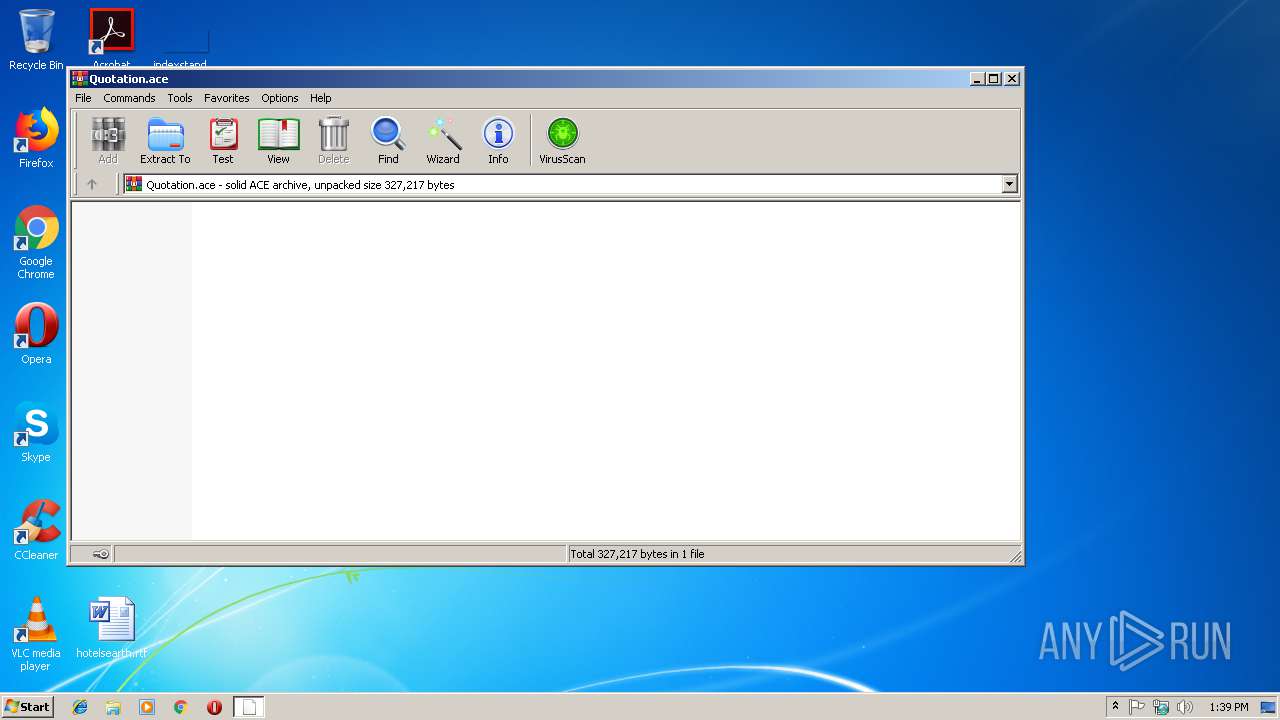
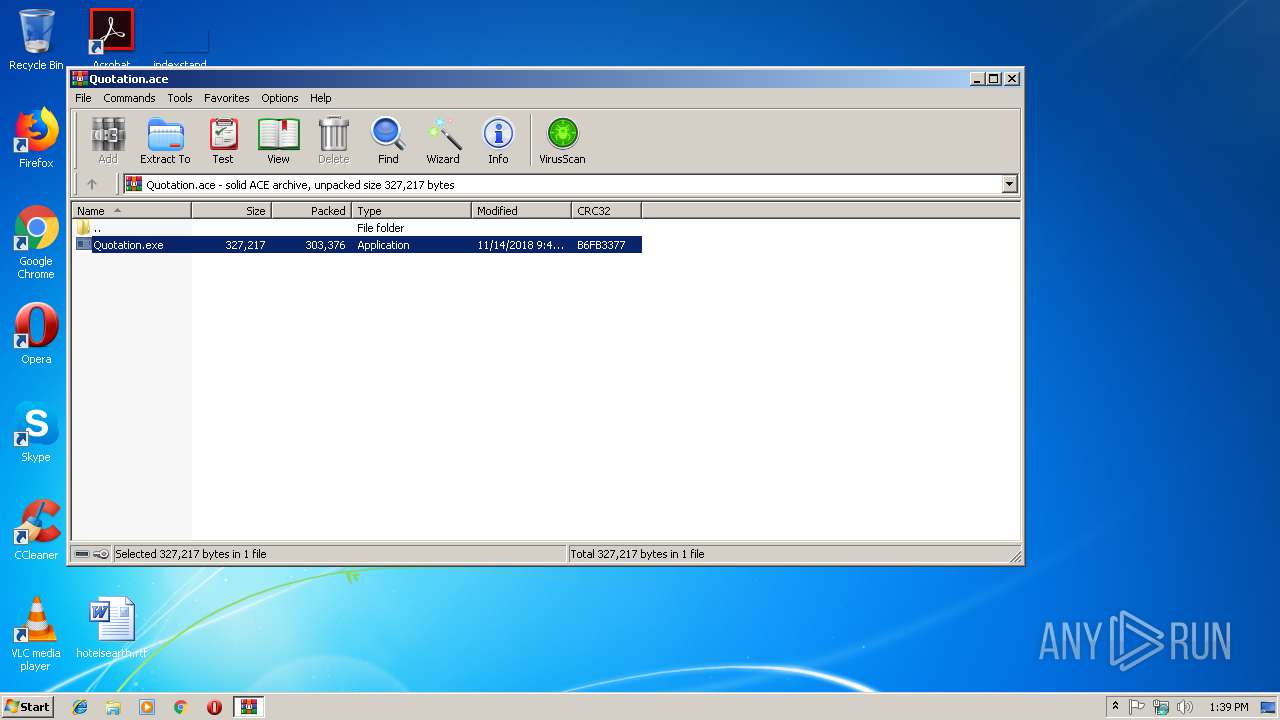
| File name: | Quotation.ace |
| Full analysis: | https://app.any.run/tasks/eb42c445-c1ef-4ec4-b746-71f1a81ee710 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | November 15, 2018, 13:39:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | ACE archive data version 20, from Win/32, version 20 to extract, solid |
| MD5: | A8688EBF68CDA818AABB00CCC040F146 |
| SHA1: | 868C9957B6578393F2B957DF92DCF9E772B3963A |
| SHA256: | 86ECA78C8168060CC9330CBC382871BB186B489A6AF4C60930F9D2A4958F262D |
| SSDEEP: | 6144:jNpexHfF1KAYqmqVp2c0+hv1W9Ir98EGkUOZGnrsKRUYrxO+:jNaHfF1KAYsSwv1958EGktCrTXrk+ |
MALICIOUS
Application was dropped or rewritten from another process
- Quotation.exe (PID: 3732)
- Quotation.exe (PID: 3480)
Changes the autorun value in the registry
- NETSTAT.EXE (PID: 3900)
Formbook was detected
- NETSTAT.EXE (PID: 3900)
- Firefox.exe (PID: 2336)
Actions looks like stealing of personal data
- NETSTAT.EXE (PID: 3900)
Connects to CnC server
- explorer.exe (PID: 1716)
FORMBOOK was detected
- explorer.exe (PID: 1716)
SUSPICIOUS
Uses NETSTAT.EXE to discover network connections
- explorer.exe (PID: 1716)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3184)
- Quotation.exe (PID: 3732)
- NETSTAT.EXE (PID: 3900)
Loads DLL from Mozilla Firefox
- NETSTAT.EXE (PID: 3900)
Application launched itself
- Quotation.exe (PID: 3732)
Creates files in the user directory
- NETSTAT.EXE (PID: 3900)
- explorer.exe (PID: 1716)
Reads Internet Cache Settings
- explorer.exe (PID: 1716)
Starts CMD.EXE for commands execution
- NETSTAT.EXE (PID: 3900)
INFO
Starts Microsoft Office Application
- explorer.exe (PID: 1716)
Creates files in the user directory
- Firefox.exe (PID: 2336)
- WINWORD.EXE (PID: 3756)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ace | | | ACE compressed archive (100) |
|---|
Total processes
43
Monitored processes
8
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1716 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2336 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | NETSTAT.EXE | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2724 | /c del "C:\Users\admin\Desktop\Quotation.exe" | C:\Windows\System32\cmd.exe | — | NETSTAT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3184 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Quotation.ace" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3480 | "C:\Users\admin\Desktop\Quotation.exe" | C:\Users\admin\Desktop\Quotation.exe | — | Quotation.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\Desktop\Quotation.exe" | C:\Users\admin\Desktop\Quotation.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3756 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\positivefi.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3900 | "C:\Windows\System32\NETSTAT.EXE" | C:\Windows\System32\NETSTAT.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 441
Read events
4 038
Write events
394
Delete events
9
Modification events
| (PID) Process: | (1716) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Quotation.ace | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\ACE Compression Software\ActiveAce\2.0 |
| Operation: | write | Name: | Count |
Value: 0 | |||
Executable files
4
Suspicious files
2
Text files
3
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3732 | Quotation.exe | C:\Users\admin\AppData\Local\Temp\Subabbot | binary | |
MD5:— | SHA256:— | |||
| 3184 | WinRAR.exe | C:\Users\admin\Desktop\Quotation.exe | executable | |
MD5:— | SHA256:— | |||
| 3732 | Quotation.exe | C:\Users\admin\AppData\Local\Temp\squamules.dll | executable | |
MD5:— | SHA256:— | |||
| 1716 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012018111520181116\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3756 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\positivefi.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3756 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1716 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\a7bd71699cd38d1c.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 3756 | WINWORD.EXE | C:\Users\admin\Desktop\~$sitivefi.rtf | pgc | |
MD5:— | SHA256:— | |||
| 1716 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 1716 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\positivefi.rtf.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
17
DNS requests
8
Threats
38
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1716 | explorer.exe | POST | — | 69.172.201.153:80 | http://www.epijet.com/c150/ | US | — | — | malicious |
1716 | explorer.exe | GET | 463 | 69.172.201.153:80 | http://www.epijet.com/c150/?E60dc=pni640ejZK98OGMew+UKzjQISQX+MOC69s07g5AQtnHb8J7/7RYHgtARVp17v2pOeG1tEg==&k2UD-=aDvHFTbp_&sql=1 | US | html | 8.64 Kb | malicious |
1716 | explorer.exe | GET | 301 | 176.28.3.57:80 | http://www.qiiomagazine.com/c150/?E60dc=Jjpw17W/CV4Dl/hw6Gffx2vQwfAt7T0J9b3FVjUPKI7wRBEZx2G8H59RxmGcU4PKrZc4kw==&k2UD-=aDvHFTbp_ | DE | html | 332 b | malicious |
1716 | explorer.exe | GET | 404 | 69.90.161.105:80 | http://www.paulandterra.com/c150/?E60dc=3trVv4qB6CUjoNOsFxZcUamXkTpBUc+SiOB7o2yJnlR94dxmw4q+EyLJged4sSbjebB7/w==&k2UD-=aDvHFTbp_&sql=1 | CA | html | 10.0 Kb | malicious |
1716 | explorer.exe | POST | — | 69.90.161.105:80 | http://www.paulandterra.com/c150/ | CA | — | — | malicious |
1716 | explorer.exe | POST | — | 69.90.161.105:80 | http://www.paulandterra.com/c150/ | CA | — | — | malicious |
1716 | explorer.exe | POST | — | 199.192.24.70:80 | http://www.jankolet.com/c150/ | US | — | — | malicious |
1716 | explorer.exe | GET | 200 | 199.192.24.70:80 | http://www.jankolet.com/c150/?E60dc=eOKNQU2qheZPtHUTgAiPln1mgMiipmw0JdfudHEk9NgG8bToTRA1eq46sWXmKfs46/6E/w==&k2UD-=aDvHFTbp_&sql=1 | US | binary | 323 Kb | malicious |
1716 | explorer.exe | POST | — | 69.172.201.153:80 | http://www.epijet.com/c150/ | US | — | — | malicious |
1716 | explorer.exe | POST | — | 199.192.24.70:80 | http://www.jankolet.com/c150/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1716 | explorer.exe | 176.28.3.57:80 | www.qiiomagazine.com | Host Europe GmbH | DE | malicious |
1716 | explorer.exe | 69.90.161.105:80 | www.paulandterra.com | Peer 1 Network (USA) Inc. | CA | malicious |
1716 | explorer.exe | 192.0.78.25:80 | www.vickiscottmiller.com | Automattic, Inc | US | malicious |
1716 | explorer.exe | 69.172.201.153:80 | www.epijet.com | Dosarrest Internet Security LTD | US | malicious |
1716 | explorer.exe | 199.192.24.70:80 | www.jankolet.com | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.qiiomagazine.com |
| malicious |
www.yumakun.com |
| unknown |
www.paulandterra.com |
| malicious |
www.moosehead411.com |
| unknown |
www.ttgan29.com |
| unknown |
www.vickiscottmiller.com |
| malicious |
www.epijet.com |
| malicious |
www.jankolet.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1716 | explorer.exe | A Network Trojan was detected | SC SPYWARE Trojan-Spy.Win32.Noon |
1716 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
1716 | explorer.exe | A Network Trojan was detected | SC SPYWARE Trojan-Spy.Win32.Noon |
1716 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
1716 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
1716 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
1716 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
1716 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
1716 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
1716 | explorer.exe | A Network Trojan was detected | SC SPYWARE Trojan-Spy.Win32.Noon |
11 ETPRO signatures available at the full report