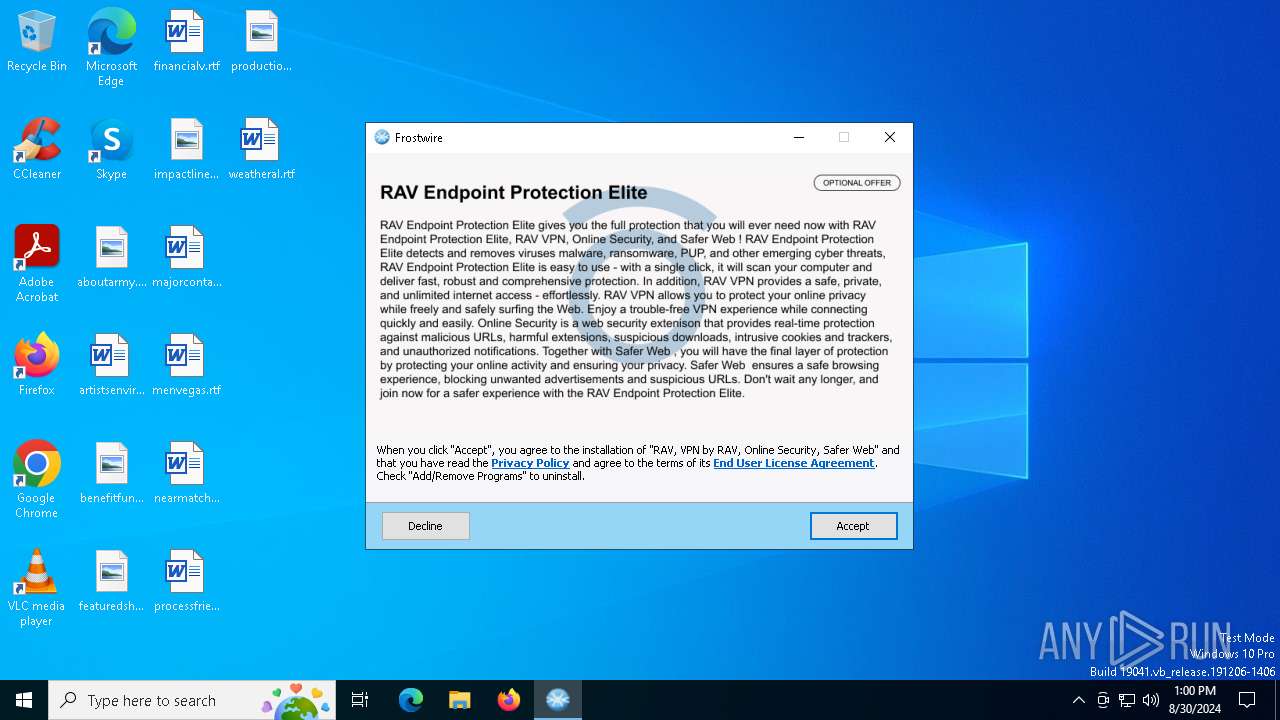
| File name: | frostwire-6.13.2.windows.exe |
| Full analysis: | https://app.any.run/tasks/e4454704-a637-453c-8f90-e0bf665b1304 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | August 30, 2024, 12:59:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | BD352ADA33C61CEB9DB09D3601B302BC |
| SHA1: | 2ECE05E008ECA40C17172AE72B5C0D29F81B664B |
| SHA256: | 887C5AF40BA3A354696EE0BE278D482BDCA6A262E3A0520BB32368CA17AC5357 |
| SSDEEP: | 98304:d+QqZ8f9adP3sBI6IauBPDZONh4DkLmDYfuXqGQoHbHL7WdY5J18sFbtm/PXLdGV:rrAnyi |
MALICIOUS
Deletes shadow copies
- frostwire-6.13.2.windows.exe (PID: 1288)
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 7160)
- rsEngineSvc.exe (PID: 6796)
- rsVPNSvc.exe (PID: 7916)
- rsDNSSvc.exe (PID: 1448)
Create files in the Startup directory
- FrostWire.exe (PID: 4364)
Changes the autorun value in the registry
- rundll32.exe (PID: 4576)
- rundll32.exe (PID: 8068)
SUSPICIOUS
Reads security settings of Internet Explorer
- frostwire-6.13.2.windows.tmp (PID: 2208)
- frostwire-6.13.2.windows.exe (PID: 1288)
- frostwire-6.13.2.windows.tmp (PID: 7052)
- prod0.exe (PID: 6128)
- FrostWire.exe (PID: 4364)
- UnifiedStub-installer.exe (PID: 7160)
- rsWSC.exe (PID: 6908)
- rsEngineSvc.exe (PID: 6788)
- rsEDRSvc.exe (PID: 3908)
- rsEngineSvc.exe (PID: 6796)
- rsVPNSvc.exe (PID: 7840)
- rsDNSSvc.exe (PID: 7820)
Reads the date of Windows installation
- frostwire-6.13.2.windows.tmp (PID: 2208)
- frostwire-6.13.2.windows.tmp (PID: 7052)
- prod0.exe (PID: 6128)
- rsEDRSvc.exe (PID: 1280)
- rsEngineSvc.exe (PID: 6796)
Executable content was dropped or overwritten
- frostwire-6.13.2.windows.exe (PID: 1076)
- frostwire-6.13.2.windows.exe (PID: 5140)
- frostwire-6.13.2.windows.tmp (PID: 7052)
- frostwire-6.13.2.windows.exe (PID: 1288)
- ogjrjir4.exe (PID: 7008)
- prod0.exe (PID: 6128)
- UnifiedStub-installer.exe (PID: 7160)
- FrostWire.exe (PID: 4364)
Drops the executable file immediately after the start
- frostwire-6.13.2.windows.exe (PID: 1076)
- frostwire-6.13.2.windows.exe (PID: 5140)
- frostwire-6.13.2.windows.tmp (PID: 7052)
- frostwire-6.13.2.windows.exe (PID: 1288)
- prod0.exe (PID: 6128)
- ogjrjir4.exe (PID: 7008)
- UnifiedStub-installer.exe (PID: 7160)
- FrostWire.exe (PID: 4364)
Reads the Windows owner or organization settings
- frostwire-6.13.2.windows.tmp (PID: 7052)
The process creates files with name similar to system file names
- frostwire-6.13.2.windows.exe (PID: 1288)
- UnifiedStub-installer.exe (PID: 7160)
Malware-specific behavior (creating "System.dll" in Temp)
- frostwire-6.13.2.windows.exe (PID: 1288)
Process drops legitimate windows executable
- frostwire-6.13.2.windows.exe (PID: 1288)
- ogjrjir4.exe (PID: 7008)
- UnifiedStub-installer.exe (PID: 7160)
Uses WMIC.EXE to obtain data on processes
- frostwire-6.13.2.windows.exe (PID: 1288)
The process drops C-runtime libraries
- frostwire-6.13.2.windows.exe (PID: 1288)
- UnifiedStub-installer.exe (PID: 7160)
Searches for installed software
- UnifiedStub-installer.exe (PID: 7160)
- rsVPNSvc.exe (PID: 7916)
