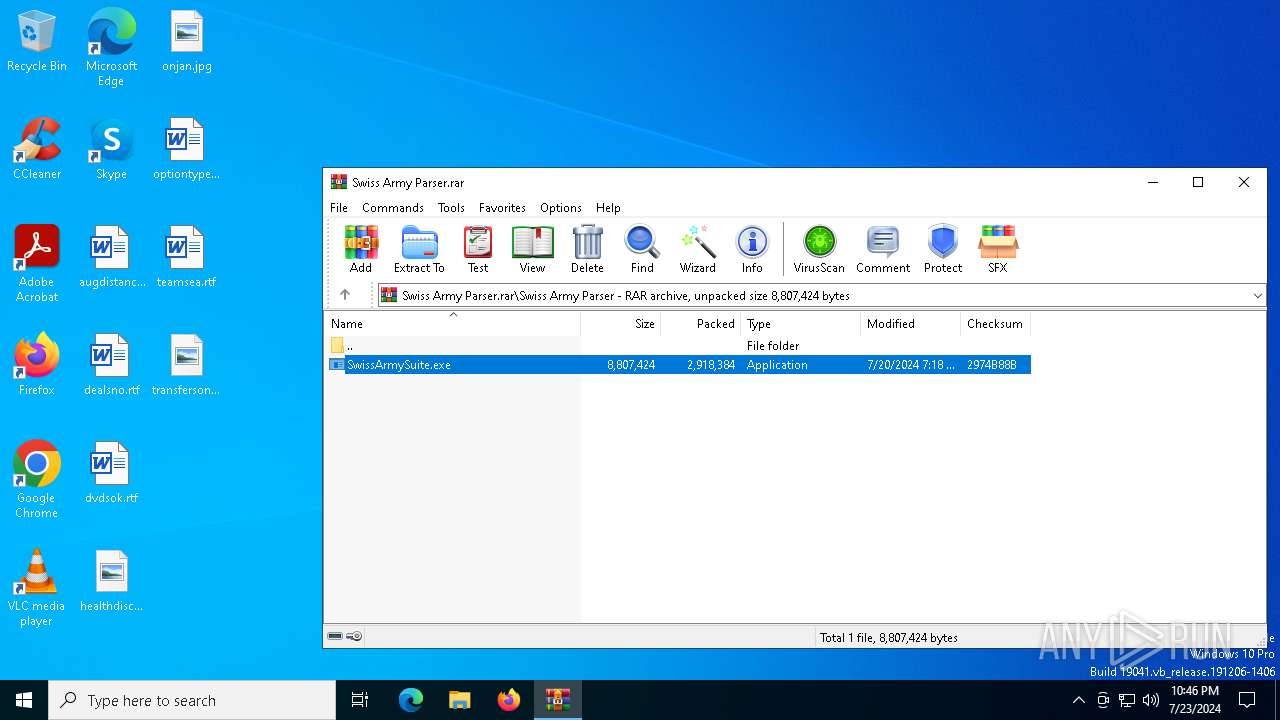
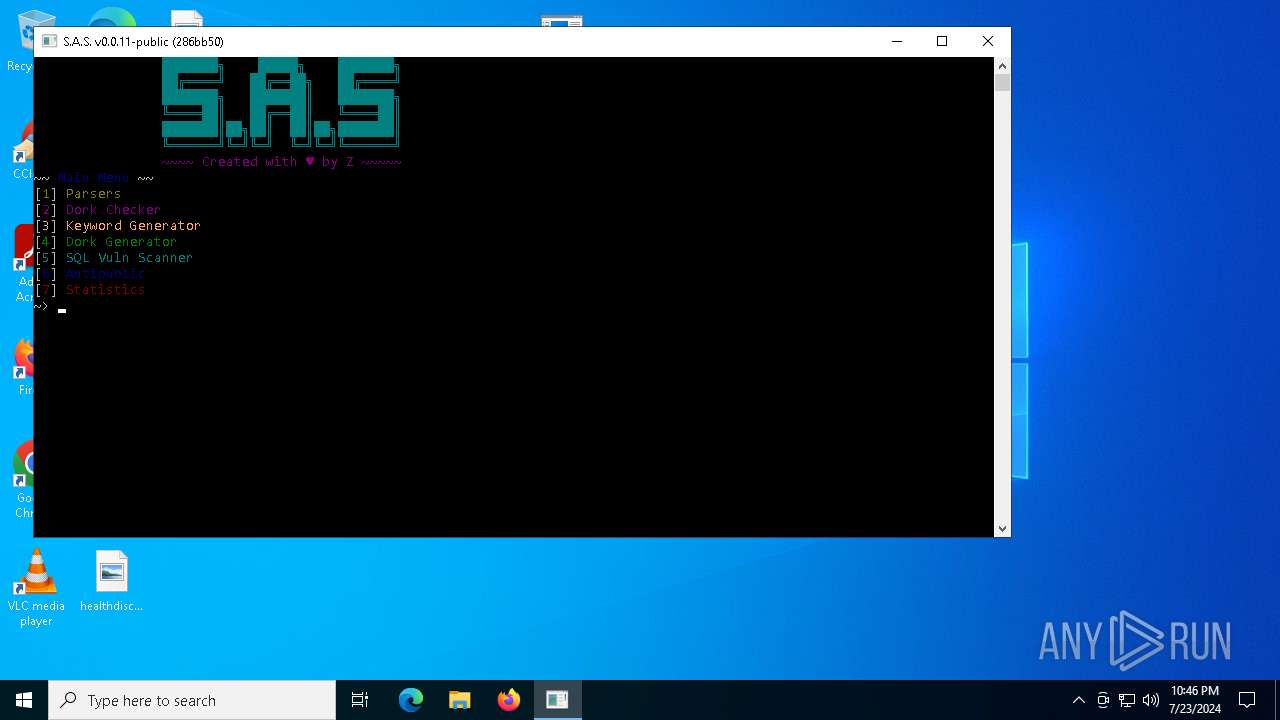
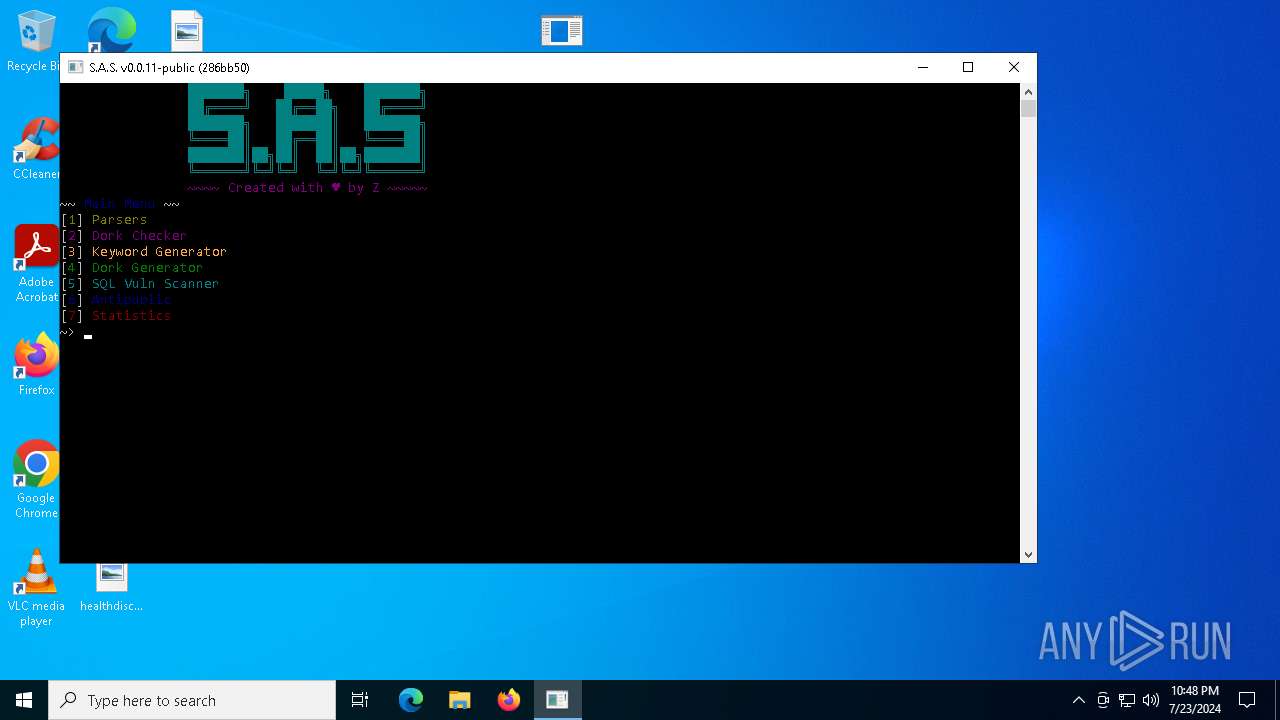
| File name: | Swiss Army Parser.rar |
| Full analysis: | https://app.any.run/tasks/c736ce6f-f0ae-4356-b692-7c19f4ce6951 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 23, 2024, 22:46:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 80A237FB71F6CB1A185D53E439E4CAC8 |
| SHA1: | 044F849C4FE64EA27A3BC469B9F19FB3B41AF5F8 |
| SHA256: | 8406AA32E2F833E014E0AFE995761556EFB0E0E71453FD4F3B4888A4A9B22C7A |
| SSDEEP: | 98304:DdJEhkBBq2ZiLlQL4JyDW7QhqNcrA2sUQeaZOFwzuYcyWMWO7nLnptWQJ7LW1i3f:OVV/ |
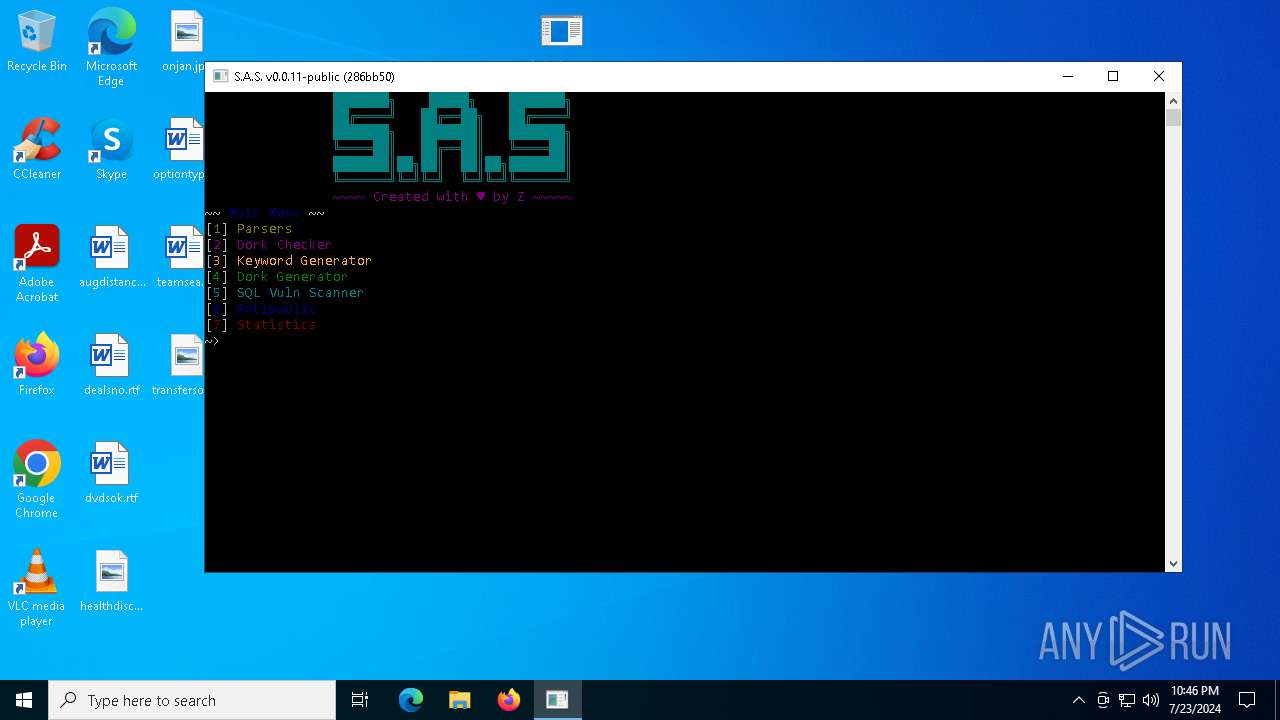
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2348)
- SwissArmySuite.exe (PID: 4748)
- LET.EXE (PID: 1264)
- SwissArmySuite.exe (PID: 6192)
Steals credentials from Web Browsers
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
ASYNCRAT has been detected (MUTEX)
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Actions looks like stealing of personal data
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 1264)
- LET.EXE (PID: 6680)
Attempting to use instant messaging service
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Stealers network behavior
- LET.EXE (PID: 2084)
- LET.EXE (PID: 2820)
- LET.EXE (PID: 6680)
STORMKITTY has been detected (YARA)
- LET.EXE (PID: 6680)
Uses Task Scheduler to autorun other applications
- svchost.com (PID: 1468)
SUSPICIOUS
Reads security settings of Internet Explorer
- SwissArmySuite.exe (PID: 4748)
- LET.EXE (PID: 1264)
- LET.EXE (PID: 2820)
- SwissArmySuite.exe (PID: 6192)
- SwissArmySuite.exe (PID: 3392)
- LET.EXE (PID: 6680)
Reads the date of Windows installation
- SwissArmySuite.exe (PID: 4748)
- LET.EXE (PID: 1264)
- LET.EXE (PID: 2820)
- SwissArmySuite.exe (PID: 6192)
- SwissArmySuite.exe (PID: 3392)
- LET.EXE (PID: 6680)
Executable content was dropped or overwritten
- SwissArmySuite.exe (PID: 4748)
- LET.EXE (PID: 1264)
- SwissArmySuite.exe (PID: 6192)
Mutex name with non-standard characters
- LET.EXE (PID: 1264)
