| File name: | 867bd2b81cb0b894b7135bc9e3c479ce4384aa384120dd3e86b5eb0e29e770a5 |
| Full analysis: | https://app.any.run/tasks/9afaf084-dfc2-450a-9866-1f55a188bd42 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 19, 2025, 13:50:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
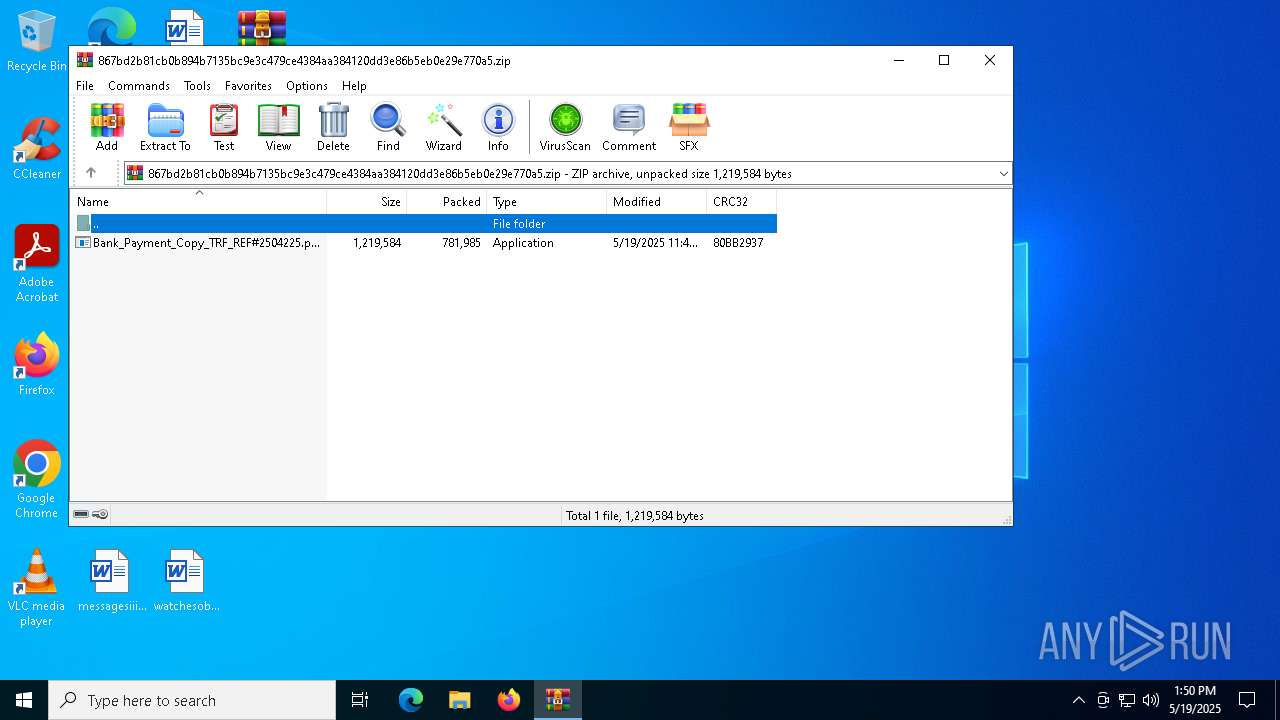
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 518B0A72F8460F216464C65009A8F5FD |
| SHA1: | E6D350CE452FF38BAA870193877EBB916189676A |
| SHA256: | 867BD2B81CB0B894B7135BC9E3C479CE4384AA384120DD3E86B5EB0E29E770A5 |
| SSDEEP: | 24576:KmQa/t2Xs+QpEjokg40dURYXoN2wxD5v6XHBmv23nZ0va9KKSbz1VSVOI/t+N3J8:KmQa/t2Xs+Qpwokg40dAYXoN2wxD5v6j |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7576)
Create files in the Startup directory
- silvexes.exe (PID: 7744)
Changes the autorun value in the registry
- RegSvcs.exe (PID: 8016)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 8016)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 8016)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 8016)
SUSPICIOUS
Executable content was dropped or overwritten
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
- RegSvcs.exe (PID: 8016)
Starts itself from another location
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7808)
Application launched itself
- silvexes.exe (PID: 7864)
Connects to FTP
- RegSvcs.exe (PID: 8016)
Checks for external IP
- RegSvcs.exe (PID: 8016)
Potential Corporate Privacy Violation
- RegSvcs.exe (PID: 8016)
Process drops legitimate windows executable
- RegSvcs.exe (PID: 8016)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7576)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7576)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7576)
INFO
Reads mouse settings
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
- silvexes.exe (PID: 7744)
- silvexes.exe (PID: 7864)
- silvexes.exe (PID: 7976)
Creates files or folders in the user directory
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
- silvexes.exe (PID: 7744)
- RegSvcs.exe (PID: 8016)
Checks supported languages
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
- silvexes.exe (PID: 7744)
- RegSvcs.exe (PID: 7768)
- silvexes.exe (PID: 7864)
- RegSvcs.exe (PID: 8016)
- silvexes.exe (PID: 7976)
- sgxIb.exe (PID: 8128)
- MpCmdRun.exe (PID: 5720)
The sample compiled with english language support
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
- RegSvcs.exe (PID: 8016)
- WinRAR.exe (PID: 7576)
Create files in a temporary directory
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
- silvexes.exe (PID: 7744)
- silvexes.exe (PID: 7864)
- silvexes.exe (PID: 7976)
- MpCmdRun.exe (PID: 5720)
Reads the machine GUID from the registry
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
- RegSvcs.exe (PID: 8016)
- RegSvcs.exe (PID: 7768)
Manual execution by a user
- Bank_Payment_Copy_TRF_REF#2504225.pdf.exe (PID: 7720)
- wscript.exe (PID: 7808)
- sgxIb.exe (PID: 8128)
Reads the computer name
- RegSvcs.exe (PID: 7768)
- RegSvcs.exe (PID: 8016)
- sgxIb.exe (PID: 8128)
- MpCmdRun.exe (PID: 5720)
Auto-launch of the file from Startup directory
- silvexes.exe (PID: 7744)
Disables trace logs
- RegSvcs.exe (PID: 8016)
Auto-launch of the file from Registry key
- RegSvcs.exe (PID: 8016)
ULTRAVNC has been detected
- RegSvcs.exe (PID: 8016)
.NET Reactor protector has been detected
- RegSvcs.exe (PID: 8016)
Checks proxy server information
- RegSvcs.exe (PID: 8016)
- slui.exe (PID: 1164)
Reads the software policy settings
- RegSvcs.exe (PID: 8016)
- slui.exe (PID: 1164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:19 04:46:58 |
| ZipCRC: | 0x80bb2937 |
| ZipCompressedSize: | 781985 |
| ZipUncompressedSize: | 1219584 |
| ZipFileName: | Bank_Payment_Copy_TRF_REF#2504225.pdf.exe |
Total processes
139
Monitored processes
15
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4696 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5204 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7576.810\Rar$Scan88490.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7576.810" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7576 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\867bd2b81cb0b894b7135bc9e3c479ce4384aa384120dd3e86b5eb0e29e770a5.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7720 | "C:\Users\admin\Desktop\Bank_Payment_Copy_TRF_REF#2504225.pdf.exe" | C:\Users\admin\Desktop\Bank_Payment_Copy_TRF_REF#2504225.pdf.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7744 | "C:\Users\admin\Desktop\Bank_Payment_Copy_TRF_REF#2504225.pdf.exe" | C:\Users\admin\AppData\Local\holloing\silvexes.exe | Bank_Payment_Copy_TRF_REF#2504225.pdf.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7768 | "C:\Users\admin\Desktop\Bank_Payment_Copy_TRF_REF#2504225.pdf.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | silvexes.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 7808 | wscript "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\silvexes.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7864 | "C:\Users\admin\AppData\Local\holloing\silvexes.exe" | C:\Users\admin\AppData\Local\holloing\silvexes.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
9 624
Read events
9 598
Write events
26
Delete events
0
Modification events
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\867bd2b81cb0b894b7135bc9e3c479ce4384aa384120dd3e86b5eb0e29e770a5.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (8016) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
3
Suspicious files
6
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7720 | Bank_Payment_Copy_TRF_REF#2504225.pdf.exe | C:\Users\admin\AppData\Local\Temp\autCCE7.tmp | binary | |
MD5:C4ACFBBA4A31D84C7BFEAAB85D195459 | SHA256:478BBC4CADDC859923450519249098BFF8AAF34AA62F0560A56EA850669132DE | |||
| 7720 | Bank_Payment_Copy_TRF_REF#2504225.pdf.exe | C:\Users\admin\AppData\Local\holloing\silvexes.exe | executable | |
MD5:60F377FAAFD5127C78469ABD8D0D3B13 | SHA256:01A6C929D3FC849F7A5D11B3C7FF3AAF3430026F3F7004D046EACE200D18DA95 | |||
| 7720 | Bank_Payment_Copy_TRF_REF#2504225.pdf.exe | C:\Users\admin\AppData\Local\Temp\semispinalis | binary | |
MD5:C4ACFBBA4A31D84C7BFEAAB85D195459 | SHA256:478BBC4CADDC859923450519249098BFF8AAF34AA62F0560A56EA850669132DE | |||
| 7744 | silvexes.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\silvexes.vbs | binary | |
MD5:13A2484AB4ACA2796A9B7C11A77BC1FA | SHA256:07E7088FAE827EB42E700D7440538564D63114BDFA9F82AA6A19B054D10F7CAE | |||
| 7744 | silvexes.exe | C:\Users\admin\AppData\Local\Temp\autD033.tmp | binary | |
MD5:C4ACFBBA4A31D84C7BFEAAB85D195459 | SHA256:478BBC4CADDC859923450519249098BFF8AAF34AA62F0560A56EA850669132DE | |||
| 7976 | silvexes.exe | C:\Users\admin\AppData\Local\Temp\autDAC2.tmp | binary | |
MD5:C4ACFBBA4A31D84C7BFEAAB85D195459 | SHA256:478BBC4CADDC859923450519249098BFF8AAF34AA62F0560A56EA850669132DE | |||
| 5720 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:15584D7015F93B49898BBCBD65CA62E0 | SHA256:D7646491BD95729E49EBC329CF86B3BD1979F65FF18895BC00D5EE34F2E0F794 | |||
| 7576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7576.810\867bd2b81cb0b894b7135bc9e3c479ce4384aa384120dd3e86b5eb0e29e770a5.zip\Bank_Payment_Copy_TRF_REF#2504225.pdf.exe | executable | |
MD5:60F377FAAFD5127C78469ABD8D0D3B13 | SHA256:01A6C929D3FC849F7A5D11B3C7FF3AAF3430026F3F7004D046EACE200D18DA95 | |||
| 7576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7576.810\Rar$Scan88490.bat | text | |
MD5:26CA33608155CF356BF82049C0D4650F | SHA256:7D35377C835D60C1F2846BC4D42CBC0A0883E5F1A47761699EA5BD9D92358AC0 | |||
| 8016 | RegSvcs.exe | C:\Users\admin\AppData\Roaming\sgxIb\sgxIb.exe | executable | |
MD5:6279D136310C22894F605938B4CB93D8 | SHA256:FB7D514B3322810463655473D2D7C704D3405C1C9DD81F0D4D423518EF416987 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
53
DNS requests
19
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.216.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.216.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8016 | RegSvcs.exe | 104.26.12.205:443 | api.ipify.org | CLOUDFLARENET | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
api.ipify.org |
| shared |
ftp.haliza.com.my |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8016 | RegSvcs.exe | Potential Corporate Privacy Violation | ET INFO Possible IP Check api.ipify.org |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
8016 | RegSvcs.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |