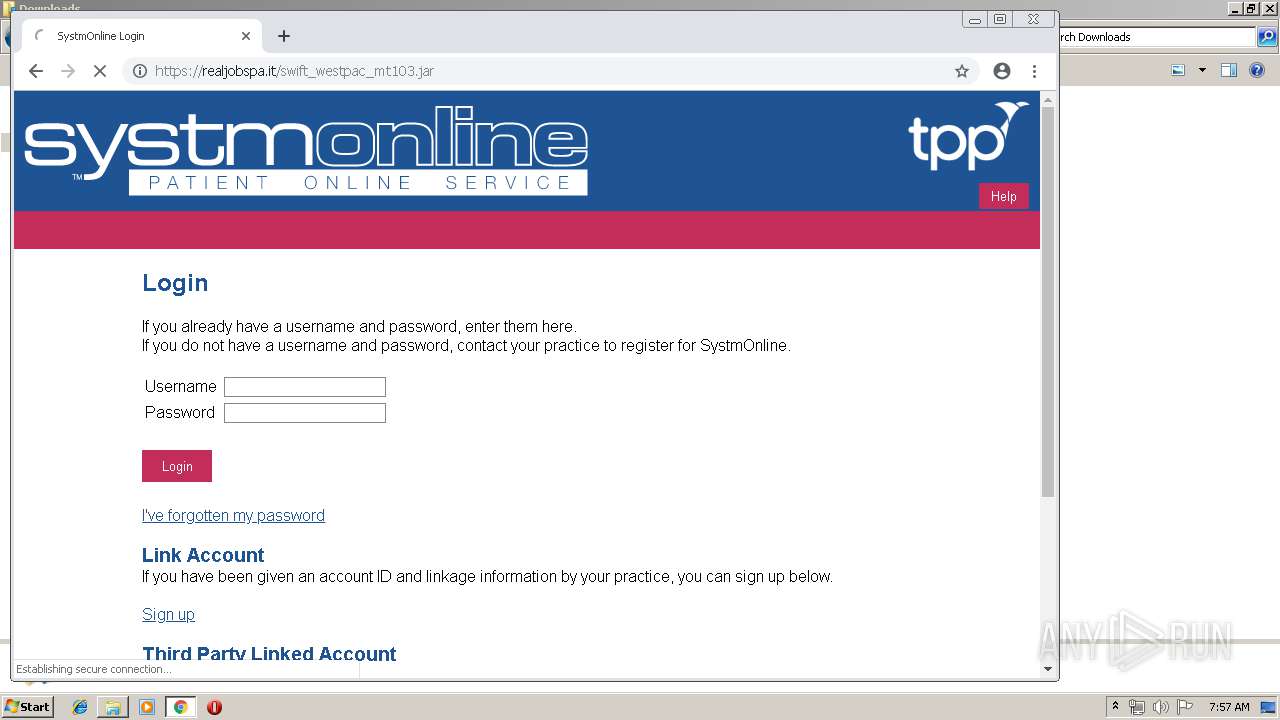
| download: | swift_westpac_mt103.jar |
| Full analysis: | https://app.any.run/tasks/7785bf1b-cc68-4537-9eef-9db9f7ad4ce6 |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | June 12, 2019, 06:55:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F94C82724B20D610DCC1C6589BB66775 |
| SHA1: | 5B54EA3F6AD8E51B28DA469C5EFB05768AB7A7E9 |
| SHA256: | 880B30F533370F8136B180AAE2305D25590502B44D924494F7880C51D9FD5E62 |
| SSDEEP: | 12288:1s68nKwjmOWA/OaMsB/LVNdK2VhZTX30iN/CYBdPPW3+4XZNFgt6JgkE4aE:TO3/td8gX3jNfBlPWFJNzKkZaE |
MALICIOUS
Changes the autorun value in the registry
- wscript.exe (PID: 3640)
- WScript.exe (PID: 1024)
- reg.exe (PID: 2888)
Writes to a start menu file
- WScript.exe (PID: 1024)
AdWind was detected
- java.exe (PID: 1712)
- java.exe (PID: 2720)
Loads dropped or rewritten executable
- svchost.exe (PID: 812)
- javaw.exe (PID: 2748)
- java.exe (PID: 1712)
- javaw.exe (PID: 3152)
- explorer.exe (PID: 116)
- cmd.exe (PID: 2500)
- javaw.exe (PID: 1912)
- wscript.exe (PID: 3640)
- javaw.exe (PID: 584)
- java.exe (PID: 2720)
Application was dropped or rewritten from another process
- java.exe (PID: 1712)
- javaw.exe (PID: 3152)
- javaw.exe (PID: 1912)
- javaw.exe (PID: 2748)
- javaw.exe (PID: 584)
- java.exe (PID: 2720)
ADWIND was detected
- javaw.exe (PID: 584)
Runs app for hidden code execution
- javaw.exe (PID: 584)
Stealing of credential data
- javaw.exe (PID: 584)
Actions looks like stealing of personal data
- javaw.exe (PID: 584)
SUSPICIOUS
Executes JAVA applets
- explorer.exe (PID: 116)
- cmd.exe (PID: 2500)
- wscript.exe (PID: 3640)
- javaw.exe (PID: 2748)
Executes scripts
- wscript.exe (PID: 3640)
- javaw.exe (PID: 3152)
- cmd.exe (PID: 1252)
- cmd.exe (PID: 1920)
- cmd.exe (PID: 3360)
- cmd.exe (PID: 3252)
- cmd.exe (PID: 1240)
- cmd.exe (PID: 2872)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 3716)
Application launched itself
- wscript.exe (PID: 3640)
Creates files in the user directory
- wscript.exe (PID: 3640)
- WScript.exe (PID: 1024)
- javaw.exe (PID: 2748)
- xcopy.exe (PID: 3244)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3640)
- javaw.exe (PID: 2748)
- java.exe (PID: 1712)
- javaw.exe (PID: 584)
