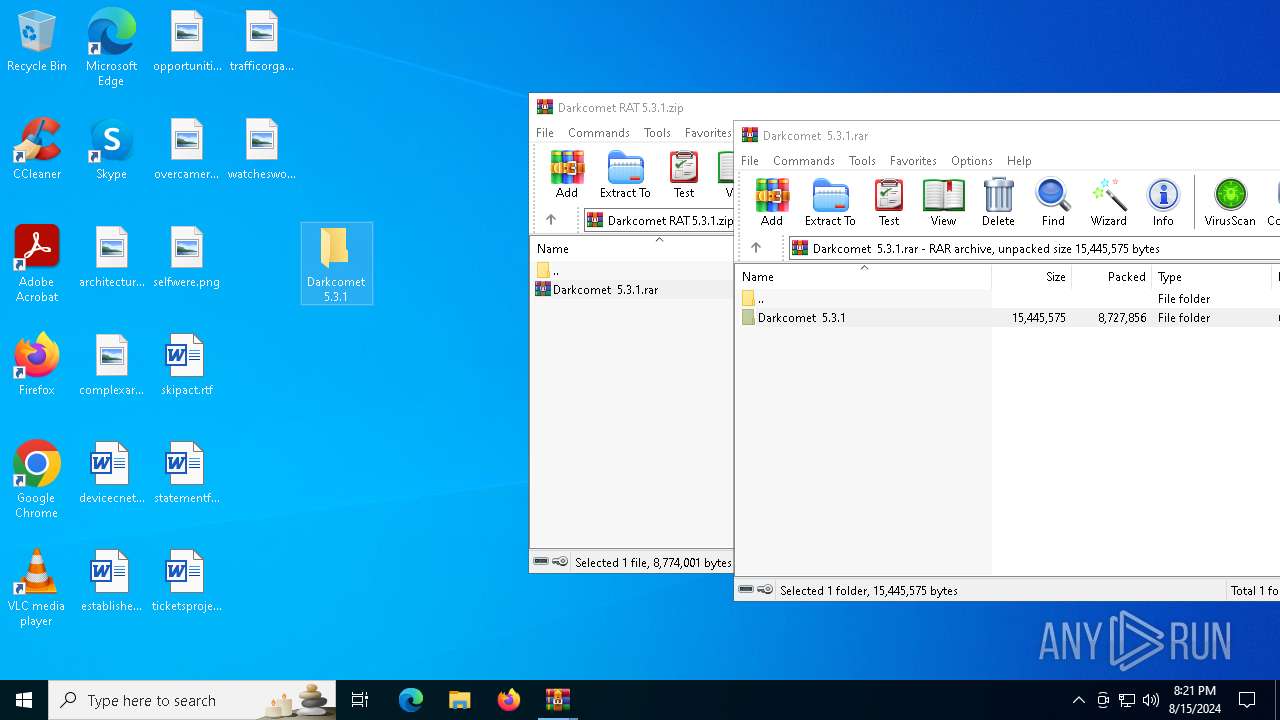
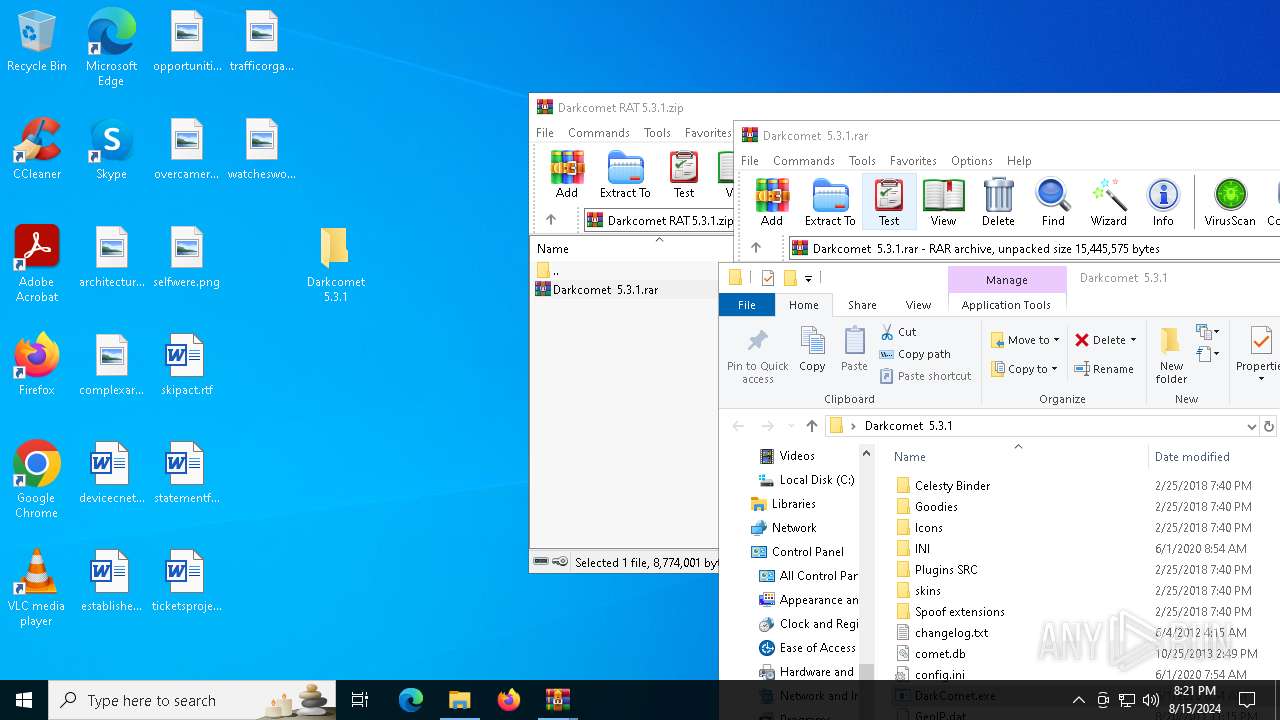
| File name: | Darkcomet RAT 5.3.1.zip |
| Full analysis: | https://app.any.run/tasks/78066446-3e1d-4861-b3d7-84e0cc6c621c |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | August 15, 2024, 20:20:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B81C14A01128F801AD3B976B9983662D |
| SHA1: | F618DCED3D25F65E524E9DCA116B6D54F9389F6D |
| SHA256: | 8899EA5C26453CCF0855540A6215A5D4827C336E06BD067B83AFE5DB705CD64B |
| SSDEEP: | 98304:+VCzJdxH9TQK4lHhqpYm2WtV3K5EjuRhOf9te/CP+MMcHWlbvHaaHkLNR+xRUOr/:JLj2LTH5exZi2/5NB6 |
MALICIOUS
Changes the login/logoff helper path in the registry
- DarkComet.exe (PID: 3028)
Changes the autorun value in the registry
- msdcsc.exe (PID: 3076)
- DarkComet.exe (PID: 5040)
- DarkComet.exe (PID: 4788)
- DarkComet.exe (PID: 3028)
DARKCOMET has been detected (YARA)
- msdcsc.exe (PID: 3076)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 6344)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2228)
- WinRAR.exe (PID: 6344)
- DarkComet.exe (PID: 3028)
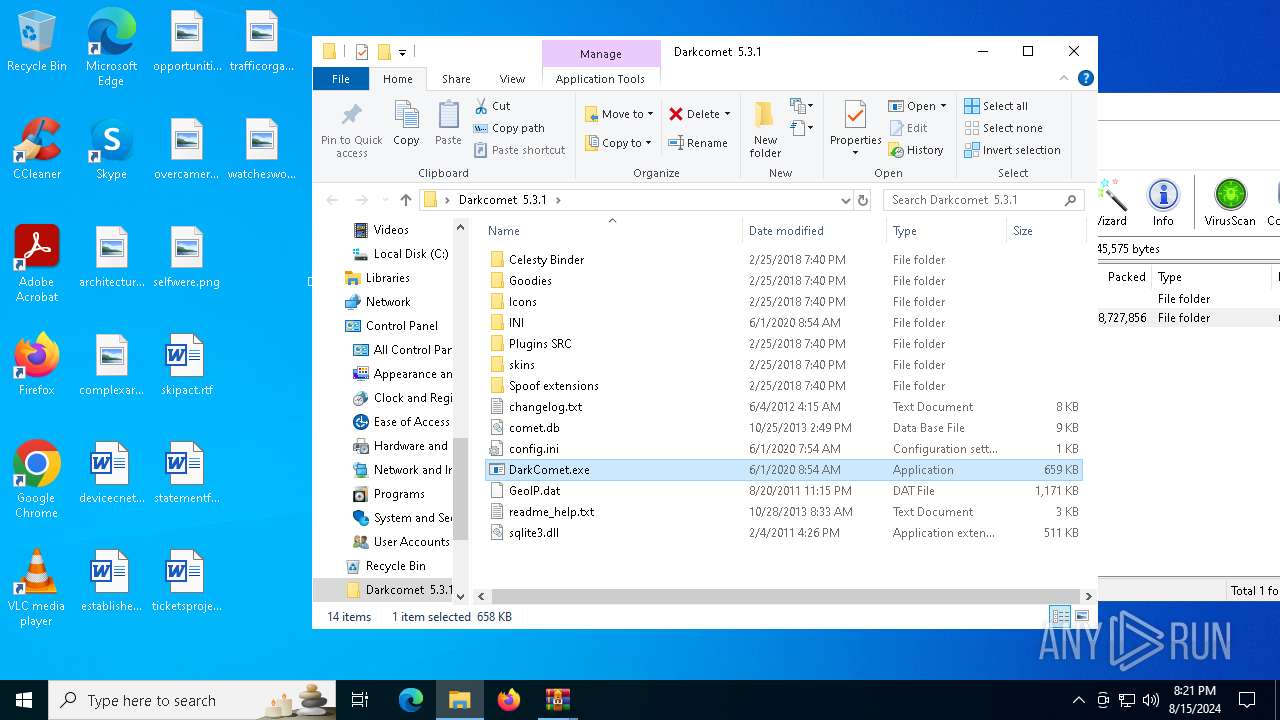
Drops the executable file immediately after the start
- DarkComet.exe (PID: 3028)
Start notepad (likely ransomware note)
- DarkComet.exe (PID: 3028)
Starts itself from another location
- DarkComet.exe (PID: 3028)
There is functionality for communication over UDP network (YARA)
- msdcsc.exe (PID: 3076)
There is functionality for taking screenshot (YARA)
- msdcsc.exe (PID: 3076)
Executable content was dropped or overwritten
- DarkComet.exe (PID: 3028)
Reads the date of Windows installation
- DarkComet.exe (PID: 3028)
INFO
Drops a (possible) Coronavirus decoy
- WinRAR.exe (PID: 2228)
- WinRAR.exe (PID: 6656)
Reads the computer name
- DarkComet.exe (PID: 3028)
- msdcsc.exe (PID: 3076)
- DarkComet.exe (PID: 6852)
- DarkComet.exe (PID: 5040)
- DarkComet.exe (PID: 4788)
- TextInputHost.exe (PID: 6160)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2228)
- WinRAR.exe (PID: 6656)
Creates files or folders in the user directory
- DarkComet.exe (PID: 3028)
- msdcsc.exe (PID: 3076)
Checks supported languages
- DarkComet.exe (PID: 3028)
- msdcsc.exe (PID: 3076)
- DarkComet.exe (PID: 6852)
- DarkComet.exe (PID: 5040)
- DarkComet.exe (PID: 4788)
- TextInputHost.exe (PID: 6160)
Manual execution by a user
- DarkComet.exe (PID: 5040)
- DarkComet.exe (PID: 4788)
- DarkComet.exe (PID: 6852)
- Taskmgr.exe (PID: 6864)
- Taskmgr.exe (PID: 4540)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 4540)
Process checks computer location settings
- DarkComet.exe (PID: 3028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (33.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:15 23:19:26 |
| ZipCRC: | 0x5122c283 |
| ZipCompressedSize: | 8761838 |
| ZipUncompressedSize: | 8774001 |
| ZipFileName: | Darkcomet RAT 5.3.1/Darkcomet 5.3.1.rar |
Total processes
145
Monitored processes
14
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2228 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6344.3552\Darkcomet 5.3.1.rar" | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
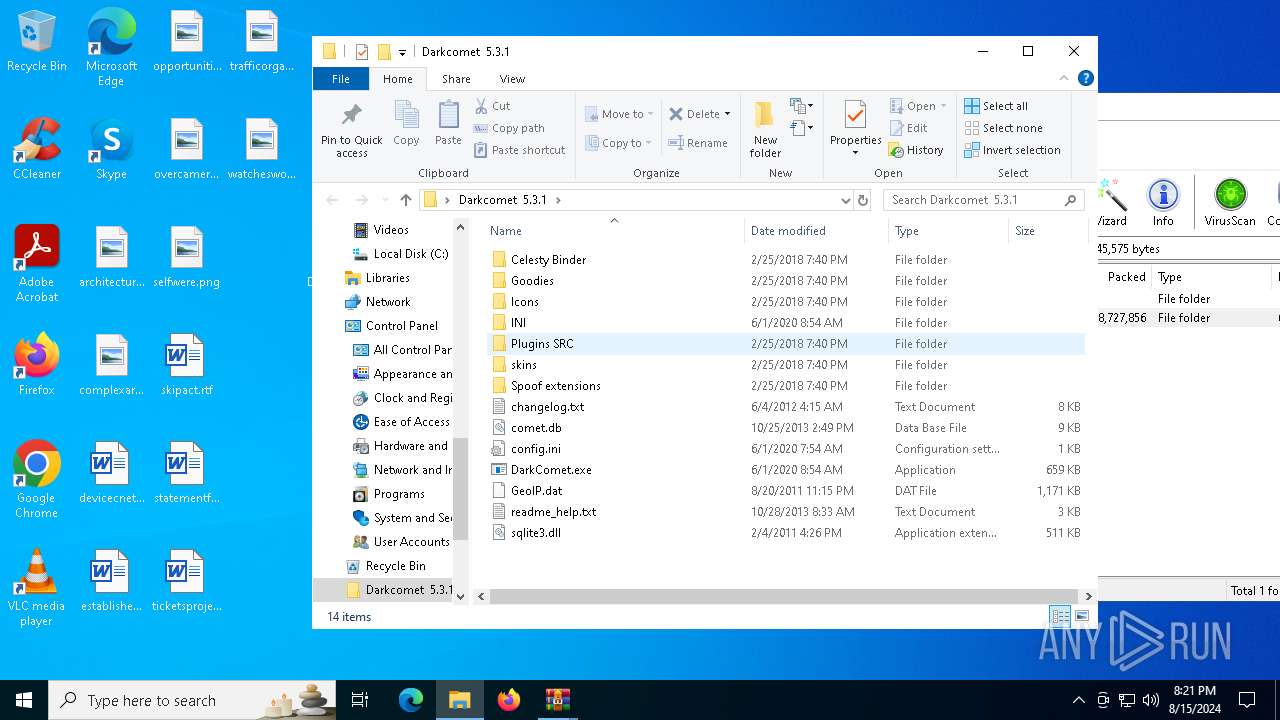
| 3028 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\DarkComet.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\DarkComet.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3076 | "C:\Users\admin\AppData\Roaming\MSDCSC\msdcsc.exe" | C:\Users\admin\AppData\Roaming\MSDCSC\msdcsc.exe | DarkComet.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 4540 | "C:\WINDOWS\system32\taskmgr.exe" /7 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4788 | "C:\Users\admin\Desktop\Darkcomet 5.3.1\DarkComet.exe" | C:\Users\admin\Desktop\Darkcomet 5.3.1\DarkComet.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 5040 | "C:\Users\admin\Desktop\Darkcomet 5.3.1\DarkComet.exe" | C:\Users\admin\Desktop\Darkcomet 5.3.1\DarkComet.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 6160 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6344 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Darkcomet RAT 5.3.1.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6656 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6344.6730\Darkcomet 5.3.1.rar" | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
27 534
Read events
27 421
Write events
112
Delete events
1
Modification events
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Darkcomet RAT 5.3.1.zip | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
10
Suspicious files
268
Text files
101
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6344.3552\Darkcomet 5.3.1.rar | — | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\Celesty Binder\Lang\ES.ini | text | |
MD5:4745B84E71D23454D2535CC608DE57D0 | SHA256:EB0553309ACD121B01566C1CA297ED46E896E3AD11C486971E8FA7275A1FF061 | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\Celesty Binder\Lang\SR.ini | text | |
MD5:FDFC0EE3AD0F395E3078F600ED9BA689 | SHA256:37DCDA2CD0682A3EDFE354111E0DD637BE6581A71E6C240AE5729CE9F6A05EF9 | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\Celesty Binder\Lang\GR.ini | text | |
MD5:8B35CDF90F3D89D2502E1F61B2BBF631 | SHA256:FCA01673CB23ABD479B6D54D19A40A87E9D72B90ECC7F5D59AF14D192CC07C7C | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\Celesty Binder\Lang\IT.ini | binary | |
MD5:1CB447996787264785C83D110C67AB13 | SHA256:840DB2223BC47B37C44393BCE4CA8583D373EF6D70B6BC9143561190AA16CDCB | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\Celesty Binder\Celesty.exe | executable | |
MD5:C3009EE63BC661D9EA75EAEB256448CA | SHA256:0BB88564A22BFD6D9AD6E4D8EFA9077792A7B6094C2A0F865D70C43E11507352 | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\comet.db | sqlite | |
MD5:A2FA02319EBECF1DA1BC197194BFAA4A | SHA256:8BCF0D3BB80840AC5D6B8D5888EFDD5DEDDA4E620F71A47C3D559DD6FC1A5222 | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\Celesty Binder\readme.txt | text | |
MD5:EC0EB4AD970DC1D264BC6C6E7471428D | SHA256:BEC0F54669D35669D4E90E4AA588B96002B8A4E85048CE1CBF707F7F86AC250D | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\Celesty Binder\Lang\EN.ini | text | |
MD5:D5B95D8DBCDCC5BE0290067BE9043009 | SHA256:48A43817F513A7DE5F033F842EA71DCEC7CFE45E2EDC87BE844E461D99E2572E | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2228.3852\Darkcomet 5.3.1\Celesty Binder\Lang\NO.ini | text | |
MD5:832AF9C517EA93DF140200EADFEB3BD6 | SHA256:570A67620D3E396B4BAD5AE46F7D72A4654625C965BDF04BD23D9341E867AC46 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
53
DNS requests
78
Threats
56
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6512 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6480 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4576 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5924 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5924 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
alfeed2.ddns.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |