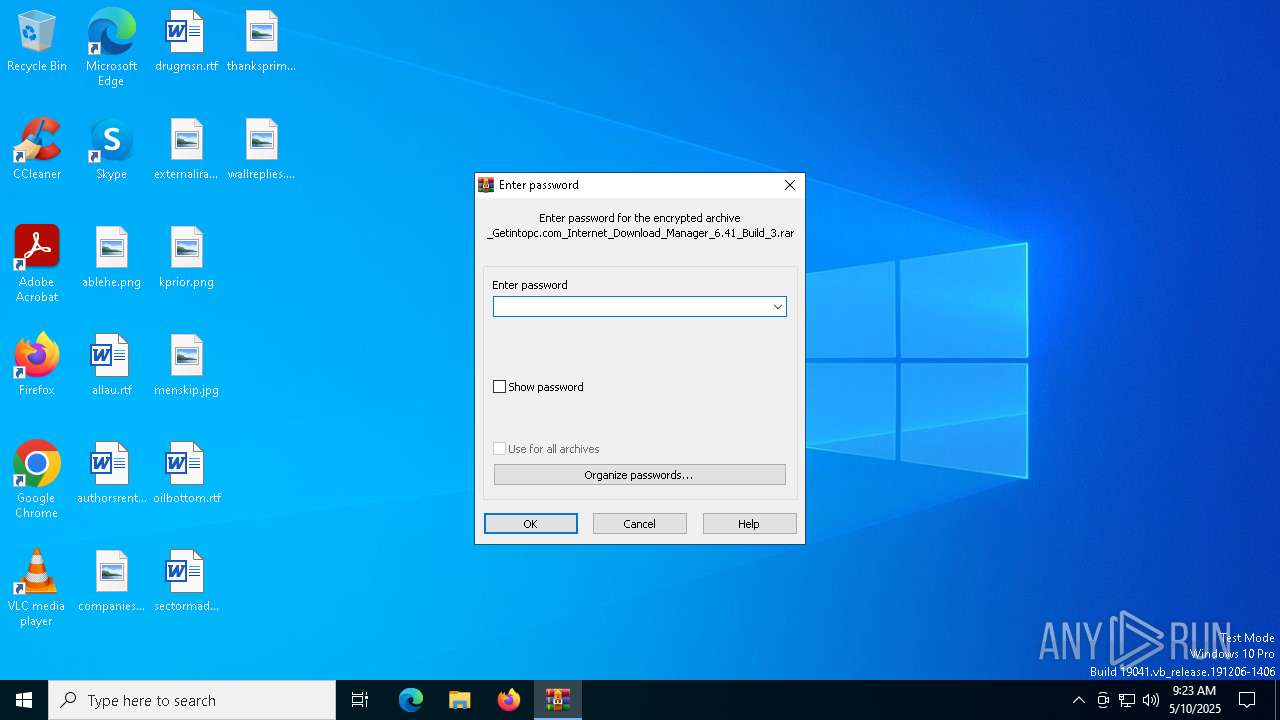
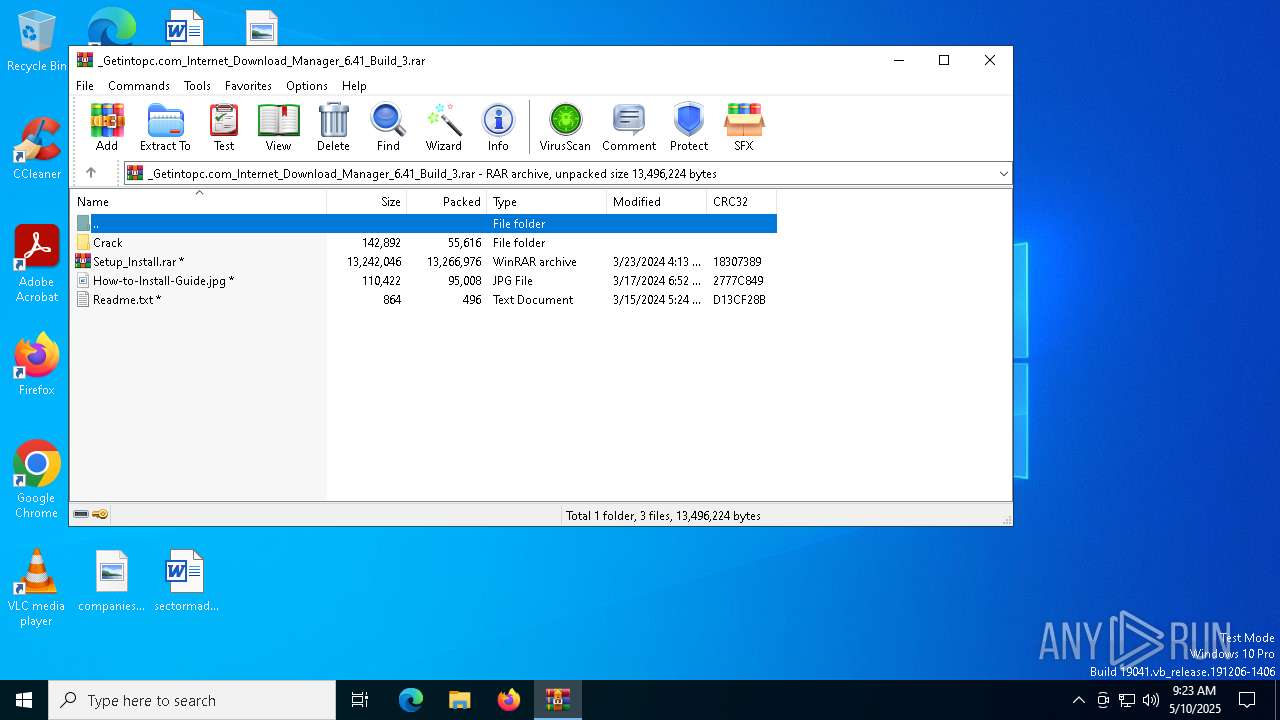
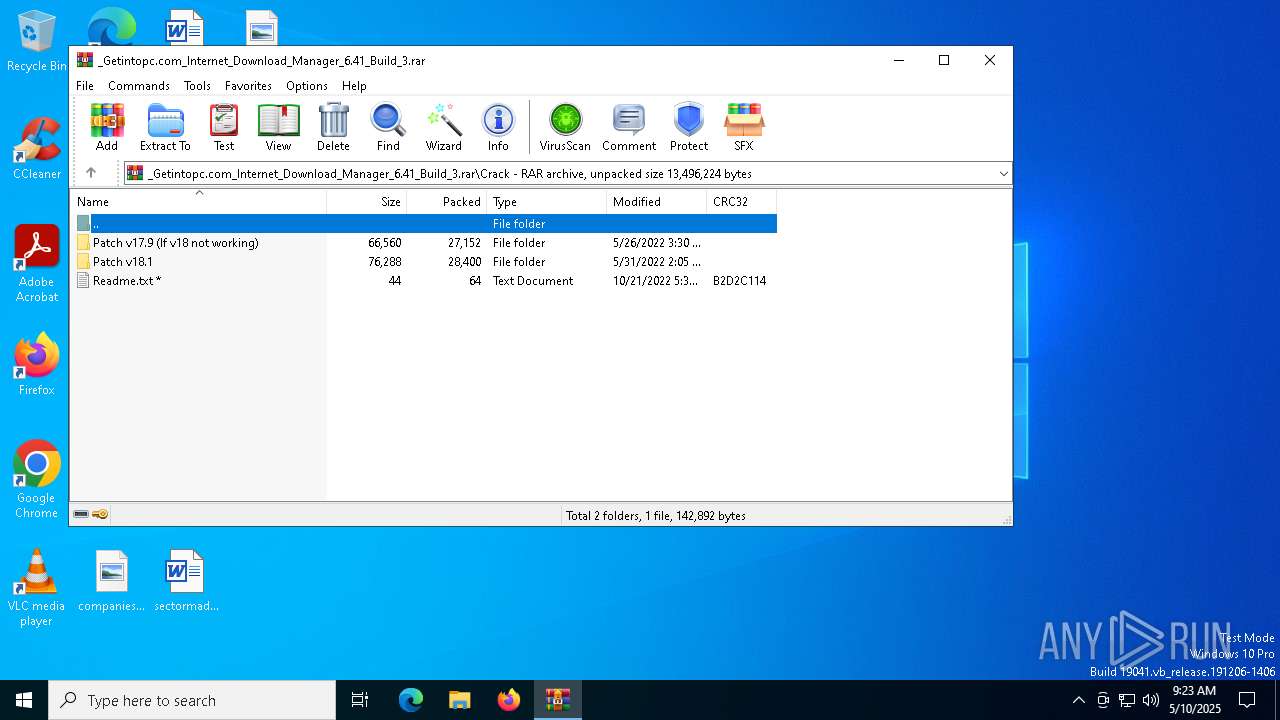
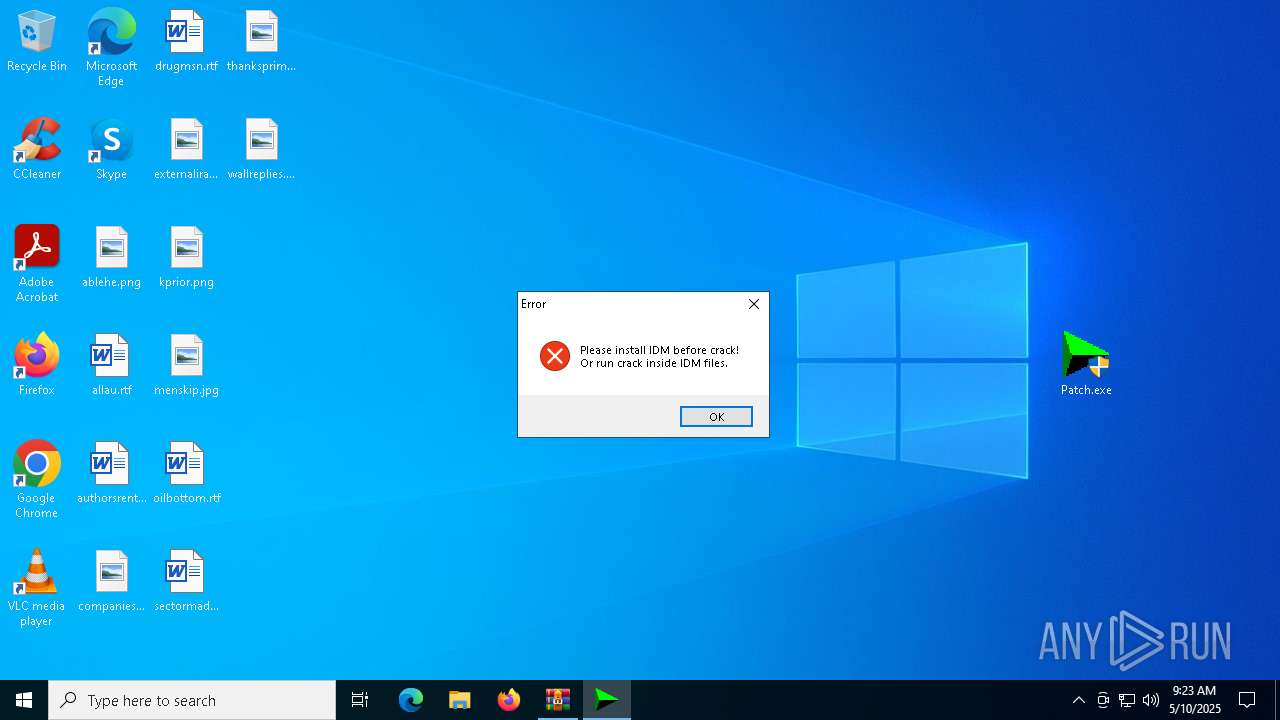
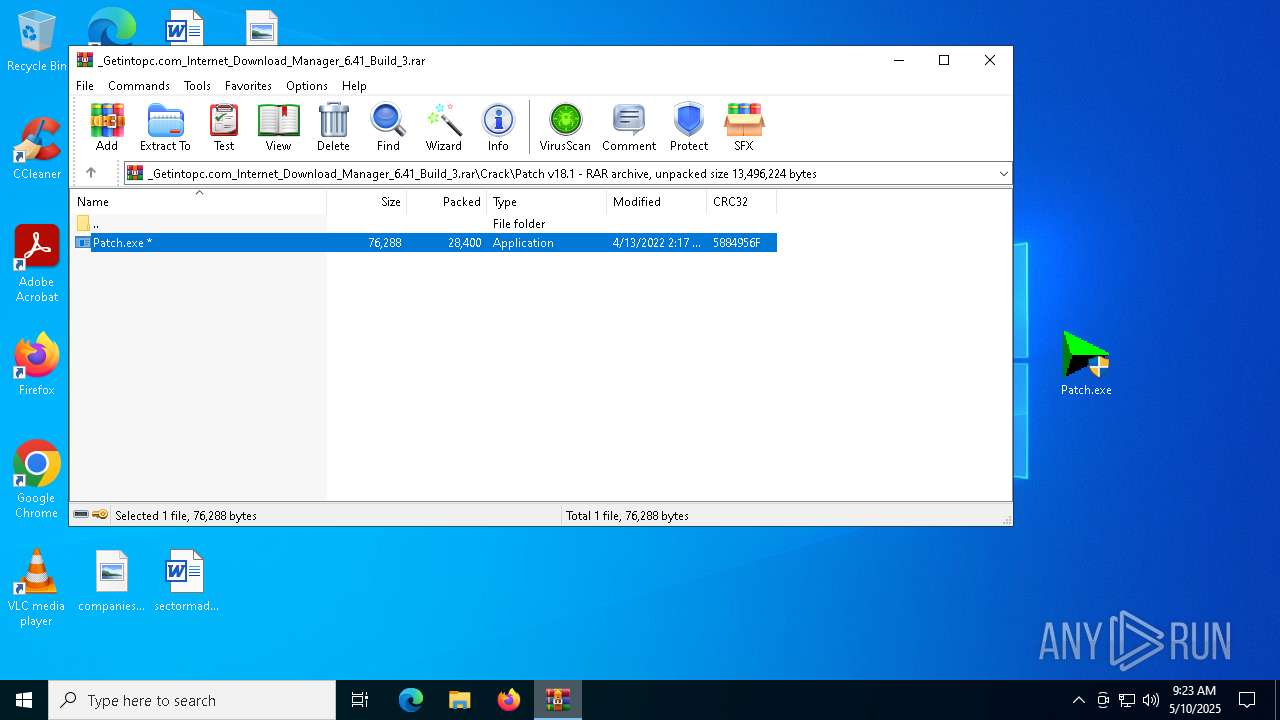
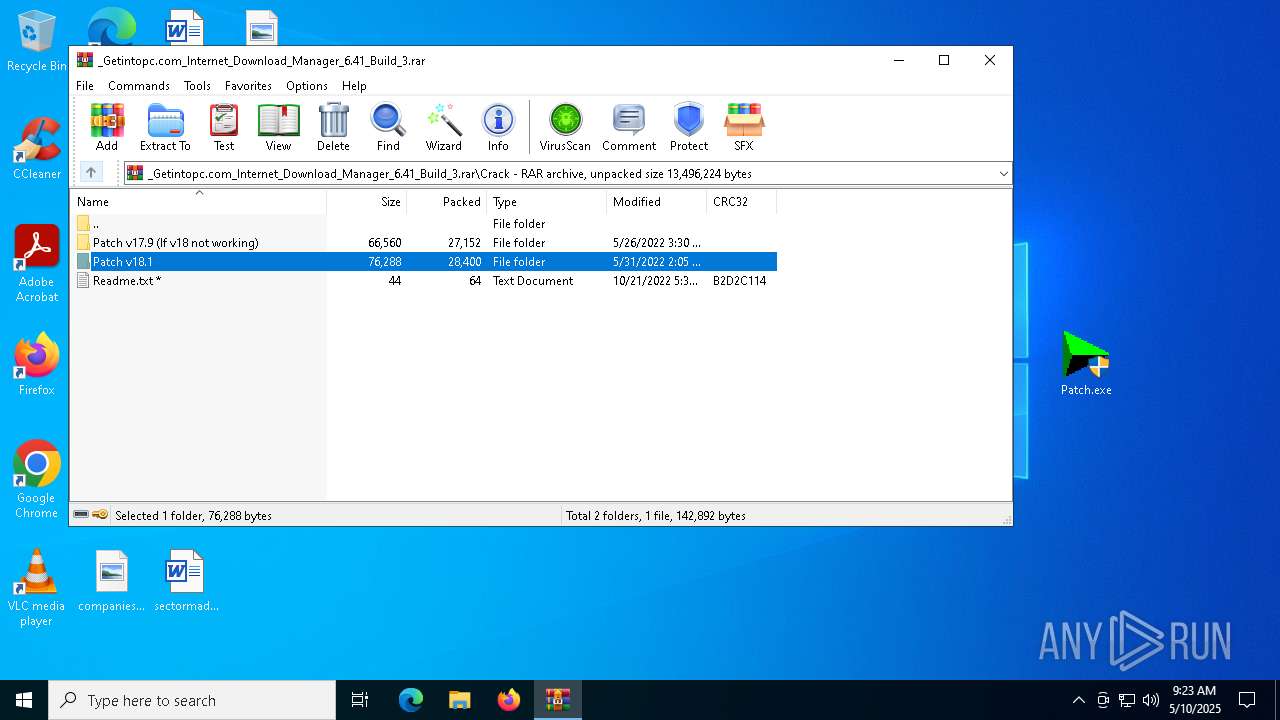
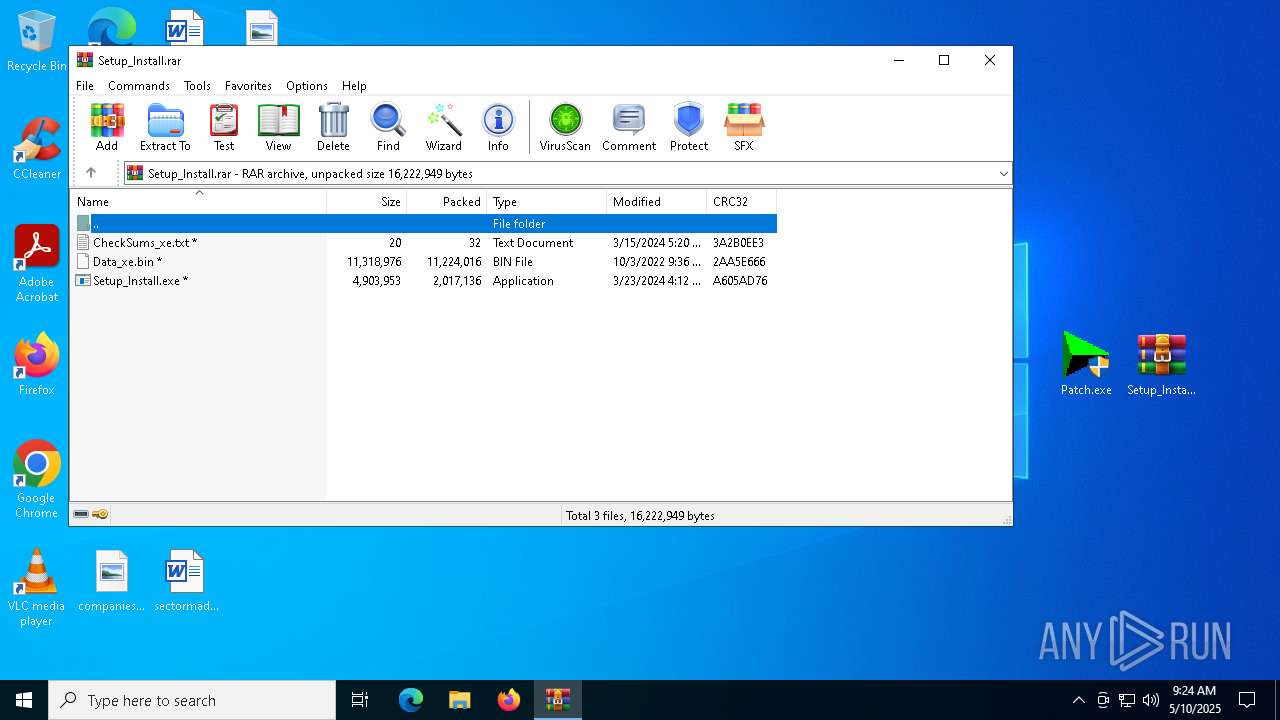
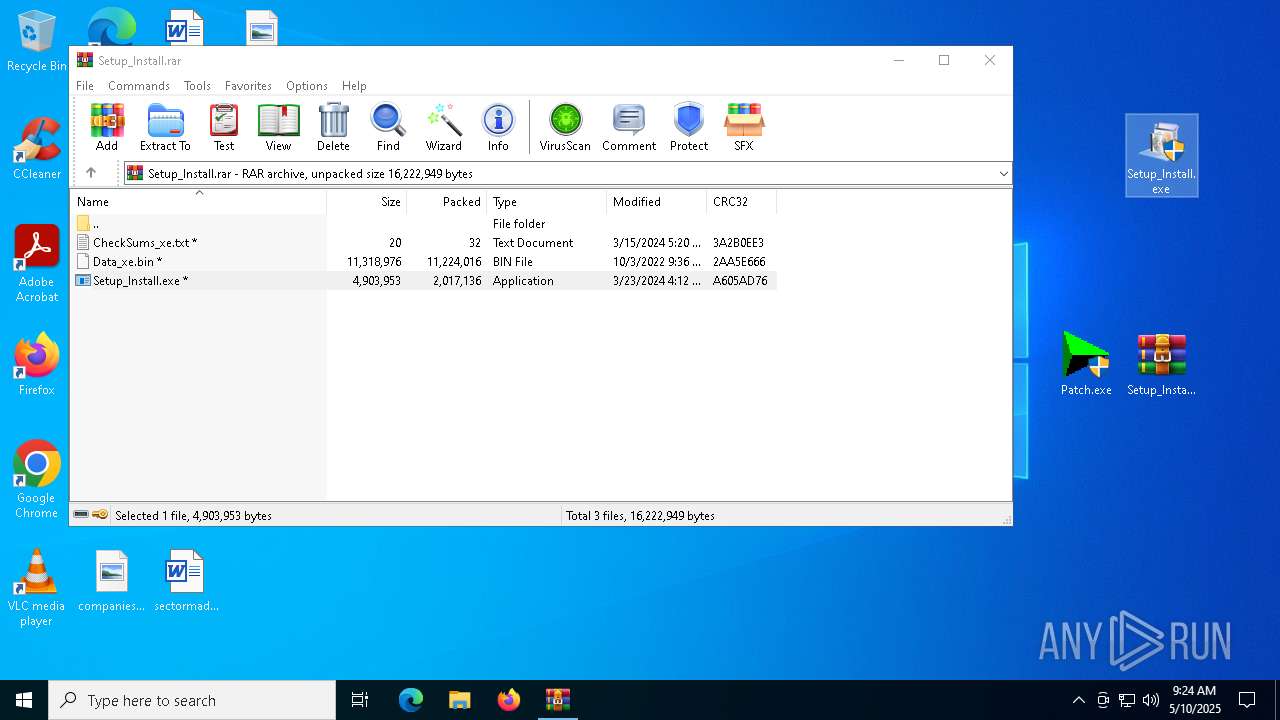
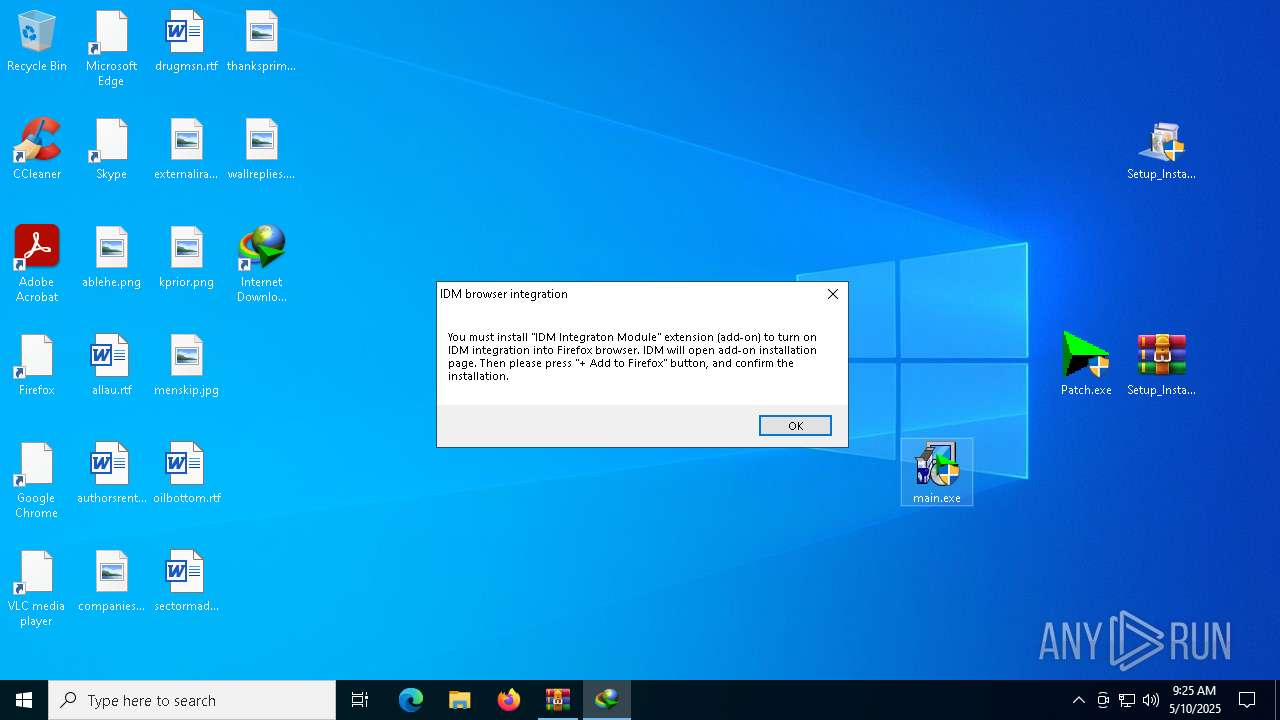
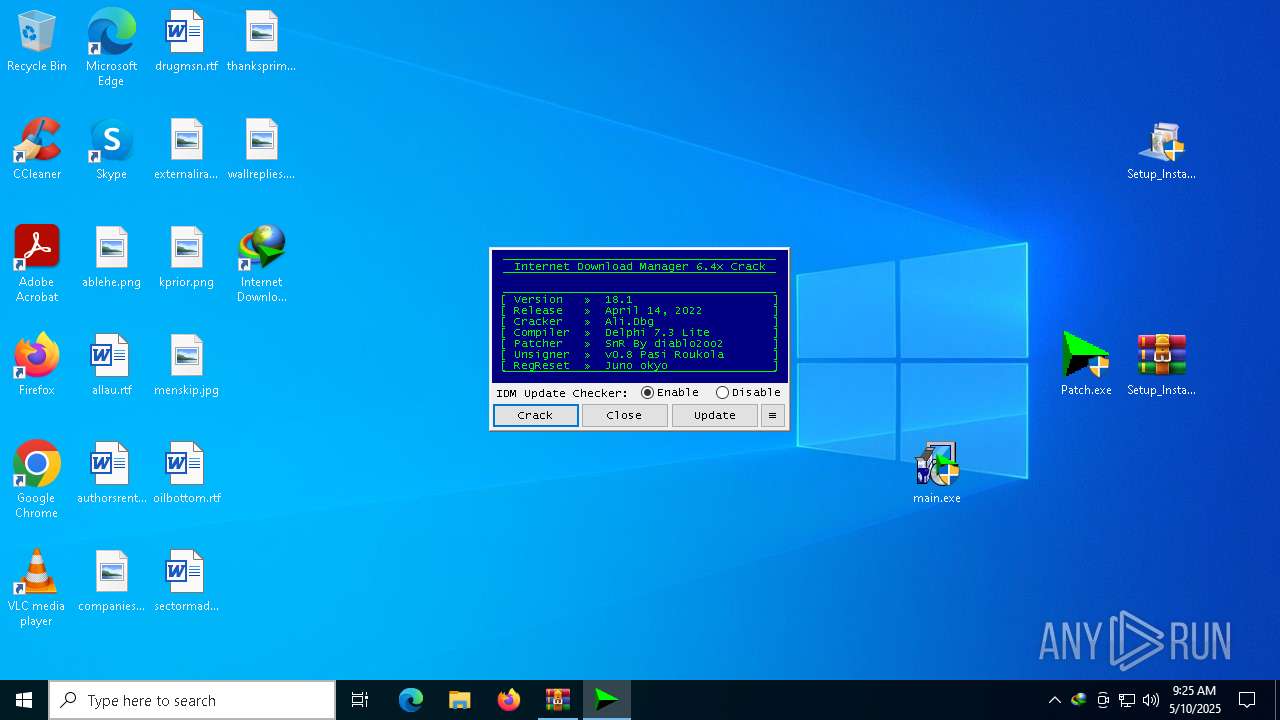
| File name: | _Getintopc.com_Internet_Download_Manager_6.41_Build_3.rar |
| Full analysis: | https://app.any.run/tasks/ad79a2d5-16fb-4447-88fe-e33d3185786c |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 10, 2025, 09:23:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 87F50E1499CFA92C3C4D49AB61B98D3D |
| SHA1: | 0E348D38F02C4E220C853E0C4D74859C160D91EB |
| SHA256: | 842177B1573BF2DFFFA813F5FF4827CB77125D06AAB0D2DC648A22AA3431D350 |
| SSDEEP: | 98304:aiCkwg8viyrgMPvFYRW/Nh3CyuhdM8QxyzaJc0GiDCz3s2EAnZzAgDgervmkC3OR:alKraoAvV55/uPrOcm+RY+s0RqXj8mu |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7380)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 4164)
Vulnerable driver has been detected
- WindowsService.exe (PID: 5260)
Creates a new scheduled task via Registry
- msiexec.exe (PID: 4164)
Connects to the CnC server
- cmd.exe (PID: 1616)
MINER has been detected (SURICATA)
- cmd.exe (PID: 1616)
XMRIG has been detected (YARA)
- cmd.exe (PID: 1616)
Registers / Runs the DLL via REGSVR32.EXE
- IDM1.tmp (PID: 5936)
