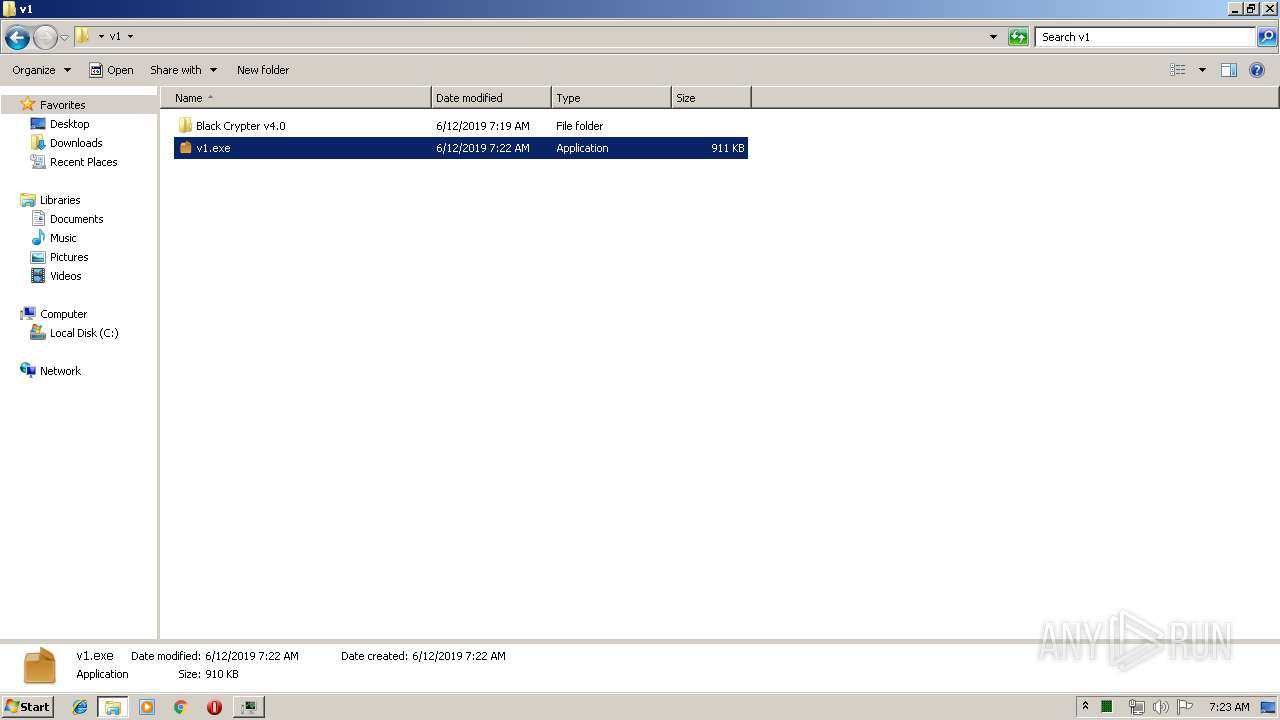
| File name: | v1.rar |
| Full analysis: | https://app.any.run/tasks/86f7076c-7f48-4f59-8a4e-79bcf222cc0c |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | June 12, 2019, 06:21:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 85B776ED7C09ACFF0D734E7C61F080B7 |
| SHA1: | C1F7C1DC24877C44736CC15DE89B4E280C3588AC |
| SHA256: | 8804ED6AD42B96A09201E265E9A3A6F3930C36C7E31AC9BC3C30EC8257C26A2D |
| SSDEEP: | 12288:IUv/R3ASL9vSyxUHle5NVoJMVbs+DAThGoDZ2vIfxUhdnnPIXo+G+dAuzoUyvEb4:IU3GC9vSyxUFeu0TDKNOjrirTGdn |
MALICIOUS
Starts Visual C# compiler
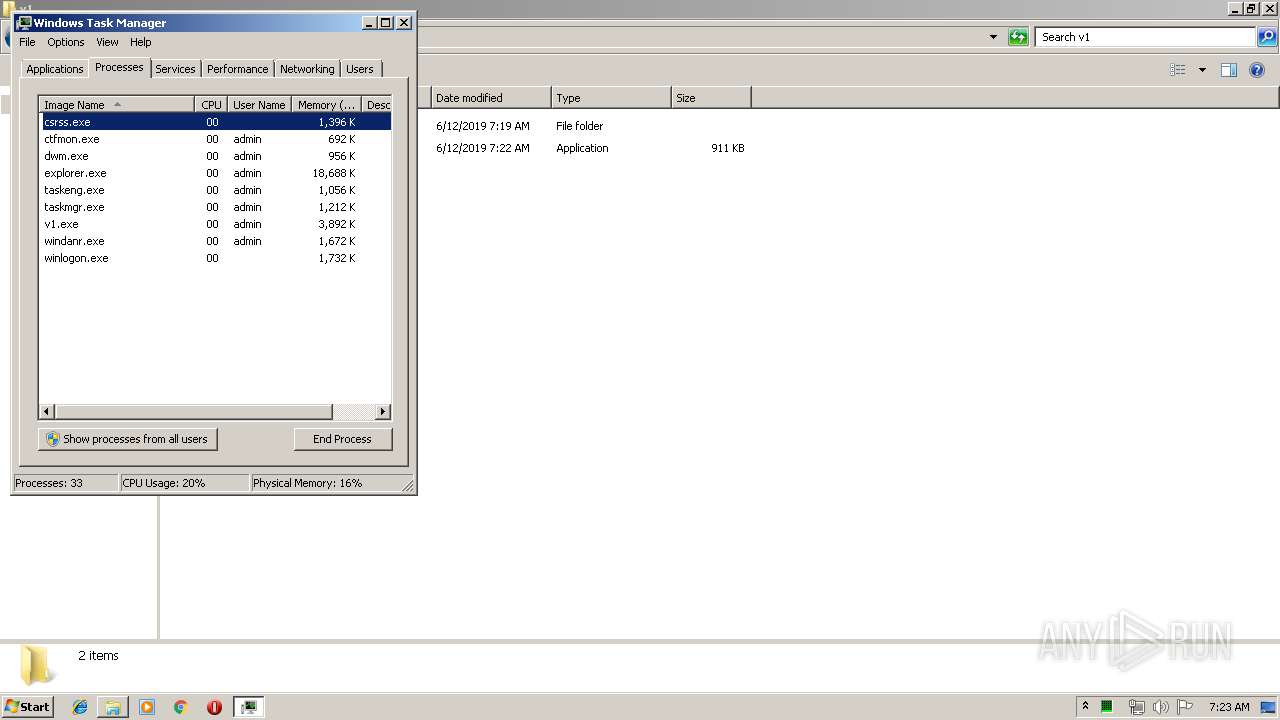
- v1.exe (PID: 2144)
- v1.exe (PID: 2928)
- v1.exe (PID: 3956)
- v1.exe (PID: 4084)
- v1.exe (PID: 704)
Application was dropped or rewritten from another process
- v1.exe (PID: 2144)
- v1.exe (PID: 2928)
- v1.exe (PID: 3956)
- v1.exe (PID: 4084)
- v1.exe (PID: 704)
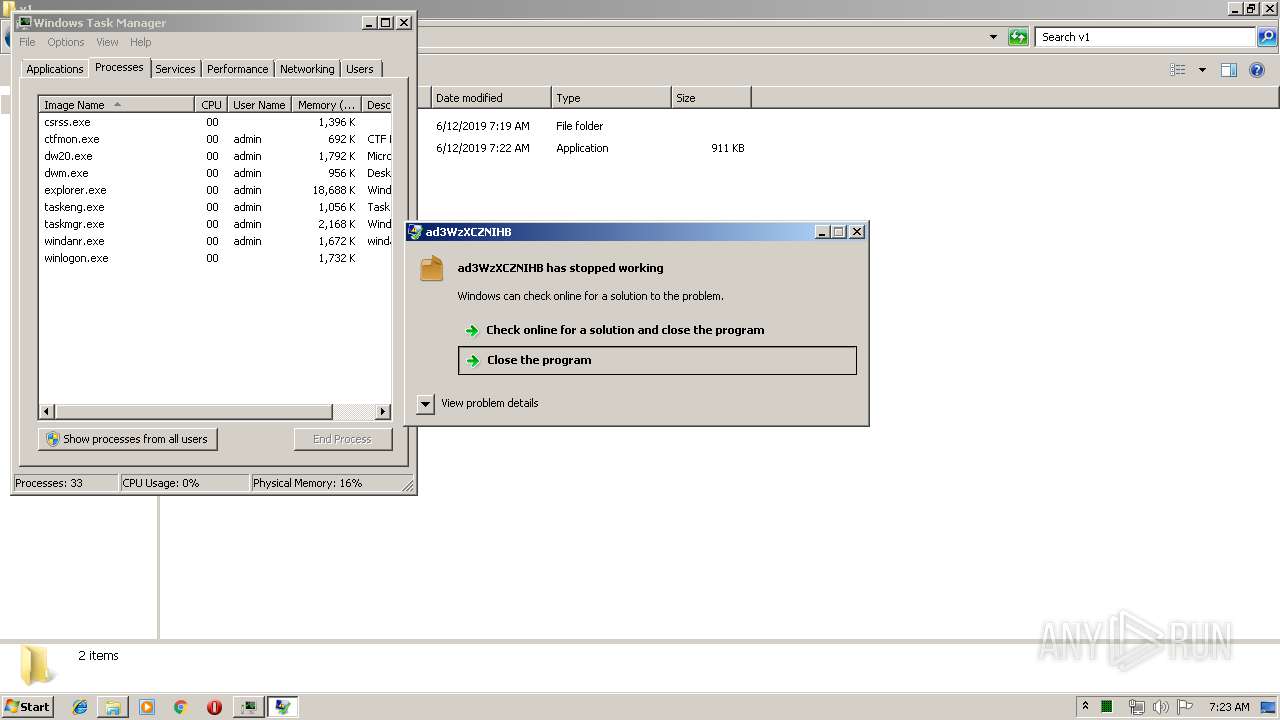
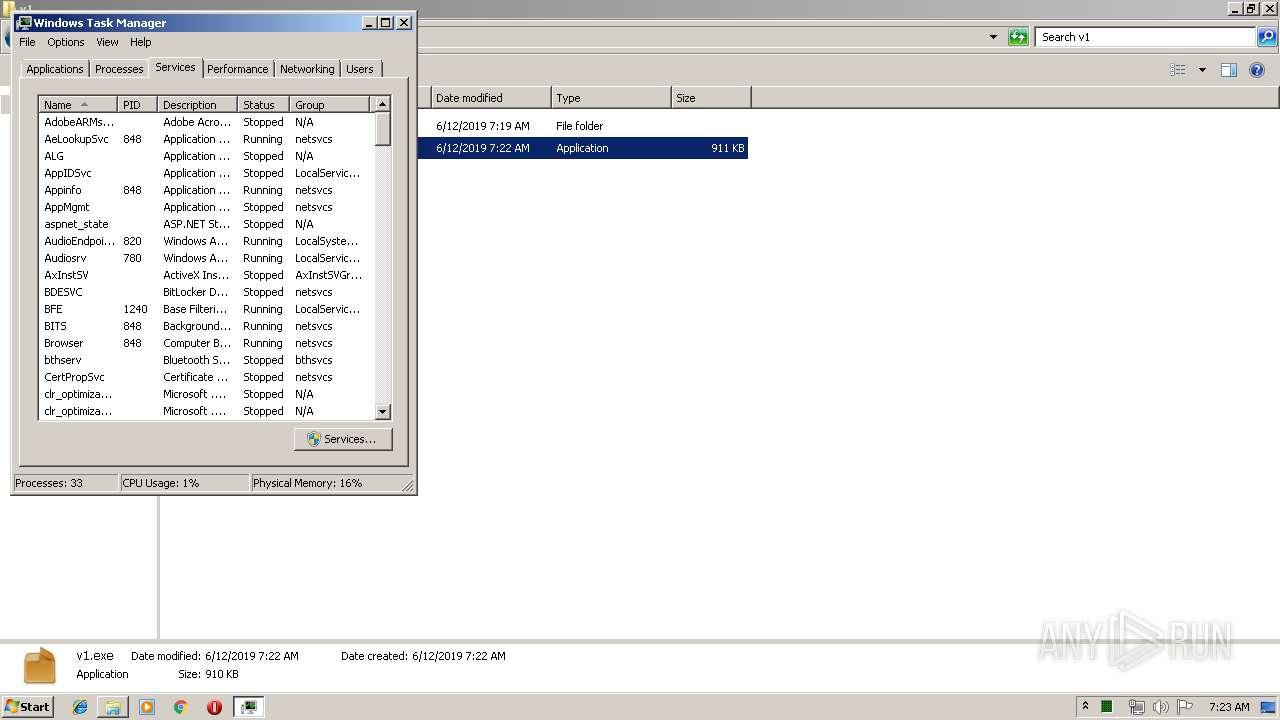
Orcus was detected
- v1.exe (PID: 2144)
- v1.exe (PID: 3956)
- v1.exe (PID: 2928)
- v1.exe (PID: 4084)
- v1.exe (PID: 704)
SUSPICIOUS
Executable content was dropped or overwritten
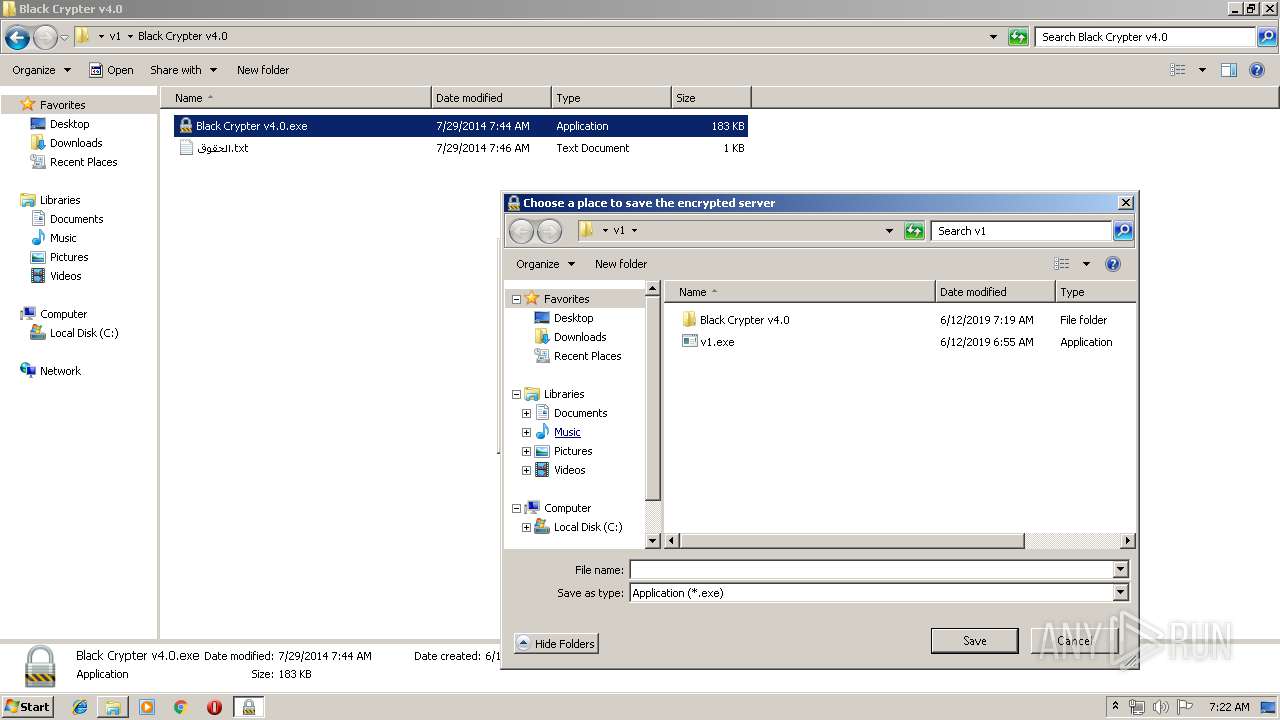
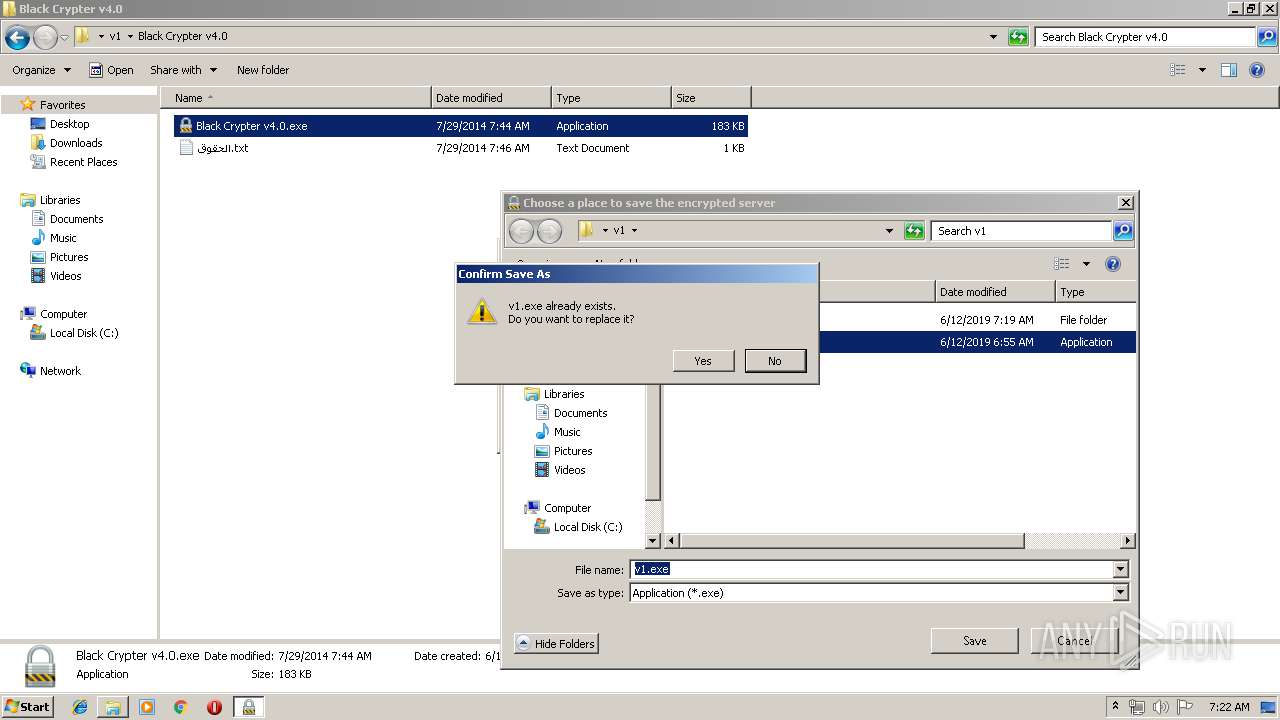
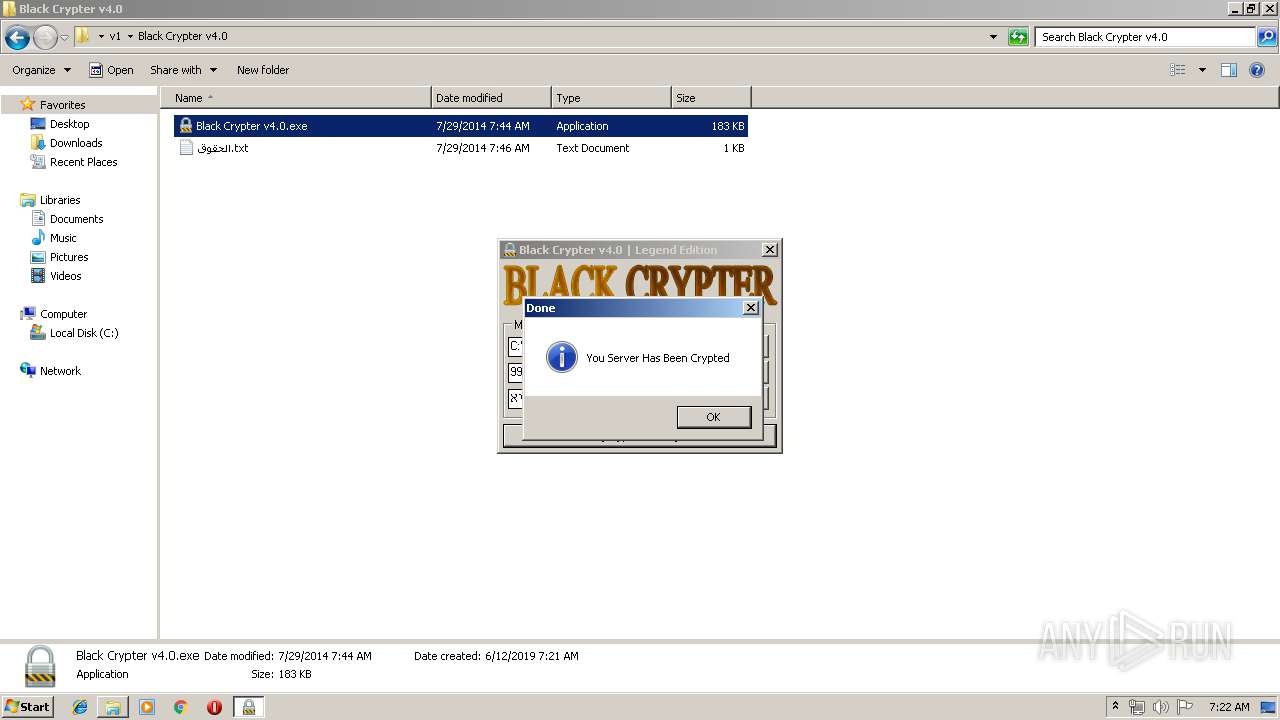
- Black Crypter v4.0.exe (PID: 1932)
INFO
Manual execution by user
- v1.exe (PID: 2144)
- Black Crypter v4.0.exe (PID: 1932)
- v1.exe (PID: 3956)
- NOTEPAD.EXE (PID: 2504)
- v1.exe (PID: 2928)
- v1.exe (PID: 4084)
- taskmgr.exe (PID: 4004)
- explorer.exe (PID: 3032)
- v1.exe (PID: 704)
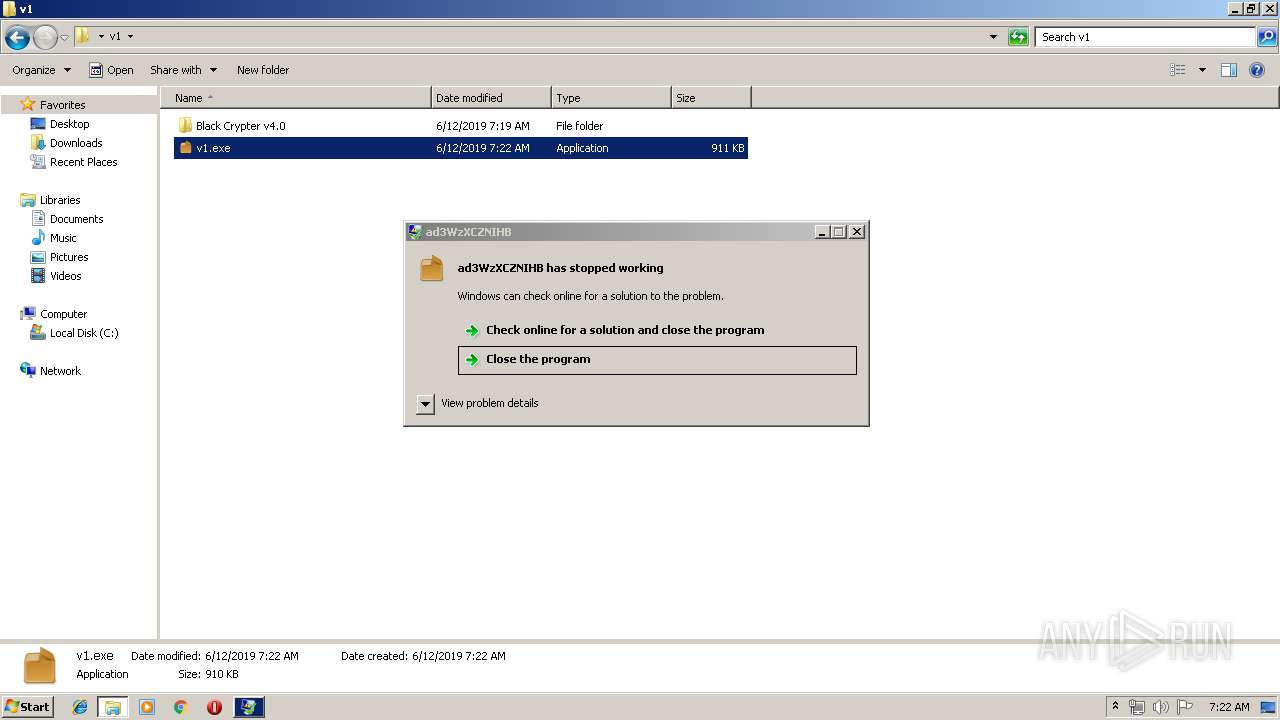
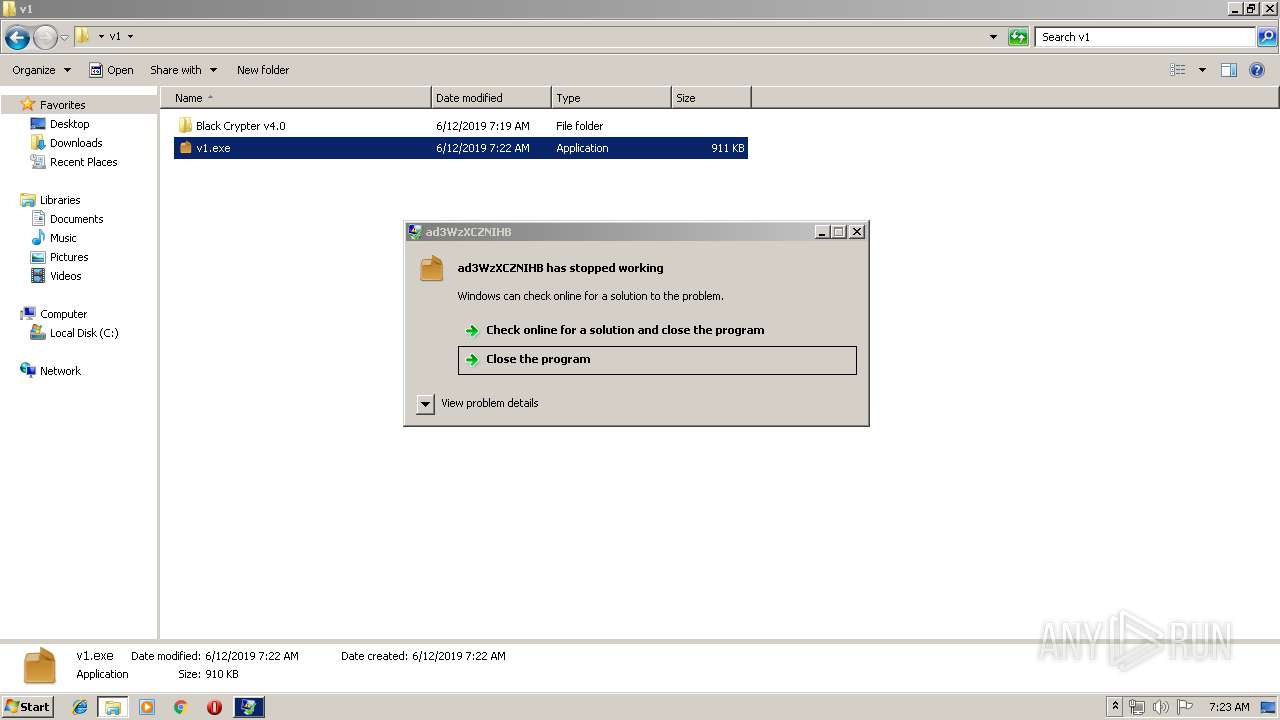
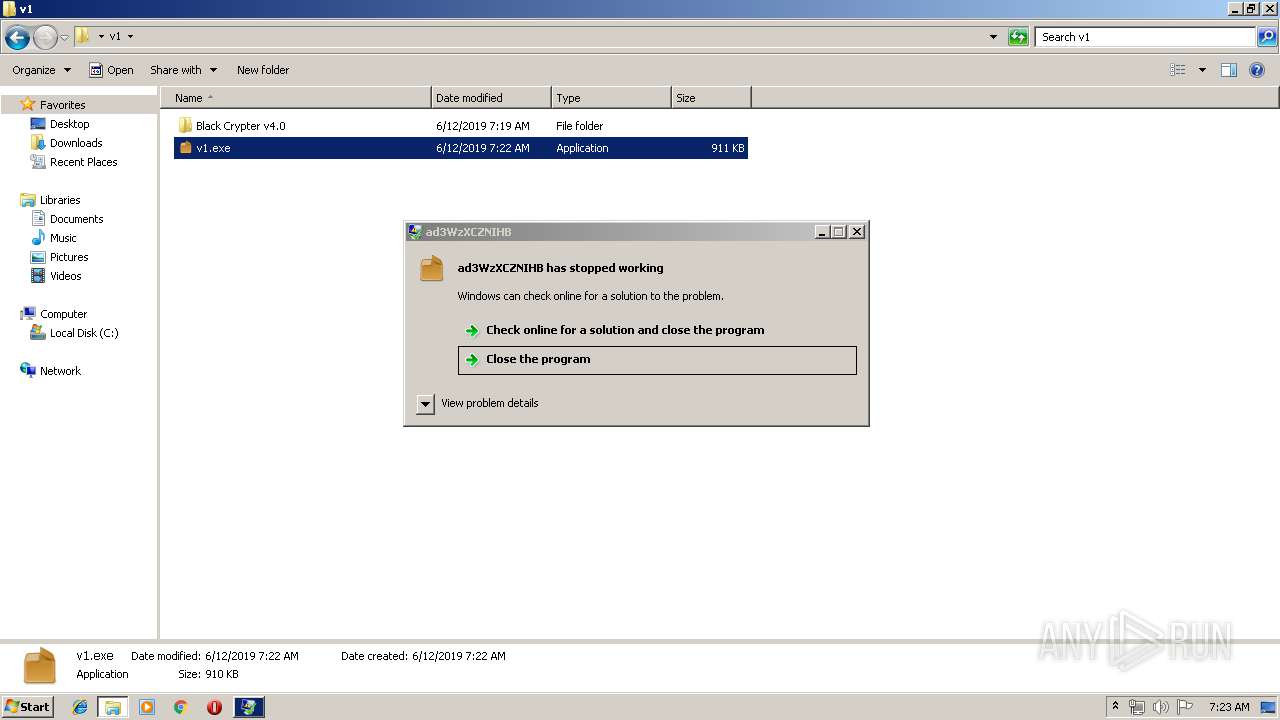
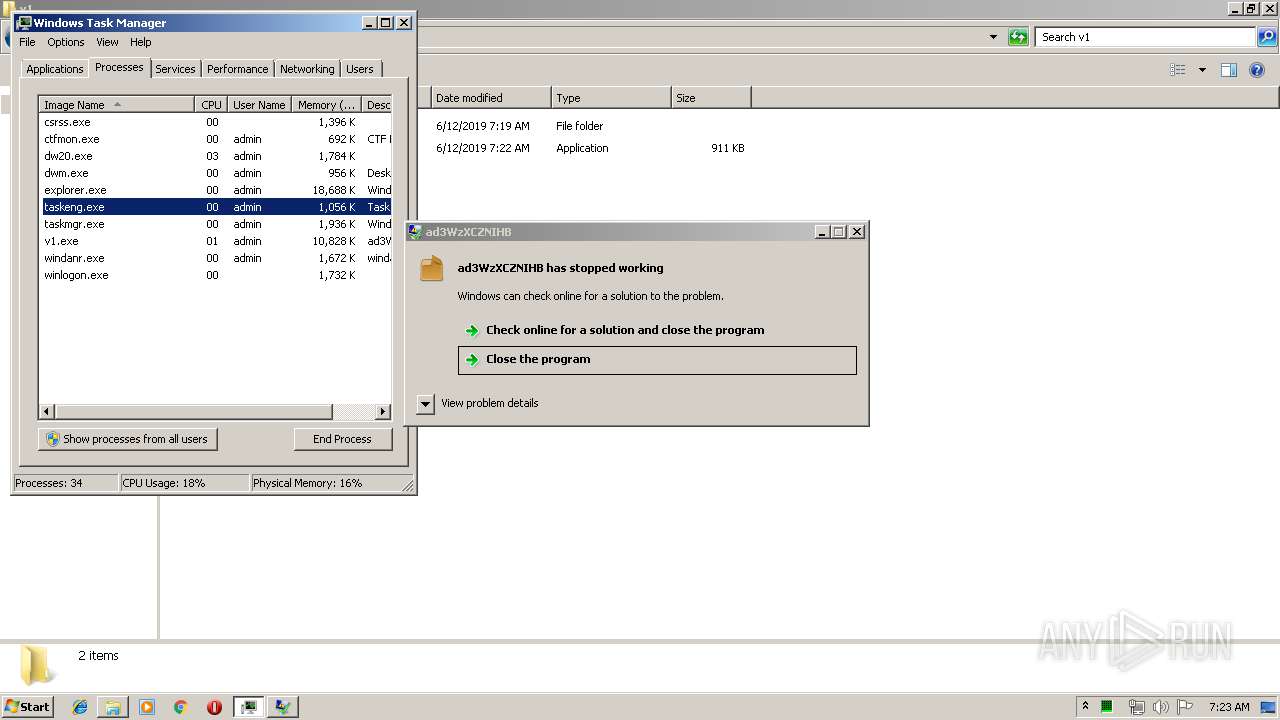
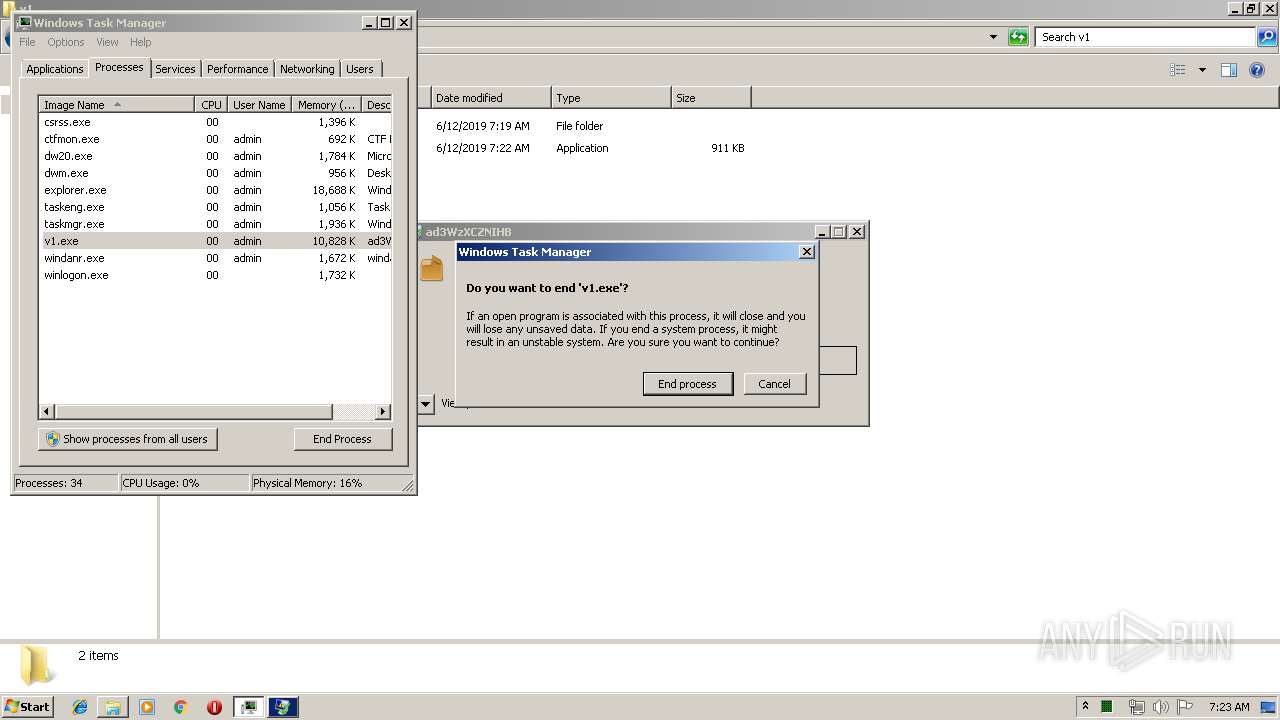
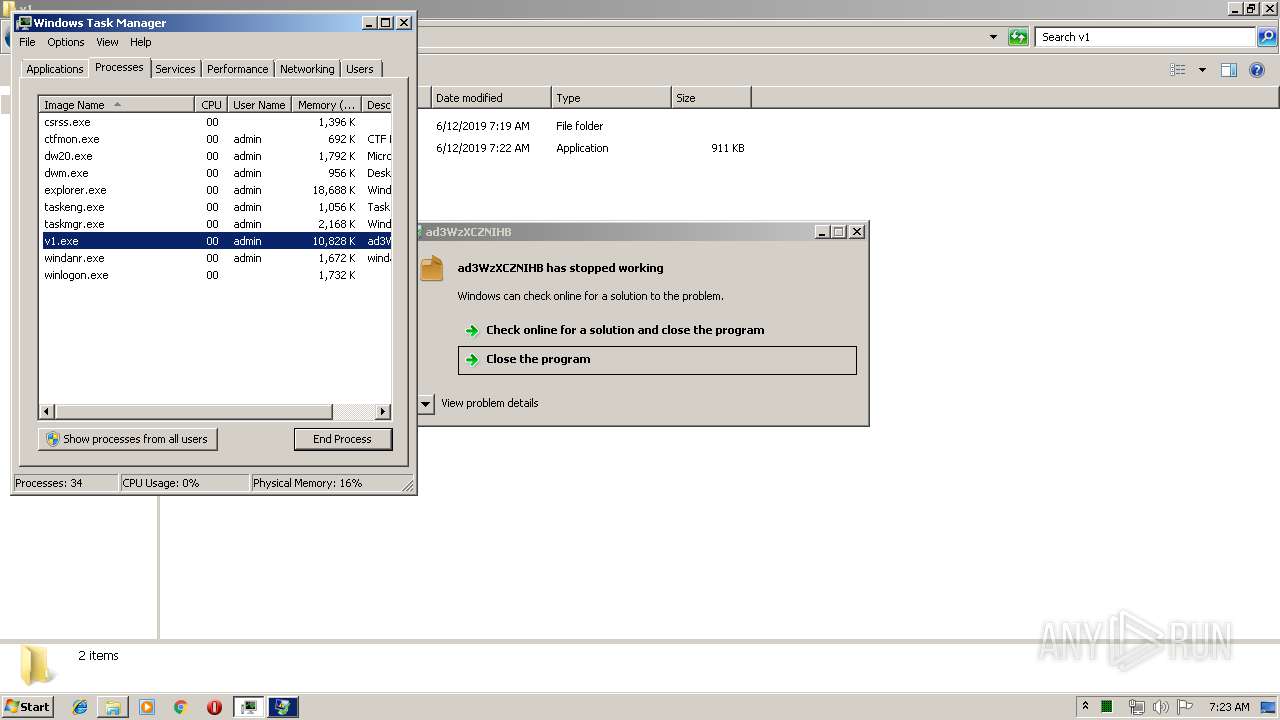
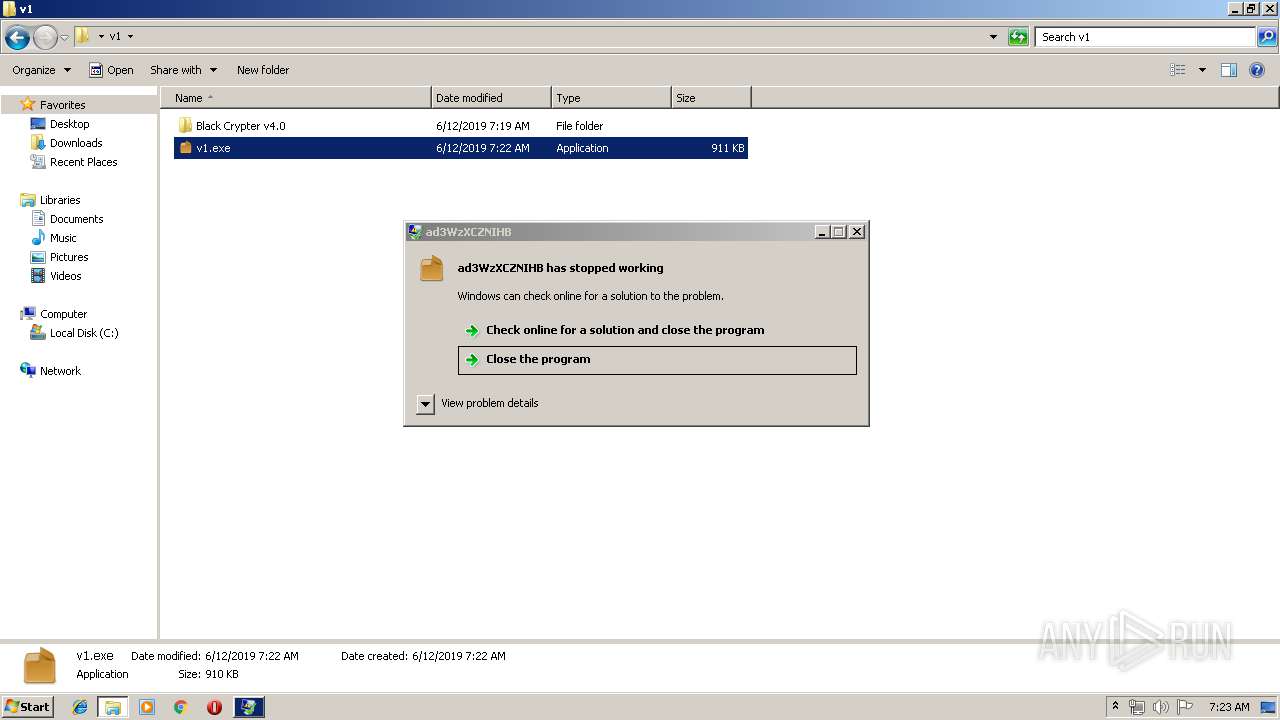
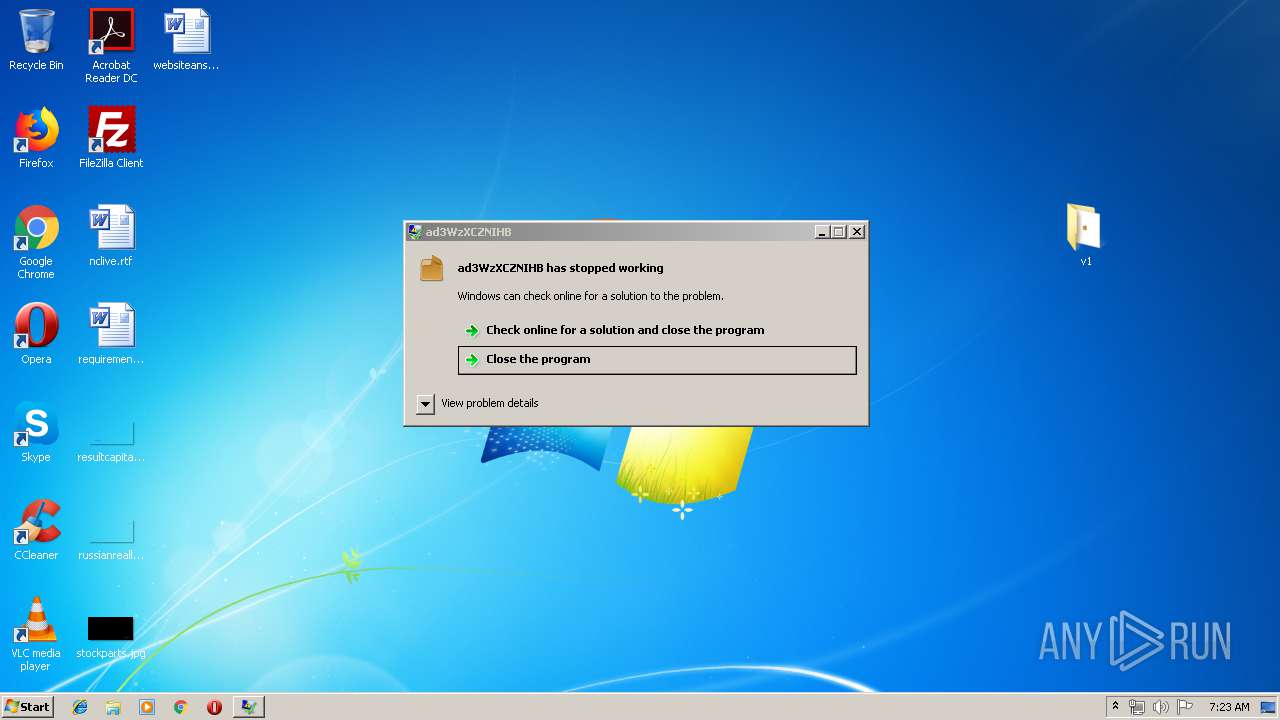
Application was crashed
- v1.exe (PID: 2144)
- v1.exe (PID: 3956)
- v1.exe (PID: 2928)
- v1.exe (PID: 4084)
- v1.exe (PID: 704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
67
Monitored processes
25
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | dw20.exe -x -s 636 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | — | v1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
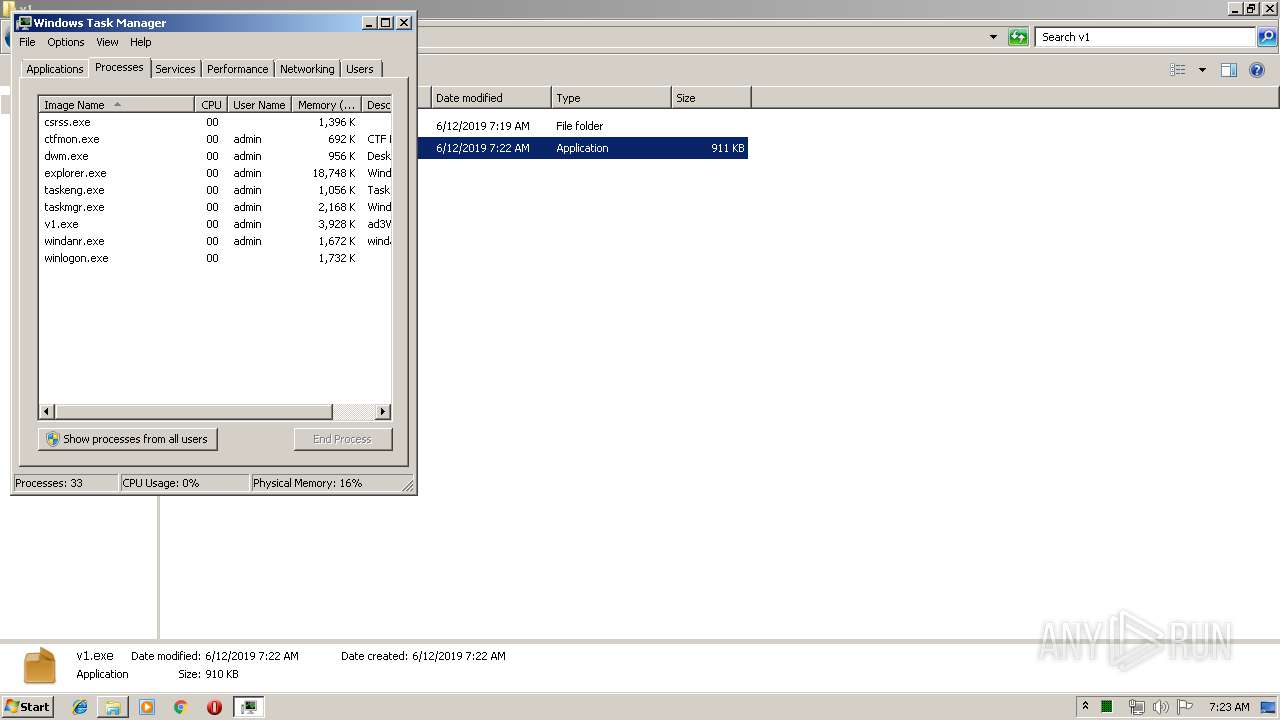
| 704 | "C:\Users\admin\Desktop\v1\v1.exe" | C:\Users\admin\Desktop\v1\v1.exe | explorer.exe | ||||||||||||
User: admin Company: auvt1KNhOBVo Integrity Level: MEDIUM Description: ad3WzXCZNIHB Exit code: 3762507597 Version: 7.9.11.45 Modules
| |||||||||||||||
| 1004 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES3042.tmp" "c:\Users\admin\AppData\Local\Temp\CSC3041.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1336 | dw20.exe -x -s 628 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | — | v1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 1360 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESA901.tmp" "c:\Users\admin\AppData\Local\Temp\CSCA900.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1696 | dw20.exe -x -s 636 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | — | v1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 1932 | "C:\Users\admin\Desktop\v1\Black Crypter v4.0\Black Crypter v4.0.exe" | C:\Users\admin\Desktop\v1\Black Crypter v4.0\Black Crypter v4.0.exe | explorer.exe | ||||||||||||
User: admin Company: Black.Hacker | Darkness Software Integrity Level: MEDIUM Description: Black Crypter v4.0 | Legend Edition Exit code: 0 Version: 4.0.0.0 Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\Desktop\v1\v1.exe" | C:\Users\admin\Desktop\v1\v1.exe | explorer.exe | ||||||||||||
User: admin Company: auvt1KNhOBVo Integrity Level: MEDIUM Description: ad3WzXCZNIHB Exit code: 3762507597 Version: 7.9.11.45 Modules
| |||||||||||||||
| 2488 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\w71deuvm.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | v1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
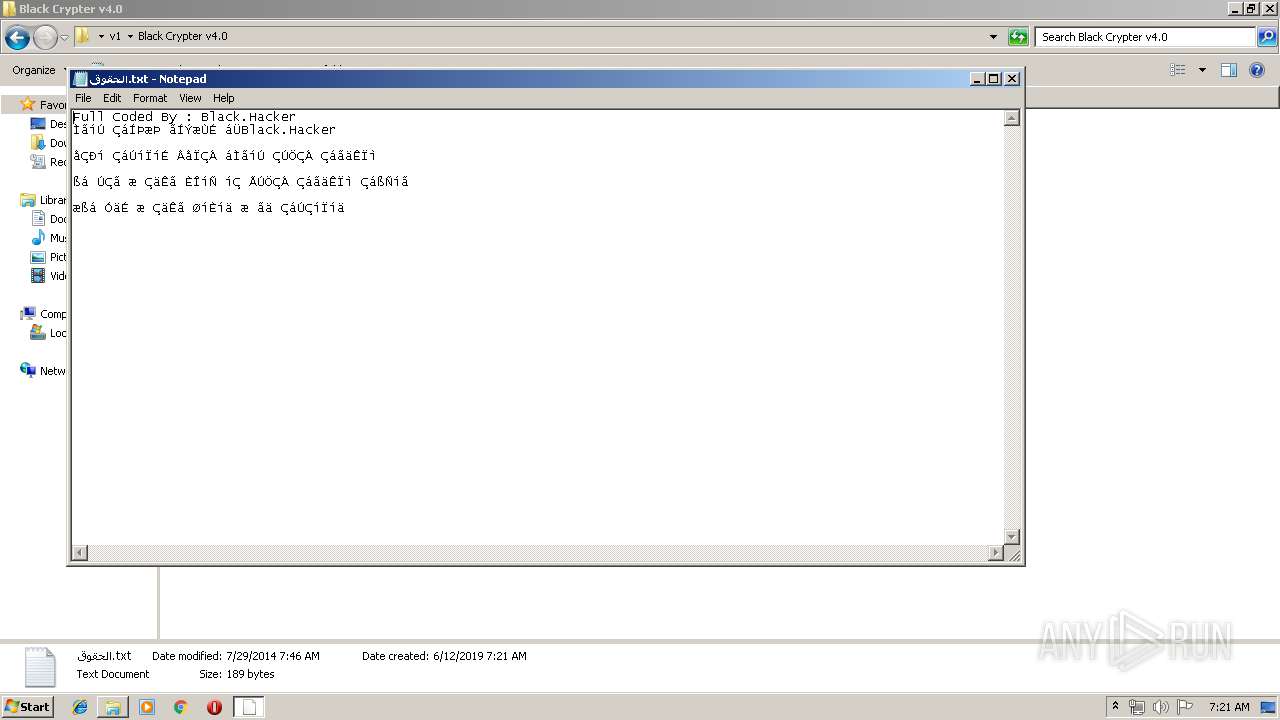
| 2504 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\v1\Black Crypter v4.0\الحقوق.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 236
Read events
1 114
Write events
116
Delete events
6
Modification events
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\v1.rar | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
3
Suspicious files
5
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2628.861\v1\Black Crypter v4.0\Black Crypter v4.0.exe | — | |
MD5:— | SHA256:— | |||
| 2628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2628.861\v1\Black Crypter v4.0\الحقوق.txt | — | |
MD5:— | SHA256:— | |||
| 2628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2628.861\v1\v1.exe | — | |
MD5:— | SHA256:— | |||
| 1932 | Black Crypter v4.0.exe | C:\Users\admin\Desktop\v1\RCX1B37.tmp | — | |
MD5:— | SHA256:— | |||
| 1932 | Black Crypter v4.0.exe | C:\Users\admin\Desktop\v1\RCX1B48.tmp | — | |
MD5:— | SHA256:— | |||
| 1932 | Black Crypter v4.0.exe | C:\Users\admin\Desktop\v1\RCX1B49.tmp | — | |
MD5:— | SHA256:— | |||
| 2144 | v1.exe | C:\Users\admin\AppData\Local\Temp\cznzrcqx.0.cs | — | |
MD5:— | SHA256:— | |||
| 2144 | v1.exe | C:\Users\admin\AppData\Local\Temp\cznzrcqx.cmdline | — | |
MD5:— | SHA256:— | |||
| 2644 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC6417.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES6418.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report