| File name: | 83babee77db36512c0eab8ea6b35e981aa4288a4095985d69b3841f8b684fe11.ps1 |
| Full analysis: | https://app.any.run/tasks/e5d85e3c-a1c9-4d1d-88bb-21f1bda073c9 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 16, 2025, 18:21:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 (with BOM) text, with very long lines (65514), with CRLF line terminators |
| MD5: | 99C23706A4BD973EBDA4BDB88B87C834 |
| SHA1: | 672A6A80BD7484229111364C73CA1973E76803F3 |
| SHA256: | 83BABEE77DB36512C0EAB8EA6B35E981AA4288A4095985D69B3841F8B684FE11 |
| SSDEEP: | 3072:RGLx9EwczhNbwXibYsKk/1g3/cNvTGFJgdqoZ3zKSGd7qfuQTUfWwLC5ImBK5W9N:RGLx9EPzhNbwXQYsKkpGyTUOwqYyfbT |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 3656)
- powershell.exe (PID: 5348)
PSLORAMYRA has been detected
- wscript.exe (PID: 2288)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 1212)
Run PowerShell with an invisible window
- powershell.exe (PID: 5348)
ASYNCRAT has been detected (MUTEX)
- RegSvcs.exe (PID: 2324)
SUSPICIOUS
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 3656)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 3656)
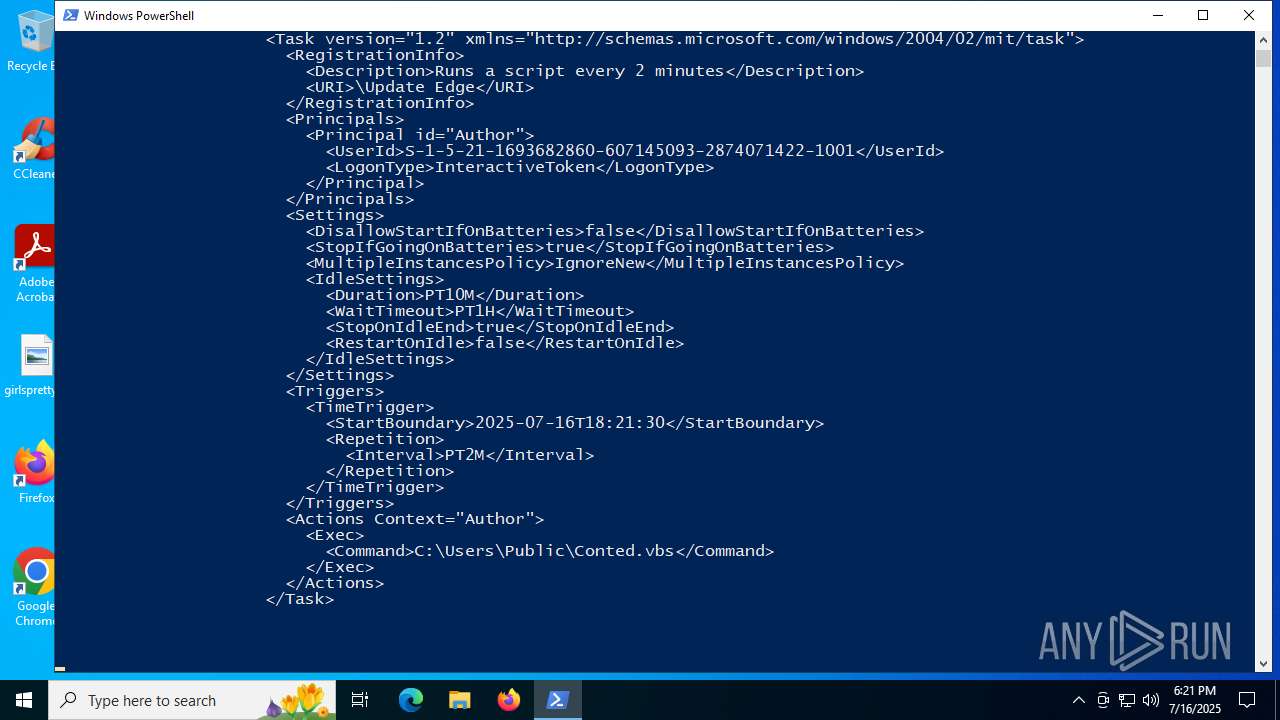
Likely accesses (executes) a file from the Public directory
- wscript.exe (PID: 2288)
- cmd.exe (PID: 1212)
- powershell.exe (PID: 5348)
The process executes via Task Scheduler
- wscript.exe (PID: 2288)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2288)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2288)
Executing commands from a ".bat" file
- wscript.exe (PID: 2288)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1212)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1212)
The process executes Powershell scripts
- cmd.exe (PID: 1212)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 5348)
Connects to unusual port
- RegSvcs.exe (PID: 2324)
INFO
Checks proxy server information
- slui.exe (PID: 3100)
Reads the software policy settings
- slui.exe (PID: 3100)
Reads the computer name
- RegSvcs.exe (PID: 2324)
Checks supported languages
- RegSvcs.exe (PID: 2324)
Reads the machine GUID from the registry
- RegSvcs.exe (PID: 2324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
Total processes
142
Monitored processes
10
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1212 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\Public\Conted.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2288 | C:\WINDOWS\System32\WScript.exe "C:\Users\Public\Conted.vbs" | C:\Windows\System32\wscript.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2324 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3100 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3656 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\83babee77db36512c0eab8ea6b35e981aa4288a4095985d69b3841f8b684fe11.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5348 | powershell.exe -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -Command "& 'C:\Users\Public\Conted.ps1'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5552 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5904 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
13 165
Read events
13 165
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3656 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF18d963.TMP | binary | |
MD5:00A03B286E6E0EBFF8D9C492365D5EC2 | SHA256:4DBFC417D053BA6867308671F1C61F4DCAFC61F058D4044DB532DA6D3BDE3615 | |||
| 3656 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bod3uoth.qzl.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3656 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:EB6E44AFD03302A6552B2B20EBCC7472 | SHA256:470C355E40398348DCBBCEAAC57FD65D033C1CE70BB252386FEC4968523D750A | |||
| 3656 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_slwgzoo5.r2s.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3656 | powershell.exe | C:\Users\Public\Conted.ps1 | text | |
MD5:089315EBEAC43E1A45DA3014F56C5006 | SHA256:3A0A477030EABA84883193EDE461D8595C3CA4345811632E295D9C2D136C1593 | |||
| 5348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lhgkeqa4.jtt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3656 | powershell.exe | C:\Users\Public\Conted.bat | text | |
MD5:759278DD3DC3679BF7EFD1EC681C0AA1 | SHA256:CBA344447D8228D88C93D64FFDCDA1DE8562EF41ADC4901191548E00BBFC5F19 | |||
| 3656 | powershell.exe | C:\Users\Public\Conted.vbs | text | |
MD5:110DA9D3474BA64FA1A18C173685C25D | SHA256:A31DBD6F7416F150403C19BE69F02D5E8608F5E7FAE88A29831D40DB15849B60 | |||
| 3656 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:834D31983D4408203A815BDAB88B230D | SHA256:F8F00F0E47767AE23EA299982B38DCE6EE852B1D3F11D976611A07968C97D2C1 | |||
| 5348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dtgbxk51.i22.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
32
DNS requests
17
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
236 | RUXIMICS.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
3768 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3768 | SIHClient.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
3768 | SIHClient.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.165.164.15:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
3768 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
236 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
236 | RUXIMICS.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6024 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6756 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
madmrx.duckdns.org |
| malicious |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2200 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2200 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |