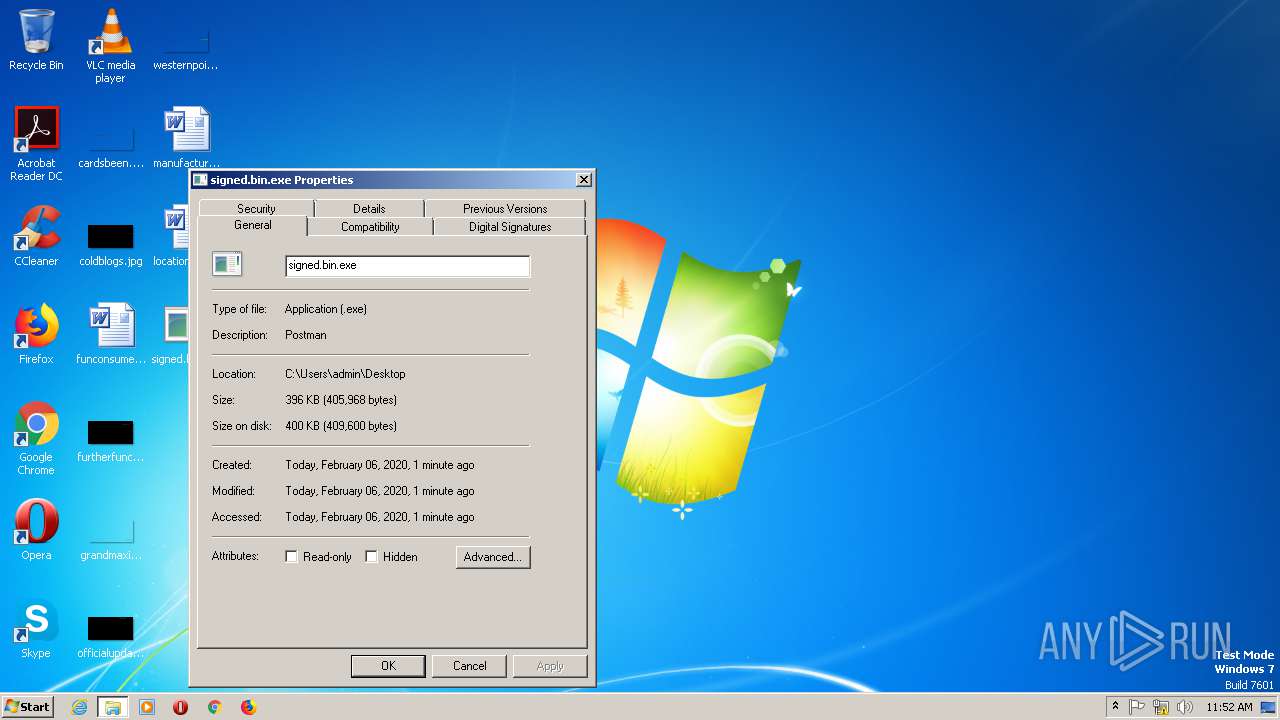
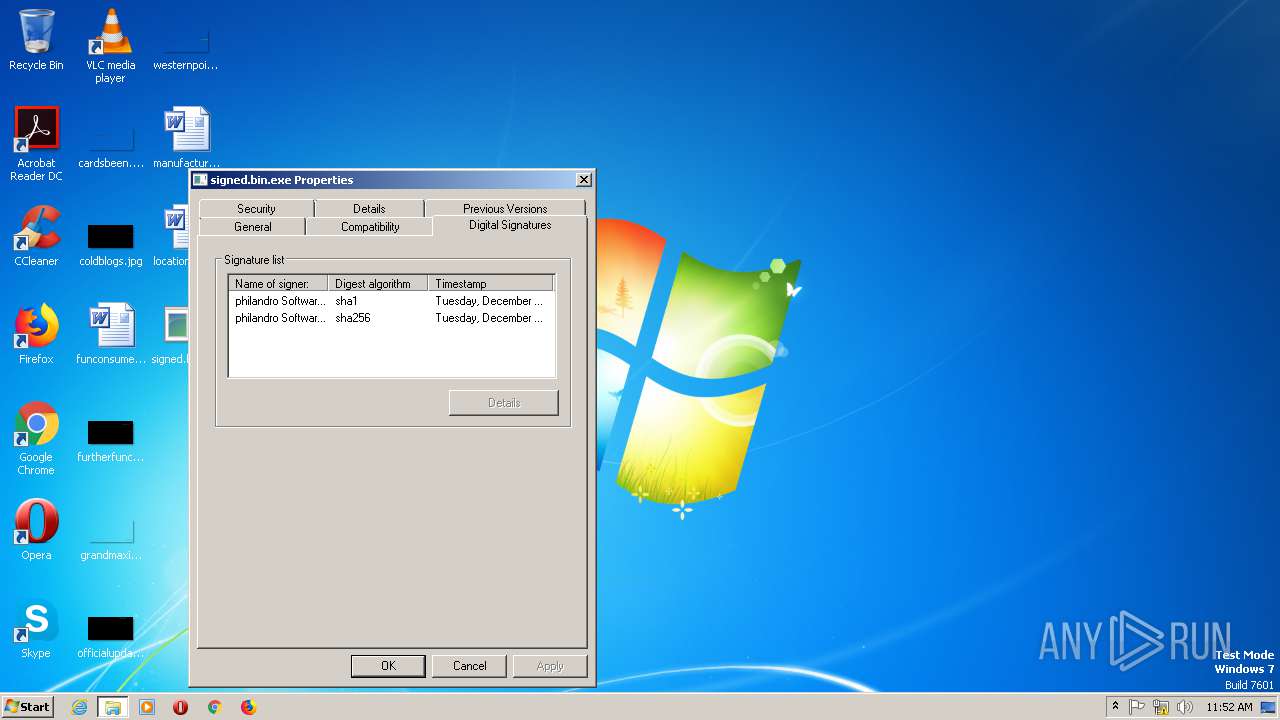
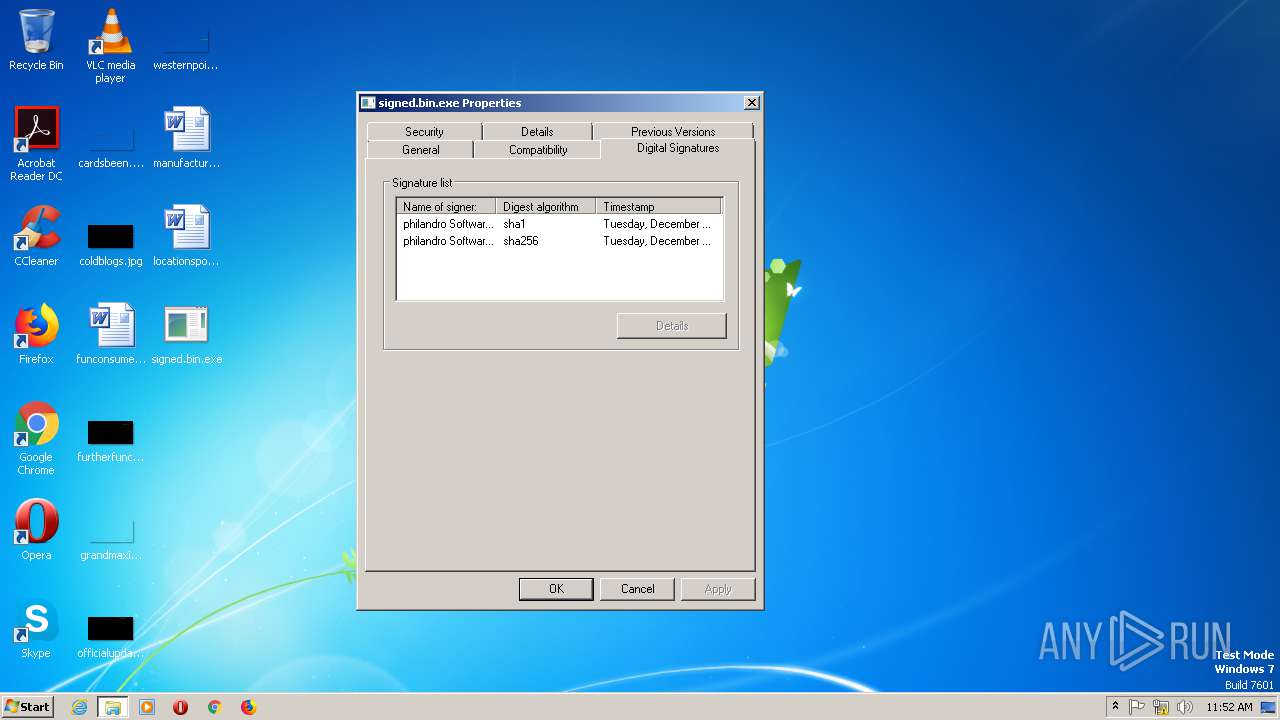
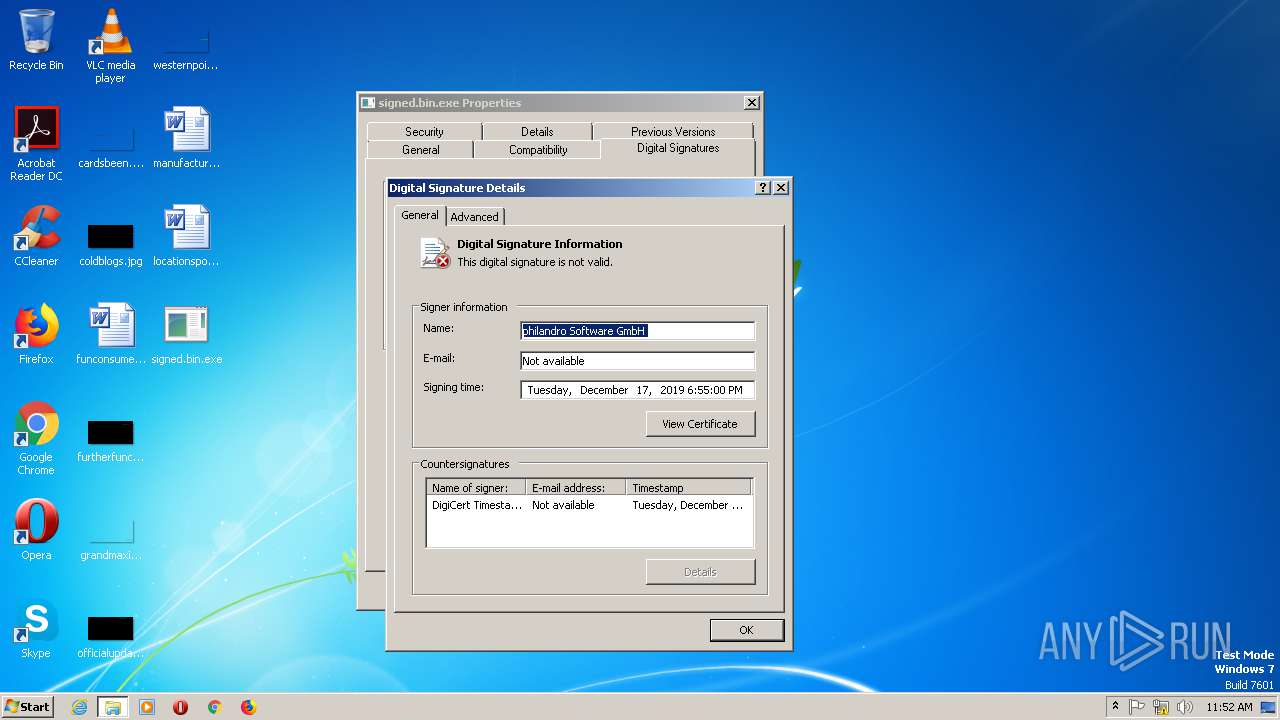
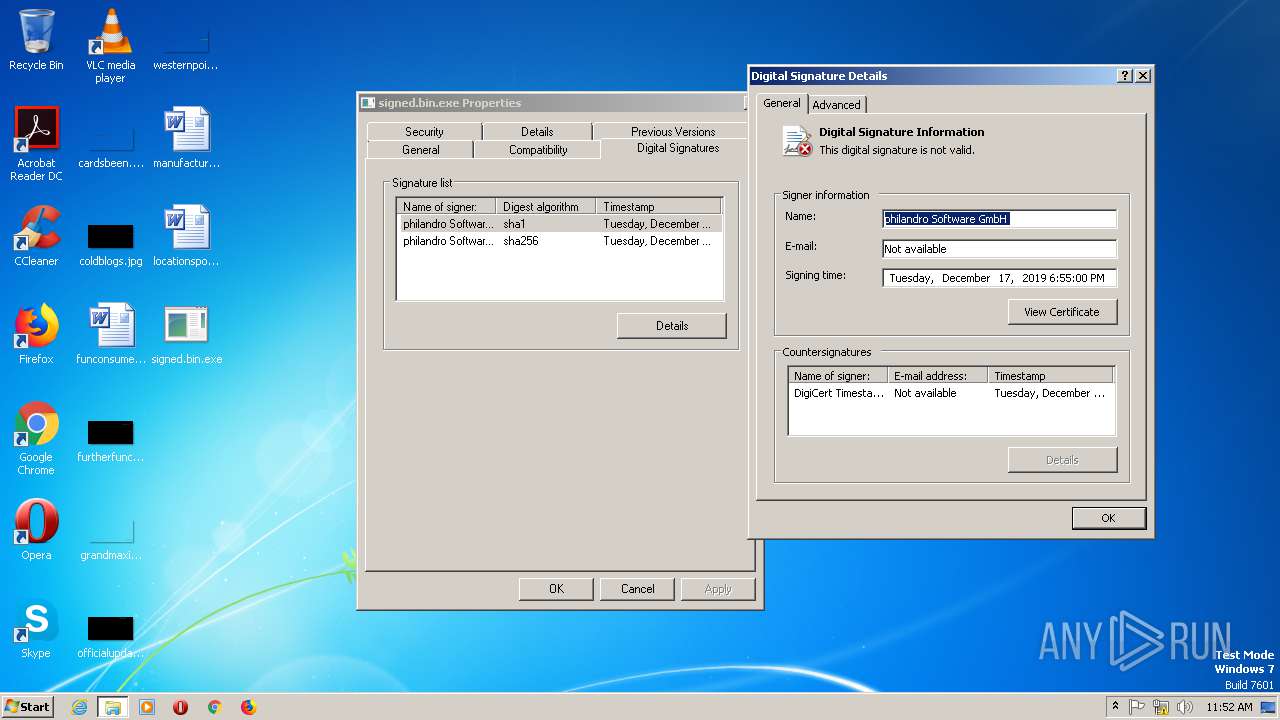
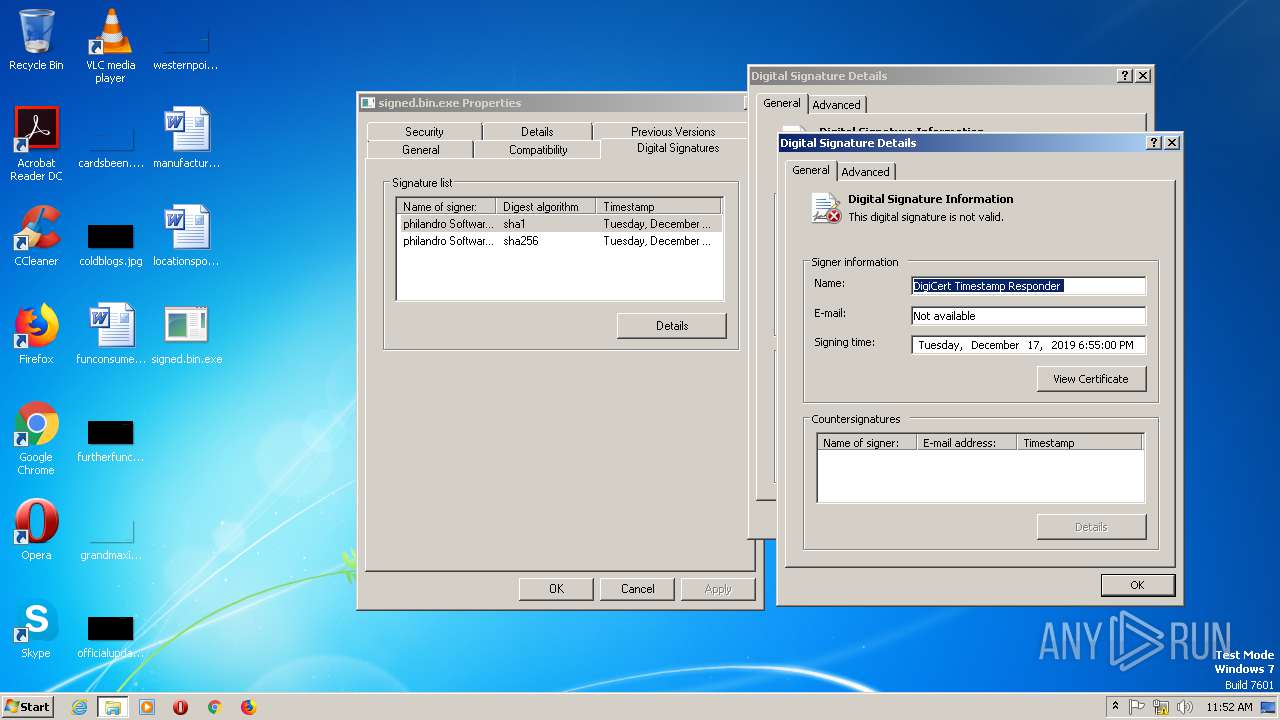
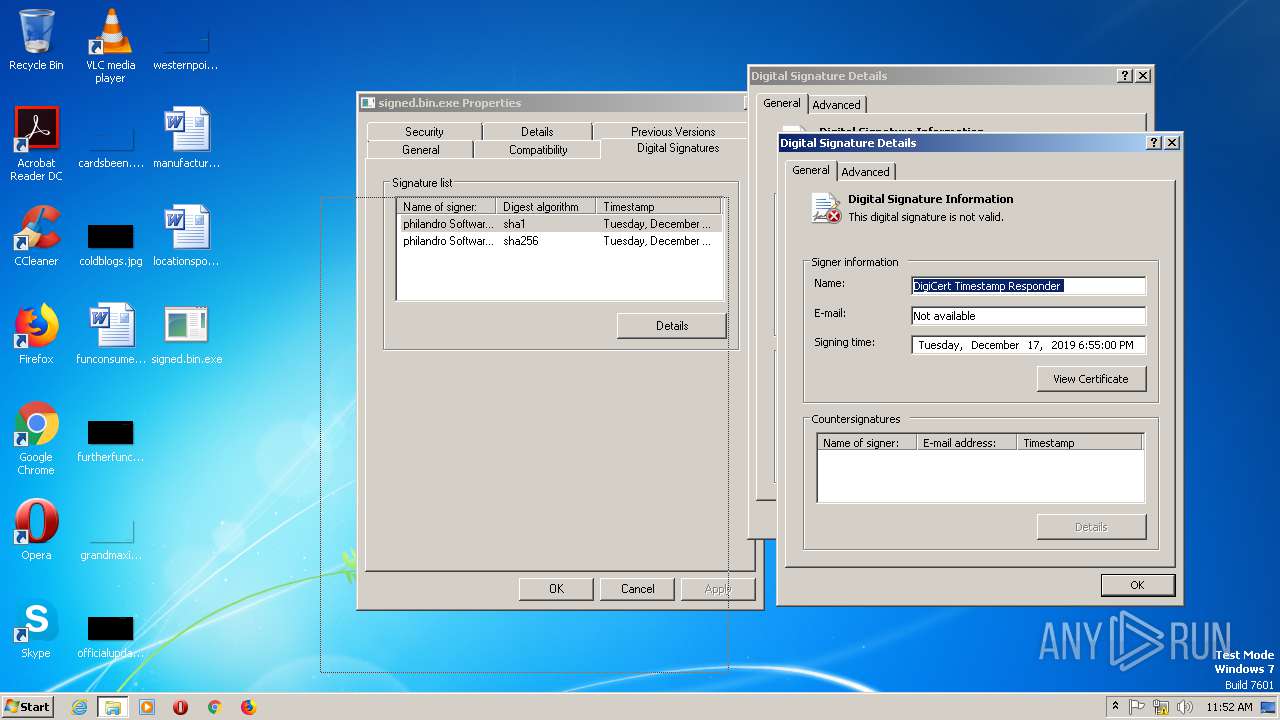
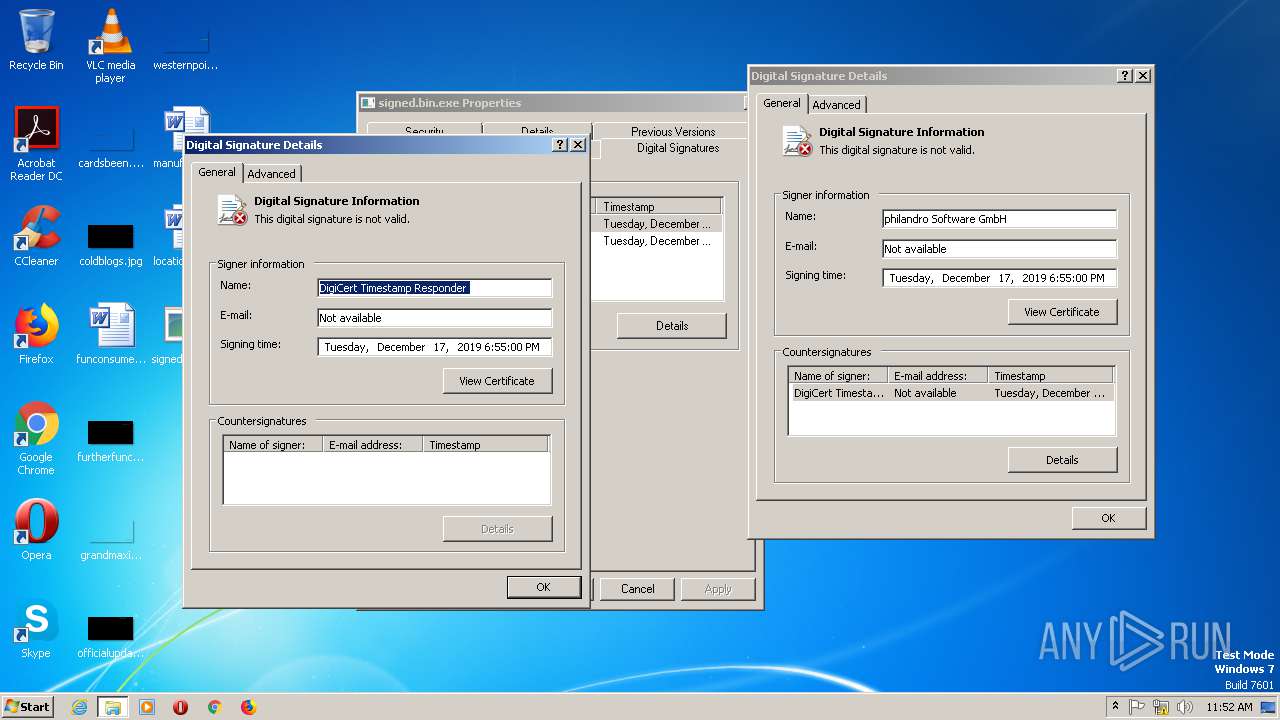
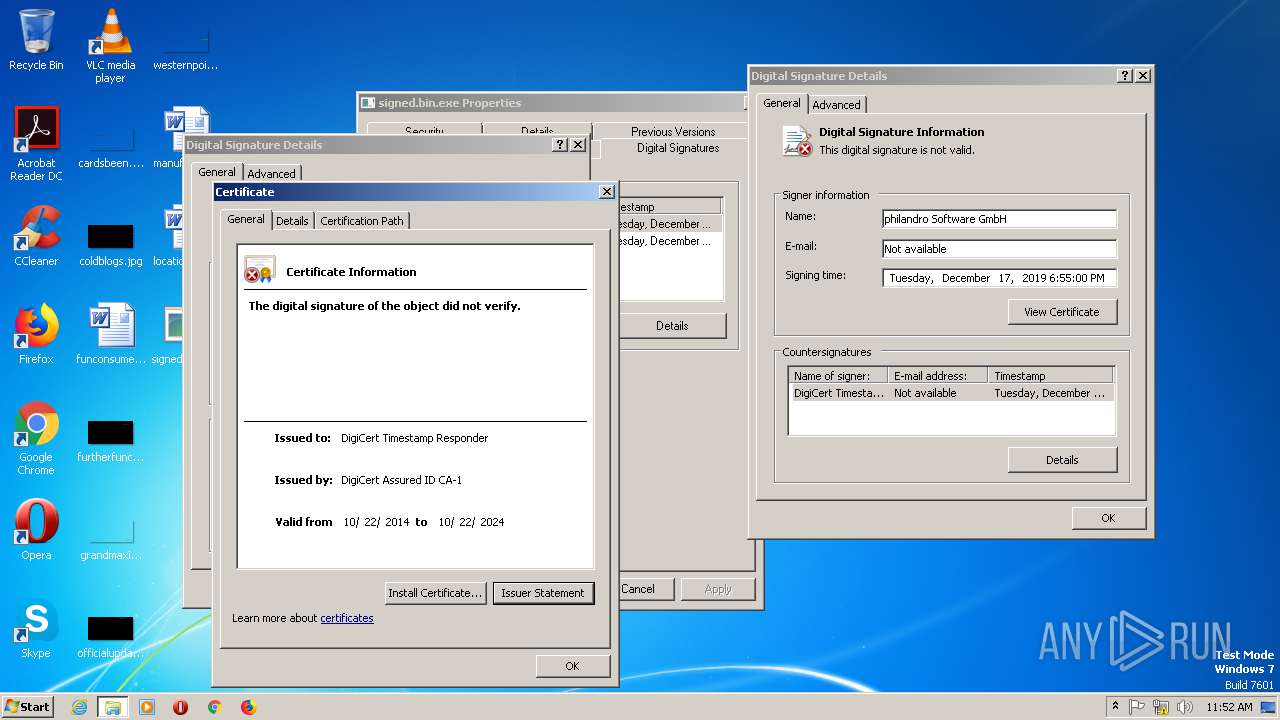
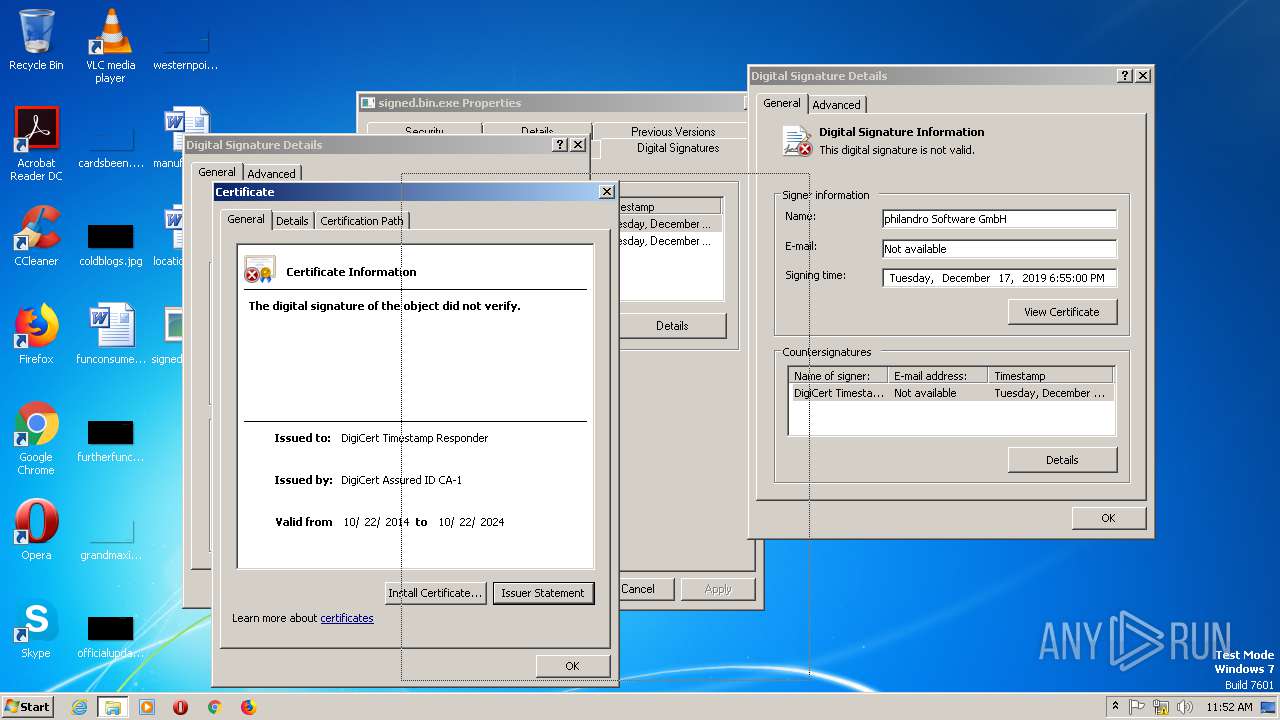
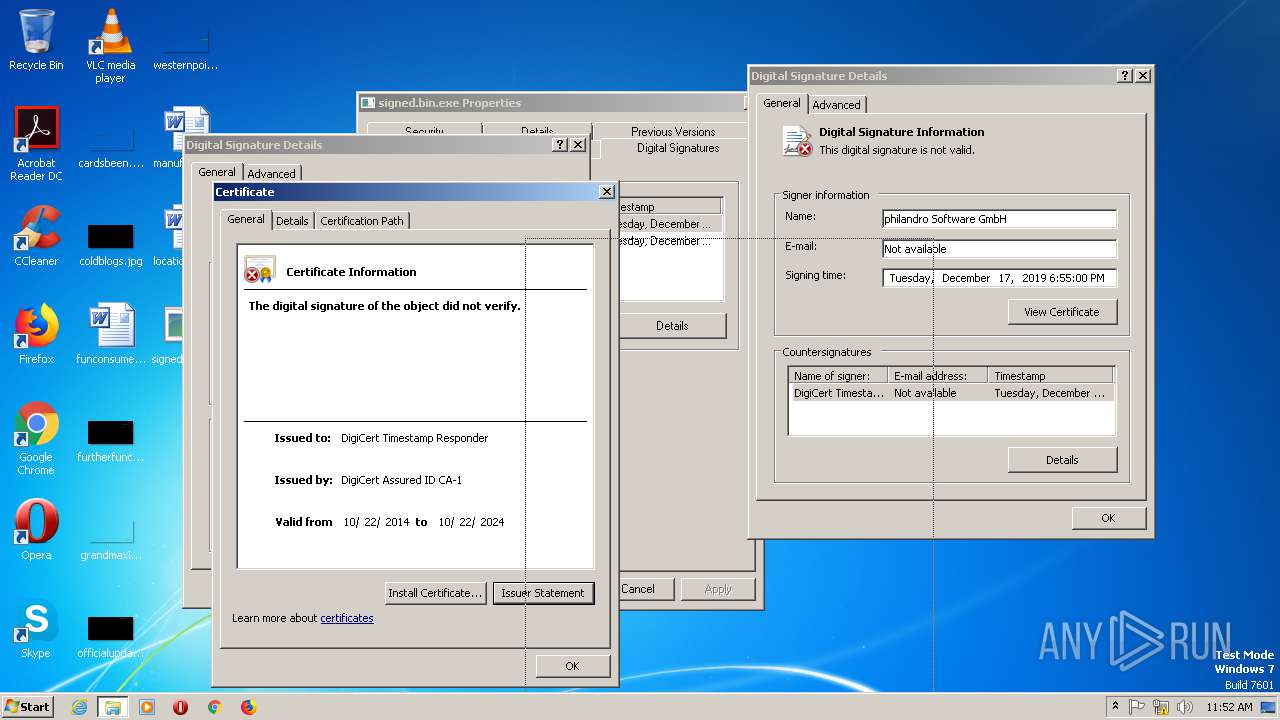
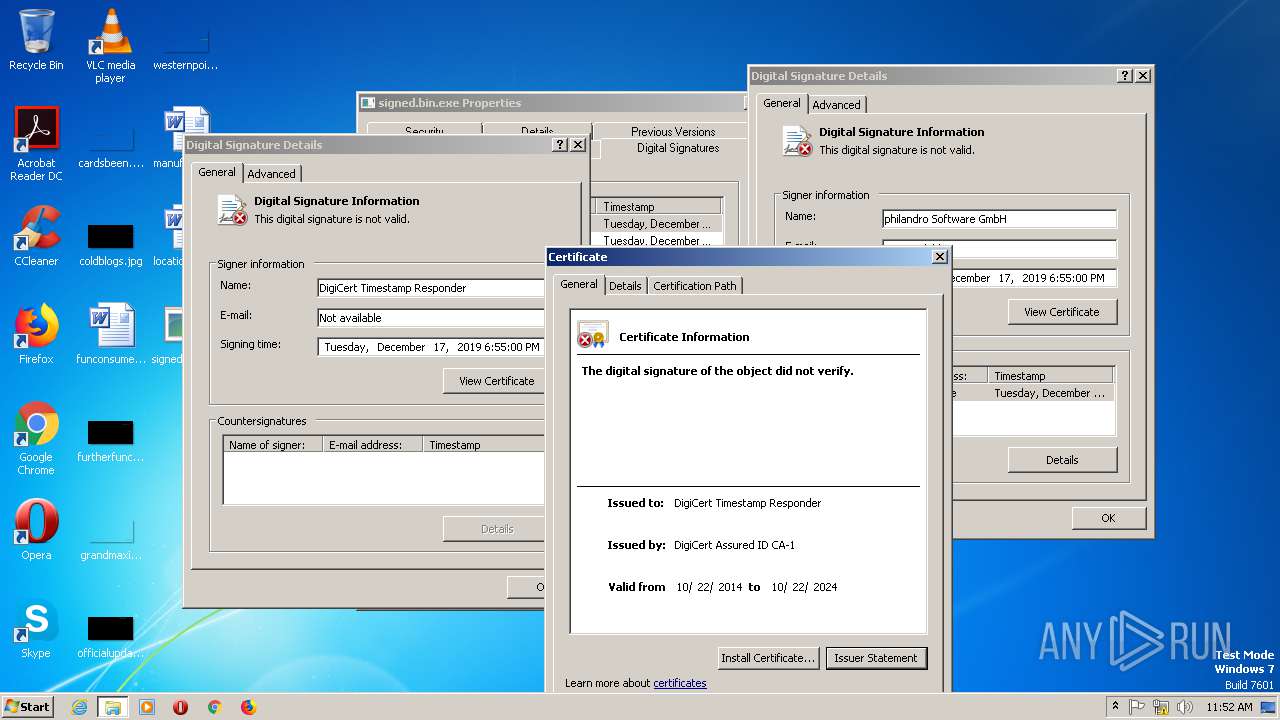
| File name: | signed.bin |
| Full analysis: | https://app.any.run/tasks/6abe17e6-02a3-4d5a-924c-c4a37a55c7c0 |
| Verdict: | Malicious activity |
| Threats: | Predator, the Thief, is an information stealer, meaning that malware steals data from infected systems. This virus can access the camera and spy on victims, steal passwords and login information, and retrieve payment data from cryptocurrency wallets. |
| Analysis date: | February 06, 2020, 11:51:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | DF19A554059A9C0D69DD48DAEF826D88 |
| SHA1: | BC9B6968D29B39357D11BF8E4F3A4EB50E705B32 |
| SHA256: | 83B42646D4983820855CD93CBCCCF9AFD7A235692B82BF3EC4B3365873C8767A |
| SSDEEP: | 12288:z3RMT/VYweCm9TwPm7eQ2VqDfJcr8kTCVqCV:zBuFexAmL2VqDfJcrKV |