Executes as Windows Service
- rsSyncSvc.exe (PID: 5464)
- rsClientSvc.exe (PID: 6412)
- rsWSC.exe (PID: 6976)
- rsEngineSvc.exe (PID: 6796)
- rsEDRSvc.exe (PID: 1280)
- WmiApSrv.exe (PID: 2328)
- rsVPNClientSvc.exe (PID: 7804)
- rsVPNSvc.exe (PID: 7916)
- WmiApSrv.exe (PID: 4120)
- rsDNSClientSvc.exe (PID: 7512)
- rsDNSResolver.exe (PID: 2524)
- rsDNSSvc.exe (PID: 1448)
- WmiApSrv.exe (PID: 7872)
Executes application which crashes
- frostwire-6.13.2.windows.tmp (PID: 7052)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 7160)
Potential Corporate Privacy Violation
- FrostWire.exe (PID: 4364)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 7160)
There is functionality for VM detection (VirtualBox)
- FrostWire.exe (PID: 4364)
There is functionality for VM detection (antiVM strings)
- FrostWire.exe (PID: 4364)
Starts CMD.EXE for commands execution
- FrostWire.exe (PID: 4364)
- rsDNSSvc.exe (PID: 1448)
There is functionality for VM detection (VMWare)
- FrostWire.exe (PID: 4364)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 7160)
Checks Windows Trust Settings
- UnifiedStub-installer.exe (PID: 7160)
- rsWSC.exe (PID: 6908)
- rsEngineSvc.exe (PID: 6788)
- rsWSC.exe (PID: 6976)
- rsEDRSvc.exe (PID: 3908)
- rsEDRSvc.exe (PID: 1280)
- rsVPNSvc.exe (PID: 7840)
- rsEngineSvc.exe (PID: 6796)
- rsDNSSvc.exe (PID: 7820)
Adds/modifies Windows certificates
- UnifiedStub-installer.exe (PID: 7160)
- rsWSC.exe (PID: 6908)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 7160)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 7160)
- rundll32.exe (PID: 4576)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 7160)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 7160)
Reads the BIOS version
- rsEDRSvc.exe (PID: 1280)
- rsEngineSvc.exe (PID: 6796)
Dropped object may contain URLs of mainers pools
- rsEngineSvc.exe (PID: 6796)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 1280)
Application launched itself
- rsAppUI.exe (PID: 6712)
- rsAppUI.exe (PID: 8080)
- rsAppUI.exe (PID: 7772)
The process checks if it is being run in the virtual environment
- rsEngineSvc.exe (PID: 6796)
- rsVPNSvc.exe (PID: 7916)
- rsDNSSvc.exe (PID: 1448)
There is functionality for taking screenshot (YARA)
- rsHelper.exe (PID: 5796)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 7492)
- cmd.exe (PID: 8072)
INFO
Create files in a temporary directory
- frostwire-6.13.2.windows.exe (PID: 1076)
- frostwire-6.13.2.windows.exe (PID: 5140)
- frostwire-6.13.2.windows.tmp (PID: 7052)
- frostwire-6.13.2.windows.exe (PID: 1288)
- prod0.exe (PID: 6128)
- FrostWire.exe (PID: 4364)
- ogjrjir4.exe (PID: 7008)
- UnifiedStub-installer.exe (PID: 7160)
- rsAppUI.exe (PID: 6712)
- rsAppUI.exe (PID: 8080)
- rsAppUI.exe (PID: 7772)
Checks supported languages
- frostwire-6.13.2.windows.exe (PID: 1076)
- frostwire-6.13.2.windows.tmp (PID: 2208)
- frostwire-6.13.2.windows.exe (PID: 5140)
- frostwire-6.13.2.windows.tmp (PID: 7052)
- frostwire-6.13.2.windows.exe (PID: 1288)
- prod0.exe (PID: 6128)
- FrostWire.exe (PID: 4364)
- ogjrjir4.exe (PID: 7008)