- java.exe (PID: 2720)
Executable content was dropped or overwritten
- xcopy.exe (PID: 3244)
- javaw.exe (PID: 584)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 2748)
- cmd.exe (PID: 4056)
- cmd.exe (PID: 1332)
- cmd.exe (PID: 828)
- cmd.exe (PID: 1396)
- cmd.exe (PID: 4028)
- cmd.exe (PID: 560)
- cmd.exe (PID: 3128)
- cmd.exe (PID: 1380)
- cmd.exe (PID: 2992)
- cmd.exe (PID: 2936)
- cmd.exe (PID: 332)
- cmd.exe (PID: 1252)
- cmd.exe (PID: 3348)
- cmd.exe (PID: 2816)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 2748)
Starts itself from another location
- javaw.exe (PID: 2748)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3560)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 3560)
Application launched itself
- chrome.exe (PID: 3560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:06:11 00:23:17 |
| ZipCRC: | 0xa523e605 |
| ZipCompressedSize: | 640709 |
| ZipUncompressedSize: | 939169 |
| ZipFileName: | xghqeaybun/resources/ndwhyfskks |
Total processes
152
Monitored processes
86
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | cmd.exe | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 560 | cmd.exe | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | C:\Users\admin\AppData\Roaming\Oracle\bin\javaw.exe -jar C:\Users\admin\teCuKjNOsLj\UPicYpKHxeQ.SkskTd | C:\Users\admin\AppData\Roaming\Oracle\bin\javaw.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 772 | reg query "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=976,11684397312337299927,3294510561378010974,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=18401828316206137569 --mojo-platform-channel-handle=2172 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 812 | C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 828 | cmd.exe | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 904 | reg query "HKEY_CURRENT_USER\Software\DownloadManager\Passwords" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1024 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\nzBHoIUFty.vbs" | C:\Windows\System32\WScript.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
19 057
Read events
18 714
Write events
338
Delete events
5
Modification events
| (PID) Process: | (1024) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\nzBHoIUFty |
| Operation: | write | Name: | |
Value: false - 6/12/2019 | |||
| (PID) Process: | (3640) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3640) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3640) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ntfsmgr |
Value: "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\ntfsmgr.jar" | |||
| (PID) Process: | (1024) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | nzBHoIUFty |
Value: wscript.exe //B "C:\Users\admin\AppData\Roaming\nzBHoIUFty.vbs" | |||
| (PID) Process: | (1024) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | nzBHoIUFty |
Value: wscript.exe //B "C:\Users\admin\AppData\Roaming\nzBHoIUFty.vbs" | |||
| (PID) Process: | (1024) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1024) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1024) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (1024) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
114
Suspicious files
81
Text files
309
Unknown types
32
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3152 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3152 | javaw.exe | C:\Users\admin\mxcgpoiqmm.vbs | text | |
MD5:— | SHA256:— | |||
| 3640 | wscript.exe | C:\Users\admin\AppData\Roaming\nzBHoIUFty.vbs | text | |
MD5:— | SHA256:— | |||
| 1024 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\nzBHoIUFty.vbs | text | |
MD5:— | SHA256:— | |||
| 1912 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3640 | wscript.exe | C:\Users\admin\AppData\Roaming\ntfsmgr.jar | java | |
MD5:— | SHA256:— | |||
| 2748 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 1712 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2500 | cmd.exe | C:\Users\admin\AppData\Local\Temp\output.txt | text | |
MD5:— | SHA256:— | |||
| 2748 | javaw.exe | C:\Users\admin\AppData\Local\Temp\_0.2816860079703849048812341403543928.class | java | |
MD5:781FB531354D6F291F1CCAB48DA6D39F | SHA256:97D585B6AFF62FB4E43E7E6A5F816DCD7A14BE11A88B109A9BA9E8CD4C456EB9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
98
DNS requests
24
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3560 | chrome.exe | GET | 200 | 173.194.135.106:80 | http://r5---sn-aigzrn7z.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=109.169.22.99&mm=28&mn=sn-aigzrn7z&ms=nvh&mt=1560322477&mv=m&pl=22&shardbypass=yes | US | crx | 842 Kb | whitelisted |
3560 | chrome.exe | GET | 302 | 172.217.21.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 504 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1024 | WScript.exe | 178.239.21.25:5000 | pm2bitcoin.com | Telekomunikacije Republike Srpske akcionarsko drustvo Banja Luka | BA | malicious |
584 | javaw.exe | 104.244.75.220:7700 | wasjar.dynu.net | FranTech Solutions | US | malicious |
3560 | chrome.exe | 216.58.205.227:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3560 | chrome.exe | 172.217.21.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
3560 | chrome.exe | 216.58.207.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
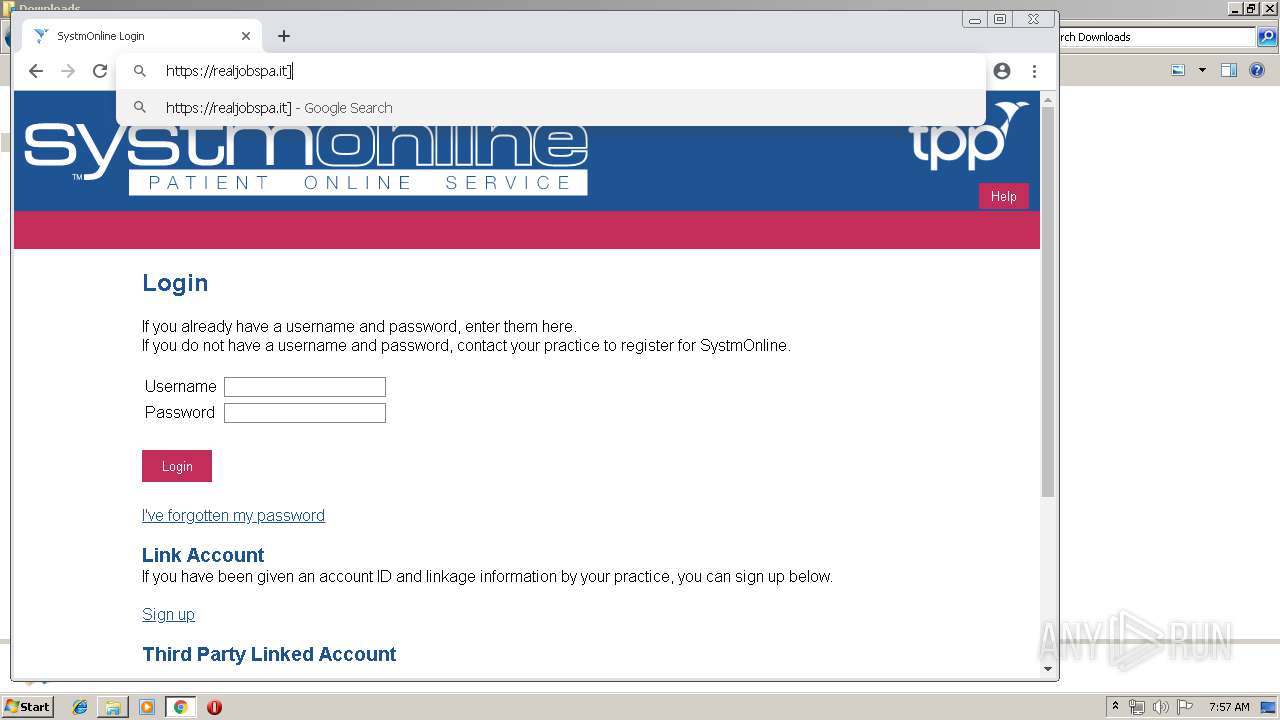
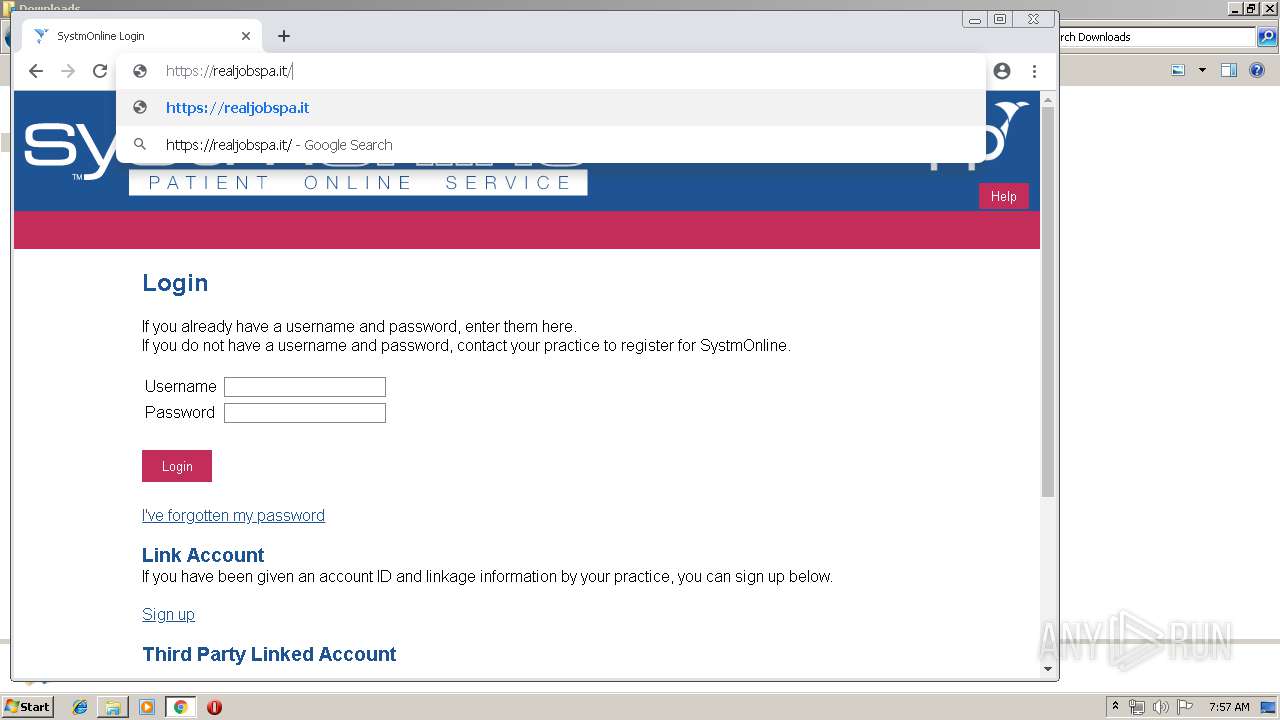
— | — | 46.37.12.168:443 | realjobspa.it | Aruba S.p.A. | IT | unknown |
3560 | chrome.exe | 216.58.205.238:443 | clients1.google.com | Google Inc. | US | whitelisted |
3560 | chrome.exe | 172.217.18.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3560 | chrome.exe | 172.217.23.132:443 | www.google.com | Google Inc. | US | whitelisted |
3560 | chrome.exe | 172.217.16.131:443 | www.google.co.uk | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pm2bitcoin.com |
| malicious |
wasjar.dynu.net |
| malicious |
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
realjobspa.it |
| unknown |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
584 | javaw.exe | A Network Trojan was detected | ET TROJAN Possible Adwind SSL Cert (assylias.Inc) |
584 | javaw.exe | A Network Trojan was detected | MALWARE [PTsecurity] Backdoor.Java.Adwind.cu |
584 | javaw.exe | A Network Trojan was detected | MALWARE [PTsecurity] Backdoor.Java.Adwind.cu |
584 | javaw.exe | A Network Trojan was detected | ET TROJAN Possible Adwind SSL Cert (assylias.Inc) |
584 | javaw.exe | A Network Trojan was detected | ET TROJAN Possible Adwind SSL Cert (assylias.Inc) |
584 | javaw.exe | A Network Trojan was detected | ET TROJAN Possible Adwind SSL Cert (assylias.Inc) |