MALICIOUS
Application was injected by another process
- svchost.exe (PID: 372)
- SearchIndexer.exe (PID: 1376)
- svchost.exe (PID: 876)
Loads the Task Scheduler COM API
- rundll32.exe (PID: 2792)
Runs injected code in another process
- rundll32.exe (PID: 2792)
Stealing of credential data
- signed.bin.exe (PID: 1620)
Connects to CnC server
- signed.bin.exe (PID: 1620)
PREDATOR was detected
- signed.bin.exe (PID: 1620)
SUSPICIOUS
Executed as Windows Service
- lpremove.exe (PID: 2924)
- rundll32.exe (PID: 2792)
- vssvc.exe (PID: 1468)
Reads the machine GUID from the registry
- rundll32.exe (PID: 2792)
Searches for installed software
- rundll32.exe (PID: 2792)
Creates files in the Windows directory
- rundll32.exe (PID: 2792)
Reads the cookies of Google Chrome
- signed.bin.exe (PID: 1620)
Application launched itself
- signed.bin.exe (PID: 2456)
Creates files in the user directory
- signed.bin.exe (PID: 1620)
Creates files in the program directory
- SearchIndexer.exe (PID: 1376)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 1468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:02:06 12:24:42+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 348160 |
| InitializedDataSize: | 42496 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6600a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.17.0.0 |
| ProductVersionNumber: | 7.17.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Postman |
| CompanyName: | Postman |
| FileDescription: | Postman |
| FileVersion: | 7.17.0.0 |
| InternalName: | ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZNHEIFOGWGHIOWR89TYGWHIRO389TYWHRIOG28TYGQHIOR28TY0GQRIHPYHQIGPRY0GHQIR8TY0HIGQORGQIROBGQUHGBUQGQRUQRUHIBQUHAHOULVBUOGH.exe |
| LegalCopyright: | Copyright © 2019 Postman, Inc. All rights reserved. |
| OriginalFileName: | ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZNHEIFOGWGHIOWR89TYGWHIRO389TYWHRIOG28TYGQHIOR28TY0GQRIHPYHQIGPRY0GHQIR8TY0HIGQORGQIROBGQUHGBUQGQRUQRUHIBQUHAHOULVBUOGH.exe |
| ProductName: | Postman |
| ProductVersion: | 7.17.0.0 |
| AssemblyVersion: | 7.17.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Feb-2020 11:24:42 |
| Comments: | Postman |
| CompanyName: | Postman |
| FileDescription: | Postman |
| FileVersion: | 7.17.0.0 |
| InternalName: | ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZNHEIFOGWGHIOWR89TYGWHIRO389TYWHRIOG28TYGQHIOR28TY0GQRIHPYHQIGPRY0GHQIR8TY0HIGQORGQIROBGQUHGBUQGQRUQRUHIBQUHAHOULVBUOGH.exe |