- UnifiedStub-installer.exe (PID: 7160)
- rsSyncSvc.exe (PID: 5464)
- rsSyncSvc.exe (PID: 7032)
- rsWSC.exe (PID: 6908)
- rsClientSvc.exe (PID: 6272)
- rsClientSvc.exe (PID: 6412)
- rsEngineSvc.exe (PID: 6788)
- rsWSC.exe (PID: 6976)
- rsEngineSvc.exe (PID: 6796)
- rsEDRSvc.exe (PID: 3908)
- rsHelper.exe (PID: 5796)
- rsEDRSvc.exe (PID: 1280)
- EPP.exe (PID: 6464)
- rsAppUI.exe (PID: 6712)
- rsAppUI.exe (PID: 6500)
- rsAppUI.exe (PID: 7332)
- rsLitmus.A.exe (PID: 7312)
- rsAppUI.exe (PID: 3684)
- rsAppUI.exe (PID: 1172)
- rsVPNClientSvc.exe (PID: 7804)
- rsVPNSvc.exe (PID: 7840)
- rsVPNSvc.exe (PID: 7916)
- rsVPNClientSvc.exe (PID: 7752)
- VPN.exe (PID: 8064)
- rsAppUI.exe (PID: 8080)
- rsAppUI.exe (PID: 1700)
- rsAppUI.exe (PID: 7488)
- rsAppUI.exe (PID: 7540)
- rsAppUI.exe (PID: 7680)
- rsDNSClientSvc.exe (PID: 8040)
- rsDNSResolver.exe (PID: 2524)
- rsDNSClientSvc.exe (PID: 7512)
- rsDNSResolver.exe (PID: 7772)
- rsDNSSvc.exe (PID: 7820)
- rsDNSResolver.exe (PID: 3004)
- DNS.exe (PID: 3004)
- rsAppUI.exe (PID: 7772)
- rsDNSSvc.exe (PID: 1448)
- rsAppUI.exe (PID: 7560)
- rsAppUI.exe (PID: 6364)
- rsAppUI.exe (PID: 7884)
- rsAppUI.exe (PID: 4876)
Process checks computer location settings
- frostwire-6.13.2.windows.tmp (PID: 2208)
- frostwire-6.13.2.windows.tmp (PID: 7052)
- prod0.exe (PID: 6128)
- FrostWire.exe (PID: 4364)
- rsAppUI.exe (PID: 1172)
- rsAppUI.exe (PID: 6712)
- rsAppUI.exe (PID: 7332)
- rsVPNSvc.exe (PID: 7916)
- rsAppUI.exe (PID: 1700)
- rsAppUI.exe (PID: 8080)
- rsAppUI.exe (PID: 7680)
- rsAppUI.exe (PID: 6364)
- rsAppUI.exe (PID: 7772)
Reads the computer name
- frostwire-6.13.2.windows.tmp (PID: 2208)
- frostwire-6.13.2.windows.tmp (PID: 7052)
- frostwire-6.13.2.windows.exe (PID: 1288)
- prod0.exe (PID: 6128)
- FrostWire.exe (PID: 4364)
- UnifiedStub-installer.exe (PID: 7160)
- rsSyncSvc.exe (PID: 7032)
- rsSyncSvc.exe (PID: 5464)
- rsWSC.exe (PID: 6908)
- rsClientSvc.exe (PID: 6272)
- rsClientSvc.exe (PID: 6412)
- rsEngineSvc.exe (PID: 6788)
- rsWSC.exe (PID: 6976)
- rsEngineSvc.exe (PID: 6796)
- rsHelper.exe (PID: 5796)
- rsEDRSvc.exe (PID: 3908)
- rsEDRSvc.exe (PID: 1280)
- rsAppUI.exe (PID: 6712)
- rsAppUI.exe (PID: 6500)
- rsAppUI.exe (PID: 3684)
- rsVPNSvc.exe (PID: 7840)
- rsVPNSvc.exe (PID: 7916)
- rsVPNClientSvc.exe (PID: 7752)
- rsVPNClientSvc.exe (PID: 7804)
- rsAppUI.exe (PID: 8080)
- rsAppUI.exe (PID: 7488)
- rsAppUI.exe (PID: 7540)
- rsDNSResolver.exe (PID: 3004)
- rsDNSResolver.exe (PID: 2524)
- rsDNSSvc.exe (PID: 7820)
- rsDNSClientSvc.exe (PID: 8040)
- rsDNSClientSvc.exe (PID: 7512)
- rsDNSSvc.exe (PID: 1448)
- rsAppUI.exe (PID: 7772)
- rsAppUI.exe (PID: 7560)
- rsAppUI.exe (PID: 4876)
- rsAppUI.exe (PID: 7884)
Reads the software policy settings
- frostwire-6.13.2.windows.tmp (PID: 7052)
- prod0.exe (PID: 6128)
- UnifiedStub-installer.exe (PID: 7160)
- WerFault.exe (PID: 5048)
- WerFault.exe (PID: 7140)
- slui.exe (PID: 6992)
- rsWSC.exe (PID: 6908)
- rsEngineSvc.exe (PID: 6788)
- rsEngineSvc.exe (PID: 6796)
- rsWSC.exe (PID: 6976)
- rsEDRSvc.exe (PID: 3908)
- rsEDRSvc.exe (PID: 1280)
- slui.exe (PID: 5244)
- rsVPNSvc.exe (PID: 7840)
- rsVPNSvc.exe (PID: 7916)
- rsDNSSvc.exe (PID: 7820)
- rsDNSSvc.exe (PID: 1448)
Reads the machine GUID from the registry
- frostwire-6.13.2.windows.tmp (PID: 7052)
- prod0.exe (PID: 6128)
- FrostWire.exe (PID: 4364)
- UnifiedStub-installer.exe (PID: 7160)
- rsWSC.exe (PID: 6908)
- rsWSC.exe (PID: 6976)
- rsEngineSvc.exe (PID: 6788)
- rsEDRSvc.exe (PID: 3908)
- rsHelper.exe (PID: 5796)
- rsEngineSvc.exe (PID: 6796)
- rsEDRSvc.exe (PID: 1280)
- rsAppUI.exe (PID: 6712)
- rsVPNSvc.exe (PID: 7916)
- rsVPNSvc.exe (PID: 7840)
- rsAppUI.exe (PID: 8080)
- rsDNSSvc.exe (PID: 7820)
- rsDNSSvc.exe (PID: 1448)
- rsAppUI.exe (PID: 7884)
- rsAppUI.exe (PID: 7772)
Checks proxy server information
- frostwire-6.13.2.windows.tmp (PID: 7052)
- frostwire-6.13.2.windows.exe (PID: 1288)
- prod0.exe (PID: 6128)
- UnifiedStub-installer.exe (PID: 7160)
- WerFault.exe (PID: 5048)
- WerFault.exe (PID: 7140)
- rsWSC.exe (PID: 6908)
- slui.exe (PID: 5244)
- rsAppUI.exe (PID: 6712)
- rsAppUI.exe (PID: 8080)
- rsAppUI.exe (PID: 7772)
Creates files or folders in the user directory
- frostwire-6.13.2.windows.exe (PID: 1288)
- FrostWire.exe (PID: 4364)
- WerFault.exe (PID: 5048)
- WerFault.exe (PID: 7140)
- UnifiedStub-installer.exe (PID: 7160)
- rsWSC.exe (PID: 6908)
- rsEngineSvc.exe (PID: 6796)
- rsAppUI.exe (PID: 6712)
- rsAppUI.exe (PID: 3684)
- rsVPNSvc.exe (PID: 7916)
- rsAppUI.exe (PID: 8080)
- rsAppUI.exe (PID: 7540)
- rsDNSSvc.exe (PID: 1448)
- rsAppUI.exe (PID: 7772)
- rsAppUI.exe (PID: 4876)
- rsAppUI.exe (PID: 7884)
Creates files in the program directory
- frostwire-6.13.2.windows.exe (PID: 1288)
- UnifiedStub-installer.exe (PID: 7160)
- rsWSC.exe (PID: 6908)
- rsEngineSvc.exe (PID: 6788)
- rsEngineSvc.exe (PID: 6796)
- rsEDRSvc.exe (PID: 3908)
- rsEDRSvc.exe (PID: 1280)
- rsVPNSvc.exe (PID: 7840)
- rsVPNSvc.exe (PID: 7916)
- rsDNSResolver.exe (PID: 3004)
- rsDNSResolver.exe (PID: 2524)
- rsDNSSvc.exe (PID: 7820)
- rsDNSSvc.exe (PID: 1448)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6484)
- WMIC.exe (PID: 6744)
- WMIC.exe (PID: 6516)
- runonce.exe (PID: 208)
- runonce.exe (PID: 1288)
Creates a software uninstall entry
- frostwire-6.13.2.windows.exe (PID: 1288)
Disables trace logs
- prod0.exe (PID: 6128)
- UnifiedStub-installer.exe (PID: 7160)
- rsEngineSvc.exe (PID: 6796)
- rsEDRSvc.exe (PID: 1280)
- rsVPNSvc.exe (PID: 7916)
- rsDNSSvc.exe (PID: 1448)
Reads Environment values
- prod0.exe (PID: 6128)
- UnifiedStub-installer.exe (PID: 7160)
- rsEngineSvc.exe (PID: 6796)
- rsEDRSvc.exe (PID: 1280)
- rsAppUI.exe (PID: 6712)
- rsVPNSvc.exe (PID: 7916)
- rsAppUI.exe (PID: 8080)
- rsDNSSvc.exe (PID: 1448)
- rsAppUI.exe (PID: 7772)
Reads CPU info
- FrostWire.exe (PID: 4364)
- rsEDRSvc.exe (PID: 1280)
- rsEngineSvc.exe (PID: 6796)
- rsVPNSvc.exe (PID: 7916)
- rsDNSSvc.exe (PID: 1448)
The process uses the downloaded file
- frostwire-6.13.2.windows.tmp (PID: 7052)
- prod0.exe (PID: 6128)
- UnifiedStub-installer.exe (PID: 7160)
- runonce.exe (PID: 208)
- rsWSC.exe (PID: 6908)
- rsEngineSvc.exe (PID: 6788)
- rsEDRSvc.exe (PID: 3908)
- rsEngineSvc.exe (PID: 6796)
- rsVPNSvc.exe (PID: 7840)
- runonce.exe (PID: 1288)
- rsDNSSvc.exe (PID: 7820)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 7160)
- rsWSC.exe (PID: 6976)
- rsEngineSvc.exe (PID: 6796)
- rsHelper.exe (PID: 5796)
- rsEDRSvc.exe (PID: 1280)
Manual execution by a user
- notepad++.exe (PID: 4980)
Reads the time zone
- runonce.exe (PID: 208)
- rsEngineSvc.exe (PID: 6796)
- rsEDRSvc.exe (PID: 1280)
- rsVPNSvc.exe (PID: 7916)
- runonce.exe (PID: 1288)
- rsDNSSvc.exe (PID: 1448)
Reads product name
- rsEDRSvc.exe (PID: 1280)
- rsEngineSvc.exe (PID: 6796)
- rsAppUI.exe (PID: 6712)
- rsAppUI.exe (PID: 8080)
- rsAppUI.exe (PID: 7772)
Found Base64 encoded text manipulation via PowerShell (YARA)
- rsEngineSvc.exe (PID: 6796)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- rsEngineSvc.exe (PID: 6796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 09:48:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 183296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.13.2.0 |
| ProductVersionNumber: | 6.13.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Frostwire Installer |
| FileVersion: | 6.13.2 |
| LegalCopyright: | © Frostwire |
| OriginalFileName: | |
| ProductName: | Frostwire |
| ProductVersion: | 6.13.2 |
Total processes
237
Monitored processes
94
Malicious processes
14
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rsClientSvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\Users\admin\AppData\Local\Temp\frostwire-6.13.2.windows.exe" | C:\Users\admin\AppData\Local\Temp\frostwire-6.13.2.windows.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Frostwire Installer Exit code: 3221226525 Version: 6.13.2 Modules
| |||||||||||||||
| 1172 | "C:\Program Files\ReasonLabs\Common\Client\v1.4.2\rsAppUI.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\ReasonLabs\EPP" --standard-schemes=mc --secure-schemes=mc --bypasscsp-schemes --cors-schemes --fetch-schemes --service-worker-schemes --streaming-schemes --app-user-model-id=com.reasonlabs.epp --app-path="C:\Program Files\ReasonLabs\Common\Client\v1.4.2\resources\app.asar" --enable-sandbox --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=2316 --field-trial-handle=1780,i,4246807896506585022,5789366815264684985,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Program Files\ReasonLabs\Common\Client\v1.4.2\rsAppUI.exe | — | rsAppUI.exe | |||||||||||
User: admin Company: Reason Cybersecurity Ltd. Integrity Level: LOW Description: ReasonLabs Application Version: 1.4.2 Modules
| |||||||||||||||
| 1280 | "C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe" | C:\Program Files\ReasonLabs\EDR\rsEDRSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Reason Cybersecurity Ltd. Integrity Level: SYSTEM Description: Reason EDR Service Version: 2.2.0 Modules
| |||||||||||||||
| 1288 | "C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\frostwire-6.13.2.windows.exe" /S | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\frostwire-6.13.2.windows.exe | frostwire-6.13.2.windows.tmp | ||||||||||||
User: admin Company: FrostWire LLC Integrity Level: HIGH Description: FrostWire - Search, Download, Play, Share. Exit code: 0 Version: 6.13.1.321 Modules
| |||||||||||||||
| 1288 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | "C:\Program Files\ReasonLabs\DNS\rsDNSSvc.exe" | C:\Program Files\ReasonLabs\DNS\rsDNSSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: rsDNSSvc Version: 3.15.0.0 Modules
| |||||||||||||||
Total events
126 876
Read events
126 258
Write events
419
Delete events
199
Modification events
| (PID) Process: | (7052) frostwire-6.13.2.windows.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 8C1B0000E9DE0F8ADCFADA01 | |||
| (PID) Process: | (7052) frostwire-6.13.2.windows.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 4EB47F2E75EE03CDE99255A611F7A07751A7E65ABF92FA212C9E3D8FE15CFC17 | |||
| (PID) Process: | (7052) frostwire-6.13.2.windows.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1288) frostwire-6.13.2.windows.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1288) frostwire-6.13.2.windows.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1288) frostwire-6.13.2.windows.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1288) frostwire-6.13.2.windows.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1288) frostwire-6.13.2.windows.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1288) frostwire-6.13.2.windows.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1288) frostwire-6.13.2.windows.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
961
Suspicious files
348
Text files
363
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7052 | frostwire-6.13.2.windows.tmp | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\is-CIG83.tmp | — | |
MD5:— | SHA256:— | |||
| 7052 | frostwire-6.13.2.windows.tmp | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\frostwire-6.13.2.windows.exe | — | |
MD5:— | SHA256:— | |||
| 5140 | frostwire-6.13.2.windows.exe | C:\Users\admin\AppData\Local\Temp\is-KOQGJ.tmp\frostwire-6.13.2.windows.tmp | executable | |
MD5:F2715A9E9A8BAE265B65108B9F823C4B | SHA256:98F0A2BBE10EE11749C9EE6E6B8A222E3FAC7121B9113053124C1EF6D39E21D5 | |||
| 7052 | frostwire-6.13.2.windows.tmp | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\zbShieldUtils.dll | executable | |
MD5:B83F5833E96C2EB13F14DCCA805D51A1 | SHA256:00E667B838A4125C8CF847936168BB77BB54580BC05669330CB32C0377C4A401 | |||
| 7052 | frostwire-6.13.2.windows.tmp | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7052 | frostwire-6.13.2.windows.tmp | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\logo.png | image | |
MD5:53DEB7AECF155880604ED15545098FE0 | SHA256:C27F37B57950DADCB4A7744F27F28C9E2353819981FD21CA9F5EDBEB243A6B63 | |||
| 7052 | frostwire-6.13.2.windows.tmp | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\loader.gif | image | |
MD5:F23A523B82AD9103A9AC1DCC33ECA72F | SHA256:59853C413B0813DED6F1E557959768D6662F010F49884D36B62C13038FAC739C | |||
| 7052 | frostwire-6.13.2.windows.tmp | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\RAV_Cross.png | image | |
MD5:CD09F361286D1AD2622BA8A57B7613BD | SHA256:B92A31D4853D1B2C4E5B9D9624F40B439856D0C6A517E100978CBDE8D3C47DC8 | |||
| 7052 | frostwire-6.13.2.windows.tmp | C:\Users\admin\AppData\Local\Temp\is-VC5JL.tmp\is-I90QM.tmp | image | |
MD5:CD09F361286D1AD2622BA8A57B7613BD | SHA256:B92A31D4853D1B2C4E5B9D9624F40B439856D0C6A517E100978CBDE8D3C47DC8 | |||
| 1076 | frostwire-6.13.2.windows.exe | C:\Users\admin\AppData\Local\Temp\is-K28I0.tmp\frostwire-6.13.2.windows.tmp | executable | |
MD5:F2715A9E9A8BAE265B65108B9F823C4B | SHA256:98F0A2BBE10EE11749C9EE6E6B8A222E3FAC7121B9113053124C1EF6D39E21D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
56
TCP/UDP connections
269
DNS requests
65
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1280 | rsEDRSvc.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
1280 | rsEDRSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
1280 | rsEDRSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAEllBL0tvuy4gAAAAAAAQ%3D | unknown | — | — | whitelisted |
1280 | rsEDRSvc.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6368 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1764 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6368 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1288 | frostwire-6.13.2.windows.exe | GET | 404 | 54.172.26.106:80 | http://logs.frostwire.com/ctr/?fwversion=6.13.1.321&id=97486673&state=start&fpc=-1 | unknown | — | — | whitelisted |
1288 | frostwire-6.13.2.windows.exe | GET | 404 | 54.172.26.106:80 | http://logs.frostwire.com/ctr/?fwversion=6.13.1.321&id=97486673&state=update&fpc=-1 | unknown | — | — | whitelisted |
1288 | frostwire-6.13.2.windows.exe | GET | 404 | 54.172.26.106:80 | http://logs.frostwire.com/ctr/?fwversion=6.13.1.321&id=97486673&state=success&fpc=-1 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7072 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6276 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7052 | frostwire-6.13.2.windows.tmp | 52.222.232.188:443 | d35suiogz1ybp7.cloudfront.net | AMAZON-02 | US | whitelisted |
7072 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1764 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1764 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6368 | SIHClient.exe | 40.127.169.103:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
d35suiogz1ybp7.cloudfront.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
shield.reasonsecurity.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1288 | frostwire-6.13.2.windows.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1288 | frostwire-6.13.2.windows.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1288 | frostwire-6.13.2.windows.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
4364 | FrostWire.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
rsEngineSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ReasonLabs\EPP\x64\SQLite.Interop.dll"...
|
rsEDRSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ReasonLabs\EDR\x64\SQLite.Interop.dll"...
|