- IDMan.exe (PID: 4300)
- Uninstall.exe (PID: 456)
- IDMan.exe (PID: 1852)
Starts NET.EXE for service management
- Uninstall.exe (PID: 456)
- net.exe (PID: 7348)
SUSPICIOUS
Reads the Windows owner or organization settings
- Setup_Install.exe (PID: 1020)
- msiexec.exe (PID: 6744)
Application launched itself
- WinRAR.exe (PID: 7384)
- cmd.exe (PID: 5360)
Executable content was dropped or overwritten
- Setup_Install.exe (PID: 1020)
- WindowsService.exe (PID: 5260)
- IDMan.exe (PID: 4300)
- Patch.exe (PID: 7868)
- wscript.exe (PID: 8132)
- rundll32.exe (PID: 6700)
- UnSigner.exe (PID: 2140)
Process drops legitimate windows executable
- Setup_Install.exe (PID: 1020)
Checks whether a specific file exists (SCRIPT)
- msiexec.exe (PID: 7240)
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 7240)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 7240)
Starts application with an unusual extension
- main.exe (PID: 1132)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7240)
- WindowsService.exe (PID: 5260)
- IDM1.tmp (PID: 5936)
- WinRAR.exe (PID: 7384)
- IDMan.exe (PID: 4300)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 4164)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 7380)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 4164)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 4164)
- cmd.exe (PID: 5360)
The process executes Powershell scripts
- msiexec.exe (PID: 4164)
Detects AdvancedInstaller (YARA)