| LegalCopyright: | Copyright © 2019 Postman, Inc. All rights reserved. |
| OriginalFilename: | ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZNHEIFOGWGHIOWR89TYGWHIRO389TYWHRIOG28TYGQHIOR28TY0GQRIHPYHQIGPRY0GHQIR8TY0HIGQORGQIROBGQUHGBUQGQRUQRUHIBQUHAHOULVBUOGH.exe |
| ProductName: | Postman |
| ProductVersion: | 7.17.0.0 |
| Assembly Version: | 7.17.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 06-Feb-2020 11:24:42 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
\x18<\x161\x18PI<\xe8\x98 | 0x00002000 | 0x000098E8 | 0x00009A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99547 |
.text | 0x0000C000 | 0x00054CF8 | 0x00054E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.96458 |
.rsrc | 0x00062000 | 0x00000810 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.64902 |
.reloc | 0x00064000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0980042 |
0x00066000 | 0x00000010 | 0x00000200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0.122276 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
42
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 876 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1376 | C:\Windows\system32\SearchIndexer.exe /Embedding | C:\Windows\System32\SearchIndexer.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1468 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1620 | "C:\Users\admin\Desktop\signed.bin.exe" | C:\Users\admin\Desktop\signed.bin.exe | signed.bin.exe | ||||||||||||
User: admin Company: Postman Integrity Level: MEDIUM Description: Postman Exit code: 1 Version: 7.17.0.0 Modules
| |||||||||||||||
| 2456 | "C:\Users\admin\Desktop\signed.bin.exe" | C:\Users\admin\Desktop\signed.bin.exe | — | explorer.exe | |||||||||||
User: admin Company: Postman Integrity Level: MEDIUM Description: Postman Exit code: 0 Version: 7.17.0.0 Modules
| |||||||||||||||
| 2792 | C:\Windows\system32\rundll32.exe /d srrstr.dll,ExecuteScheduledSPPCreation | C:\Windows\system32\rundll32.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2924 | C:\Windows\system32\lpremove.exe | C:\Windows\system32\lpremove.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: MUI Language pack cleanup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
471
Read events
255
Write events
216
Delete events
0
Modification events
| (PID) Process: | (372) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {00E51A5A-6FF0-414A-B358-C7EB6484BAF5} |
Value: 525400363EFF | |||
| (PID) Process: | (2924) lpremove.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MUI\Settings |
| Operation: | write | Name: | NextSQMCollection |
Value: C06363B89C23D601 | |||
| (PID) Process: | (2792) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000CC5D4BCFE3DCD501E80A0000700B0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2792) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000000631C0CFE3DCD501E80A0000700B0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2792) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000006EBAC9CFE3DCD501E80A0000700B0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2792) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000C81CCCCFE3DCD501E80A0000700B0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2792) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000C81CCCCFE3DCD501E80A0000700B0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2792) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000C81CCCCFE3DCD501E80A0000700B0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2792) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000C81CCCCFE3DCD501E80A0000700B0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2792) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000227FCECFE3DCD501E80A0000700B0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
6
Text files
7
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2792 | rundll32.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 372 | svchost.exe | C:\Windows\System32\catroot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\catdb | — | |
MD5:— | SHA256:— | |||
| 372 | svchost.exe | C:\Windows\system32\CatRoot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\catdb | — | |
MD5:— | SHA256:— | |||
| 372 | svchost.exe | C:\Windows\System32\catroot2\edb.log | — | |
MD5:— | SHA256:— | |||
| 372 | svchost.exe | C:\Windows\system32\CatRoot2\edb.log | — | |
MD5:— | SHA256:— | |||
| 2792 | rundll32.exe | C:\System Volume Information\SPP\SppGroupCache\Temp_{C86F5967-FB3B-4527-B8DB-7B4F47A608D5}_DriverPackageInfo | — | |
MD5:— | SHA256:— | |||
| 2792 | rundll32.exe | Volume{4b10993c-02aa-11e8-b4df-806e6f6e6963}\System Volume Information\SPP\SppGroupCache\{C86F5967-FB3B-4527-B8DB-7B4F47A608D5}_DriverPackageInfo | — | |
MD5:— | SHA256:— | |||
| 2792 | rundll32.exe | C:\System Volume Information\SPP\SppCbsHiveStore\{cd42efe1-f6f1-427c-b004-033192c625a4}{34DB2682-78C2-4033-B3C0-FD1A536362EE} | — | |
MD5:— | SHA256:— | |||
| 2792 | rundll32.exe | C:\System Volume Information\SPP\SppCbsHiveStore\{cd42efe1-f6f1-427c-b004-033192c625a4}{CA1E8372-8823-4E81-B773-879EE19CB886} | — | |
MD5:— | SHA256:— | |||
| 2792 | rundll32.exe | C:\System Volume Information\SPP\SppCbsHiveStore\{cd42efe1-f6f1-427c-b004-033192c625a4}{12D03905-B33E-453B-95D0-DD947FA22C45} | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
1
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1620 | signed.bin.exe | GET | 200 | 81.177.140.34:80 | http://nikitakoteqka1.myjino.ru/api/info.get | RU | text | 72 b | malicious |
1620 | signed.bin.exe | POST | 200 | 81.177.140.34:80 | http://nikitakoteqka1.myjino.ru/api/gate.get?p1=1&p2=14&p3=0&p4=0&p5=0&p6=0&p7=0 | RU | binary | 1 b | malicious |
1620 | signed.bin.exe | GET | 200 | 81.177.140.34:80 | http://nikitakoteqka1.myjino.ru/api/download.get | RU | binary | 1 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1620 | signed.bin.exe | 81.177.140.34:80 | nikitakoteqka1.myjino.ru | JSC RTComm.RU | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nikitakoteqka1.myjino.ru |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1620 | signed.bin.exe | A Network Trojan was detected | STEALER [PTsecurity] Predator |
2 ETPRO signatures available at the full report