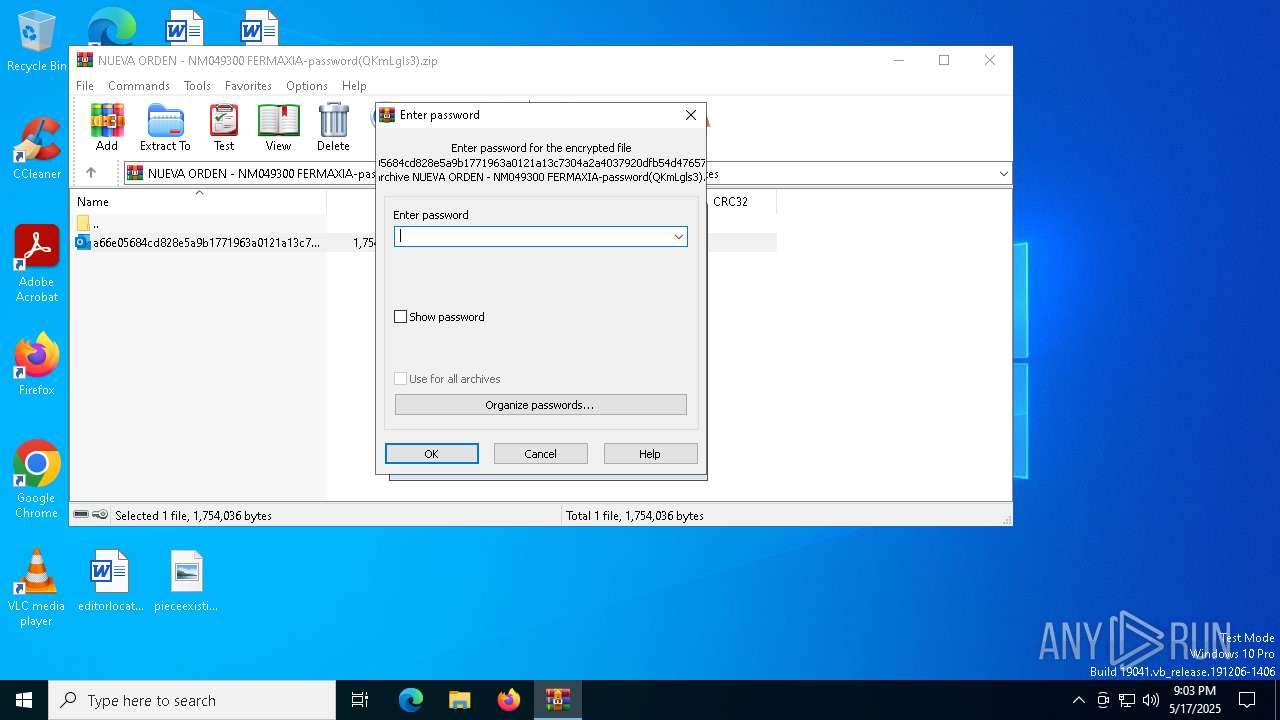
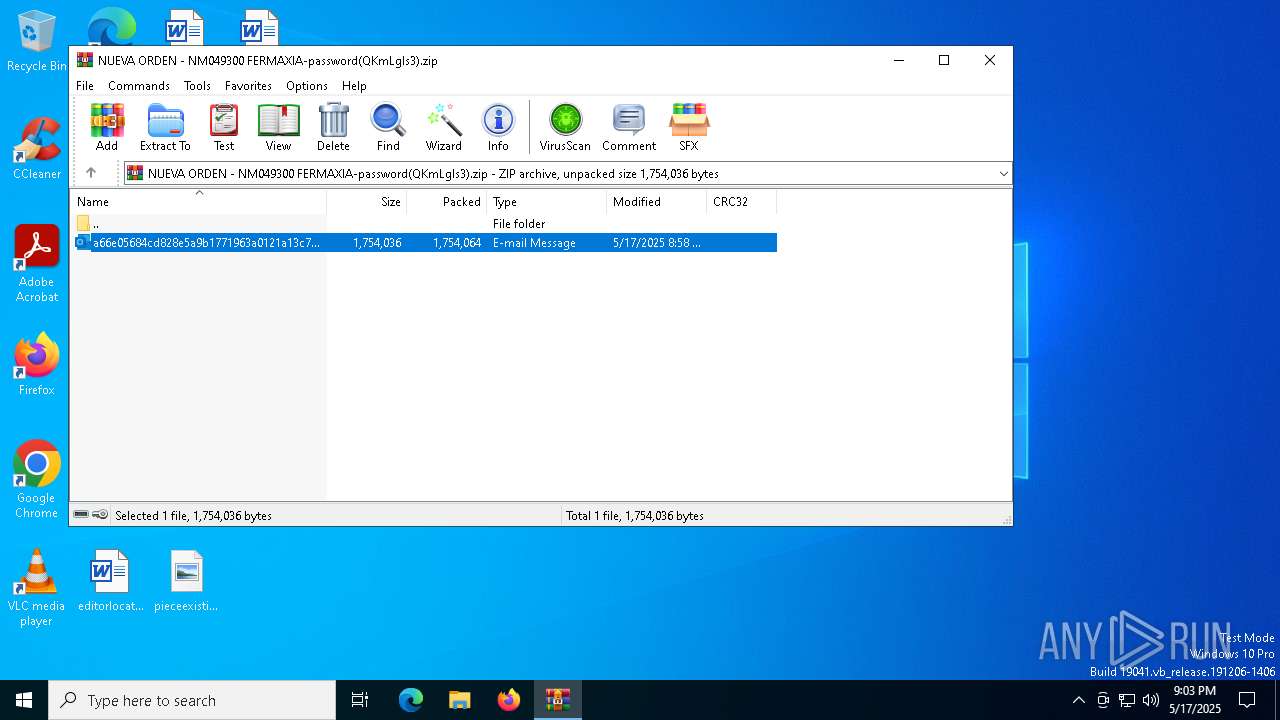
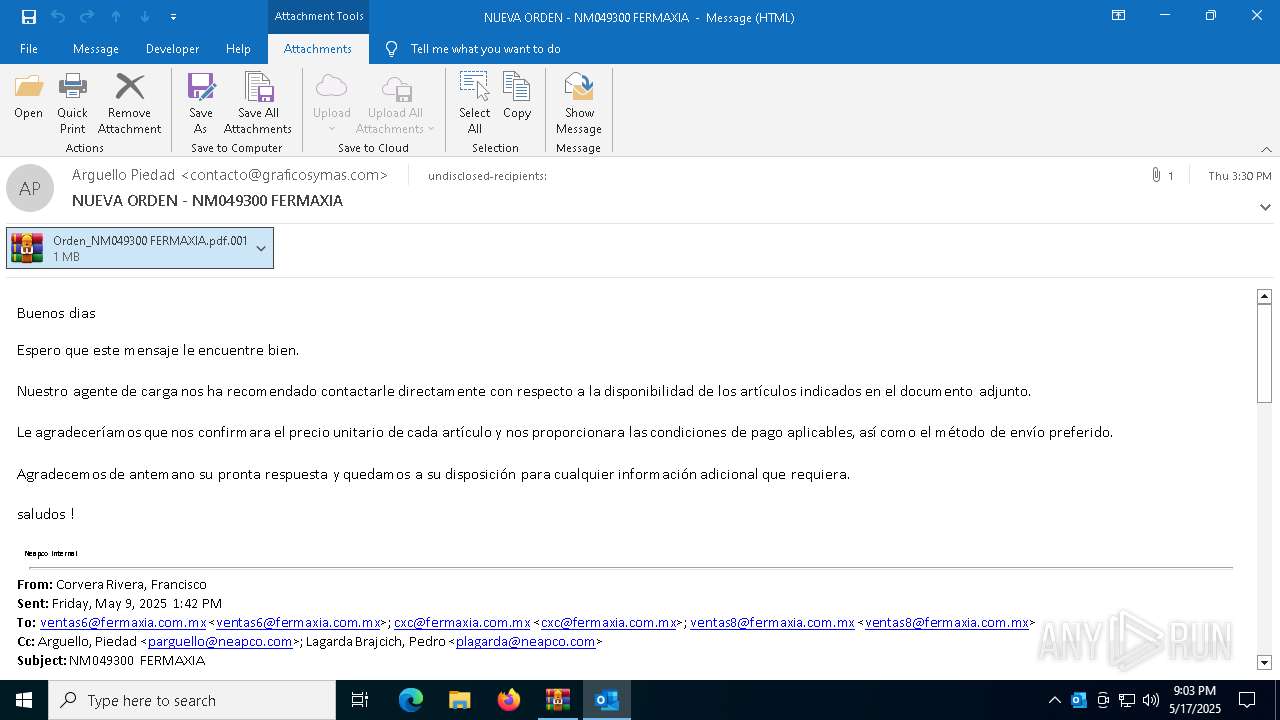
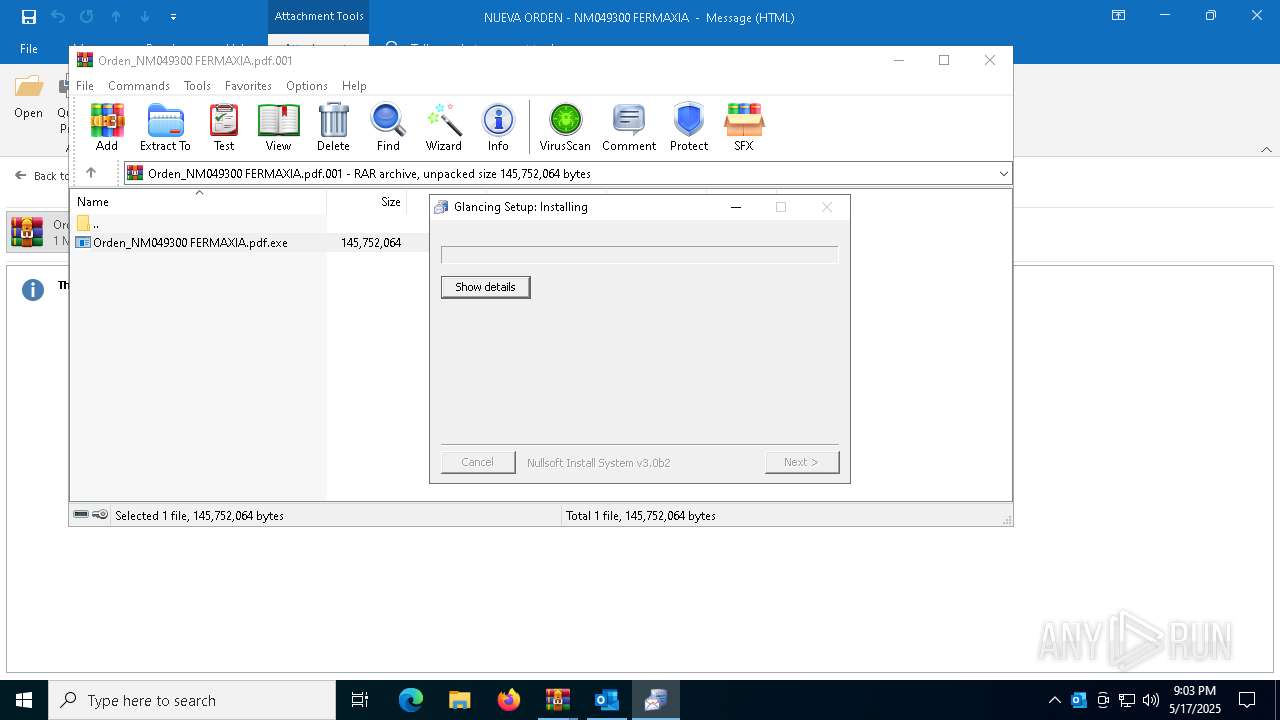
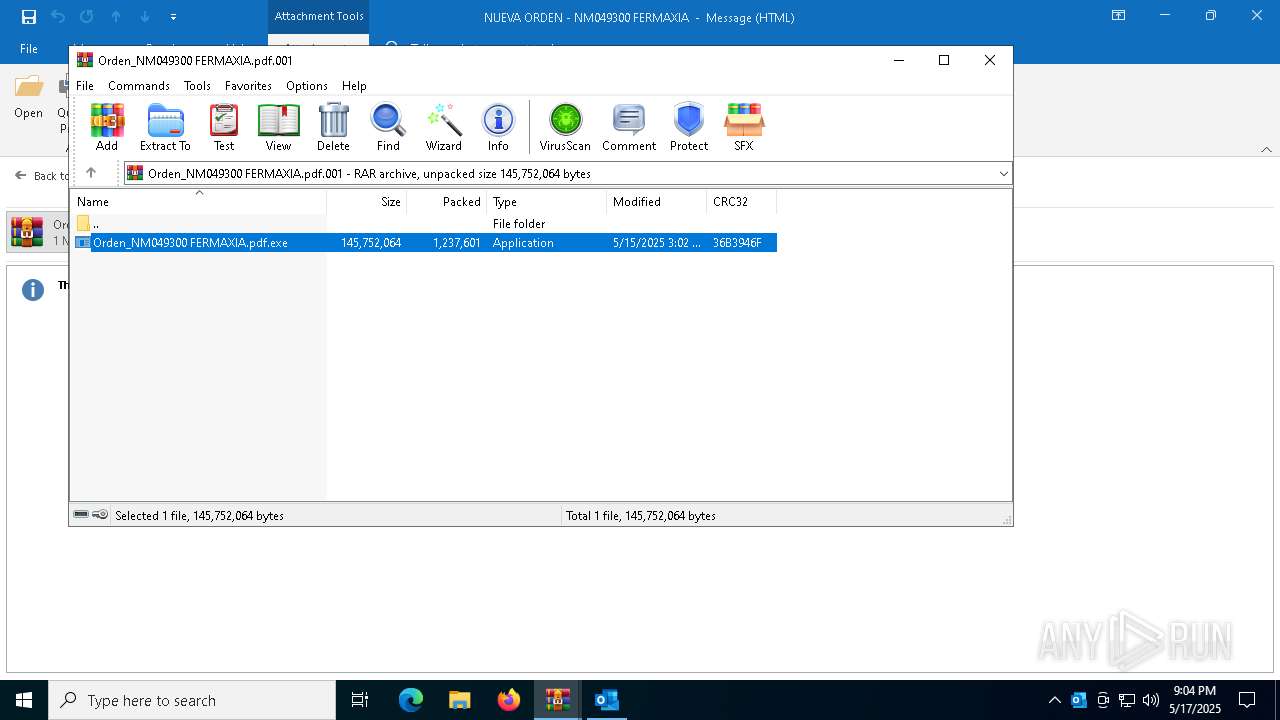
| File name: | NUEVA ORDEN - NM049300 FERMAXIA-password(QKmLgls3).zip |
| Full analysis: | https://app.any.run/tasks/2d543986-6846-409b-bc9d-82498f126a66 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 17, 2025, 21:03:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 45477E866DC304F06C3AE2C406B2BED1 |
| SHA1: | D253C156CE77E1A28ABD5F87A42A06FB486A542B |
| SHA256: | 845C7E0DBF037BC7528DCE1B3FB517DBDD584A3FDEB85E224069B7061F0F4883 |
| SSDEEP: | 98304:bjrTPmpBjzZOlbAYKuWIMSjWUO2CAGa3MvjO2roaiuhLBSjXSAN3b/RiFgEjsiM6:O6qSmEY |
MALICIOUS
Executing a file with an untrusted certificate
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 5072)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
AGENTTESLA has been detected (SURICATA)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Actions looks like stealing of personal data
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Steals credentials from Web Browsers
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7364)
- WinRAR.exe (PID: 5392)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 7364)
The process creates files with name similar to system file names
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 5072)
Executable content was dropped or overwritten
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 5072)
Malware-specific behavior (creating "System.dll" in Temp)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 5072)
Executes application which crashes
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 5072)
There is functionality for taking screenshot (YARA)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
Application launched itself
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
Connects to the server without a host name
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Checks for external IP
- svchost.exe (PID: 2196)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Connects to FTP
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Connects to unusual port
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7364)
Checks supported languages
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 5072)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Create files in a temporary directory
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 5072)
Reads the computer name
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 6156)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 5072)
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Checks proxy server information
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Reads the machine GUID from the registry
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Disables trace logs
- Orden_NM049300 FERMAXIA.pdf.exe (PID: 7676)
Reads the software policy settings
- slui.exe (PID: 7548)
Creates files or folders in the user directory
- WerFault.exe (PID: 7500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:17 20:58:56 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 1754064 |
| ZipUncompressedSize: | 1754036 |
| ZipFileName: | a66e05684cd828e5a9b1771963a0121a13c7304a2a4037920dfb54d476575f9c.eml |
Total processes
143
Monitored processes
12
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1388 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5072 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5392.14650\Orden_NM049300 FERMAXIA.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5392.14650\Orden_NM049300 FERMAXIA.pdf.exe | WinRAR.exe | ||||||||||||
User: admin Company: R.R. Donnelley & Sons Company Integrity Level: MEDIUM Description: ACT Manufacturing Inc. Exit code: 3221225477 Version: 3.0.0.0 Modules
| |||||||||||||||
| 5392 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\35DF3V1S\Orden_NM049300 FERMAXIA.pdf.001" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6156 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5392.13661\Orden_NM049300 FERMAXIA.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5392.13661\Orden_NM049300 FERMAXIA.pdf.exe | WinRAR.exe | ||||||||||||
User: admin Company: R.R. Donnelley & Sons Company Integrity Level: MEDIUM Description: ACT Manufacturing Inc. Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 7012 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "9F09EE2E-B312-4E10-BCE8-22920467A975" "39441797-2E6A-461B-B26B-4DE0BFF62422" "7976" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 7364 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NUEVA ORDEN - NM049300 FERMAXIA-password(QKmLgls3).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7500 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5072 -s 132 | C:\Windows\SysWOW64\WerFault.exe | — | Orden_NM049300 FERMAXIA.pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7516 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7548 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 764
Read events
19 620
Write events
2 004
Delete events
140
Modification events
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NUEVA ORDEN - NM049300 FERMAXIA-password(QKmLgls3).zip | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {5FA29220-36A1-40F9-89C6-F4B384B7642E} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 01000000000000009248B9246FC7DB01 | |||
Executable files
2
Suspicious files
20
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7976 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb7364.10660\a66e05684cd828e5a9b1771963a0121a13c7304a2a4037920dfb54d476575f9c.eml:OECustomProperty | binary | |
MD5:E73E334EC26BCBE52B32894E68513680 | SHA256:90AA4D98ED3930924B435B01AA9938E0190F41983954D96667B647C02F2479D0 | |||
| 7976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:85C1200EBF51EFAD4AC0FDC1B705A921 | SHA256:200F63D0C1099B63CCABBE94F89885DB6EFDC76A4438F5CA85A943FB01FDC6CF | |||
| 5392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5392.13661\Orden_NM049300 FERMAXIA.pdf.exe | — | |
MD5:— | SHA256:— | |||
| 7976 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:80ED9D82948FFBC71240A1DCA8EED06E | SHA256:F6504177CB2C270FFDF993181BD3EB6C3BC02ED69685E00377B51381B4C9B14A | |||
| 7976 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:0E0DC6CD722B151F4AFCCAC1E0B62113 | SHA256:A67D5FEAF3B0E70D0EE074346A6FB1AB2726B6C95FEF514C84B7596CF3C10263 | |||
| 7976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:53758F208018359AE194A908DF871461 | SHA256:0B8864800653A673DB23C892823499618D0E86091DE7F4F99B53AE8DAF57E412 | |||
| 7976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6156 | Orden_NM049300 FERMAXIA.pdf.exe | C:\Users\admin\hundredfold\optativs\Uncontainableness\Waneatta\vikingetid\Sammenhftet.doi | — | |
MD5:— | SHA256:— | |||
| 7976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\6CF1ECB7.dat | image | |
MD5:B9B94095F69913212FAD8C83A833C03D | SHA256:4B628A711BB7D4DAB5F643BF48819E7234D0F2FECF5B5BF96F0577291480F1E3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
34
DNS requests
23
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7976 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1188 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1188 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7976 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | GET | 200 | 75.127.7.164:80 | http://75.127.7.164/phVcVwKV127.bin | unknown | — | — | unknown |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7976 | OUTLOOK.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7976 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7676 | Orden_NM049300 FERMAXIA.pdf.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
7676 | Orden_NM049300 FERMAXIA.pdf.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |