| File name: | 87195b982b8300765deca2337f4789bd456f280c1e9f59e323bb260e47c5f710 |
| Full analysis: | https://app.any.run/tasks/27175d6d-7016-47f2-8225-11602fb839f4 |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | August 30, 2024, 10:00:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, ASCII text, with very long lines (22772), with CRLF line terminators |
| MD5: | 380A1A10A6AE1042B7601DD23C2D9026 |
| SHA1: | DD545A60D19563B656A306CBFE4F83D05EF5100A |
| SHA256: | 87195B982B8300765DECA2337F4789BD456F280C1E9F59E323BB260E47C5F710 |
| SSDEEP: | 24576:6IReDjcRFT52eRJVnnqYuEkMx6h89RxFriyIAiw+F8WSLCNOPGchoEKP6pgH85D:rf7xD1RxzIxmfzD |
MALICIOUS
Uses base64 encoding (SCRIPT)
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Creates a new folder (SCRIPT)
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Detects the decoding of a binary file from Base64 (SCRIPT)
- mmc.exe (PID: 6188)
- mmc.exe (PID: 3584)
GRIMRESOURCES has been detected (YARA)
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
COBALTSTRIKE has been detected (YARA)
- Warp.exe (PID: 2016)
SUSPICIOUS
Reads Microsoft Outlook installation path
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Reads Internet Explorer settings
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Runs shell command (SCRIPT)
- mmc.exe (PID: 6188)
- mmc.exe (PID: 3584)
Sets XML DOM element text (SCRIPT)
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Creates FileSystem object to access computer's file system (SCRIPT)
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Saves data to a binary file (SCRIPT)
- mmc.exe (PID: 6188)
- mmc.exe (PID: 3584)
Executable content was dropped or overwritten
- mmc.exe (PID: 6188)
Drops 7-zip archiver for unpacking
- mmc.exe (PID: 6188)
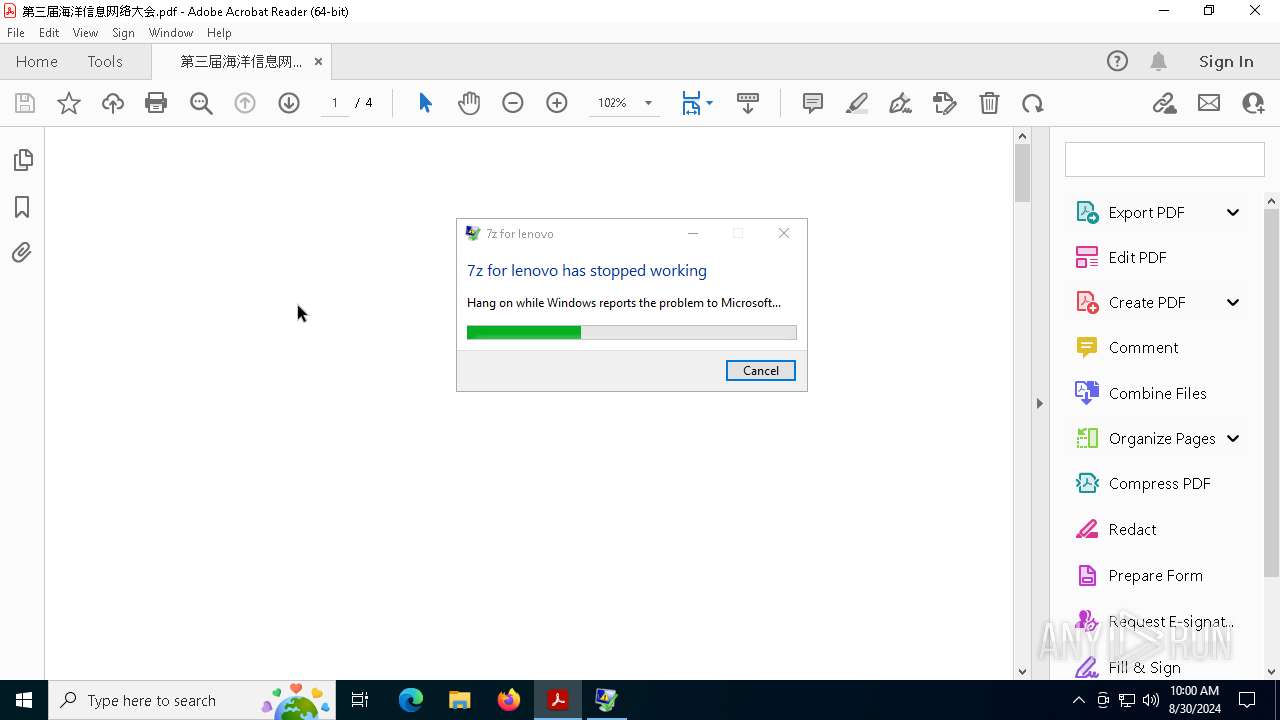
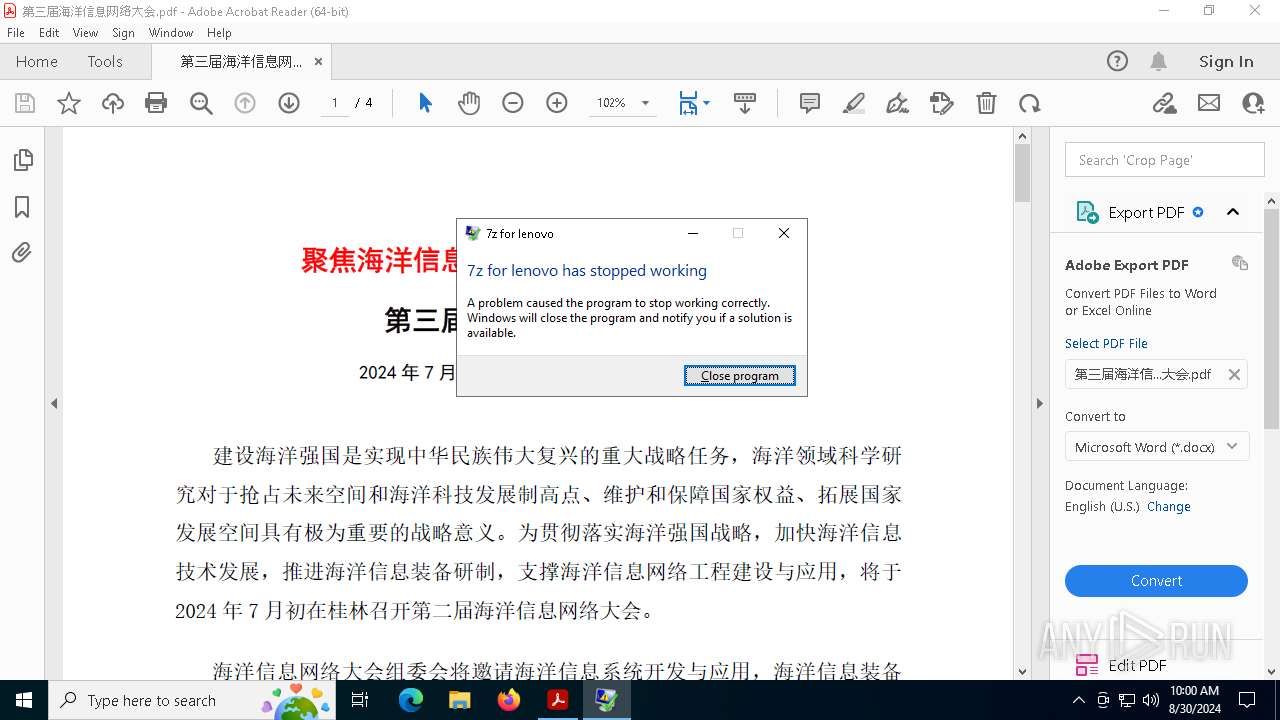
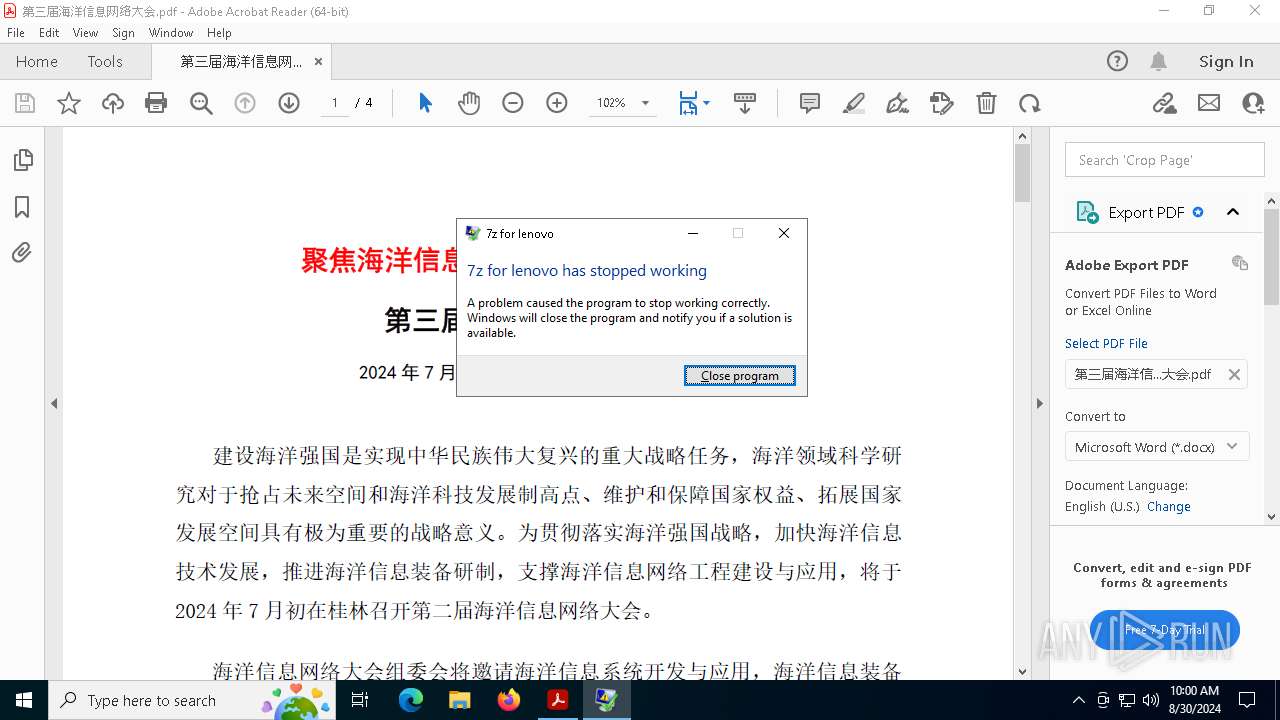
Executes application which crashes
- Warp.exe (PID: 3800)
Writes binary data to a Stream object (SCRIPT)
- mmc.exe (PID: 6188)
- mmc.exe (PID: 3584)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Reads security settings of Internet Explorer
- Warp.exe (PID: 2016)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 252)
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
- Acrobat.exe (PID: 6208)
- AdobeARM.exe (PID: 6876)
Reads the computer name
- identity_helper.exe (PID: 4016)
- Warp.exe (PID: 2016)
- Warp.exe (PID: 3800)
Reads Environment values
- identity_helper.exe (PID: 4016)
Checks supported languages
- identity_helper.exe (PID: 4016)
- Warp.exe (PID: 2016)
- Warp.exe (PID: 3800)
- acrobat_sl.exe (PID: 7572)
Application launched itself
- msedge.exe (PID: 2252)
- msedge.exe (PID: 5548)
- Acrobat.exe (PID: 3832)
- Acrobat.exe (PID: 6208)
- AcroCEF.exe (PID: 7548)
Reads Microsoft Office registry keys
- msedge.exe (PID: 2252)
- msedge.exe (PID: 5548)
- mmc.exe (PID: 6188)
- mmc.exe (PID: 3584)
Reads security settings of Internet Explorer
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Manual execution by a user
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6660)
- mmc.exe (PID: 6188)
- mmc.exe (PID: 2016)
Creates files or folders in the user directory
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
Checks proxy server information
- mmc.exe (PID: 3584)
- mmc.exe (PID: 6188)
- WerFault.exe (PID: 7304)
- Warp.exe (PID: 2016)
Creates files in the program directory
- mmc.exe (PID: 6188)
Create files in a temporary directory
- mmc.exe (PID: 3584)
Reads the software policy settings
- WerFault.exe (PID: 7304)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 6876)
Reads the machine GUID from the registry
- Warp.exe (PID: 2016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
CobalStrike
(PID) Process(2016) Warp.exe
C2 (1)delospartnership.info/js/MFWBlackFilter.js
BeaconTypeHTTPS
Port443
SleepTime11687
MaxGetSize1401668
Jitter32
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC/ZHDdu5y1xYV1yefVzjxPl09w
Qu6rVEQ4WpMZSL4Ik0AhBQCFIQXeSx4KqxERkKJOf8VYuf5pR80j6GLw1UZMnlHH
ZJ8/BQnw2VWAfWrk/Zx4ElceXfKmP2rK53UTzYLXTngLQ8pCM0NsYLO5DTI2M3Jf
gsiaFPFr7OugH0XDCQIDAQAB
-----END PUBLIC KEY-----
DNS_strategyround-robin
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\dvdplay.exe
Spawnto_x64%windir%\sysnative\mshta.exe
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark987654321
bStageCleanupTrue
bCFGCautionFalse
UserAgentMozilla/5.0 (Windows NT 6.1; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0
HttpPostUri/api/services/Accessibility/TTS/Create
Malleable_C2_InstructionsRemove 1 bytes at the end, Remove 1102 bytes from the beginning, Base64 decode, XOR mask w/ random key
HttpGet_Metadata
ConstHeaders (5)Host: static.mafengwo.net
Accept: application/json, text/plain, */*
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.5