- Setup_Install.exe (PID: 1020)
There is functionality for taking screenshot (YARA)
- Setup_Install.exe (PID: 1020)
- IDMan.exe (PID: 1852)
- IDMan.exe (PID: 4300)
Drops a system driver (possible attempt to evade defenses)
- WindowsService.exe (PID: 5260)
- rundll32.exe (PID: 6700)
Connects to unusual port
- WindowsService.exe (PID: 5260)
- cmd.exe (PID: 1616)
Starts CMD.EXE for commands execution
- WindowsService.exe (PID: 5260)
- Patch.exe (PID: 7868)
- cmd.exe (PID: 5360)
Potential Corporate Privacy Violation
- cmd.exe (PID: 1616)
Creates a software uninstall entry
- IDM1.tmp (PID: 5936)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 5936)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 5936)
- regsvr32.exe (PID: 7892)
- regsvr32.exe (PID: 7952)
- regsvr32.exe (PID: 7884)
- IDMan.exe (PID: 4300)
- regsvr32.exe (PID: 3024)
- regsvr32.exe (PID: 4012)
- regsvr32.exe (PID: 8124)
- regsvr32.exe (PID: 7900)
ADVANCEDINSTALLER mutex has been found
- Setup_Install.exe (PID: 1020)
The process executes VB scripts
- Patch.exe (PID: 7868)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 456)
Uses REG/REGEDIT.EXE to modify registry
- Patch.exe (PID: 7868)
- cmd.exe (PID: 5360)
Executing commands from a ".bat" file
- Patch.exe (PID: 7868)
Identifying current user with WHOAMI command
- cmd.exe (PID: 7268)
Uses TASKKILL.EXE to kill process
- Patch.exe (PID: 7868)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7384)
- WinRAR.exe (PID: 6028)
- msiexec.exe (PID: 6744)
- msiexec.exe (PID: 7240)
Checks supported languages
- Patch.exe (PID: 8028)
- msiexec.exe (PID: 5116)
- msiexec.exe (PID: 6744)
- msiexec.exe (PID: 7240)
- msiexec.exe (PID: 4164)
- IDM1.tmp (PID: 5936)
- main.exe (PID: 1132)
- WindowsService.exe (PID: 5260)
- Setup_Install.exe (PID: 1020)
- idmBroker.exe (PID: 7992)
- IDMan.exe (PID: 4300)
Manual execution by a user
- Patch.exe (PID: 8028)
- Patch.exe (PID: 7980)
- WinRAR.exe (PID: 6028)
- Setup_Install.exe (PID: 1660)
- Setup_Install.exe (PID: 1020)
- firefox.exe (PID: 3156)
- Patch.exe (PID: 4448)
- Patch.exe (PID: 7868)
- IDMan.exe (PID: 8032)
Reads Environment values
- Setup_Install.exe (PID: 1020)
- msiexec.exe (PID: 7240)
- msiexec.exe (PID: 5116)
- msiexec.exe (PID: 4164)
Reads the computer name
- msiexec.exe (PID: 6744)
- Setup_Install.exe (PID: 1020)
- Patch.exe (PID: 8028)
- msiexec.exe (PID: 5116)
- msiexec.exe (PID: 7240)
- msiexec.exe (PID: 4164)
- main.exe (PID: 1132)
- IDM1.tmp (PID: 5936)
- WindowsService.exe (PID: 5260)
- IDMan.exe (PID: 4300)
- idmBroker.exe (PID: 7992)
Creates files or folders in the user directory
- Setup_Install.exe (PID: 1020)
- msiexec.exe (PID: 6744)
- WindowsService.exe (PID: 5260)
- IDM1.tmp (PID: 5936)
- IDMan.exe (PID: 4300)
Create files in a temporary directory
- Setup_Install.exe (PID: 1020)
- main.exe (PID: 1132)
- IDM1.tmp (PID: 5936)
- powershell.exe (PID: 7380)
- IDMan.exe (PID: 4300)
