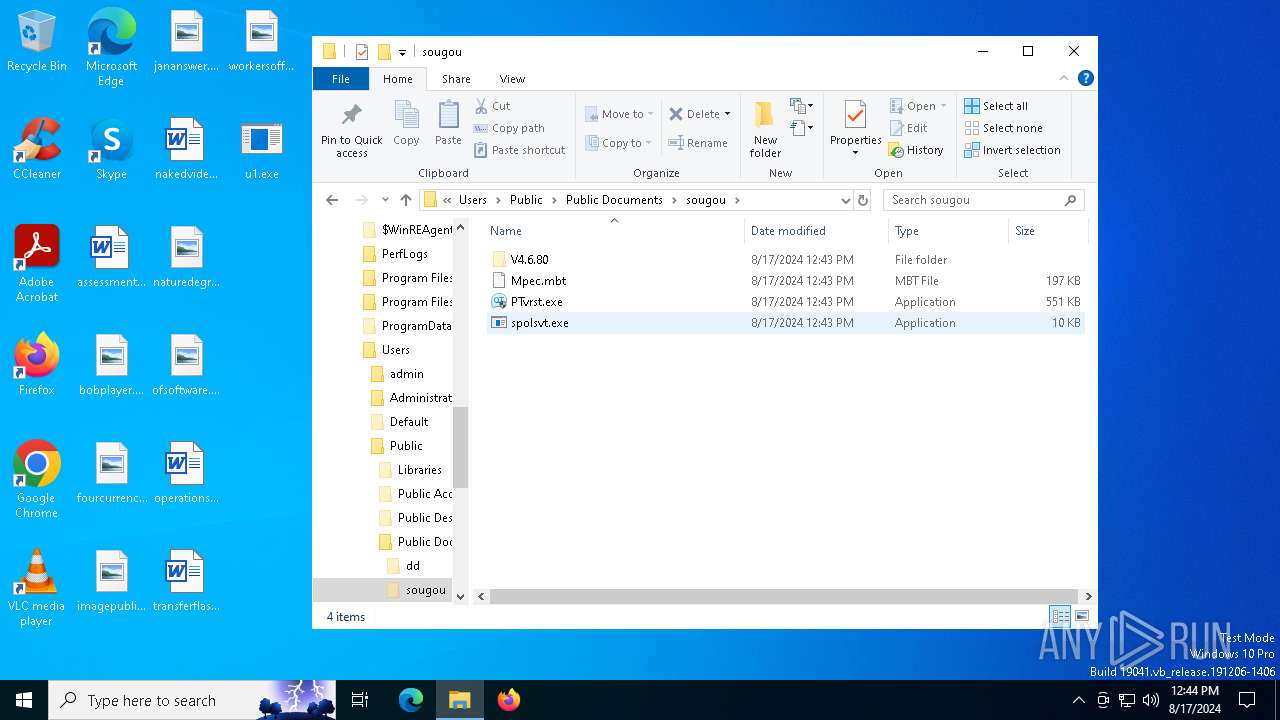
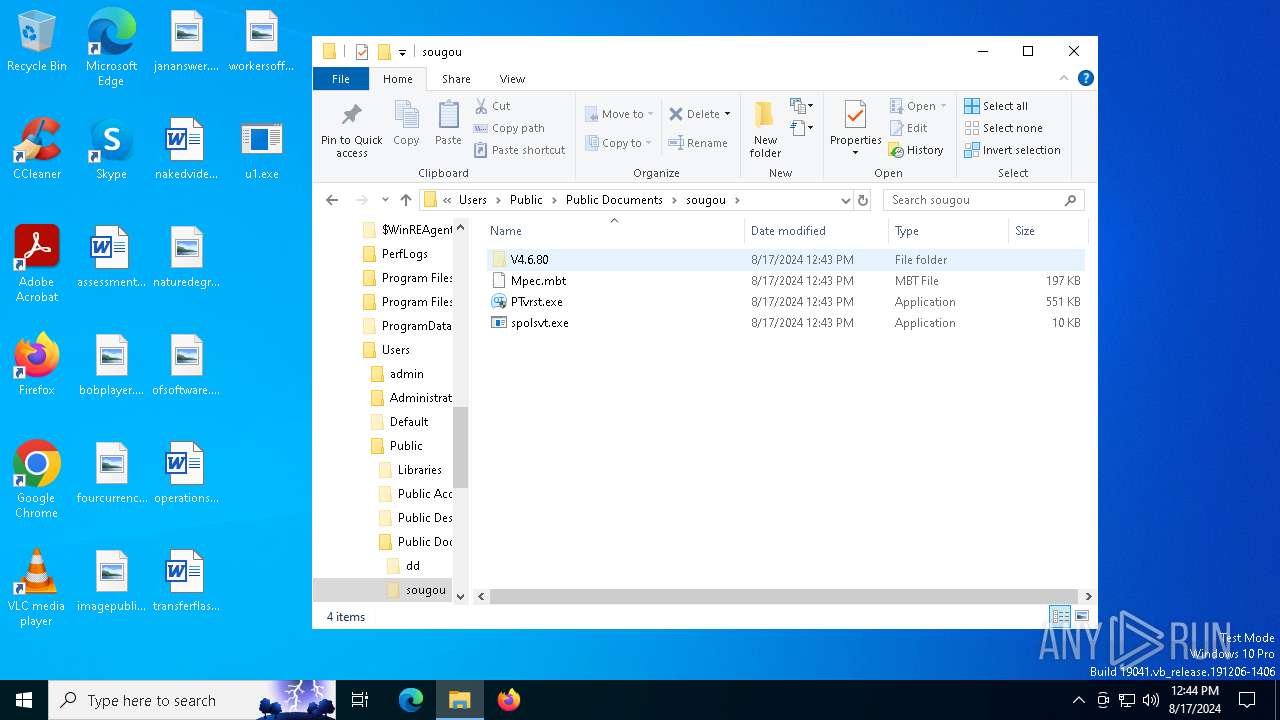
| File name: | 0x0002000000022ab4-26 |
| Full analysis: | https://app.any.run/tasks/793dd37d-f320-4071-9283-b6a861e6505a |
| Verdict: | Malicious activity |
| Threats: | FatalRAT is a malware that gives hackers remote access and control of the system and lets them steal sensitive information like login credentials and financial data. FatalRAT has been associated with cyber espionage campaigns, particularly targeting organizations in the Asia-Pacific (APAC) region. |
| Analysis date: | August 17, 2024, 12:42:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 88D245BF3DEE802B32EBB65E55FA2299 |
| SHA1: | 7C57652A6C91C837537B7DA4DB5AE70571C3CABA |
| SHA256: | 888B722DD8C0F1389856DBBE154FD76FD6E7118999CDCCF67F99433FA39D0D4A |
| SSDEEP: | 98304:tAjfEKQyAKv44X/Zbqqr5lu/9Y+6cJu0wXhQKfrgpcucjwgrmahI86ydKRYl11Ro:++yrwr |
MALICIOUS
UAC/LUA settings modification
- u1.exe (PID: 6868)
FATALRAT has been detected (SURICATA)
- spolsvt.exe (PID: 6368)
Connects to the CnC server
- spolsvt.exe (PID: 6368)
Changes the autorun value in the registry
- u1.exe (PID: 6868)
SUSPICIOUS
Drops the executable file immediately after the start
- 0x0002000000022ab4-26.exe (PID: 6476)
- u1.exe (PID: 6868)
- spolsvt.exe (PID: 7000)
Process drops legitimate windows executable
- u1.exe (PID: 6868)
- spolsvt.exe (PID: 7000)
- WinRAR.exe (PID: 6676)
Executable content was dropped or overwritten
- u1.exe (PID: 6868)
- spolsvt.exe (PID: 7000)
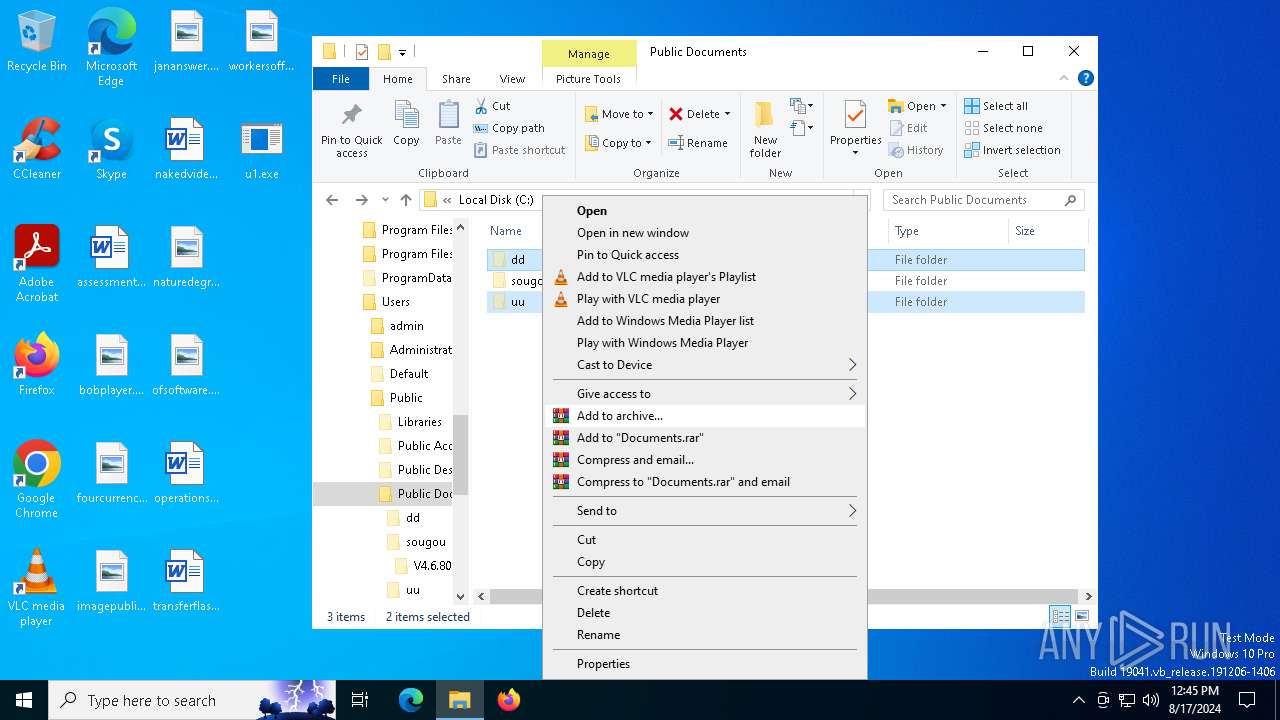
Likely accesses (executes) a file from the Public directory
- QTalk.exe (PID: 6944)
- spolsvt.exe (PID: 7000)
- spolsvt.exe (PID: 6368)
- svcoth.exe (PID: 6204)
- WinRAR.exe (PID: 6676)
- curl.exe (PID: 4592)
- powershell.exe (PID: 6628)
- curl.exe (PID: 6468)
Starts itself from another location
- u1.exe (PID: 6868)
Starts a Microsoft application from unusual location
- spolsvt.exe (PID: 7000)
- spolsvt.exe (PID: 6368)
- svcoth.exe (PID: 6204)
Contacting a server suspected of hosting an CnC
- spolsvt.exe (PID: 6368)
Connects to unusual port
- spolsvt.exe (PID: 6368)
INFO
Checks supported languages
- 0x0002000000022ab4-26.exe (PID: 6476)
- TextInputHost.exe (PID: 6740)
- u1.exe (PID: 6868)
- QTalk.exe (PID: 6944)
- spolsvt.exe (PID: 7000)
- spolsvt.exe (PID: 6368)
- svcoth.exe (PID: 6204)
- curl.exe (PID: 6468)
- curl.exe (PID: 4592)
Manual execution by a user
- u1.exe (PID: 6868)
- WinRAR.exe (PID: 6676)
- powershell.exe (PID: 6628)
Reads the computer name
- TextInputHost.exe (PID: 6740)
- spolsvt.exe (PID: 6368)
- curl.exe (PID: 4592)
Process checks whether UAC notifications are on
- u1.exe (PID: 6868)
Reads CPU info
- spolsvt.exe (PID: 6368)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:08:14 19:57:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 110592 |
| InitializedDataSize: | 5369856 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x130c0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileDescription: | 驱动人生 |
| LegalCopyright: | 驱动人生 |
| OriginalFileName: | 驱动人生.exe |
| ProductVersion: | 5.3.9.9 |
Total processes
143
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
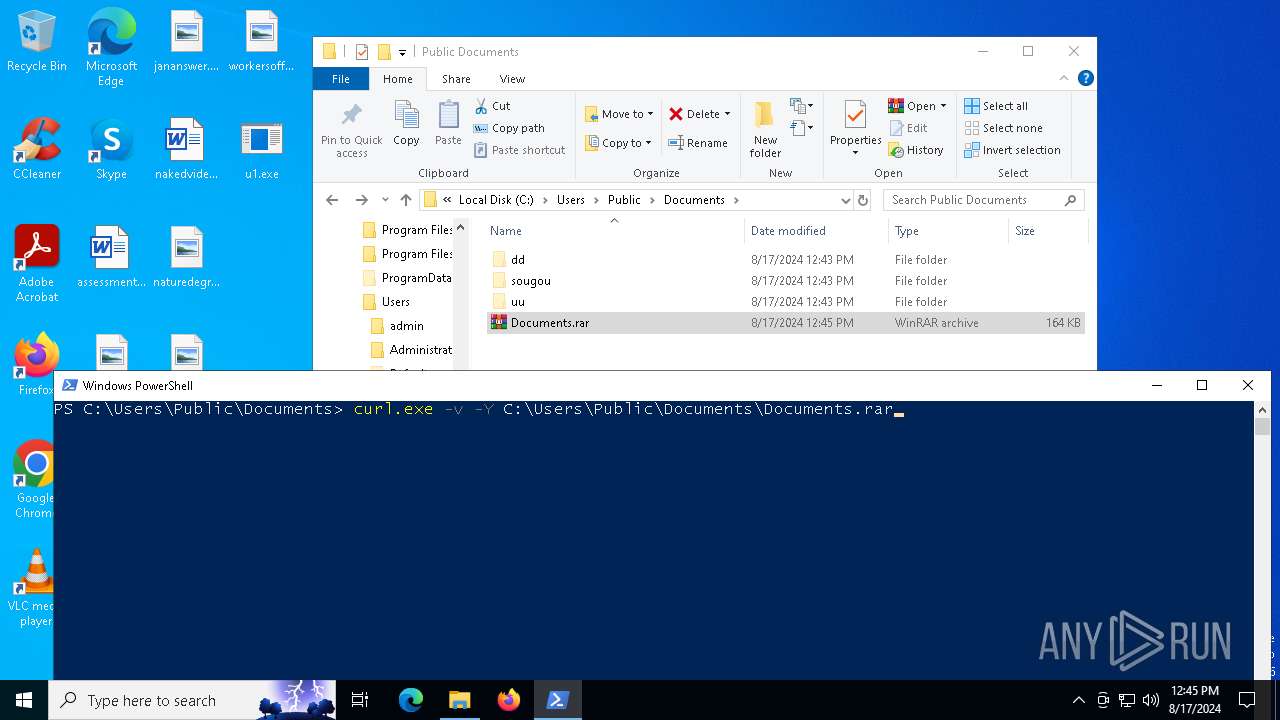
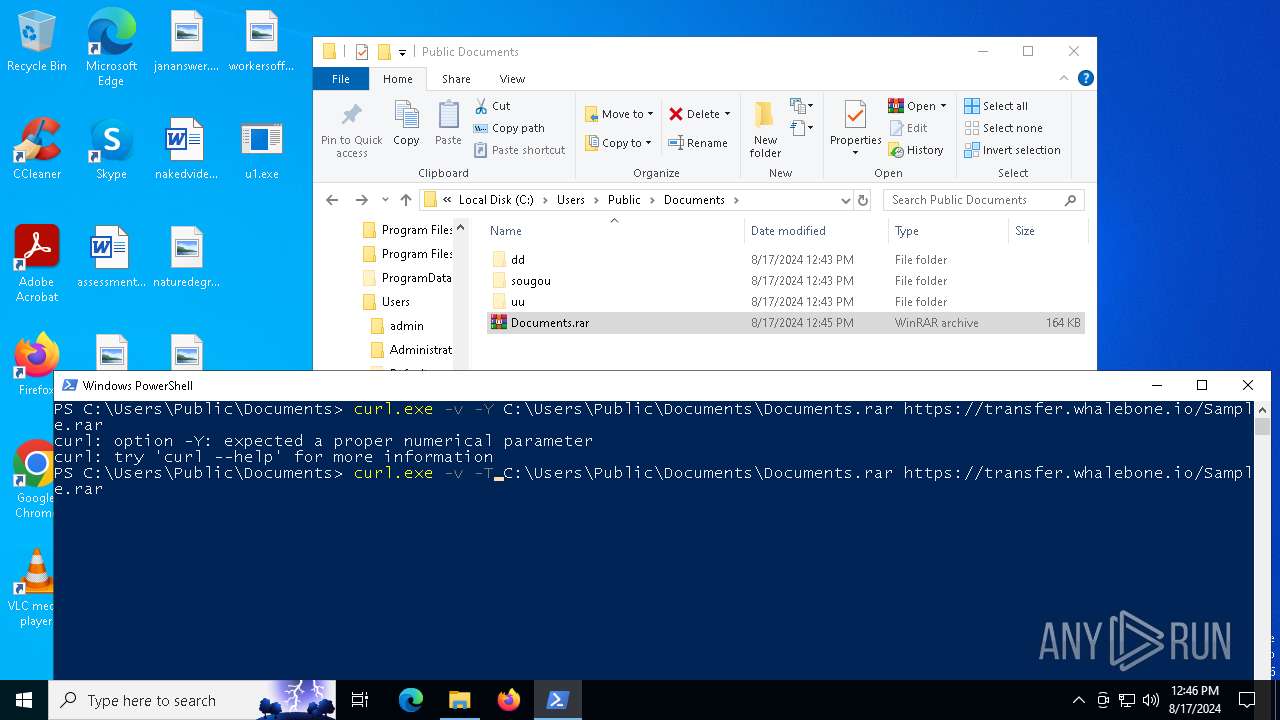
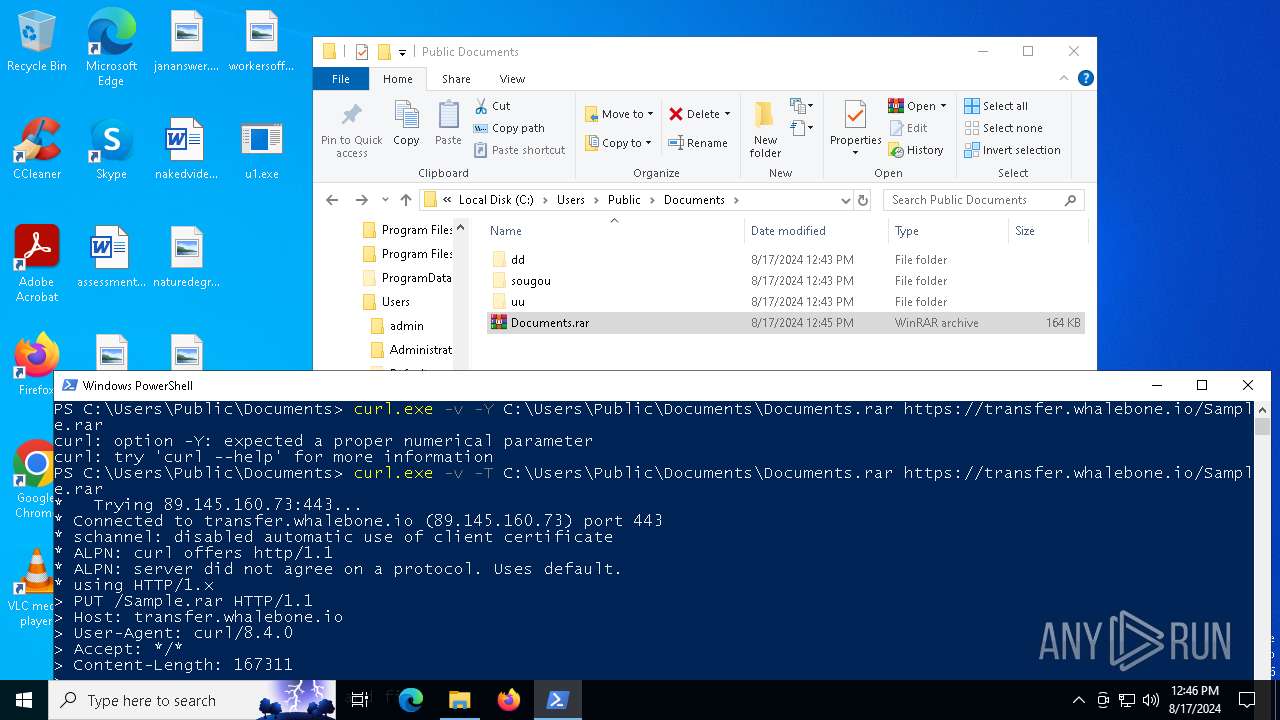
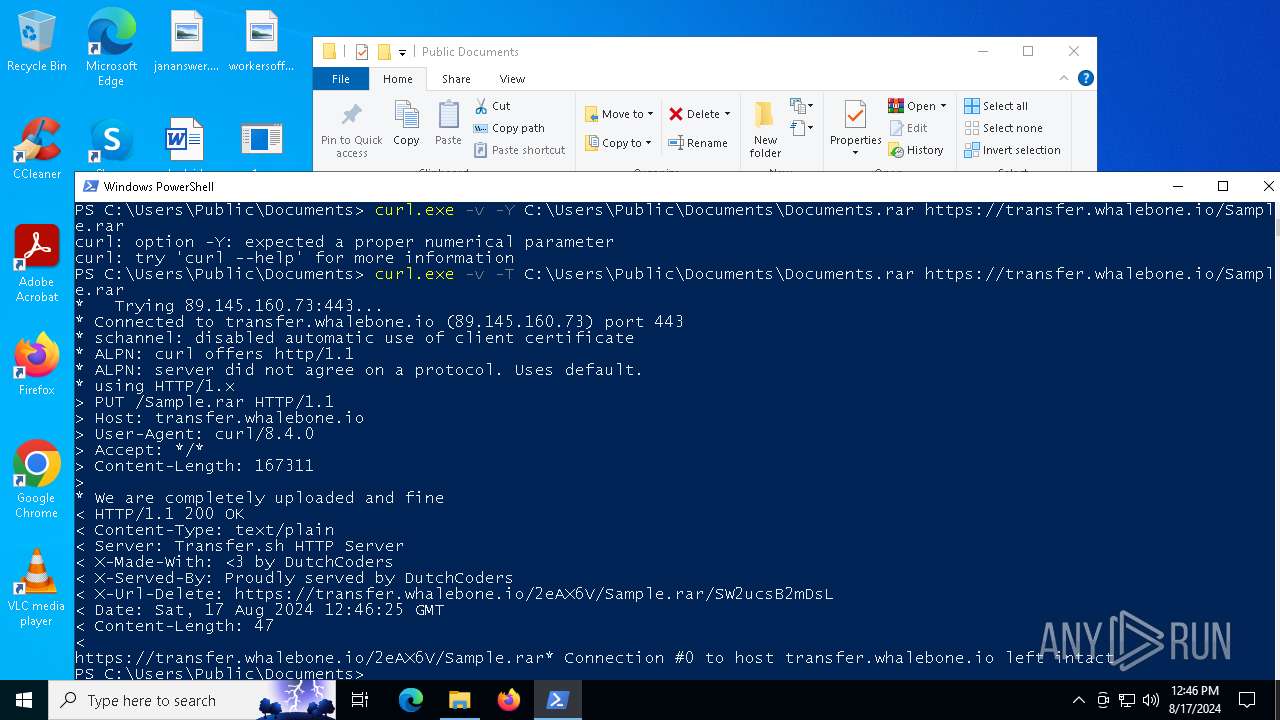
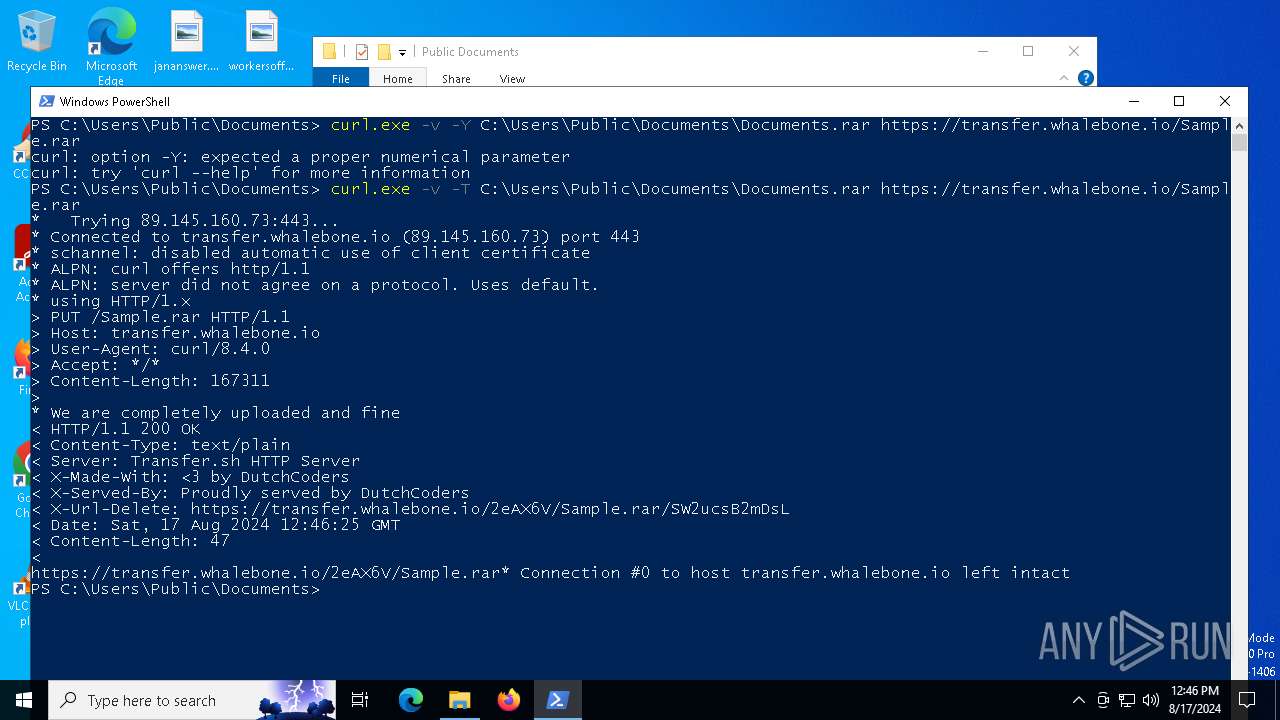
| 4592 | "C:\WINDOWS\system32\curl.exe" -v -T C:\Users\Public\Documents\Documents.rar https://transfer.whalebone.io/Sample.rar | C:\Windows\System32\curl.exe | powershell.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
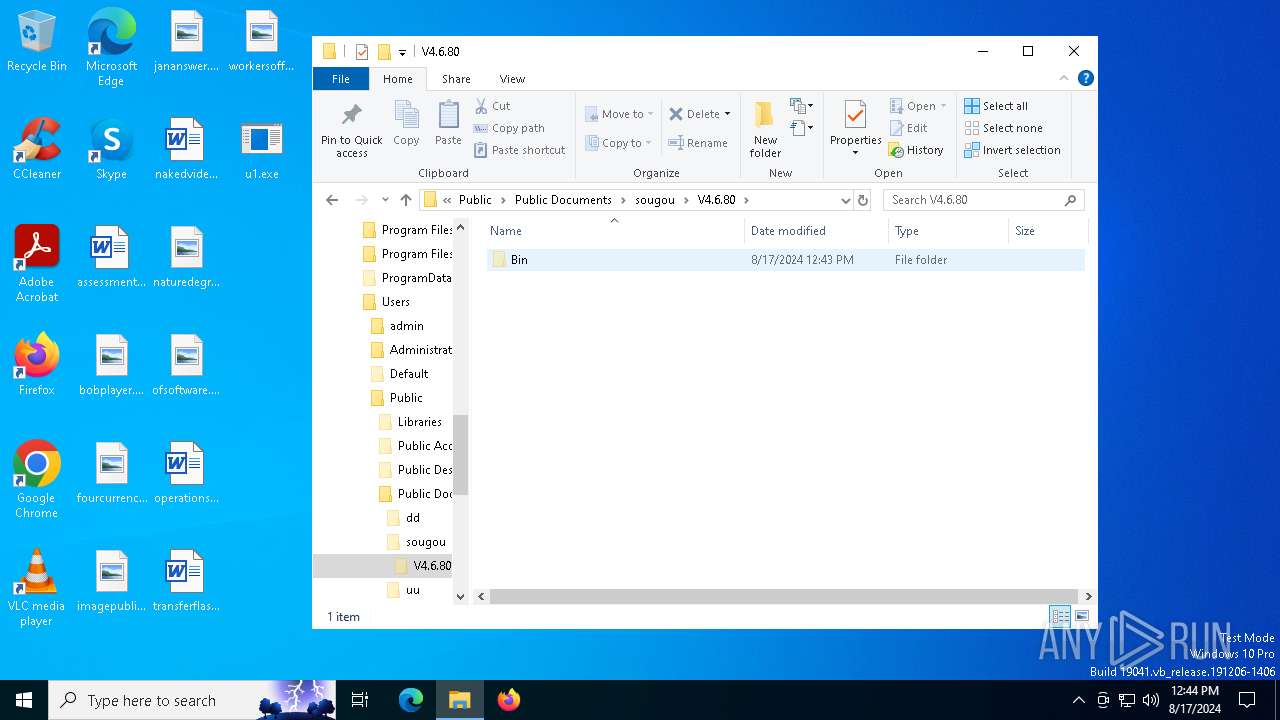
| 6204 | C:\Users\Public\Documents\uu\svcoth.exe | C:\Users\Public\Documents\uu\svcoth.exe | — | spolsvt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Version: 5.1.2600.0 (xpclient.010817-1148) Modules
| |||||||||||||||
| 6356 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6368 | C:\Users\Public\Documents\dd\spolsvt.exe | C:\Users\Public\Documents\dd\spolsvt.exe | spolsvt.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Version: 5.1.2600.0 (xpclient.010817-1148) Modules
| |||||||||||||||
| 6468 | "C:\WINDOWS\system32\curl.exe" -v -Y C:\Users\Public\Documents\Documents.rar https://transfer.whalebone.io/Sample.rar | C:\Windows\System32\curl.exe | — | powershell.exe | |||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 2 Version: 8.4.0 Modules
| |||||||||||||||
| 6476 | "C:\Users\admin\Desktop\0x0002000000022ab4-26.exe" | C:\Users\admin\Desktop\0x0002000000022ab4-26.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 驱动人生 Exit code: 0 Modules
| |||||||||||||||
