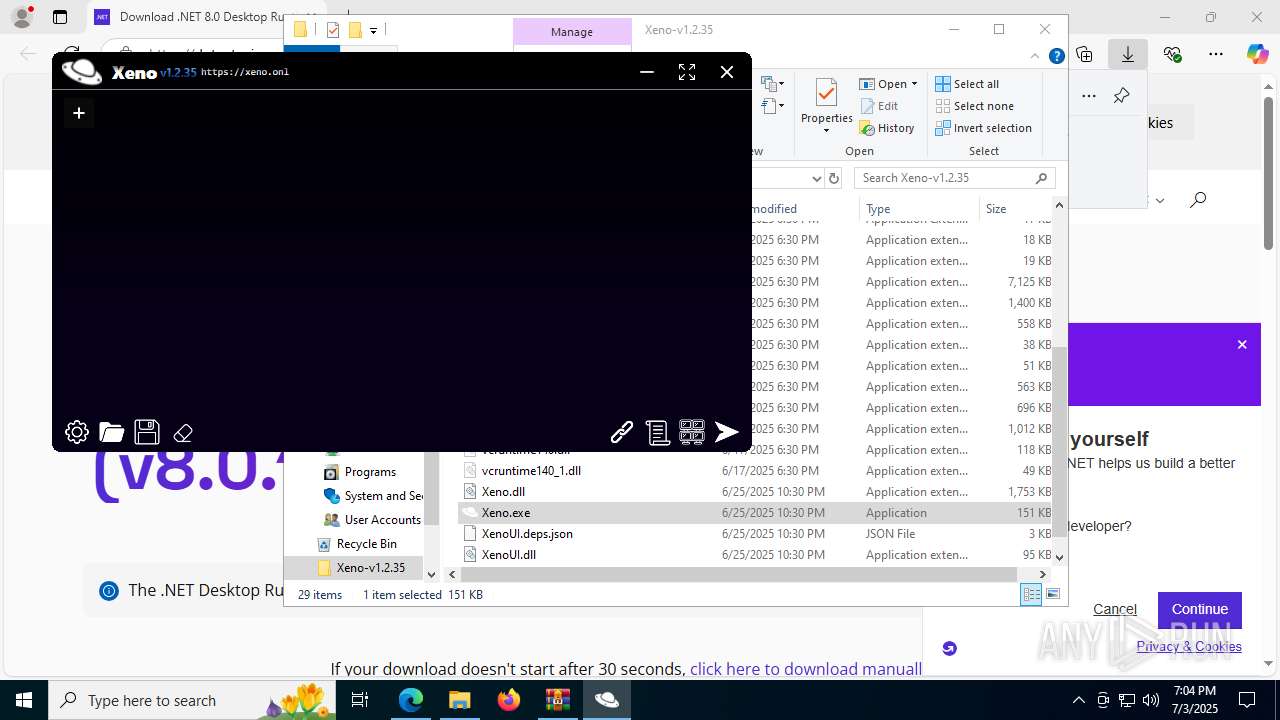
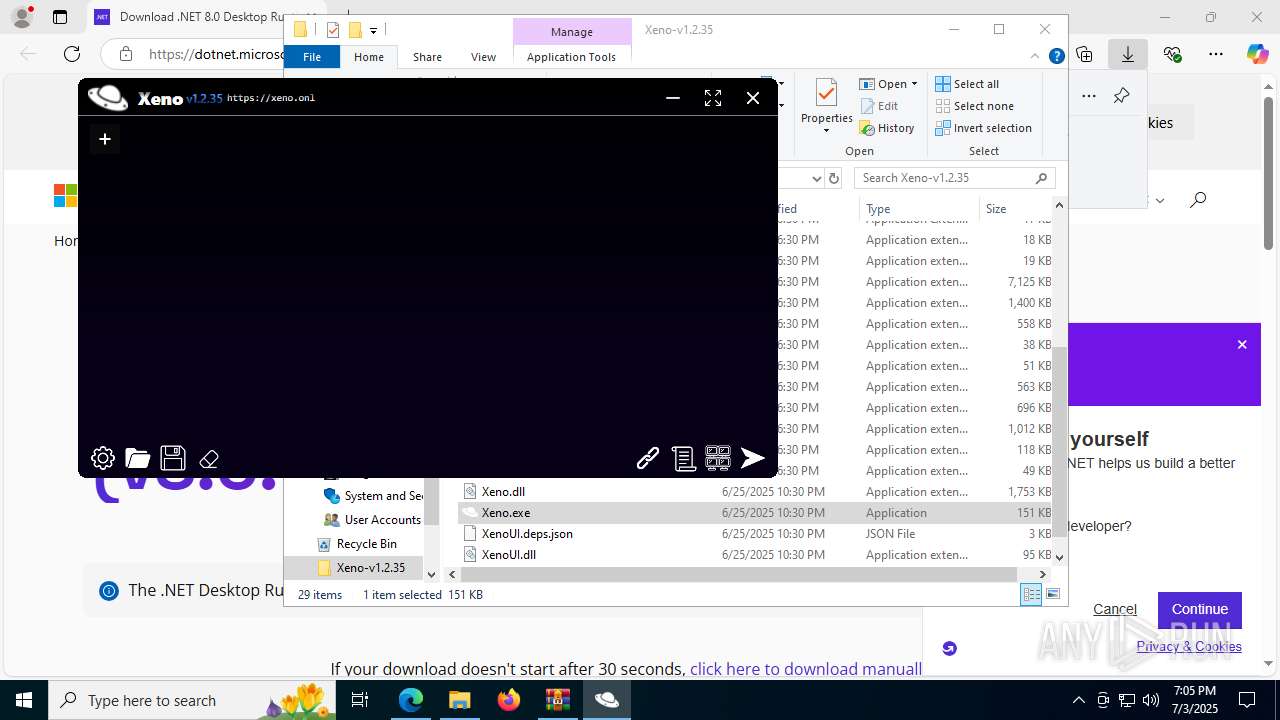
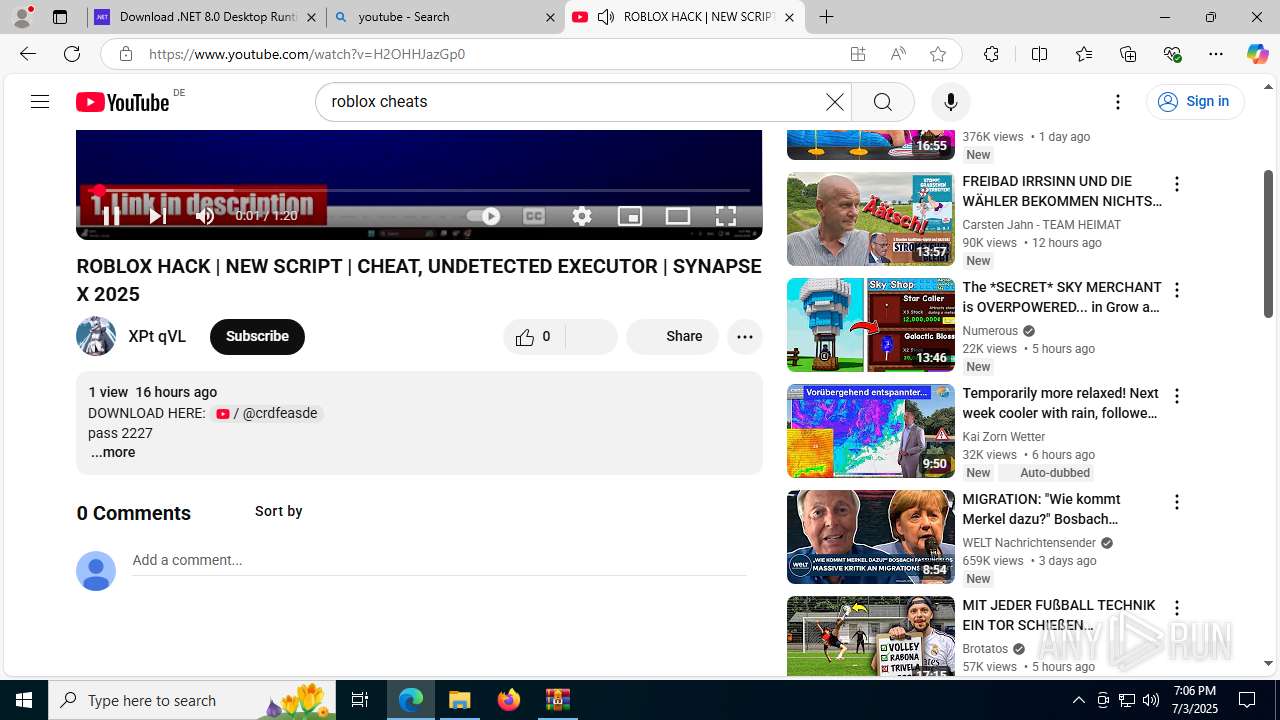
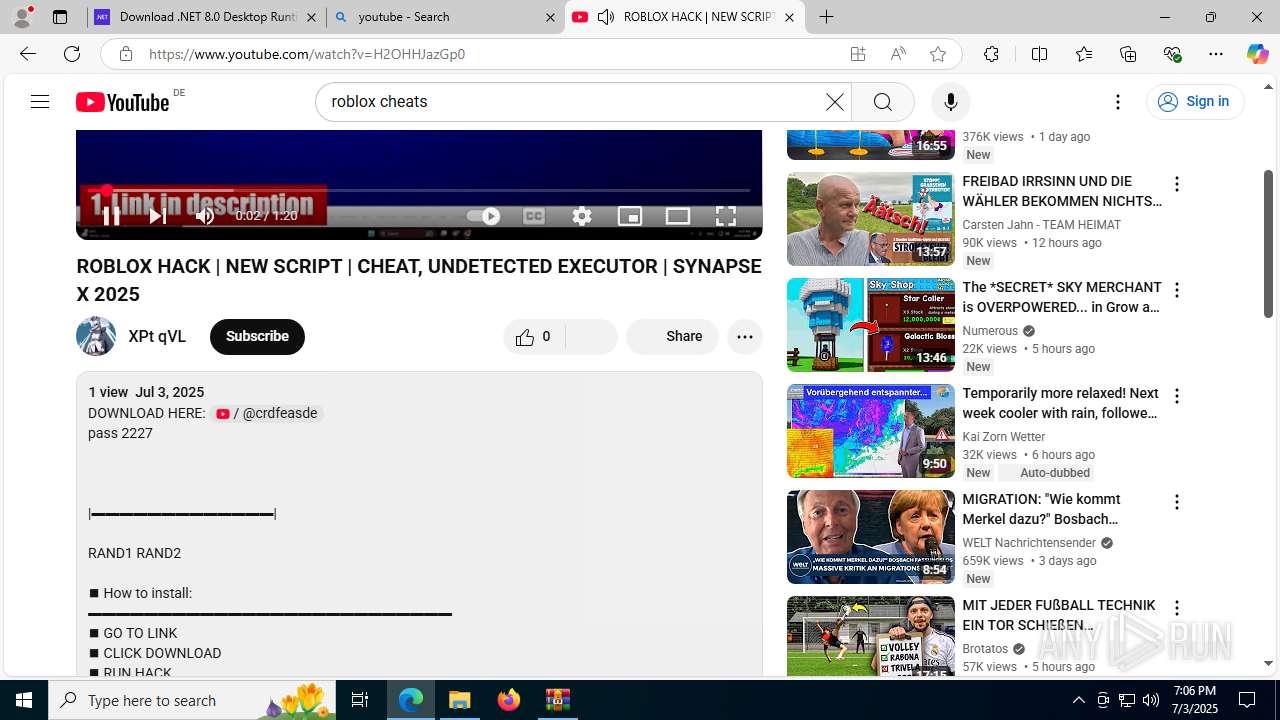
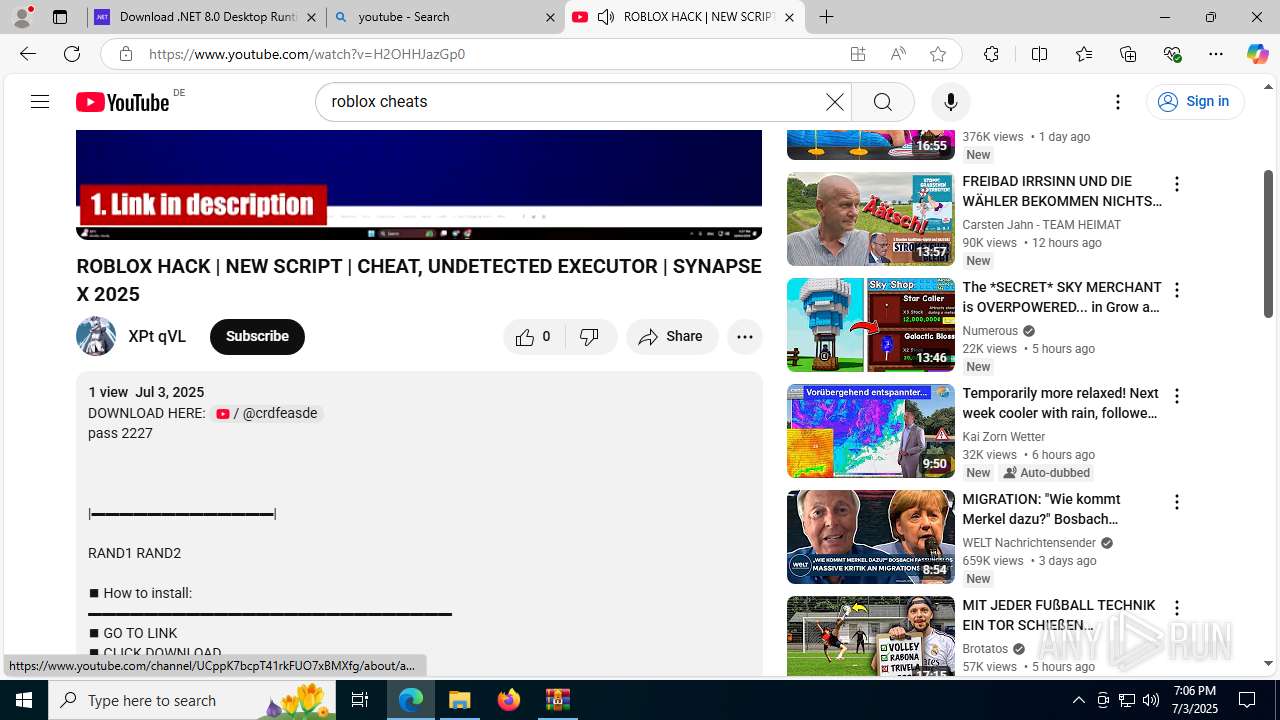
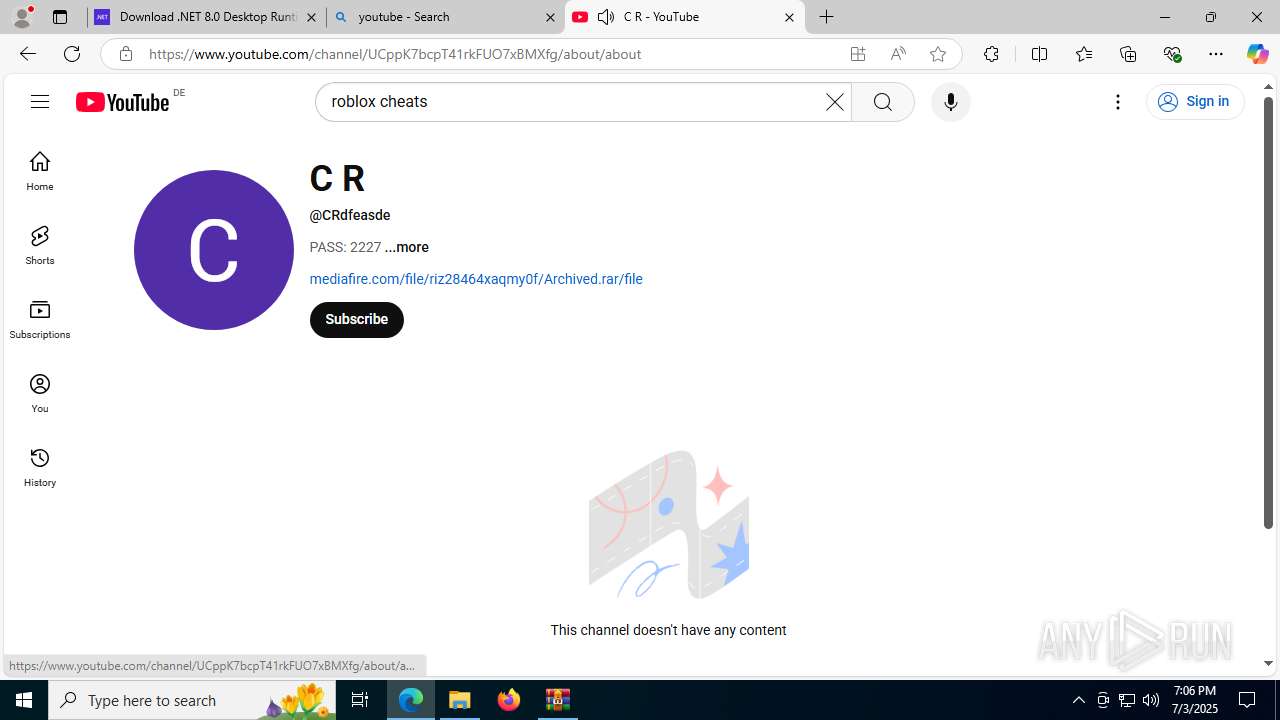
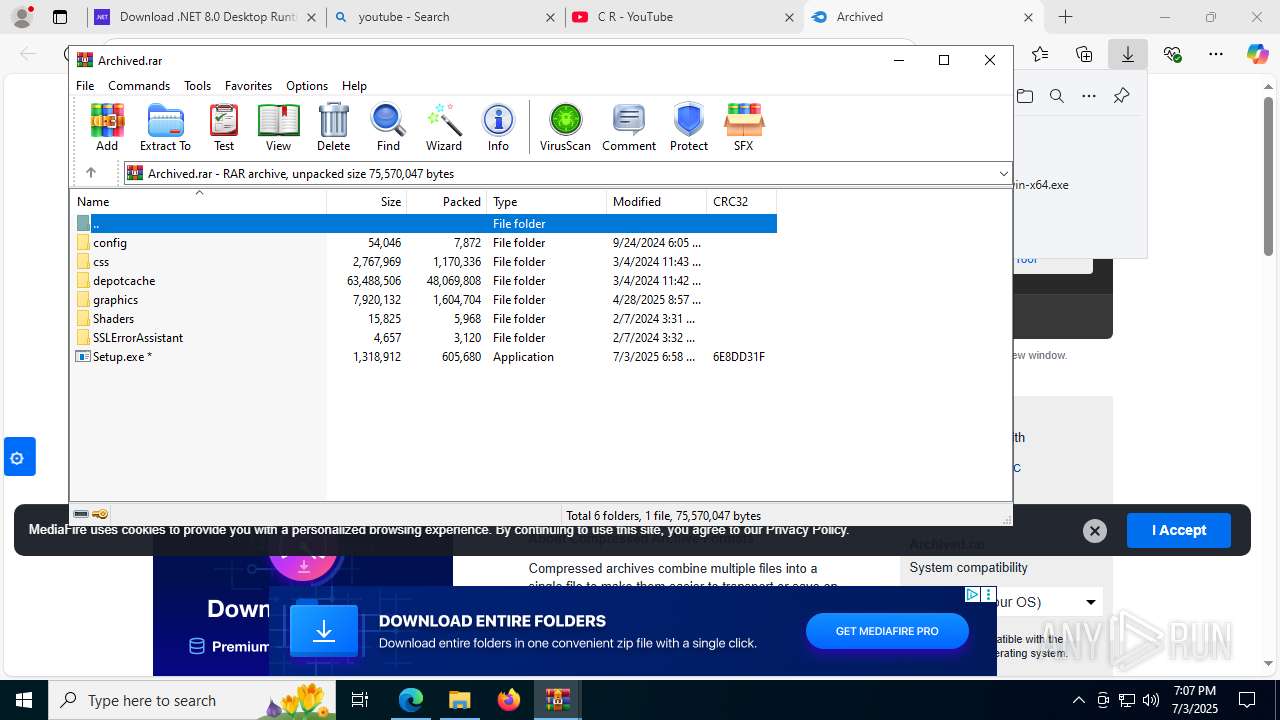
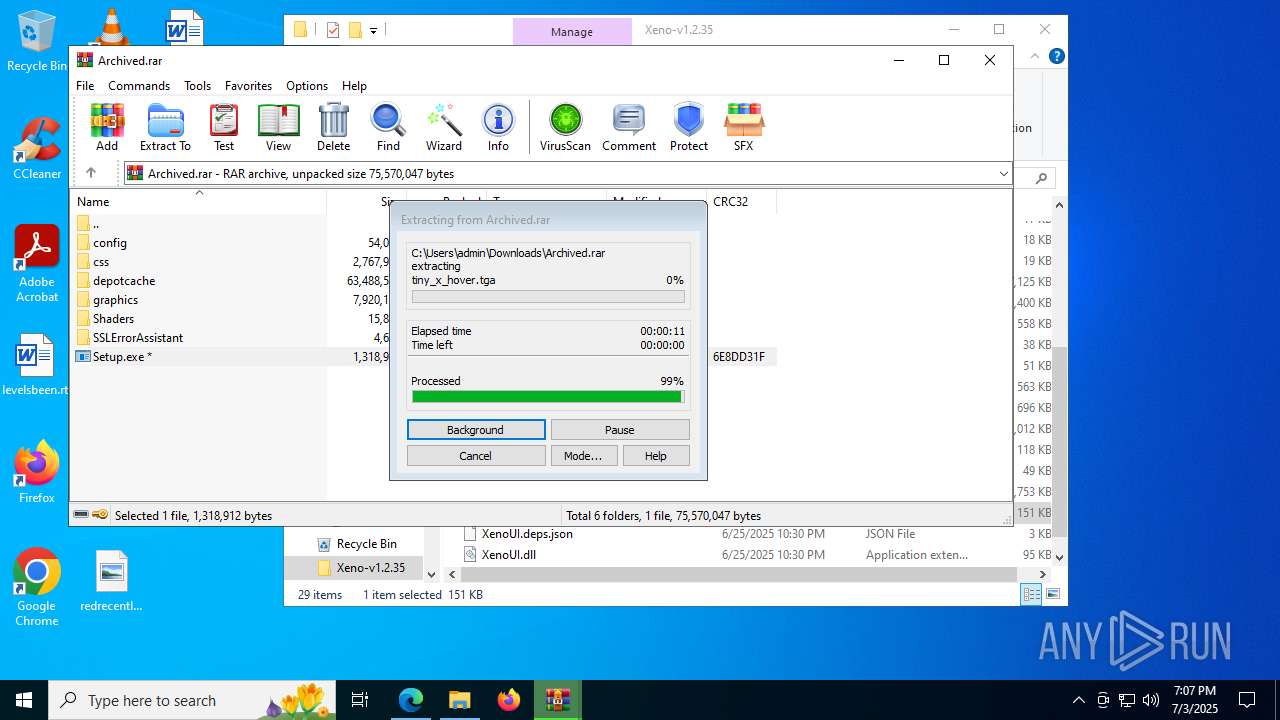
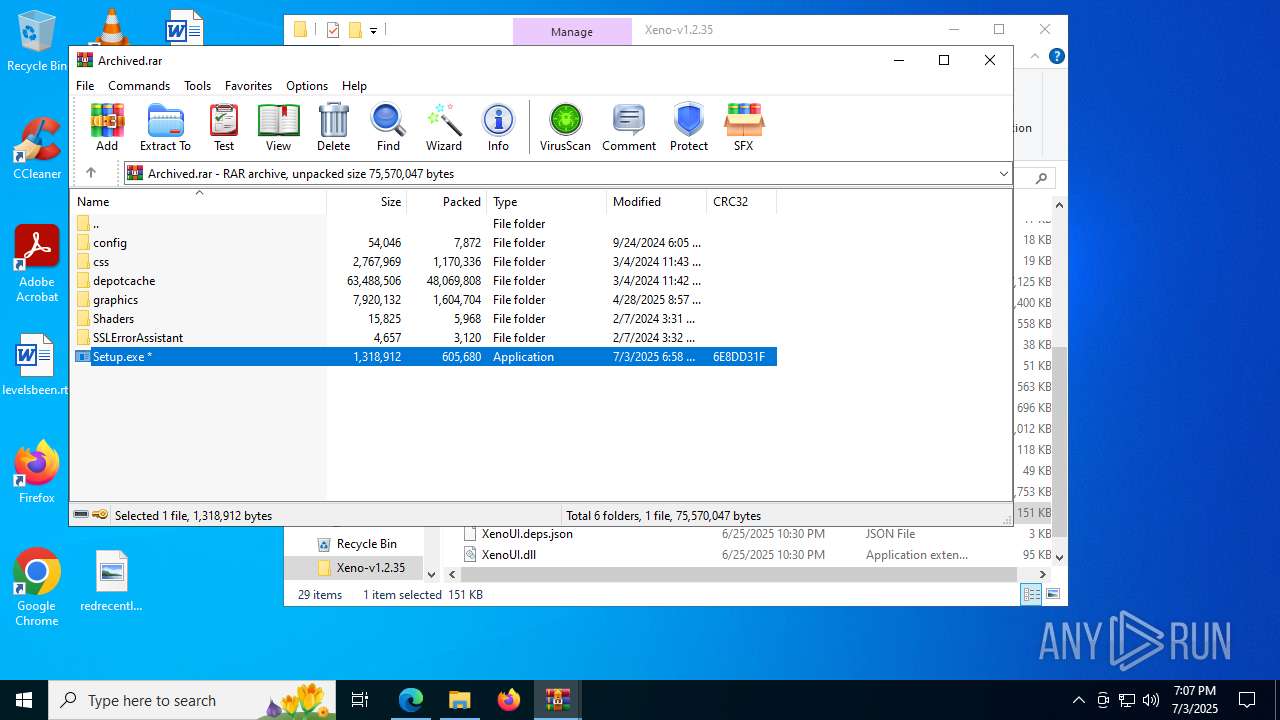
| File name: | Xeno-v1.2.35(1).zip |
| Full analysis: | https://app.any.run/tasks/81d44489-28ac-46e6-b967-794816f7dd80 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 03, 2025, 19:03:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 5B972608EF083C229F35E5AA50D1CBC6 |
| SHA1: | C88E0F408AAF43FE308E3710DD72CE96565ABCAF |
| SHA256: | 8792E16BFB30A0AA1BC78A8DD337CE270A49C4BF0CD49A911252623253A9782B |
| SSDEEP: | 98304:Q9DxwlilnX4eK0lJBSJc0uULC1lWUL/vygq+iDqA+j7bHn10pPS9nzOljtf8xMut:6VDRkhDJJwH |
MALICIOUS
Changes the autorun value in the registry
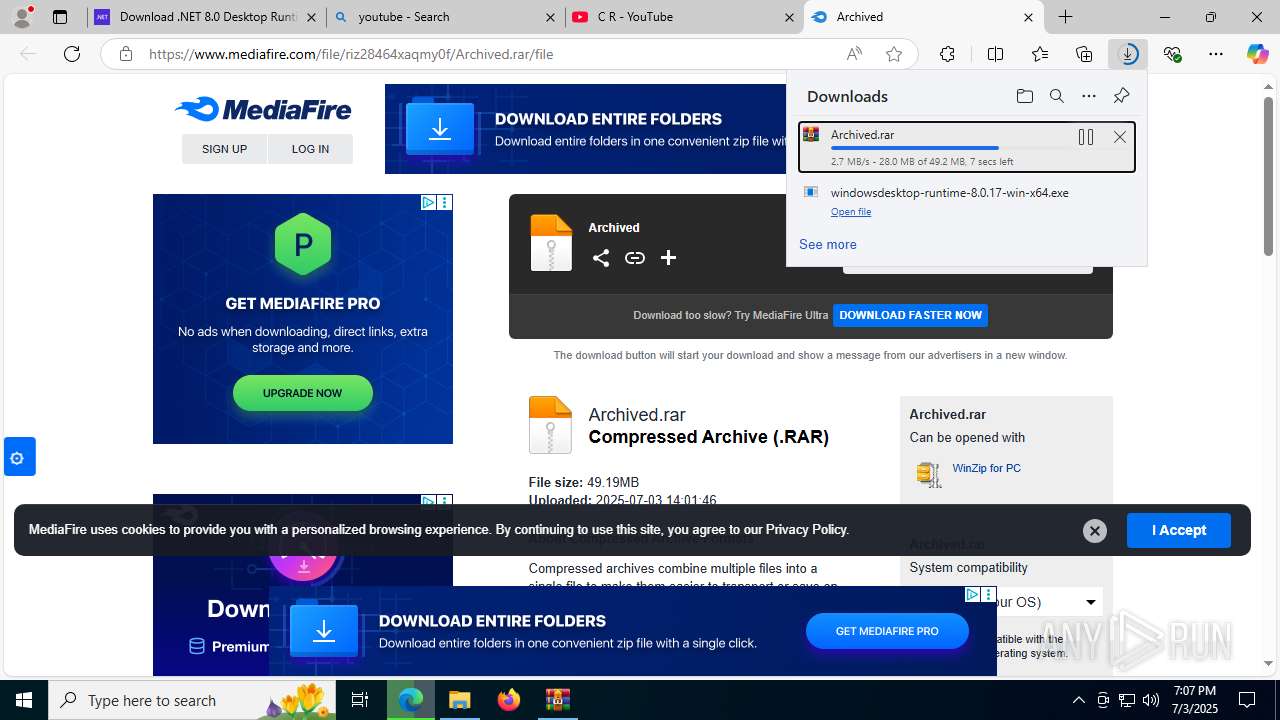
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
LUMMA mutex has been found
- MSBuild.exe (PID: 7764)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 7764)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 7764)
SUSPICIOUS
The process drops C-runtime libraries
- WinRAR.exe (PID: 4968)
- msiexec.exe (PID: 7904)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4968)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7620)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
- msiexec.exe (PID: 7904)
Reads security settings of Internet Explorer
- Xeno.exe (PID: 304)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
- Xeno.exe (PID: 1812)
- Xeno.exe (PID: 7368)
- WinRAR.exe (PID: 1192)
Executable content was dropped or overwritten
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7620)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
Searches for installed software
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7904)
Starts itself from another location
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
Creates a software uninstall entry
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
The process creates files with name similar to system file names
- msiexec.exe (PID: 7904)
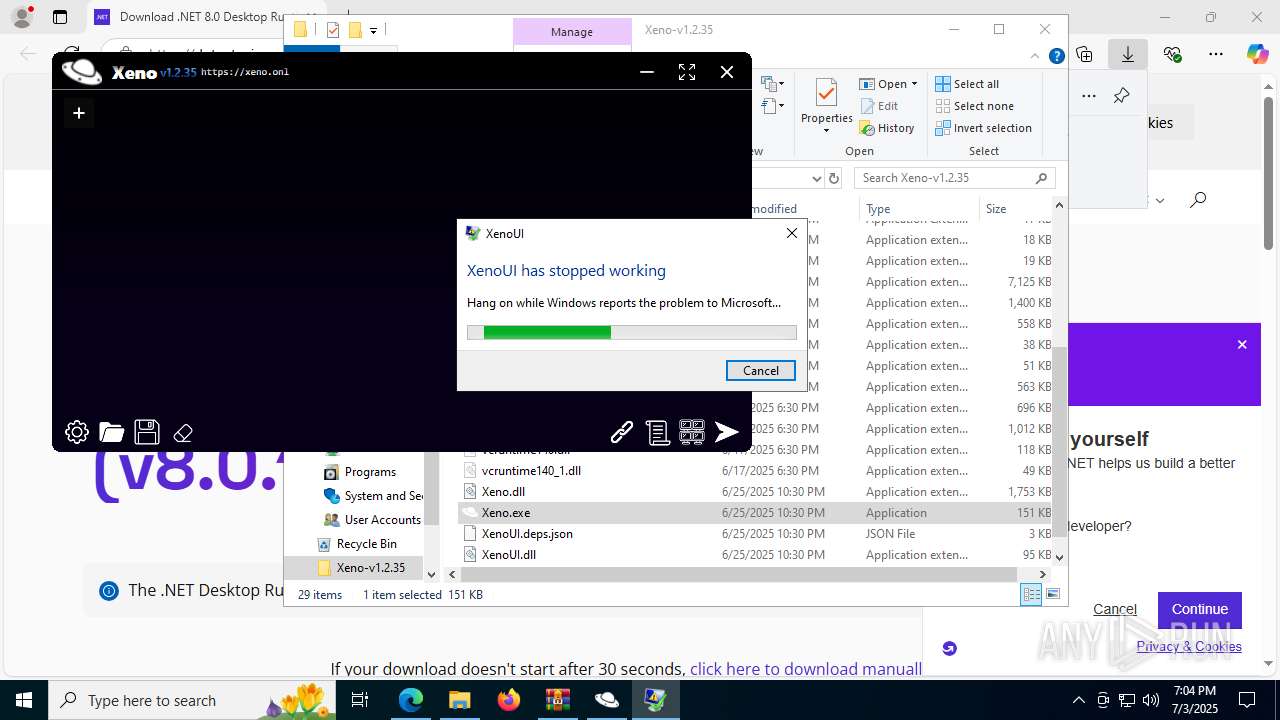
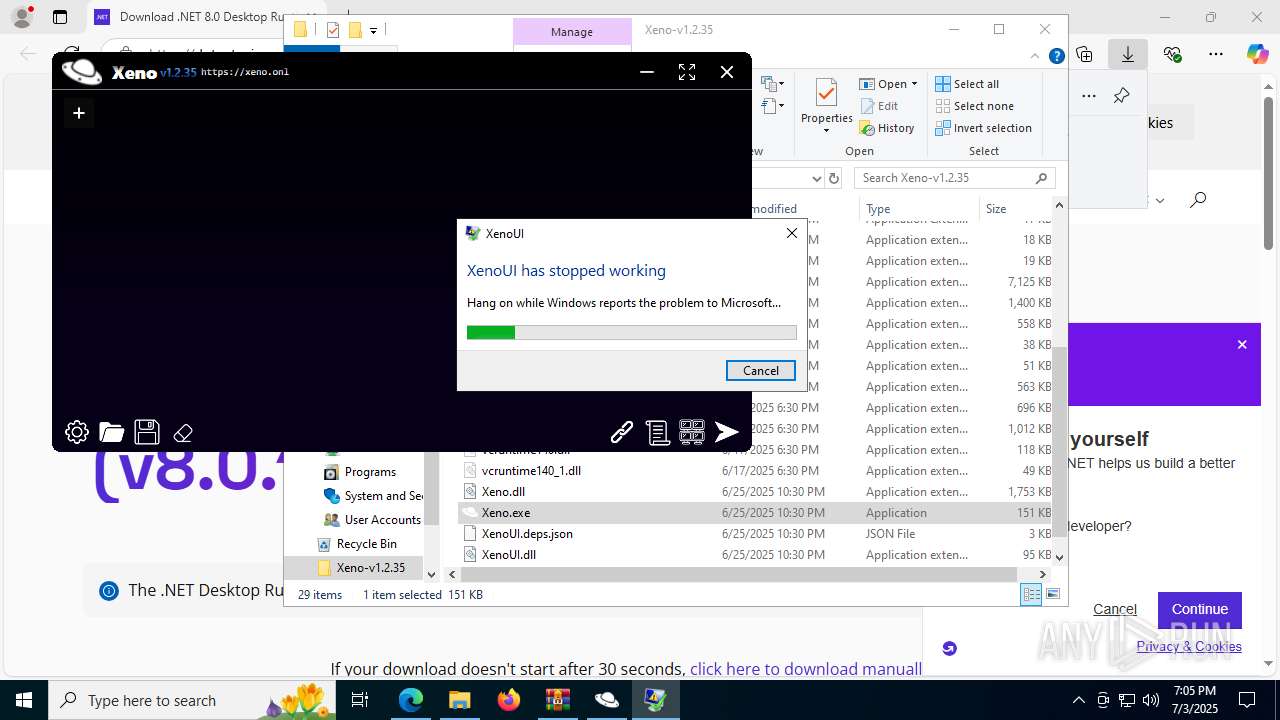
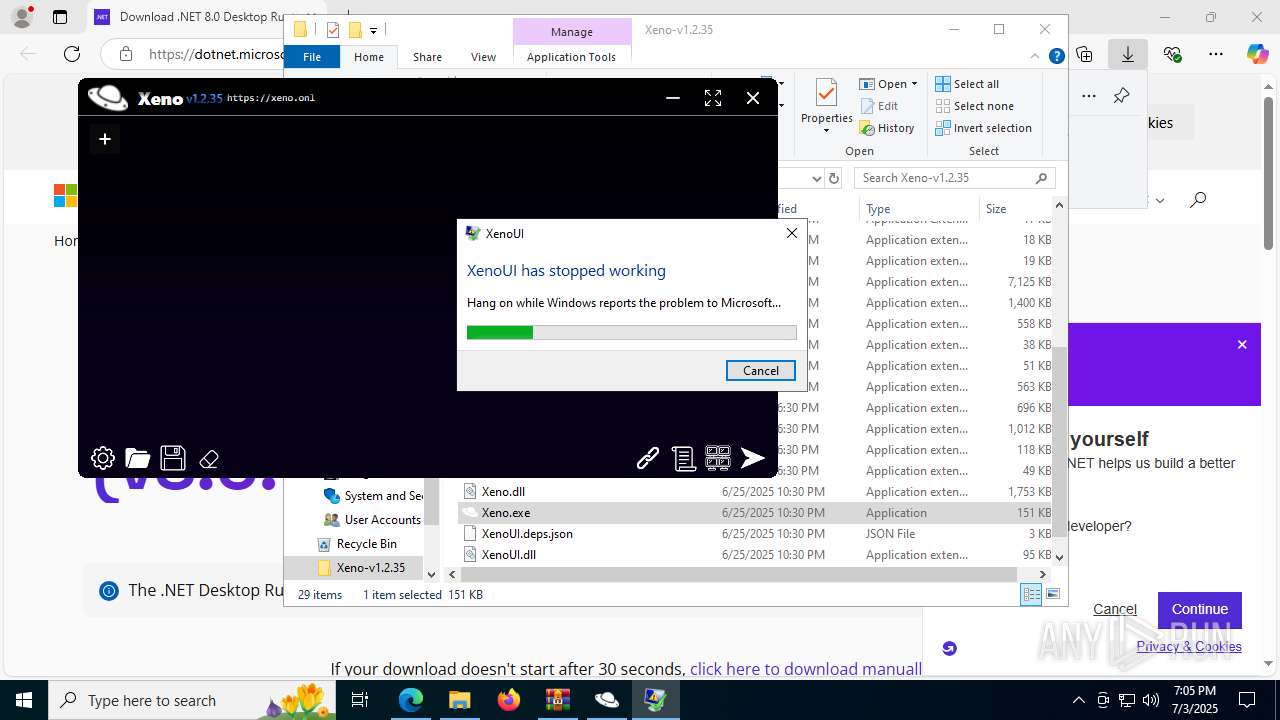
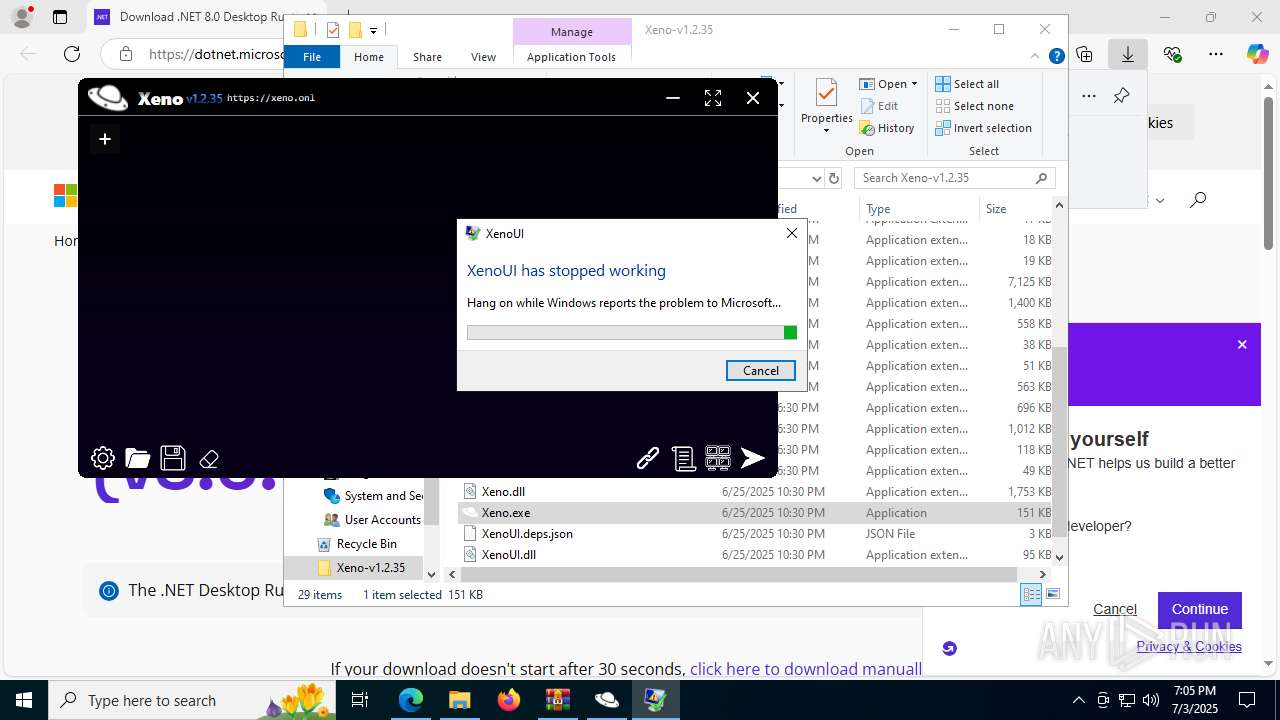
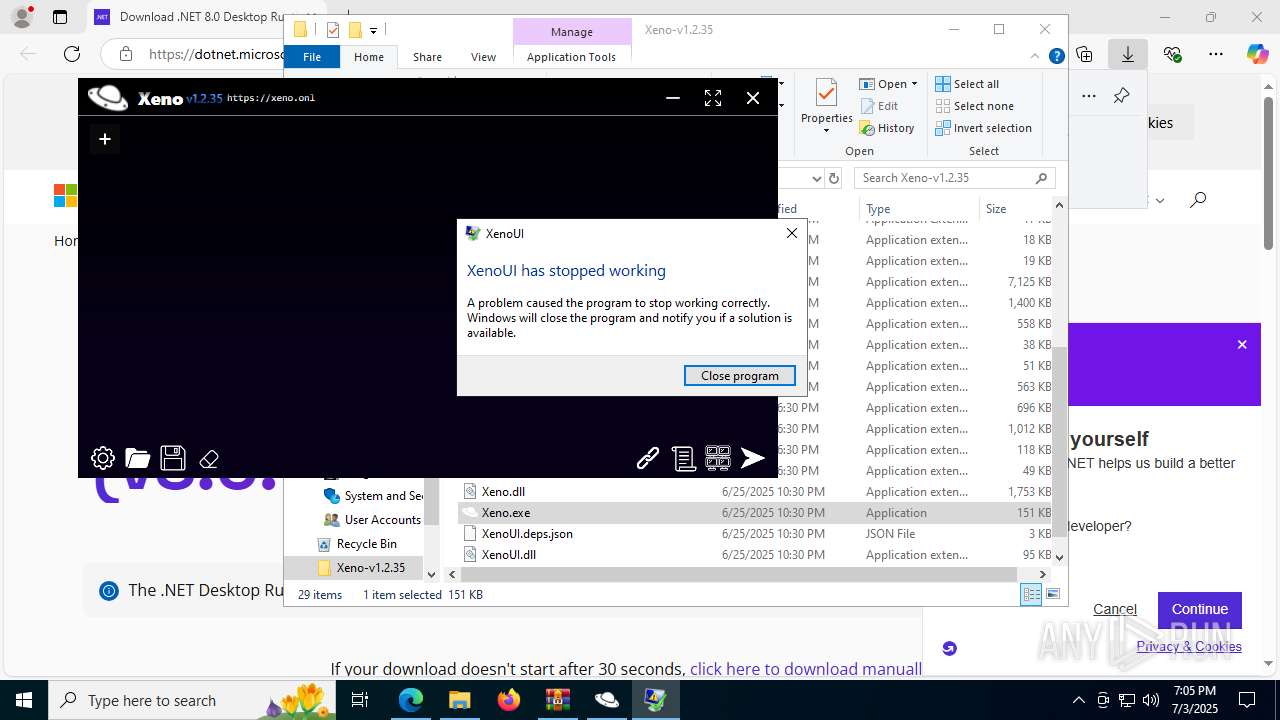
Executes application which crashes
- Xeno.exe (PID: 7368)
- Xeno.exe (PID: 1812)
There is functionality for taking screenshot (YARA)
- MSBuild.exe (PID: 7764)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4968)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7620)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
- msiexec.exe (PID: 7904)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4968)
- msedge.exe (PID: 7004)
- msiexec.exe (PID: 7904)
- WinRAR.exe (PID: 1192)
Checks supported languages
- Xeno.exe (PID: 304)
- identity_helper.exe (PID: 7324)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7620)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
- msiexec.exe (PID: 7904)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
- msiexec.exe (PID: 7228)
- msiexec.exe (PID: 7384)
- msiexec.exe (PID: 7560)
- msiexec.exe (PID: 7976)
- Xeno.exe (PID: 1812)
- Xeno.exe (PID: 7368)
- Setup.exe (PID: 5220)
- MSBuild.exe (PID: 7764)
Application launched itself
- msedge.exe (PID: 4444)
- msedge.exe (PID: 7004)
- chrome.exe (PID: 7048)
- chrome.exe (PID: 8968)
- chrome.exe (PID: 8760)
- chrome.exe (PID: 8240)
- msedge.exe (PID: 8264)
Manual execution by a user
- Xeno.exe (PID: 304)
- Xeno.exe (PID: 7368)
- Xeno.exe (PID: 1812)
Reads the computer name
- Xeno.exe (PID: 304)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
- identity_helper.exe (PID: 7324)
- msiexec.exe (PID: 7904)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
- msiexec.exe (PID: 7384)
- msiexec.exe (PID: 7560)
- msiexec.exe (PID: 7976)
- msiexec.exe (PID: 7228)
- Xeno.exe (PID: 1812)
- Xeno.exe (PID: 7368)
- MSBuild.exe (PID: 7764)
Reads Environment values
- identity_helper.exe (PID: 7324)
Create files in a temporary directory
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7620)
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
- Xeno.exe (PID: 7368)
- Xeno.exe (PID: 1812)
Process checks computer location settings
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7644)
Launching a file from a Registry key
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
Reads the machine GUID from the registry
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
- msiexec.exe (PID: 7904)
- MSBuild.exe (PID: 7764)