The sample compiled with english language support
- WinRAR.exe (PID: 6028)
- Setup_Install.exe (PID: 1020)
- msiexec.exe (PID: 6744)
- msiexec.exe (PID: 7240)
- IDMan.exe (PID: 4300)
- rundll32.exe (PID: 6700)
- Patch.exe (PID: 7868)
- wscript.exe (PID: 8132)
- UnSigner.exe (PID: 2140)
Process checks computer location settings
- msiexec.exe (PID: 7240)
- IDM1.tmp (PID: 5936)
- IDMan.exe (PID: 4300)
INTERNETDOWNLOADMANAGER mutex has been found
- main.exe (PID: 1132)
- IDM1.tmp (PID: 5936)
- IDMan.exe (PID: 4300)
Reads the software policy settings
- powershell.exe (PID: 7380)
- IDMan.exe (PID: 4300)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7380)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7380)
The sample compiled with japanese language support
- WindowsService.exe (PID: 5260)
Checks proxy server information
- WindowsService.exe (PID: 5260)
- IDMan.exe (PID: 4300)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7380)
Creates files in the program directory
- IDM1.tmp (PID: 5936)
- cmd.exe (PID: 1616)
- IDMan.exe (PID: 4300)
Disables trace logs
- IDMan.exe (PID: 4300)
Reads the machine GUID from the registry
- IDMan.exe (PID: 4300)
Application launched itself
- firefox.exe (PID: 8148)
- firefox.exe (PID: 3156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
448
Monitored processes
316
