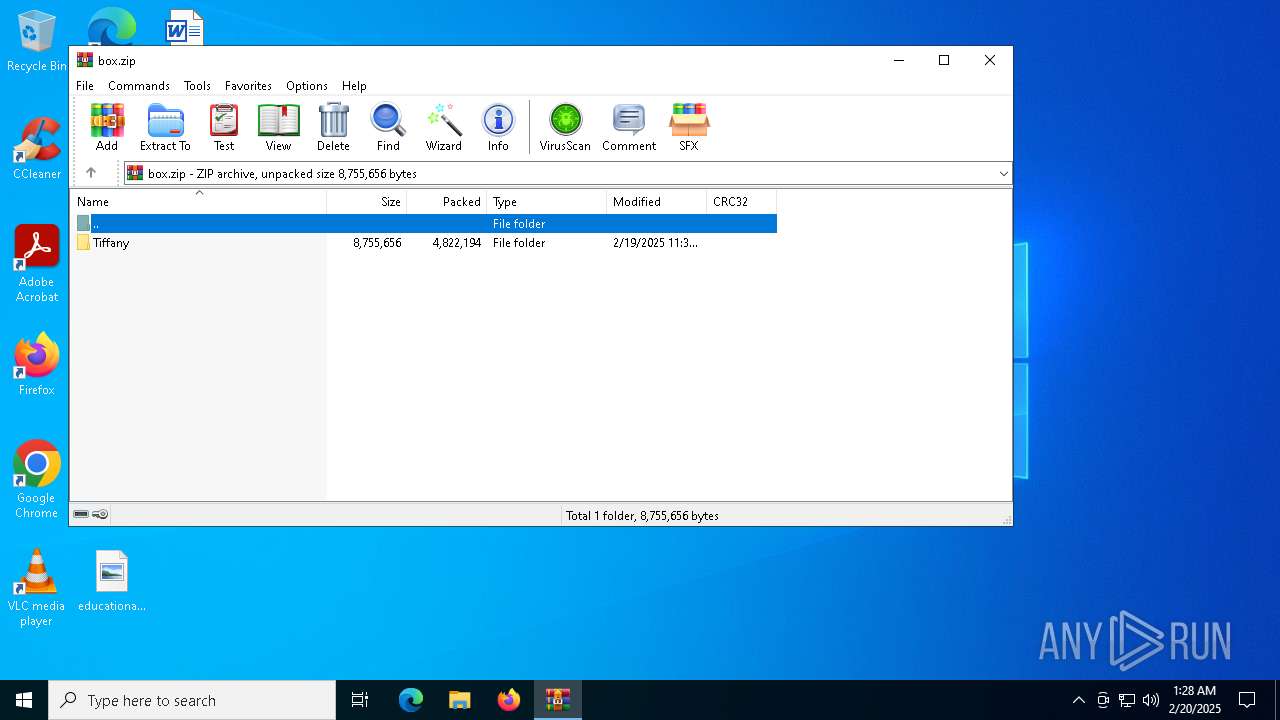
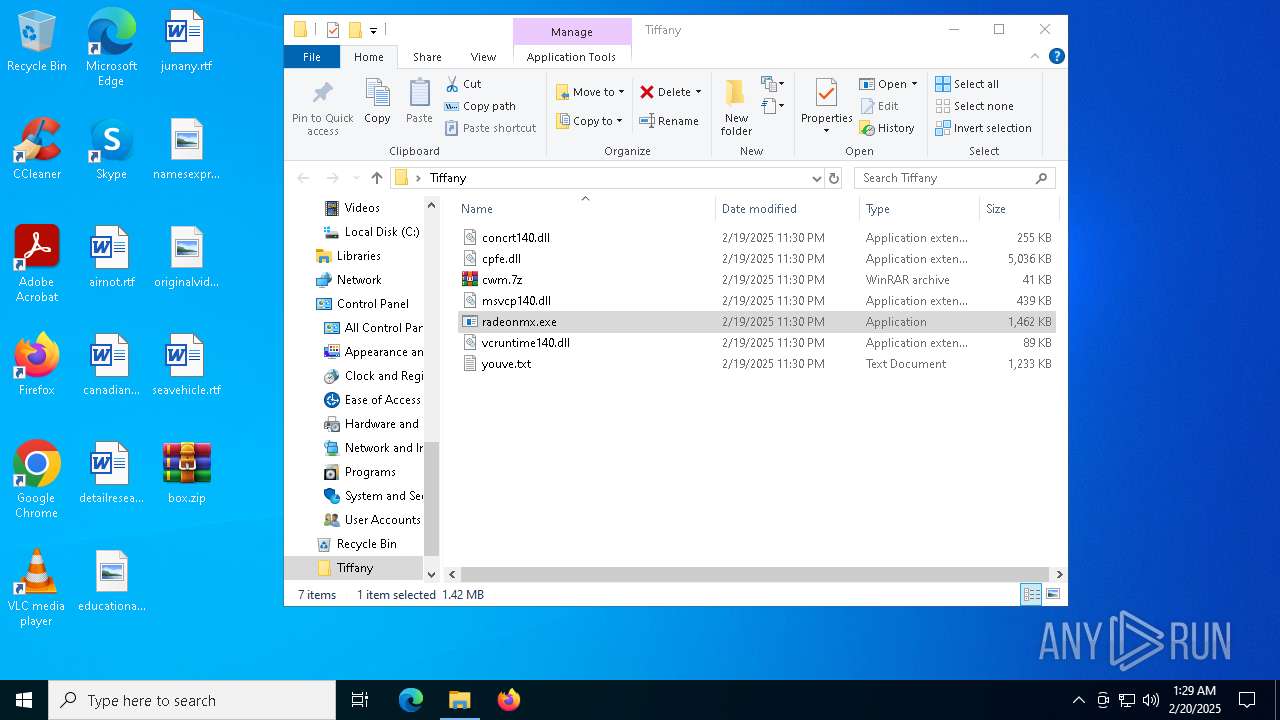
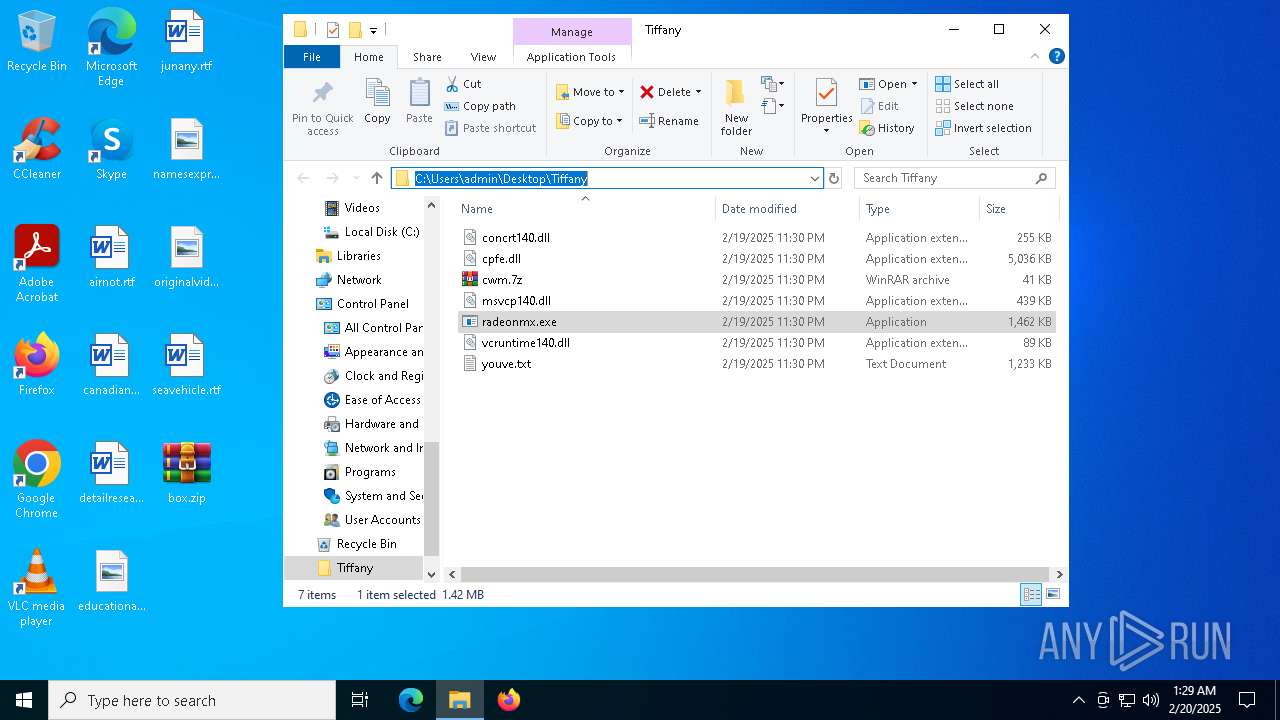
| File name: | box.zip |
| Full analysis: | https://app.any.run/tasks/0804c92e-61cf-471c-80bf-8c42f48eee6d |
| Verdict: | Malicious activity |
| Threats: | The Arechclient2 malware is a sophisticated .NET-based Remote Access Trojan (RAT) that collects sensitive information, such as browser credentials, from infected computers. It employs various stealth techniques, including Base64 encoding to obscure its code and the ability to pause activities to evade automated security tools. The malware also can adjust Windows Defender settings and uses code injection to manipulate legitimate processes. |
| Analysis date: | February 20, 2025, 01:28:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 78E4722D827D3AC1D739A6F2B0AC6120 |
| SHA1: | 849AEEAAFDA71301DE6A89C940493C7EC1276516 |
| SHA256: | 871F93042433B599C49BE3802B7A5694E2EC9F5BA42286661E643BD291E2597B |
| SSDEEP: | 98304:JGviaSl/W8F/RMLtuEww7AXkt7EJSGHL+EEMp8eu8kY0DG9tbbpDDUl+bgHr/Z0T:d4QSXCRcvp6 |
MALICIOUS
Actions looks like stealing of personal data
- MSBuild.exe (PID: 3832)
ARECHCLIENT2 has been detected (SURICATA)
- MSBuild.exe (PID: 3832)
XORed URL has been found (YARA)
- MSBuild.exe (PID: 3832)
ARECHCLIENT2 has been detected (YARA)
- MSBuild.exe (PID: 3832)
SUSPICIOUS
The process drops C-runtime libraries
