| File name: | SECOEX NEW ORDER # 032619 - 2019 29 01.doc |
| Full analysis: | https://app.any.run/tasks/53f1eeca-e203-4382-810a-ac824bb0069c |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | January 30, 2019, 06:04:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | 654350C185200BB3211AB252799AA538 |
| SHA1: | 1C4EB2F6DBDD6F70CBF3E49524A7D3317D7D0C58 |
| SHA256: | 886DE6BEA0D3EECB52E03FEB785449BBC0B18AC4D4EE07857AE0109014A52298 |
| SSDEEP: | 12288:7Lxi5OASJhLcV8AGwtEauih3mLso8eZgXtfrUNIC80j3/T6Re3P8o9zxocbUZPZ2:tAmiCD8pXA80j3GW8KzxocbUZPZ2 |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3000)
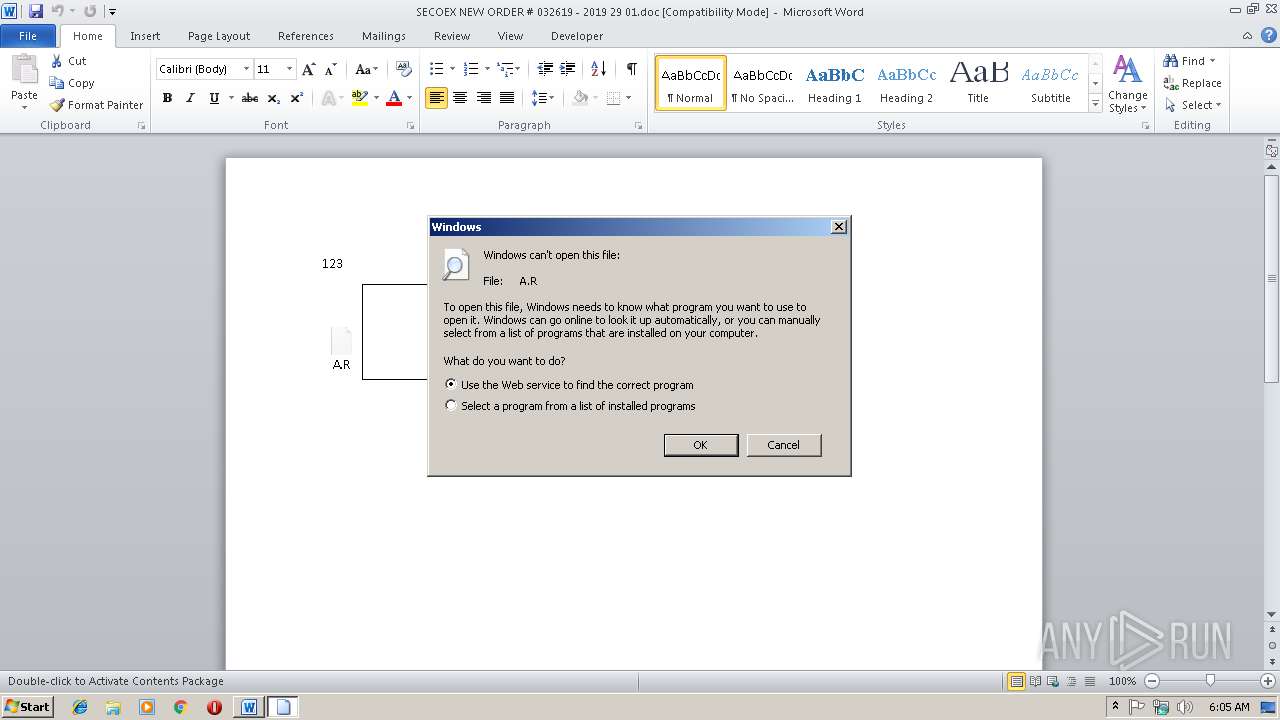
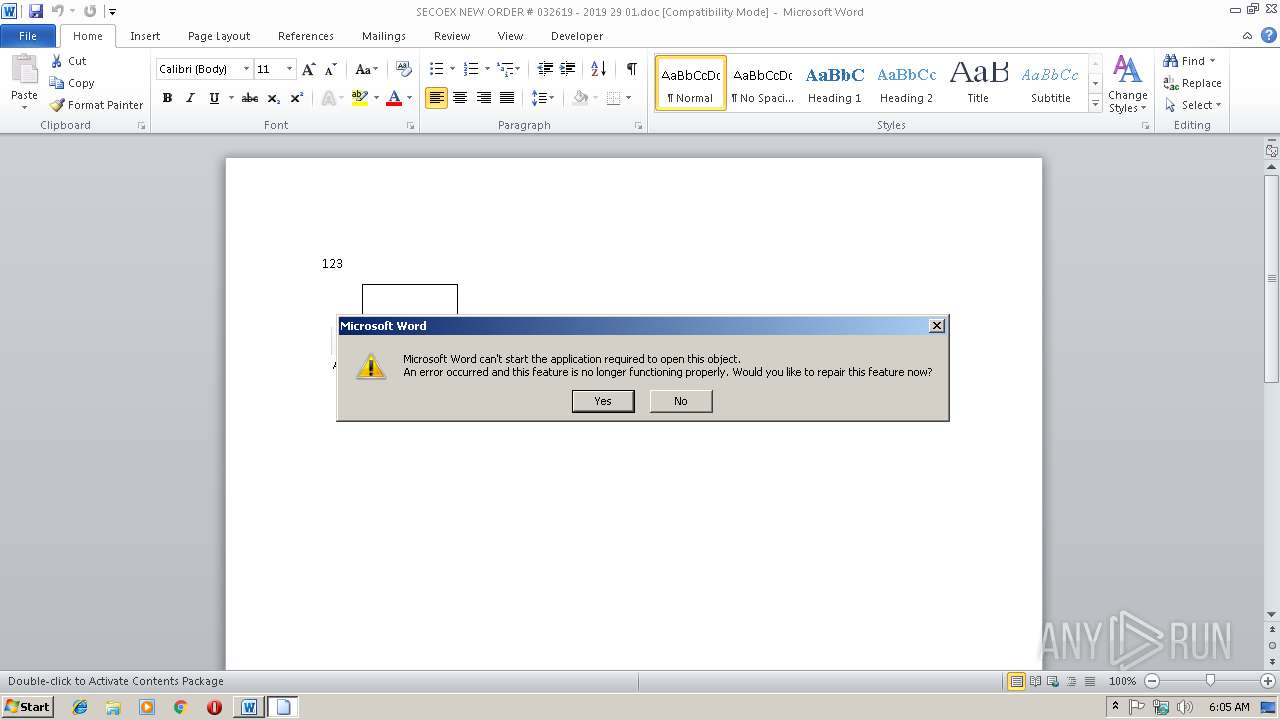
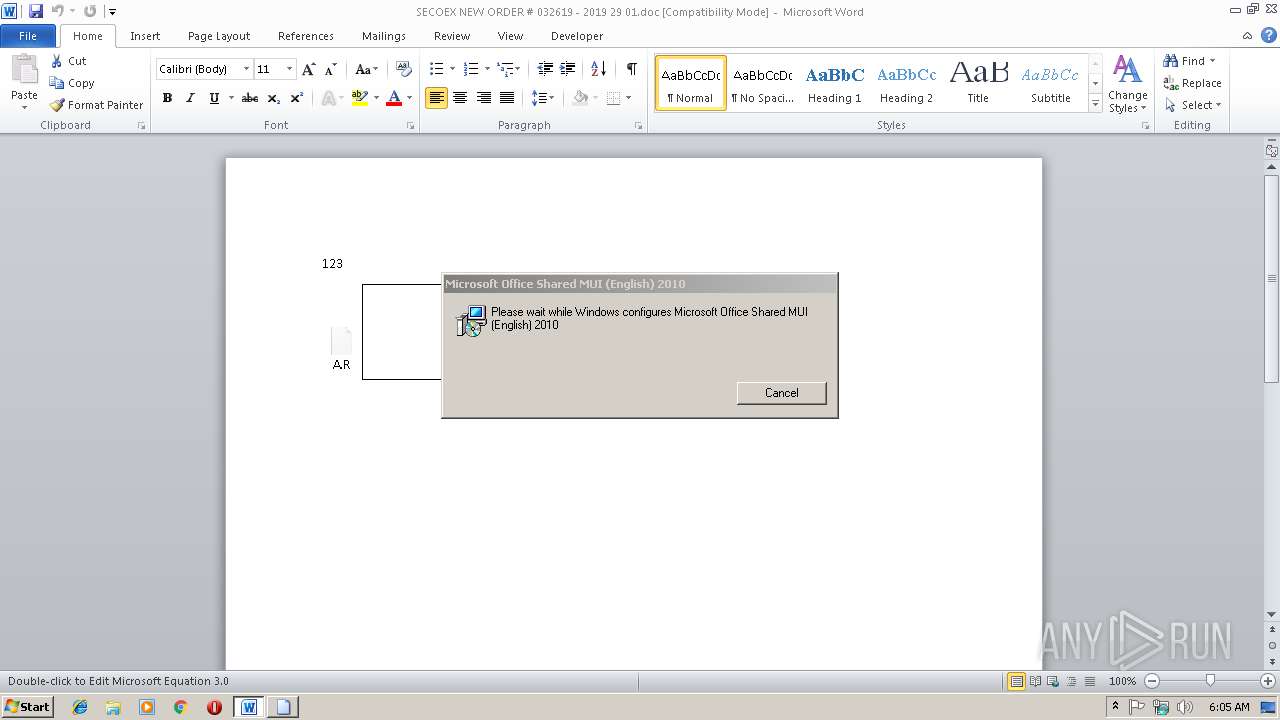
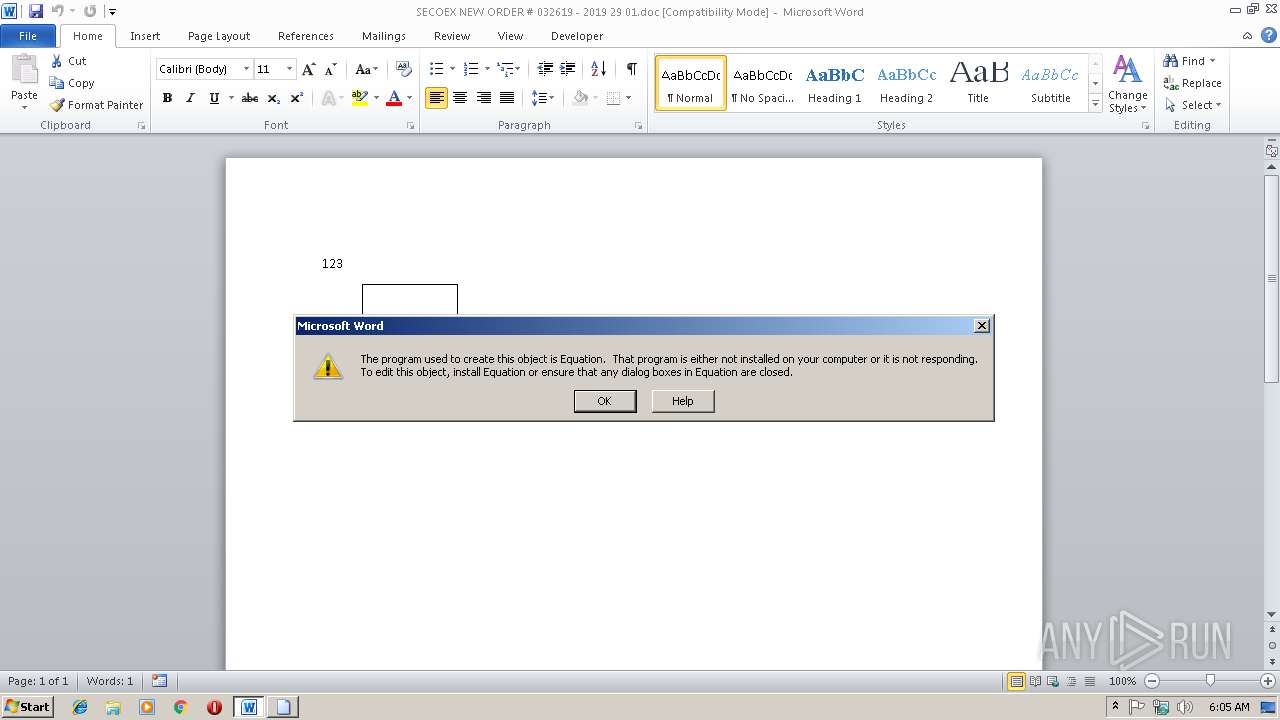
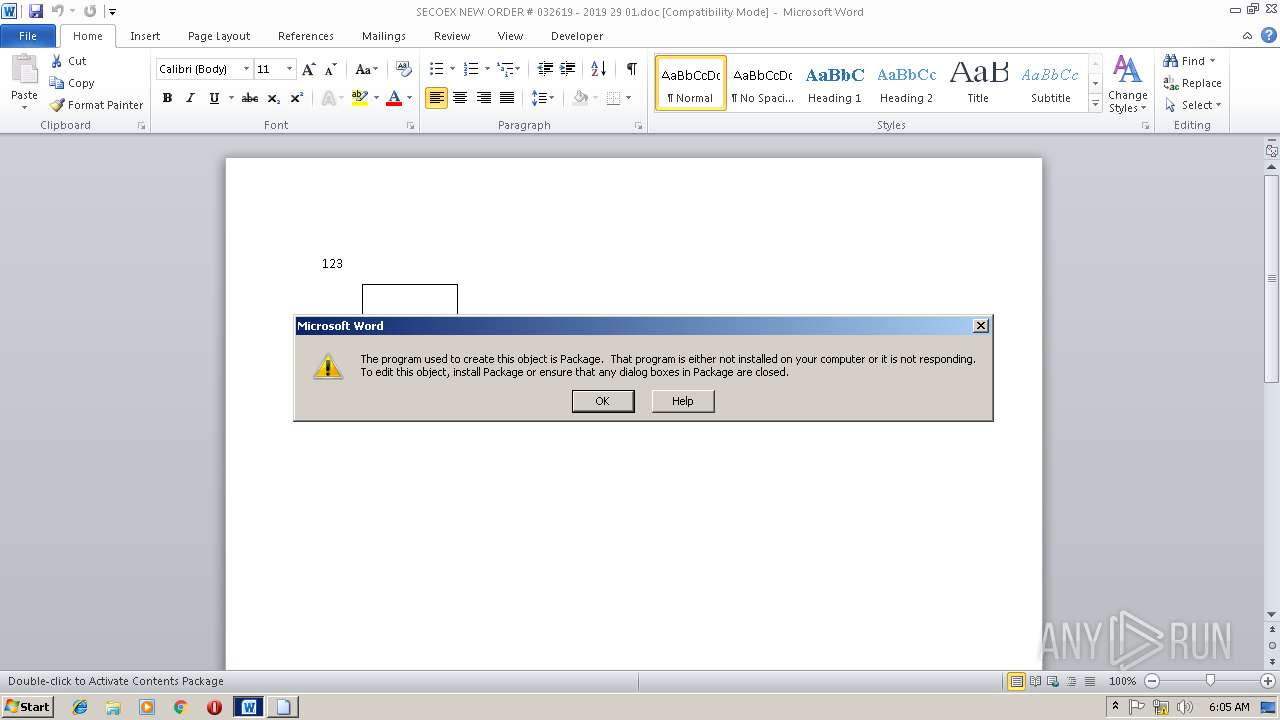
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3944)
- EQNEDT32.EXE (PID: 2608)
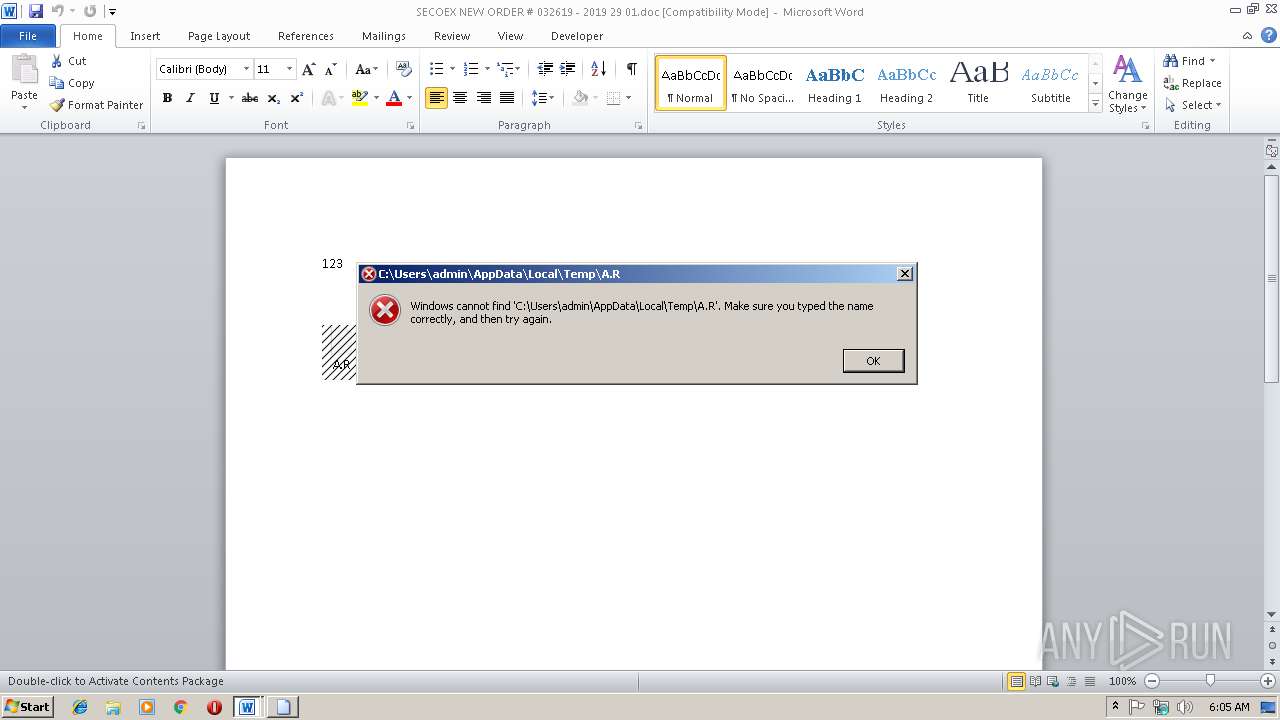
Application was dropped or rewritten from another process
- A.R (PID: 3104)
- A.R (PID: 2328)
- EQNEDT32.EXE (PID: 2608)
- EQNEDT32.EXE (PID: 3944)
- EQNEDT32.EXE (PID: 2736)
- msohtmed.exe (PID: 3400)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3000)
LOKIBOT was detected
- A.R (PID: 3104)
Connects to CnC server
- A.R (PID: 3104)
Loads dropped or rewritten executable
- Setup.exe (PID: 3428)
- WerFault.exe (PID: 3928)
- EQNEDT32.EXE (PID: 3944)
- EQNEDT32.EXE (PID: 2608)
- WINWORD.EXE (PID: 3000)
- WerFault.exe (PID: 2356)
- EQNEDT32.EXE (PID: 2736)
- Setup.exe (PID: 3728)
Actions looks like stealing of personal data
- A.R (PID: 3104)
Detected artifacts of LokiBot
- A.R (PID: 3104)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 2604)
- cmd.exe (PID: 4060)
Starts CMD.EXE for commands execution
- EQNEDT32.EXE (PID: 3944)
- EQNEDT32.EXE (PID: 2608)
Loads DLL from Mozilla Firefox
- A.R (PID: 3104)
Uses RUNDLL32.EXE to load library
- WINWORD.EXE (PID: 3000)
Searches for installed software
- Setup.exe (PID: 3428)
- Setup.exe (PID: 3728)
Executable content was dropped or overwritten
- A.R (PID: 3104)
- Setup.exe (PID: 3428)
- MsiExec.exe (PID: 3412)
- MsiExec.exe (PID: 3408)
- MsiExec.exe (PID: 3360)
- msiexec.exe (PID: 2696)
- Setup.exe (PID: 3728)
- MsiExec.exe (PID: 3656)
- MsiExec.exe (PID: 2804)
- MsiExec.exe (PID: 1144)
- MsiExec.exe (PID: 328)
- MsiExec.exe (PID: 3648)
- MsiExec.exe (PID: 2244)
- MsiExec.exe (PID: 3504)
- MsiExec.exe (PID: 3484)
- MsiExec.exe (PID: 3204)
Creates files in the Windows directory
- msiexec.exe (PID: 2696)
Creates files in the user directory
- A.R (PID: 3104)
Disables SEHOP
- msiexec.exe (PID: 2696)
Starts Microsoft Office Application
- msiexec.exe (PID: 2696)
Removes files from Windows directory
- msiexec.exe (PID: 2696)
Creates COM task schedule object
- msohtmed.exe (PID: 3400)
- msiexec.exe (PID: 2696)
Modifies the open verb of a shell class
- msiexec.exe (PID: 2696)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3000)
- Setup.exe (PID: 3428)
- Setup.exe (PID: 3728)
- MsiExec.exe (PID: 3204)
- msohtmed.exe (PID: 3400)
Creates files in the user directory
- WINWORD.EXE (PID: 3000)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 3000)
- A.R (PID: 3104)
- msiexec.exe (PID: 2696)
Application was crashed
- EQNEDT32.EXE (PID: 3944)
- EQNEDT32.EXE (PID: 2608)
Application launched itself
- msiexec.exe (PID: 2696)
Creates files in the program directory
- MsiExec.exe (PID: 1868)
- msiexec.exe (PID: 2696)
- MsiExec.exe (PID: 3584)
- MsiExec.exe (PID: 3184)
- MsiExec.exe (PID: 1940)
- MsiExec.exe (PID: 3808)
- MsiExec.exe (PID: 3300)
- MsiExec.exe (PID: 2636)
- MsiExec.exe (PID: 3272)
- MsiExec.exe (PID: 3608)
- MsiExec.exe (PID: 3108)
- MsiExec.exe (PID: 3240)
- MsiExec.exe (PID: 2172)
Loads dropped or rewritten executable
- msiexec.exe (PID: 2696)
- MsiExec.exe (PID: 1868)
- MsiExec.exe (PID: 1892)
- MsiExec.exe (PID: 3412)
- MsiExec.exe (PID: 3408)
- MsiExec.exe (PID: 3584)
- MsiExec.exe (PID: 3360)
- MsiExec.exe (PID: 3184)
- MsiExec.exe (PID: 2804)
- MsiExec.exe (PID: 640)
- MsiExec.exe (PID: 3656)
- MsiExec.exe (PID: 1940)
- MsiExec.exe (PID: 3808)
- MsiExec.exe (PID: 1144)
- MsiExec.exe (PID: 348)
- MsiExec.exe (PID: 2636)
- MsiExec.exe (PID: 3648)
- MsiExec.exe (PID: 3696)
- MsiExec.exe (PID: 3052)
- MsiExec.exe (PID: 1736)
- MsiExec.exe (PID: 2244)
- MsiExec.exe (PID: 3272)
- MsiExec.exe (PID: 3608)
- MsiExec.exe (PID: 3484)
- MsiExec.exe (PID: 584)
- MsiExec.exe (PID: 3300)
- MsiExec.exe (PID: 328)
- MsiExec.exe (PID: 3504)
- MsiExec.exe (PID: 3108)
- MsiExec.exe (PID: 3204)
- MsiExec.exe (PID: 3240)
- MsiExec.exe (PID: 2172)
- MSIE64D.tmp (PID: 4072)
Writes to a desktop.ini file (may be used to cloak folders)
- msiexec.exe (PID: 2696)
Creates a software uninstall entry
- msiexec.exe (PID: 2696)
Starts application with an unusual extension
- msiexec.exe (PID: 2696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
EXIF
RTF
| Author: | wuyan |
|---|---|
| LastModifiedBy: | wuyan |
| CreateDate: | 2019:01:03 16:14:00 |
| ModifyDate: | 2019:01:03 16:34:00 |
| RevisionNumber: | 3 |
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | 4 |
| Characters: | 24 |
| CharactersWithSpaces: | 27 |
| InternalVersionNumber: | 57435 |
Total processes
87
Monitored processes
49
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | C:\Windows\system32\MsiExec.exe -Embedding 9A817A5273F43153503F85ECD2A99546 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 348 | C:\Windows\system32\MsiExec.exe -Embedding F7CE8DE19A3FC1C016D09C9AE494FA7A | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | C:\Windows\system32\MsiExec.exe -Embedding 24E8119070EBD6F94C12F2709F33546D | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 640 | C:\Windows\system32\MsiExec.exe -Embedding A1CD76748791CEA376CFAF81DAA2589C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1144 | C:\Windows\system32\MsiExec.exe -Embedding ACBC7F869D030ADC276085C491D99667 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1736 | C:\Windows\system32\MsiExec.exe -Embedding 613094E5BA553848840C89CCCA574114 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1868 | C:\Windows\system32\MsiExec.exe -Embedding 81C015DC76C951533385E95EA0F118BB M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | C:\Windows\system32\MsiExec.exe -Embedding F1D7D4D0B75295F817CE86705CA5242F | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1940 | C:\Windows\system32\MsiExec.exe -Embedding F7BB81ADFD27485E2056F5513C4DAFBD M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2172 | C:\Windows\system32\MsiExec.exe -Embedding EE632CFE737515385E1401EC443F1285 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
29 427
Read events
17 292
Write events
11 259
Delete events
876
Modification events
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | x(, |
Value: 78282C00B80B0000010000000000000000000000 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1312686103 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312686224 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312686225 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: B80B0000A49451B761B8D40100000000 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | q), |
Value: 71292C00B80B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | q), |
Value: 71292C00B80B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
472
Suspicious files
52
Text files
74
Unknown types
153
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVREC58.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3928 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERF737.tmp.hdmp | — | |
MD5:— | SHA256:— | |||
| 3928 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERF7B5.tmp.mdmp | — | |
MD5:— | SHA256:— | |||
| 2356 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER1F4F.tmp.appcompat.txt | — | |
MD5:— | SHA256:— | |||
| 3104 | A.R | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.lck | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$COEX NEW ORDER # 032619 - 2019 29 01.doc | pgc | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3928 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\EQNEDT32.EXE.3944.dmp | dmp | |
MD5:— | SHA256:— | |||
| 2696 | msiexec.exe | C:\Windows\Installer\MSI4286.tmp | — | |
MD5:— | SHA256:— | |||
| 2696 | msiexec.exe | C:\Windows\Installer\MSI4304.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
1
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3104 | A.R | POST | — | 104.27.185.190:80 | http://mayorhost.icu/fre.php | US | — | — | malicious |
3104 | A.R | POST | — | 104.27.185.190:80 | http://mayorhost.icu/fre.php | US | — | — | malicious |
3104 | A.R | POST | — | 104.27.185.190:80 | http://mayorhost.icu/fre.php | US | — | — | malicious |
3104 | A.R | POST | — | 104.27.185.190:80 | http://mayorhost.icu/fre.php | US | — | — | malicious |
3104 | A.R | POST | — | 104.27.185.190:80 | http://mayorhost.icu/fre.php | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3104 | A.R | 104.27.185.190:80 | mayorhost.icu | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mayorhost.icu |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3104 | A.R | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3104 | A.R | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3104 | A.R | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3104 | A.R | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3104 | A.R | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
3104 | A.R | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3104 | A.R | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3104 | A.R | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3104 | A.R | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3104 | A.R | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
5 ETPRO signatures available at the full report
Process | Message |
|---|---|
msiexec.exe | Failed to release Service
|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
addinutil.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
addinutil.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|