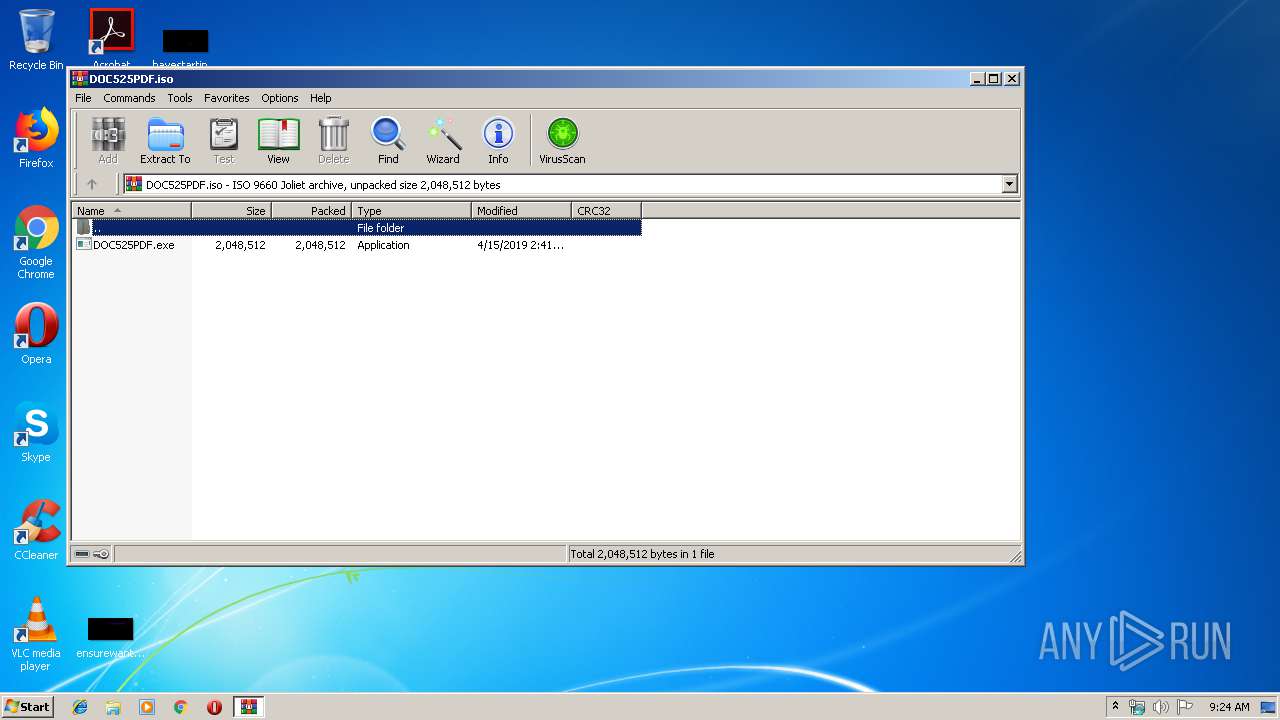
| File name: | DOC525PDF.iso |
| Full analysis: | https://app.any.run/tasks/115bb939-2538-4c70-b560-3518e1fb6f90 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | April 15, 2019, 08:24:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | ISO 9660 CD-ROM filesystem data 'DOC525PDF' |
| MD5: | 0D467CCA2A1762327A6B51E774D764C8 |
| SHA1: | CDB7AC919B47EE863D9237AC999119EF0D3CAFBA |
| SHA256: | 83E9970D0ED88F5C3CEB9CAEBFB85348EC4A19BED82928E7B921B11FFCA2BC7C |
| SSDEEP: | 24576:3AHnh+eWsN3skA4RV1Hom2KXMmHa/K5KMmxThqItFi605qXaSJpgJpszqEH5:qh+ZkldoPK8Ya/D |
MALICIOUS
Application was dropped or rewritten from another process
- DOC525PDF.exe (PID: 3480)
Actions looks like stealing of personal data
- vbc.exe (PID: 3820)
- vbc.exe (PID: 3164)
Detected Hawkeye Keylogger
- RegAsm.exe (PID: 2312)
Stealing of credential data
- vbc.exe (PID: 3820)
- vbc.exe (PID: 3164)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3800)
- WinRAR.exe (PID: 3632)
Executes scripts
- RegAsm.exe (PID: 2312)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 3820)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
ISO
| System: | Win32 |
|---|---|
| VolumeName: | DOC525PDF |
| VolumeBlockCount: | 1031 |
| VolumeBlockSize: | 2048 |
| RootDirectoryCreateDate: | 2019:04:15 02:50:44+01:00 |
| Software: | PowerISO |
| VolumeCreateDate: | 2019:04:15 02:50:44.00+01:00 |
| VolumeModifyDate: | 2019:04:15 02:50:44.00+01:00 |
Composite
| VolumeSize: | 2.0 MB |
|---|
Total processes
41
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2312 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | DOC525PDF.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 3048 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\DOC525PDF.iso | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3164 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmpABF4.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 3480 | "C:\Users\admin\Desktop\DOC525PDF.exe" | C:\Users\admin\Desktop\DOC525PDF.exe | — | explorer.exe | |||||||||||
User: admin Company: DeviceCredentialDeployment Integrity Level: MEDIUM Description: cmmon32 Exit code: 0 Version: 28.303.676.215 Modules
| |||||||||||||||
| 3632 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\DOC525PDF.iso" | C:\Program Files\WinRAR\WinRAR.exe | rundll32.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3800 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\DOC525PDF.iso" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3820 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmp8291.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
Total events
589
Read events
482
Write events
107
Delete events
0
Modification events
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\isoburn.exe,-350 |
Value: Disc Image File | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.iso\OpenWithProgids |
| Operation: | write | Name: | Windows.IsoFile |
Value: | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\isoburn.exe,-352 |
Value: Windows Disc Image Burner | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\System32\isoburn.exe |
Value: Windows Disc Image Burner | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\WinRAR\WinRAR.exe |
Value: WinRAR archiver | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3048) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
Executable files
2
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3800 | WinRAR.exe | C:\Users\admin\Desktop\DOC525PDF.exe | executable | |
MD5:— | SHA256:— | |||
| 3632 | WinRAR.exe | C:\Users\admin\Desktop\DOC525PDF.exe | executable | |
MD5:— | SHA256:— | |||
| 3820 | vbc.exe | C:\Users\admin\AppData\Local\Temp\tmp8291.tmp | text | |
MD5:3E1E093DCCE32C716267A28292E0EE27 | SHA256:56285445424AD06DC043154819B5BDABAA7C26F5779CA3E37E08424ED9926CB8 | |||
| 3164 | vbc.exe | C:\Users\admin\AppData\Local\Temp\tmpABF4.tmp | text | |
MD5:7FB9A9AD0FD9B1E0108ED71FBB276048 | SHA256:7D63C301317E144B0133A72250AE2D8E09AF65A92E6A807EC58A71939FE530A9 | |||
| 2312 | RegAsm.exe | C:\Users\admin\AppData\Local\Temp\25291068-43af-3e16-50f6-5889d9ce7904 | text | |
MD5:CC31A51EBE8F2F7B120C0731335A04A9 | SHA256:BBBFD2DBB09BA2B61BA9CE2846F2BC9604A87F3717F63ECB92831B6D80A9D443 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2312 | RegAsm.exe | 185.193.52.212:21 | ftp.datacity.ro | Sc Ad Net Market Media Srl | RO | malicious |
2312 | RegAsm.exe | 185.193.52.212:55095 | ftp.datacity.ro | Sc Ad Net Market Media Srl | RO | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ftp.datacity.ro |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2312 | RegAsm.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2312 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Spyware.HawkEyeKeyLogger Exfiltration over FTP |
2312 | RegAsm.exe | A Network Trojan was detected | ET TROJAN HawkEye Keylogger FTP |