Write to the desktop.ini file (may be used to cloak folders)
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Starts application with an unusual extension
- cmd.exe (PID: 4564)
- cmd.exe (PID: 6312)
- cmd.exe (PID: 5052)
- cmd.exe (PID: 3560)
- SwissArmySuite.exe (PID: 3392)
- cmd.exe (PID: 6948)
- cmd.exe (PID: 3188)
- LET.EXE (PID: 6680)
Starts CMD.EXE for commands execution
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 4564)
- cmd.exe (PID: 6312)
- cmd.exe (PID: 5052)
- cmd.exe (PID: 3560)
- cmd.exe (PID: 6948)
- cmd.exe (PID: 3188)
Application launched itself
- LET.EXE (PID: 2820)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4564)
- cmd.exe (PID: 5052)
- cmd.exe (PID: 6948)
Potential Corporate Privacy Violation
- LET.EXE (PID: 2820)
- LET.EXE (PID: 6680)
Checks for external IP
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
The process connected to a server suspected of theft
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Found regular expressions for crypto-addresses (YARA)
- SWISSARMYSUITE.EXE (PID: 3488)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 2820)
- LET.EXE (PID: 6680)
INFO
Manual execution by a user
- SwissArmySuite.exe (PID: 4748)
- SwissArmySuite.exe (PID: 6192)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2348)
Reads the software policy settings
- slui.exe (PID: 4648)
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Checks supported languages
- SwissArmySuite.exe (PID: 4748)
- LET.EXE (PID: 1264)
- LET.EXE (PID: 2820)
- SWISSARMYSUITE.EXE (PID: 3488)
- LET.EXE (PID: 2084)
- chcp.com (PID: 2340)
- chcp.com (PID: 2332)
- chcp.com (PID: 6384)
- SwissArmySuite.exe (PID: 6192)
- chcp.com (PID: 6324)
- SwissArmySuite.exe (PID: 3392)
- LET.EXE (PID: 6680)
- svchost.com (PID: 5436)
- svchost.com (PID: 5304)
- SWISSARMYSUITE.EXE (PID: 2112)
- chcp.com (PID: 3960)
- chcp.com (PID: 6288)
- svchost.com (PID: 1468)
Create files in a temporary directory
- SwissArmySuite.exe (PID: 4748)
- LET.EXE (PID: 1264)
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- SwissArmySuite.exe (PID: 3392)
