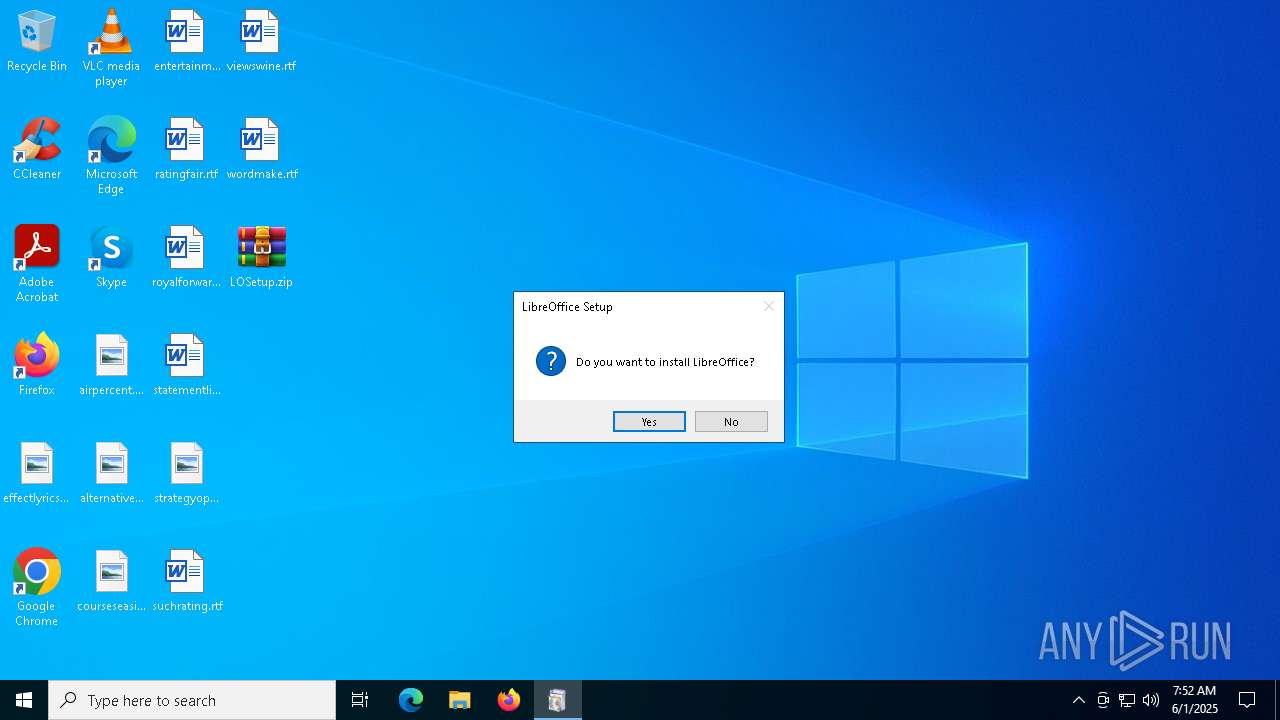
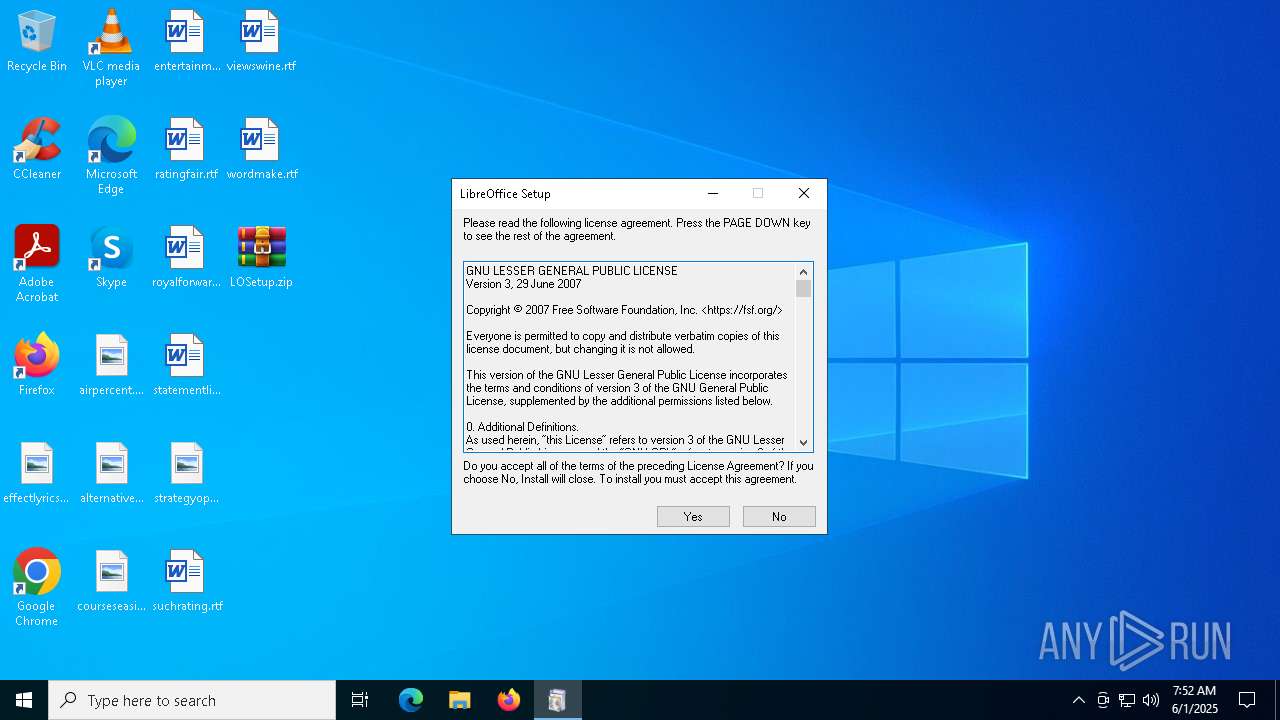
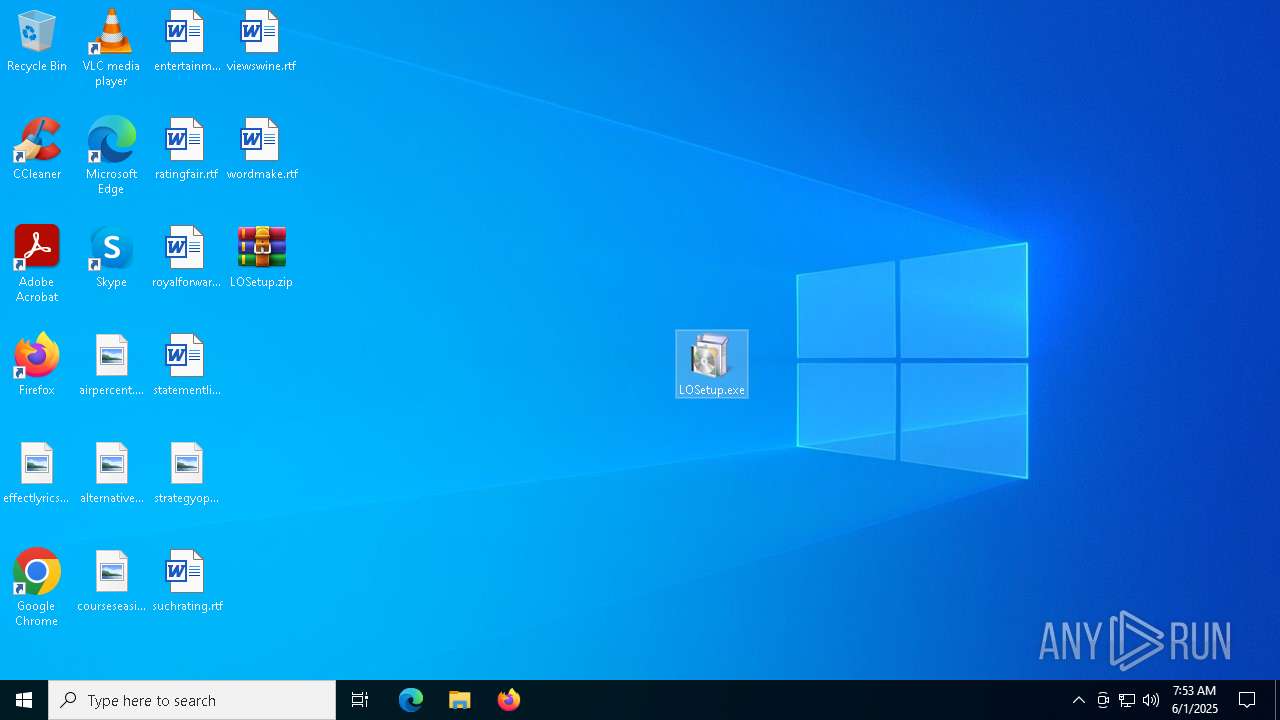
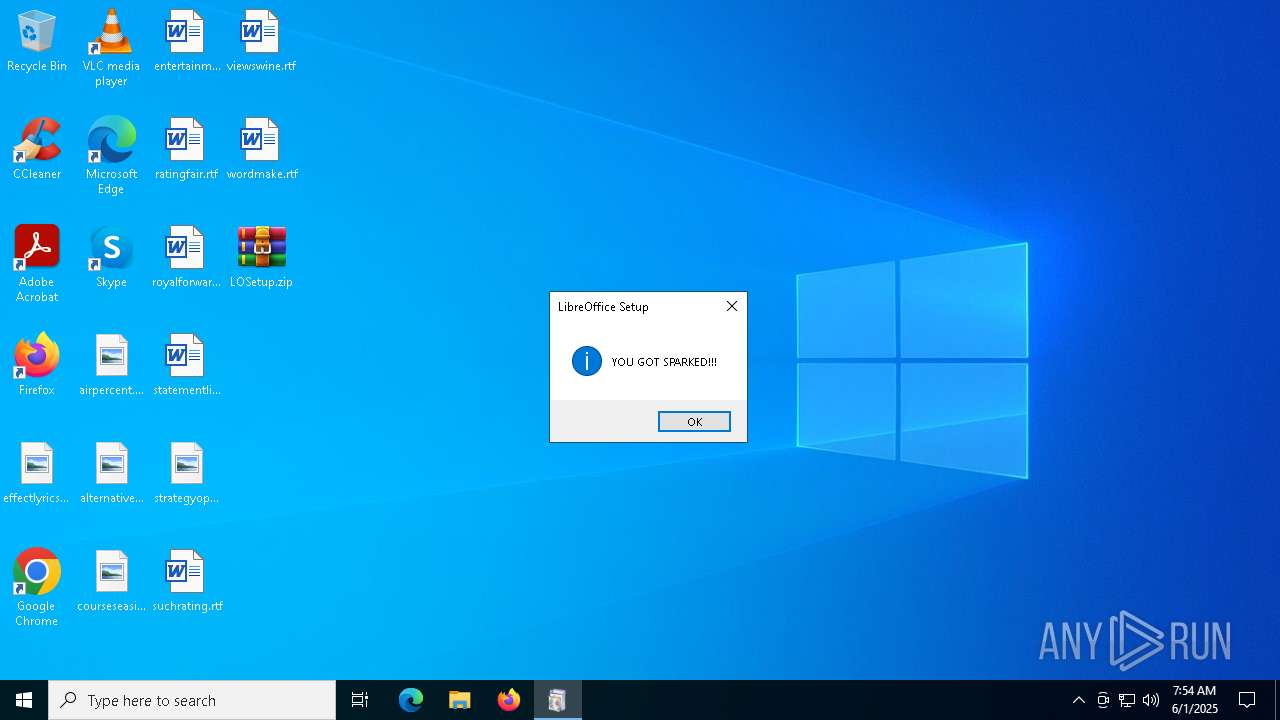
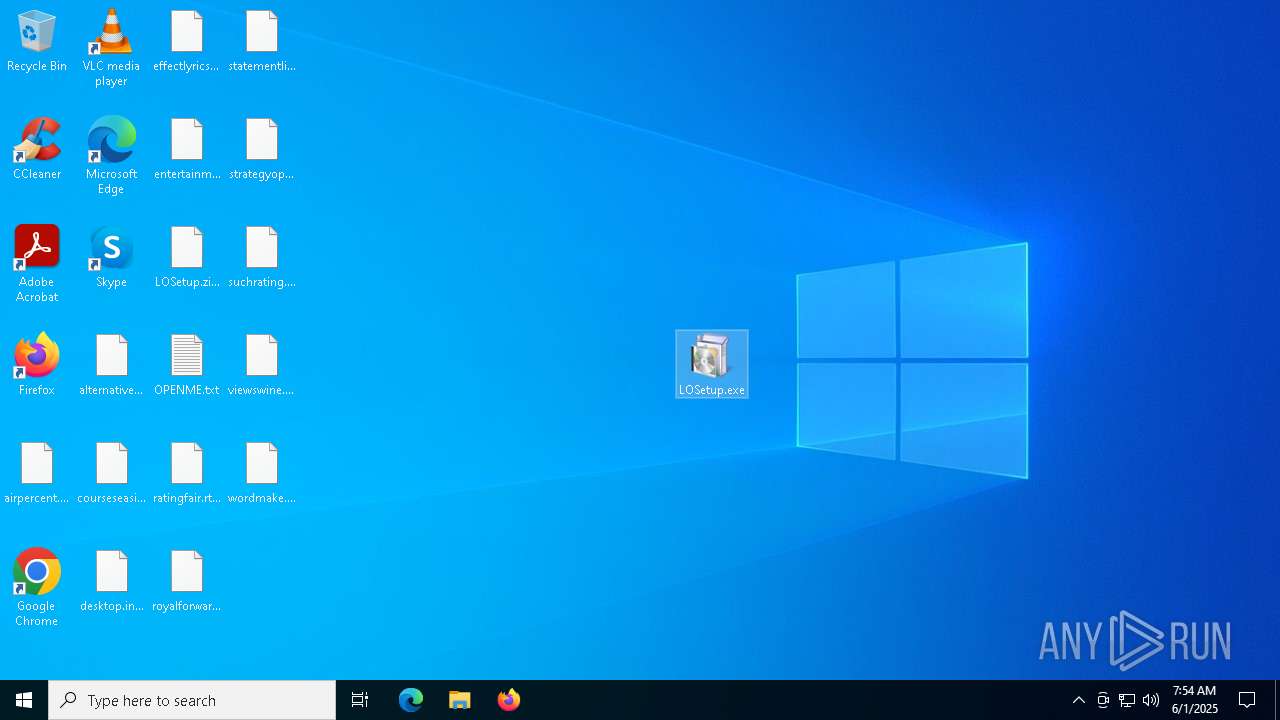
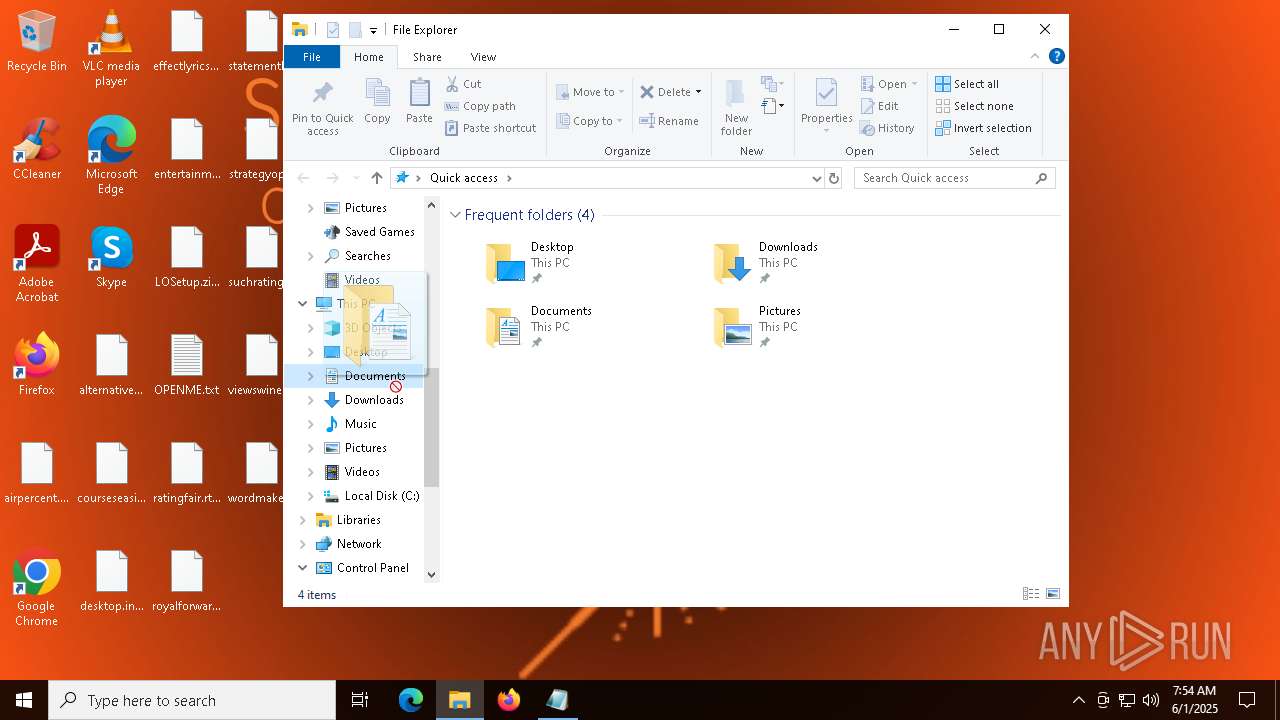
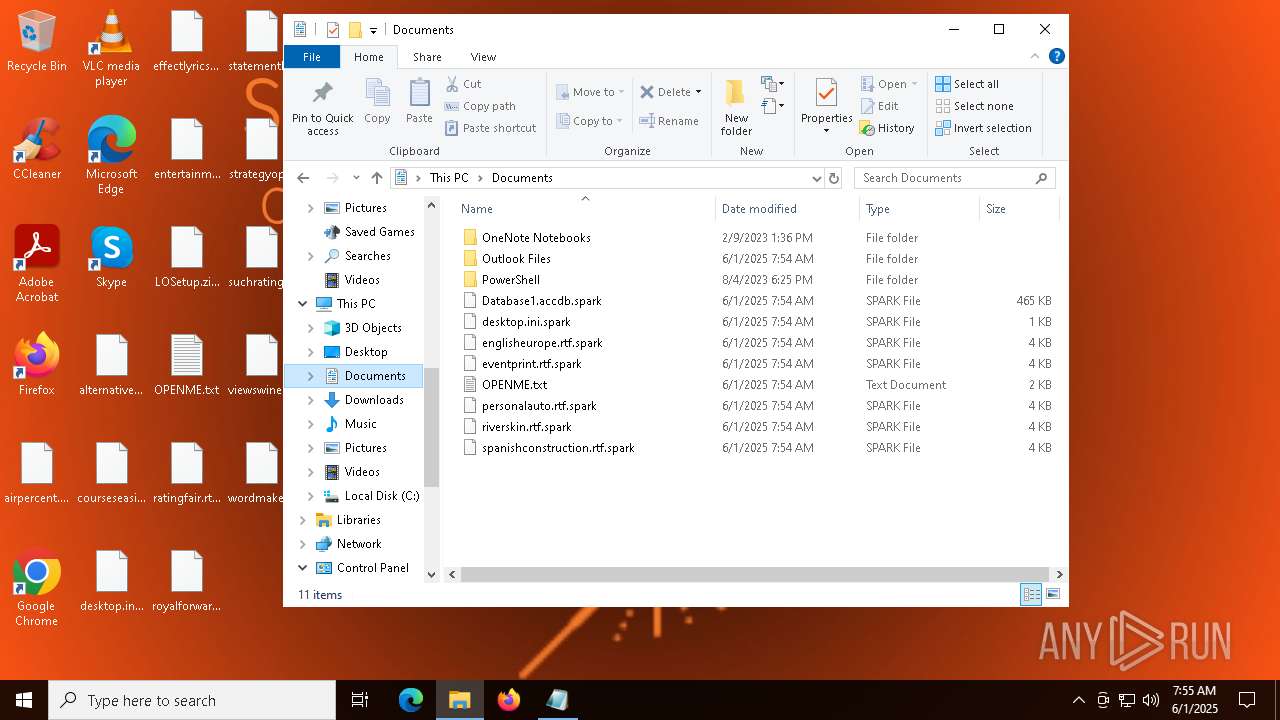
| File name: | LOSetup.zip |
| Full analysis: | https://app.any.run/tasks/8da9fb05-2288-475a-9e2a-bec1b8ff2cd4 |
| Verdict: | Malicious activity |
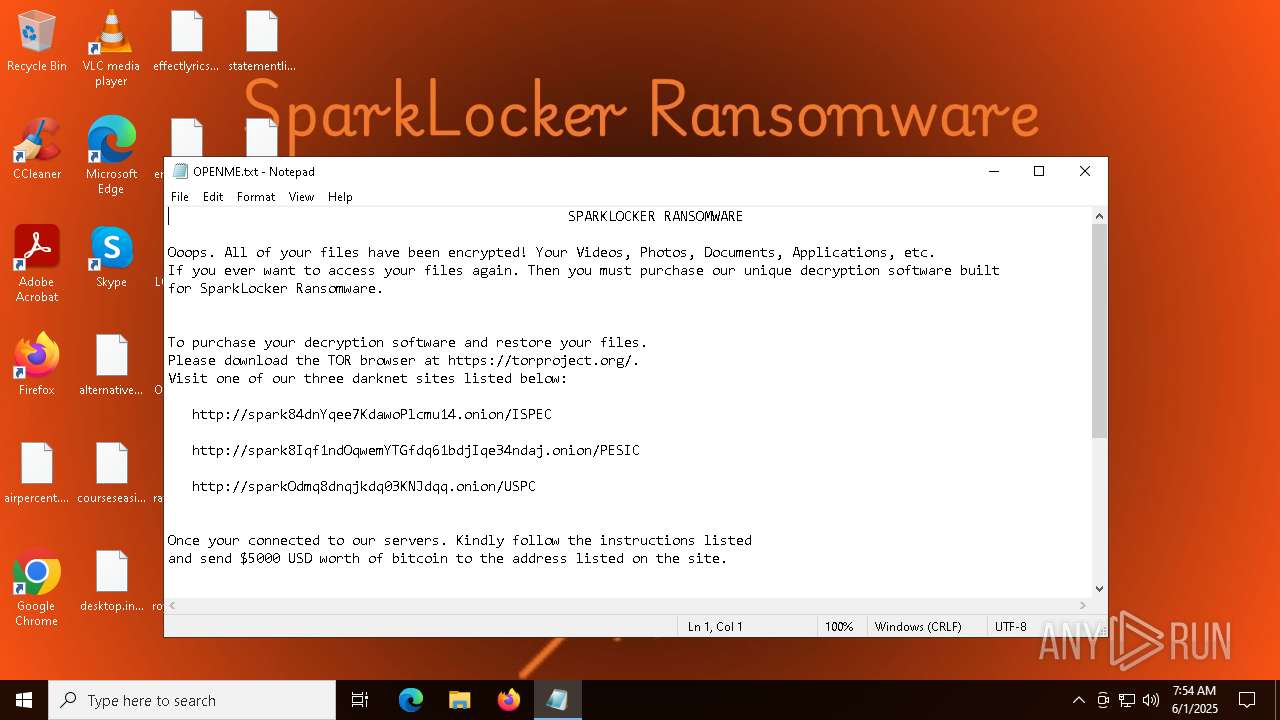
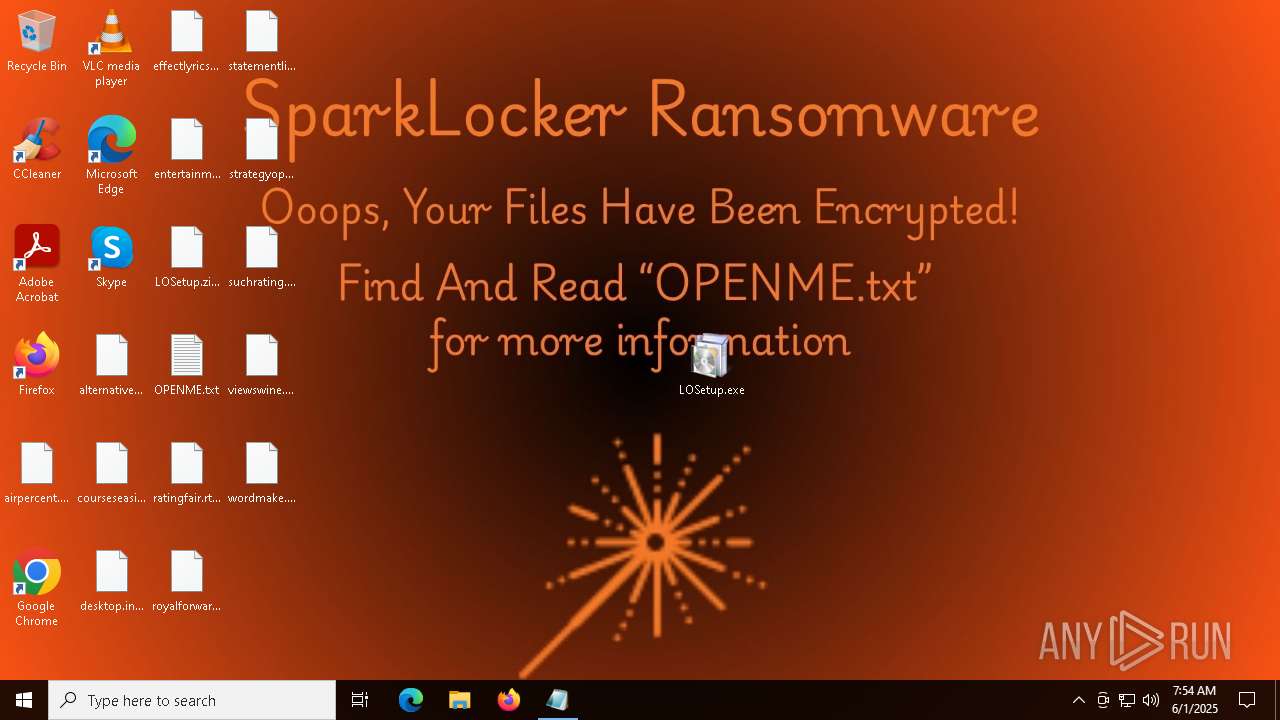
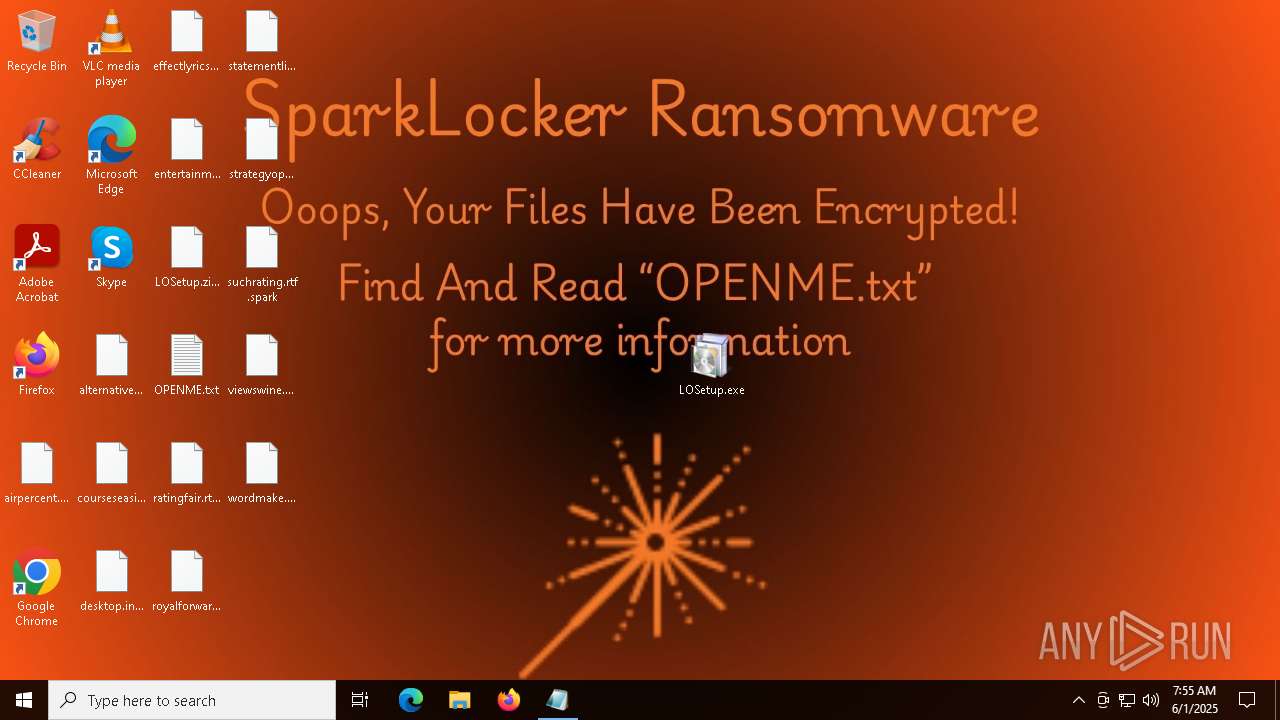
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | June 01, 2025, 07:52:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FE3293895736FB7221E329777FC56042 |
| SHA1: | 044D178341B597DCC533F90631A8A4A8890E3C04 |
| SHA256: | 88546439312F037D367F55A0BAFB50DB9B2ACB69BCF11EAEAF50D9E153A81F1C |
| SSDEEP: | 12288:m/Y+B4FT25qt7XpdfWVwKwrUtX/K3+quwufS1:mAHFTKq1XpdfWjwIVKOfwufs |
MALICIOUS
CHAOS has been detected (YARA)
- audiodg.exe (PID: 7968)
- userinit.exe (PID: 8092)
Create files in the Startup directory
- userinit.exe (PID: 8092)
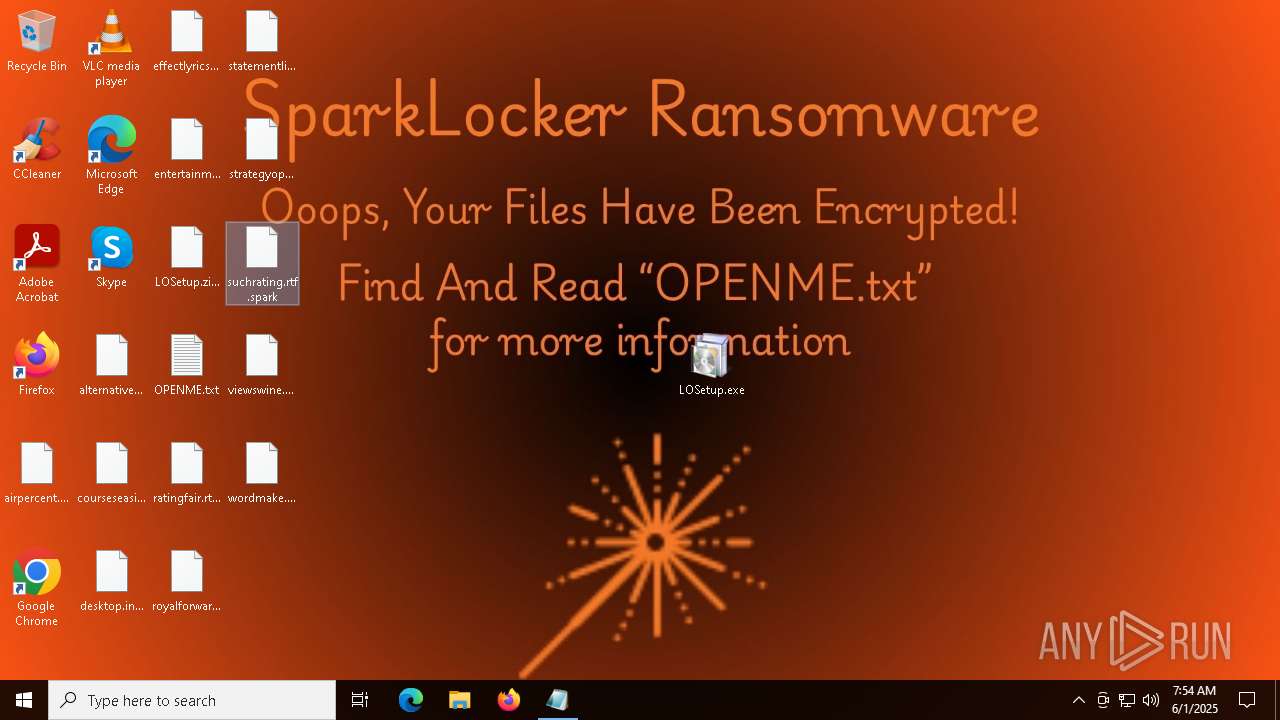
Renames files like ransomware
- userinit.exe (PID: 8092)
SPARK has been detected
- userinit.exe (PID: 8092)
RANSOMWARE has been detected
- userinit.exe (PID: 8092)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 5324)
Starts a Microsoft application from unusual location
- LOSetup.exe (PID: 6660)
Executable content was dropped or overwritten
- LOSetup.exe (PID: 6660)
- audiodg.exe (PID: 7968)
Starts itself from another location
- audiodg.exe (PID: 7968)
Write to the desktop.ini file (may be used to cloak folders)
- userinit.exe (PID: 8092)
Found regular expressions for crypto-addresses (YARA)
- audiodg.exe (PID: 7968)
- userinit.exe (PID: 8092)
Reads the date of Windows installation
- audiodg.exe (PID: 7968)
- userinit.exe (PID: 8092)
Reads security settings of Internet Explorer
- audiodg.exe (PID: 7968)
- userinit.exe (PID: 8092)
Start notepad (likely ransomware note)
- userinit.exe (PID: 8092)
INFO
Manual execution by a user
- LOSetup.exe (PID: 6660)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5324)
The sample compiled with english language support
- WinRAR.exe (PID: 5324)
Checks supported languages
- LOSetup.exe (PID: 6660)
- audiodg.exe (PID: 7968)
- userinit.exe (PID: 8092)
Reads the computer name
- LOSetup.exe (PID: 6660)
- audiodg.exe (PID: 7968)
- userinit.exe (PID: 8092)
Create files in a temporary directory
- LOSetup.exe (PID: 6660)
- userinit.exe (PID: 8092)
Reads the software policy settings
- slui.exe (PID: 6028)
- slui.exe (PID: 5008)
Launch of the file from Startup directory
- userinit.exe (PID: 8092)
Reads the machine GUID from the registry
- userinit.exe (PID: 8092)
Checks proxy server information
- slui.exe (PID: 5008)
Creates files or folders in the user directory
- userinit.exe (PID: 8092)
- audiodg.exe (PID: 7968)
Process checks computer location settings
- audiodg.exe (PID: 7968)
- userinit.exe (PID: 8092)
Reads Microsoft Office registry keys
- userinit.exe (PID: 8092)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:01 00:49:28 |
| ZipCRC: | 0xb1df1e94 |
| ZipCompressedSize: | 286536 |
| ZipUncompressedSize: | 342016 |
| ZipFileName: | LOSetup.exe |
Total processes
135
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2332 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5324 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\LOSetup.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6028 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6660 | "C:\Users\admin\Desktop\LOSetup.exe" | C:\Users\admin\Desktop\LOSetup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.10240.16384 (th1.150709-1700) Modules
| |||||||||||||||
| 7728 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7800 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\OPENME.txt | C:\Windows\System32\notepad.exe | — | userinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7968 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\audiodg.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\audiodg.exe | LOSetup.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 1 Version: 0.0.0.0 Modules
| |||||||||||||||
| 8092 | "C:\Users\admin\AppData\Roaming\userinit.exe" | C:\Users\admin\AppData\Roaming\userinit.exe | audiodg.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
7 631
Read events
7 610
Write events
21
Delete events
0
Modification events
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\LOSetup.zip | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
1
Text files
542
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5324.16807\LOSetup.exe | executable | |
MD5:933038787587E4FE2D0848C73AEB9C64 | SHA256:234D8F5C19B85043EBF78E73777BFDD850DCC4C2DF3513A00C2784129ACC6AC9 | |||
| 6660 | LOSetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\audiodg.exe | executable | |
MD5:DD14E7E88F194BEC0A6B0539CB823EA3 | SHA256:AAD32ECDB090DA1B8D2F721158C9D24BD9F968067087ADFD4FB355E7733F1C0E | |||
| 8092 | userinit.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\userinit.url | binary | |
MD5:8E7E072EE14A94F290D9E69C2E0A8D2B | SHA256:3BB380DB03DA1ED7C225BAF4339685761DA6AC73151B8991986F9BBBB5ABEE83 | |||
| 7968 | audiodg.exe | C:\Users\admin\AppData\Roaming\userinit.exe | executable | |
MD5:DD14E7E88F194BEC0A6B0539CB823EA3 | SHA256:AAD32ECDB090DA1B8D2F721158C9D24BD9F968067087ADFD4FB355E7733F1C0E | |||
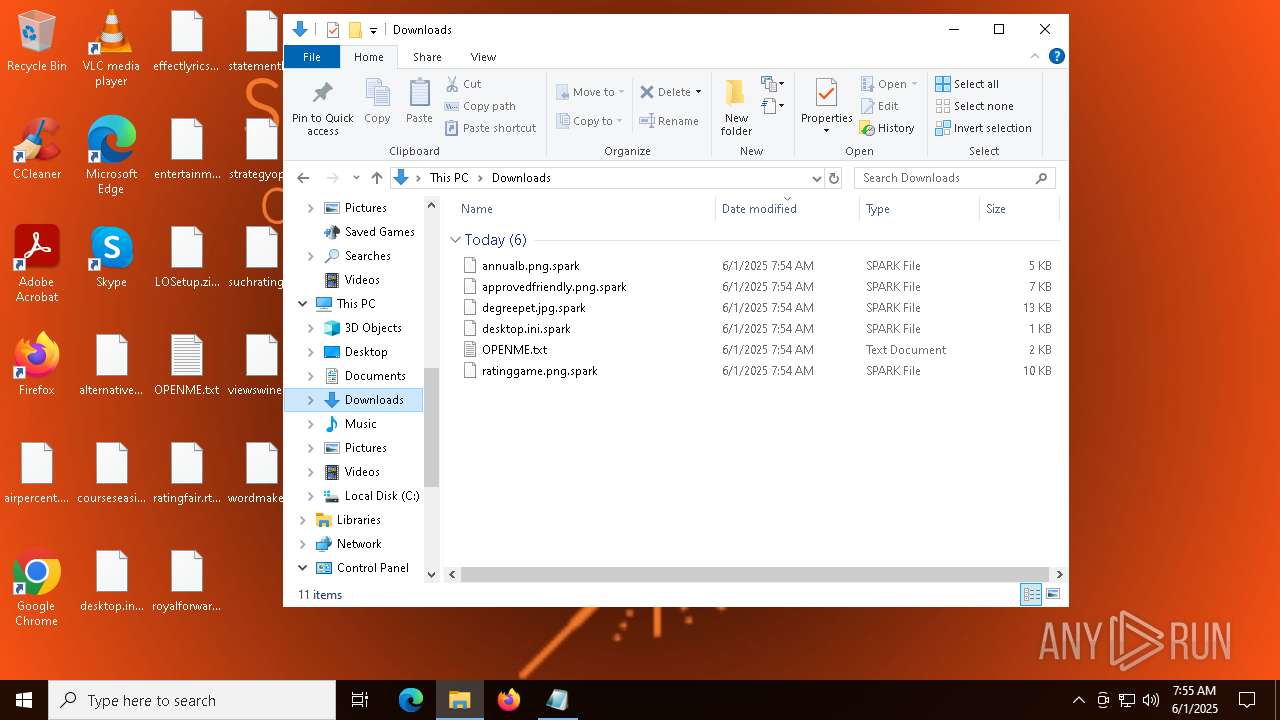
| 8092 | userinit.exe | C:\Users\admin\Desktop\OPENME.txt | text | |
MD5:EDD089842C1888A2419D9D9A7B1E22AB | SHA256:9B9C08ADF31FEC714B4A2F0A2F2FB1AC2E2AF954713BE44D41DB6B98540F551F | |||
| 8092 | userinit.exe | C:\Users\admin\Desktop\airpercent.png.spark | text | |
MD5:AB52238C37285B023E1A16E0A9E49C65 | SHA256:D013615725AD400CA936FF8C972843312436DADE5DDC7DC702E683AB6E29477B | |||
| 8092 | userinit.exe | C:\Users\admin\Desktop\courseseasily.jpg.spark | text | |
MD5:6BC46912DED8A69C0910BEA761FA3665 | SHA256:684E9ED3ABC035C53D3F0E9E3550952D4EB24DD37298FB0C19BE4C207D8048DF | |||
| 8092 | userinit.exe | C:\Users\admin\Desktop\airpercent.png | text | |
MD5:AB52238C37285B023E1A16E0A9E49C65 | SHA256:D013615725AD400CA936FF8C972843312436DADE5DDC7DC702E683AB6E29477B | |||
| 8092 | userinit.exe | C:\Users\admin\Desktop\courseseasily.jpg | text | |
MD5:6BC46912DED8A69C0910BEA761FA3665 | SHA256:684E9ED3ABC035C53D3F0E9E3550952D4EB24DD37298FB0C19BE4C207D8048DF | |||
| 8092 | userinit.exe | C:\Users\admin\Desktop\alternativemode.png.spark | text | |
MD5:9696618EF59372BBD247955306F0C75C | SHA256:A4AC420A5B9AE890C6EA97DA27261FDF97C07EB91AEB0761A093092BBC42C5F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
31
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6456 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6456 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.63.118.230:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7552 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |