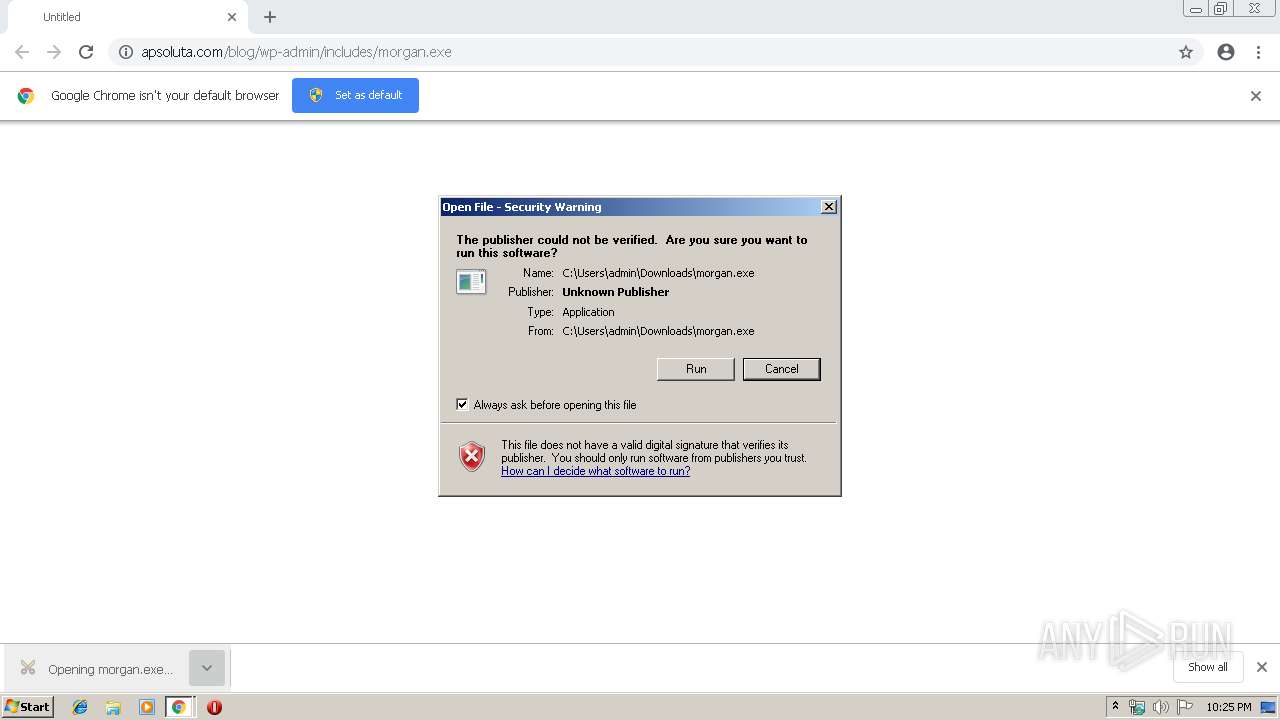
| URL: | http://apsoluta.com/blog/wp-admin/includes/morgan.exe |
| Full analysis: | https://app.any.run/tasks/de987b3b-7b7b-4384-a051-86dbee0e5000 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | March 21, 2019, 22:25:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 57759BF47849CC2A5E73C5506794566E |
| SHA1: | A7040C835E6071706CD925B1CD24686A53250098 |
| SHA256: | 84C22552C6592295E995088420E5341316687F1504B412BD5C9580C6BBC6DF24 |
| SSDEEP: | 3:N1KftQiLKKLJ+zeBAn:CKohJ+zeAn |
MALICIOUS
Application was dropped or rewritten from another process
- morgan.exe (PID: 2556)
- morgan.exe (PID: 1564)
- bin.exe (PID: 2256)
Downloads executable files from the Internet
- chrome.exe (PID: 3552)
Changes the autorun value in the registry
- morgan.exe (PID: 1564)
Detected AgentTesla Keylogger
- morgan.exe (PID: 1564)
Actions looks like stealing of personal data
- morgan.exe (PID: 1564)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 1016)
- chrome.exe (PID: 3552)
- morgan.exe (PID: 1564)
Application launched itself
- morgan.exe (PID: 2556)
Creates files in the user directory
- morgan.exe (PID: 1564)
Cleans NTFS data-stream (Zone Identifier)
- morgan.exe (PID: 1564)
Loads DLL from Mozilla Firefox
- morgan.exe (PID: 1564)
Connects to SMTP port
- morgan.exe (PID: 1564)
INFO
Application launched itself
- chrome.exe (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
13
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" http://apsoluta.com/blog/wp-admin/includes/morgan.exe | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1624 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=972,1896986431677722932,8391010336390516234,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=197129593697026374 --mojo-platform-channel-handle=940 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=972,1896986431677722932,8391010336390516234,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=16371416827029298170 --mojo-platform-channel-handle=3556 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1564 | "C:\Users\admin\Downloads\morgan.exe" | C:\Users\admin\Downloads\morgan.exe | morgan.exe | ||||||||||||
User: admin Company: Soltec Integrity Level: MEDIUM Description: ML Accessories (Knightsbridge) Exit code: 0 Version: 7.10.8.10 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,1896986431677722932,8391010336390516234,131072 --enable-features=PasswordImport --service-pipe-token=3147202355033370032 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3147202355033370032 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\bin.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\bin.exe | — | morgan.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,1896986431677722932,8391010336390516234,131072 --enable-features=PasswordImport --service-pipe-token=13023954533611201428 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13023954533611201428 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2088 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2556 | "C:\Users\admin\Downloads\morgan.exe" | C:\Users\admin\Downloads\morgan.exe | — | chrome.exe | |||||||||||
User: admin Company: Soltec Integrity Level: MEDIUM Description: ML Accessories (Knightsbridge) Exit code: 0 Version: 7.10.8.10 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=73.0.3683.75 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6f720f18,0x6f720f28,0x6f720f34 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
1 294
Read events
1 230
Write events
61
Delete events
3
Modification events
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1268) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1016-13197680746610250 |
Value: 259 | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
7
Suspicious files
9
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\61375455-eb5e-4b9e-997b-8f328d0c32f7.tmp | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 1016 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
8
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3552 | chrome.exe | GET | 200 | 69.89.31.185:80 | http://apsoluta.com/blog/wp-admin/includes/morgan.exe | US | executable | 1.19 Mb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1564 | morgan.exe | 208.91.199.224:587 | smtp.sanrex-sg.com | PDR | US | shared |
3552 | chrome.exe | 216.58.205.238:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3552 | chrome.exe | 172.217.18.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3552 | chrome.exe | 172.217.16.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3552 | chrome.exe | 69.89.31.185:80 | apsoluta.com | Unified Layer | US | suspicious |
3552 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
apsoluta.com |
| malicious |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
safebrowsing.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
smtp.sanrex-sg.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3552 | chrome.exe | A Network Trojan was detected | ET TROJAN EXE Download Request To Wordpress Folder Likely Malicious |
3552 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |