| File name: | 850fa36792359354c8b5cf86ebb2d6923aa64dece7fc5d555d90d156eaa0409e |
| Full analysis: | https://app.any.run/tasks/a85f4bbd-e304-4edd-a125-d5e536a9aab6 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | January 11, 2025, 00:03:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | A7649256FCE8B15959EDD1004DF7781B |
| SHA1: | 314294D940B110265283531E9E62B3DEA6FB4506 |
| SHA256: | 850FA36792359354C8B5CF86EBB2D6923AA64DECE7FC5D555D90D156EAA0409E |
| SSDEEP: | 49152:bPPkzemqoSut3Jh4+QQ/btosJwIA4hHmZlKH2Tw/Pq83zw0bCjvk9G661QGtCO/k:7P/mp7t3T4+B/btosJwIA4hHmZlKH2Tp |
MALICIOUS
STORMKITTY has been detected (YARA)
- RegSvcs.exe (PID: 6432)
ASYNCRAT has been detected (MUTEX)
- RegSvcs.exe (PID: 6432)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 6432)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 6432)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 7096)
- cmd.exe (PID: 6208)
Starts CMD.EXE for commands execution
- RegSvcs.exe (PID: 6432)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7096)
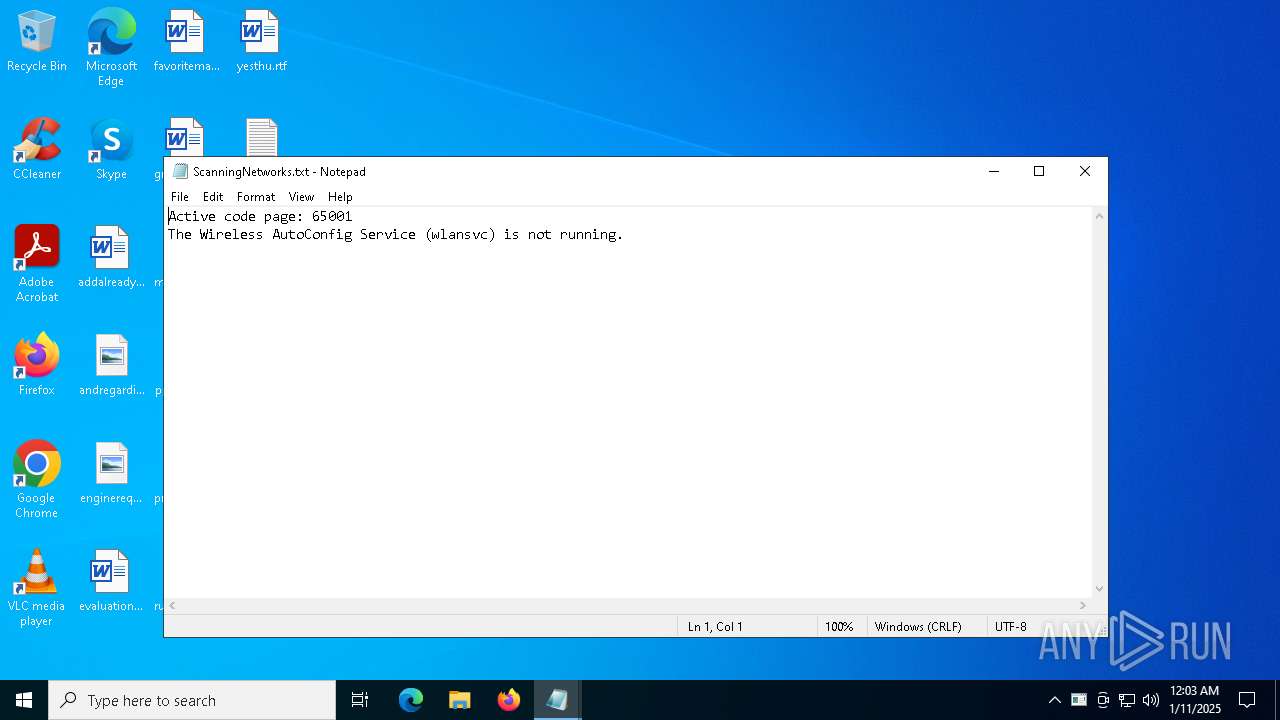
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 7096)
- cmd.exe (PID: 6208)
Write to the desktop.ini file (may be used to cloak folders)
- RegSvcs.exe (PID: 6432)
Checks for external IP
- svchost.exe (PID: 2192)
- RegSvcs.exe (PID: 6432)
Potential Corporate Privacy Violation
- RegSvcs.exe (PID: 6432)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RegSvcs.exe (PID: 6432)
The process connected to a server suspected of theft
- RegSvcs.exe (PID: 6432)
Possible usage of Discord/Telegram API has been detected (YARA)
- RegSvcs.exe (PID: 6432)
INFO
The sample compiled with english language support
- 850fa36792359354c8b5cf86ebb2d6923aa64dece7fc5d555d90d156eaa0409e.exe (PID: 6272)
Checks supported languages
- 850fa36792359354c8b5cf86ebb2d6923aa64dece7fc5d555d90d156eaa0409e.exe (PID: 6272)
- chcp.com (PID: 7144)
- RegSvcs.exe (PID: 6432)
- chcp.com (PID: 4056)
Changes the display of characters in the console
- cmd.exe (PID: 6208)
- cmd.exe (PID: 7096)
Reads mouse settings
- 850fa36792359354c8b5cf86ebb2d6923aa64dece7fc5d555d90d156eaa0409e.exe (PID: 6272)
Create files in a temporary directory
- 850fa36792359354c8b5cf86ebb2d6923aa64dece7fc5d555d90d156eaa0409e.exe (PID: 6272)
- RegSvcs.exe (PID: 6432)
Reads the machine GUID from the registry
- RegSvcs.exe (PID: 6432)
Reads CPU info
- RegSvcs.exe (PID: 6432)
Disables trace logs
- RegSvcs.exe (PID: 6432)
Checks proxy server information
- RegSvcs.exe (PID: 6432)
Reads the software policy settings
- RegSvcs.exe (PID: 6432)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3876)
- notepad.exe (PID: 6848)
- notepad.exe (PID: 4548)
- notepad.exe (PID: 1944)
- notepad.exe (PID: 7128)
Manual execution by a user
- notepad.exe (PID: 4548)
- notepad.exe (PID: 1944)
- notepad.exe (PID: 6848)
- WINWORD.EXE (PID: 6684)
- notepad.exe (PID: 7128)
- notepad.exe (PID: 3876)
- WINWORD.EXE (PID: 7080)
- notepad.exe (PID: 3524)
Drops encrypted VBS script (Microsoft Script Encoder)
- WINWORD.EXE (PID: 6684)
- RegSvcs.exe (PID: 6432)
Sends debugging messages
- WINWORD.EXE (PID: 6684)
The process uses the downloaded file
- WINWORD.EXE (PID: 6684)
Creates files or folders in the user directory
- RegSvcs.exe (PID: 6432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:12:18 10:47:24+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 633856 |
| InitializedDataSize: | 481792 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20577 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Total processes
152
Monitored processes
21
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1556 | findstr All | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
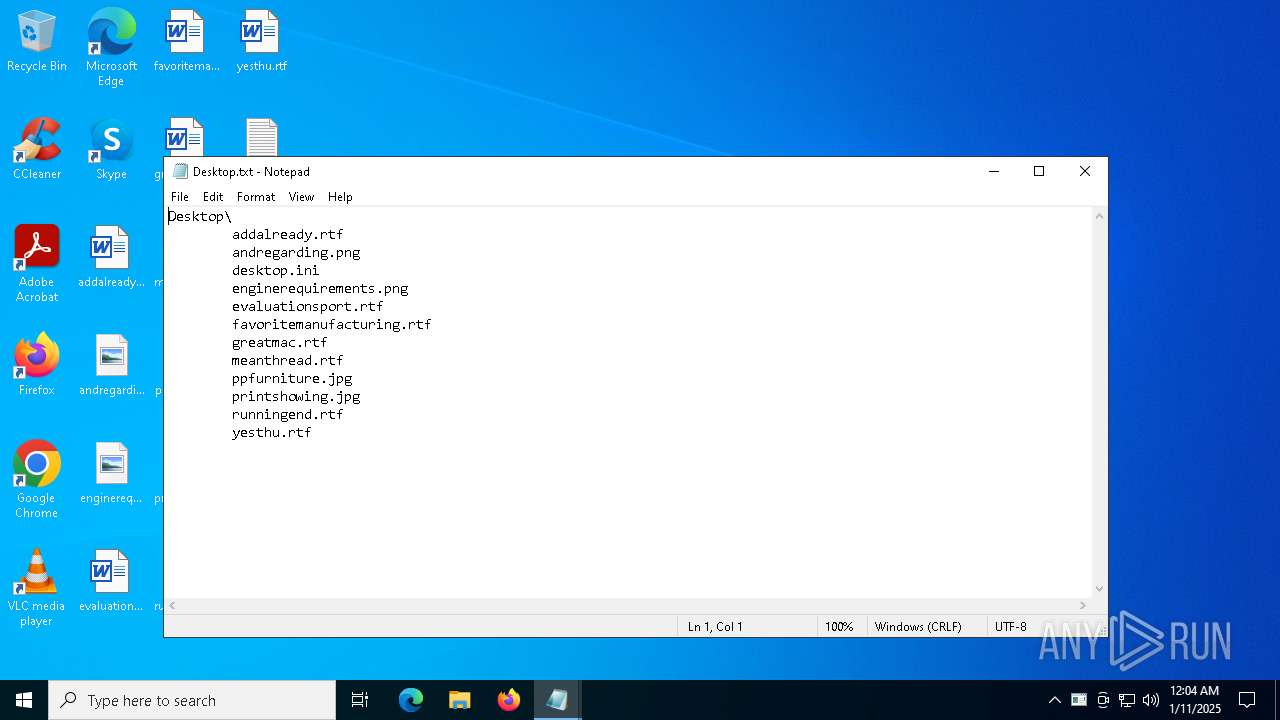
| 1944 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Desktop.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Temp.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | netsh wlan show networks mode=bssid | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3876 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Startup.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4056 | chcp 65001 | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4548 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\ScanningNetworks.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6204 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "CD710F86-F795-4C52-A17D-35A6CFB82ADC" "29F53E92-1FAF-431D-B846-4C2B5E569A0B" "6684" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
20 914
Read events
20 453
Write events
432
Delete events
29
Modification events
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6432) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\RegSvcs_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
17
Suspicious files
150
Text files
72
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6432 | RegSvcs.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\desktop.ini | text | |
MD5:3A37312509712D4E12D27240137FF377 | SHA256:B029393EA7B7CF644FB1C9F984F57C1980077562EE2E15D0FFD049C4C48098D3 | |||
| 6272 | 850fa36792359354c8b5cf86ebb2d6923aa64dece7fc5d555d90d156eaa0409e.exe | C:\Users\admin\AppData\Local\Temp\aut55B5.tmp | binary | |
MD5:B02C4BBEF41D57DCF18E74EC3118F908 | SHA256:13C19DC9064FD845F3BAE9E6628607567F5DCCB136A87472F696B5A70FD230F2 | |||
| 6272 | 850fa36792359354c8b5cf86ebb2d6923aa64dece7fc5d555d90d156eaa0409e.exe | C:\Users\admin\AppData\Local\Temp\corynteria | binary | |
MD5:E7F040AECE4EAFBD290B73E61EA01AD2 | SHA256:8449A5E04C8082ED45E6EDED4374A13128FA65029950C6C1971A75F8042537B1 | |||
| 6432 | RegSvcs.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\desktop.ini | text | |
MD5:9E36CC3537EE9EE1E3B10FA4E761045B | SHA256:4B9D687AC625690FD026ED4B236DAD1CAC90EF69E7AD256CC42766A065B50026 | |||
| 6432 | RegSvcs.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\comethese.png | image | |
MD5:9AF670DBC69313C6F80563A733E04931 | SHA256:4548D0355870F58541A3ED29138CEC02B2A90BB9BEA660C3B8968E51FE3255CB | |||
| 6432 | RegSvcs.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\thanfall.png | image | |
MD5:B41CCDDC76072BB8C2665D0E7207C31C | SHA256:6EA38CA4F2A195F68C5A2E3FAAEC5E44085F184B8AD96B9E1F09DD7B2ED92B48 | |||
| 6432 | RegSvcs.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\specificled.png | image | |
MD5:D50D1B0B6BCF889B3D7D130707C5A37A | SHA256:12C05392A7EAA8F4DF01D54C1DD6C1380E6AE43EFAF55BE2A6CE9D2876ABE97F | |||
| 6432 | RegSvcs.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\professionaltechnologies.png | image | |
MD5:D03BAFC0A806A1735387C401597D5B07 | SHA256:76C04B4A083C44A3A4C8E69F83679D8BDC63A7DBB19A6EBFFBC582F4C502C9CD | |||
| 6432 | RegSvcs.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\Camera Roll\desktop.ini | text | |
MD5:D48FCE44E0F298E5DB52FD5894502727 | SHA256:231A08CABA1F9BA9F14BD3E46834288F3C351079FCEDDA15E391B724AC0C7EA8 | |||
| 6432 | RegSvcs.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\enginerequirements.png | image | |
MD5:FC31012F9F3AF486BBC79265D712B88A | SHA256:CF0769045D60E60FB1FD59C0F91375F58276AB04382B833F9D8406734575A534 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
82
DNS requests
37
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6356 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6432 | RegSvcs.exe | GET | 200 | 104.16.185.241:80 | http://icanhazip.com/ | unknown | — | — | shared |
4164 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4164 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6684 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6684 | WINWORD.EXE | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 2.23.242.9:443 | go.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
icanhazip.com |
| shared |
api.mylnikov.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6432 | RegSvcs.exe | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
6432 | RegSvcs.exe | Potential Corporate Privacy Violation | ET POLICY Observed Wifi Geolocation Domain (api .mylnikov .org in TLS SNI) |
2192 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6432 | RegSvcs.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
6432 | RegSvcs.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6432 | RegSvcs.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
6432 | RegSvcs.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6432 | RegSvcs.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Telegram |
6432 | RegSvcs.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|