Content-type: application/json
SessionId (3)mask
base64url
parameter: v
HttpPost_Metadata
ConstHeaders (5)Host: tongji.mafengwo.cn
Accept: application/json, text/plain, */*
Accept-Encoding: gzip, deflate, br, zstd
Accept-Language: zh-Hans
Content-type: application/json, application/json;charset=utf-8
SessionId (3)mask
base64url
parameter: q
Output (5)mask
netbios
prepend: {"text":"
append: ","timestamp":1619438443384,"appid":"231e66a83e25807b37aadae6d233d5af","referer":"https%3A%2F%2Fwww.mafengwo.cn%2Fsearch%2Fq.php%3Fq%3Dhjhoip%26seid%3D01B33405-0DDA-494F-BBF7-BC7BA4786030"}
print
bUsesCookies0000
Proxy_BehaviorUse IE settings
tcpFrameHeader0005aa0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0005a30000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXFalse
bProcInject_UseRWXTrue
bProcInject_MinAllocSize3817
ProcInject_PrependAppend_x869090..
ProcInject_PrependAppend_x649090..
ProcInject_Stub0b34150c342e35d2ffacb2227620d91c
ProcInject_AllocationMethodNtMapViewOfSection
BeaconTypeSMB
Port2
TRiD
| .svg | | | Scalable Vector Graphics (var.3) (64.4) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (22.2) |
| .html | | | HyperText Markup Language (13.3) |
EXIF
XMP
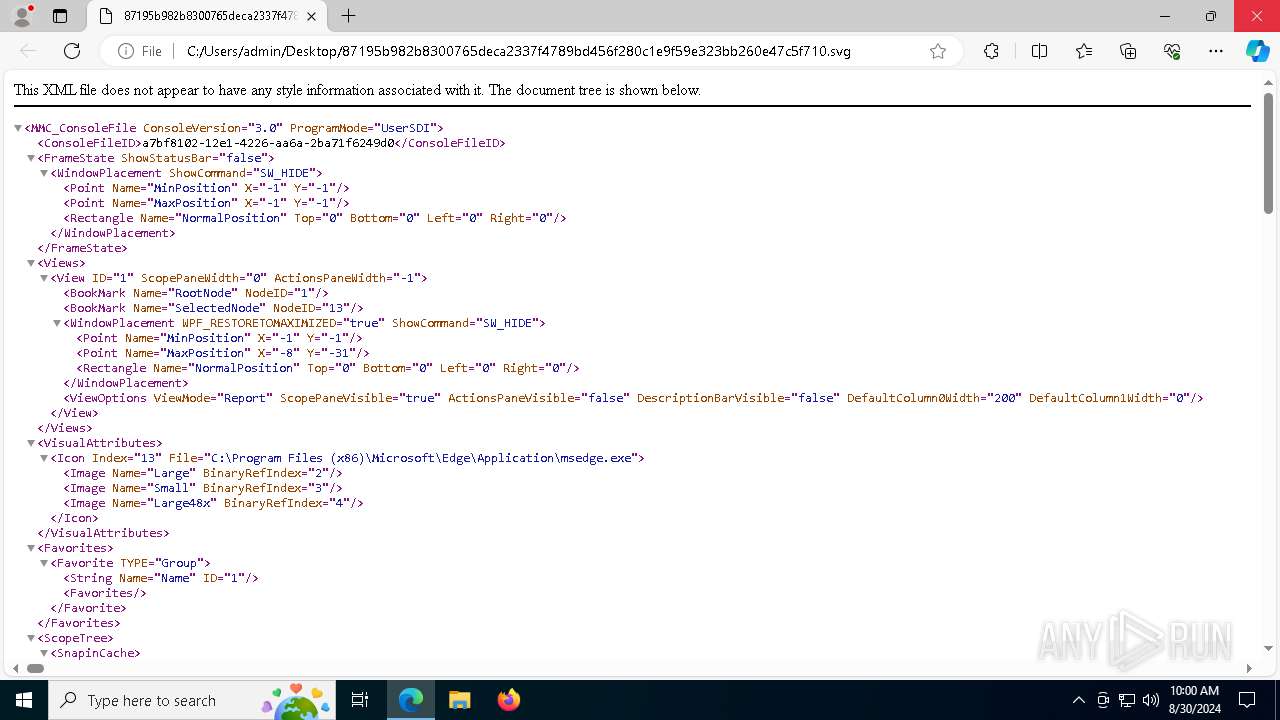
| MMC_ConsoleFileConsoleVersion: | 3 |
|---|---|
| MMC_ConsoleFileProgramMode: | UserSDI |
| MMC_ConsoleFileConsoleFileID: | a7bf8102-12e1-4226-aa6a-2ba71f6249d0 |
| MMC_ConsoleFileFrameStateShowStatusBar: | - |
| MMC_ConsoleFileFrameStateWindowPlacementShowCommand: | SW_HIDE |
| MMC_ConsoleFileFrameStateWindowPlacementPointName: | MinPosition |
| MMC_ConsoleFileFrameStateWindowPlacementPointX: | -1 |
| MMC_ConsoleFileFrameStateWindowPlacementPointY: | -1 |
| MMC_ConsoleFileFrameStateWindowPlacementRectangleName: | NormalPosition |
| MMC_ConsoleFileFrameStateWindowPlacementRectangleTop: | - |
| MMC_ConsoleFileFrameStateWindowPlacementRectangleBottom: | - |
| MMC_ConsoleFileFrameStateWindowPlacementRectangleLeft: | - |
| MMC_ConsoleFileFrameStateWindowPlacementRectangleRight: | - |
| MMC_ConsoleFileViewsViewId: | 1 |
| MMC_ConsoleFileViewsViewScopePaneWidth: | - |
| MMC_ConsoleFileViewsViewActionsPaneWidth: | -1 |
| MMC_ConsoleFileViewsViewBookMarkName: | RootNode |
| MMC_ConsoleFileViewsViewBookMarkNodeID: | 1 |
| MMC_ConsoleFileViewsViewWindowPlacementWpfRestoretomaximized: | |
| MMC_ConsoleFileViewsViewWindowPlacementShowCommand: | SW_HIDE |
| MMC_ConsoleFileViewsViewWindowPlacementPointName: | MinPosition |
| MMC_ConsoleFileViewsViewWindowPlacementPointX: | -1 |
| MMC_ConsoleFileViewsViewWindowPlacementPointY: | -1 |
| MMC_ConsoleFileViewsViewWindowPlacementRectangleName: | NormalPosition |
| MMC_ConsoleFileViewsViewWindowPlacementRectangleTop: | - |
| MMC_ConsoleFileViewsViewWindowPlacementRectangleBottom: | - |
| MMC_ConsoleFileViewsViewWindowPlacementRectangleLeft: | - |
| MMC_ConsoleFileViewsViewWindowPlacementRectangleRight: | - |
| MMC_ConsoleFileViewsViewViewOptionsViewMode: | Report |
| MMC_ConsoleFileViewsViewViewOptionsScopePaneVisible: | |
| MMC_ConsoleFileViewsViewViewOptionsActionsPaneVisible: | - |
| MMC_ConsoleFileViewsViewViewOptionsDescriptionBarVisible: | - |
| MMC_ConsoleFileViewsViewViewOptionsDefaultColumn0Width: | 200 |
| MMC_ConsoleFileViewsViewViewOptionsDefaultColumn1Width: | - |
| MMC_ConsoleFileVisualAttributesIconIndex: | 13 |
| MMC_ConsoleFileVisualAttributesIconFile: | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe |
| MMC_ConsoleFileVisualAttributesIconImageName: | Large |
| MMC_ConsoleFileVisualAttributesIconImageBinaryRefIndex: | 2 |
| MMC_ConsoleFileFavoritesFavoriteType: | Group |
| MMC_ConsoleFileFavoritesFavoriteStringName: | Name |
| MMC_ConsoleFileFavoritesFavoriteStringId: | 1 |
| MMC_ConsoleFileFavoritesFavoriteFavorites: | - |
| MMC_ConsoleFileScopeTreeSnapinCacheSnapinClsid: | {C96401CC-0E17-11D3-885B-00C04F72C717} |
| MMC_ConsoleFileScopeTreeSnapinCacheSnapinAllExtensionsEnabled: | |
| MMC_ConsoleFileScopeTreeNodesNodeId: | 1 |
| MMC_ConsoleFileScopeTreeNodesNodeImageIdx: | - |
| MMC_ConsoleFileScopeTreeNodesNodeClsid: | {C96401CC-0E17-11D3-885B-00C04F72C717} |
| MMC_ConsoleFileScopeTreeNodesNodePreload: | |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeId: | 13 |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeImageIdx: | - |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeClsid: | {C96401D1-0E17-11D3-885B-00C04F72C717} |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodePreload: | |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeNodes: | - |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeStringName: | Name |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeStringId: | 38 |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeComponentDatasComponentDataGuidName: | Snapin |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeComponentDatasComponentDataGuid: | {C96401D1-0E17-11D3-885B-00C04F72C717} |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeComponentDatasComponentDataStreamBinaryRefIndex: | - |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeComponents: | - |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeComponentsComponentViewID: | 1 |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeComponentsComponentGuidName: | Snapin |
| MMC_ConsoleFileScopeTreeNodesNodeNodesNodeComponentsComponentGuid: | {C96401CF-0E17-11D3-885B-00C04F72C717} |
| MMC_ConsoleFileScopeTreeNodesNodeStringName: | Name |
| MMC_ConsoleFileScopeTreeNodesNodeStringId: | 10 |
| MMC_ConsoleFileScopeTreeNodesNodeComponentDatasComponentDataGuidName: | Snapin |
| MMC_ConsoleFileScopeTreeNodesNodeComponentDatasComponentDataGuid: | {C96401CC-0E17-11D3-885B-00C04F72C717} |
| MMC_ConsoleFileScopeTreeNodesNodeComponents: | - |
| MMC_ConsoleFileConsoleTaskpads: | - |
| MMC_ConsoleFileViewSettingsCache: | - |
| MMC_ConsoleFileColumnSettingsCache: | - |
| MMC_ConsoleFileStringTablesIdentifierPoolAbsoluteMin: | 1 |
| MMC_ConsoleFileStringTablesIdentifierPoolAbsoluteMax: | 65535 |
| MMC_ConsoleFileStringTablesIdentifierPoolNextAvailable: | 40 |
| MMC_ConsoleFileStringTablesStringTableGuid: | {71E5B33E-1064-11D2-808F-0000F875A9CE} |
| MMC_ConsoleFileStringTablesStringTableStringsStringId: | 1 |
| MMC_ConsoleFileStringTablesStringTableStringsStringRefs: | 1 |
| MMC_ConsoleFileStringTablesStringTableStringsString: | Favorites |
| MMC_ConsoleFileBinaryStorageBinary: | (Binary data 28 bytes, use -b option to extract) |
| MMC_ConsoleFileBinaryStorageBinaryName: | CONSOLE_FILE_ICON_LARGE |
Total processes
186
Monitored processes
55
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4132 --field-trial-handle=2300,i,18158378424380019336,16536304608940082474,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 252 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\87195b982b8300765deca2337f4789bd456f280c1e9f59e323bb260e47c5f710.svg | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5496 --field-trial-handle=2444,i,2845615682389100023,16487756783935221517,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 888 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\AppData\Local\Temp\第三届海洋信息网络大会.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1172 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2288 --field-trial-handle=2300,i,18158378424380019336,16536304608940082474,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1828 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x1e8,0x1c0,0x1e0,0x16c,0x2a0,0x7fffd20a5fd8,0x7fffd20a5fe4,0x7fffd20a5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2016 | "C:\WINDOWS\system32\mmc.exe" "C:\Users\admin\Desktop\87195b982b8300765deca2337f4789bd456f280c1e9f59e323bb260e47c5f710.msc" | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Cloudflare\Warp.exe" t 8.8.8.8 | C:\Program Files\Cloudflare\Warp.exe | mmc.exe | ||||||||||||
User: admin Company: 7z Integrity Level: HIGH Description: 7z for lenovo Version: 2.7.20.7251 Modules
CobalStrike(PID) Process(2016) Warp.exe C2 (1)delospartnership.info/js/MFWBlackFilter.js BeaconTypeHTTPS Port443 SleepTime11687 MaxGetSize1401668 Jitter32 PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC/ZHDdu5y1xYV1yefVzjxPl09w
Qu6rVEQ4WpMZSL4Ik0AhBQCFIQXeSx4KqxERkKJOf8VYuf5pR80j6GLw1UZMnlHH
ZJ8/BQnw2VWAfWrk/Zx4ElceXfKmP2rK53UTzYLXTngLQ8pCM0NsYLO5DTI2M3Jf
gsiaFPFr7OugH0XDCQIDAQAB
-----END PUBLIC KEY----- DNS_strategyround-robin DNS_strategy_rotate_seconds-1 DNS_strategy_fail_x-1 DNS_strategy_fail_seconds-1 SpawnTo00000000000000000000000000000000 Spawnto_x86%windir%\syswow64\dvdplay.exe Spawnto_x64%windir%\sysnative\mshta.exe CryptoScheme0 HttpGet_VerbGET HttpPost_VerbPOST HttpPostChunk0 Watermark987654321 bStageCleanupTrue bCFGCautionFalse UserAgentMozilla/5.0 (Windows NT 6.1; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0 HttpPostUri/api/services/Accessibility/TTS/Create Malleable_C2_InstructionsRemove 1 bytes at the end, Remove 1102 bytes from the beginning, Base64 decode, XOR mask w/ random key HttpGet_Metadata ConstHeaders (5)Host: static.mafengwo.net Accept: application/json, text/plain, */* Accept-Encoding: gzip, deflate, br Accept-Language: en-US,en;q=0.5 Content-type: application/json SessionId (3)mask base64url parameter: v HttpPost_Metadata ConstHeaders (5)Host: tongji.mafengwo.cn Accept: application/json, text/plain, */* Accept-Encoding: gzip, deflate, br, zstd Accept-Language: zh-Hans Content-type: application/json, application/json;charset=utf-8 SessionId (3)mask base64url parameter: q Output (5)mask netbios prepend: {"text":" append: ","timestamp":1619438443384,"appid":"231e66a83e25807b37aadae6d233d5af","referer":"https%3A%2F%2Fwww.mafengwo.cn%2Fsearch%2Fq.php%3Fq%3Dhjhoip%26seid%3D01B33405-0DDA-494F-BBF7-BC7BA4786030"} print bUsesCookies0000 Proxy_BehaviorUse IE settings tcpFrameHeader0005aa0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 smbFrameHeader0005a30000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 KillDate0-0-0 bProcInject_StartRWXFalse bProcInject_UseRWXTrue bProcInject_MinAllocSize3817 ProcInject_PrependAppend_x869090.. ProcInject_PrependAppend_x649090.. ProcInject_Stub0b34150c342e35d2ffacb2227620d91c ProcInject_AllocationMethodNtMapViewOfSection (PID) Process(2016) Warp.exe BeaconTypeSMB Port2 | |||||||||||||||
| 2136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3640 --field-trial-handle=2300,i,18158378424380019336,16536304608940082474,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2232 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2720 --field-trial-handle=2444,i,2845615682389100023,16487756783935221517,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
49 647
Read events
49 319
Write events
313
Delete events
15
Modification events
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31128259 | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (252) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
3
Suspicious files
214
Text files
80
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF12a0dc.TMP | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF12a0dc.TMP | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF12a0dc.TMP | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF12a149.TMP | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF12a0fb.TMP | — | |
MD5:— | SHA256:— | |||
| 2252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
61
DNS requests
44
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7444 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6208 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
7444 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6244 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6856 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5476 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2252 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5476 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5476 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
update.googleapis.com |
| whitelisted |