| File name: | 18.exe |
| Full analysis: | https://app.any.run/tasks/49149cd0-a7cf-4258-aa91-7bd49b4bd6d8 |
| Verdict: | Malicious activity |
| Threats: | Sality is a highly sophisticated malware known for infecting executable files and rapidly spreading across networks. It primarily creates a peer-to-peer botnet that is used for malicious activities such as spamming, data theft, and downloading additional malware. Sality has strong persistence mechanisms, including disabling security software, making it difficult to remove. Its ability to spread quickly and silently, along with its polymorphic nature, allows it to evade detection by traditional antivirus solutions. |
| Analysis date: | October 30, 2023, 10:10:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 39053070221731475E730D1BE9BBBD20 |
| SHA1: | 7A5D5A3F0E643A440F4A91F57F2C38FBA98F689F |
| SHA256: | 86DB2B85EE8BAFB506518366FFE89EE7CACCE765D8803465688973DDD228FE43 |
| SSDEEP: | 3072:L7TXv1dANwp1qUTqXMlvee/PxY1E27ZuNp9X+LQbiwk1ZDXyANV:ZdAN41DqXcuElnVkQbiwk1ZDXyUV |
MALICIOUS
Runs injected code in another process
- 18.exe (PID: 3820)
- 18.exe (PID: 2636)
Changes appearance of the Explorer extensions
- 18.exe (PID: 3820)
Application was injected by another process
- taskeng.exe (PID: 368)
- ctfmon.exe (PID: 1708)
- explorer.exe (PID: 1400)
- dwm.exe (PID: 928)
Changes firewall settings
- 18.exe (PID: 2636)
UAC/LUA settings modification
- 18.exe (PID: 2636)
SALITY has been detected (SURICATA)
- 18.exe (PID: 2636)
- taskeng.exe (PID: 368)
Connects to the CnC server
- 18.exe (PID: 2636)
- taskeng.exe (PID: 368)
Drops the executable file immediately after the start
- 18.exe (PID: 2636)
Changes Security Center notification settings
- 18.exe (PID: 2636)
Creates a writable file the system directory
- 18.exe (PID: 2636)
SUSPICIOUS
Reads the Internet Settings
- 18.exe (PID: 3820)
- taskeng.exe (PID: 368)
Starts SC.EXE for service management
- cmd.exe (PID: 2680)
- 18.exe (PID: 2636)
Starts CMD.EXE for commands execution
- 18.exe (PID: 3820)
Executes as Windows Service
- 18.exe (PID: 2636)
Process drops legitimate windows executable
- 18.exe (PID: 2636)
Checks Windows Trust Settings
- 18.exe (PID: 2636)
Reads settings of System Certificates
- taskeng.exe (PID: 368)
INFO
Checks supported languages
- 18.exe (PID: 3820)
- 18.exe (PID: 2636)
Reads the computer name
- 18.exe (PID: 3820)
- 18.exe (PID: 2636)
Manual execution by a user
- regedit.exe (PID: 2428)
- regedit.exe (PID: 3296)
Changes appearance of the Explorer extensions
- taskeng.exe (PID: 368)
Drops the executable file immediately after the start
- taskeng.exe (PID: 368)
Create files in a temporary directory
- taskeng.exe (PID: 368)
- 18.exe (PID: 2636)
Reads the machine GUID from the registry
- 18.exe (PID: 2636)
Checks proxy server information
- taskeng.exe (PID: 368)
Creates files or folders in the user directory
- taskeng.exe (PID: 368)
Reads security settings of Internet Explorer
- taskeng.exe (PID: 368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:08:09 16:37:49+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 57344 |
| InitializedDataSize: | 28672 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5013 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.0.10 |
| ProductVersionNumber: | 1.3.0.10 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| Comments: | 2013-12-13T11:25:29.968000 |
| CompanyName: | 百度在线网络技术(北京)有限公司 |
| FileDescription: | 升级模块 |
| FileVersion: | 1.3.0.10 |
| InternalName: | BDMiniDlUpdate.exe |
| LegalCopyright: | Copyright (C) 2013 Baidu Inc. |
| LegalTrademarks: | Baidu |
| OriginalFileName: | BDMiniDlUpdate.exe |
| PrivateBuild: | 1.3.0.10 |
| ProductName: | 百度软件中心助手 |
| ProductVersion: | 1.3.0.10 |
| SpecialBuild: | - |
Total processes
102
Monitored processes
37
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
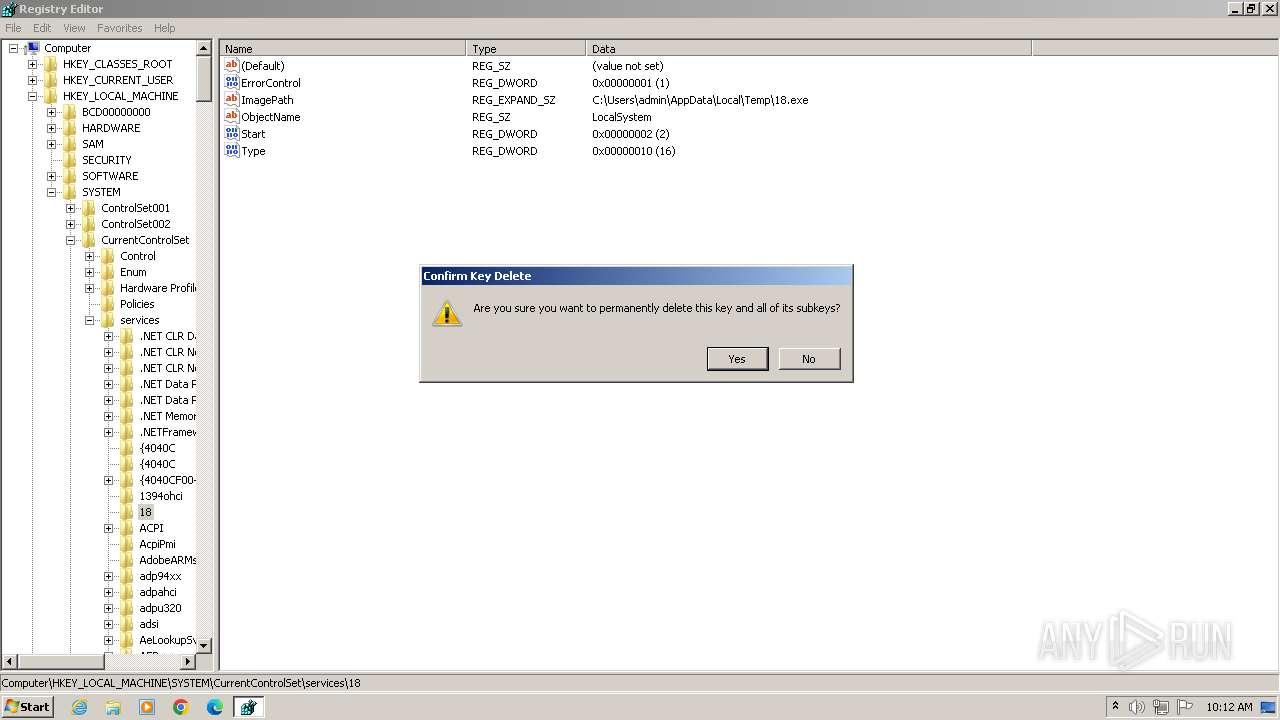
| 284 | "C:\Windows\System32\sc.exe" config "18" start= auto binPath= "C:\Users\admin\AppData\Local\Temp\18_238.exe" | C:\Windows\System32\sc.exe | — | 18.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | taskeng.exe {A138C7FA-105D-4695-A941-2BE80CB32127} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 528 | "C:\Windows\System32\sc.exe" config "18" start= auto binPath= "C:\Users\admin\AppData\Local\Temp\18_320.exe" | C:\Windows\System32\sc.exe | — | 18.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | sc create "18" binPath= "C:\Users\admin\AppData\Local\Temp\18.exe" start= auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 928 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1400 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1708 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1736 | "C:\Windows\System32\sc.exe" config "18" start= auto binPath= "C:\Users\admin\AppData\Local\Temp\18_401.exe" | C:\Windows\System32\sc.exe | — | 18.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2060 | "C:\Windows\System32\sc.exe" config "18" start= auto binPath= "C:\Users\admin\AppData\Local\Temp\18_418.exe" | C:\Windows\System32\sc.exe | — | 18.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2080 | "C:\Windows\System32\sc.exe" config "18" start= auto binPath= "C:\Users\admin\AppData\Local\Temp\18_254.exe" | C:\Windows\System32\sc.exe | — | 18.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 076
Read events
11 936
Write events
1 137
Delete events
3
Modification events
| (PID) Process: | (3820) 18.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | Hidden |
Value: 1 | |||
| (PID) Process: | (3820) 18.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3820) 18.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3820) 18.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3820) 18.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1400) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000F6D6788197A75D498472ACE88906AC8D0000000002000000000010660000000100002000000048832D3FD0459F35F292D4F0571B992C6EB9F500D4ED7BC3B99927FC5331D217000000000E80000000020000200000003EFBFF3AEC091353AF9E58D48DF2D06E9D1BDED94E4937159293C20E513DDF0F3000000087034FE3522EDDAC6E83C331CAE7E3CB92B187260C4DAD8D1C31F9039AB30BE9E56E6C6EE2A54DD7C0FCB3257D6FF55F4000000040B806FFF8B32ABD66EABA7F35A86503B0F300E1B9A976FC4B3F6328F133A31ACB461ADFC86BE84974CB3AD9119C225504F24589D1CDC1655DA54BABE9CEF265 | |||
| (PID) Process: | (2636) 18.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Svc |
| Operation: | write | Name: | AntiVirusOverride |
Value: 0 | |||
| (PID) Process: | (2636) 18.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Svc |
| Operation: | write | Name: | FirewallOverride |
Value: 0 | |||
| (PID) Process: | (2636) 18.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 1 | |||
| (PID) Process: | (2636) 18.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\SharedAccess\Parameters\FirewallPolicy\StandardProfile |
| Operation: | write | Name: | EnableFirewall |
Value: 0 | |||
Executable files
31
Suspicious files
15
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2636 | 18.exe | C:\Windows\SYSTEM.INI | binary | |
MD5:15DEDB02EB1D938A2928571B57BFC7E2 | SHA256:8B600C39163AAD2F697EBE1D5203A7B2133206AA76A7BBCD83DDC460547F1566 | |||
| 2636 | 18.exe | C:\Windows\TEMP\winxeai.exe | executable | |
MD5:25AA9BB549ECC7BB6100F8D179452508 | SHA256:DF83A0D6940600E4C4954F4874FCD4DD73E781E6690C3BF56F51C95285484A3C | |||
| 2636 | 18.exe | C:\eimvqn.pif | executable | |
MD5:1A29971DBF7B2CE40E5B5020FBD37FA3 | SHA256:7275C9D95787C3580AEAD769BF67E7464F5D640BFF3C753B1B619A0EF79DCBB1 | |||
| 2636 | 18.exe | C:\Users\admin\AppData\Local\Temp\18_189.exe | executable | |
MD5:39053070221731475E730D1BE9BBBD20 | SHA256:86DB2B85EE8BAFB506518366FFE89EE7CACCE765D8803465688973DDD228FE43 | |||
| 2636 | 18.exe | C:\Users\admin\AppData\Local\Temp\18_173.exe | executable | |
MD5:39053070221731475E730D1BE9BBBD20 | SHA256:86DB2B85EE8BAFB506518366FFE89EE7CACCE765D8803465688973DDD228FE43 | |||
| 2636 | 18.exe | C:\PROGRA~1\COMMON~1\MICROS~1\IME14\SHARED\IMEKLMG.EXE | executable | |
MD5:99384D3C21859C15846CA6575681CF71 | SHA256:52716B2B63C304311F48467A1D1DDE828F2B0506BBF711FF8599350432100603 | |||
| 368 | taskeng.exe | C:\Users\admin\AppData\Local\Temp\oteky.exe | executable | |
MD5:25AA9BB549ECC7BB6100F8D179452508 | SHA256:DF83A0D6940600E4C4954F4874FCD4DD73E781E6690C3BF56F51C95285484A3C | |||
| 2636 | 18.exe | C:\autorun.inf | text | |
MD5:B792FED2E65B9531FFC81527FCDC5B3F | SHA256:7F279D67AB16FCEDBF50821569577DAAD64C39BFFF31757089F451E56F732B08 | |||
| 2636 | 18.exe | C:\Users\admin\AppData\Local\Temp\18_238.exe | executable | |
MD5:39053070221731475E730D1BE9BBBD20 | SHA256:86DB2B85EE8BAFB506518366FFE89EE7CACCE765D8803465688973DDD228FE43 | |||
| 2636 | 18.exe | C:\Users\admin\AppData\Local\Temp\18_222.exe | executable | |
MD5:39053070221731475E730D1BE9BBBD20 | SHA256:86DB2B85EE8BAFB506518366FFE89EE7CACCE765D8803465688973DDD228FE43 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
34
DNS requests
16
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2636 | 18.exe | GET | 200 | 104.198.2.251:80 | http://www.careerdesk.org/images/xs.jpg?21e7de=2222046 | unknown | — | — | unknown |
2636 | 18.exe | GET | 200 | 34.174.61.199:80 | http://arthur.niria.biz/xs.jpg?21ea11=8890436 | unknown | — | — | unknown |
2636 | 18.exe | GET | 302 | 72.14.178.174:80 | http://amsamex.com/xs.jpg?21ef51=6671859 | unknown | — | — | unknown |
— | — | GET | 200 | 34.174.61.199:80 | http://apple-pie.in/images/xs.jpg?21f28d=13348686 | unknown | — | — | unknown |
368 | taskeng.exe | GET | 200 | 104.198.2.251:80 | http://www.careerdesk.org/images/xs.jpg?2206ff=15610105 | unknown | — | — | unknown |
368 | taskeng.exe | GET | 200 | 34.174.61.199:80 | http://arthur.niria.biz/xs.jpg?2208c4=2230468 | unknown | — | — | unknown |
368 | taskeng.exe | GET | 302 | 72.14.178.174:80 | http://amsamex.com/xs.jpg?220a1c=11154060 | unknown | — | — | unknown |
2636 | 18.exe | GET | 200 | 67.26.83.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5be3f3a9fc175c91 | unknown | compressed | 4.66 Kb | unknown |
2636 | 18.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.51 Kb | unknown |
368 | taskeng.exe | GET | 302 | 37.230.104.89:80 | http://www.ampyazilim.com.tr/images/xs2.jpg?220dc6=22317500 | unknown | html | 683 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2636 | 18.exe | 104.198.2.251:80 | www.careerdesk.org | GOOGLE-CLOUD-PLATFORM | US | unknown |
2636 | 18.exe | 34.174.61.199:80 | arthur.niria.biz | GOOGLE-CLOUD-PLATFORM | US | unknown |
2636 | 18.exe | 72.14.178.174:80 | amsamex.com | Linode, LLC | US | unknown |
2636 | 18.exe | 13.32.23.204:443 | d39f23jfph0ylk.cloudfront.net | AMAZON-02 | US | whitelisted |
2636 | 18.exe | 67.26.83.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
2636 | 18.exe | 108.138.2.173:80 | o.ss2.us | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
althawry.org |
| unknown |
www.careerdesk.org |
| unknown |
arthur.niria.biz |
| unknown |
amsamex.com |
| unknown |
d39f23jfph0ylk.cloudfront.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
apple-pie.in |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2636 | 18.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value Snkz |
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2636 | 18.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value Snkz |
2636 | 18.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value btst |
12 ETPRO signatures available at the full report