- WinRAR.exe (PID: 6156)
- radeonmx.exe (PID: 6788)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6156)
- radeonmx.exe (PID: 6788)
Starts CMD.EXE for commands execution
- radeonmx.exe (PID: 6788)
Connects to unusual port
- MSBuild.exe (PID: 3832)
Executable content was dropped or overwritten
- radeonmx.exe (PID: 6788)
Starts a Microsoft application from unusual location
- radeonmx.exe (PID: 6788)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6156)
- radeonmx.exe (PID: 6788)
Reads the computer name
- radeonmx.exe (PID: 6788)
- MSBuild.exe (PID: 3832)
Creates files or folders in the user directory
- radeonmx.exe (PID: 6788)
Create files in a temporary directory
- radeonmx.exe (PID: 6788)
- MSBuild.exe (PID: 3832)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 3832)
Checks supported languages
- MSBuild.exe (PID: 3832)
- radeonmx.exe (PID: 6788)
Disables trace logs
- MSBuild.exe (PID: 3832)
Application launched itself
- firefox.exe (PID: 6700)
- firefox.exe (PID: 6704)
Manual execution by a user
- notepad++.exe (PID: 6676)
- firefox.exe (PID: 6700)
- radeonmx.exe (PID: 6788)
Checks proxy server information
- MSBuild.exe (PID: 3832)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(3832) MSBuild.exe
Decrypted-URLs (3)http://dl.google.com/chrome/install/375.126/chrome_installer.exeb
https://github.com
https://pastebin.com/raw/DWCCqGB0wKo+g
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:19 18:30:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Tiffany/ |
Total processes
150
Monitored processes
21
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1804 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4552 -childID 9 -isForBrowser -prefsHandle 5244 -prefMapHandle 4500 -prefsLen 31970 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {a289c9bf-0828-4eb8-ab48-2a9dc677136c} 6704 "\\.\pipe\gecko-crash-server-pipe.6704" 16f1e072150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1828 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4776 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4936 -prefMapHandle 4856 -prefsLen 38303 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {491528d7-4613-41f1-881a-d416880aae9a} 6704 "\\.\pipe\gecko-crash-server-pipe.6704" 16f243c6710 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5796 -childID 6 -isForBrowser -prefsHandle 5440 -prefMapHandle 5908 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c3bbbaf0-aa7e-4174-ad72-d3146df74f57} 6704 "\\.\pipe\gecko-crash-server-pipe.6704" 16f27c71850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 3832 | C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
xor-url(PID) Process(3832) MSBuild.exe Decrypted-URLs (3)http://dl.google.com/chrome/install/375.126/chrome_installer.exeb https://github.com https://pastebin.com/raw/DWCCqGB0wKo+g | |||||||||||||||
| 3836 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4024 -childID 8 -isForBrowser -prefsHandle 4616 -prefMapHandle 4552 -prefsLen 31970 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {d9a29942-530d-4226-8377-57ee2631fbf5} 6704 "\\.\pipe\gecko-crash-server-pipe.6704" 16f1e6e4d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 4320 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5036 -childID 4 -isForBrowser -prefsHandle 5040 -prefMapHandle 5044 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {fe1218ea-9e58-45ca-98e2-4d24c5001690} 6704 "\\.\pipe\gecko-crash-server-pipe.6704" 16f1e6e4150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 5836 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4076 -childID 2 -isForBrowser -prefsHandle 4072 -prefMapHandle 4032 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ef22cb7d-6366-4372-93c8-e455a524bd82} 6704 "\\.\pipe\gecko-crash-server-pipe.6704" 16f22957690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 6156 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\box.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6492 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5952 -childID 7 -isForBrowser -prefsHandle 5776 -prefMapHandle 5964 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f386a55e-c818-40d6-920e-aa2352eff95b} 6704 "\\.\pipe\gecko-crash-server-pipe.6704" 16f29377310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 6640 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5132 -childID 5 -isForBrowser -prefsHandle 5136 -prefMapHandle 5140 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9bf49de4-1e4b-4bce-93c2-40a98271ed09} 6704 "\\.\pipe\gecko-crash-server-pipe.6704" 16f1e6e4310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
18 380
Read events
18 347
Write events
33
Delete events
0
Modification events
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\box.zip | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
9
Suspicious files
245
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6808 | cmd.exe | C:\Users\admin\AppData\Local\Temp\xfjuctihwu | — | |
MD5:— | SHA256:— | |||
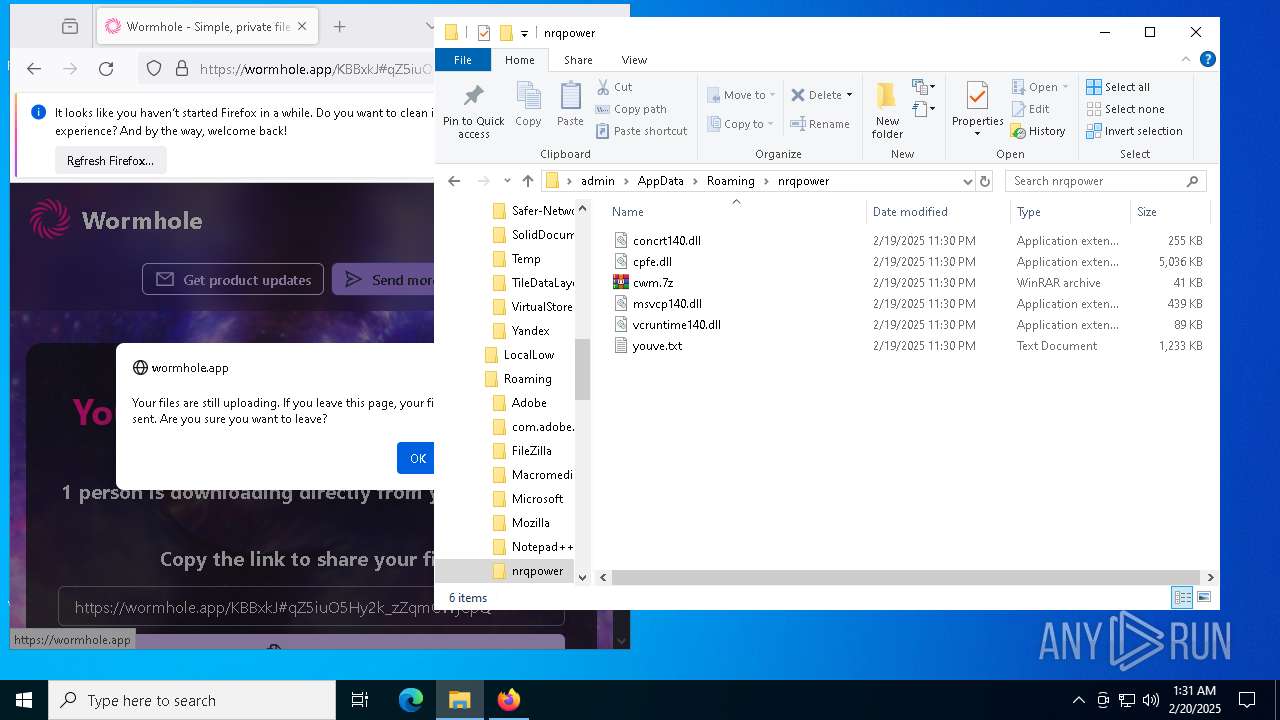
| 6156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6156.25356\Tiffany\concrt140.dll | executable | |
MD5:F36DAE6EA00F102B60A5011AF0732123 | SHA256:0A3894DD420ED6B4C7EBBDE463DBBDE69CDB032E290B1C86C21CCDAA4DA95526 | |||
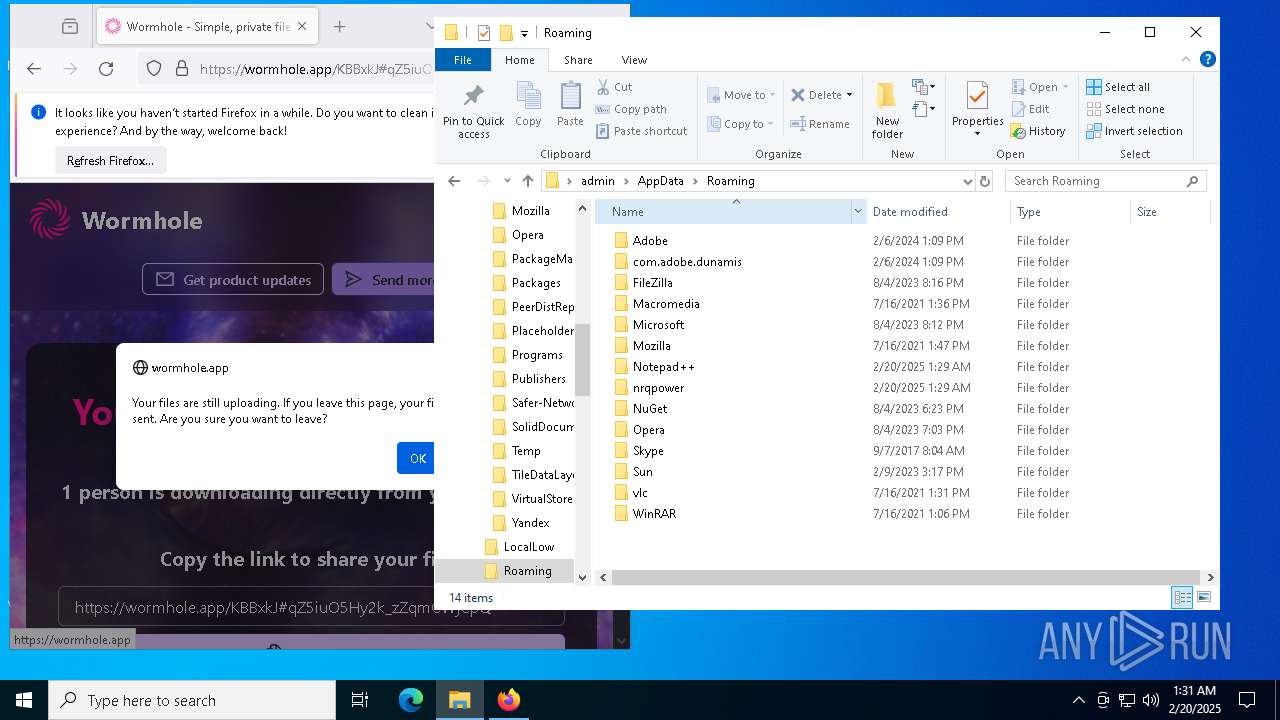
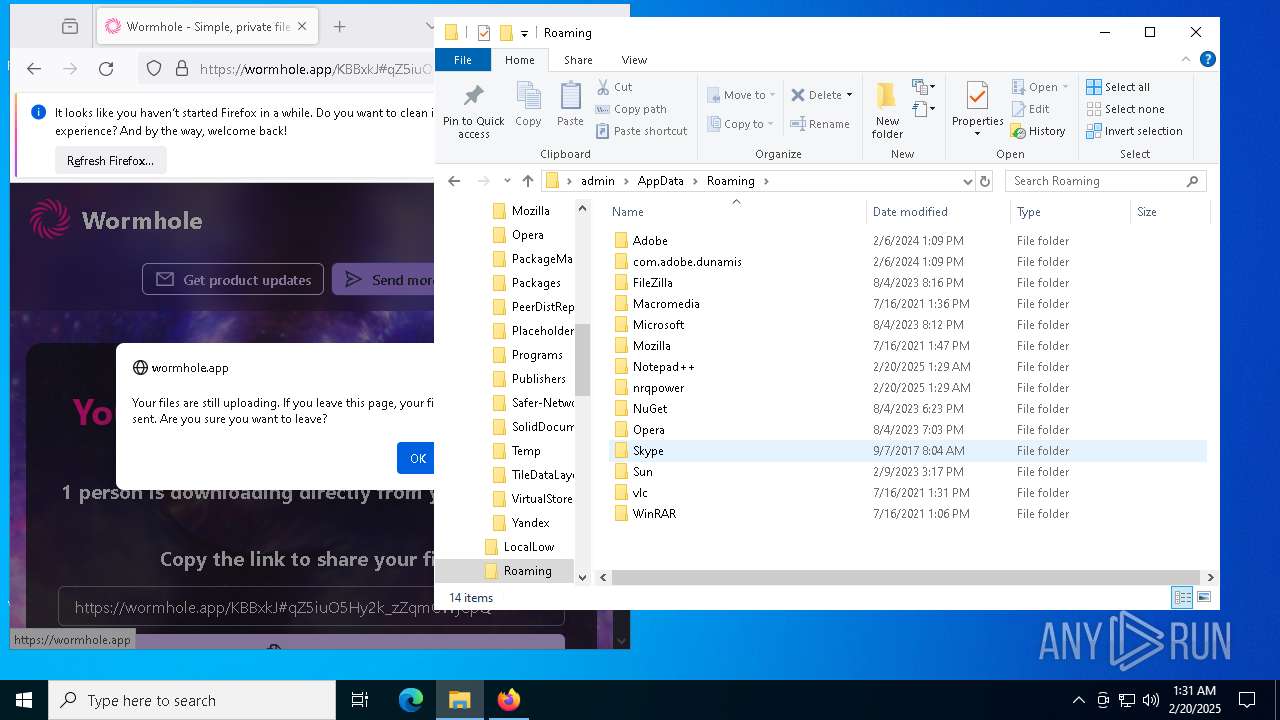
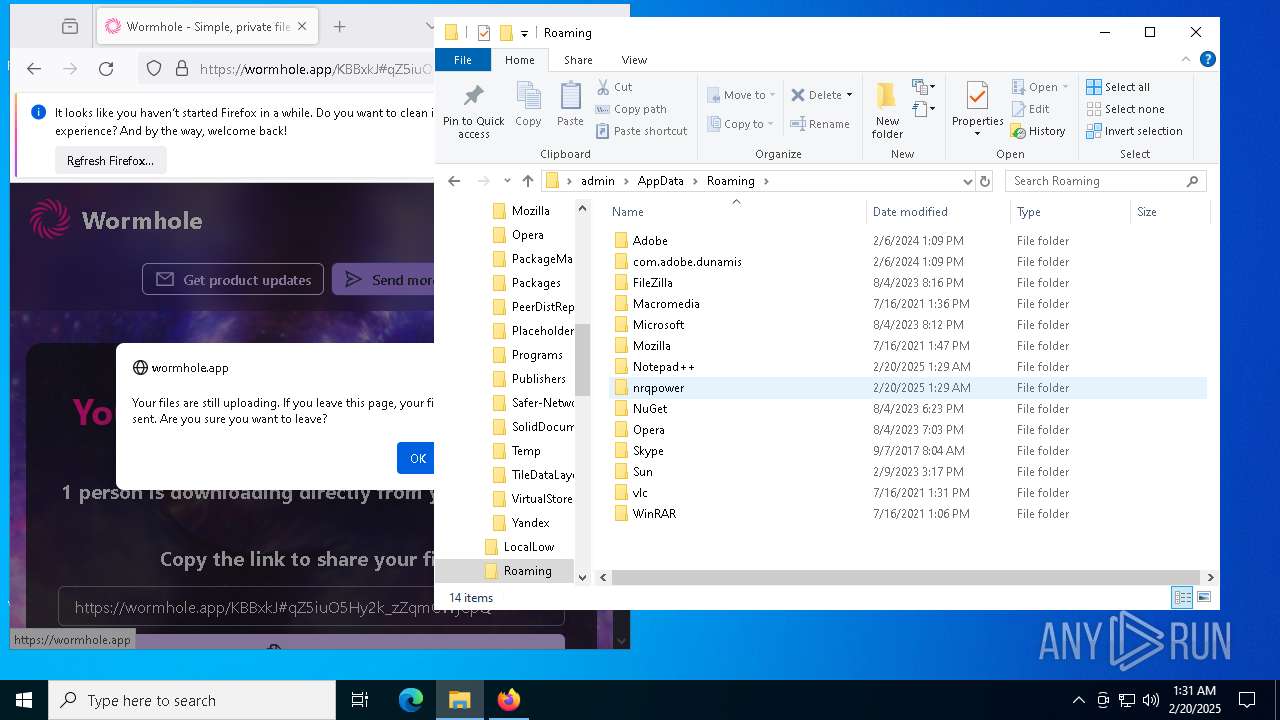
| 6788 | radeonmx.exe | C:\Users\admin\AppData\Roaming\nrqpower\vcruntime140.dll | executable | |
MD5:984C36E57E47581E267151ACA04E9580 | SHA256:E0850AD7C2431F822359E129C85B708373759A1AAADB70B3740642EA44345A04 | |||
| 6788 | radeonmx.exe | C:\Users\admin\AppData\Roaming\nrqpower\concrt140.dll | executable | |
MD5:F36DAE6EA00F102B60A5011AF0732123 | SHA256:0A3894DD420ED6B4C7EBBDE463DBBDE69CDB032E290B1C86C21CCDAA4DA95526 | |||
| 6788 | radeonmx.exe | C:\Users\admin\AppData\Roaming\nrqpower\msvcp140.dll | executable | |
MD5:CDAE969102E88F6704D853F9521EEDD2 | SHA256:4AD3DE3443D7658F74C978E7EB04730E3D812BC592FEE47BE4E6348D1FB4814E | |||
| 6156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6156.25356\Tiffany\radeonmx.exe | executable | |
MD5:38901633C833CBA7F682472CED0DBE4B | SHA256:A5C5487194F761DAC90E178C9C1753C0F47B041F3168B5C23A587F33F69E5089 | |||
| 6156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6156.25356\Tiffany\youve.txt | binary | |
MD5:073AEFDA3658A87C69413D6C8A945F2E | SHA256:16AE3090962BE67DD50D26504441FD72DFB03DD3FF74B09AF9CAEA387EECACF0 | |||
| 6788 | radeonmx.exe | C:\Users\admin\AppData\Local\Temp\10d4fb61 | binary | |
MD5:EB40EED61E96C5B5D36C6F388DF63709 | SHA256:8E2207E13C47E72A883015323A2F1D76596107E1FF71B4861EEE03B977AD02FD | |||
| 6156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6156.25356\Tiffany\cwm.7z | binary | |
MD5:BE15CFC47C332BD4248BB38C6131953F | SHA256:DA4A6578EDCA41CB20B3D28083F7221B7E8581A0F3F50FBE7CE80166DD1823E2 | |||
| 6704 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
186
DNS requests
125
Threats
216
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2144 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3224 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6704 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
3224 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6704 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
3832 | MSBuild.exe | GET | 200 | 92.255.85.36:9000 | http://92.255.85.36:9000/wbinjget?q=EF680CC9EFE0A8BCEC05D07897760CE8 | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2040 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 184.86.251.27:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 2.19.106.8:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3832 | MSBuild.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 13 |
3832 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Arechclient2 Backdoor/SecTopRAT Related Activity M2 (GET) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wormhole .app) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wormhole .app) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wormhole .app) |
6704 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (wormhole .app) |
6704 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (wormhole .app) |
6704 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (wormhole .app) |
6704 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (wormhole .app) |
6932 | firefox.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard Low Port) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|