- SwissArmySuite.exe (PID: 6192)
- LET.EXE (PID: 6680)
Checks proxy server information
- slui.exe (PID: 4648)
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Reads the computer name
- SwissArmySuite.exe (PID: 4748)
- LET.EXE (PID: 1264)
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- SwissArmySuite.exe (PID: 6192)
- SwissArmySuite.exe (PID: 3392)
- LET.EXE (PID: 6680)
Process checks computer location settings
- SwissArmySuite.exe (PID: 4748)
- LET.EXE (PID: 1264)
- LET.EXE (PID: 2820)
- SwissArmySuite.exe (PID: 6192)
- SwissArmySuite.exe (PID: 3392)
- LET.EXE (PID: 6680)
Reads the machine GUID from the registry
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Reads Environment values
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Creates files or folders in the user directory
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Disables trace logs
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Reads CPU info
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Attempting to use instant messaging service
- LET.EXE (PID: 2820)
- LET.EXE (PID: 2084)
- LET.EXE (PID: 6680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
StormKitty
(PID) Process(6680) LET.EXE
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
Protocoltelegram
URLhttps://api.telegram.org/bot1784055443:AAG-bXLYtnFpjJ_L3ogxA3bq6Mx09cqh8ug/send
Token7044437613:AAEXeS1SKGTrEjQ8F-7vSegWo8OLABeJY5k
ChatId6052812018
Version
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignatureeyEXLhs9pLjRXABIynCdINbSrxourxH8huz0AlQXcwg4tPRafbGDPEaCb/YD2zJJdVu05HHePBU+sdSztnCDLxwcQ9ew34ZHIm+Gywvp/7+hPtmuLGuI8R83qU25GmByv6M41p6R1B8TbeLSzUBrjfsTxhG5FHV3BHnDTRnQ3K6n9NDZAf+xjEynSZAUdAihxjENRmSxbzmCdSy37iCLzgC+zbEIMqWBM7s6gmtpNMovzsSrI8Pfevr+ykaIKSB35WqyWBUyTq4v4uTfM9BpP3gWQHkrR6tt8mm7zeh6vYaC...
Keys
AESce498183f557f217d115bbfa78eba978b90248dad2f2de75c114e95e7cd11552
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
183
Monitored processes
46