| 6628 | "PowerShell.exe" -noexit -command Set-Location -literalPath 'C:\Users\Public\Documents' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
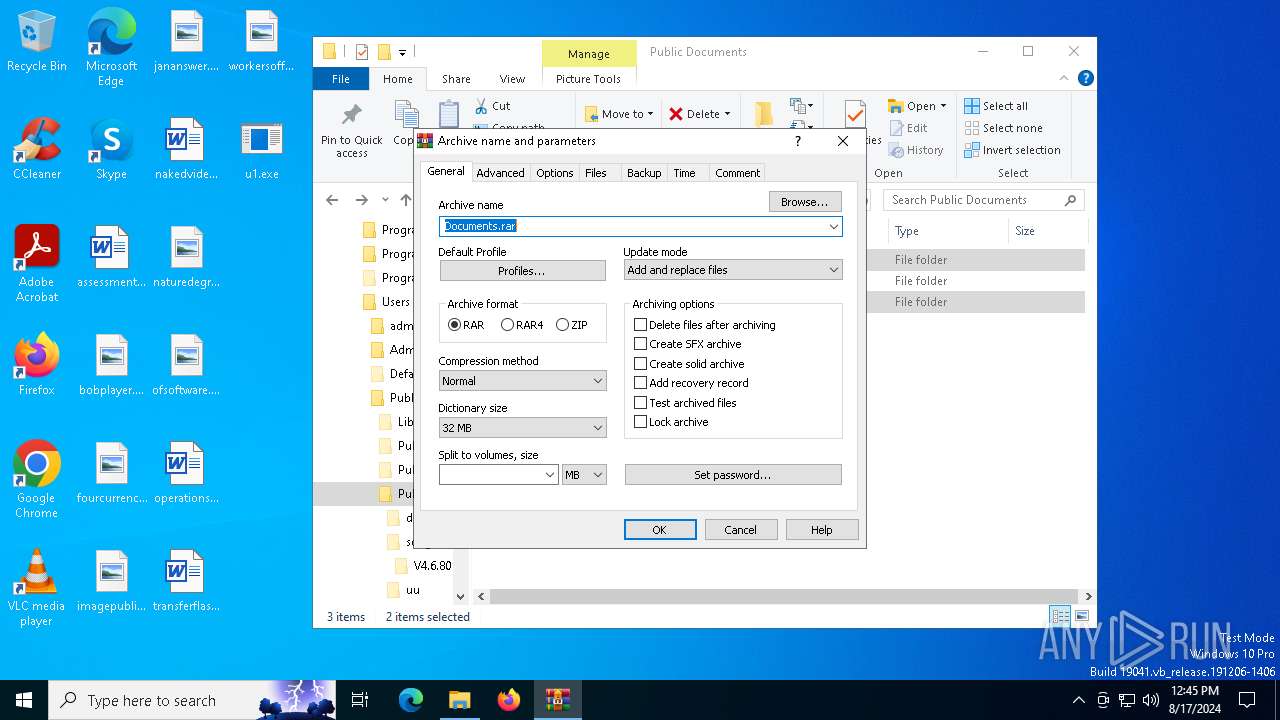
| 6676 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- . C:\Users\Public\Documents\dd C:\Users\Public\Documents\uu | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6688 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6740 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
Total events
11 728
Read events
11 702
Write events
26
Delete events
0
Modification events
| (PID) Process: | (6868) u1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | write | Name: | C:\Users\Public\Documents\sougou\PTvrst.exe |
Value: ~ RUNASADMIN | |||
| (PID) Process: | (6868) u1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (6868) u1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Çý¶¯ÈËÉú |
Value: C:\Users\Public\Documents\sougou\PTvrst.exe | |||
| (PID) Process: | (6368) spolsvt.exe | Key: | HKEY_CURRENT_USER\System\CurrentControlSet\Services |
| Operation: | write | Name: | Group |
Value: ÓеÀ | |||
| (PID) Process: | (6368) spolsvt.exe | Key: | HKEY_CURRENT_USER\System\CurrentControlSet\Services |
| Operation: | write | Name: | InstallTime |
Value: 2024-08-17 12:43 | |||
| (PID) Process: | (6368) spolsvt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: spolsvt.exe | |||
| (PID) Process: | (6368) spolsvt.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | ID |
Value: 998081703 | |||
| (PID) Process: | (6368) spolsvt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\DWM |
| Operation: | write | Name: | SuppressDisableCompositionUI |
Value: 0 | |||
| (PID) Process: | (6676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
5
Suspicious files
8
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6868 | u1.exe | C:\Users\Public\Documents\sougou\PTvrst.exe | executable | |
MD5:B254C92BAC10E00139120BF72A5BAB1B | SHA256:1B2EEF220C8EA69589CDB4165A73A875D62255BE22F172EB8981D7B26F906A1A | |||
| 7000 | spolsvt.exe | C:\Users\Public\Documents\dd\spolsvt.exe | executable | |
MD5:CDCE4713E784AE069D73723034A957FF | SHA256:B29E48102ECB3D3614E8980A8B8CC63DD2B993C6346F466479244EC2B47B69D8 | |||
| 6628 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:74577AFAD2E896BDBC2A7719D3D60FEE | SHA256:1E6B27EC1A8E5C064194DE194B086BC745EB225E9FED8C8471E53E3D1DC20F7A | |||
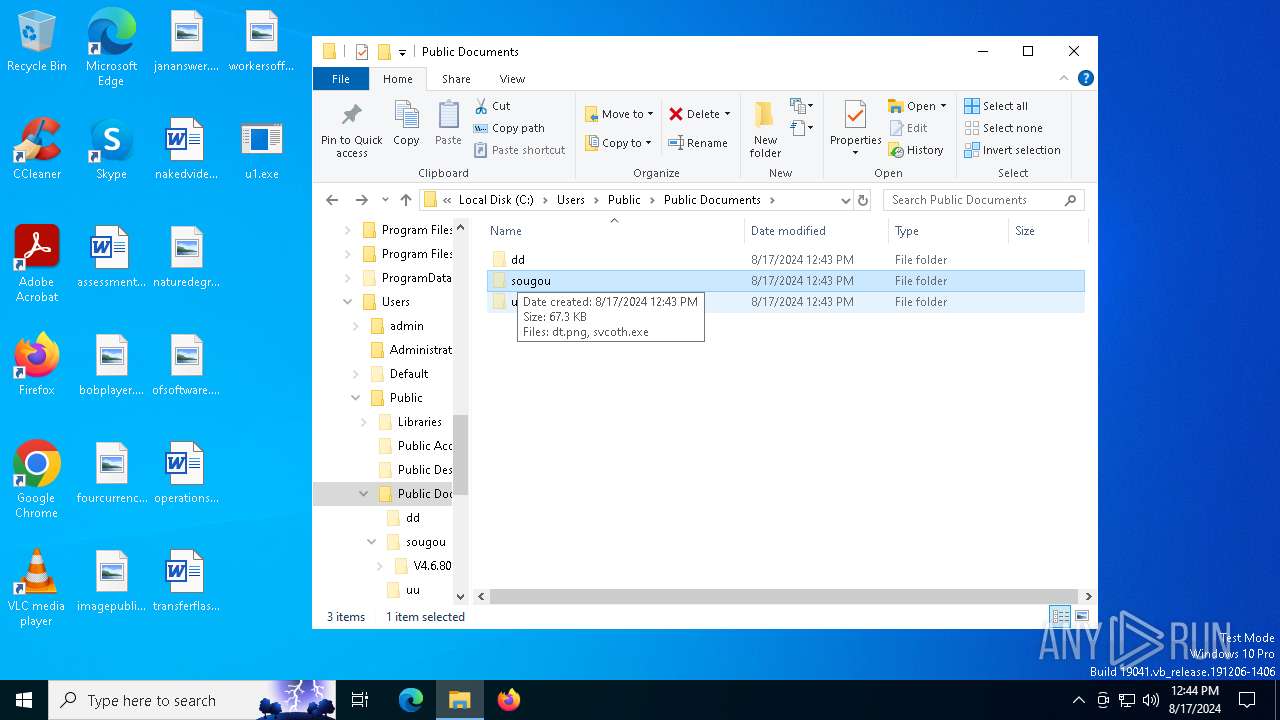
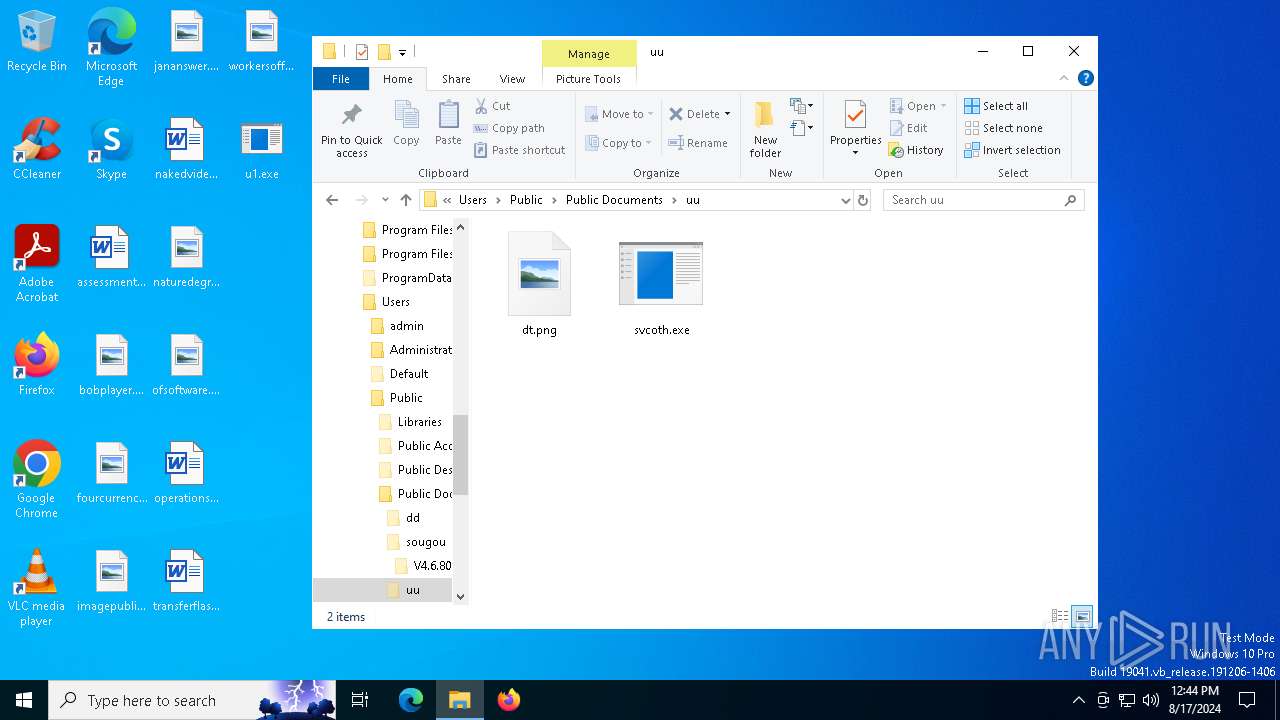
| 7000 | spolsvt.exe | C:\Users\Public\Documents\uu\dt.png | binary | |
MD5:16B48B25456A9D507EB7A0BFB8338BF0 | SHA256:34C013B6D09CA9F0CB8232B2C3E5384B39474D40CD191472BBBC21AA69401D1C | |||
| 6628 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-Interactive | binary | |
MD5:7F7251D0C00A4D010FE7EFA9FBCCCA55 | SHA256:9E94FB729E958C19A8986FE05BF4325C16B66182691F647AD09F446249989E7A | |||
| 6628 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1YIXL7PAVZCTZVMBM5ZA.temp | binary | |
MD5:74577AFAD2E896BDBC2A7719D3D60FEE | SHA256:1E6B27EC1A8E5C064194DE194B086BC745EB225E9FED8C8471E53E3D1DC20F7A | |||
| 6628 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10bc8b.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bpr2gtbv.wjz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7000 | spolsvt.exe | C:\Users\Public\Documents\dd\yh.png | binary | |
MD5:117E91E581EA17168E717BD56BC48A3F | SHA256:53E715D9F8540016083FBD343237087FCAEDEC05C17DC93087CADA2B312D937A | |||
| 6868 | u1.exe | C:\Users\Public\Documents\sougou\Mpec.mbt | binary | |
MD5:F1776F8A75946D171AD83BBD93F94D96 | SHA256:9C7689CD94796A74A1B7397818A10D1896F40EF7FA84C006C8BA3927F8FFE967 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
45
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2456 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6932 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
768 | lsass.exe | GET | 200 | 2.16.202.121:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgN1znF5sGbSUaj3fYrkNhSayQ%3D%3D | unknown | — | — | whitelisted |
5880 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 304 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1784 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 104.126.37.152:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2456 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2456 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
seo.wccabc.com |
| unknown |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6368 | spolsvt.exe | Malware Command and Control Activity Detected | ET MALWARE FatalRAT CnC Activity |
6368 | spolsvt.exe | Malware Command and Control Activity Detected | ET MALWARE FatalRAT CnC Activity |