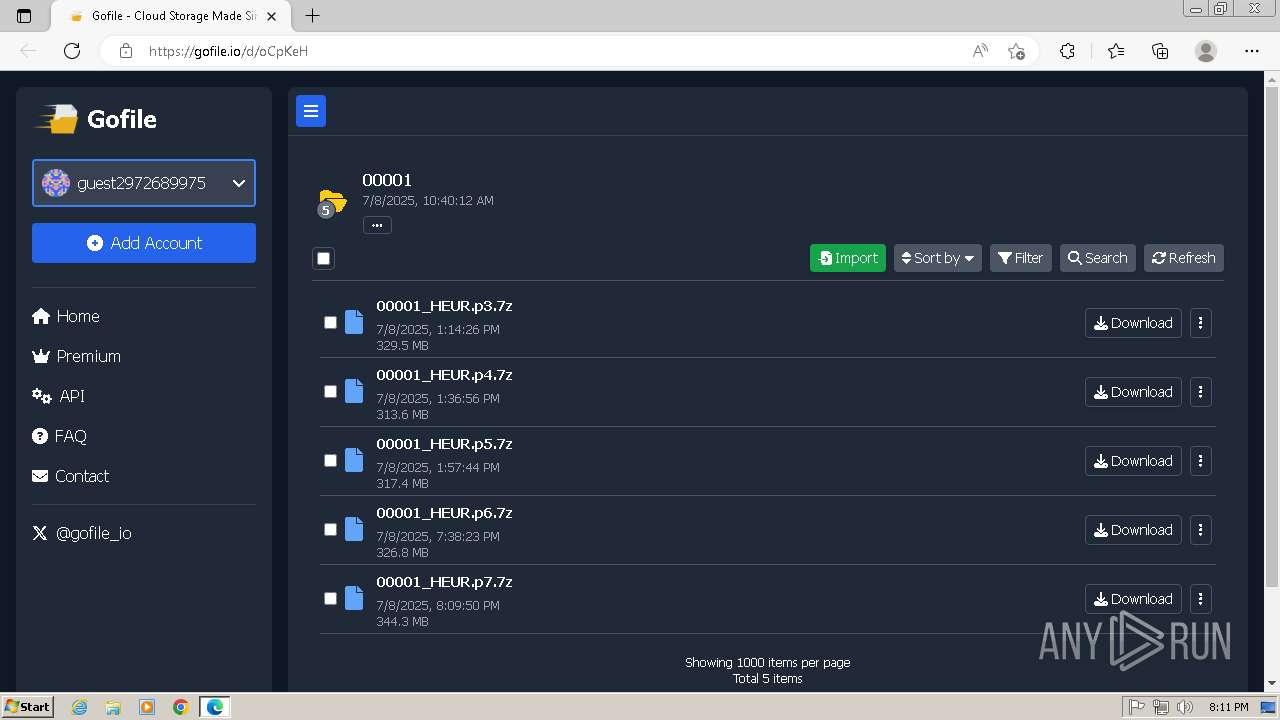
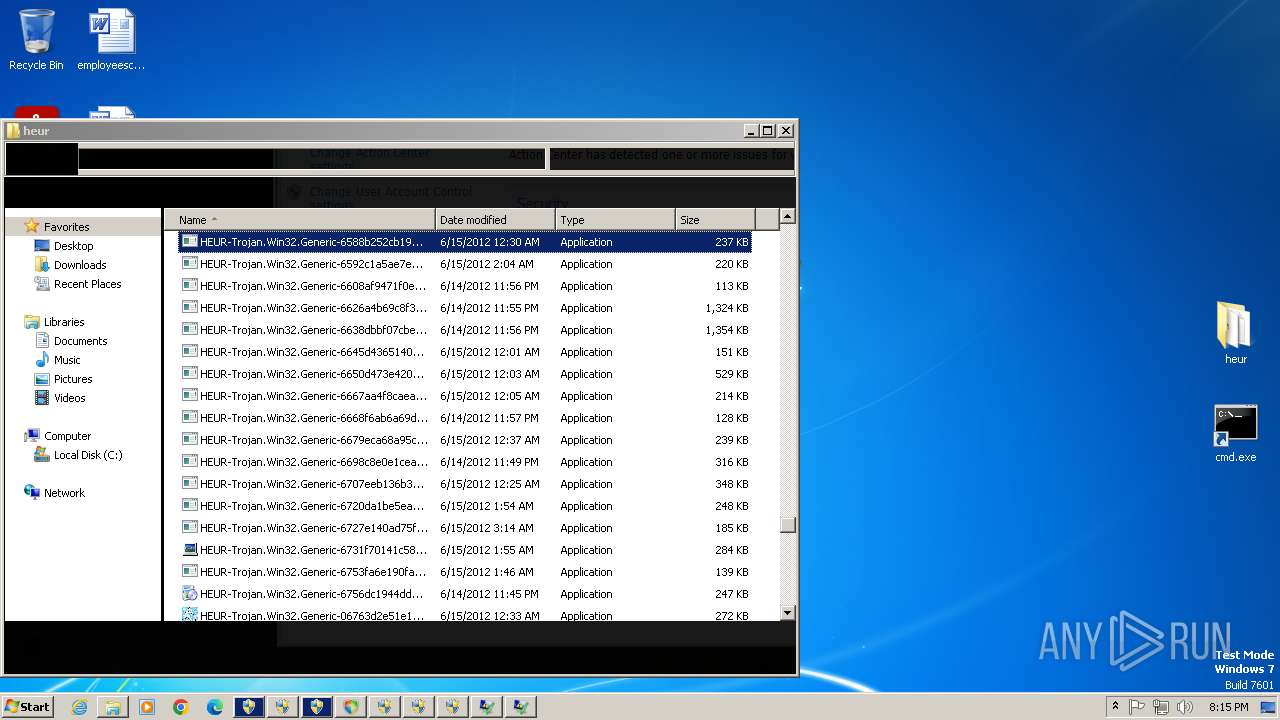
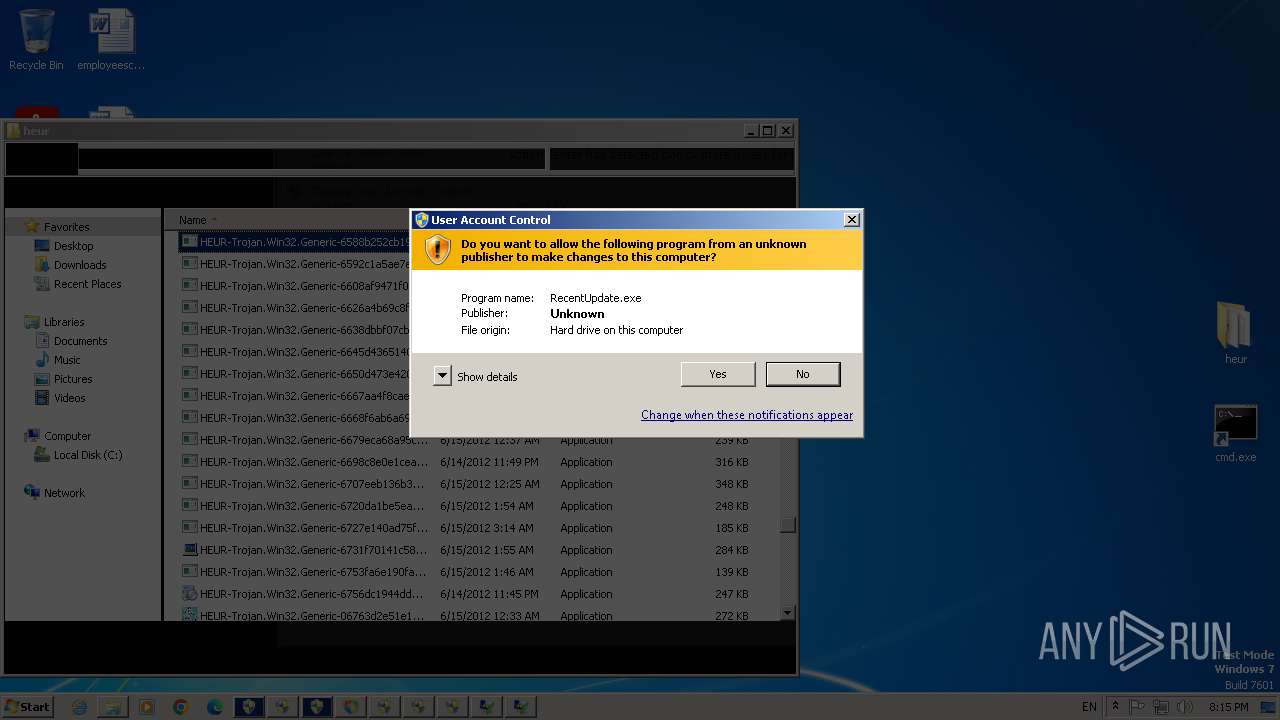
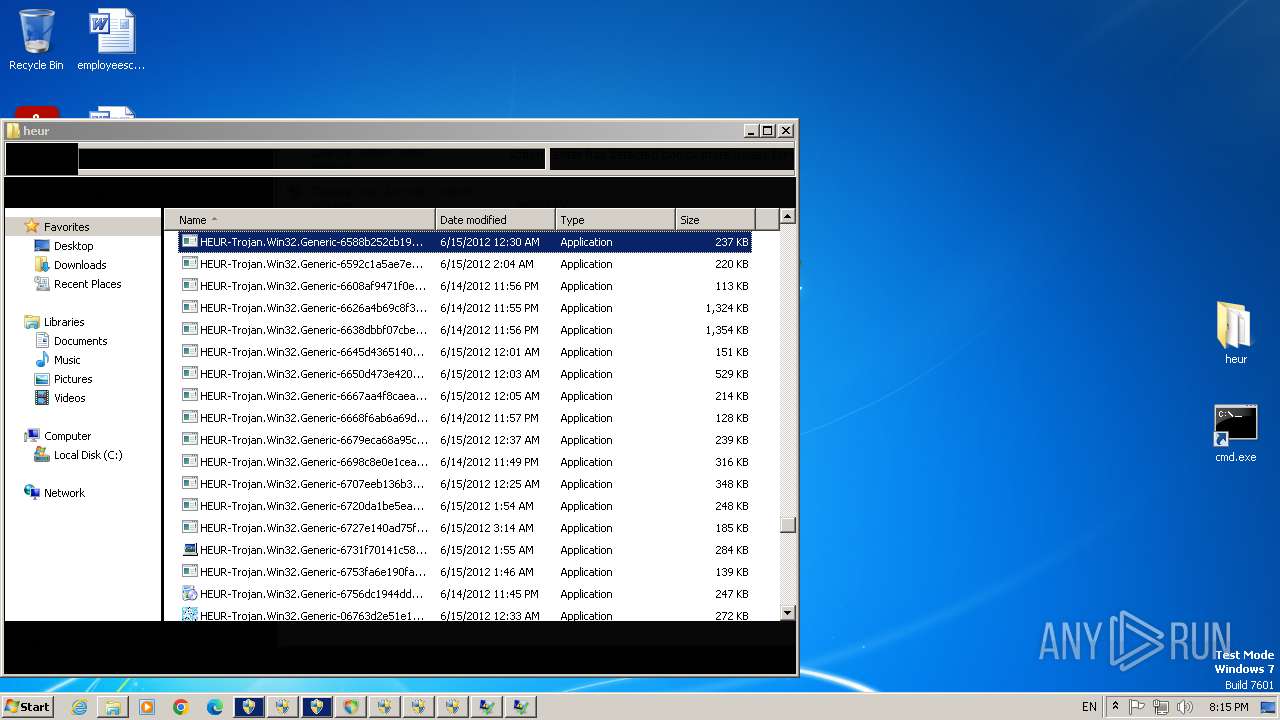
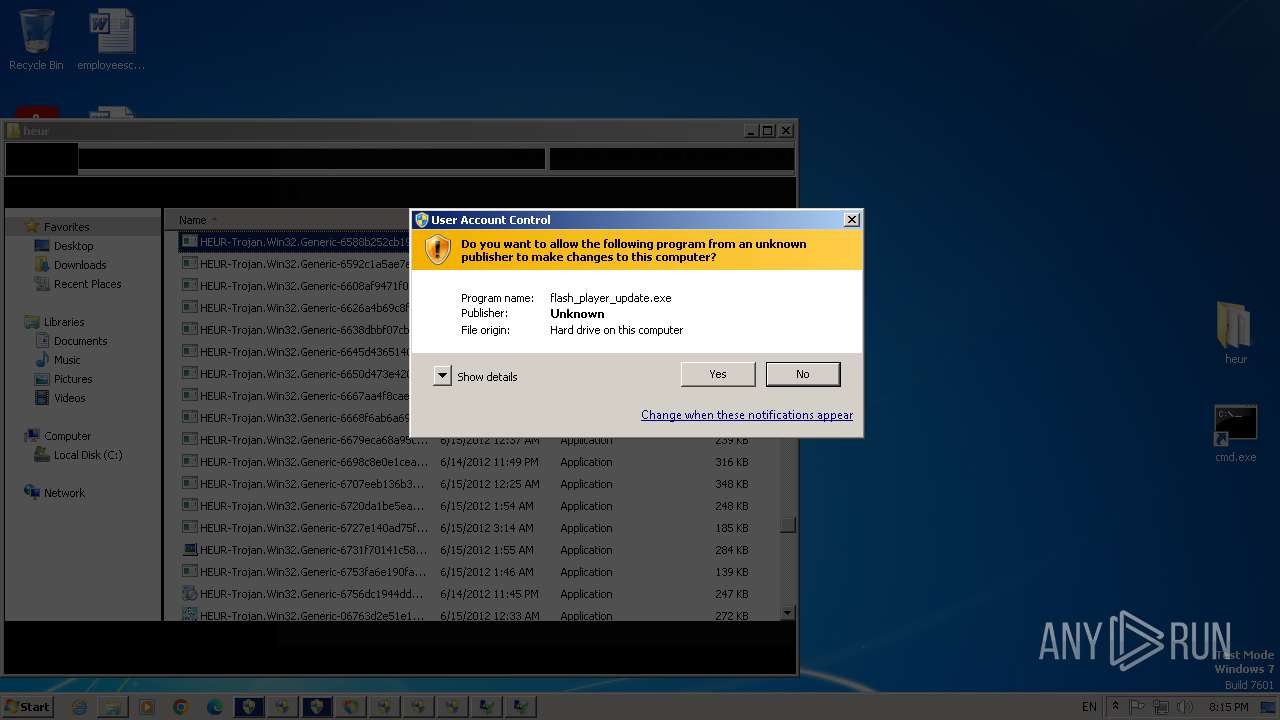
| URL: | https://gofile.io/d/oCpKeH |
| Full analysis: | https://app.any.run/tasks/fdfea30c-458f-40cf-8812-516a3b699176 |
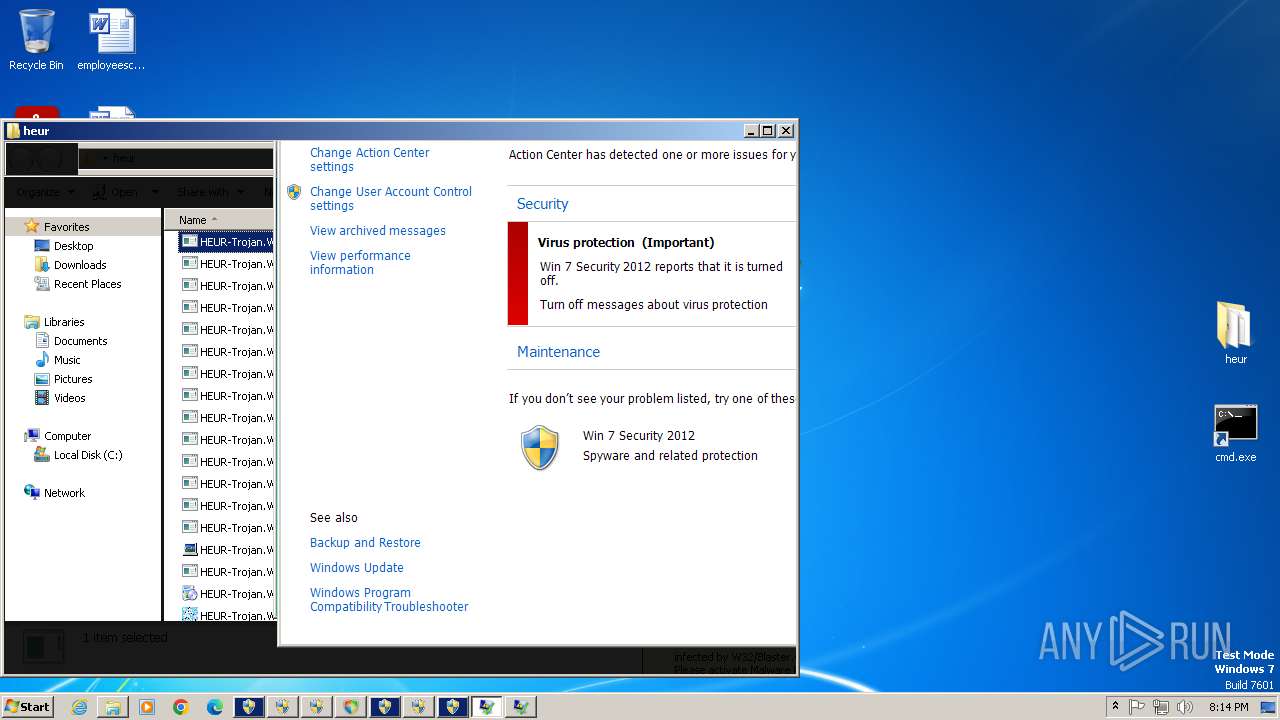
| Verdict: | Malicious activity |
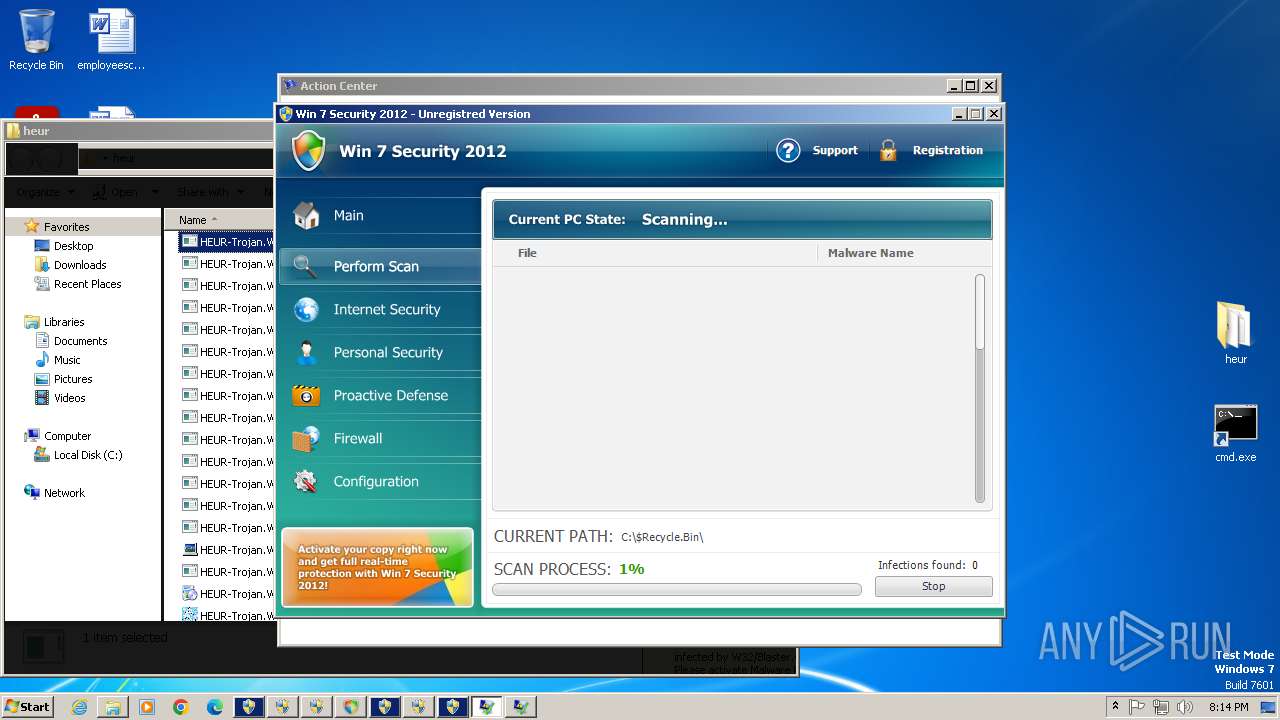
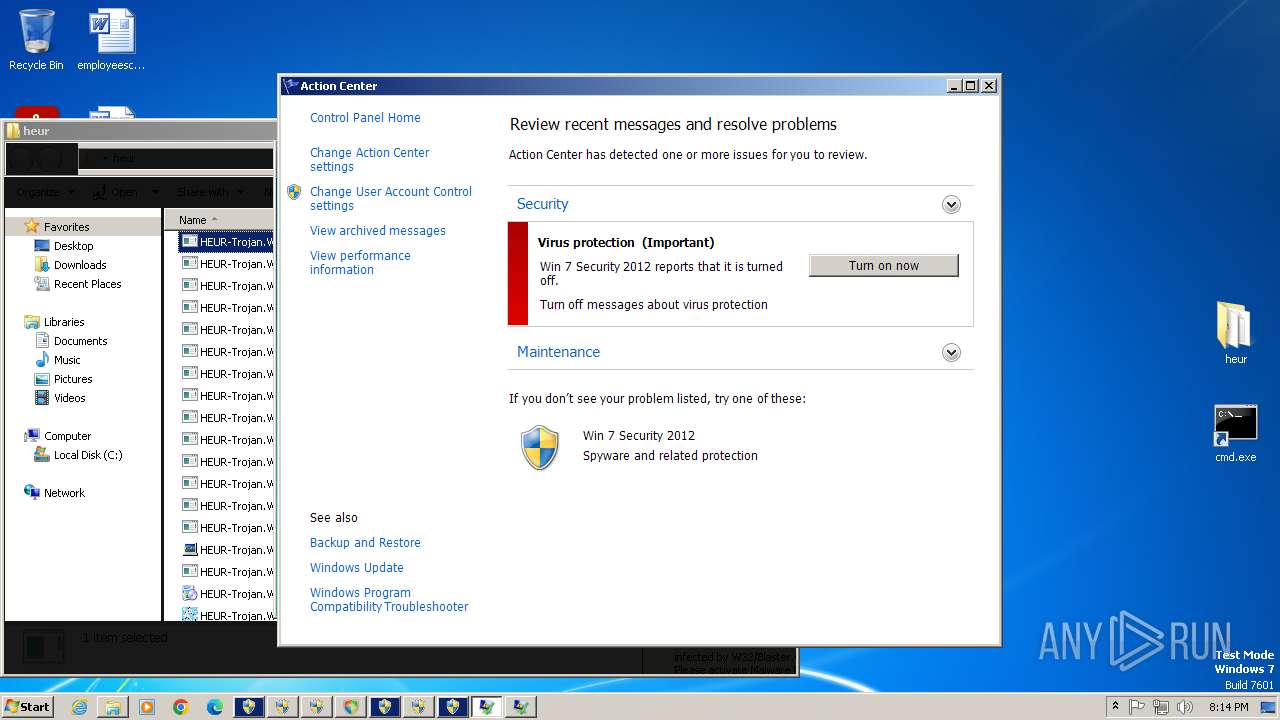
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | July 08, 2025, 19:11:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MD5: | EEFEB339808EE82B6F14CFE8EE8295EF |
| SHA1: | 30337FCF74C145D4CADC9D0ECBCBAA7332C0A587 |
| SHA256: | 87AF714936A2543A83049EDCA85E61F5910CA2D2C3B5615E7A302399D2FA95BA |
| SSDEEP: | 3:N8rxL13Vn:2ZJV |
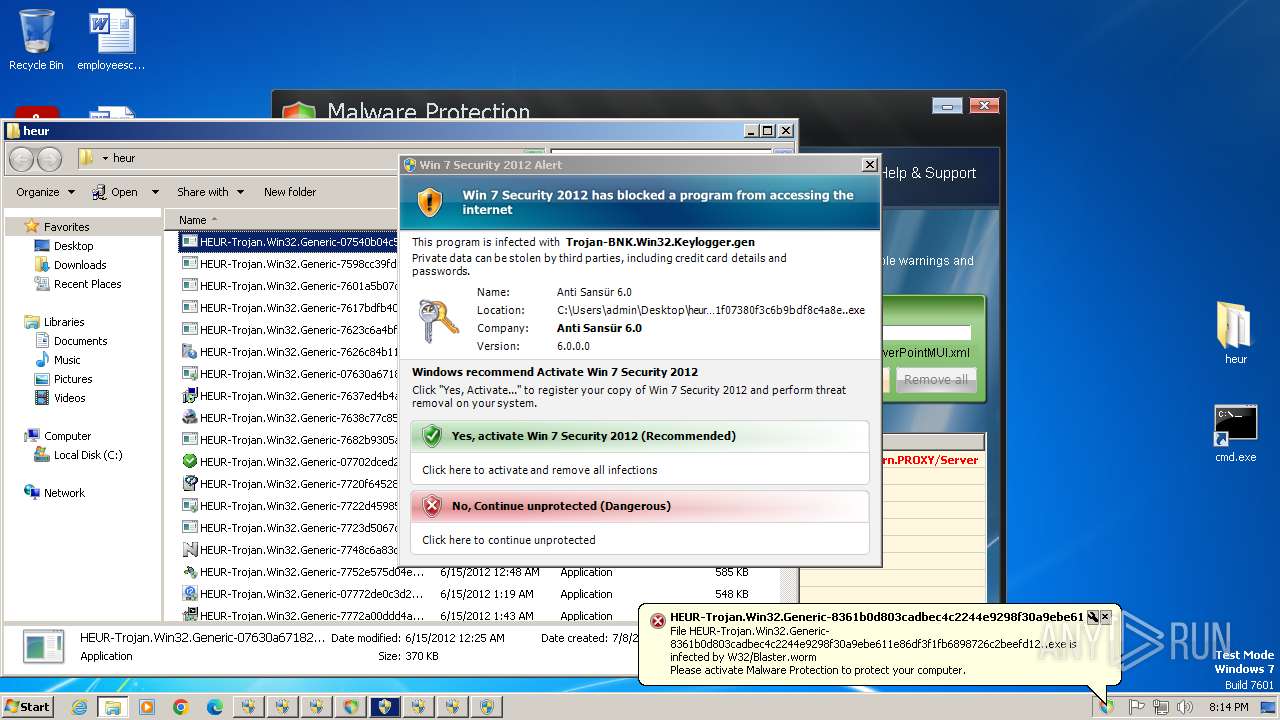
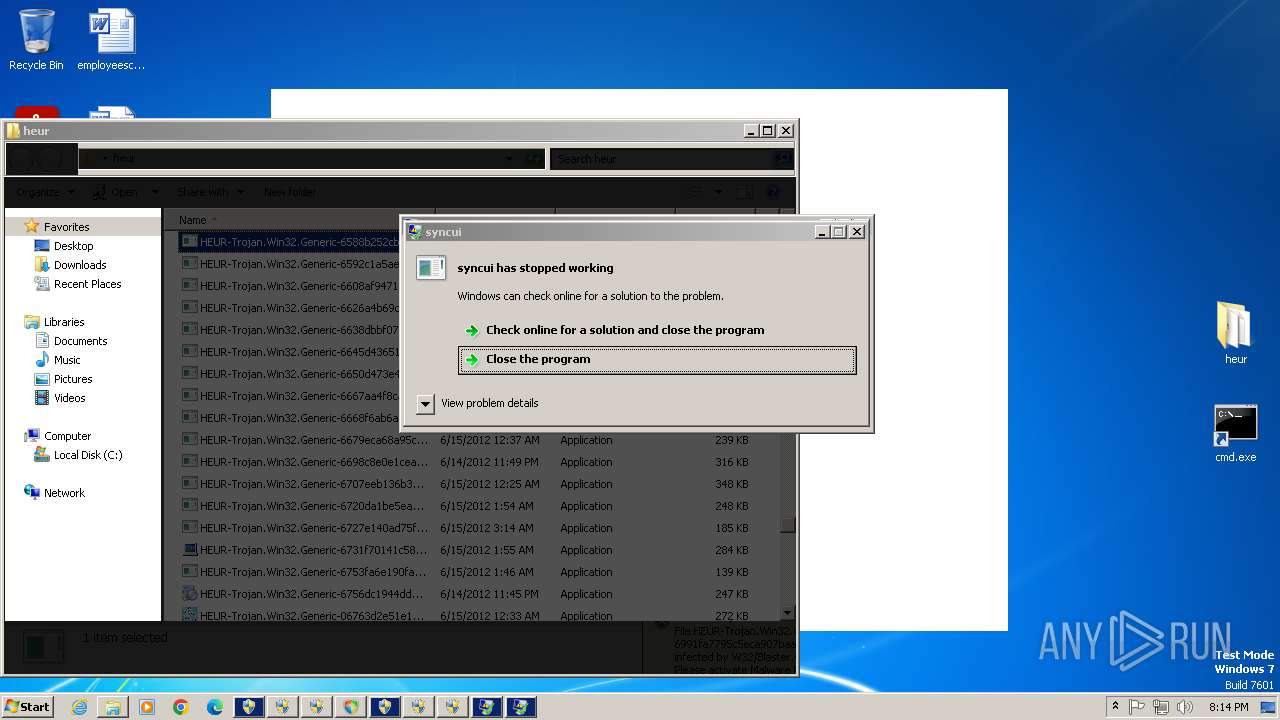
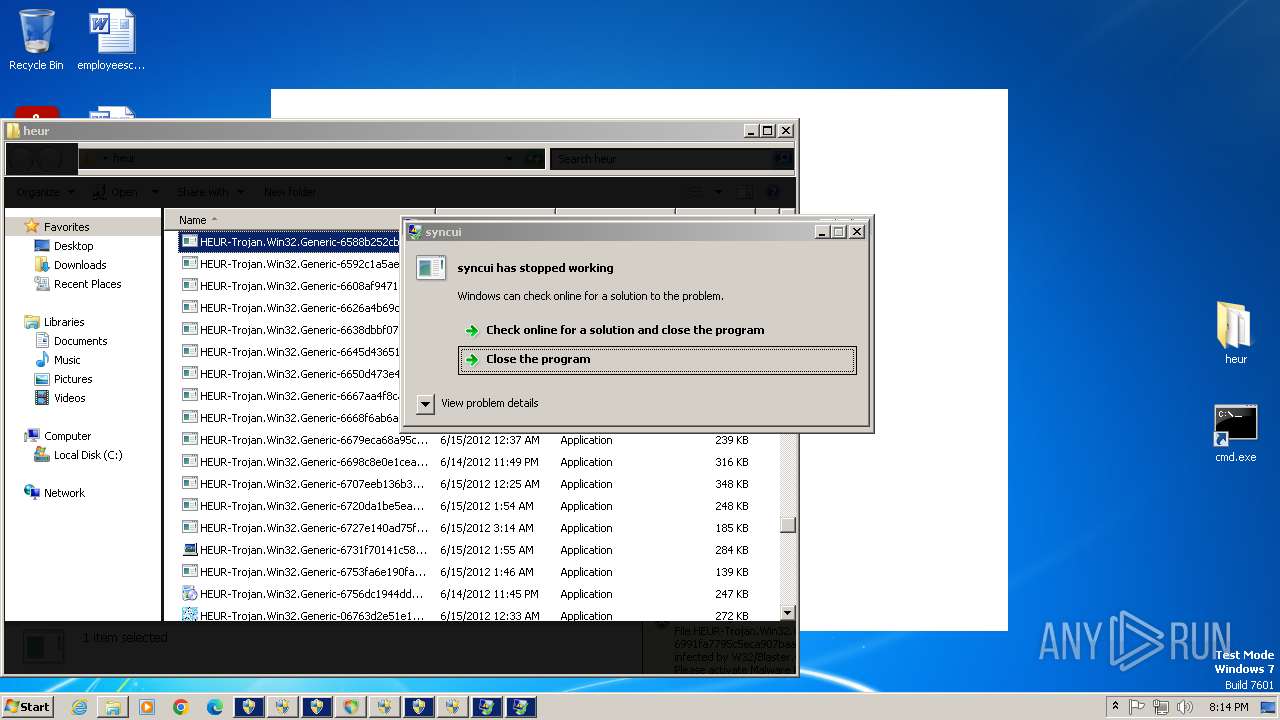
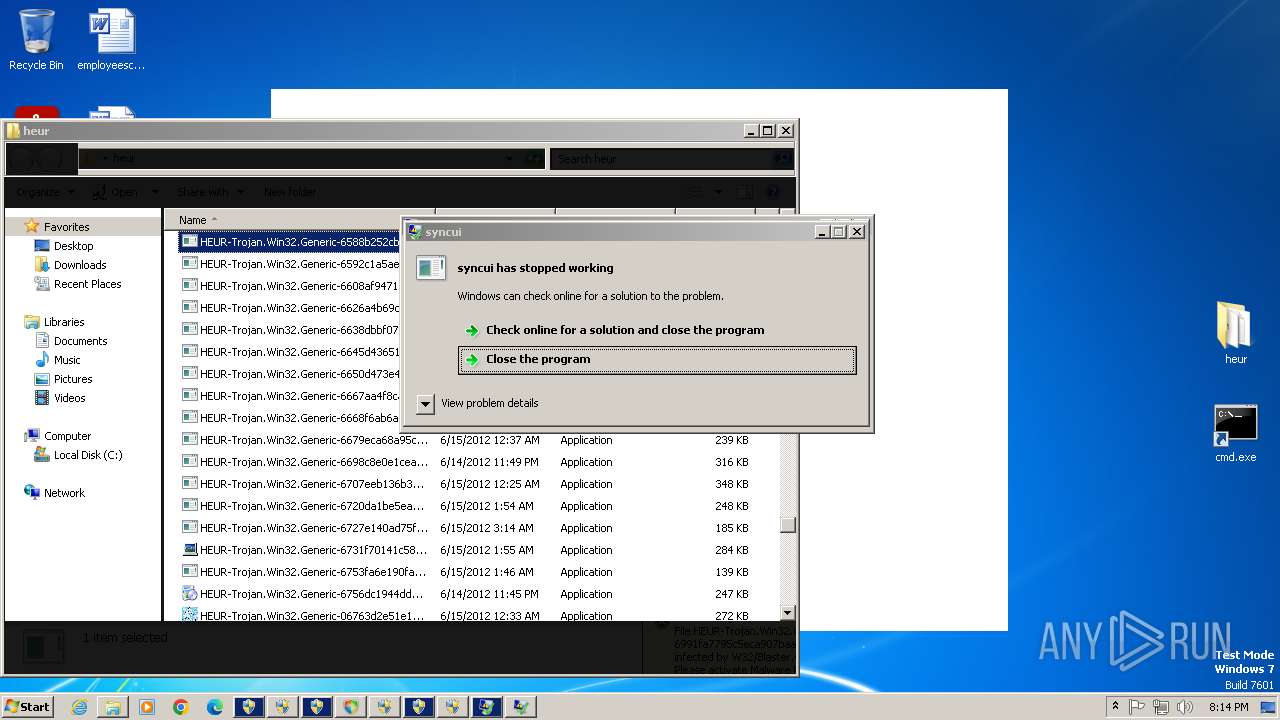
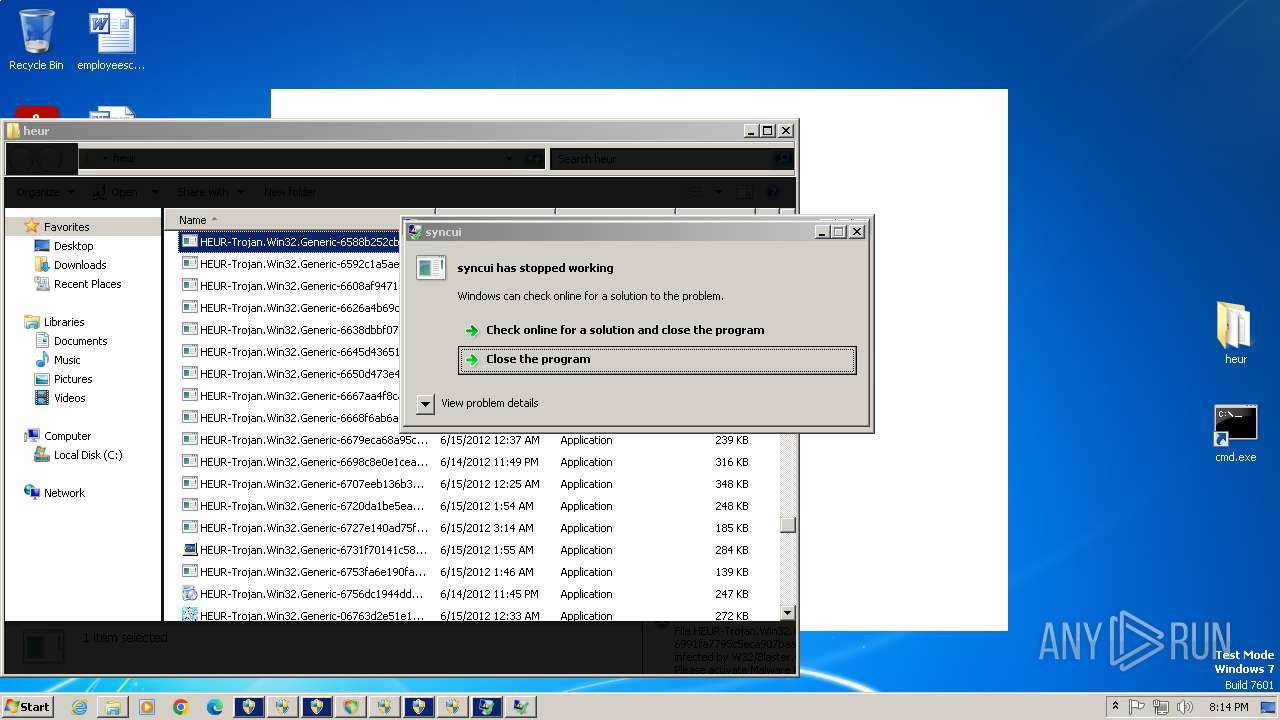
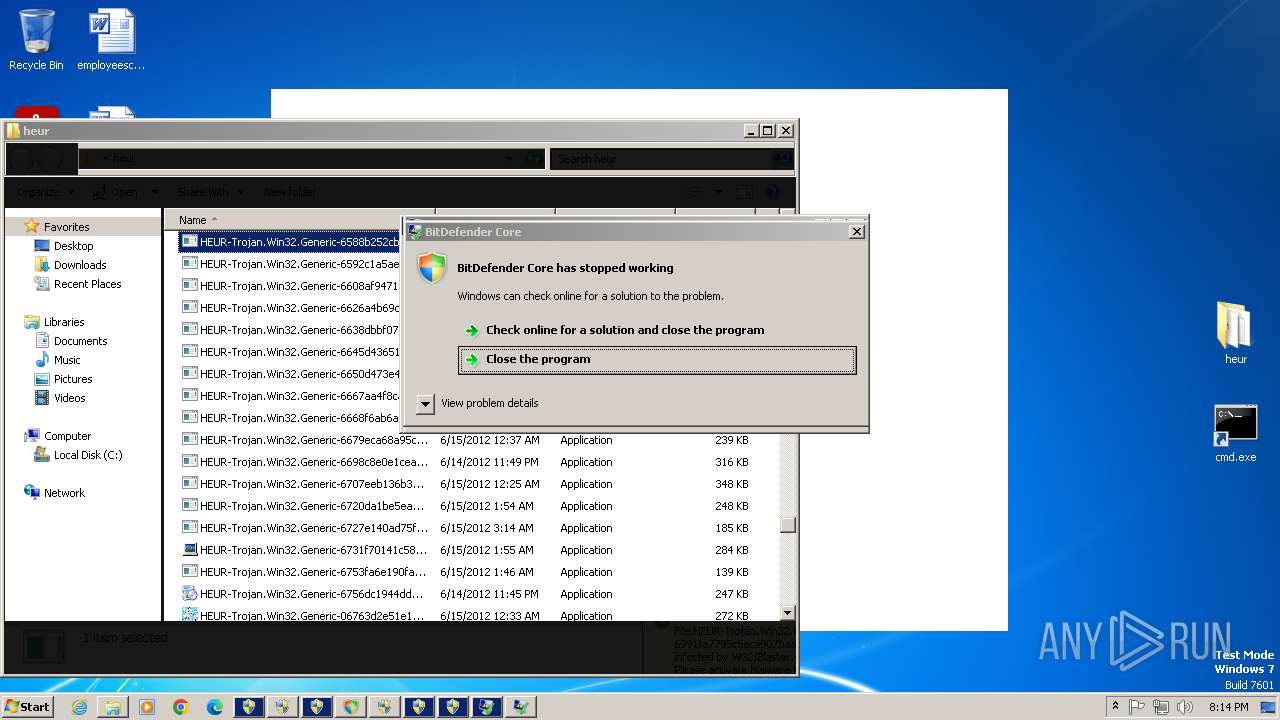
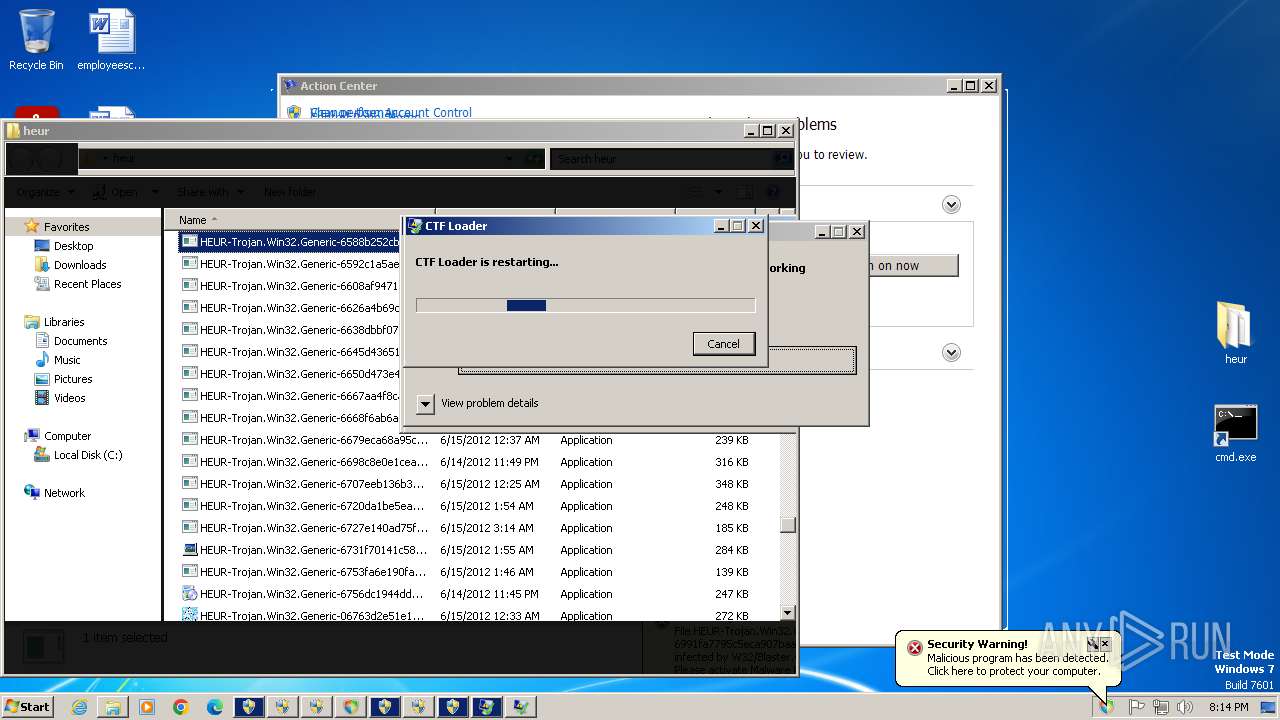
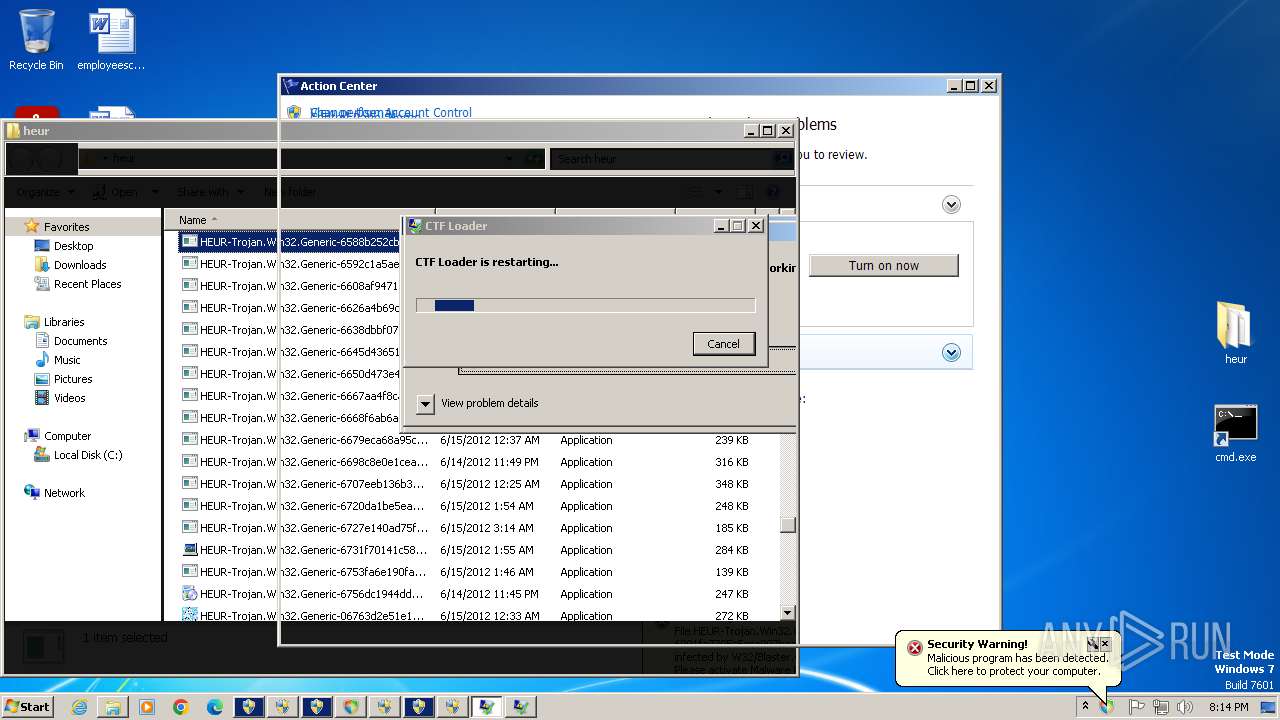
MALICIOUS
Changes the autorun value in the registry
- HEUR-Trojan.Win32.Generic-9280a1ecaff98076cfdd98083535a371148879b12a8c55463ec3bb62f98de0a1..exe (PID: 3772)
- svchost.exe (PID: 2796)
- HEUR-Trojan.Win32.Generic-9067c8411d9138a24167da423db123d337bf7889e0d7f91bc8b46e4987bc5a78..exe (PID: 3396)
- HEUR-Trojan.Win32.Generic-9085f8a76c559da7f3626b70e2de94b5142cd2c8630c9fbd654f73106b1f96c5..exe (PID: 672)
- nA41221ObIgM41221.exe (PID: 1372)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- defender.exe (PID: 2828)
- nA41221ObIgM41221.exe (PID: 3040)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- HEUR-Trojan.Win32.Generic-6931df583187624fd800d8c4348cbeeab8fa523c950a6bab39ca99e32db943a3..exe (PID: 1884)
- explorer.exe (PID: 1452)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
XTREME mutex has been found
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 3024)
- msedge.exe (PID: 1780)
- svchost.exe (PID: 2796)
- system.exe (PID: 1572)
- msedge.exe (PID: 1972)
- system.exe (PID: 284)
- system.exe (PID: 5124)
- msedge.exe (PID: 5920)
Changes the login/logoff helper path in the registry
- svchost.exe (PID: 556)
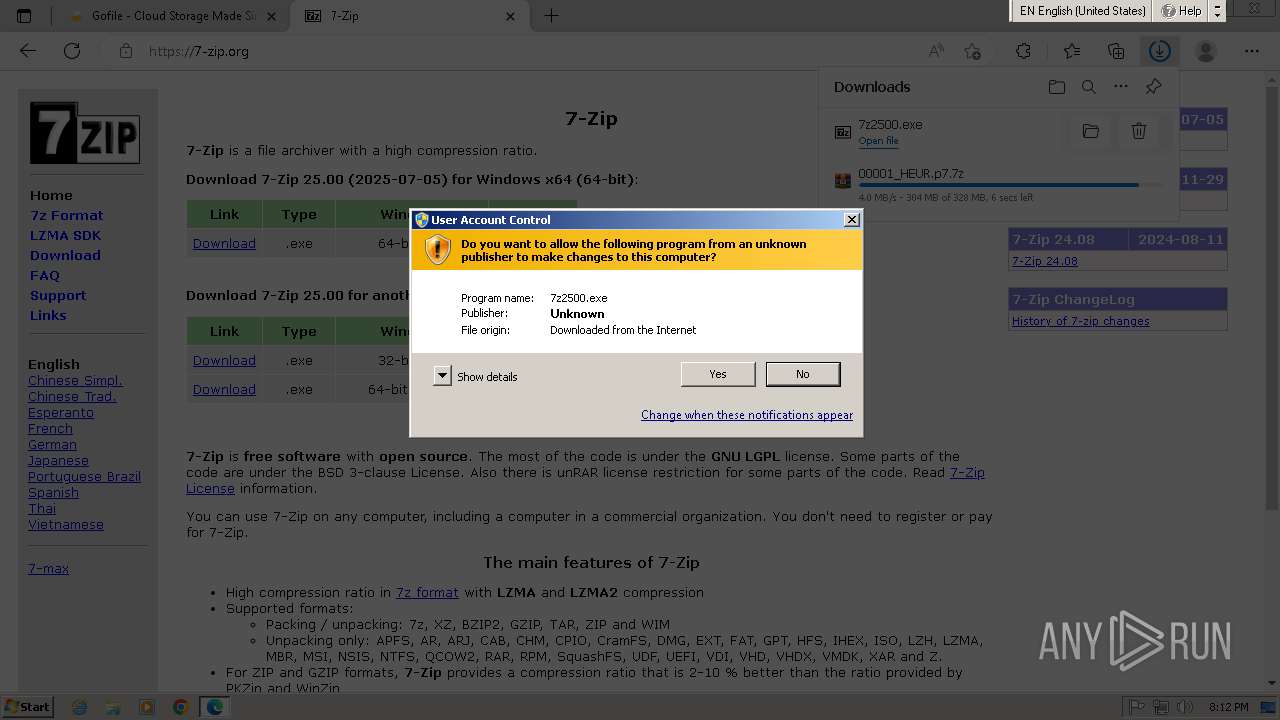
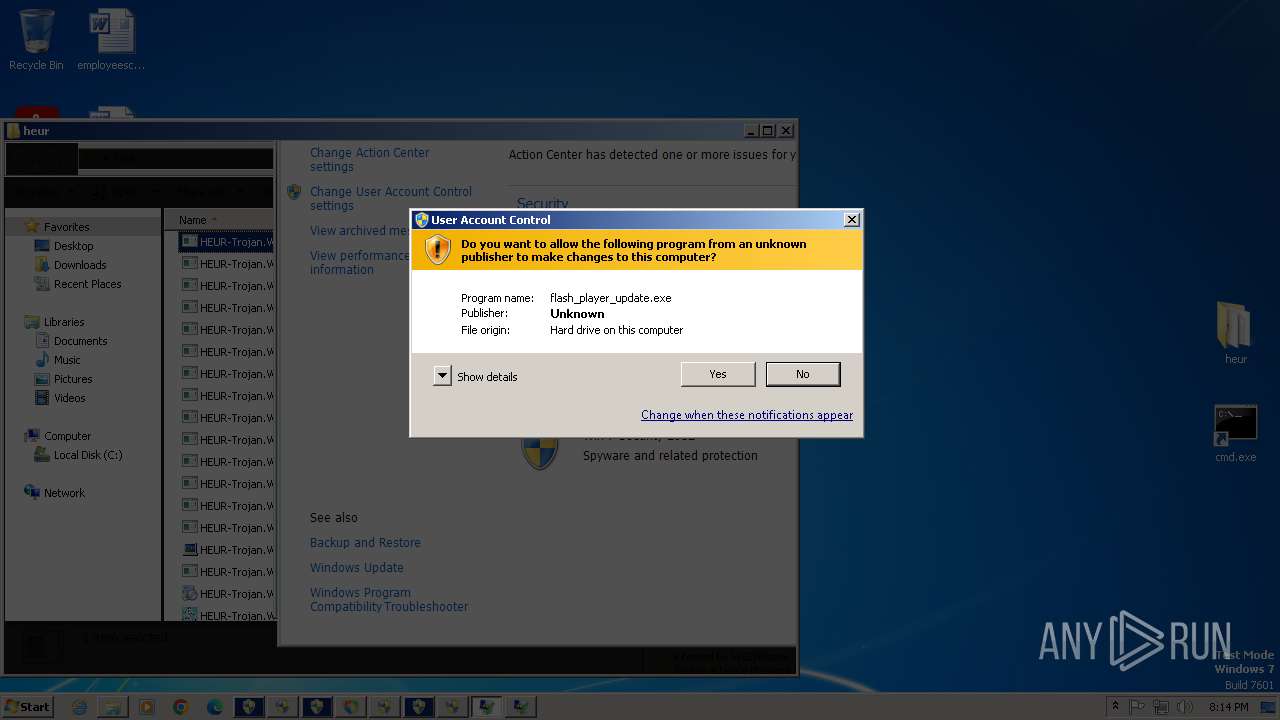
Executing a file with an untrusted certificate
- vbc.exe (PID: 1028)
- vbc.exe (PID: 3124)
- HEUR-Trojan.Win32.Generic-6991fa7795c5eca907baa44cdb93162fe35c0f1628bdb56822517e71877e0bf9..exe (PID: 3500)
DARKCOMET mutex has been found
- vbc.exe (PID: 1028)
Actions looks like stealing of personal data
- HEUR-Trojan.Win32.Generic-8840f33e1015f6545a747c2917f86af96898ff9ee9f19f1719e573ed8876e4f0..exe (PID: 1924)
Steals credentials from Web Browsers
- HEUR-Trojan.Win32.Generic-8840f33e1015f6545a747c2917f86af96898ff9ee9f19f1719e573ed8876e4f0..exe (PID: 1924)
PKYBOT mutex has been found
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2440)
Connects to the CnC server
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- explorer.exe (PID: 1452)
CYBERGATE mutex has been found
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
- explorer.exe (PID: 1452)
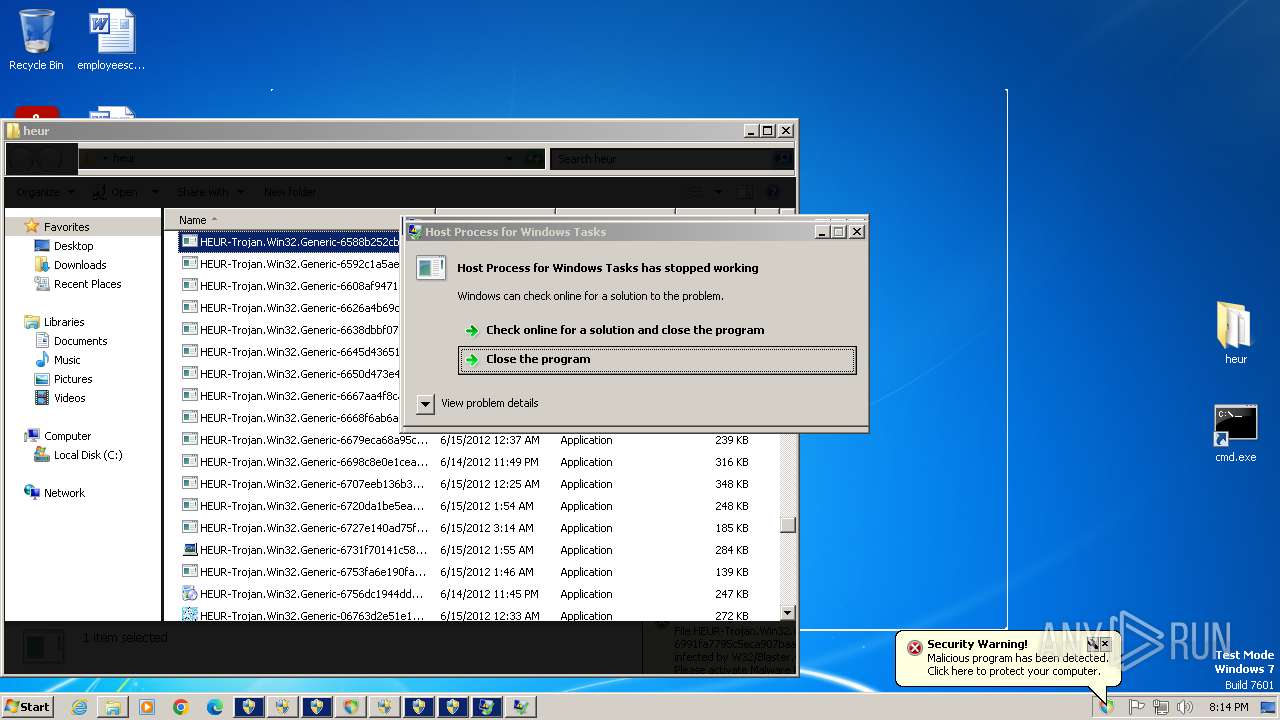
Application was injected by another process
- dllhost.exe (PID: 2800)
- taskeng.exe (PID: 292)
- ctfmon.exe (PID: 1356)
- dwm.exe (PID: 664)
- dllhost.exe (PID: 4916)
- WerFault.exe (PID: 4248)
- WerFault.exe (PID: 5204)
SPYEYE has been detected (SURICATA)
- explorer.exe (PID: 1452)
Runs injected code in another process
- HEUR-Trojan.Win32.Generic-6963f86855ac1cfd80e79b19c06ab713aa92518fc122b06eb50c5ea537d3e18b..exe (PID: 3740)
XORed URL has been found (YARA)
- defender.exe (PID: 2828)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
CYBERGATE has been detected (YARA)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
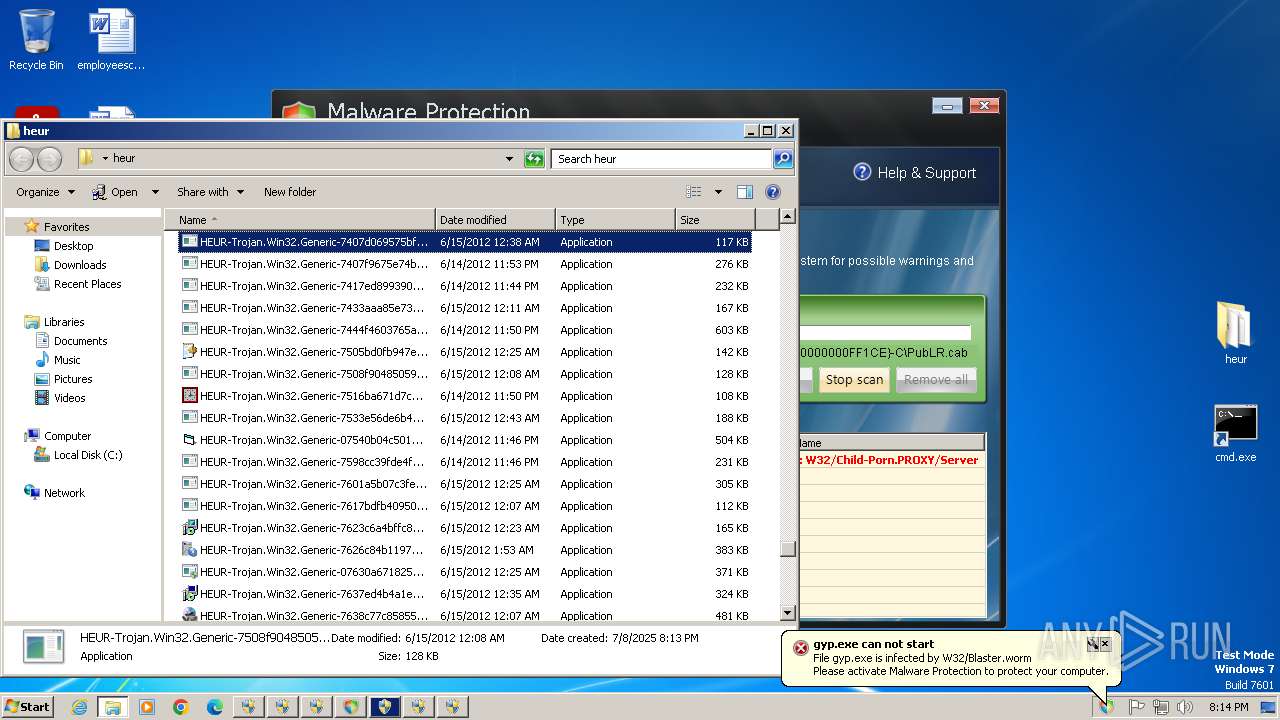
SUSPICIOUS
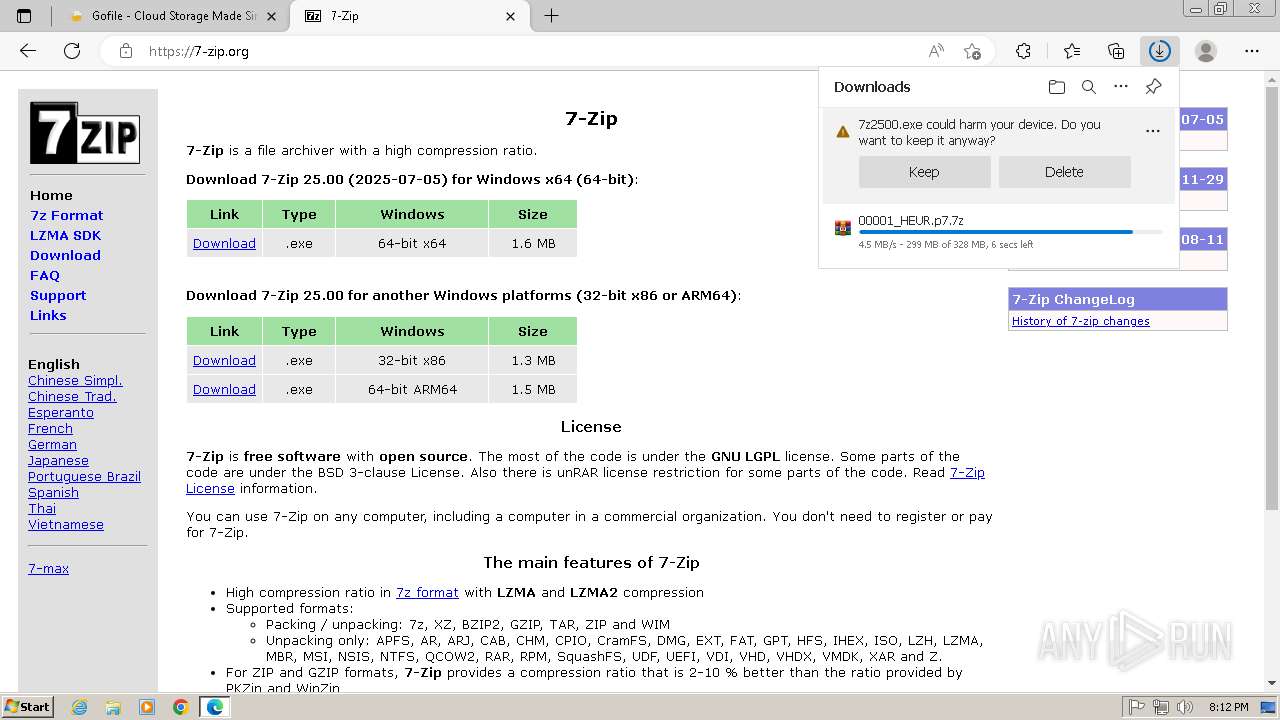
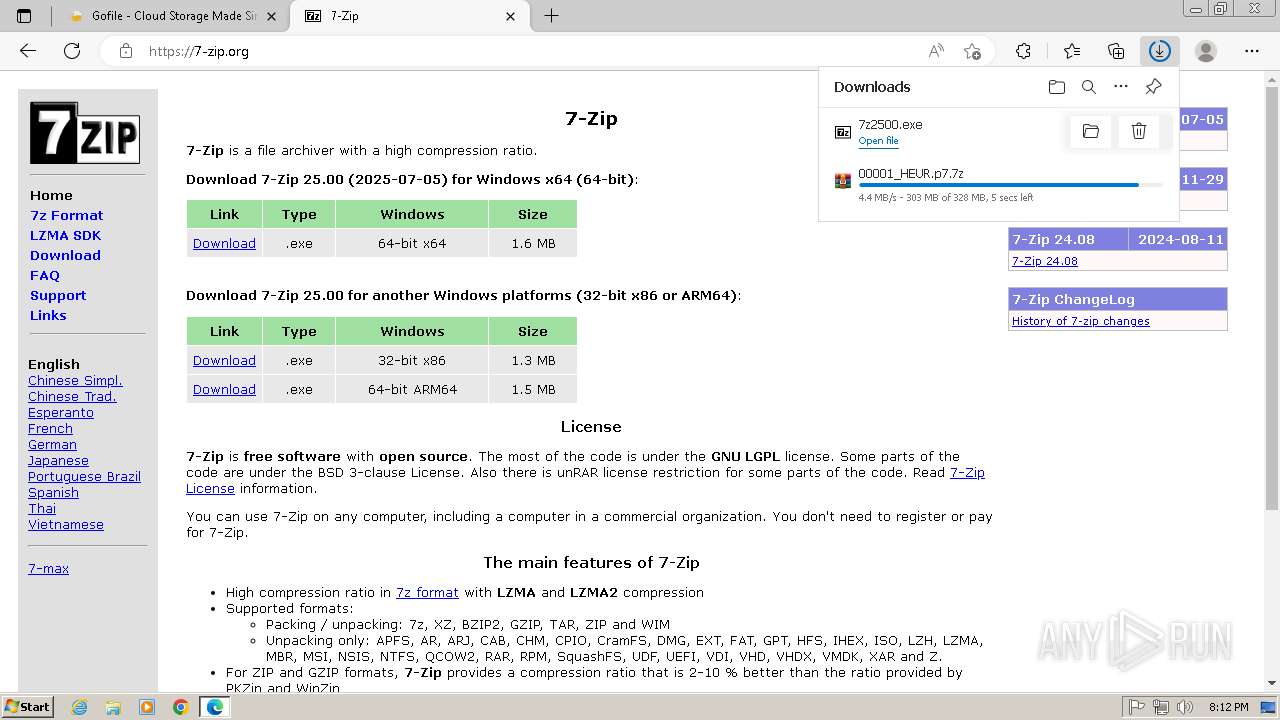
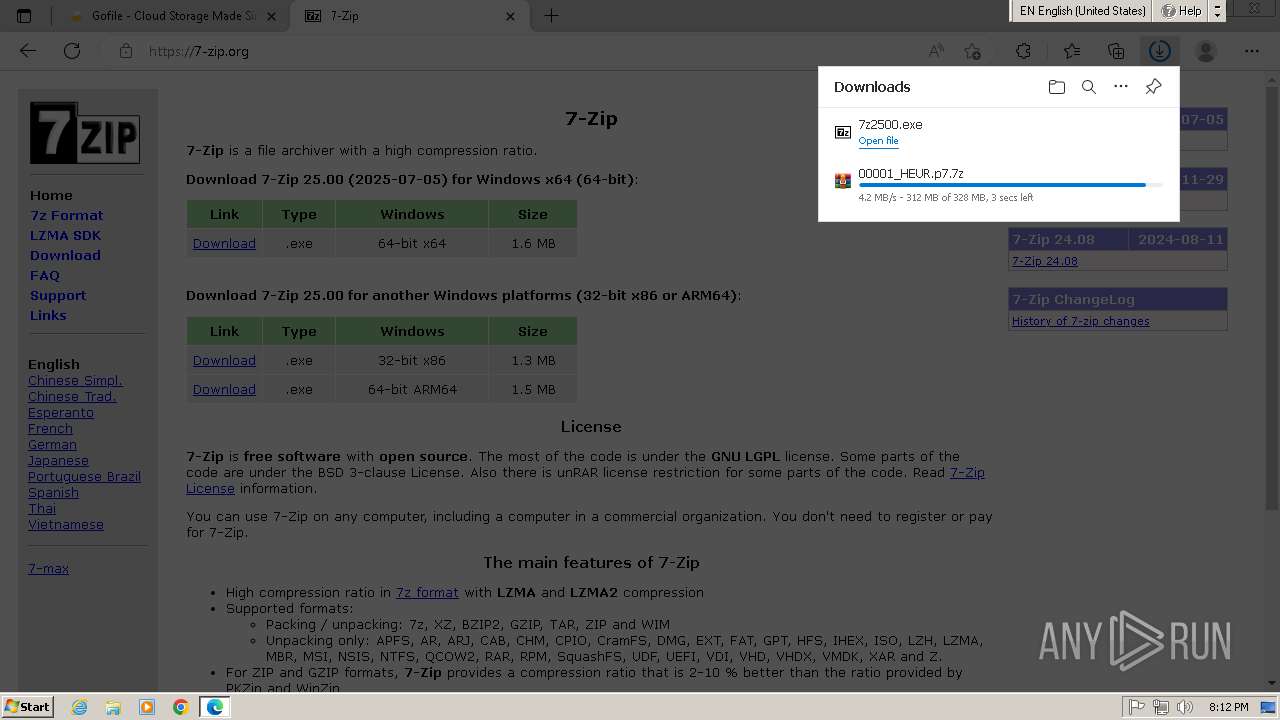
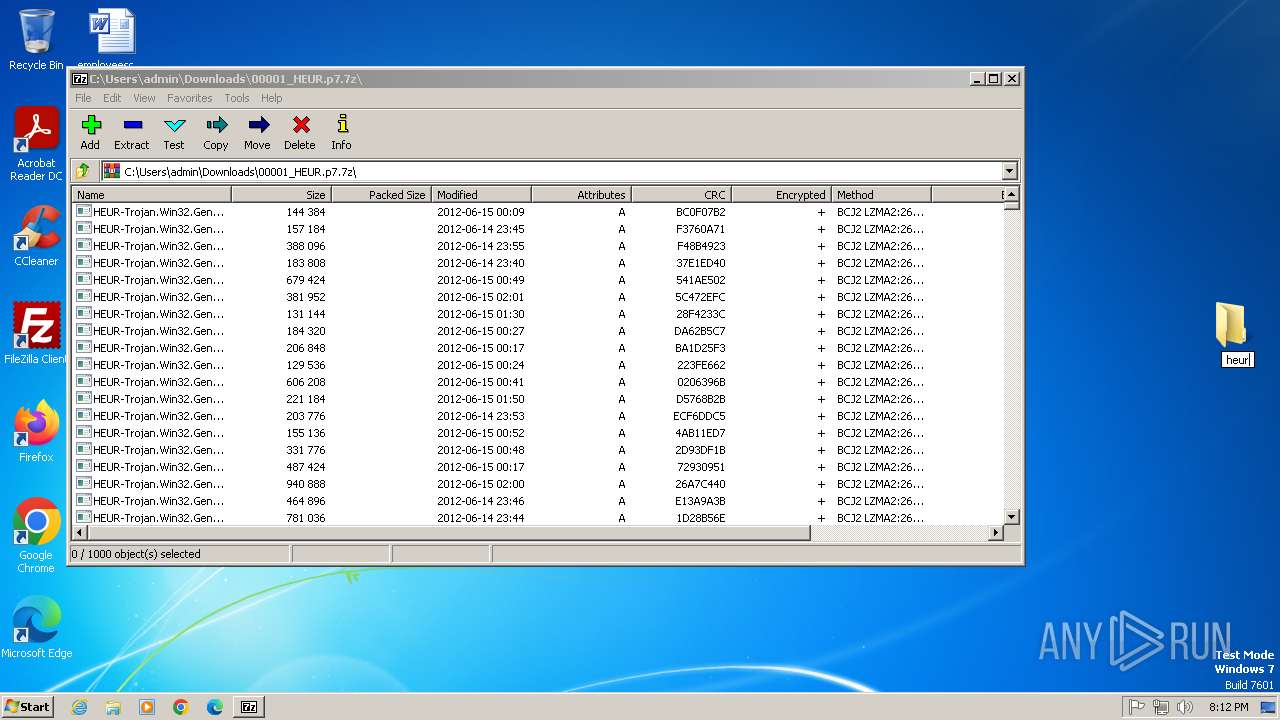
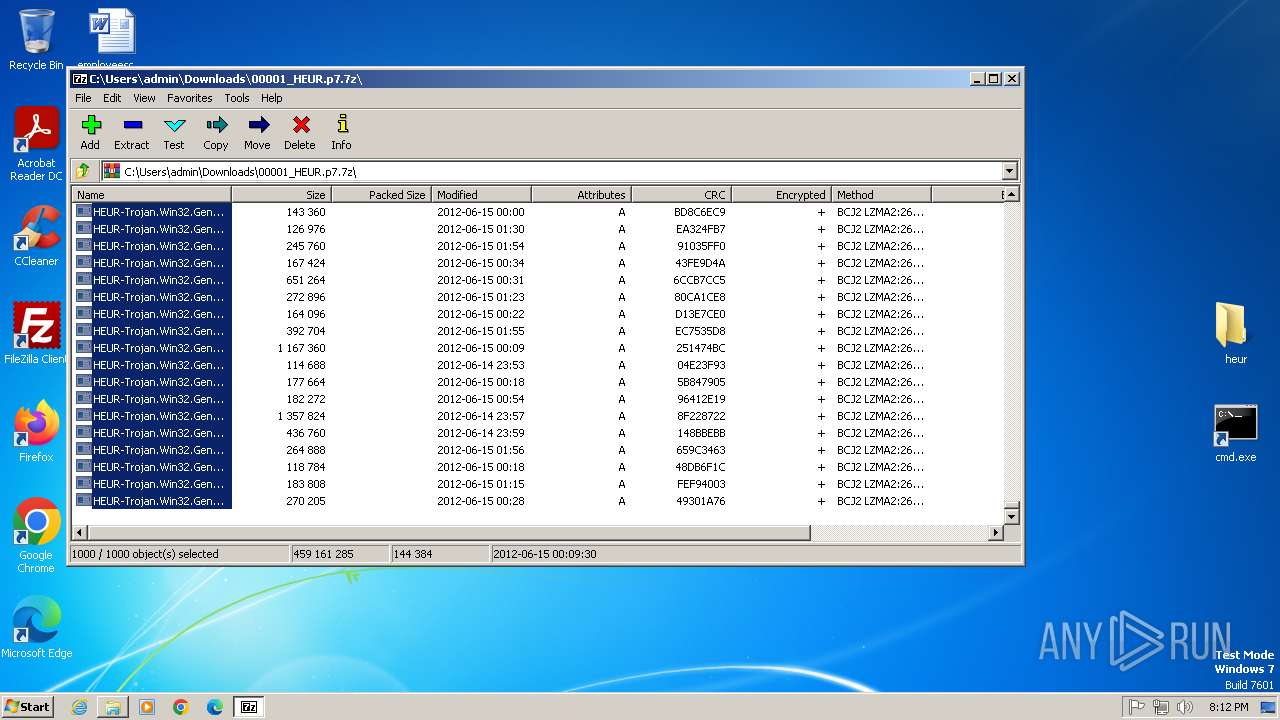
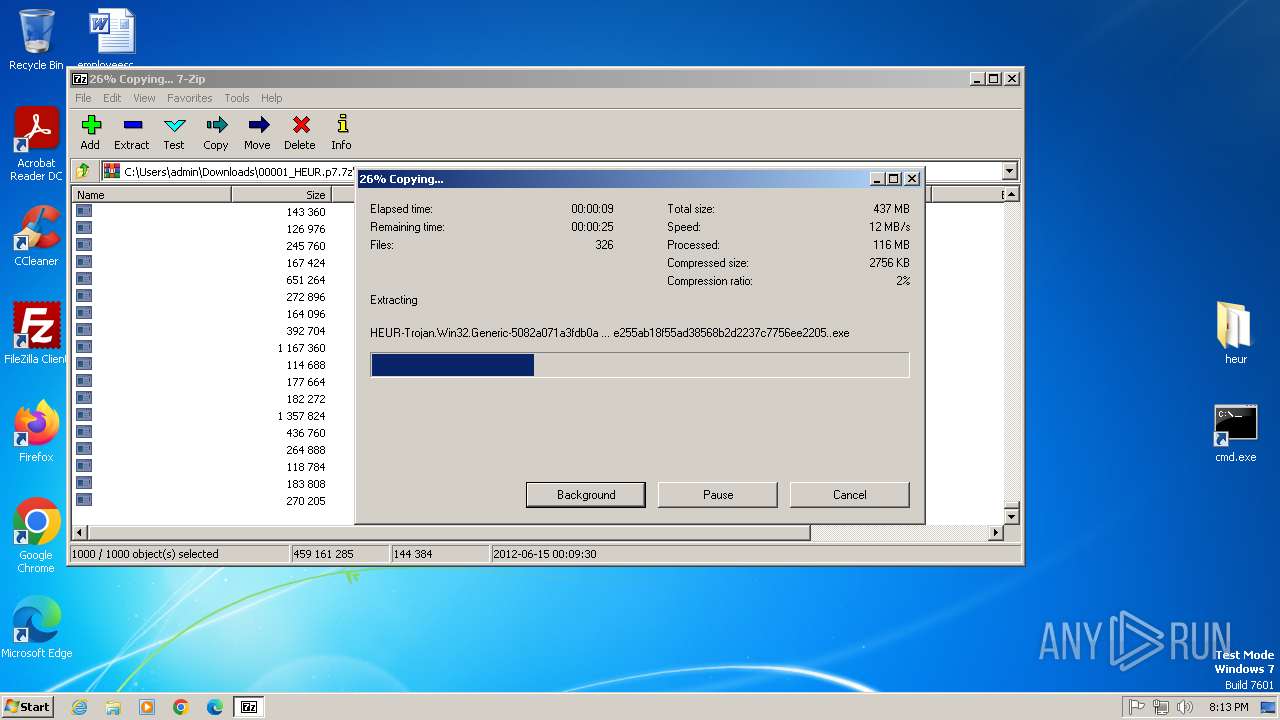
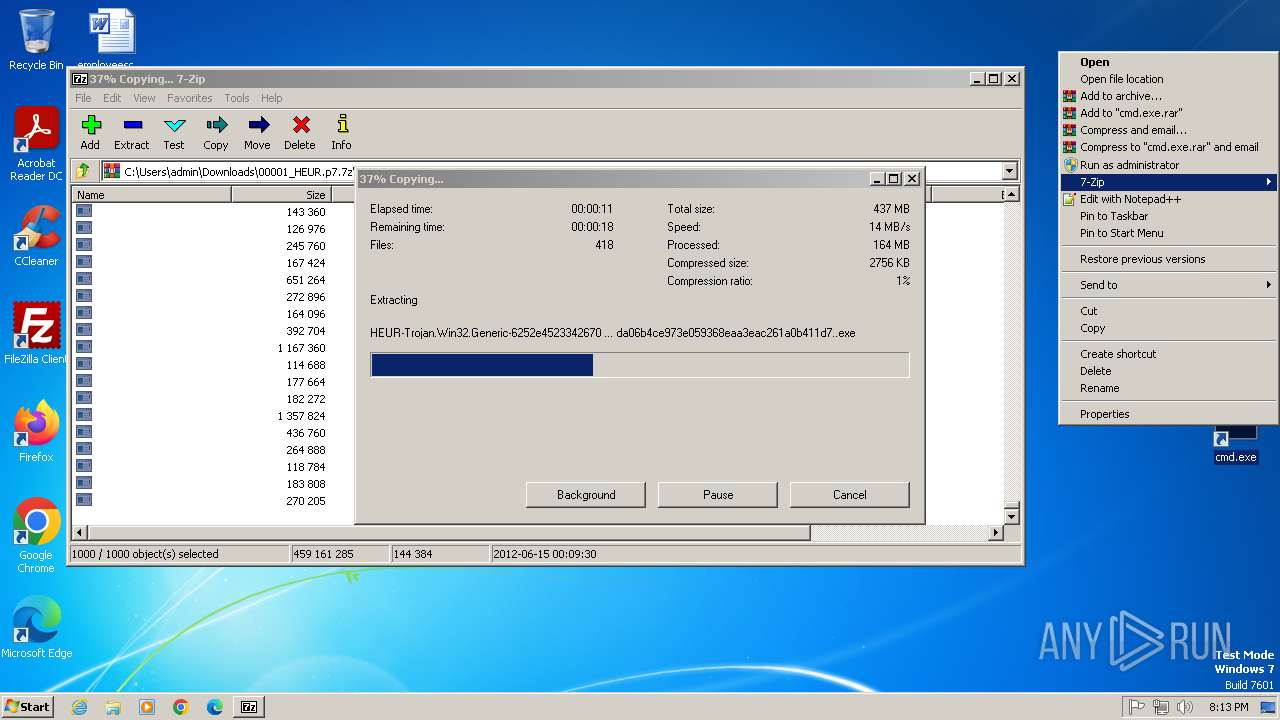
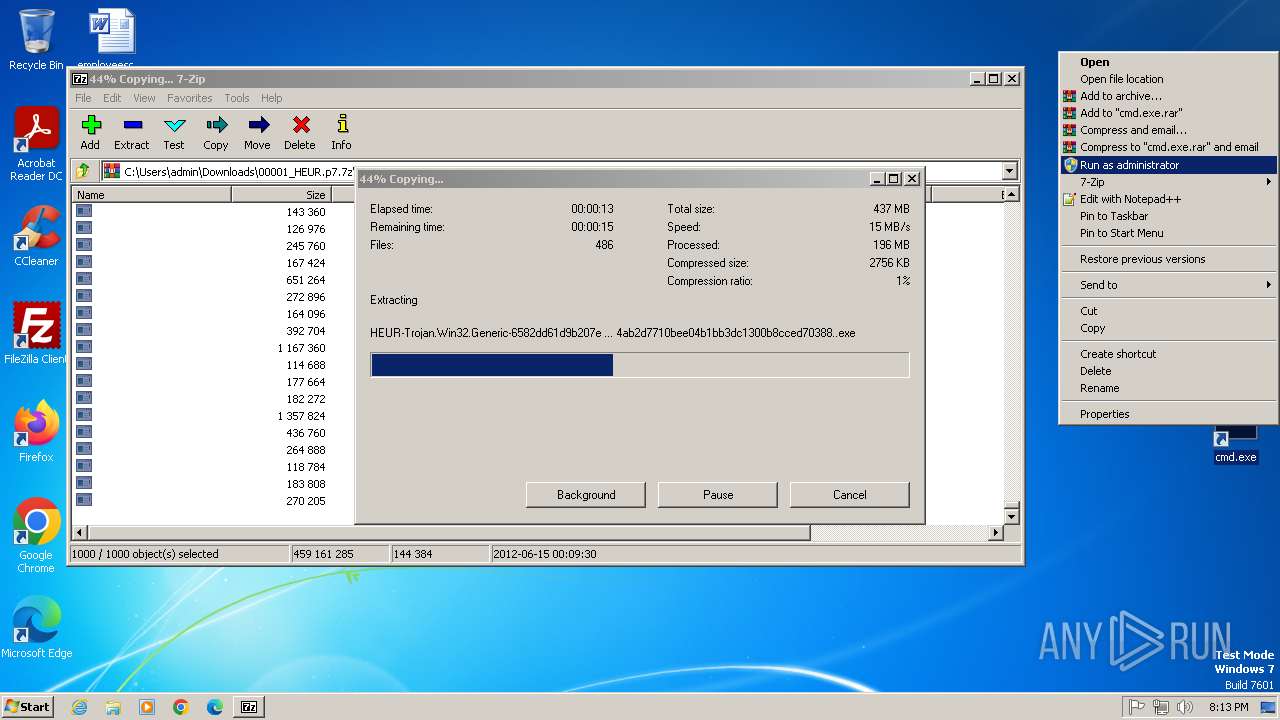
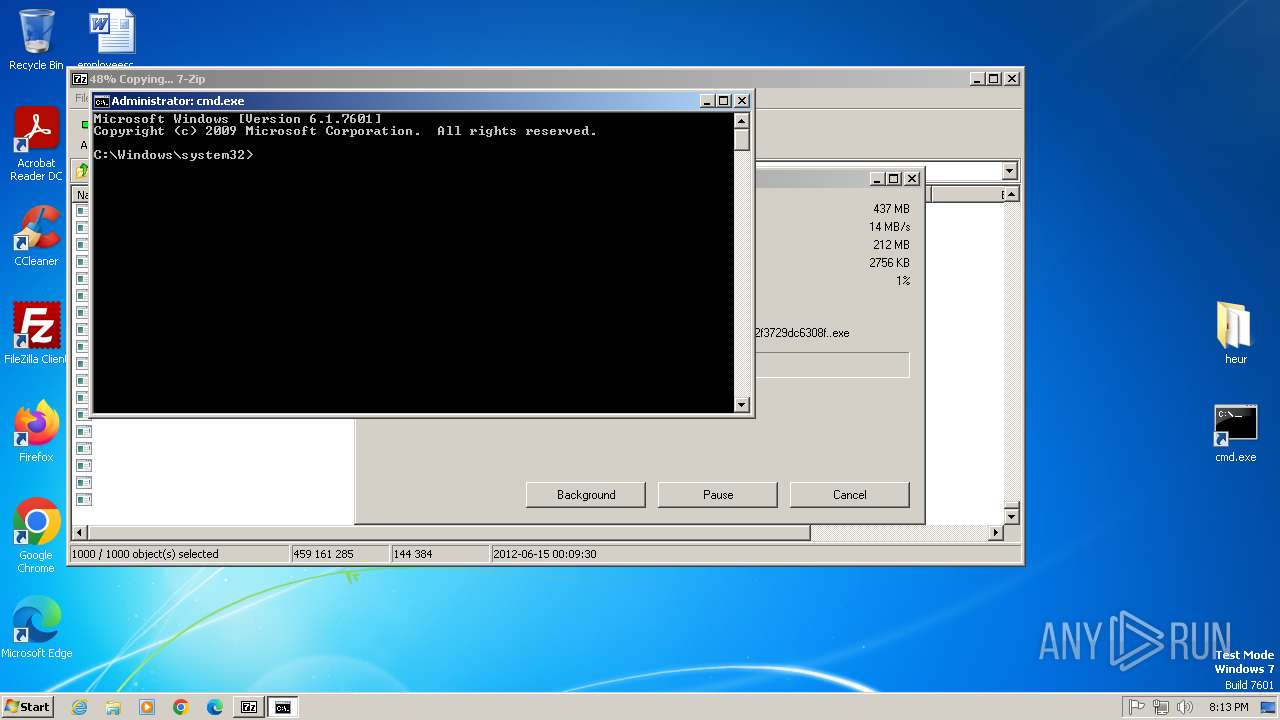
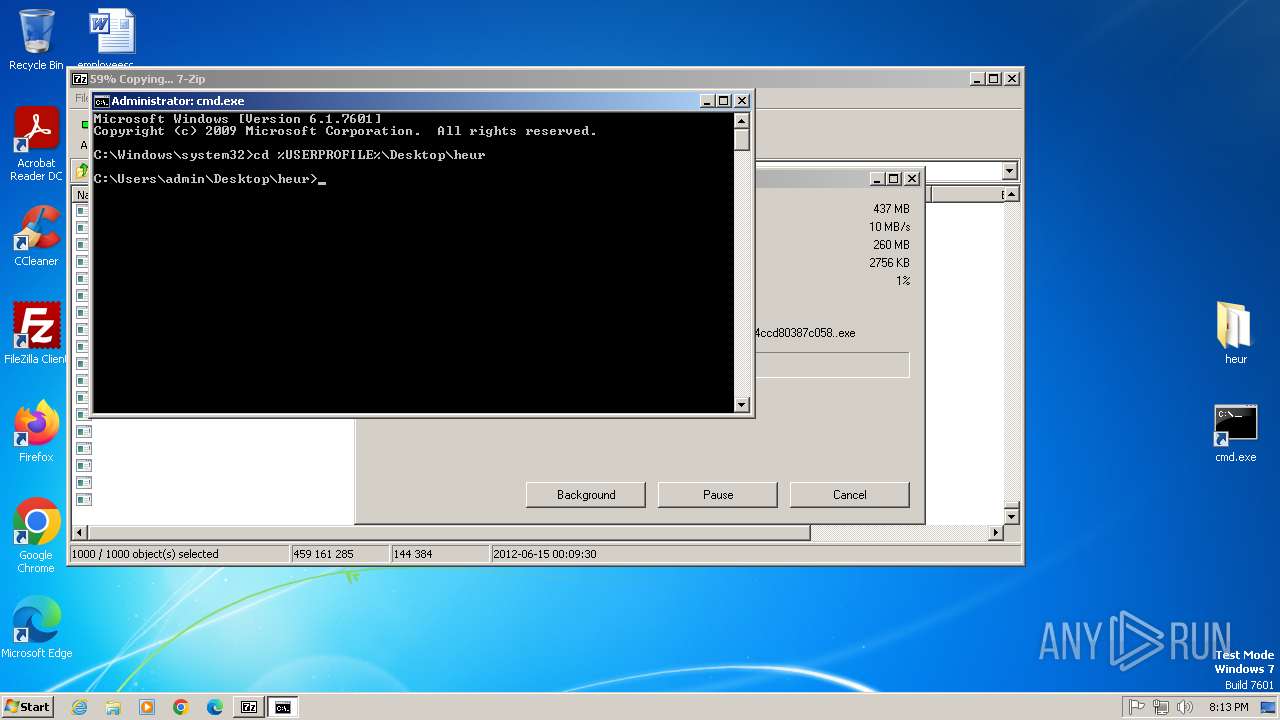
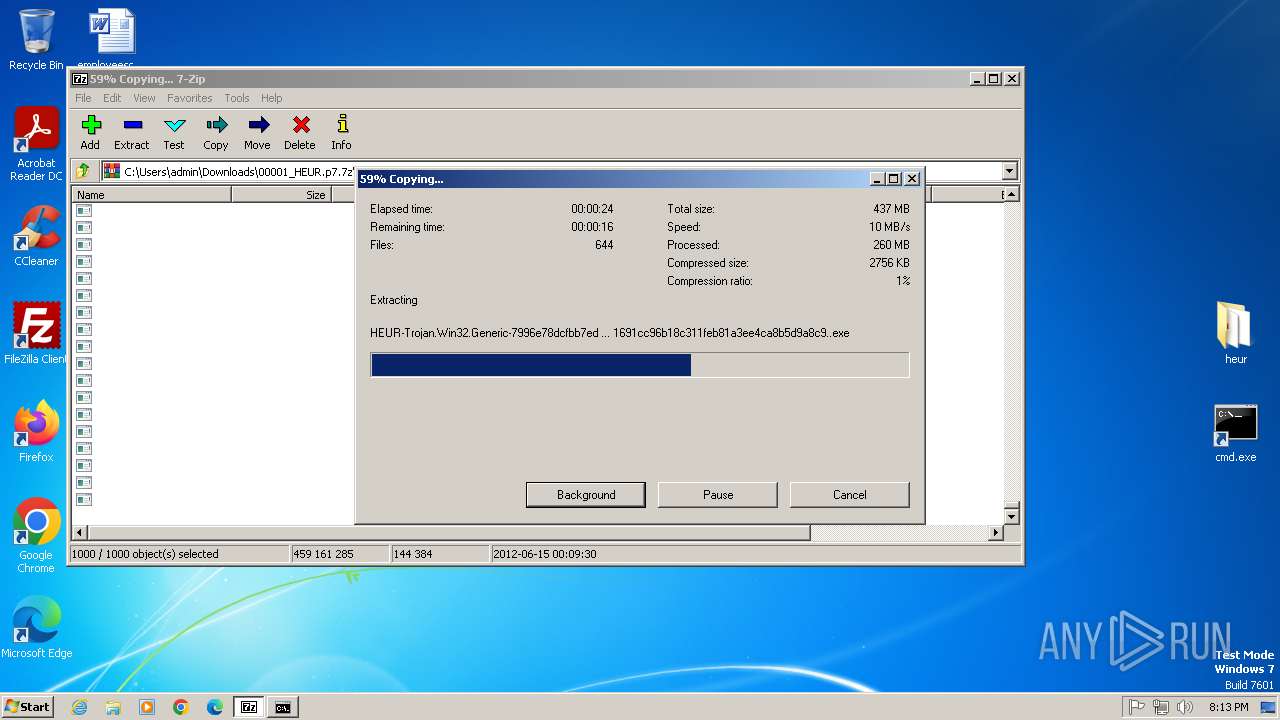
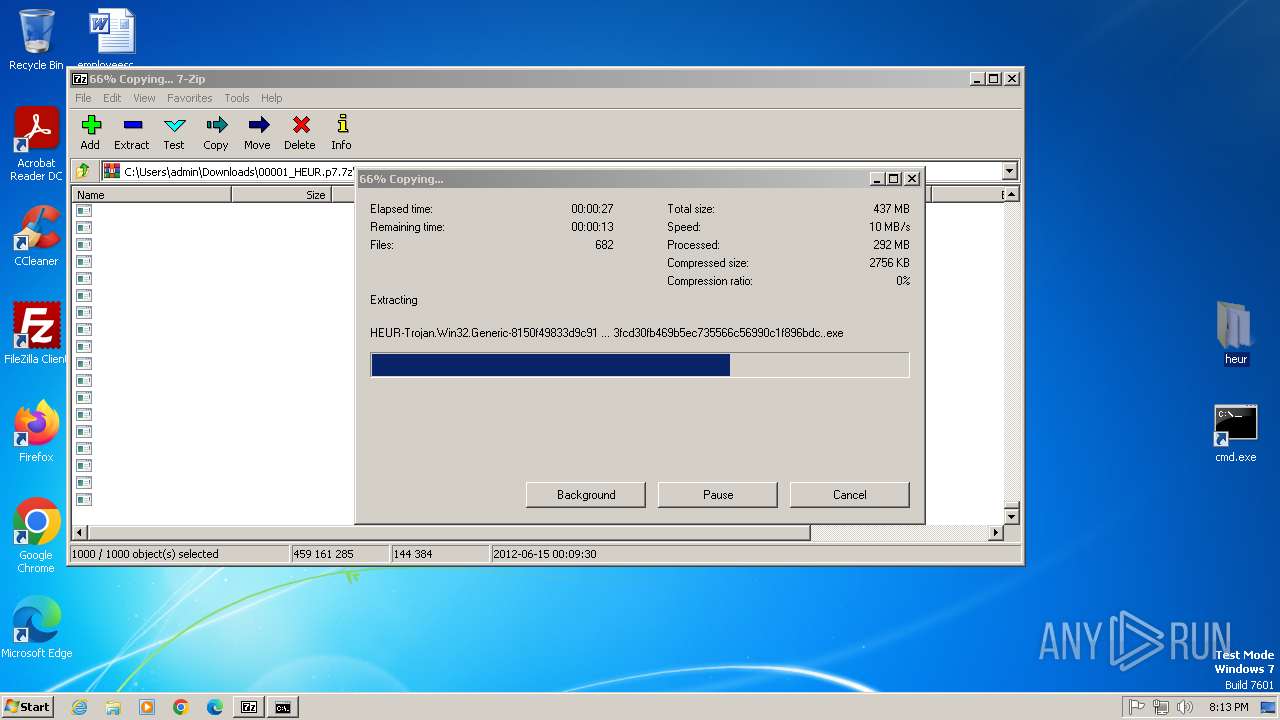
Drops 7-zip archiver for unpacking
- msedge.exe (PID: 2932)
- msedge.exe (PID: 3656)
- 7z2500.exe (PID: 3056)
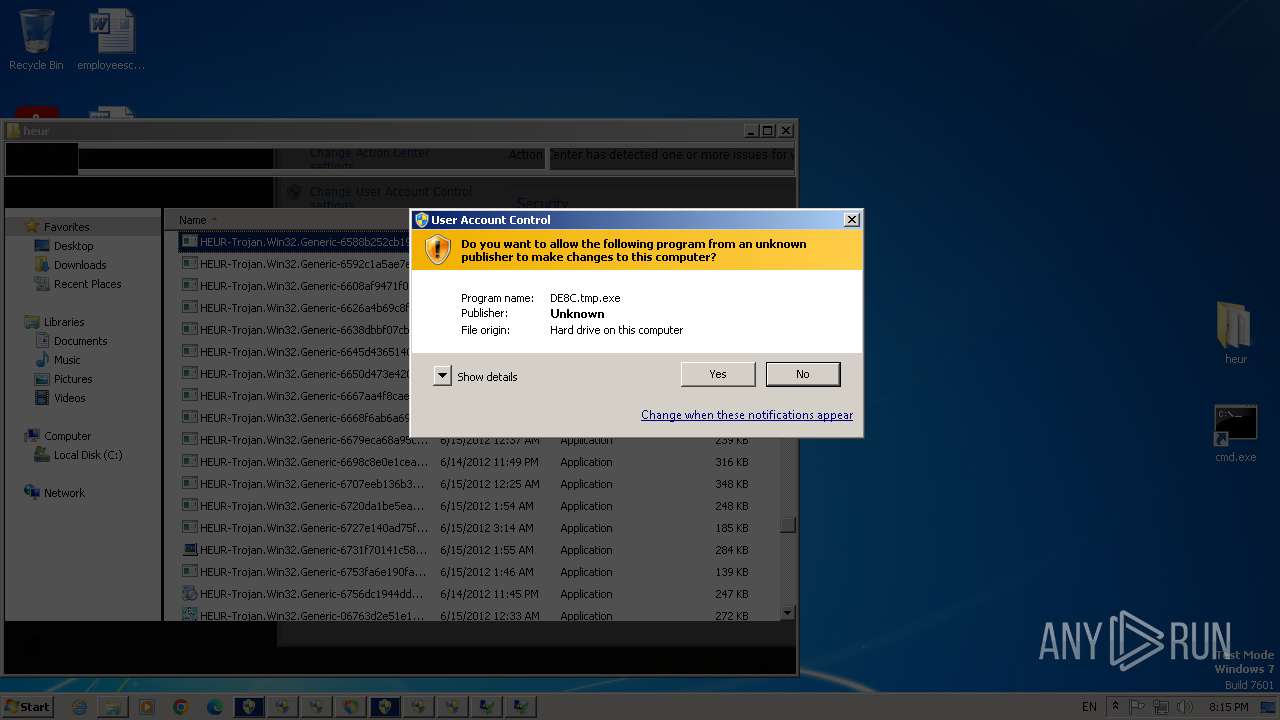
Executable content was dropped or overwritten
- 7zFM.exe (PID: 4092)
- 7z2500.exe (PID: 3056)
- vbc.exe (PID: 3728)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
- HEUR-Trojan.Win32.Generic-9176ae2b2804002b00ce55eefdc4dd97eb34aab7031ae43c13cbfa9921c3eb46..exe (PID: 2624)
- HEUR-Trojan.Win32.Generic-9142b4b9280b9d0ccb2906d42edd0c9a29ee9399d21dbc5a56869f9ebbea2514..exe (PID: 3516)
- svchost.exe (PID: 556)
- HEUR-Trojan.Win32.Generic-9090f383d746829072f03748c311808279c52b6cb17ed66584e546304a528067..exe (PID: 1168)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
- RuneHack.exe (PID: 3924)
- dllhost.exe (PID: 3228)
- sysprep.exe (PID: 3404)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
- HEUR-Trojan.Win32.Generic-08764e0f3e20057c324a3b9f8a27ce1042288a90a933df2330925169624bc201..exe (PID: 1564)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2440)
- HEUR-Trojan.Win32.Generic-8629d6b2bc7b0877fc9858784e861eb7728f1475df1bb6b6552437ab68435f33..exe (PID: 2444)
- HEUR-Trojan.Win32.Generic-8493e31df664dff6f41a8376f132fcc9871098ff51fea29453156eb1475bef61..exe (PID: 4076)
- HEUR-Trojan.Win32.Generic-8507bb1cb0f4712a03d3ebb084da330a9ab8eec22f331cf3f1849cd7403aecde..exe (PID: 1744)
- FA81.exe (PID: 3648)
- HEUR-Trojan.Win32.Generic-8394dfb52477a7b153a9cdd608826ce0df4166b73244f78486d7ea9cb9792244..exe (PID: 3340)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- HEUR-Trojan.Win32.Generic-8394dfb52477a7b153a9cdd608826ce0df4166b73244f78486d7ea9cb9792244..exe (PID: 3900)
- HEUR-Trojan.Win32.Generic-08394ffe3f87c3b3be04b763677d89783217fedd9a2efb96a436e99172cf441d..exe (PID: 3792)
- sysprep.exe (PID: 3780)
- sysprep.exe (PID: 2708)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 1336)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 3788)
- sysprep.exe (PID: 2112)
- sysprep.exe (PID: 2364)
- explorer.exe (PID: 1452)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
Process drops legitimate windows executable
- 7zFM.exe (PID: 4092)
- vbc.exe (PID: 3728)
- HEUR-Trojan.Win32.Generic-9176ae2b2804002b00ce55eefdc4dd97eb34aab7031ae43c13cbfa9921c3eb46..exe (PID: 2624)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- HEUR-Trojan.Win32.Generic-8493e31df664dff6f41a8376f132fcc9871098ff51fea29453156eb1475bef61..exe (PID: 4076)
- HEUR-Trojan.Win32.Generic-08394ffe3f87c3b3be04b763677d89783217fedd9a2efb96a436e99172cf441d..exe (PID: 3792)
Creates a software uninstall entry
- 7z2500.exe (PID: 3056)
Creates/Modifies COM task schedule object
- 7z2500.exe (PID: 3056)
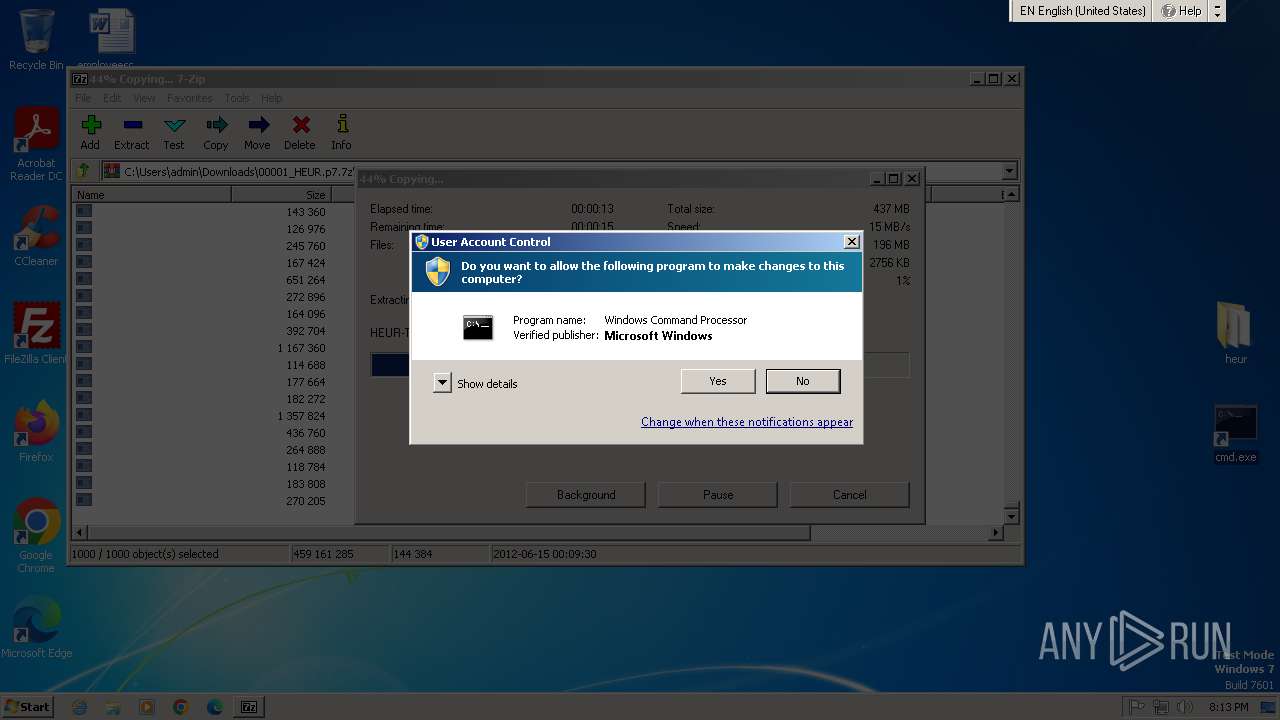
Starts CMD.EXE for commands execution
- explorer.exe (PID: 1452)
- vbc.exe (PID: 3728)
- RuneHack.exe (PID: 3924)
Reads the BIOS version
- HEUR-Trojan.Win32.Generic-9356e380f6da9efb80d2a8f6417aef094c9e46abe3f30065d1f2e48d3814e4f2..exe (PID: 3928)
- HEUR-Trojan.Win32.Generic-8792a3468196865f986758095c7286fc0bdab460c4525de03c88f1b2f4f39ad0..exe (PID: 1060)
Starts a Microsoft application from unusual location
- HEUR-Trojan.Win32.Generic-9289d5a5494d04e0d6e092bf5289a63a5b080a0792bf902394c102c2cd79b95a..exe (PID: 3812)
- HEUR-Trojan.Win32.Generic-9176ae2b2804002b00ce55eefdc4dd97eb34aab7031ae43c13cbfa9921c3eb46..exe (PID: 2624)
- vbc.exe (PID: 1028)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
- vbc.exe (PID: 3124)
The process executes VB scripts
- HEUR-Trojan.Win32.Generic-9280a1ecaff98076cfdd98083535a371148879b12a8c55463ec3bb62f98de0a1..exe (PID: 3772)
The process creates files with name similar to system file names
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- msedge.exe (PID: 1780)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- HEUR-Trojan.Win32.Generic-08394ffe3f87c3b3be04b763677d89783217fedd9a2efb96a436e99172cf441d..exe (PID: 3792)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3536)
- cmd.exe (PID: 996)
- cmd.exe (PID: 3824)
- cmd.exe (PID: 3212)
Reads the Internet Settings
- HEUR-Trojan.Win32.Generic-9269aff1e9ab7517f19e4b47e5d05ec385f59efc9790951fcfb2e100ef7ab175..exe (PID: 3456)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
- HEUR-Trojan.Win32.Generic-9165bfd840fc2d5b45049c58f7680007235d05c2628bb95e54bcd6877a18d991..exe (PID: 3672)
- HEUR-Trojan.Win32.Generic-9067c8411d9138a24167da423db123d337bf7889e0d7f91bc8b46e4987bc5a78..exe (PID: 3396)
- HEUR-Trojan.Win32.Generic-9142b4b9280b9d0ccb2906d42edd0c9a29ee9399d21dbc5a56869f9ebbea2514..exe (PID: 3516)
- HEUR-Trojan.Win32.Generic-9086fd10fdc222be3b7361f21dc6df536ee6e9dabc50dd169716d5dd2293c19e..exe (PID: 2144)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
- RuneHack.exe (PID: 3924)
- nA41221ObIgM41221.exe (PID: 1372)
- HEUR-Trojan.Win32.Generic-8918f5c21c853bc791c65863a01b7f42e47f24c4019b3d82fdda9f2b6adda6e5..exe (PID: 3444)
- HEUR-Trojan.Win32.Generic-8969bb7ab1fd45e2355a9674cdfc9085afb1339f7cccd3c1e154341cf6521562..exe (PID: 3644)
- HEUR-Trojan.Win32.Generic-8840f33e1015f6545a747c2917f86af96898ff9ee9f19f1719e573ed8876e4f0..exe (PID: 1924)
- gyp.exe (PID: 2992)
- HEUR-Trojan.Win32.Generic-08764e0f3e20057c324a3b9f8a27ce1042288a90a933df2330925169624bc201..exe (PID: 1564)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 2720)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2440)
- nA41221ObIgM41221.exe (PID: 3040)
- gyp.exe (PID: 392)
- gyp.exe (PID: 2964)
- gyp.exe (PID: 704)
- gyp.exe (PID: 1380)
- gyp.exe (PID: 2940)
- gyp.exe (PID: 3612)
- gyp.exe (PID: 4008)
- gyp.exe (PID: 3740)
- gyp.exe (PID: 1156)
- gyp.exe (PID: 4048)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 3308)
- gyp.exe (PID: 2436)
- gyp.exe (PID: 2744)
- gyp.exe (PID: 3800)
- gyp.exe (PID: 3280)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 4068)
- HEUR-Trojan.Win32.Generic-8507bb1cb0f4712a03d3ebb084da330a9ab8eec22f331cf3f1849cd7403aecde..exe (PID: 1744)
- gyp.exe (PID: 3744)
- gyp.exe (PID: 3972)
- gyp.exe (PID: 2072)
- HEUR-Trojan.Win32.Generic-8399e9ed8b206acdcef6f103794bab682c3e628732c3242841f639008c5340ba..exe (PID: 2564)
- FA81.exe (PID: 3648)
- gyp.exe (PID: 4032)
- gyp.exe (PID: 2572)
- gyp.exe (PID: 1572)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 1580)
- gyp.exe (PID: 2108)
- gyp.exe (PID: 3872)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- gyp.exe (PID: 2484)
- gyp.exe (PID: 1960)
- gyp.exe (PID: 3312)
- gyp.exe (PID: 548)
- gyp.exe (PID: 1776)
- gyp.exe (PID: 3408)
- gyp.exe (PID: 3088)
- gyp.exe (PID: 820)
- gyp.exe (PID: 1800)
- gyp.exe (PID: 3956)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 3216)
- gyp.exe (PID: 2136)
- gyp.exe (PID: 2532)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 1844)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 1124)
- gyp.exe (PID: 1500)
- gyp.exe (PID: 1180)
- gyp.exe (PID: 2512)
- gyp.exe (PID: 3056)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 3424)
- gyp.exe (PID: 2676)
- gyp.exe (PID: 2712)
- gyp.exe (PID: 1576)
- gyp.exe (PID: 3004)
Application launched itself
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 1980)
- HEUR-Trojan.Win32.Generic-9191ae6eb7e7c960afdee1815853b664710eb9c578eb293130147c25c92f650f..exe (PID: 1584)
- HEUR-Trojan.Win32.Generic-9162c1643afeaf61ed44aebae58797a26d5b94e85d84311e719736fa03153c34..exe (PID: 2084)
- HEUR-Trojan.Win32.Generic-9096cd34c8f099659c52b6dfc49b62e25a797fb4ebcc9f9956bb41b2a626f585..exe (PID: 344)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2112)
- system.exe (PID: 2236)
- HEUR-Trojan.Win32.Generic-8700cb1c24c03ab8e654fb18f74db9e394d2f6049de6b87c55b4c49ebf2229fd..exe (PID: 3388)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 1180)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 2332)
- sysprep.exe (PID: 1884)
- HEUR-Trojan.Win32.Generic-6963f86855ac1cfd80e79b19c06ab713aa92518fc122b06eb50c5ea537d3e18b..exe (PID: 2096)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 2072)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 2236)
- system.exe (PID: 2368)
- sysprep.exe (PID: 780)
- system.exe (PID: 5796)
Connects to unusual port
- vbc.exe (PID: 3728)
- explorer.exe (PID: 1452)
Reads security settings of Internet Explorer
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
- HEUR-Trojan.Win32.Generic-9067c8411d9138a24167da423db123d337bf7889e0d7f91bc8b46e4987bc5a78..exe (PID: 3396)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
- RuneHack.exe (PID: 3924)
- nA41221ObIgM41221.exe (PID: 1372)
- HEUR-Trojan.Win32.Generic-8969bb7ab1fd45e2355a9674cdfc9085afb1339f7cccd3c1e154341cf6521562..exe (PID: 3644)
- HEUR-Trojan.Win32.Generic-8918f5c21c853bc791c65863a01b7f42e47f24c4019b3d82fdda9f2b6adda6e5..exe (PID: 3444)
- gyp.exe (PID: 2992)
- HEUR-Trojan.Win32.Generic-08764e0f3e20057c324a3b9f8a27ce1042288a90a933df2330925169624bc201..exe (PID: 1564)
- gyp.exe (PID: 2720)
- gyp.exe (PID: 3300)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2440)
- gyp.exe (PID: 392)
- gyp.exe (PID: 4008)
- gyp.exe (PID: 704)
- gyp.exe (PID: 1380)
- gyp.exe (PID: 2940)
- gyp.exe (PID: 2964)
- nA41221ObIgM41221.exe (PID: 3040)
- gyp.exe (PID: 3612)
- gyp.exe (PID: 1156)
- gyp.exe (PID: 3740)
- gyp.exe (PID: 4048)
- gyp.exe (PID: 3308)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 2436)
- gyp.exe (PID: 3800)
- gyp.exe (PID: 2744)
- gyp.exe (PID: 3280)
- gyp.exe (PID: 4068)
- HEUR-Trojan.Win32.Generic-8507bb1cb0f4712a03d3ebb084da330a9ab8eec22f331cf3f1849cd7403aecde..exe (PID: 1744)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 3744)
- gyp.exe (PID: 3972)
- HEUR-Trojan.Win32.Generic-8399e9ed8b206acdcef6f103794bab682c3e628732c3242841f639008c5340ba..exe (PID: 2564)
- gyp.exe (PID: 2072)
- FA81.exe (PID: 3648)
- gyp.exe (PID: 4032)
- gyp.exe (PID: 1572)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 1580)
- gyp.exe (PID: 2572)
- gyp.exe (PID: 2108)
- gyp.exe (PID: 3872)
- gyp.exe (PID: 2484)
- gyp.exe (PID: 3312)
- gyp.exe (PID: 3088)
- gyp.exe (PID: 548)
- gyp.exe (PID: 1776)
- gyp.exe (PID: 1960)
- gyp.exe (PID: 820)
- gyp.exe (PID: 1800)
- gyp.exe (PID: 3408)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 3956)
- gyp.exe (PID: 3216)
- gyp.exe (PID: 2136)
- gyp.exe (PID: 2532)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 1844)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 1500)
- gyp.exe (PID: 1124)
- gyp.exe (PID: 1180)
- gyp.exe (PID: 2512)
- gyp.exe (PID: 3056)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 3424)
- gyp.exe (PID: 2676)
- gyp.exe (PID: 2712)
- gyp.exe (PID: 1576)
- gyp.exe (PID: 3004)
Uses TASKKILL.EXE to kill process
- HEUR-Trojan.Win32.Generic-9177d2c0031c53aff941ca7264b8204c2fdec09341f04a09733bf99eb25d12fe..exe (PID: 3232)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 2312)
- explorer.exe (PID: 3844)
- explorer.exe (PID: 3508)
- explorer.exe (PID: 3504)
- explorer.exe (PID: 3320)
Uses RUNDLL32.EXE to load library
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
Detected use of alternative data streams (AltDS)
- RuneHack.exe (PID: 3924)
- cmd.exe (PID: 1880)
Starts itself from another location
- RuneHack.exe (PID: 3924)
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
Changes default file association
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
Reads the date of Windows installation
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2440)
- gyp.exe (PID: 2940)
- HEUR-Trojan.Win32.Generic-6922d9eceea6fdc843b0c2594c09da4bedd7c4a9080c6472b5bac1361c11c6b9..exe (PID: 3272)
There is functionality for taking screenshot (YARA)
- svchost.exe (PID: 2796)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
Access to an unwanted program domain was detected
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
Contacting a server suspected of hosting an CnC
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- explorer.exe (PID: 1452)
Creates file in the systems drive root
- explorer.exe (PID: 1452)
- HEUR-Trojan.Win32.Generic-6931df583187624fd800d8c4348cbeeab8fa523c950a6bab39ca99e32db943a3..exe (PID: 1884)
Changes internet zones settings
- explorer.exe (PID: 1452)
Modifies the phishing filter of IE
- explorer.exe (PID: 1452)
Reads Microsoft Outlook installation path
- gyp.exe (PID: 5624)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 1452)
- explorer.exe (PID: 2312)
- svchost.exe (PID: 2796)
- explorer.exe (PID: 3508)
- explorer.exe (PID: 3844)
- explorer.exe (PID: 3504)
- explorer.exe (PID: 3320)
The sample compiled with english language support
- msedge.exe (PID: 2932)
- msedge.exe (PID: 3656)
- 7zFM.exe (PID: 4092)
- 7z2500.exe (PID: 3056)
- vbc.exe (PID: 3728)
- HEUR-Trojan.Win32.Generic-9176ae2b2804002b00ce55eefdc4dd97eb34aab7031ae43c13cbfa9921c3eb46..exe (PID: 2624)
- svchost.exe (PID: 556)
- dllhost.exe (PID: 3228)
- sysprep.exe (PID: 3404)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- HEUR-Trojan.Win32.Generic-8493e31df664dff6f41a8376f132fcc9871098ff51fea29453156eb1475bef61..exe (PID: 4076)
- HEUR-Trojan.Win32.Generic-08394ffe3f87c3b3be04b763677d89783217fedd9a2efb96a436e99172cf441d..exe (PID: 3792)
- sysprep.exe (PID: 2112)
- sysprep.exe (PID: 2364)
- explorer.exe (PID: 1452)
Application launched itself
- msedge.exe (PID: 2932)
Creates files in the program directory
- 7z2500.exe (PID: 3056)
- HEUR-Trojan.Win32.Generic-9090f383d746829072f03748c311808279c52b6cb17ed66584e546304a528067..exe (PID: 1168)
- nA41221ObIgM41221.exe (PID: 1372)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
Executable content was dropped or overwritten
- msedge.exe (PID: 2932)
- msedge.exe (PID: 3656)
- msedge.exe (PID: 1780)
Checks supported languages
- 7z2500.exe (PID: 3056)
- 7zFM.exe (PID: 4092)
- HEUR-Trojan.Win32.Generic-9412c909c3448441125750d543bfc601cfe33ad4a31470c27918b6a3ed32796f..exe (PID: 2272)
- HEUR-Trojan.Win32.Generic-9391c23c1d6f599a85f08b8b8bd34b02119049da669962d16773c1dd2c0e0fde..exe (PID: 1120)
- HEUR-Trojan.Win32.Generic-9356e380f6da9efb80d2a8f6417aef094c9e46abe3f30065d1f2e48d3814e4f2..exe (PID: 3928)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2112)
- HEUR-Trojan.Win32.Generic-9289d5a5494d04e0d6e092bf5289a63a5b080a0792bf902394c102c2cd79b95a..exe (PID: 3812)
- HEUR-Trojan.Win32.Generic-9375c6293126d57dc2f846b766e410a178f22beef9bdc576e3bcc30f04958e36..exe (PID: 3184)
- vbc.exe (PID: 3728)
- HEUR-Trojan.Win32.Generic-9280a1ecaff98076cfdd98083535a371148879b12a8c55463ec3bb62f98de0a1..exe (PID: 3772)
- HEUR-Trojan.Win32.Generic-9259c75a3ce10d8c97c42505fd4057fe42911c1189bd2629f872ce5e10c5700e..exe (PID: 2868)
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 1980)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 3108)
- HEUR-Trojan.Win32.Generic-9269aff1e9ab7517f19e4b47e5d05ec385f59efc9790951fcfb2e100ef7ab175..exe (PID: 3456)
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 3024)
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
- HEUR-Trojan.Win32.Generic-9191ae6eb7e7c960afdee1815853b664710eb9c578eb293130147c25c92f650f..exe (PID: 1584)
- HEUR-Trojan.Win32.Generic-9191ae6eb7e7c960afdee1815853b664710eb9c578eb293130147c25c92f650f..exe (PID: 3004)
- HEUR-Trojan.Win32.Generic-9165bfd840fc2d5b45049c58f7680007235d05c2628bb95e54bcd6877a18d991..exe (PID: 3672)
- HEUR-Trojan.Win32.Generic-9176ae2b2804002b00ce55eefdc4dd97eb34aab7031ae43c13cbfa9921c3eb46..exe (PID: 2624)
- HEUR-Trojan.Win32.Generic-9162c1643afeaf61ed44aebae58797a26d5b94e85d84311e719736fa03153c34..exe (PID: 2084)
- HEUR-Trojan.Win32.Generic-9162c1643afeaf61ed44aebae58797a26d5b94e85d84311e719736fa03153c34..exe (PID: 3340)
- HEUR-Trojan.Win32.Generic-9177d2c0031c53aff941ca7264b8204c2fdec09341f04a09733bf99eb25d12fe..exe (PID: 3232)
- HEUR-Trojan.Win32.Generic-9090f383d746829072f03748c311808279c52b6cb17ed66584e546304a528067..exe (PID: 1168)
- HEUR-Trojan.Win32.Generic-9096cd34c8f099659c52b6dfc49b62e25a797fb4ebcc9f9956bb41b2a626f585..exe (PID: 344)
- HEUR-Trojan.Win32.Generic-9142b4b9280b9d0ccb2906d42edd0c9a29ee9399d21dbc5a56869f9ebbea2514..exe (PID: 3516)
- HEUR-Trojan.Win32.Generic-9086fd10fdc222be3b7361f21dc6df536ee6e9dabc50dd169716d5dd2293c19e..exe (PID: 2144)
- HEUR-Trojan.Win32.Generic-9096cd34c8f099659c52b6dfc49b62e25a797fb4ebcc9f9956bb41b2a626f585..exe (PID: 2696)
- HEUR-Trojan.Win32.Generic-9085f8a76c559da7f3626b70e2de94b5142cd2c8630c9fbd654f73106b1f96c5..exe (PID: 672)
- HEUR-Trojan.Win32.Generic-9067c8411d9138a24167da423db123d337bf7889e0d7f91bc8b46e4987bc5a78..exe (PID: 3396)
- HEUR-Trojan.Win32.Generic-9063ab88dba834f74760b613da46b858441e18b02c1ebc80744f7454e26272b2..exe (PID: 2936)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
- RuneHack.exe (PID: 3924)
- defender.exe (PID: 2828)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2480)
- dw20.exe (PID: 4052)
- nA41221ObIgM41221.exe (PID: 1372)
- HEUR-Trojan.Win32.Generic-8969bb7ab1fd45e2355a9674cdfc9085afb1339f7cccd3c1e154341cf6521562..exe (PID: 3644)
- HEUR-Trojan.Win32.Generic-8943b14b23f23a5cdd1a1e1d21a855e64826c67e163fa2ff97e712086ad609f0..exe (PID: 3896)
- HEUR-Trojan.Win32.Generic-8918f5c21c853bc791c65863a01b7f42e47f24c4019b3d82fdda9f2b6adda6e5..exe (PID: 3444)
- HEUR-Trojan.Win32.Generic-8964d564cda4ecd1351bca67548802fe818c6da7475f0fbf702e0bf543f363b8..exe (PID: 2088)
- HEUR-Trojan.Win32.Generic-8916d140c0132a93cf5e5272fb314799bb3e80214d2073fdad03155a56679e9b..exe (PID: 2464)
- HEUR-Trojan.Win32.Generic-8958cc492cbb582da9d3e18c45d34e164cf792698e7c35c9451428285f372f38..exe (PID: 3752)
- HEUR-Trojan.Win32.Generic-08920c9d18793fa9b072cc8582475d5df5df0d13c0d9cde36231d8da19670273..exe (PID: 1928)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- HEUR-Trojan.Win32.Generic-8844a0d8e92b4ce20257be7a119f760326dc272479144315e4d05e778119e802..exe (PID: 3684)
- vbc.exe (PID: 1028)
- HEUR-Trojan.Win32.Generic-8840f33e1015f6545a747c2917f86af96898ff9ee9f19f1719e573ed8876e4f0..exe (PID: 1924)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2440)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
- HEUR-Trojan.Win32.Generic-8796c958e875048e58fa857bbf8d5d07e7b38635e2bdc073dfd83fcbe4438703..exe (PID: 3024)
- HEUR-Trojan.Win32.Generic-8792a3468196865f986758095c7286fc0bdab460c4525de03c88f1b2f4f39ad0..exe (PID: 1060)
- gyp.exe (PID: 2992)
- HEUR-Trojan.Win32.Generic-8789ad5e8b6ef8d6d403425642e13cd57b00827203b1f25a65f33448d0fb389a..exe (PID: 2864)
- gyp.exe (PID: 3232)
- HEUR-Trojan.Win32.Generic-08764e0f3e20057c324a3b9f8a27ce1042288a90a933df2330925169624bc201..exe (PID: 1564)
- nA41221ObIgM41221.exe (PID: 3040)
- gyp.exe (PID: 2720)
- gyp.exe (PID: 3300)
- HEUR-Trojan.Win32.Generic-8723c2a21a3235fd2401fd415cdf17131b8c7c0931320fbd7246339395f38b5d..exe (PID: 2408)
- gyp.exe (PID: 392)
- gyp.exe (PID: 1380)
- gyp.exe (PID: 2940)
- gyp.exe (PID: 704)
- gyp.exe (PID: 3612)
- gyp.exe (PID: 4008)
- gyp.exe (PID: 2964)
- system.exe (PID: 2236)
- HEUR-Trojan.Win32.Generic-8641e1062420633a19c065f0c61b522a072933d482c6ba2f1ca477e9ee1f0ad4..exe (PID: 3840)
- HEUR-Trojan.Win32.Generic-8635dcd525a0e063d17f662e38ed6a5e825280a9ee448c87b1f303b6e42668da..exe (PID: 3780)
- HEUR-Trojan.Win32.Generic-8700cb1c24c03ab8e654fb18f74db9e394d2f6049de6b87c55b4c49ebf2229fd..exe (PID: 3388)
- system.exe (PID: 1572)
- gyp.exe (PID: 1156)
- igfxhs32.exe (PID: 2084)
- gyp.exe (PID: 4048)
- HEUR-Trojan.Win32.Generic-8629d6b2bc7b0877fc9858784e861eb7728f1475df1bb6b6552437ab68435f33..exe (PID: 2444)
- gyp.exe (PID: 3740)
- gyp.exe (PID: 3248)
- gyp.exe (PID: 3892)
- gyp.exe (PID: 3656)
- gyp.exe (PID: 2612)
- HEUR-Trojan.Win32.Generic-8700cb1c24c03ab8e654fb18f74db9e394d2f6049de6b87c55b4c49ebf2229fd..exe (PID: 2224)
- gyp.exe (PID: 2488)
- gyp.exe (PID: 3308)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 3808)
- gyp.exe (PID: 1624)
- HEUR-Trojan.Win32.Generic-8535e165c3f3452e189fae164f5bab853db4eb7984e28750856c3ff40663df1c..exe (PID: 2600)
- gyp.exe (PID: 2436)
- gyp.exe (PID: 3092)
- gyp.exe (PID: 3264)
- HEUR-Trojan.Win32.Generic-8558c6f4bab45169a7e4bb60e1ce771631c0edd86fce5e4dd9916bc5bfdcdebc..exe (PID: 3652)
- HEUR-Trojan.Win32.Generic-8535e165c3f3452e189fae164f5bab853db4eb7984e28750856c3ff40663df1c..exe (PID: 3876)
- gyp.exe (PID: 3800)
- gyp.exe (PID: 2744)
- HEUR-Trojan.Win32.Generic-8507bb1cb0f4712a03d3ebb084da330a9ab8eec22f331cf3f1849cd7403aecde..exe (PID: 1744)
- gyp.exe (PID: 3280)
- HEUR-Trojan.Win32.Generic-8493e31df664dff6f41a8376f132fcc9871098ff51fea29453156eb1475bef61..exe (PID: 4076)
- FA81.exe (PID: 3648)
- gyp.exe (PID: 4068)
- gyp.exe (PID: 3972)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 3744)
- HEUR-Trojan.Win32.Generic-8444b2fd287ff2610cddd68665a80d3b372b33b5ec0210c4f50a60af053b150c..exe (PID: 2940)
- gyp.exe (PID: 2072)
- gyp.exe (PID: 2964)
- gyp.exe (PID: 1736)
- gyp.exe (PID: 4032)
- gyp.exe (PID: 1580)
- HEUR-Trojan.Win32.Generic-8399e9ed8b206acdcef6f103794bab682c3e628732c3242841f639008c5340ba..exe (PID: 2564)
- gyp.exe (PID: 1572)
- gyp.exe (PID: 2572)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 3752)
- gyp.exe (PID: 3496)
- gyp.exe (PID: 3100)
- gyp.exe (PID: 3872)
- gyp.exe (PID: 2108)
- gyp.exe (PID: 3960)
- gyp.exe (PID: 944)
- HEUR-Trojan.Win32.Generic-8394dfb52477a7b153a9cdd608826ce0df4166b73244f78486d7ea9cb9792244..exe (PID: 3340)
- HEUR-Trojan.Win32.Generic-8394dfb52477a7b153a9cdd608826ce0df4166b73244f78486d7ea9cb9792244..exe (PID: 3900)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- gyp.exe (PID: 3564)
- HEUR-Trojan.Win32.Generic-8347cb82b5e788c0ae544b44926b8a4f1ba03398b954bd1cac86d7c01db5b9f5..exe (PID: 2300)
- gyp.exe (PID: 2428)
- HEUR-Trojan.Win32.Generic-08394ffe3f87c3b3be04b763677d89783217fedd9a2efb96a436e99172cf441d..exe (PID: 3792)
- gyp.exe (PID: 3984)
- gyp.exe (PID: 2308)
- gyp.exe (PID: 2296)
- gyp.exe (PID: 3968)
- gyp.exe (PID: 2388)
- gyp.exe (PID: 3072)
- gyp.exe (PID: 1948)
- gyp.exe (PID: 3412)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 3128)
- gyp.exe (PID: 3692)
- gyp.exe (PID: 2888)
- gyp.exe (PID: 760)
- gyp.exe (PID: 3912)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 3312)
- gyp.exe (PID: 548)
- gyp.exe (PID: 1776)
- gyp.exe (PID: 3368)
- gyp.exe (PID: 1960)
- gyp.exe (PID: 3088)
- gyp.exe (PID: 2484)
- gyp.exe (PID: 1800)
- gyp.exe (PID: 3408)
- gyp.exe (PID: 820)
- gyp.exe (PID: 2232)
- gyp.exe (PID: 3200)
- gyp.exe (PID: 1488)
- gyp.exe (PID: 1832)
- gyp.exe (PID: 2876)
- gyp.exe (PID: 2584)
- gyp.exe (PID: 2784)
- gyp.exe (PID: 3552)
- gyp.exe (PID: 3720)
- gyp.exe (PID: 2664)
- gyp.exe (PID: 3124)
- gyp.exe (PID: 2536)
- gyp.exe (PID: 3956)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 128)
- gyp.exe (PID: 2532)
- gyp.exe (PID: 2136)
- gyp.exe (PID: 3224)
- gyp.exe (PID: 3216)
- gyp.exe (PID: 2616)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 1180)
- HEUR-Trojan.Win32.Generic-7505bd0fb947ea639d8de22ab6cb296f88ac1687ec7b90df1e4fe1d16aa63ac8..exe (PID: 3772)
- gyp.exe (PID: 872)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 2332)
- gyp.exe (PID: 4048)
- gyp.exe (PID: 2604)
- gyp.exe (PID: 2756)
- gyp.exe (PID: 1504)
- gyp.exe (PID: 3824)
- gyp.exe (PID: 2120)
- gyp.exe (PID: 1848)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 1336)
- gyp.exe (PID: 2736)
- gyp.exe (PID: 3764)
- gyp.exe (PID: 3164)
- gyp.exe (PID: 2324)
- gyp.exe (PID: 3268)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 3788)
- gyp.exe (PID: 3128)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 1844)
- gyp.exe (PID: 1180)
- gyp.exe (PID: 1500)
- gyp.exe (PID: 1124)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 2512)
- HEUR-Trojan.Win32.Generic-7006ca17ff34ba7828f984f28ac634b6cadffe1f94a965ebd8d7523aae0b1c70..exe (PID: 988)
- gyp.exe (PID: 2676)
- gyp.exe (PID: 3424)
- gyp.exe (PID: 3056)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 2712)
- gyp.exe (PID: 1020)
- gyp.exe (PID: 1576)
- gyp.exe (PID: 1156)
- gyp.exe (PID: 3176)
- HEUR-Trojan.Win32.Generic-6992e3b2574f41b2cfefbefc29cb51e8375279e08529404b3a2d10b618320dbf..exe (PID: 2036)
- HEUR-Trojan.Win32.Generic-7001c944da78d9a35e46789eec46d571f9791d138862e42f87fcc5c15da9e540..exe (PID: 1416)
- HEUR-Trojan.Win32.Generic-6991fa7795c5eca907baa44cdb93162fe35c0f1628bdb56822517e71877e0bf9..exe (PID: 3500)
- 9A0D2F91826.exe (PID: 344)
- HEUR-Trojan.Win32.Generic-6963f86855ac1cfd80e79b19c06ab713aa92518fc122b06eb50c5ea537d3e18b..exe (PID: 3740)
- gyp.exe (PID: 2884)
- HEUR-Trojan.Win32.Generic-6931df583187624fd800d8c4348cbeeab8fa523c950a6bab39ca99e32db943a3..exe (PID: 1884)
- gyp.exe (PID: 4032)
- HEUR-Trojan.Win32.Generic-6963f86855ac1cfd80e79b19c06ab713aa92518fc122b06eb50c5ea537d3e18b..exe (PID: 2096)
- gyp.exe (PID: 1864)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 2072)
- HEUR-Trojan.Win32.Generic-6920c0773de587665e13d688a9a0c0913ab889657e77c54afc8058cd0d4fc29e..exe (PID: 740)
- gyp.exe (PID: 752)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 2236)
- HEUR-Trojan.Win32.Generic-6922d9eceea6fdc843b0c2594c09da4bedd7c4a9080c6472b5bac1361c11c6b9..exe (PID: 3272)
- system.exe (PID: 2368)
- gyp.exe (PID: 3108)
- gyp.exe (PID: 3528)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
- system.exe (PID: 284)
- gyp.exe (PID: 5316)
- gyp.exe (PID: 5308)
- gyp.exe (PID: 5344)
- gyp.exe (PID: 5352)
- gyp.exe (PID: 5300)
- B6232F3A826.exe (PID: 5580)
- gyp.exe (PID: 5820)
- gyp.exe (PID: 5896)
- gyp.exe (PID: 5564)
- gyp.exe (PID: 6032)
- gyp.exe (PID: 5624)
- gyp.exe (PID: 3004)
- system.exe (PID: 5796)
- system.exe (PID: 5124)
The sample compiled with russian language support
- 7zFM.exe (PID: 4092)
- 7z2500.exe (PID: 3056)
Reads the computer name
- 7z2500.exe (PID: 3056)
- 7zFM.exe (PID: 4092)
- HEUR-Trojan.Win32.Generic-9412c909c3448441125750d543bfc601cfe33ad4a31470c27918b6a3ed32796f..exe (PID: 2272)
- vbc.exe (PID: 3728)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9269aff1e9ab7517f19e4b47e5d05ec385f59efc9790951fcfb2e100ef7ab175..exe (PID: 3456)
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 1980)
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 3024)
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
- HEUR-Trojan.Win32.Generic-9177d2c0031c53aff941ca7264b8204c2fdec09341f04a09733bf99eb25d12fe..exe (PID: 3232)
- HEUR-Trojan.Win32.Generic-9085f8a76c559da7f3626b70e2de94b5142cd2c8630c9fbd654f73106b1f96c5..exe (PID: 672)
- HEUR-Trojan.Win32.Generic-9142b4b9280b9d0ccb2906d42edd0c9a29ee9399d21dbc5a56869f9ebbea2514..exe (PID: 3516)
- HEUR-Trojan.Win32.Generic-9165bfd840fc2d5b45049c58f7680007235d05c2628bb95e54bcd6877a18d991..exe (PID: 3672)
- HEUR-Trojan.Win32.Generic-9096cd34c8f099659c52b6dfc49b62e25a797fb4ebcc9f9956bb41b2a626f585..exe (PID: 344)
- HEUR-Trojan.Win32.Generic-9090f383d746829072f03748c311808279c52b6cb17ed66584e546304a528067..exe (PID: 1168)
- HEUR-Trojan.Win32.Generic-9067c8411d9138a24167da423db123d337bf7889e0d7f91bc8b46e4987bc5a78..exe (PID: 3396)
- defender.exe (PID: 2828)
- HEUR-Trojan.Win32.Generic-9086fd10fdc222be3b7361f21dc6df536ee6e9dabc50dd169716d5dd2293c19e..exe (PID: 2144)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
- dw20.exe (PID: 4052)
- RuneHack.exe (PID: 3924)
- nA41221ObIgM41221.exe (PID: 1372)
- HEUR-Trojan.Win32.Generic-8969bb7ab1fd45e2355a9674cdfc9085afb1339f7cccd3c1e154341cf6521562..exe (PID: 3644)
- HEUR-Trojan.Win32.Generic-8964d564cda4ecd1351bca67548802fe818c6da7475f0fbf702e0bf543f363b8..exe (PID: 2088)
- HEUR-Trojan.Win32.Generic-8918f5c21c853bc791c65863a01b7f42e47f24c4019b3d82fdda9f2b6adda6e5..exe (PID: 3444)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- vbc.exe (PID: 1028)
- HEUR-Trojan.Win32.Generic-8840f33e1015f6545a747c2917f86af96898ff9ee9f19f1719e573ed8876e4f0..exe (PID: 1924)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2440)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
- HEUR-Trojan.Win32.Generic-8792a3468196865f986758095c7286fc0bdab460c4525de03c88f1b2f4f39ad0..exe (PID: 1060)
- gyp.exe (PID: 3232)
- HEUR-Trojan.Win32.Generic-8789ad5e8b6ef8d6d403425642e13cd57b00827203b1f25a65f33448d0fb389a..exe (PID: 2864)
- gyp.exe (PID: 2992)
- HEUR-Trojan.Win32.Generic-08764e0f3e20057c324a3b9f8a27ce1042288a90a933df2330925169624bc201..exe (PID: 1564)
- gyp.exe (PID: 2720)
- gyp.exe (PID: 3300)
- HEUR-Trojan.Win32.Generic-8796c958e875048e58fa857bbf8d5d07e7b38635e2bdc073dfd83fcbe4438703..exe (PID: 3024)
- gyp.exe (PID: 392)
- gyp.exe (PID: 704)
- gyp.exe (PID: 1380)
- gyp.exe (PID: 2940)
- gyp.exe (PID: 3612)
- nA41221ObIgM41221.exe (PID: 3040)
- gyp.exe (PID: 4008)
- gyp.exe (PID: 2964)
- gyp.exe (PID: 1156)
- HEUR-Trojan.Win32.Generic-8641e1062420633a19c065f0c61b522a072933d482c6ba2f1ca477e9ee1f0ad4..exe (PID: 3840)
- system.exe (PID: 2236)
- gyp.exe (PID: 3740)
- gyp.exe (PID: 4048)
- HEUR-Trojan.Win32.Generic-8629d6b2bc7b0877fc9858784e861eb7728f1475df1bb6b6552437ab68435f33..exe (PID: 2444)
- system.exe (PID: 1572)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 3308)
- gyp.exe (PID: 2436)
- HEUR-Trojan.Win32.Generic-8535e165c3f3452e189fae164f5bab853db4eb7984e28750856c3ff40663df1c..exe (PID: 3876)
- gyp.exe (PID: 3092)
- HEUR-Trojan.Win32.Generic-8535e165c3f3452e189fae164f5bab853db4eb7984e28750856c3ff40663df1c..exe (PID: 2600)
- gyp.exe (PID: 2744)
- gyp.exe (PID: 3264)
- gyp.exe (PID: 3800)
- HEUR-Trojan.Win32.Generic-8493e31df664dff6f41a8376f132fcc9871098ff51fea29453156eb1475bef61..exe (PID: 4076)
- HEUR-Trojan.Win32.Generic-8507bb1cb0f4712a03d3ebb084da330a9ab8eec22f331cf3f1849cd7403aecde..exe (PID: 1744)
- gyp.exe (PID: 3280)
- gyp.exe (PID: 4068)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 3744)
- gyp.exe (PID: 3972)
- gyp.exe (PID: 2072)
- HEUR-Trojan.Win32.Generic-8399e9ed8b206acdcef6f103794bab682c3e628732c3242841f639008c5340ba..exe (PID: 2564)
- gyp.exe (PID: 4032)
- FA81.exe (PID: 3648)
- gyp.exe (PID: 1580)
- gyp.exe (PID: 1572)
- gyp.exe (PID: 3872)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 2108)
- gyp.exe (PID: 2572)
- gyp.exe (PID: 3564)
- gyp.exe (PID: 3960)
- gyp.exe (PID: 3752)
- gyp.exe (PID: 944)
- gyp.exe (PID: 3100)
- gyp.exe (PID: 3496)
- gyp.exe (PID: 2428)
- gyp.exe (PID: 3072)
- gyp.exe (PID: 3412)
- gyp.exe (PID: 3984)
- gyp.exe (PID: 1948)
- gyp.exe (PID: 3968)
- gyp.exe (PID: 2296)
- gyp.exe (PID: 2308)
- gyp.exe (PID: 2388)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 3912)
- gyp.exe (PID: 760)
- gyp.exe (PID: 3692)
- gyp.exe (PID: 1960)
- gyp.exe (PID: 3368)
- gyp.exe (PID: 548)
- gyp.exe (PID: 2484)
- gyp.exe (PID: 1776)
- gyp.exe (PID: 3088)
- gyp.exe (PID: 3312)
- gyp.exe (PID: 1800)
- gyp.exe (PID: 820)
- gyp.exe (PID: 3408)
- gyp.exe (PID: 2232)
- gyp.exe (PID: 3200)
- gyp.exe (PID: 1488)
- gyp.exe (PID: 1832)
- gyp.exe (PID: 2876)
- gyp.exe (PID: 2584)
- gyp.exe (PID: 2784)
- gyp.exe (PID: 3552)
- gyp.exe (PID: 2536)
- gyp.exe (PID: 3124)
- gyp.exe (PID: 3720)
- gyp.exe (PID: 128)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 3956)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 2136)
- gyp.exe (PID: 2532)
- gyp.exe (PID: 3216)
- gyp.exe (PID: 872)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 1180)
- gyp.exe (PID: 2616)
- gyp.exe (PID: 3224)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 2332)
- gyp.exe (PID: 1504)
- gyp.exe (PID: 2604)
- gyp.exe (PID: 2756)
- gyp.exe (PID: 4048)
- gyp.exe (PID: 3824)
- gyp.exe (PID: 2120)
- gyp.exe (PID: 1848)
- gyp.exe (PID: 2324)
- gyp.exe (PID: 2736)
- gyp.exe (PID: 3764)
- gyp.exe (PID: 3164)
- gyp.exe (PID: 3268)
- gyp.exe (PID: 1844)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 3128)
- gyp.exe (PID: 1180)
- gyp.exe (PID: 1500)
- gyp.exe (PID: 1124)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 2512)
- gyp.exe (PID: 3056)
- gyp.exe (PID: 2676)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 3424)
- gyp.exe (PID: 2712)
- gyp.exe (PID: 1576)
- gyp.exe (PID: 1020)
- gyp.exe (PID: 1156)
- gyp.exe (PID: 3176)
- HEUR-Trojan.Win32.Generic-7006ca17ff34ba7828f984f28ac634b6cadffe1f94a965ebd8d7523aae0b1c70..exe (PID: 988)
- gyp.exe (PID: 2884)
- gyp.exe (PID: 4032)
- gyp.exe (PID: 1864)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 2072)
- gyp.exe (PID: 3528)
- gyp.exe (PID: 752)
- gyp.exe (PID: 3108)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 2236)
- 9A0D2F91826.exe (PID: 344)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
- system.exe (PID: 2368)
- system.exe (PID: 284)
- HEUR-Trojan.Win32.Generic-6920c0773de587665e13d688a9a0c0913ab889657e77c54afc8058cd0d4fc29e..exe (PID: 740)
- HEUR-Trojan.Win32.Generic-6963f86855ac1cfd80e79b19c06ab713aa92518fc122b06eb50c5ea537d3e18b..exe (PID: 3740)
- gyp.exe (PID: 5820)
- gyp.exe (PID: 5896)
- gyp.exe (PID: 6032)
- B6232F3A826.exe (PID: 5580)
- HEUR-Trojan.Win32.Generic-6922d9eceea6fdc843b0c2594c09da4bedd7c4a9080c6472b5bac1361c11c6b9..exe (PID: 3272)
- HEUR-Trojan.Win32.Generic-6931df583187624fd800d8c4348cbeeab8fa523c950a6bab39ca99e32db943a3..exe (PID: 1884)
- gyp.exe (PID: 5624)
- gyp.exe (PID: 3004)
- system.exe (PID: 5796)
- system.exe (PID: 5124)
Manual execution by a user
- 7zFM.exe (PID: 4092)
- cmd.exe (PID: 580)
- HEUR-Trojan.Win32.Generic-9391c23c1d6f599a85f08b8b8bd34b02119049da669962d16773c1dd2c0e0fde..exe (PID: 1120)
- HEUR-Trojan.Win32.Generic-9412c909c3448441125750d543bfc601cfe33ad4a31470c27918b6a3ed32796f..exe (PID: 2272)
- HEUR-Trojan.Win32.Generic-9356e380f6da9efb80d2a8f6417aef094c9e46abe3f30065d1f2e48d3814e4f2..exe (PID: 3928)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2112)
- HEUR-Trojan.Win32.Generic-9289d5a5494d04e0d6e092bf5289a63a5b080a0792bf902394c102c2cd79b95a..exe (PID: 3812)
- HEUR-Trojan.Win32.Generic-9375c6293126d57dc2f846b766e410a178f22beef9bdc576e3bcc30f04958e36..exe (PID: 3184)
- HEUR-Trojan.Win32.Generic-9371d4f137b3a7ea0ea83654828eb66192adf99c4a5fea4aeb92789e450d9831..exe (PID: 3872)
- HEUR-Trojan.Win32.Generic-9269aff1e9ab7517f19e4b47e5d05ec385f59efc9790951fcfb2e100ef7ab175..exe (PID: 3456)
- HEUR-Trojan.Win32.Generic-9280a1ecaff98076cfdd98083535a371148879b12a8c55463ec3bb62f98de0a1..exe (PID: 3772)
- HEUR-Trojan.Win32.Generic-9259c75a3ce10d8c97c42505fd4057fe42911c1189bd2629f872ce5e10c5700e..exe (PID: 2868)
- HEUR-Trojan.Win32.Generic-9229df14951e496a7a57b910ac25c7d3413c282b37b2dbc0ff00b8f4a89c6dd1..exe (PID: 3000)
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 1980)
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
- HEUR-Trojan.Win32.Generic-9191ae6eb7e7c960afdee1815853b664710eb9c578eb293130147c25c92f650f..exe (PID: 1584)
- HEUR-Trojan.Win32.Generic-9177d2c0031c53aff941ca7264b8204c2fdec09341f04a09733bf99eb25d12fe..exe (PID: 3232)
- HEUR-Trojan.Win32.Generic-9176ae2b2804002b00ce55eefdc4dd97eb34aab7031ae43c13cbfa9921c3eb46..exe (PID: 2624)
- HEUR-Trojan.Win32.Generic-9165bfd840fc2d5b45049c58f7680007235d05c2628bb95e54bcd6877a18d991..exe (PID: 3672)
- HEUR-Trojan.Win32.Generic-9162c1643afeaf61ed44aebae58797a26d5b94e85d84311e719736fa03153c34..exe (PID: 2084)
- HEUR-Trojan.Win32.Generic-9090f383d746829072f03748c311808279c52b6cb17ed66584e546304a528067..exe (PID: 1168)
- HEUR-Trojan.Win32.Generic-9086fd10fdc222be3b7361f21dc6df536ee6e9dabc50dd169716d5dd2293c19e..exe (PID: 2144)
- HEUR-Trojan.Win32.Generic-9085f8a76c559da7f3626b70e2de94b5142cd2c8630c9fbd654f73106b1f96c5..exe (PID: 672)
- HEUR-Trojan.Win32.Generic-9142b4b9280b9d0ccb2906d42edd0c9a29ee9399d21dbc5a56869f9ebbea2514..exe (PID: 3516)
- HEUR-Trojan.Win32.Generic-9096cd34c8f099659c52b6dfc49b62e25a797fb4ebcc9f9956bb41b2a626f585..exe (PID: 344)
- HEUR-Trojan.Win32.Generic-9082eaeb6b865e352e1eef8f4cbb7c290a47ef2781b57a0b0b82d0db7b8dc21c..exe (PID: 524)
- HEUR-Trojan.Win32.Generic-9063ab88dba834f74760b613da46b858441e18b02c1ebc80744f7454e26272b2..exe (PID: 2936)
- HEUR-Trojan.Win32.Generic-9059d7ffc25e712afce102c8287e13df2ceb47898da61e84f8412a1ac6744bd0..exe (PID: 1272)
- HEUR-Trojan.Win32.Generic-9084b67f13f1d3561ea0ed1ca145d70a2e4dfb3cd0e1e76661f8f8f1daaa5f3b..exe (PID: 2992)
- HEUR-Trojan.Win32.Generic-9067c8411d9138a24167da423db123d337bf7889e0d7f91bc8b46e4987bc5a78..exe (PID: 3396)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2480)
- HEUR-Trojan.Win32.Generic-8969bb7ab1fd45e2355a9674cdfc9085afb1339f7cccd3c1e154341cf6521562..exe (PID: 3644)
- HEUR-Trojan.Win32.Generic-8943b14b23f23a5cdd1a1e1d21a855e64826c67e163fa2ff97e712086ad609f0..exe (PID: 3896)
- HEUR-Trojan.Win32.Generic-08920c9d18793fa9b072cc8582475d5df5df0d13c0d9cde36231d8da19670273..exe (PID: 1928)
- HEUR-Trojan.Win32.Generic-8958cc492cbb582da9d3e18c45d34e164cf792698e7c35c9451428285f372f38..exe (PID: 3752)
- HEUR-Trojan.Win32.Generic-8964d564cda4ecd1351bca67548802fe818c6da7475f0fbf702e0bf543f363b8..exe (PID: 2088)
- HEUR-Trojan.Win32.Generic-8916d140c0132a93cf5e5272fb314799bb3e80214d2073fdad03155a56679e9b..exe (PID: 2464)
- HEUR-Trojan.Win32.Generic-8918f5c21c853bc791c65863a01b7f42e47f24c4019b3d82fdda9f2b6adda6e5..exe (PID: 3444)
- HEUR-Trojan.Win32.Generic-8844a0d8e92b4ce20257be7a119f760326dc272479144315e4d05e778119e802..exe (PID: 3684)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- HEUR-Trojan.Win32.Generic-8840f33e1015f6545a747c2917f86af96898ff9ee9f19f1719e573ed8876e4f0..exe (PID: 1924)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
- HEUR-Trojan.Win32.Generic-8796c958e875048e58fa857bbf8d5d07e7b38635e2bdc073dfd83fcbe4438703..exe (PID: 3024)
- HEUR-Trojan.Win32.Generic-8792a3468196865f986758095c7286fc0bdab460c4525de03c88f1b2f4f39ad0..exe (PID: 1060)
- HEUR-Trojan.Win32.Generic-8789ad5e8b6ef8d6d403425642e13cd57b00827203b1f25a65f33448d0fb389a..exe (PID: 2864)
- gyp.exe (PID: 2992)
- gyp.exe (PID: 3232)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 392)
- gyp.exe (PID: 3612)
- gyp.exe (PID: 2964)
- gyp.exe (PID: 1380)
- gyp.exe (PID: 4008)
- gyp.exe (PID: 1156)
- gyp.exe (PID: 4048)
- gyp.exe (PID: 3740)
- gyp.exe (PID: 2612)
- gyp.exe (PID: 2488)
- gyp.exe (PID: 3248)
- gyp.exe (PID: 3892)
- gyp.exe (PID: 3656)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 3808)
- gyp.exe (PID: 2764)
- gyp.exe (PID: 1624)
- gyp.exe (PID: 3308)
- gyp.exe (PID: 3092)
- gyp.exe (PID: 2436)
- gyp.exe (PID: 672)
- gyp.exe (PID: 2744)
- gyp.exe (PID: 3800)
- gyp.exe (PID: 3280)
- gyp.exe (PID: 4068)
- gyp.exe (PID: 3744)
- gyp.exe (PID: 3972)
- gyp.exe (PID: 2072)
- gyp.exe (PID: 2964)
- gyp.exe (PID: 4032)
- gyp.exe (PID: 1580)
- gyp.exe (PID: 1736)
- gyp.exe (PID: 2572)
- gyp.exe (PID: 3564)
- gyp.exe (PID: 3872)
- gyp.exe (PID: 2108)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 1572)
- gyp.exe (PID: 944)
- gyp.exe (PID: 3752)
- gyp.exe (PID: 3496)
- gyp.exe (PID: 3100)
- gyp.exe (PID: 3412)
- gyp.exe (PID: 3072)
- gyp.exe (PID: 1948)
- gyp.exe (PID: 3984)
- gyp.exe (PID: 2308)
- gyp.exe (PID: 2296)
- gyp.exe (PID: 3968)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 760)
- gyp.exe (PID: 2888)
- gyp.exe (PID: 3912)
- gyp.exe (PID: 2388)
- gyp.exe (PID: 3692)
- gyp.exe (PID: 3252)
- gyp.exe (PID: 3280)
- gyp.exe (PID: 3012)
- gyp.exe (PID: 1776)
- gyp.exe (PID: 1960)
- gyp.exe (PID: 3368)
- gyp.exe (PID: 1800)
- gyp.exe (PID: 3312)
- gyp.exe (PID: 548)
- gyp.exe (PID: 3088)
- gyp.exe (PID: 4044)
- gyp.exe (PID: 2484)
- gyp.exe (PID: 3408)
- gyp.exe (PID: 820)
- gyp.exe (PID: 2232)
- gyp.exe (PID: 1488)
- gyp.exe (PID: 1832)
- gyp.exe (PID: 3200)
- gyp.exe (PID: 2876)
- gyp.exe (PID: 2584)
- gyp.exe (PID: 2784)
- gyp.exe (PID: 3552)
- gyp.exe (PID: 3720)
- gyp.exe (PID: 2724)
- gyp.exe (PID: 3556)
- gyp.exe (PID: 1980)
- gyp.exe (PID: 1272)
- gyp.exe (PID: 1936)
- gyp.exe (PID: 1332)
- gyp.exe (PID: 1484)
- gyp.exe (PID: 1656)
- gyp.exe (PID: 128)
- gyp.exe (PID: 2664)
- gyp.exe (PID: 2536)
- gyp.exe (PID: 3956)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 3216)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 2532)
- gyp.exe (PID: 872)
- gyp.exe (PID: 3224)
- gyp.exe (PID: 2136)
- gyp.exe (PID: 2616)
- gyp.exe (PID: 2756)
- gyp.exe (PID: 2604)
- gyp.exe (PID: 1504)
- gyp.exe (PID: 4048)
- gyp.exe (PID: 3824)
- gyp.exe (PID: 1848)
- gyp.exe (PID: 2120)
- gyp.exe (PID: 3764)
- gyp.exe (PID: 3164)
- gyp.exe (PID: 2468)
- gyp.exe (PID: 1380)
- gyp.exe (PID: 2324)
- gyp.exe (PID: 2736)
- gyp.exe (PID: 3268)
- gyp.exe (PID: 2772)
- gyp.exe (PID: 1604)
- gyp.exe (PID: 3128)
- gyp.exe (PID: 3768)
- gyp.exe (PID: 2204)
- gyp.exe (PID: 1844)
- gyp.exe (PID: 1124)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 1180)
- gyp.exe (PID: 1500)
- gyp.exe (PID: 3056)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 2512)
- gyp.exe (PID: 3424)
Reads the Internet Settings
- explorer.exe (PID: 1452)
- explorer.exe (PID: 2312)
- explorer.exe (PID: 3508)
- explorer.exe (PID: 3844)
- explorer.exe (PID: 3320)
- explorer.exe (PID: 3504)
The sample compiled with Italian language support
- 7zFM.exe (PID: 4092)
The sample compiled with czech language support
- 7zFM.exe (PID: 4092)
The sample compiled with turkish language support
- 7zFM.exe (PID: 4092)
The sample compiled with portuguese language support
- 7zFM.exe (PID: 4092)
The sample compiled with polish language support
- 7zFM.exe (PID: 4092)
The sample compiled with spanish language support
- 7zFM.exe (PID: 4092)
The sample compiled with korean language support
- 7zFM.exe (PID: 4092)
The sample compiled with chinese language support
- 7zFM.exe (PID: 4092)
The sample compiled with german language support
- 7zFM.exe (PID: 4092)
Reads the machine GUID from the registry
- HEUR-Trojan.Win32.Generic-9412c909c3448441125750d543bfc601cfe33ad4a31470c27918b6a3ed32796f..exe (PID: 2272)
- HEUR-Trojan.Win32.Generic-9391c23c1d6f599a85f08b8b8bd34b02119049da669962d16773c1dd2c0e0fde..exe (PID: 1120)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 1980)
- RuneHack.exe (PID: 3924)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
- defender.exe (PID: 2828)
- HEUR-Trojan.Win32.Generic-8964d564cda4ecd1351bca67548802fe818c6da7475f0fbf702e0bf543f363b8..exe (PID: 2088)
- HEUR-Trojan.Win32.Generic-8840f33e1015f6545a747c2917f86af96898ff9ee9f19f1719e573ed8876e4f0..exe (PID: 1924)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
- HEUR-Trojan.Win32.Generic-8792a3468196865f986758095c7286fc0bdab460c4525de03c88f1b2f4f39ad0..exe (PID: 1060)
- HEUR-Trojan.Win32.Generic-9300d6b3aa972e79da286df5b1cb3345529cf2d1cbf09c2e7f7e38e096e48ac5..exe (PID: 2440)
- gyp.exe (PID: 2940)
- system.exe (PID: 2236)
- HEUR-Trojan.Win32.Generic-8641e1062420633a19c065f0c61b522a072933d482c6ba2f1ca477e9ee1f0ad4..exe (PID: 3840)
- HEUR-Trojan.Win32.Generic-8629d6b2bc7b0877fc9858784e861eb7728f1475df1bb6b6552437ab68435f33..exe (PID: 2444)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 2236)
- system.exe (PID: 2368)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 2072)
- system.exe (PID: 5796)
- gyp.exe (PID: 5624)
Create files in a temporary directory
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9244dcc1c02a21cc94ebca28bd2a9d0c6a0dd070186c0929d73af105edc91153..exe (PID: 3024)
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
- HEUR-Trojan.Win32.Generic-9096cd34c8f099659c52b6dfc49b62e25a797fb4ebcc9f9956bb41b2a626f585..exe (PID: 344)
- HEUR-Trojan.Win32.Generic-9142b4b9280b9d0ccb2906d42edd0c9a29ee9399d21dbc5a56869f9ebbea2514..exe (PID: 3516)
- HEUR-Trojan.Win32.Generic-9055becec457a46a9280c07ea1f4f5edf38be463d4fc5356b1626694257d9a73..exe (PID: 2856)
- defender.exe (PID: 2828)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- vbc.exe (PID: 1028)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
- gyp.exe (PID: 3232)
- gyp.exe (PID: 2992)
- gyp.exe (PID: 2720)
- HEUR-Trojan.Win32.Generic-08764e0f3e20057c324a3b9f8a27ce1042288a90a933df2330925169624bc201..exe (PID: 1564)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 704)
- gyp.exe (PID: 392)
- gyp.exe (PID: 2940)
- gyp.exe (PID: 3612)
- gyp.exe (PID: 1380)
- gyp.exe (PID: 2964)
- gyp.exe (PID: 4008)
- gyp.exe (PID: 1156)
- HEUR-Trojan.Win32.Generic-8641e1062420633a19c065f0c61b522a072933d482c6ba2f1ca477e9ee1f0ad4..exe (PID: 3840)
- system.exe (PID: 1572)
- gyp.exe (PID: 3740)
- gyp.exe (PID: 4048)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 3308)
- gyp.exe (PID: 2436)
- gyp.exe (PID: 3092)
- gyp.exe (PID: 3800)
- gyp.exe (PID: 2744)
- gyp.exe (PID: 3264)
- HEUR-Trojan.Win32.Generic-8493e31df664dff6f41a8376f132fcc9871098ff51fea29453156eb1475bef61..exe (PID: 4076)
- HEUR-Trojan.Win32.Generic-8507bb1cb0f4712a03d3ebb084da330a9ab8eec22f331cf3f1849cd7403aecde..exe (PID: 1744)
- gyp.exe (PID: 3280)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 4068)
- gyp.exe (PID: 3972)
- gyp.exe (PID: 2072)
- gyp.exe (PID: 3744)
- gyp.exe (PID: 4032)
- FA81.exe (PID: 3648)
- gyp.exe (PID: 1580)
- gyp.exe (PID: 1572)
- gyp.exe (PID: 2108)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 2572)
- gyp.exe (PID: 3872)
- gyp.exe (PID: 3496)
- gyp.exe (PID: 3752)
- gyp.exe (PID: 3960)
- gyp.exe (PID: 3100)
- gyp.exe (PID: 3564)
- gyp.exe (PID: 944)
- gyp.exe (PID: 2428)
- gyp.exe (PID: 3412)
- gyp.exe (PID: 3072)
- HEUR-Trojan.Win32.Generic-08394ffe3f87c3b3be04b763677d89783217fedd9a2efb96a436e99172cf441d..exe (PID: 3792)
- gyp.exe (PID: 3984)
- gyp.exe (PID: 3968)
- gyp.exe (PID: 2308)
- gyp.exe (PID: 2296)
- gyp.exe (PID: 3912)
- gyp.exe (PID: 1948)
- gyp.exe (PID: 2388)
- gyp.exe (PID: 3180)
- gyp.exe (PID: 2888)
- gyp.exe (PID: 760)
- gyp.exe (PID: 3692)
- gyp.exe (PID: 2484)
- gyp.exe (PID: 3368)
- gyp.exe (PID: 548)
- gyp.exe (PID: 1776)
- gyp.exe (PID: 3312)
- gyp.exe (PID: 3088)
- gyp.exe (PID: 1960)
- gyp.exe (PID: 1800)
- gyp.exe (PID: 820)
- gyp.exe (PID: 3408)
- gyp.exe (PID: 3200)
- gyp.exe (PID: 1488)
- gyp.exe (PID: 1832)
- gyp.exe (PID: 2876)
- gyp.exe (PID: 2232)
- gyp.exe (PID: 2584)
- gyp.exe (PID: 2784)
- gyp.exe (PID: 3720)
- gyp.exe (PID: 3552)
- gyp.exe (PID: 2536)
- gyp.exe (PID: 2664)
- gyp.exe (PID: 3124)
- gyp.exe (PID: 128)
- gyp.exe (PID: 3956)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 2588)
- gyp.exe (PID: 2532)
- gyp.exe (PID: 3216)
- gyp.exe (PID: 2136)
- gyp.exe (PID: 3224)
- gyp.exe (PID: 872)
- gyp.exe (PID: 2616)
- gyp.exe (PID: 4048)
- gyp.exe (PID: 1504)
- gyp.exe (PID: 2604)
- gyp.exe (PID: 2756)
- gyp.exe (PID: 3824)
- gyp.exe (PID: 1848)
- gyp.exe (PID: 2120)
- gyp.exe (PID: 2324)
- gyp.exe (PID: 3764)
- gyp.exe (PID: 3164)
- gyp.exe (PID: 2736)
- gyp.exe (PID: 3268)
- gyp.exe (PID: 1844)
- gyp.exe (PID: 1124)
- gyp.exe (PID: 3128)
- gyp.exe (PID: 3300)
- gyp.exe (PID: 1180)
- gyp.exe (PID: 1840)
- gyp.exe (PID: 3056)
- gyp.exe (PID: 1500)
- gyp.exe (PID: 2512)
- gyp.exe (PID: 2676)
- gyp.exe (PID: 3424)
- gyp.exe (PID: 1116)
- gyp.exe (PID: 2712)
- gyp.exe (PID: 1020)
- gyp.exe (PID: 1576)
- gyp.exe (PID: 1156)
- gyp.exe (PID: 3176)
- gyp.exe (PID: 2884)
- gyp.exe (PID: 4032)
- gyp.exe (PID: 3528)
- gyp.exe (PID: 752)
- gyp.exe (PID: 1864)
- gyp.exe (PID: 3108)
- system.exe (PID: 284)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
- gyp.exe (PID: 5820)
- gyp.exe (PID: 6032)
- gyp.exe (PID: 5896)
- gyp.exe (PID: 5624)
- gyp.exe (PID: 3004)
- system.exe (PID: 5124)
Creates files or folders in the user directory
- vbc.exe (PID: 3728)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9177d2c0031c53aff941ca7264b8204c2fdec09341f04a09733bf99eb25d12fe..exe (PID: 3232)
- HEUR-Trojan.Win32.Generic-9176ae2b2804002b00ce55eefdc4dd97eb34aab7031ae43c13cbfa9921c3eb46..exe (PID: 2624)
- HEUR-Trojan.Win32.Generic-9142b4b9280b9d0ccb2906d42edd0c9a29ee9399d21dbc5a56869f9ebbea2514..exe (PID: 3516)
- RuneHack.exe (PID: 3924)
- sysprep.exe (PID: 3404)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- HEUR-Trojan.Win32.Generic-8805fd6a8f953a3acf2a725e9b77511d7ef567269099baac2e8d28edcfe05eb6..exe (PID: 2972)
- HEUR-Trojan.Win32.Generic-8792a3468196865f986758095c7286fc0bdab460c4525de03c88f1b2f4f39ad0..exe (PID: 1060)
- HEUR-Trojan.Win32.Generic-8629d6b2bc7b0877fc9858784e861eb7728f1475df1bb6b6552437ab68435f33..exe (PID: 2444)
- HEUR-Trojan.Win32.Generic-8493e31df664dff6f41a8376f132fcc9871098ff51fea29453156eb1475bef61..exe (PID: 4076)
- HEUR-Trojan.Win32.Generic-8394dfb52477a7b153a9cdd608826ce0df4166b73244f78486d7ea9cb9792244..exe (PID: 3340)
- HEUR-Trojan.Win32.Generic-8394dfb52477a7b153a9cdd608826ce0df4166b73244f78486d7ea9cb9792244..exe (PID: 3900)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- sysprep.exe (PID: 2708)
- sysprep.exe (PID: 3780)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 3788)
- HEUR-Trojan.Win32.Generic-7417ed899390881c0e43965095d908b9f2dbb46caf4be8c91a912153a74bbc9e..exe (PID: 1336)
- sysprep.exe (PID: 2112)
- sysprep.exe (PID: 2364)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6922d9eceea6fdc843b0c2594c09da4bedd7c4a9080c6472b5bac1361c11c6b9..exe (PID: 3272)
- WerFault.exe (PID: 5204)
- WerFault.exe (PID: 4248)
Launching a file from a Registry key
- HEUR-Trojan.Win32.Generic-9280a1ecaff98076cfdd98083535a371148879b12a8c55463ec3bb62f98de0a1..exe (PID: 3772)
- svchost.exe (PID: 2796)
- HEUR-Trojan.Win32.Generic-9067c8411d9138a24167da423db123d337bf7889e0d7f91bc8b46e4987bc5a78..exe (PID: 3396)
- HEUR-Trojan.Win32.Generic-9085f8a76c559da7f3626b70e2de94b5142cd2c8630c9fbd654f73106b1f96c5..exe (PID: 672)
- nA41221ObIgM41221.exe (PID: 1372)
- HEUR-Trojan.Win32.Generic-8867fddb7b10545f2a22b3564beb2d04bd5e1de931fb6b333dc3b399d9865d9b..exe (PID: 2544)
- defender.exe (PID: 2828)
- nA41221ObIgM41221.exe (PID: 3040)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- HEUR-Trojan.Win32.Generic-6931df583187624fd800d8c4348cbeeab8fa523c950a6bab39ca99e32db943a3..exe (PID: 1884)
- explorer.exe (PID: 1452)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
Checks proxy server information
- HEUR-Trojan.Win32.Generic-9269aff1e9ab7517f19e4b47e5d05ec385f59efc9790951fcfb2e100ef7ab175..exe (PID: 3456)
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
- HEUR-Trojan.Win32.Generic-9165bfd840fc2d5b45049c58f7680007235d05c2628bb95e54bcd6877a18d991..exe (PID: 3672)
- HEUR-Trojan.Win32.Generic-9142b4b9280b9d0ccb2906d42edd0c9a29ee9399d21dbc5a56869f9ebbea2514..exe (PID: 3516)
- HEUR-Trojan.Win32.Generic-9086fd10fdc222be3b7361f21dc6df536ee6e9dabc50dd169716d5dd2293c19e..exe (PID: 2144)
- HEUR-Trojan.Win32.Generic-9067c8411d9138a24167da423db123d337bf7889e0d7f91bc8b46e4987bc5a78..exe (PID: 3396)
- nA41221ObIgM41221.exe (PID: 1372)
- nA41221ObIgM41221.exe (PID: 3040)
- HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe (PID: 1036)
- dllhost.exe (PID: 4916)
Disables trace logs
- HEUR-Trojan.Win32.Generic-9314ecbe3e93ab923b26db3d556b735317eb757139c14f25c3ae0f056506970c..exe (PID: 2420)
Failed to create an executable file in Windows directory
- HEUR-Trojan.Win32.Generic-9194db85f2d2fa871997a8ce78d0469727f06770c5fad17f193a9918d338b6ea..exe (PID: 1092)
- HEUR-Trojan.Win32.Generic-8969bb7ab1fd45e2355a9674cdfc9085afb1339f7cccd3c1e154341cf6521562..exe (PID: 3644)
- HEUR-Trojan.Win32.Generic-8918f5c21c853bc791c65863a01b7f42e47f24c4019b3d82fdda9f2b6adda6e5..exe (PID: 3444)
- HEUR-Trojan.Win32.Generic-8493e31df664dff6f41a8376f132fcc9871098ff51fea29453156eb1475bef61..exe (PID: 4076)
- HEUR-Trojan.Win32.Generic-8399e9ed8b206acdcef6f103794bab682c3e628732c3242841f639008c5340ba..exe (PID: 2564)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
Checks transactions between databases Windows and Oracle
- explorer.exe (PID: 2312)
- explorer.exe (PID: 3844)
- explorer.exe (PID: 3508)
- explorer.exe (PID: 3504)
- explorer.exe (PID: 3320)
Reads Environment values
- RuneHack.exe (PID: 3924)
- HEUR-Trojan.Win32.Generic-8840f33e1015f6545a747c2917f86af96898ff9ee9f19f1719e573ed8876e4f0..exe (PID: 1924)
Compiled with Borland Delphi (YARA)
- dllhost.exe (PID: 2800)
- HEUR-Trojan.Win32.Generic-9412c909c3448441125750d543bfc601cfe33ad4a31470c27918b6a3ed32796f..exe (PID: 2272)
- svchost.exe (PID: 2796)
- defender.exe (PID: 2828)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- svchost.exe (PID: 2796)
UPX packer has been detected
- svchost.exe (PID: 2796)
- HEUR-Trojan.Win32.Generic-6931df583187624fd800d8c4348cbeeab8fa523c950a6bab39ca99e32db943a3..exe (PID: 1884)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 1744)
- HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe (PID: 3384)
- HEUR-Trojan.Win32.Generic-6920c0773de587665e13d688a9a0c0913ab889657e77c54afc8058cd0d4fc29e..exe (PID: 740)
Mpress packer has been detected
- defender.exe (PID: 2828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(2828) defender.exe
Decrypted-URLs (7)http://billpaygateway.com/support.php
http://licence24online.com/activate/activate.php?id=%uid%&
http://licence24online.com/activate/activate.php?id=%uid%&mail=%email%&order_id=%order%
http://mww-protection.com/buynow.php?bid=48
http://mww-protection.com/support.html
http://soft-4download.com/404.php?id=48
http://sp-protection.com/
(PID) Process(1744) HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe
Decrypted-URLs (1)http://www.server.com/sqlite3.dll
(PID) Process(3384) HEUR-Trojan.Win32.Generic-6930ba87a54756f7516007e0dae3217eb994ec44a8a0daaa9a37f89d4240f88e..exe
Decrypted-URLs (1)http://www.server.com/sqlite3.dll
Total processes
464
Monitored processes
363
Malicious processes
31
Suspicious processes
33
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=3844 --field-trial-handle=1368,i,5794656408797037170,5356790748642057879,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 128 | "C:\Users\admin\AppData\Local\gyp.exe" -a "C:\Users\admin\Desktop\heur\HEUR-Trojan.Win32.Generic-7444f4603765a665753fefbaecb73ed5faabe2023f7de34fab7e8ec224b64c42..exe" | C:\Users\admin\AppData\Local\gyp.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Gemplus Cryptographic Service Provider Exit code: 0 Version: 5.1.2522.0 (main.010719-1909) Modules
| |||||||||||||||
| 284 | "C:\Users\admin\AppData\Roaming\InstallDir\system.exe" | C:\Users\admin\AppData\Roaming\InstallDir\system.exe | — | system.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 292 | taskeng.exe {665B2EB3-4094-4F5C-9CFD-B00E6B5BA3D1} | C:\Windows\System32\taskeng.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 344 | "C:\Users\admin\Desktop\heur\HEUR-Trojan.Win32.Generic-9096cd34c8f099659c52b6dfc49b62e25a797fb4ebcc9f9956bb41b2a626f585..exe" | C:\Users\admin\Desktop\heur\HEUR-Trojan.Win32.Generic-9096cd34c8f099659c52b6dfc49b62e25a797fb4ebcc9f9956bb41b2a626f585..exe | — | explorer.exe | |||||||||||
User: admin Company: asasasas Integrity Level: MEDIUM Description: asasasa Exit code: 0 Version: 3.05.0009 Modules
| |||||||||||||||
| 344 | "C:\config.Bin\9A0D2F91826.exe" | C:\config.Bin\9A0D2F91826.exe | explorer.exe | ||||||||||||
User: admin Company: AVM GmbH Integrity Level: MEDIUM Description: Loon Gang Adler Exit code: 0 Version: 9.9 Modules
| |||||||||||||||
| 392 | "C:\Users\admin\AppData\Local\gyp.exe" -a "C:\Users\admin\Desktop\heur\HEUR-Trojan.Win32.Generic-8702c07d36d27e91f94b20a2147cda31f1d918fb9dc43dfc84f9a28d241170fc..exe" | C:\Users\admin\AppData\Local\gyp.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Gemplus Cryptographic Service Provider Exit code: 0 Version: 5.1.2522.0 (main.010719-1909) Modules
| |||||||||||||||
| 524 | "C:\Users\admin\Desktop\heur\HEUR-Trojan.Win32.Generic-9082eaeb6b865e352e1eef8f4cbb7c290a47ef2781b57a0b0b82d0db7b8dc21c..exe" | C:\Users\admin\Desktop\heur\HEUR-Trojan.Win32.Generic-9082eaeb6b865e352e1eef8f4cbb7c290a47ef2781b57a0b0b82d0db7b8dc21c..exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\gyp.exe" -a "C:\Users\admin\Desktop\heur\HEUR-Trojan.Win32.Generic-7790ce2450044c34945164bfac2eb52541f3bb419d37713dcf0817c37ba8cbe4..exe" | C:\Users\admin\AppData\Local\gyp.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Gemplus Cryptographic Service Provider Exit code: 0 Version: 5.1.2522.0 (main.010719-1909) Modules
| |||||||||||||||
| 556 | svchost.exe | C:\Windows\System32\svchost.exe | HEUR-Trojan.Win32.Generic-9063ab88dba834f74760b613da46b858441e18b02c1ebc80744f7454e26272b2..exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
307 963
Read events
305 190
Write events
2 586
Delete events
187
Modification events
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: A0014E0106982F00 | |||
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 1 | |||
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 1 | |||
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\IEToEdge |
| Operation: | delete value | Name: | DisabledPendingAutoUpdateConsent |
Value: | |||
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: D4DA6D5AB446 | |||
| (PID) Process: | (2932) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
1 065
Suspicious files
770
Text files
163
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18144e.TMP | — | |
MD5:— | SHA256:— | |||
| 2932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF18146d.TMP | — | |
MD5:— | SHA256:— | |||
| 2932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1814bb.TMP | — | |
MD5:— | SHA256:— | |||
| 2932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:C612E96CBFAC63232FC2062E15600FB1 | SHA256:DB3C05D5EC0B6719A73E7F0BE84BCE9342772DA70567E7CE08CF6573480B38FF | |||
| 2932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:61FE7896F9494DCDF53480A325F4FB85 | SHA256:ACFD3CD36E0DFCF1DCB67C7F31F2A5B9BA0815528A0C604D4330DFAA9E683E51 | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma~RF1812c7.TMP | binary | |
MD5:C612E96CBFAC63232FC2062E15600FB1 | SHA256:DB3C05D5EC0B6719A73E7F0BE84BCE9342772DA70567E7CE08CF6573480B38FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
92
DNS requests
127
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1036 | HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe | GET | — | 142.250.186.132:80 | http://www.google.com/ | unknown | — | — | whitelisted |
3656 | msedge.exe | GET | 301 | 49.12.202.237:80 | http://7-zip.org/ | unknown | — | — | unknown |
1036 | HEUR-Trojan.Win32.Generic-8361b0d803cadbec4c2244e9298f30a9ebe611e86df3f1fb6898726c2beefd12..exe | GET | 301 | 35.158.87.123:80 | http://psfk.com/img/icons/twitter.png?v19=29&tq=gHZutDyMv5rJejXia9nrmsl6giWz%2BJZbVyA%3D | unknown | — | — | malicious |
1452 | explorer.exe | POST | 403 | 172.67.167.202:80 | http://weddingbee.com/gate.php | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2932 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3656 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3656 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3656 | msedge.exe | 45.112.123.126:443 | gofile.io | AMAZON-02 | SG | whitelisted |
3656 | msedge.exe | 51.159.98.203:443 | s.gofile.io | Online S.a.s. | FR | whitelisted |
3656 | msedge.exe | 51.75.242.210:443 | api.gofile.io | OVH SAS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
gofile.io |
| whitelisted |
s.gofile.io |
| whitelisted |
api.gofile.io |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
store6.gofile.io |
| whitelisted |
ntp.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3656 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
3656 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
3656 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
3656 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
3656 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
3656 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
3656 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
3656 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
3656 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
3656 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
Process | Message |
|---|---|
HEUR-Trojan.Win32.Generic-9356e380f6da9efb80d2a8f6417aef094c9e46abe3f30065d1f2e48d3814e4f2..exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2010 Oreans Technologies ---
------------------------------------------------
|
HEUR-Trojan.Win32.Generic-9162c1643afeaf61ed44aebae58797a26d5b94e85d84311e719736fa03153c34..exe | 4203164 |
HEUR-Trojan.Win32.Generic-9085f8a76c559da7f3626b70e2de94b5142cd2c8630c9fbd654f73106b1f96c5..exe | 60000 60080
|
HEUR-Trojan.Win32.Generic-8916d140c0132a93cf5e5272fb314799bb3e80214d2073fdad03155a56679e9b..exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2009 Oreans Technologies ---
------------------------------------------------
|
HEUR-Trojan.Win32.Generic-8964d564cda4ecd1351bca67548802fe818c6da7475f0fbf702e0bf543f363b8..exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
HEUR-Trojan.Win32.Generic-8964d564cda4ecd1351bca67548802fe818c6da7475f0fbf702e0bf543f363b8..exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
HEUR-Trojan.Win32.Generic-8916d140c0132a93cf5e5272fb314799bb3e80214d2073fdad03155a56679e9b..exe | 5000 |
HEUR-Trojan.Win32.Generic-08764e0f3e20057c324a3b9f8a27ce1042288a90a933df2330925169624bc201..exe | In the fifth, your ass goes down. Say it. |
HEUR-Trojan.Win32.Generic-8796c958e875048e58fa857bbf8d5d07e7b38635e2bdc073dfd83fcbe4438703..exe | 60000 60080
|
9A0D2F91826.exe | 5858C9BA |