| File name: | 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry |
| Full analysis: | https://app.any.run/tasks/909ca2e5-2364-48ad-a0d0-5c55d3f8c904 |
| Verdict: | Malicious activity |
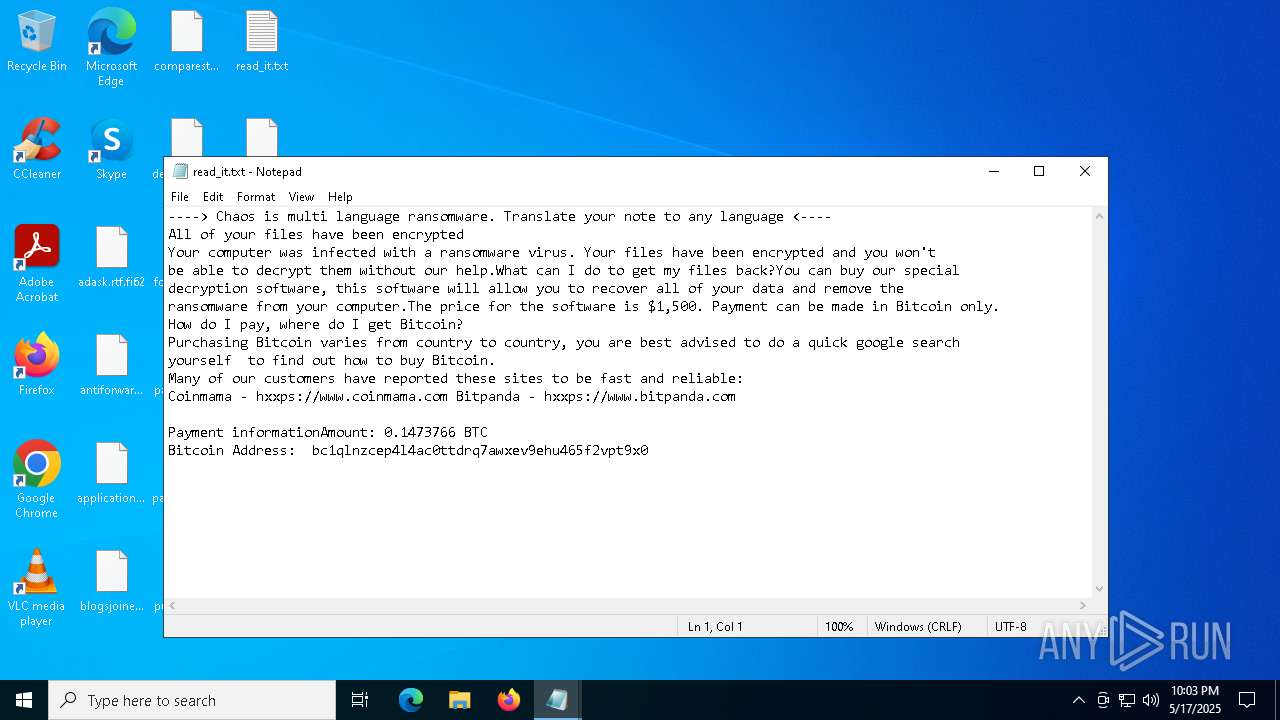
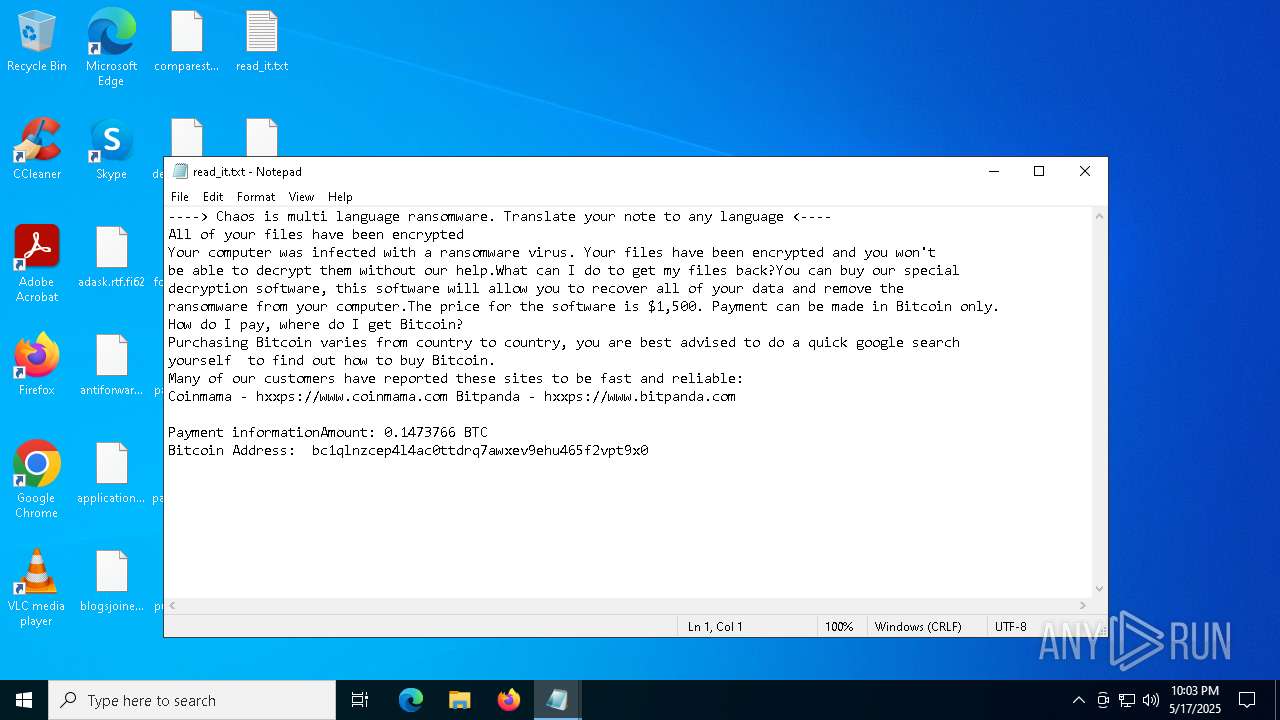
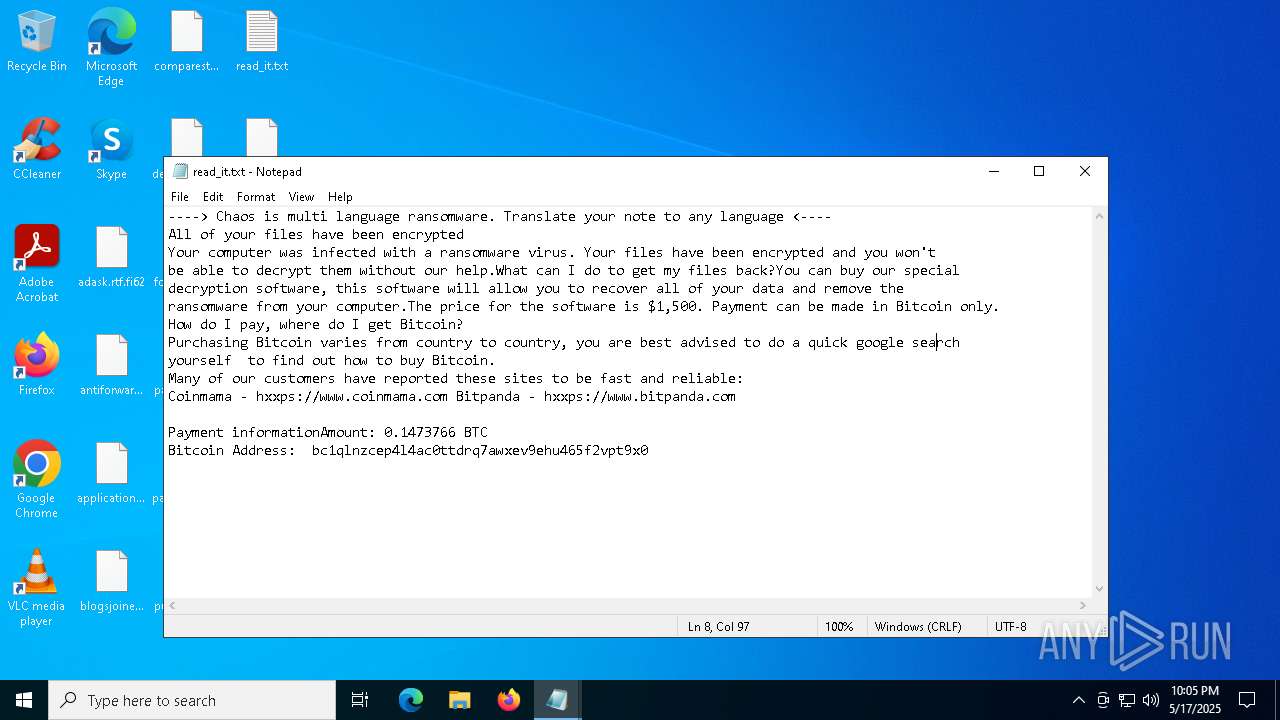
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | May 17, 2025, 22:03:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 97D43133E09F70F8069255AE58D8E184 |
| SHA1: | F7B4CDA386AB532DDA653DF5F094F7FD1B516D53 |
| SHA256: | 8788C583CE745BB570F7945965CF7448395EE73BB95B03D0C8BD62B2AF03EFD0 |
| SSDEEP: | 384:Kh9Dqdp1nBWAgHyUBi+UxJTr91Cg4+b5KrOw0:Gqdp1BSHq+U/Tr9e+bMr2 |
MALICIOUS
Create files in the Startup directory
- svchost.exe (PID: 1056)
Renames files like ransomware
- svchost.exe (PID: 1056)
RANSOMWARE has been detected
- svchost.exe (PID: 1056)
CHAOS has been detected (YARA)
- svchost.exe (PID: 1056)
SUSPICIOUS
Reads security settings of Internet Explorer
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
- svchost.exe (PID: 1056)
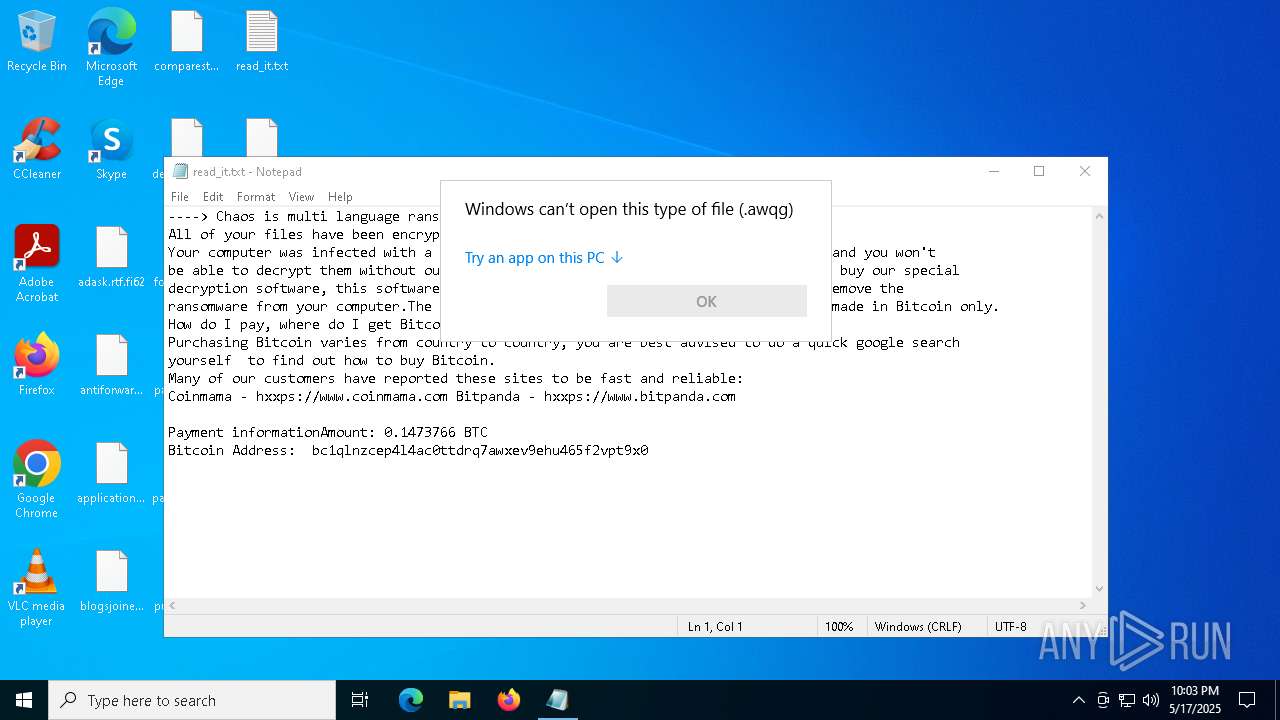
The process creates files with name similar to system file names
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
Executable content was dropped or overwritten
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
Reads the date of Windows installation
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
- svchost.exe (PID: 1056)
Starts itself from another location
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
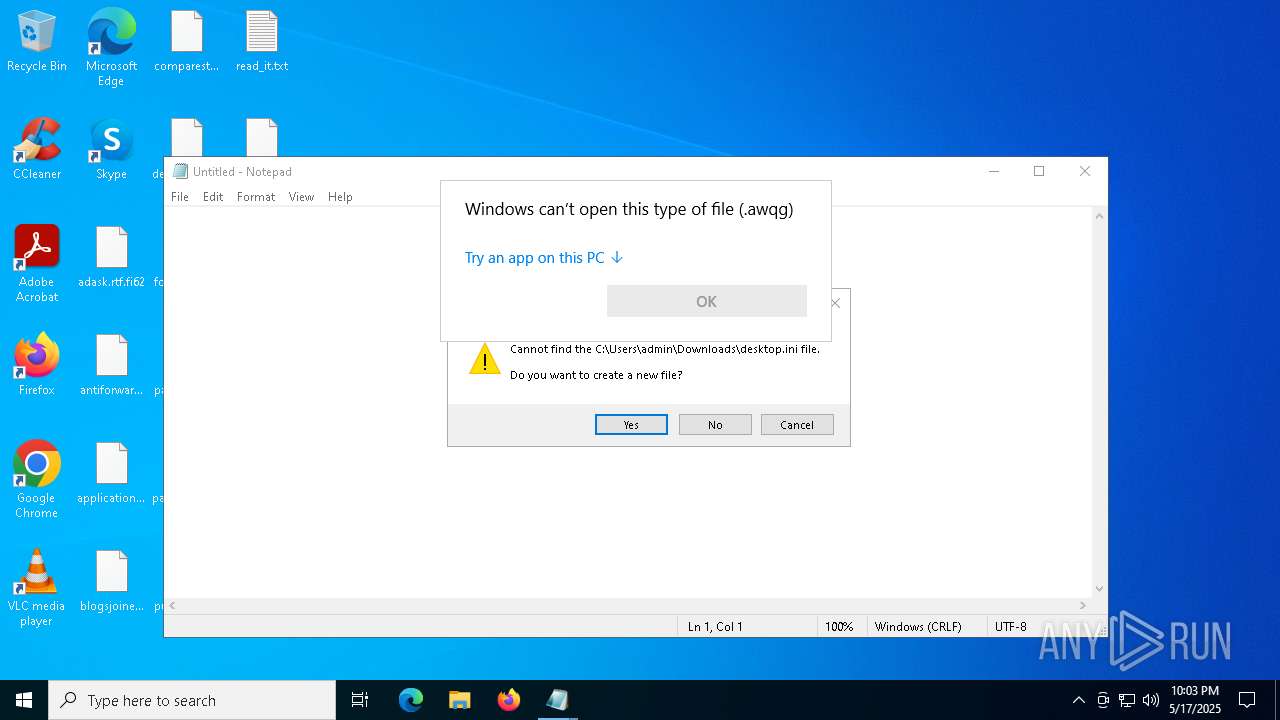
Write to the desktop.ini file (may be used to cloak folders)
- svchost.exe (PID: 1056)
Found regular expressions for crypto-addresses (YARA)
- svchost.exe (PID: 1056)
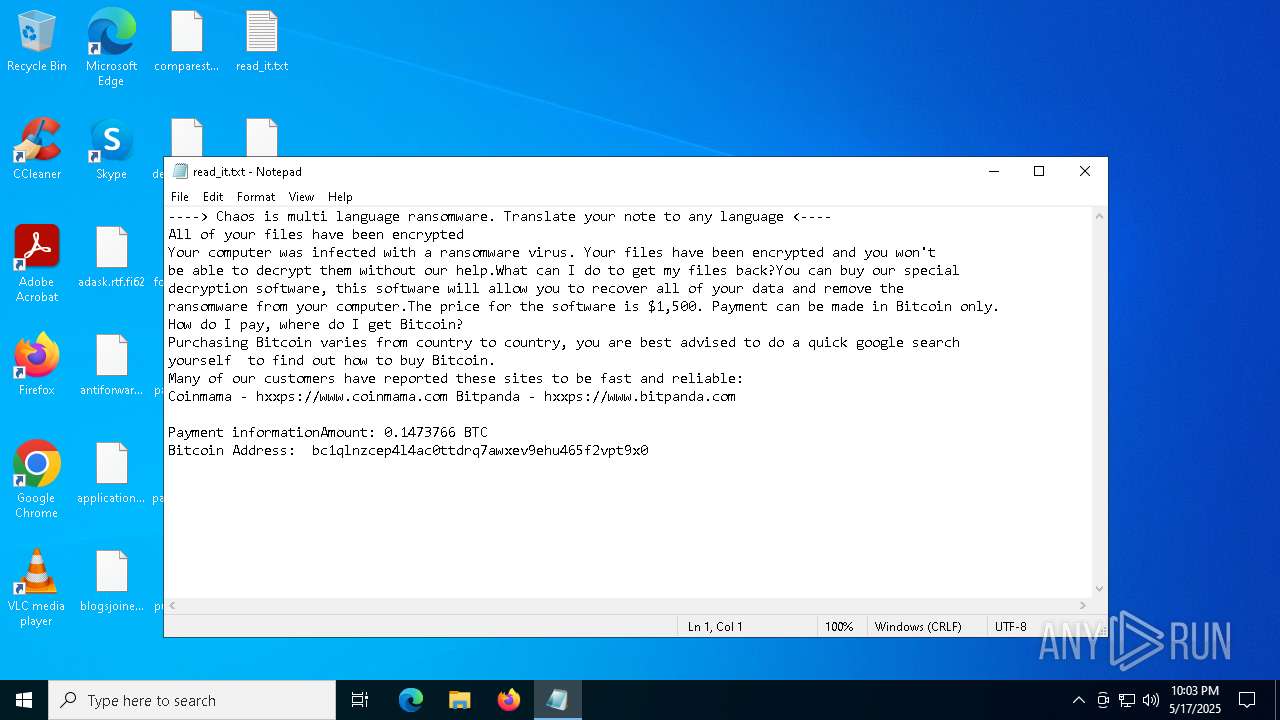
Start notepad (likely ransomware note)
- svchost.exe (PID: 1056)
INFO
Reads the computer name
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
- svchost.exe (PID: 1056)
Creates files or folders in the user directory
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
- svchost.exe (PID: 1056)
Process checks computer location settings
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
- svchost.exe (PID: 1056)
Checks supported languages
- 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe (PID: 2432)
- svchost.exe (PID: 1056)
Auto-launch of the file from Startup directory
- svchost.exe (PID: 1056)
Reads the machine GUID from the registry
- svchost.exe (PID: 1056)
Reads security settings of Internet Explorer
- notepad.exe (PID: 976)
- notepad.exe (PID: 1280)
Manual execution by a user
- notepad.exe (PID: 976)
- rundll32.exe (PID: 5072)
- rundll32.exe (PID: 1132)
- OpenWith.exe (PID: 6268)
- OpenWith.exe (PID: 7152)
- notepad.exe (PID: 1184)
- rundll32.exe (PID: 5964)
- OpenWith.exe (PID: 2240)
- OpenWith.exe (PID: 920)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7152)
- OpenWith.exe (PID: 6268)
- OpenWith.exe (PID: 2240)
- OpenWith.exe (PID: 920)
- svchost.exe (PID: 1056)
Checks proxy server information
- slui.exe (PID: 5380)
Reads the software policy settings
- slui.exe (PID: 5380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:17 14:50:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 21504 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x734e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | ezz.exe |
| LegalCopyright: | |
| OriginalFileName: | ezz.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
136
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Downloads\nationmail.jpg.fiov | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\read_it.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1132 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Downloads\nationmail.jpg | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\desktop.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\read_it.txt | C:\Windows\System32\notepad.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Downloads\percenteither.png.qcv4 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\Desktop\2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe" | C:\Users\admin\Desktop\2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 1 Version: 0.0.0.0 Modules
| |||||||||||||||
| 5072 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Downloads\percenteither.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5380 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 647
Read events
9 646
Write events
1
Delete events
0
Modification events
| (PID) Process: | (1056) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
Executable files
1
Suspicious files
1
Text files
615
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1056 | svchost.exe | C:\Users\admin\Desktop\adask.rtf.fi62 | text | |
MD5:78CDB6CE3D7806E065115C723AF1EE3F | SHA256:2E8C3CB57F54151392274860EB4359AC79B4E637FF3051808D68D7CBA8CC1037 | |||
| 1056 | svchost.exe | C:\Users\admin\Desktop\read_it.txt | text | |
MD5:4217B8B83CE3C3F70029A056546F8FD0 | SHA256:7D767E907BE373C680D1F7884D779588EB643BEBB3F27BF3B5ED4864AA4D8121 | |||
| 1056 | svchost.exe | C:\Users\admin\Desktop\adask.rtf | text | |
MD5:78CDB6CE3D7806E065115C723AF1EE3F | SHA256:2E8C3CB57F54151392274860EB4359AC79B4E637FF3051808D68D7CBA8CC1037 | |||
| 1056 | svchost.exe | C:\Users\admin\Desktop\antiforward.rtf | text | |
MD5:6A33B93FD9444CBE29BD4A6373DA9911 | SHA256:B76A74852D3A6D63BCA658611E29B9D832BEF8B6C75FCADE016F6F1883B8C436 | |||
| 2432 | 2025-05-17_97d43133e09f70f8069255ae58d8e184_chaos_destroyer_elex_wannacry.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:97D43133E09F70F8069255AE58D8E184 | SHA256:8788C583CE745BB570F7945965CF7448395EE73BB95B03D0C8BD62B2AF03EFD0 | |||
| 1056 | svchost.exe | C:\Users\admin\Desktop\antiforward.rtf.ocqb | text | |
MD5:6A33B93FD9444CBE29BD4A6373DA9911 | SHA256:B76A74852D3A6D63BCA658611E29B9D832BEF8B6C75FCADE016F6F1883B8C436 | |||
| 1056 | svchost.exe | C:\Users\admin\Desktop\applicationfast.rtf.83fd | text | |
MD5:F5DB4394D70E6AB75ABAA02153EA1038 | SHA256:351A8C37480185852FC82E4FE984ADBBF2B26283A87DA209A01AD115529B4690 | |||
| 1056 | svchost.exe | C:\Users\admin\Desktop\formerunknown.jpg | text | |
MD5:F59C60E0D8B10A32F8A93DE3B7914A60 | SHA256:1F6580197D9F3A2832588652D9A1B75D62C6C40C6A24509D21F5F4A6599B2A1D | |||
| 1056 | svchost.exe | C:\Users\admin\Desktop\desktop.ini | text | |
MD5:DCD3363B48D4D35E23E4AD01EFC7095D | SHA256:A0C14635804F7C5978E4A5463E78940416EC9BDCC1EEF850BA3B65A4A6B48C12 | |||
| 1056 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.url | binary | |
MD5:83660DEB1A47E0B191FDA82BDFD61827 | SHA256:87089BD6FEDDA43B5E4D738B5BF246BA1B2E5C248B9220F0D1E742B827F30B0D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
49
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6344 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6344 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
6344 | SIHClient.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
6344 | SIHClient.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
6344 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
6344 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
6344 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6344 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |