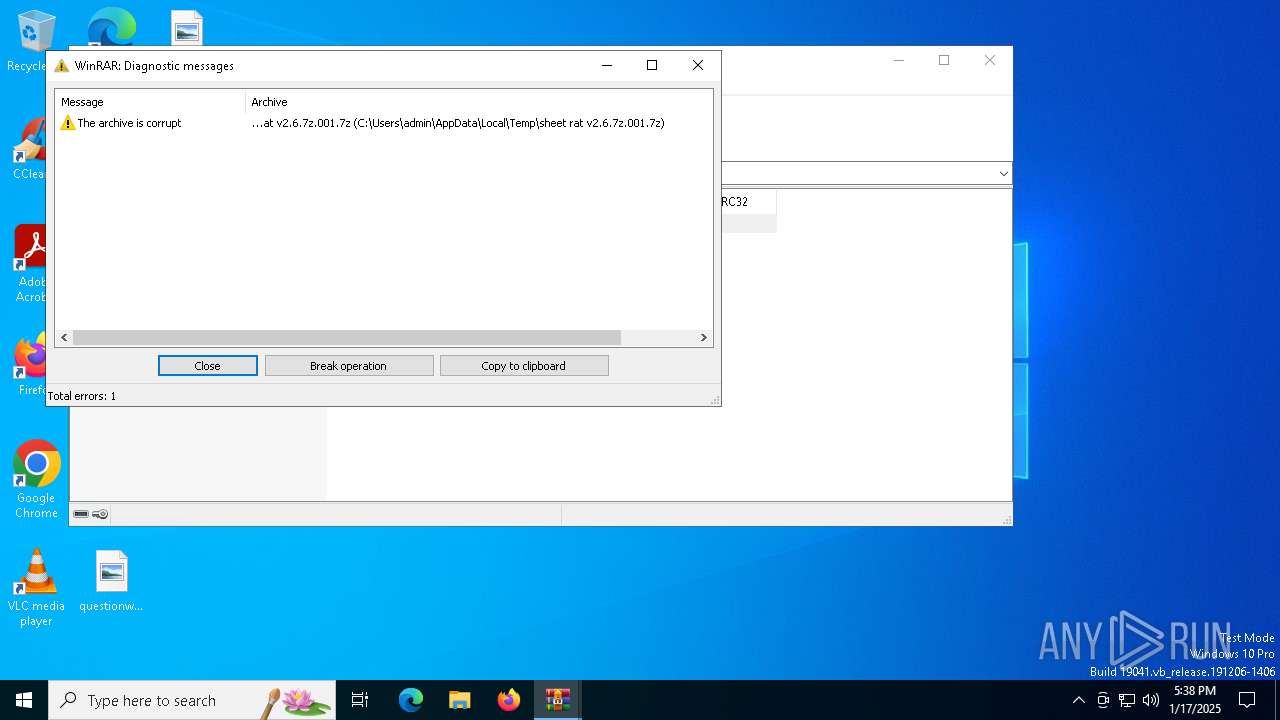
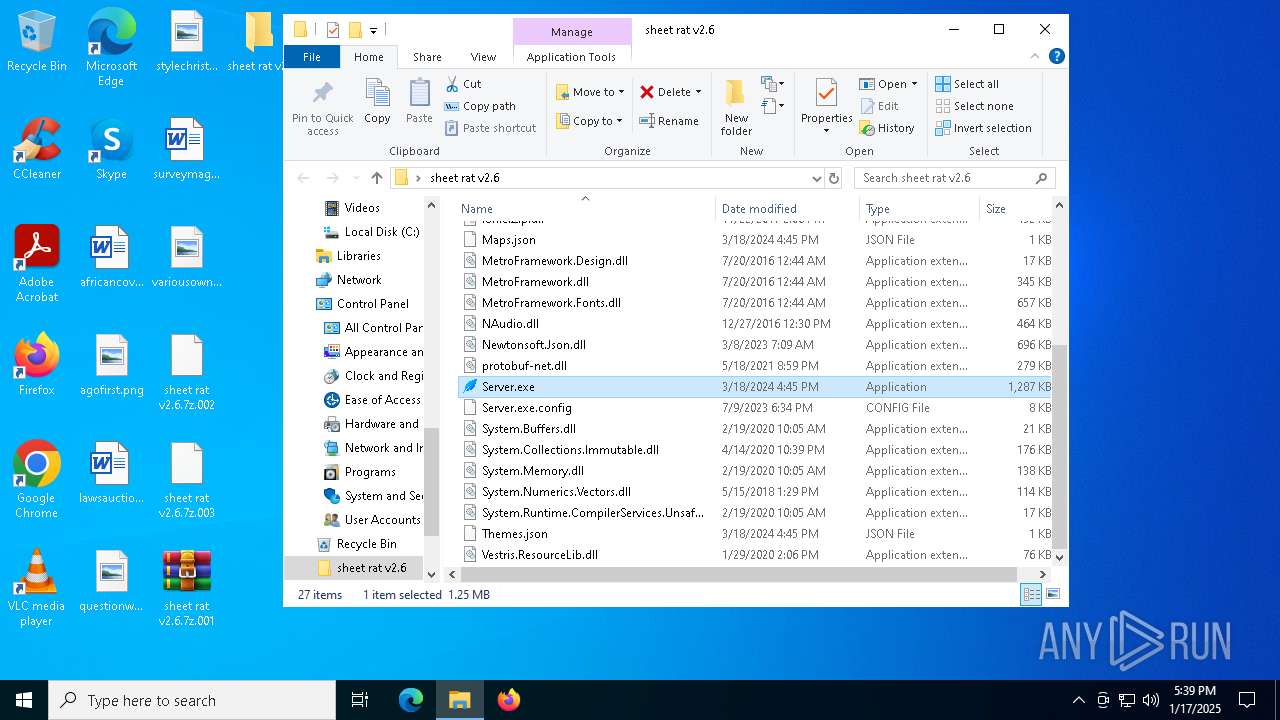
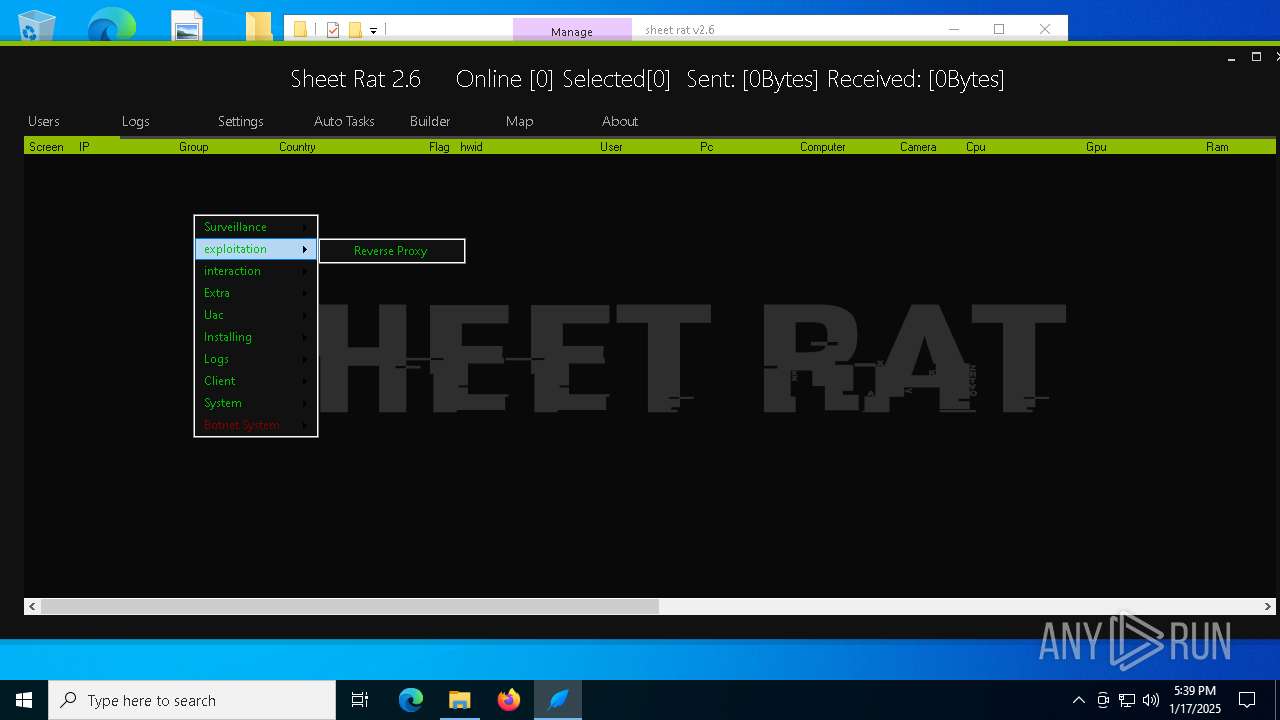
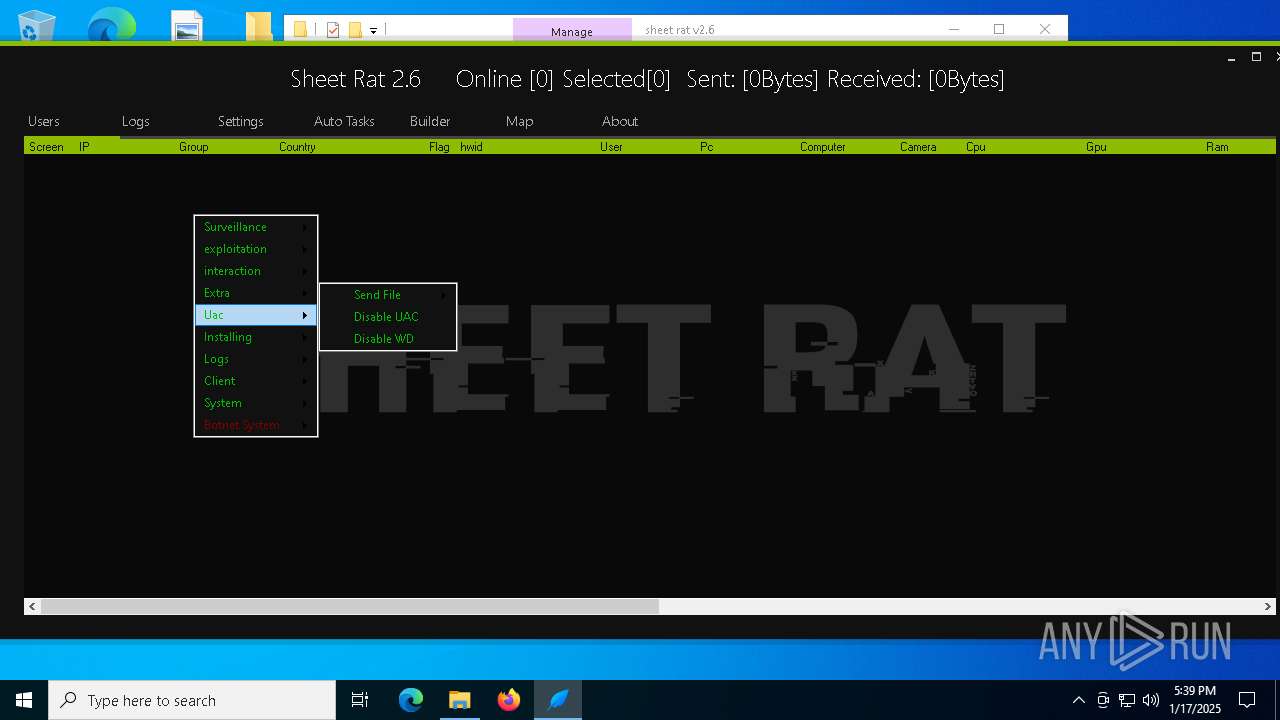
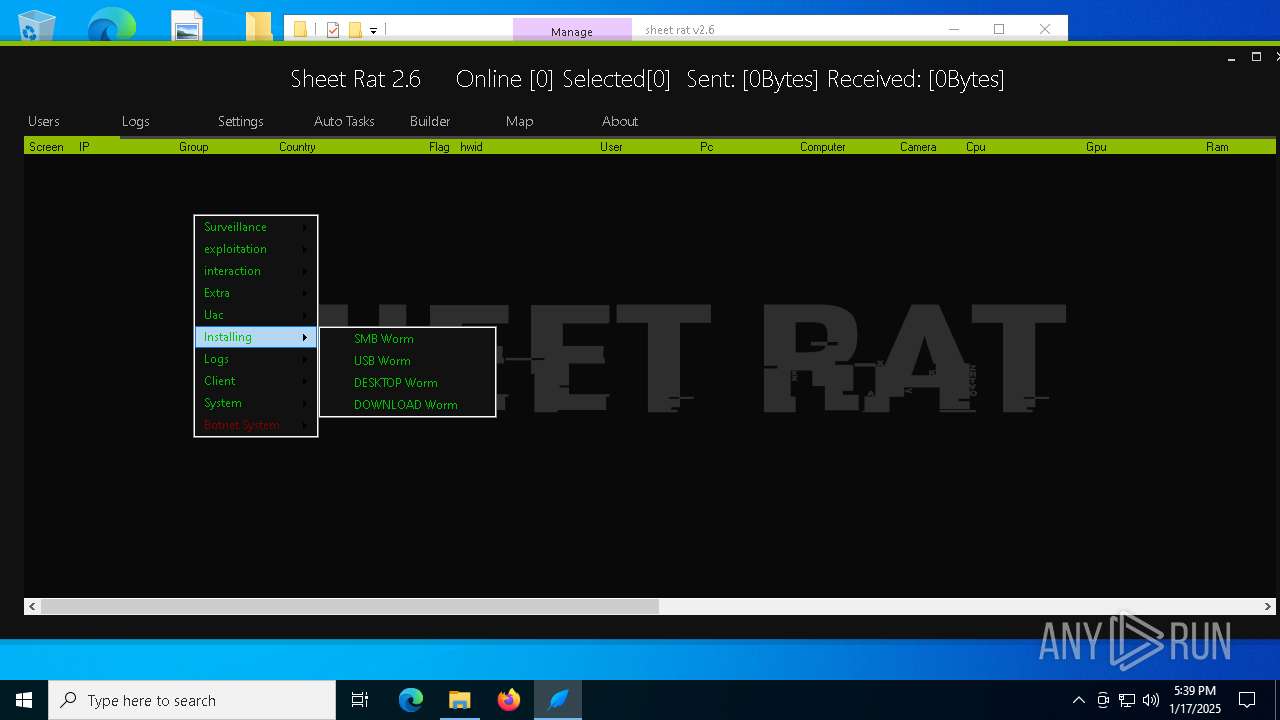
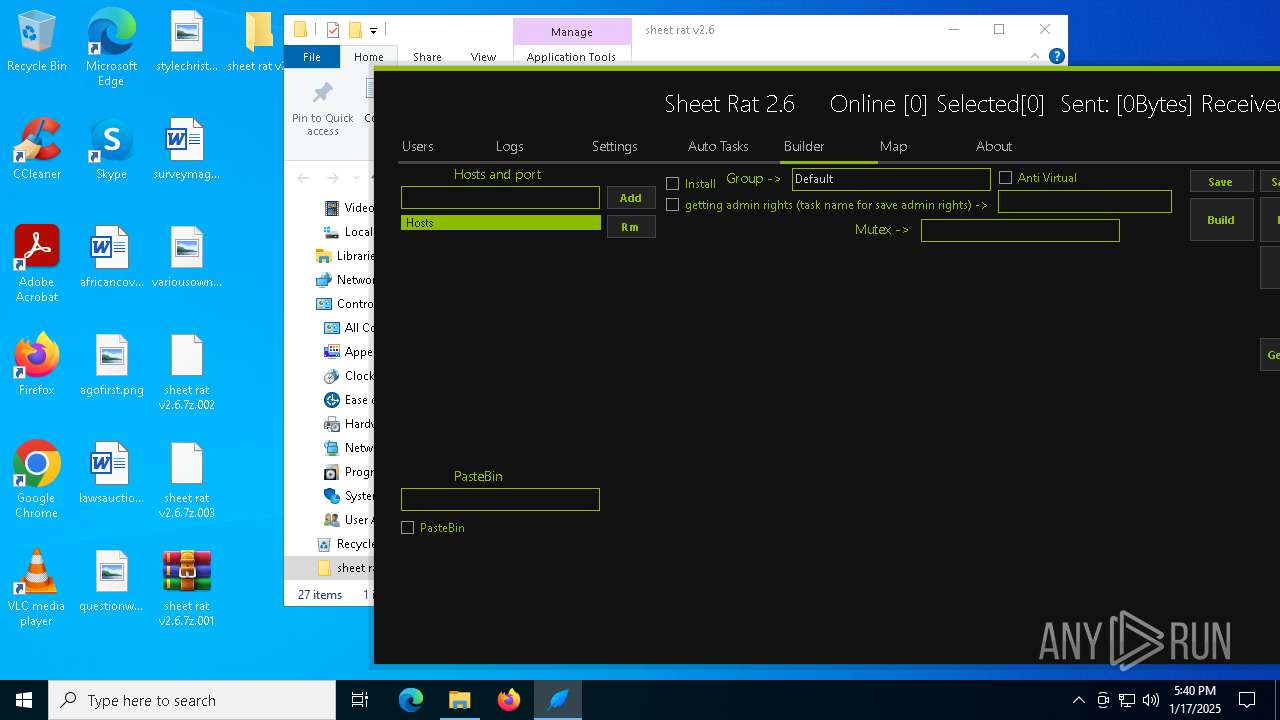
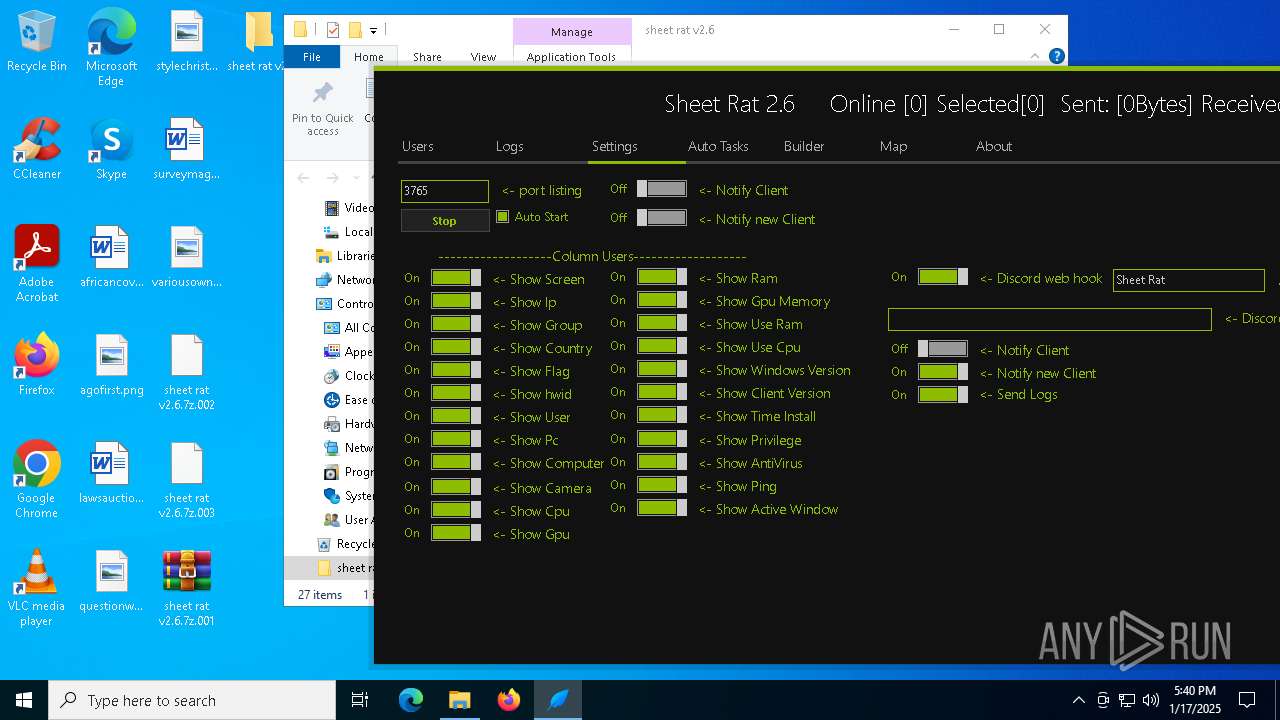
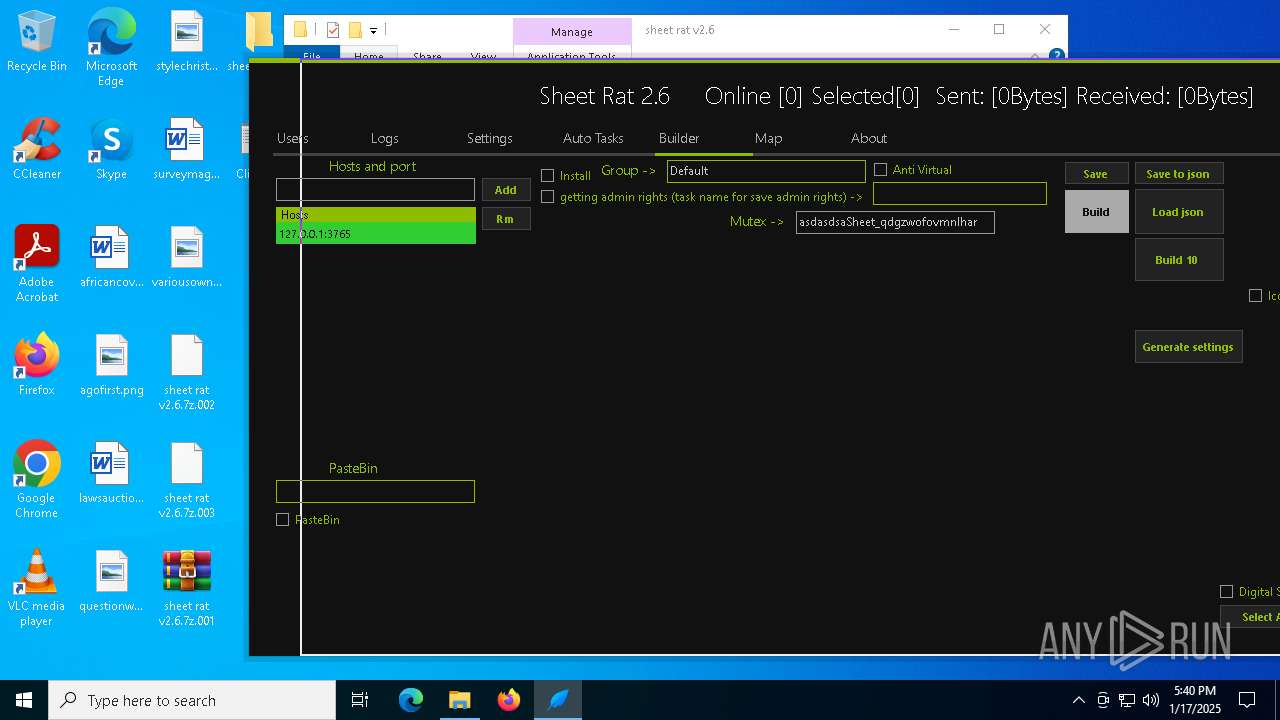
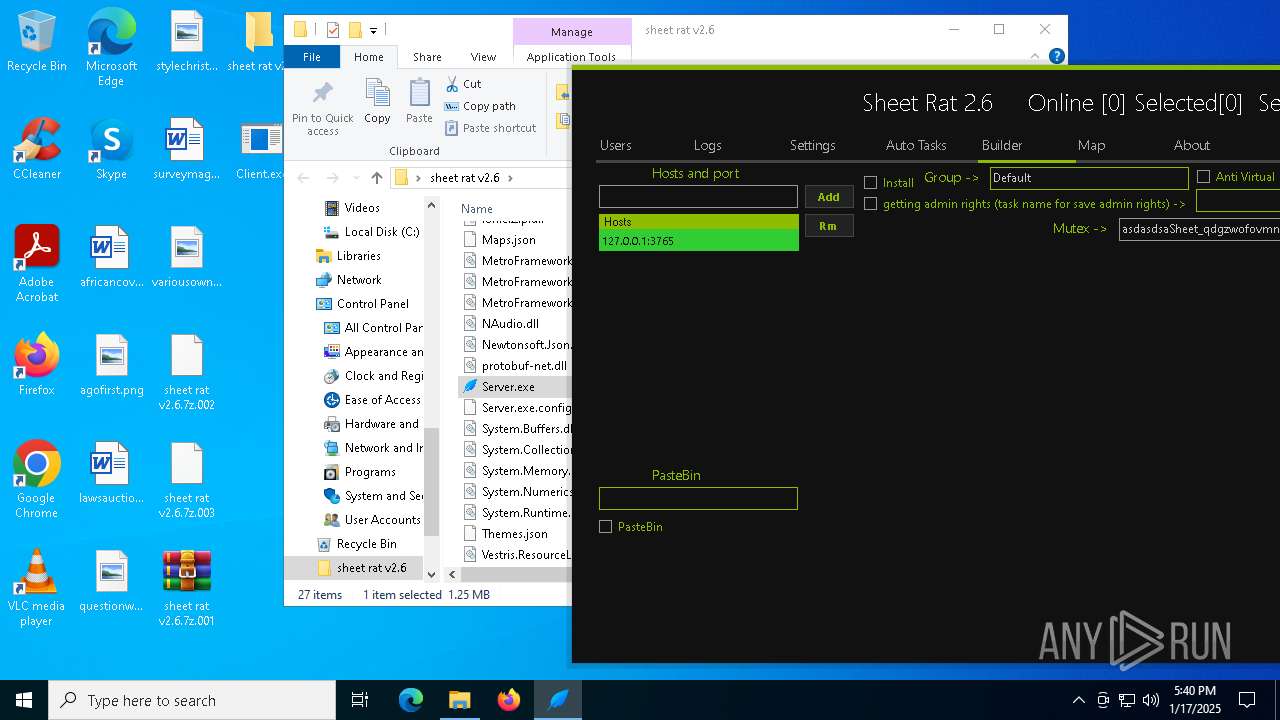
| File name: | sheet rat v2.6.7z.001 |
| Full analysis: | https://app.any.run/tasks/5c52a463-8c19-4161-b1a9-98c16e9a813a |
| Verdict: | Malicious activity |
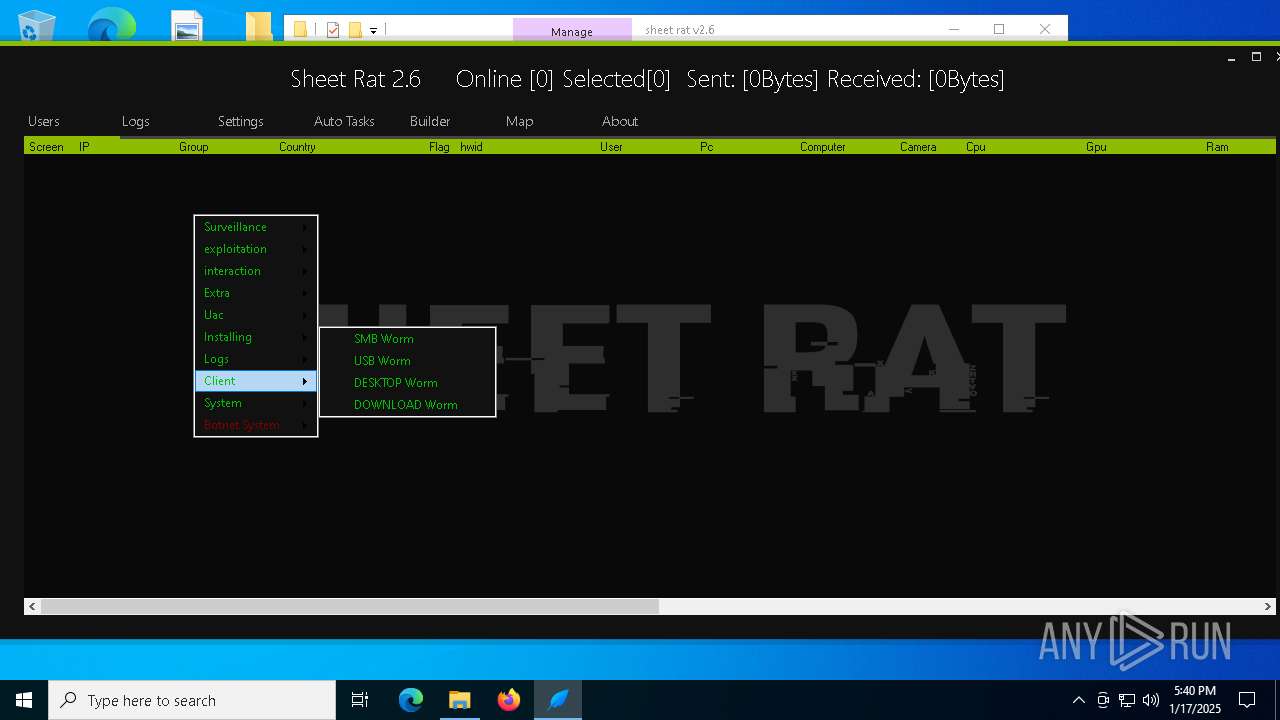
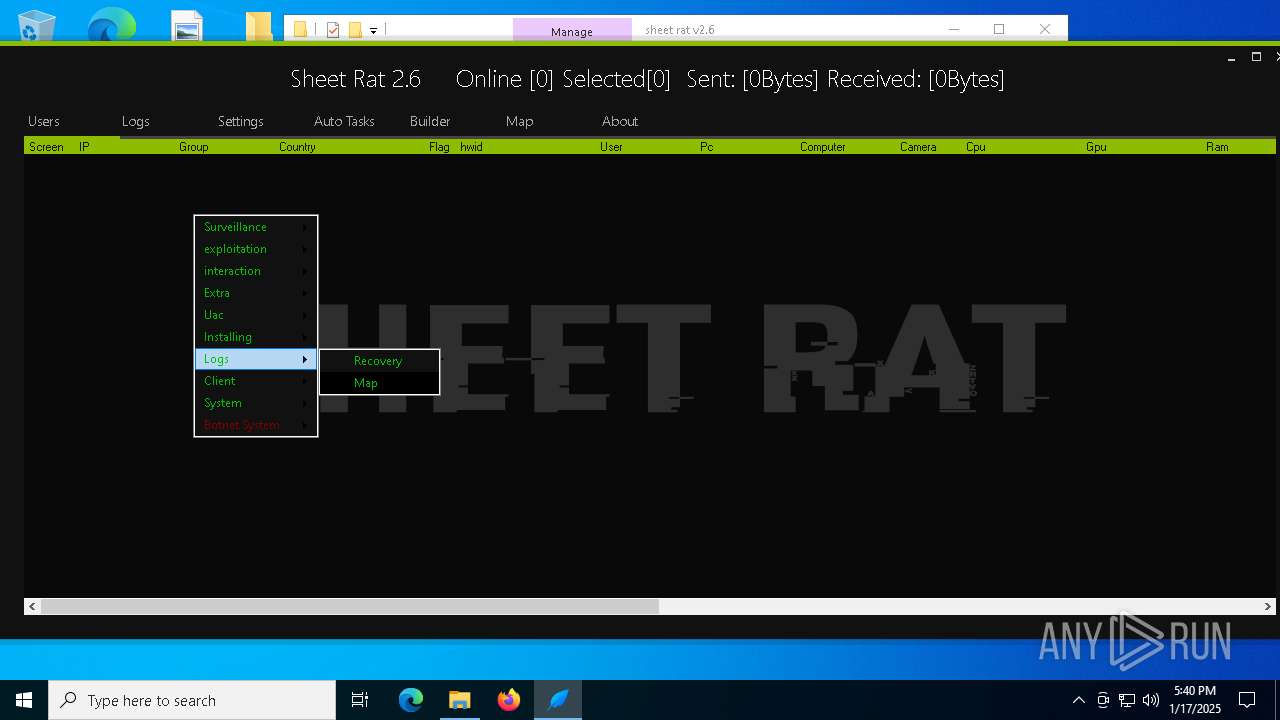
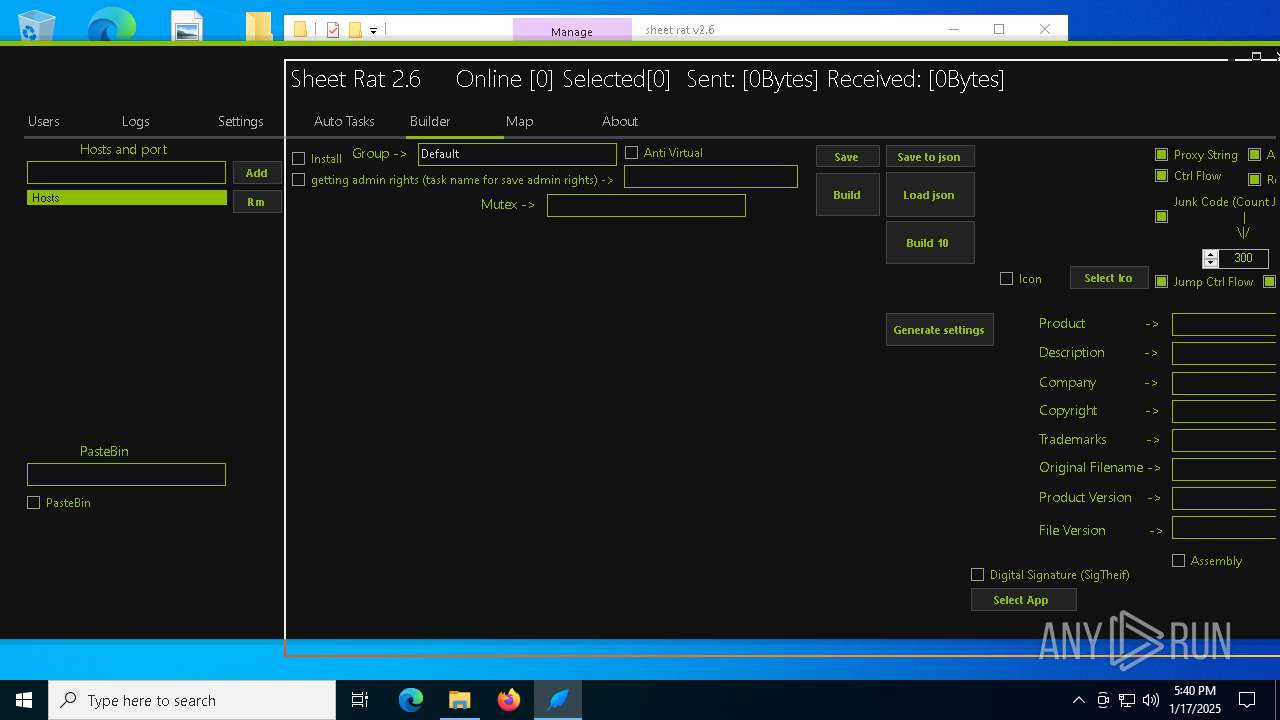
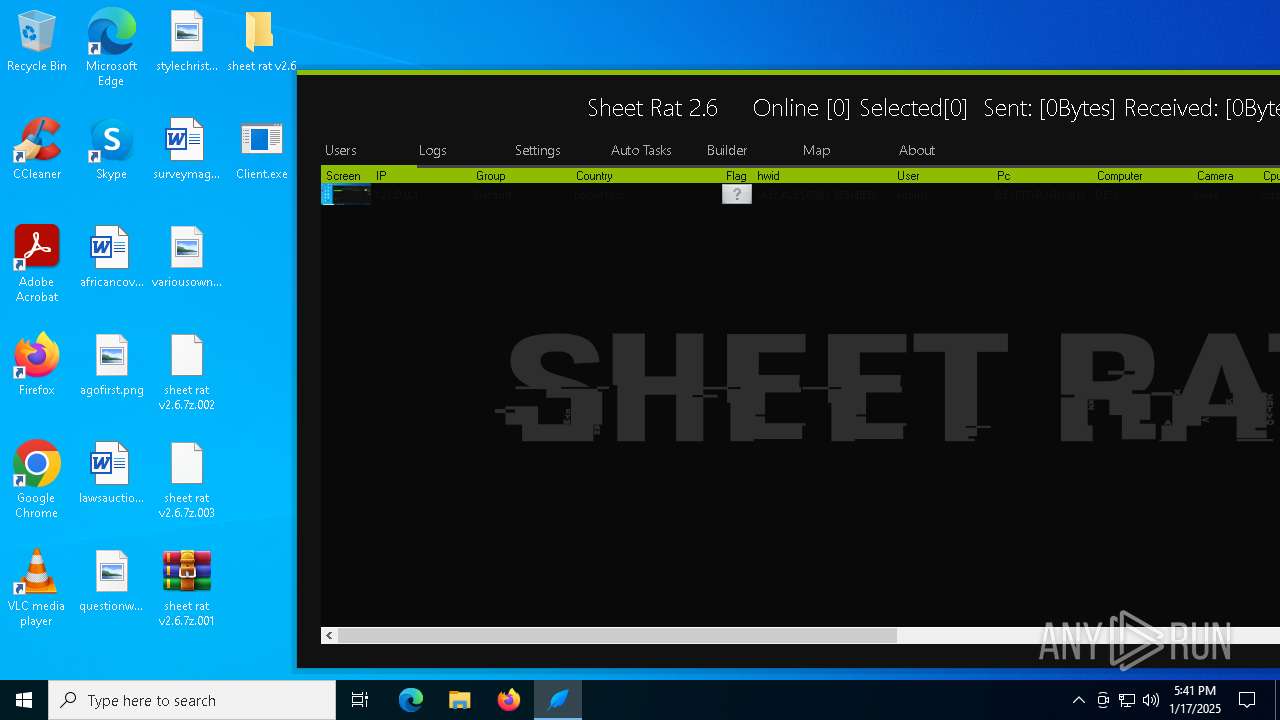
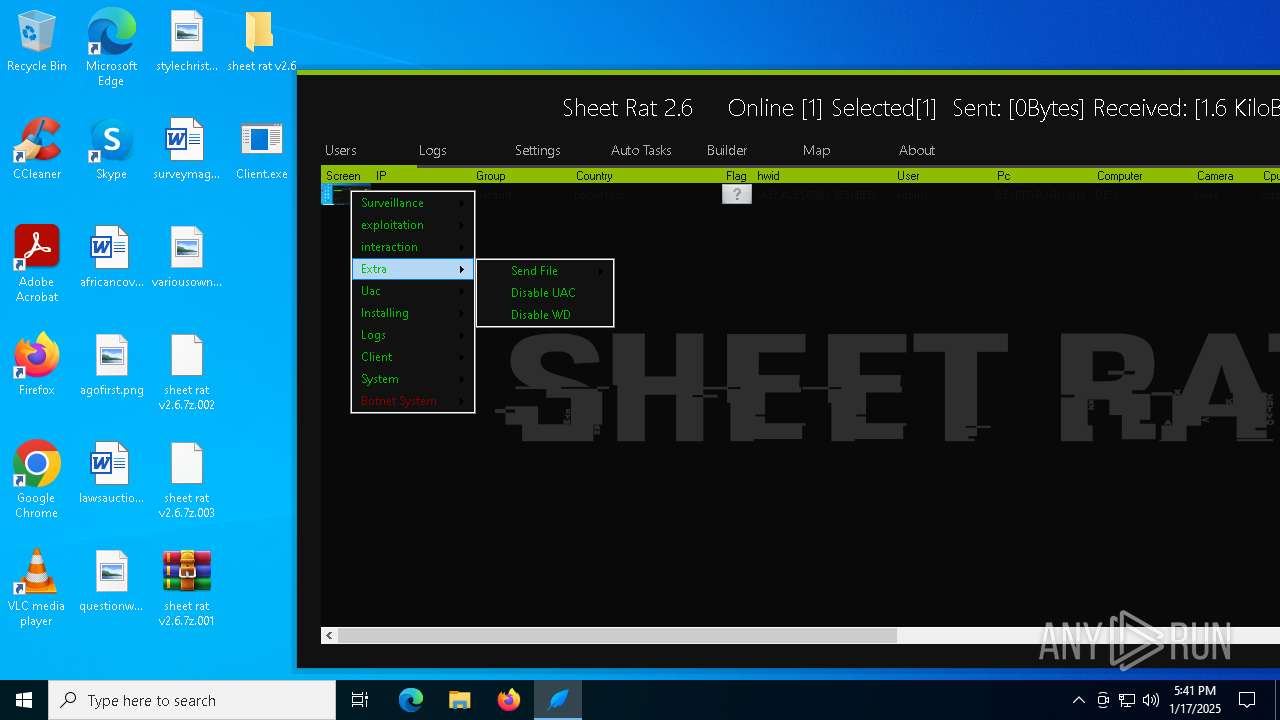
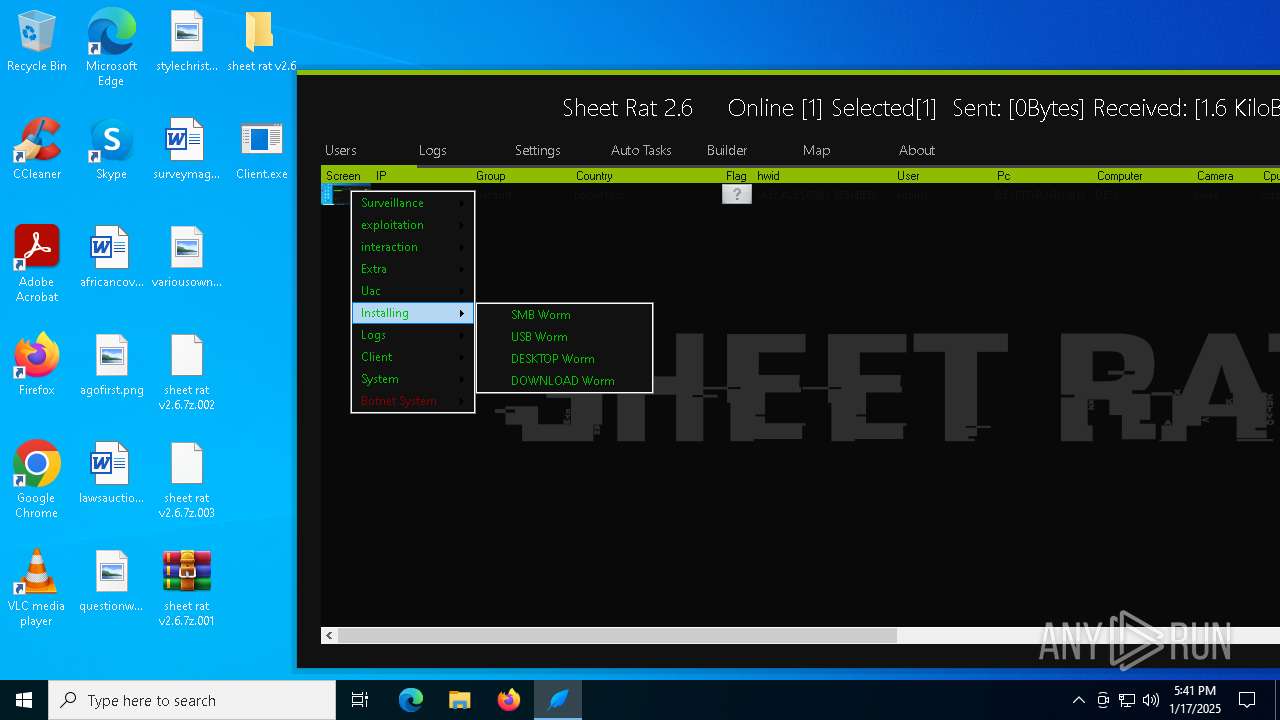
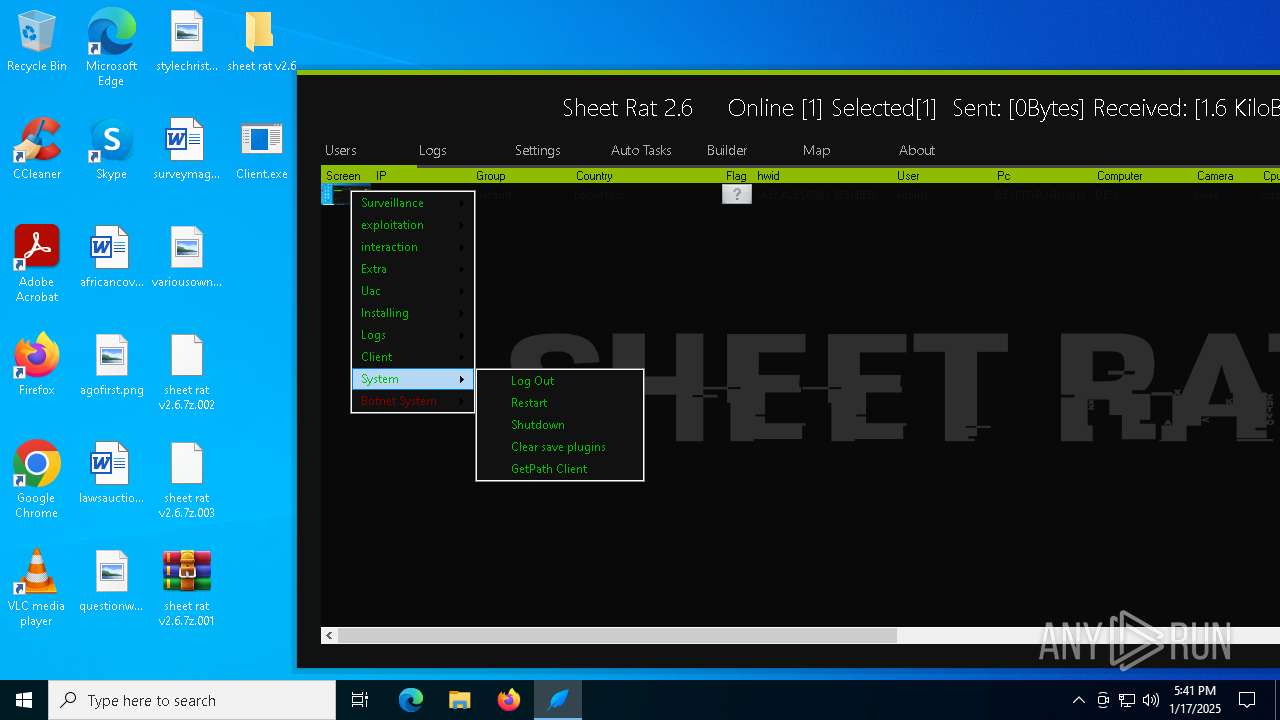
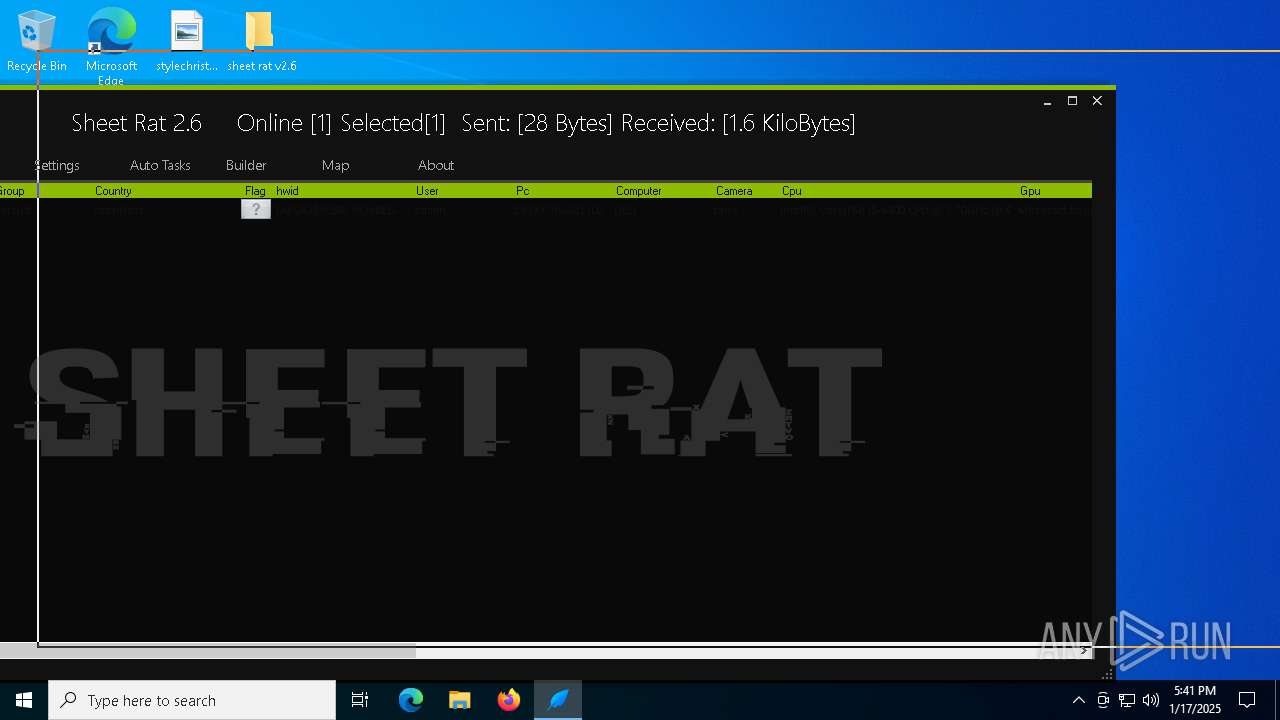
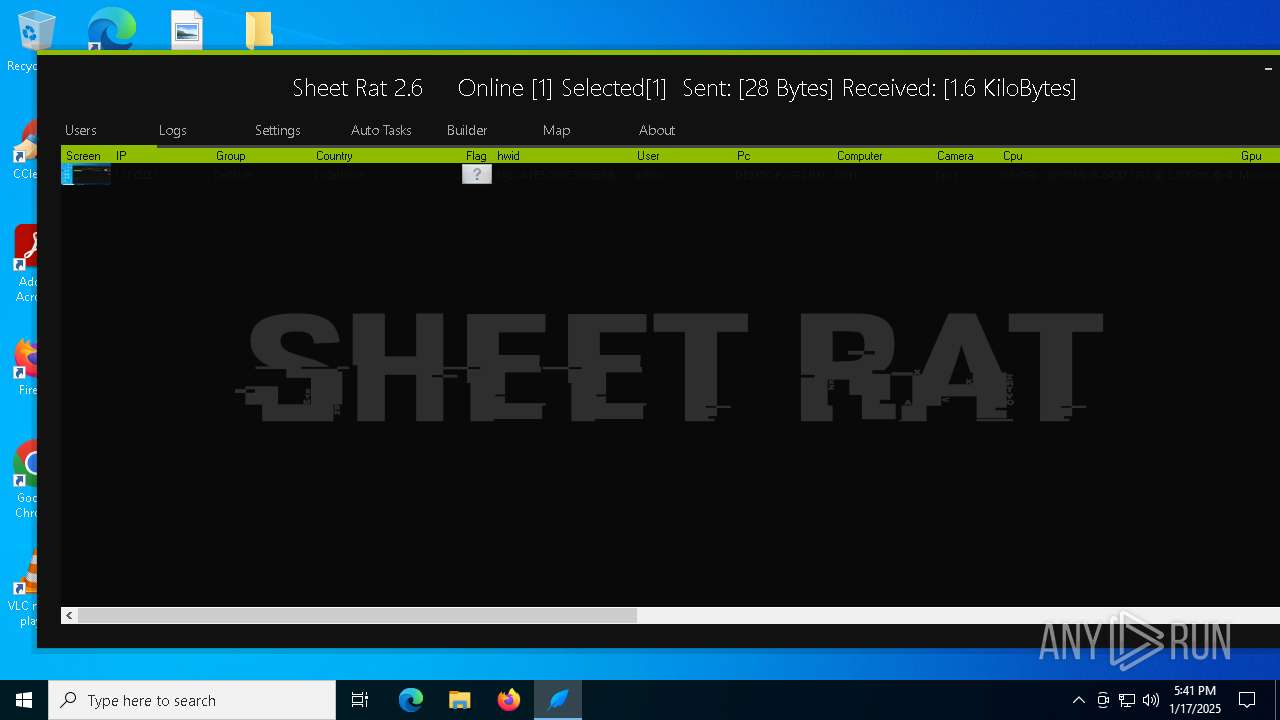
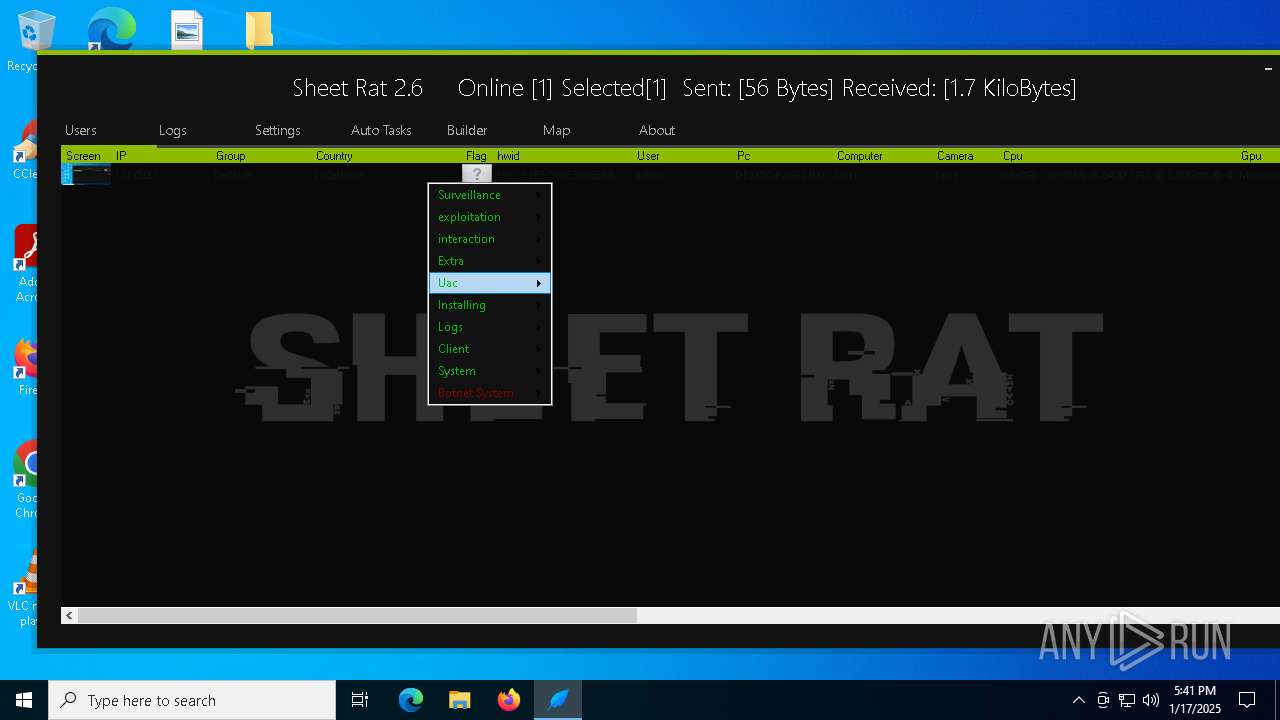
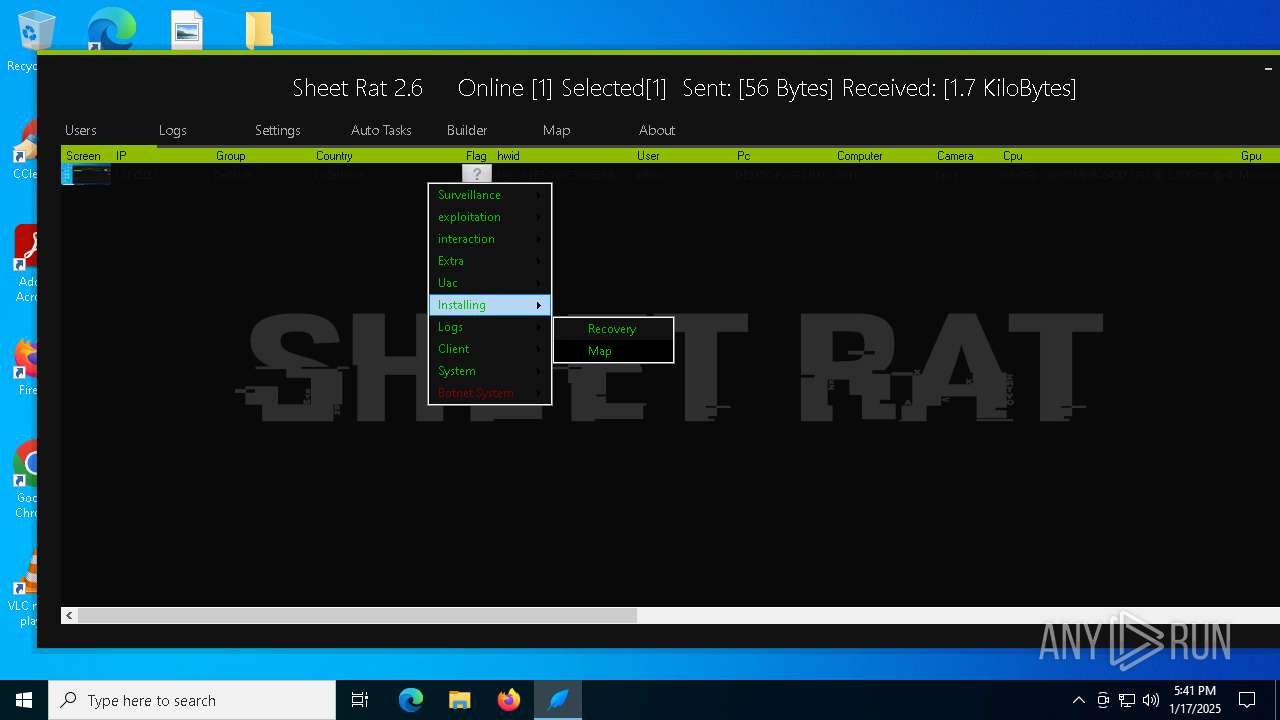
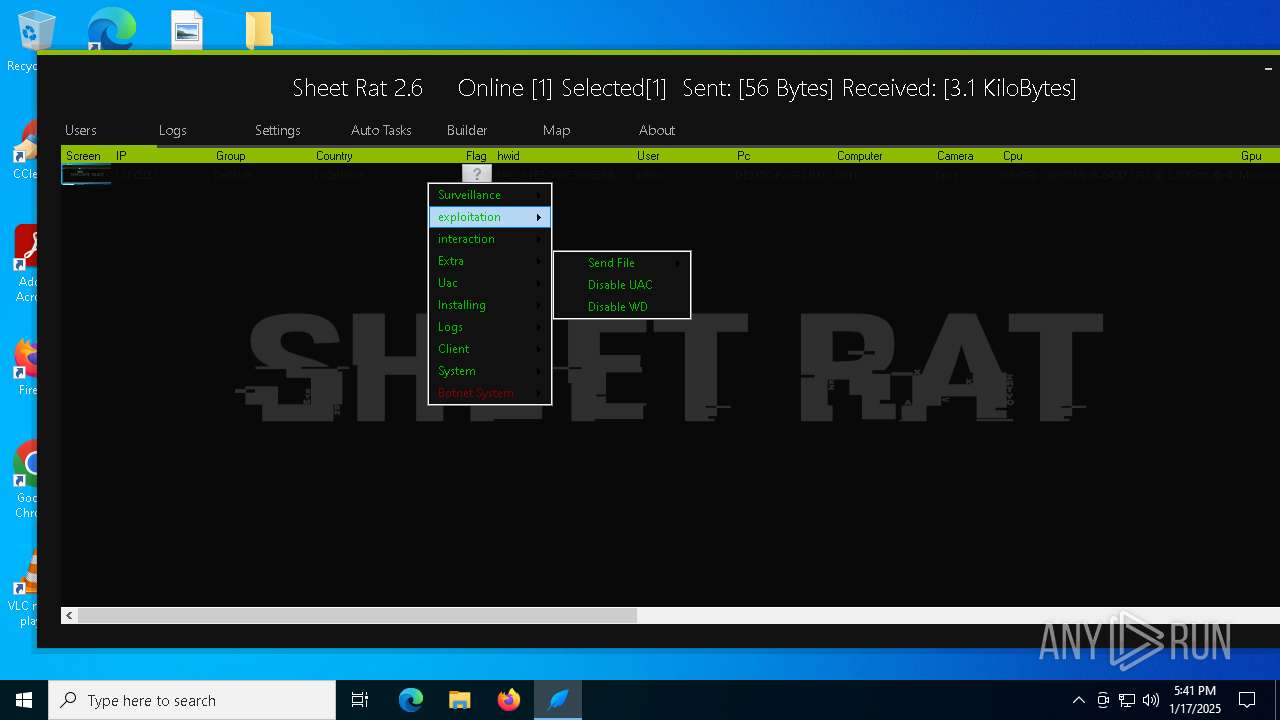
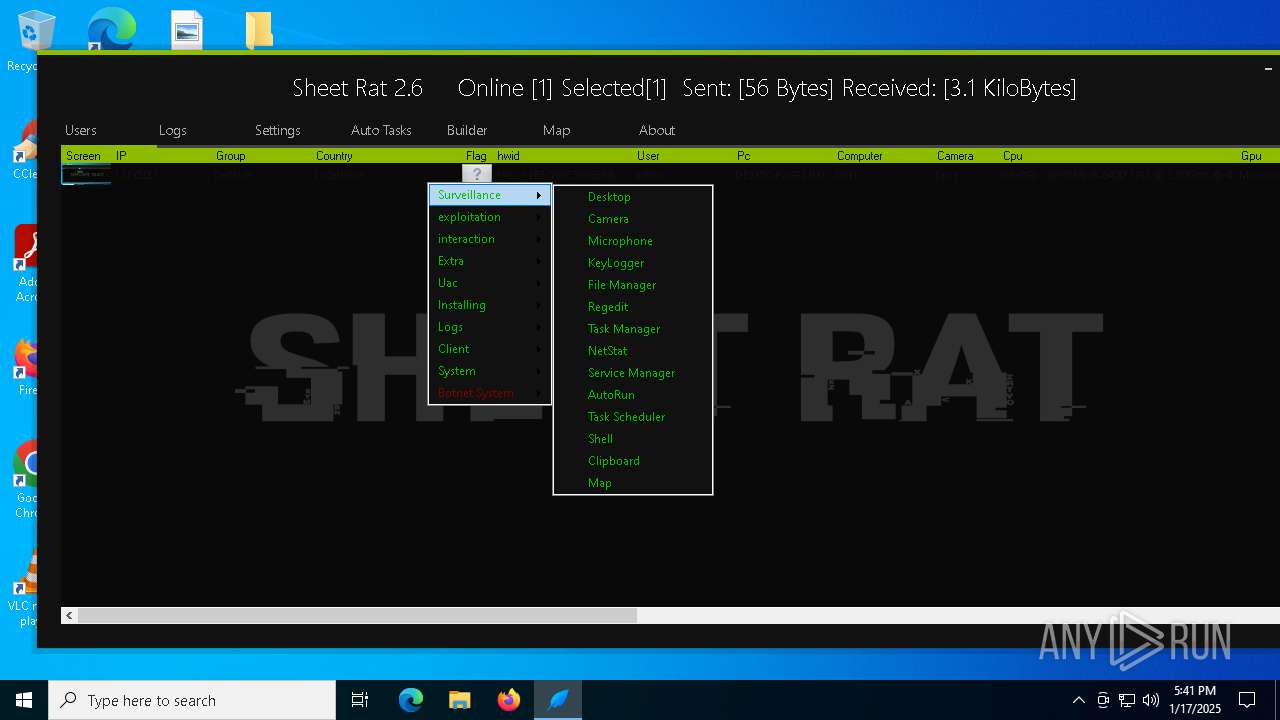
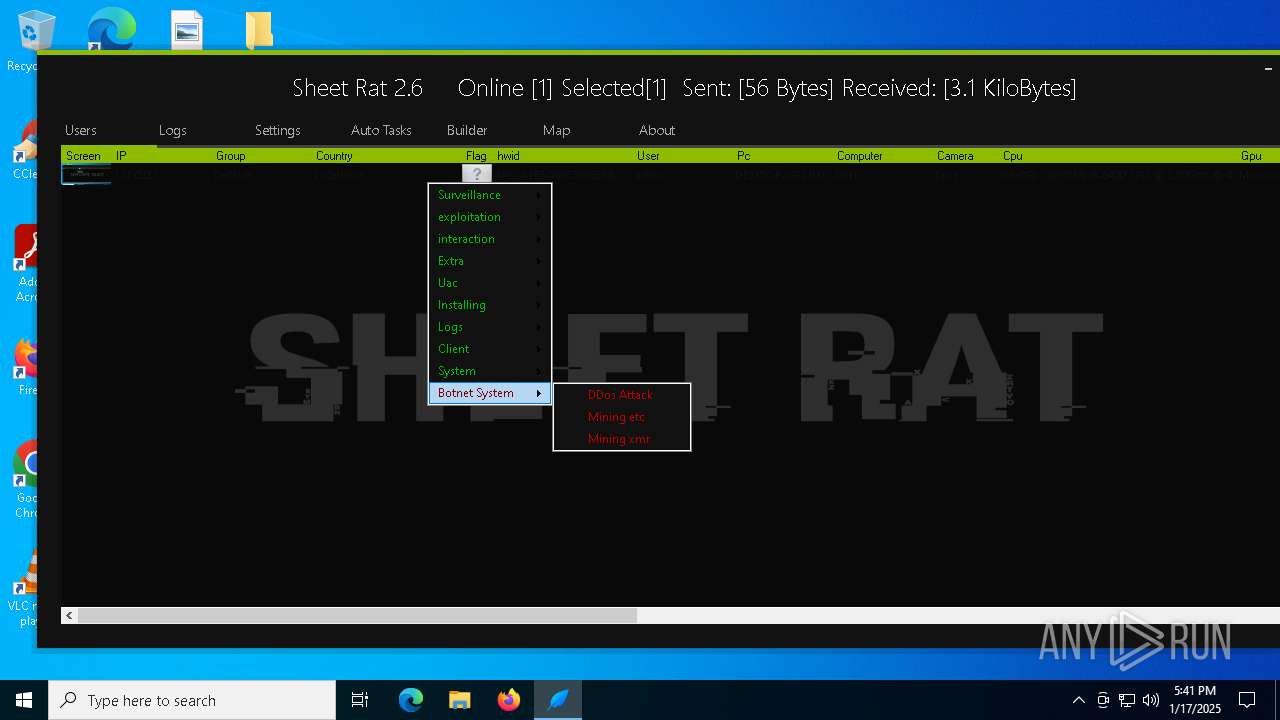
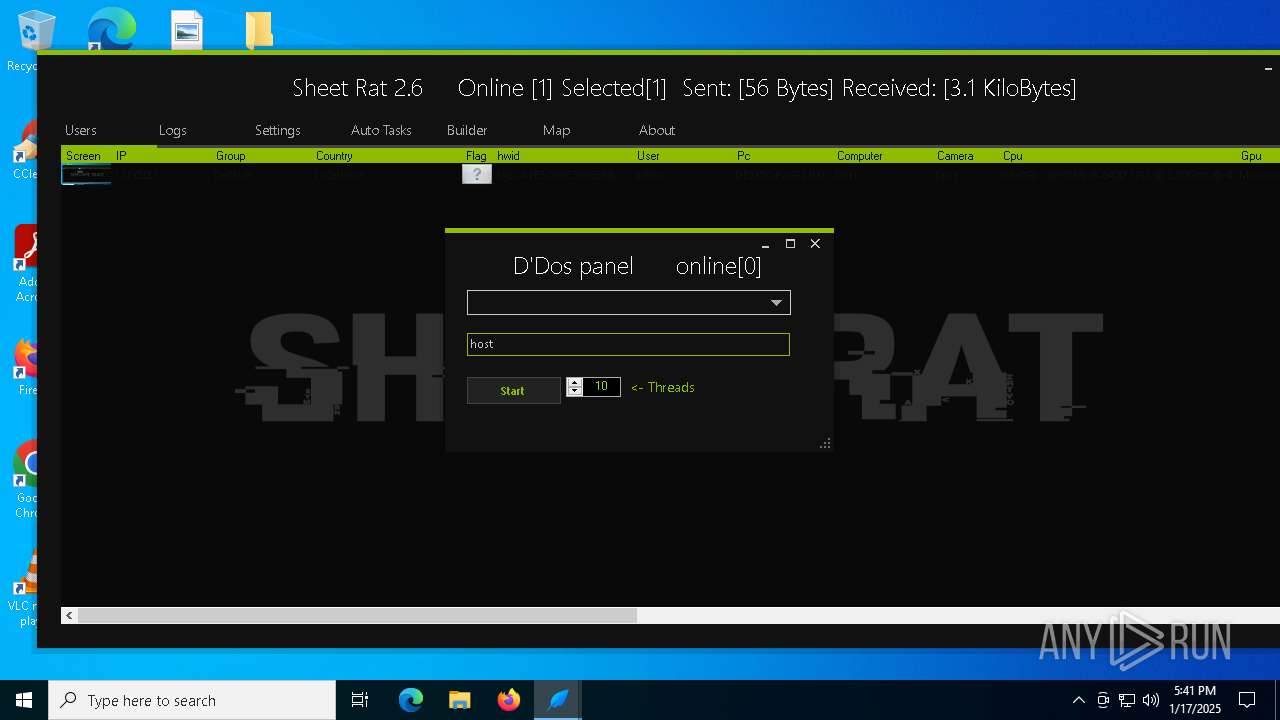
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | January 17, 2025, 17:38:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C0C323D32B96CF6B849529E28D014620 |
| SHA1: | 5B59C1AE04DCF73E0751B2E0A7F70EEA3FEA931B |
| SHA256: | 87F3F88F44E157807A9A269CC4AC828938CE146ACDD224C5713F706BA6E36082 |
| SSDEEP: | 98304:/vmLLUuVz+BZF7/Qtzowr0ghzbIv6CFvhnodBqIQukPcjn1SuoAu/l5vY9qo/oQN:cth8+YQDxrvlivPmMA |
MALICIOUS
SHEETRAT has been detected (YARA)
- Server.exe (PID: 3620)
XORed URL has been found (YARA)
- Server.exe (PID: 3620)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6032)
Reads security settings of Internet Explorer
- Server.exe (PID: 3620)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6032)
Executable content was dropped or overwritten
- Server.exe (PID: 3620)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6032)
The process checks if it is being run in the virtual environment
- Client.exe (PID: 6320)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6032)
Manual execution by a user
- WinRAR.exe (PID: 6032)
- Server.exe (PID: 3620)
- Client.exe (PID: 6320)
The sample compiled with japanese language support
- WinRAR.exe (PID: 6032)
The sample compiled with english language support
- WinRAR.exe (PID: 6032)
- Server.exe (PID: 3620)
SQLite executable
- Server.exe (PID: 3620)
Checks supported languages
- Server.exe (PID: 3620)
- Client.exe (PID: 6320)
Reads the machine GUID from the registry
- Server.exe (PID: 3620)
- Client.exe (PID: 6320)
Creates files or folders in the user directory
- Server.exe (PID: 3620)
Reads the computer name
- Client.exe (PID: 6320)
The process uses the downloaded file
- WinRAR.exe (PID: 6032)
- Server.exe (PID: 3620)
Disables trace logs
- Server.exe (PID: 3620)
Checks proxy server information
- Server.exe (PID: 3620)
Reads the software policy settings
- Server.exe (PID: 3620)
Sends debugging messages
- Server.exe (PID: 3620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(3620) Server.exe
Decrypted-URLs (1)http://marketdedamoroza.webhop.me/index.html
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
137
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3620 | "C:\Users\admin\Desktop\sheet rat v2.6\Server.exe" | C:\Users\admin\Desktop\sheet rat v2.6\Server.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Sheet Rat Exit code: 0 Version: 1.0.0.0 Modules
xor-url(PID) Process(3620) Server.exe Decrypted-URLs (1)http://marketdedamoroza.webhop.me/index.html | |||||||||||||||
| 4392 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\sheet rat v2.6.7z.001.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4840 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\sheet rat v2.6.7z.001" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6320 | "C:\Users\admin\Desktop\Client.exe" | C:\Users\admin\Desktop\Client.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Client Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
10 874
Read events
10 742
Write events
129
Delete events
3
Modification events
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\sheet rat v2.6.7z.001.7z | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0A01000054000000CA04000017020000 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
64
Suspicious files
19
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\Maps.json | text | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\MetroFramework.Fonts.dll | executable | |
MD5:65EF4B23060128743CEF937A43B82AA3 | SHA256:C843869AACA5135C2D47296985F35C71CA8AF4431288D04D481C4E46CC93EE26 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\IconExtractor.dll | executable | |
MD5:640D8FFA779C6DD5252A262E440C66C0 | SHA256:440912D85D2F98BB4F508AB82847067C18E1E15BE0D8ECDCFF0CC19327527FC2 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\NAudio.dll | executable | |
MD5:2E68AEB46E26A29FFE74CF97B94CBAF0 | SHA256:8E347ABC9301D67DD7493A0FBBE5CC1F912900C204A84220CC8CDF0E0B8DF0DE | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\dnlib.dll | executable | |
MD5:508CCDE8BC7003696F32AF7054CA3D97 | SHA256:4758C7C39522E17BF93B3993ADA4A1F7DD42BB63331BAC0DCD729885E1BA062A | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\Plugins\AutoRun.dll | executable | |
MD5:2D1298818AA582A1F1DD51DEDF879CBF | SHA256:F8C4E2F96FE1030A276CD7FB6C5E5A0A675F953F2B33DB08FDFF3D472658D098 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\Themes.json | binary | |
MD5:FDF6D963491B41D9BA798F60FE27EF8C | SHA256:BFE1437218DD94CCD078A8683F59B65E28D8D63DEFA7F419B2CEF81BC031A7BF | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.37006\sheet rat v2.6\Server.exe.config | xml | |
MD5:2083876EC03AD06E5C16490FCB4AB8B6 | SHA256:28026DE2C65972CB8FAC1FF2865C33E24D1086F7242B2FE951CEF172909AD128 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
43
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1540 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1540 | RUXIMICS.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7096 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7096 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6648 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3620 | Server.exe | GET | 200 | 142.250.185.78:80 | http://mt2.google.com/maps/vt/lyrs=m@333000000&hl=en&x=2&y=2&z=2&s= | unknown | — | — | whitelisted |
3620 | Server.exe | GET | 200 | 142.250.185.78:80 | http://mt3.google.com/maps/vt/lyrs=m@333000000&hl=en&x=3&y=2&z=2&s=Gal | unknown | — | — | whitelisted |
3620 | Server.exe | GET | 200 | 142.250.185.78:80 | http://mt0.google.com/maps/vt/lyrs=m@333000000&hl=en&x=2&y=1&z=2&s=Galileo | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
3996 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
1540 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1540 | RUXIMICS.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1540 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
5064 | SearchApp.exe | 92.123.104.26:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| unknown |
settings-win.data.microsoft.com |
| unknown |
crl.microsoft.com |
| unknown |
www.microsoft.com |
| unknown |
www.bing.com |
| unknown |
login.live.com |
| unknown |
ocsp.digicert.com |
| unknown |
go.microsoft.com |
| unknown |
slscr.update.microsoft.com |
| unknown |
fe3cr.delivery.mp.microsoft.com |
| unknown |
Threats
Process | Message |
|---|---|
Server.exe | SQLiteVersion: 3.8.11.1 | 2015-07-29 20:00:57 cf538e2783e468bbc25e7cb2a9ee64d3e0e80b2f | INTEROP_CODEC INTEROP_EXTENSION_FUNCTIONS INTEROP_VIRTUAL_TABLE NET_40 PRELOAD_NATIVE_LIBRARY THROW_ON_DISPOSED TRACE TRACE_PRELOAD TRACE_SHARED TRACE_WARNING USE_PREPARE_V2 WINDOWS
|