Reads the software policy settings
- msiexec.exe (PID: 7904)
- Xeno.exe (PID: 1812)
- Xeno.exe (PID: 7368)
- WerFault.exe (PID: 8152)
- WerFault.exe (PID: 5724)
- MSBuild.exe (PID: 7764)
- slui.exe (PID: 7700)
Creates files in the program directory
- windowsdesktop-runtime-8.0.17-win-x64.exe (PID: 7840)
- Xeno.exe (PID: 7368)
Creates files or folders in the user directory
- WerFault.exe (PID: 8152)
- WerFault.exe (PID: 5724)
Checks proxy server information
- Xeno.exe (PID: 1812)
- WerFault.exe (PID: 5724)
- Xeno.exe (PID: 7368)
- WerFault.exe (PID: 8152)
- slui.exe (PID: 7700)
Creates a software uninstall entry
- msiexec.exe (PID: 7904)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:25 18:31:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Xeno-v1.2.35/ |
Total processes
291
Monitored processes
133
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Users\admin\Desktop\Xeno-v1.2.35\Xeno.exe" | C:\Users\admin\Desktop\Xeno-v1.2.35\Xeno.exe | explorer.exe | ||||||||||||
User: admin Company: XenoUI Integrity Level: MEDIUM Description: XenoUI Exit code: 2147516547 Version: 1.2.35 Modules
| |||||||||||||||
| 360 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=10740,i,1107551662705902317,14337019489246509310,262144 --variations-seed-version --mojo-platform-channel-handle=10988 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 728 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3608,i,1107551662705902317,14337019489246509310,262144 --variations-seed-version --mojo-platform-channel-handle=3784 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1052 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --disable-quic --onnx-enabled-for-ee --string-annotations --always-read-main-dll --field-trial-handle=6112,i,1107551662705902317,14337019489246509310,262144 --variations-seed-version --mojo-platform-channel-handle=6328 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Archived.rar" | C:\Program Files\WinRAR\WinRAR.exe | msedge.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=3796,i,1107551662705902317,14337019489246509310,262144 --variations-seed-version --mojo-platform-channel-handle=4140 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1212 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x290,0x294,0x298,0x288,0x2a0,0x7ffc44c2f208,0x7ffc44c2f214,0x7ffc44c2f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1468 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=35 --always-read-main-dll --field-trial-handle=6500,i,1107551662705902317,14337019489246509310,262144 --variations-seed-version --mojo-platform-channel-handle=5208 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1812 | "C:\Users\admin\Desktop\Xeno-v1.2.35\Xeno.exe" | C:\Users\admin\Desktop\Xeno-v1.2.35\Xeno.exe | explorer.exe | ||||||||||||
User: admin Company: XenoUI Integrity Level: MEDIUM Description: XenoUI Exit code: 3762504530 Version: 1.2.35 Modules
| |||||||||||||||
| 1840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc414ffff8,0x7ffc41500004,0x7ffc41500010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
51 063
Read events
50 009
Write events
992
Delete events
62
Modification events
| (PID) Process: | (4968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Xeno-v1.2.35(1).zip | |||
| (PID) Process: | (304) Xeno.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (304) Xeno.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
513
Suspicious files
1 313
Text files
429
Unknown types
657
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\bin\Monaco\vs\editor\editor.main.css | text | |
MD5:23C7DB6E12F6454EF6E7FB98D17924D8 | SHA256:615824C59ED1E07F5924286E9F02F3120B9064D59E115D3F668A914E07839451 | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\bin\Monaco\vs\base\worker\workerMain.js | s | |
MD5:D0AC5294C58E523CDDF25BC6D785FA48 | SHA256:E90D1A8F116FA74431117A3AD78DDE16DDE060A4BF7528DFE3D5A3AD6156504B | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\bin\Monaco\vs\editor\editor.main.js | s | |
MD5:2DC0068CDBC03CE43A75AB0B2DF664E2 | SHA256:B604B6148F70FE9DB882CCE2A7D327B2422AD2F203A805491002A8C564E3C3FF | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\api-ms-win-crt-math-l1-1-0.dll | executable | |
MD5:E10E077BB06209AEDD0D0D378C758F73 | SHA256:8A7BFF1C918539A75C25568DB25933D653C003E016FD7791A37186B42BBB7C20 | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\api-ms-win-crt-runtime-l1-1-0.dll | executable | |
MD5:F91E1FF896B5616919AC97C7095C513E | SHA256:07382C0D91DAD2BB6BA8BD06EA02F12C57ABF7C4E5A70672E9F2954D09A4FFD4 | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\api-ms-win-crt-heap-l1-1-0.dll | executable | |
MD5:98DA186FD7D7873C164A51C5D7B77F1A | SHA256:80139E4CAA379D87B1D1DAFC23ACE71D2B330368115F6314140D4AE59C2A78E8 | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\api-ms-win-crt-filesystem-l1-1-0.dll | executable | |
MD5:42A2A95F1BB940D01F55EB1674A81FE2 | SHA256:51541EC6684B43157A85EA46A42EBED4555BE06BED0D0D07FF3EA6377301318D | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\api-ms-win-crt-string-l1-1-0.dll | executable | |
MD5:0F593E50BE4715AA8E1F6EB39434EDD5 | SHA256:BF4EA10BE1B64C442AC0CCF4BDF69F6703467176A27E9E14A488D26448A6E179 | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\api-ms-win-crt-convert-l1-1-0.dll | executable | |
MD5:C8DBF0CA88FACFE87899168A7F7DB52C | SHA256:94B6E91B93C2202DABD659BFF294BEE87C22897A30A6B4930B49051C2FB502DC | |||
| 4968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4968.21984\Xeno-v1.2.35\api-ms-win-crt-stdio-l1-1-0.dll | executable | |
MD5:429C26ED27A026442F89C95FF16CE8C2 | SHA256:2A466648AFFD3D51B944F563BB65046A3DA91006A0D90FB2C0B123487A1FC1B3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
405
DNS requests
550
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2764 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4836 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4836 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3752 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:eIEx1XSdZxz912cBYm6cuBRfaWuxicLQ3Zw-oBmJIpU&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
7004 | msedge.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7996 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1752098729&P2=404&P3=2&P4=fKT4xxs6NZqQoQsH%2f4rn3KqCszxW7rIVQcy8CVuxxobd%2bsLdE8OCokyJEJi0i6WIzPQU9712xgzZUEQmYVlLqA%3d%3d | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
8152 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3936 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2764 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2764 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET INFO DNS Query to Cloudflare Page Developer Domain (pages .dev) |
7368 | Xeno.exe | Misc activity | ET INFO Observed Cloudflare Page Developer Domain (pages .dev in TLS SNI) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Pages platform for frontend developers to collaborate and deploy websites (pages .dev) |
3752 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
3752 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3752 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
Process | Message |
|---|---|
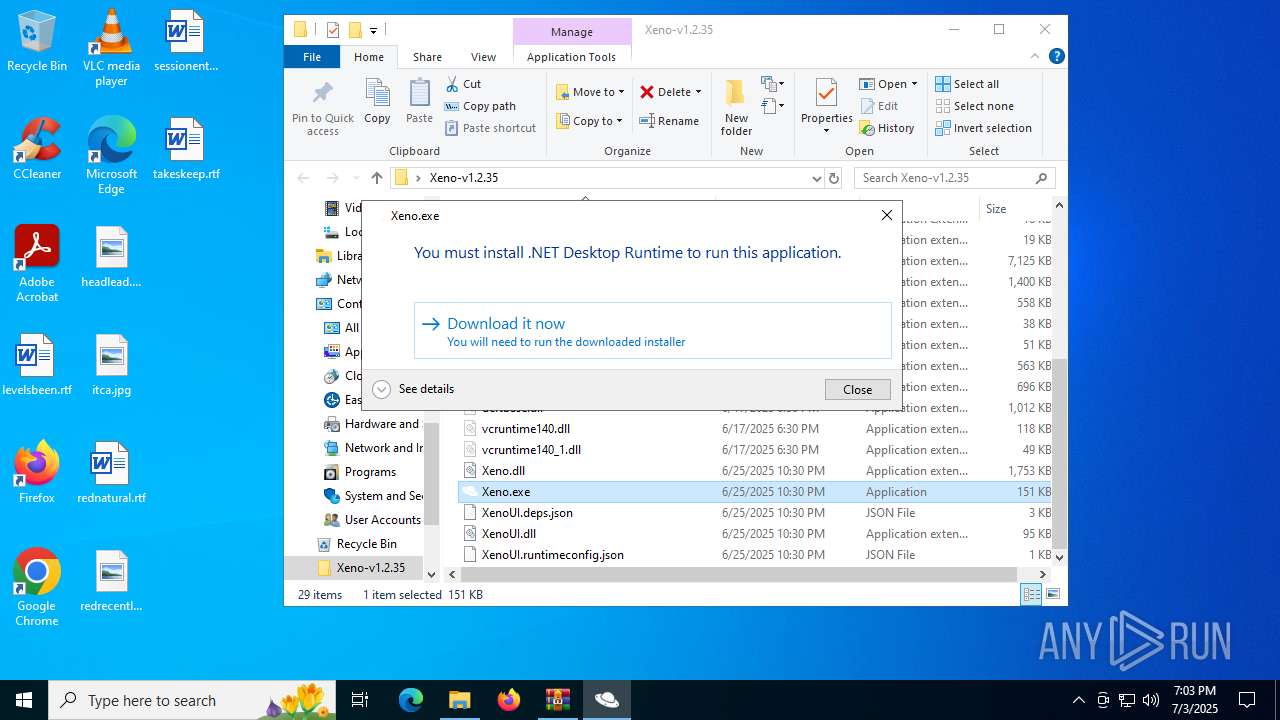
Xeno.exe | You must install .NET to run this application.
App: C:\Users\admin\Desktop\Xeno-v1.2.35\Xeno.exe
Architecture: x64
App host version: 8.0.17
.NET location: Not found
Learn more:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win-x64&os=win10&apphost_version=8.0.17 |
Xeno.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
Xeno.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
Xeno.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
Xeno.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|