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | C:\Windows\System32\schtasks.exe /create /f /sc ONLOGON /RL HIGHEST /tn Chrome Update /tr C:\Users\admin\AppData\Local\Temp\LET.EXE | C:\Windows\SysWOW64\schtasks.exe | — | svchost.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 2147500037 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1252 | "C:\Users\admin\AppData\Local\Temp\SWISSARMYSUITE.EXE" | C:\Users\admin\AppData\Local\Temp\SWISSARMYSUITE.EXE | — | SwissArmySuite.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SwissArmySuite Exit code: 3221226540 Version: 0.1.0 Modules
| |||||||||||||||
| 1264 | "C:\Users\admin\AppData\Local\Temp\LET.EXE" | C:\Users\admin\AppData\Local\Temp\LET.EXE | SwissArmySuite.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1468 | "C:\WINDOWS\svchost.com" "C:\Windows\System32\schtasks.exe" /create /f /sc ONLOGON /RL HIGHEST /tn "Chrome Update" /tr "C:\Users\admin\AppData\Local\Temp\LET.EXE" | C:\Windows\svchost.com | LET.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1552 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1772 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SWISSARMYSUITE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\AppData\Local\Temp\3582-490\LET.EXE" | C:\Users\admin\AppData\Local\Temp\3582-490\LET.EXE | LET.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2112 | C:\Users\admin\AppData\Local\Temp\SWISSA~1.EXE | C:\Users\admin\AppData\Local\Temp\SWISSARMYSUITE.EXE | — | svchost.com | |||||||||||
User: admin Integrity Level: HIGH Description: SwissArmySuite Exit code: 3221225786 Version: 0.1.0 Modules
| |||||||||||||||
| 2332 | chcp 65001 | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | chcp 65001 | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
38 465
Read events
38 380
Write events
85
Delete events
0
Modification events
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Swiss Army Parser.rar | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3B010000A7000000FB04000090020000 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
13
Suspicious files
14
Text files
118
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1264 | LET.EXE | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncConfig.exe | executable | |
MD5:0C5EC1AE9A301408AF26032B445FBB08 | SHA256:3A8010F1E4E028782093877D969EB127B80AE48B7215A8D3F91E8AB9C165AC7A | |||
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2348.9396\Swiss Army Parser\SwissArmySuite.exe | executable | |
MD5:F1EB8D59EE24B6E1DD3D7B7F155FED5F | SHA256:BF73C67869DB2375CC4E01202AD26EDD9300EB00BF3FEDD0F20C86848F32986C | |||
| 2820 | LET.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\dealsno.rtf | text | |
MD5:F72A1343BFFF48CD524AD504B4620FE5 | SHA256:EA651F4E8DC6291BC171F8FA48B2B46DDD99E204C191E3B54B5E79F22A1AA303 | |||
| 2820 | LET.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\desktop.ini | text | |
MD5:3A37312509712D4E12D27240137FF377 | SHA256:B029393EA7B7CF644FB1C9F984F57C1980077562EE2E15D0FFD049C4C48098D3 | |||
| 2820 | LET.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\desktop.ini | text | |
MD5:29EAE335B77F438E05594D86A6CA22FF | SHA256:88856962CEF670C087EDA4E07D8F78465BEEABB6143B96BD90F884A80AF925B4 | |||
| 2820 | LET.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\datemotor.png | image | |
MD5:875477E1E0EB31BCA686D0A5F0F55057 | SHA256:3A27AC790309C64A81D2A578CC29E927213E33CC671D0E2E17BAEF671D7A539E | |||
| 2820 | LET.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\idlesbian.png | image | |
MD5:A6E3B16712B3BB93F50A56100A6B77A5 | SHA256:43F736EB1650DD720823DA3A430B5A36138D3822B5042CDF3060BB0DF794627C | |||
| 2820 | LET.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Documents\desktop.ini | text | |
MD5:ECF88F261853FE08D58E2E903220DA14 | SHA256:CAFEC240D998E4B6E92AD1329CD417E8E9CBD73157488889FD93A542DE4A4844 | |||
| 1264 | LET.EXE | C:\Users\admin\AppData\Local\Microsoft\OneDrive\OneDrive.exe | executable | |
MD5:178B773B3FB050FCE26E40A9E8C2EE9A | SHA256:1E03573733F25B44004049A535E7E79366FD86FE953F6DFEDAAD05513B46A6C5 | |||
| 1264 | LET.EXE | C:\ProgramData\Adobe\ARM\S\388\AdobeARMHelper.exe | executable | |
MD5:85A67D34298E33D2D5A9EC789B6AB594 | SHA256:1DEE143B4F88F2375B85C6271A58E2E78FED081BEAE4090678CB2DD7A37FB2D4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
63
DNS requests
24
Threats
35
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6680 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2820 | LET.EXE | GET | 200 | 104.16.184.241:80 | http://icanhazip.com/ | unknown | — | — | shared |
6524 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6680 | LET.EXE | GET | 200 | 104.16.184.241:80 | http://icanhazip.com/ | unknown | — | — | shared |
2084 | LET.EXE | GET | 200 | 104.16.184.241:80 | http://icanhazip.com/ | unknown | — | — | shared |
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3560 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3076 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6312 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4648 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5368 | SearchApp.exe | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2820 | LET.EXE | Potential Corporate Privacy Violation | ET POLICY Observed Wifi Geolocation Domain (api .mylnikov .org in TLS SNI) |
2820 | LET.EXE | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
2284 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
2284 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
2820 | LET.EXE | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
2820 | LET.EXE | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
2820 | LET.EXE | Misc activity | ET HUNTING Telegram API Certificate Observed |
2820 | LET.EXE | Misc activity | ET HUNTING Telegram API Certificate Observed |
2820 | LET.EXE | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Telegram |
2820 | LET.EXE | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
Process | Message |
|---|---|
SwissArmySuite.exe | C:\Users\admin\AppData\Local\Temp\LET.EXE |
SwissArmySuite.exe | C:\Users\admin\AppData\Local\Temp\SWISSARMYSUITE.EXE |
SwissArmySuite.exe | C:\Users\admin\AppData\Local\Temp\LET.EXE |
SwissArmySuite.exe | C:\Users\admin\AppData\Local\Temp\SWISSARMYSUITE.EXE |