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | REG DELETE "HKCU\Software\Classes\Wow6432Node\CLSID\{D5B91409-A8CA-4973-9A0B-59F713D25671}" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | /s "C:\Program Files (x86)\Internet Download Manager\IDMShellExt64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | "C:\Program Files (x86)\Internet Download Manager\Uninstall.exe" -instdriv | C:\Program Files (x86)\Internet Download Manager\Uninstall.exe | — | IDMan.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager installer Exit code: 1 Version: 6, 41, 3, 1 Modules
| |||||||||||||||
| 516 | REG DELETE "HKLM\Software\Classes\CLSID\{9C9D53D4-A978-43FC-93E2-1C21B529E6D7}" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | reg query "HKLM\Software\Classes\Wow6432Node\CLSID\{E6871B76-C3C8-44DD-B947-ABFFE144860D}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4232 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4908 -prefMapHandle 4900 -prefsLen 38187 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {bad24bc8-2514-456b-ab98-4fa483a62f16} 8148 "\\.\pipe\gecko-crash-server-pipe.8148" 157a49d9310 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 644 | reg query "HKCU\Software\Classes\Wow6432Node\CLSID\{9C9D53D4-A978-43FC-93E2-1C21B529E6D7}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | reg query "HKU\.DEFAULT\Software\Classes\CLSID\{E6871B76-C3C8-44DD-B947-ABFFE144860D}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | reg query "HKU\.DEFAULT\Software\Classes\Wow6432Node\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
57 650
Read events
56 612
Write events
770
Delete events
268
Modification events
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\_Getintopc.com_Internet_Download_Manager_6.41_Build_3.rar | |||
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
35
Suspicious files
111
Text files
34
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb7384.34248\Setup_Install.rar | — | |
MD5:— | SHA256:— | |||
| 7384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7384.35155\Setup_Install.rar | — | |
MD5:— | SHA256:— | |||
| 1020 | Setup_Install.exe | C:\Users\admin\AppData\Local\Temp\MSICAC1.tmp | executable | |
MD5:5A1F2196056C0A06B79A77AE981C7761 | SHA256:52F41817669AF7AC55B1516894EE705245C3148F2997FA0E6617E9CC6353E41E | |||
| 1020 | Setup_Install.exe | C:\Users\admin\AppData\Roaming\Getintopc.com\EXE - Step 3 - Setup_Install 1.0.0\install\A9F990C\GetintoPC-Top-EXE.msi | executable | |
MD5:412AB643D36494C1BEE50FA456BB7E72 | SHA256:BD0D85EE49DFE1715698BB723F8B451E8A3E95CE8B2191C9D56227F593665218 | |||
| 7384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7384.32620\Crack\Patch v18.1\Patch.exe | executable | |
MD5:DCDC109069B6E0D80D776C143FECDE3F | SHA256:FE44F050AB9EA33F87ACEF449ED57157A331A19956207D6243522676C894E284 | |||
| 6744 | msiexec.exe | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngen.log | text | |
MD5:F061D6B8FAACB175E95D5BBDAB01C4D7 | SHA256:93F0E87EC057B4602AB3F3768684A433E49C742B06393C12884652A7207DC296 | |||
| 1020 | Setup_Install.exe | C:\Users\admin\AppData\Local\Temp\MSICA05.tmp | executable | |
MD5:5A1F2196056C0A06B79A77AE981C7761 | SHA256:52F41817669AF7AC55B1516894EE705245C3148F2997FA0E6617E9CC6353E41E | |||
| 4164 | msiexec.exe | C:\Windows\SystemTemp\msiD270.txt | — | |
MD5:— | SHA256:— | |||
| 4164 | msiexec.exe | C:\Windows\SystemTemp\scrD271.ps1 | — | |
MD5:— | SHA256:— | |||
| 4164 | msiexec.exe | C:\Windows\SystemTemp\scrD272.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
51
DNS requests
69
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.175:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7856 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7856 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5260 | WindowsService.exe | GET | 200 | 188.138.25.13:83 | http://www.google.com.hlcn6aqosrzm20d1.fast-dns-host.com:83/md5_GIP.txt | unknown | — | — | unknown |
5260 | WindowsService.exe | GET | 200 | 188.138.25.13:83 | http://www.google.com.6cfi8pleroy0g4wj.fast-dns-host.com:83/Resource_GIP.bin | unknown | — | — | unknown |
5260 | WindowsService.exe | GET | 200 | 188.138.25.13:83 | http://www.google.com.hlcn6aqosrzm20d1.fast-dns-host.com:83/md5_GIP.txt | unknown | — | — | unknown |
8148 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.175:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
1616 | cmd.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
1616 | cmd.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |