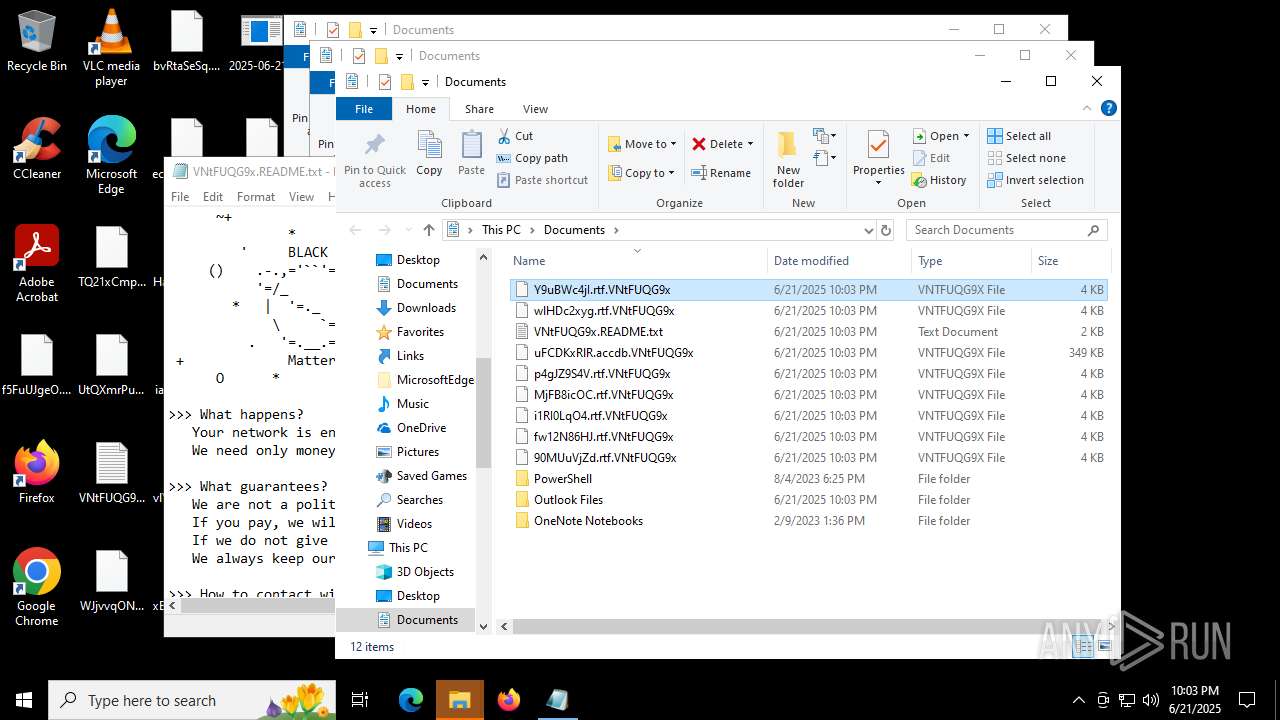
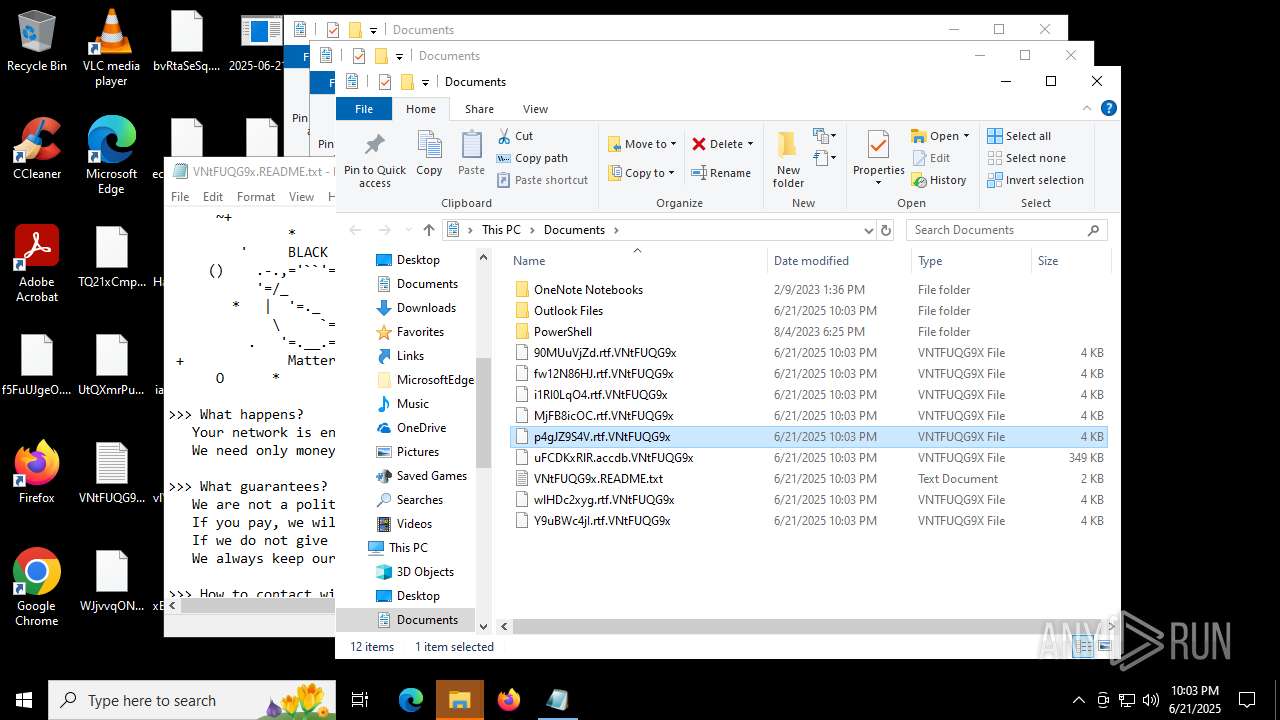
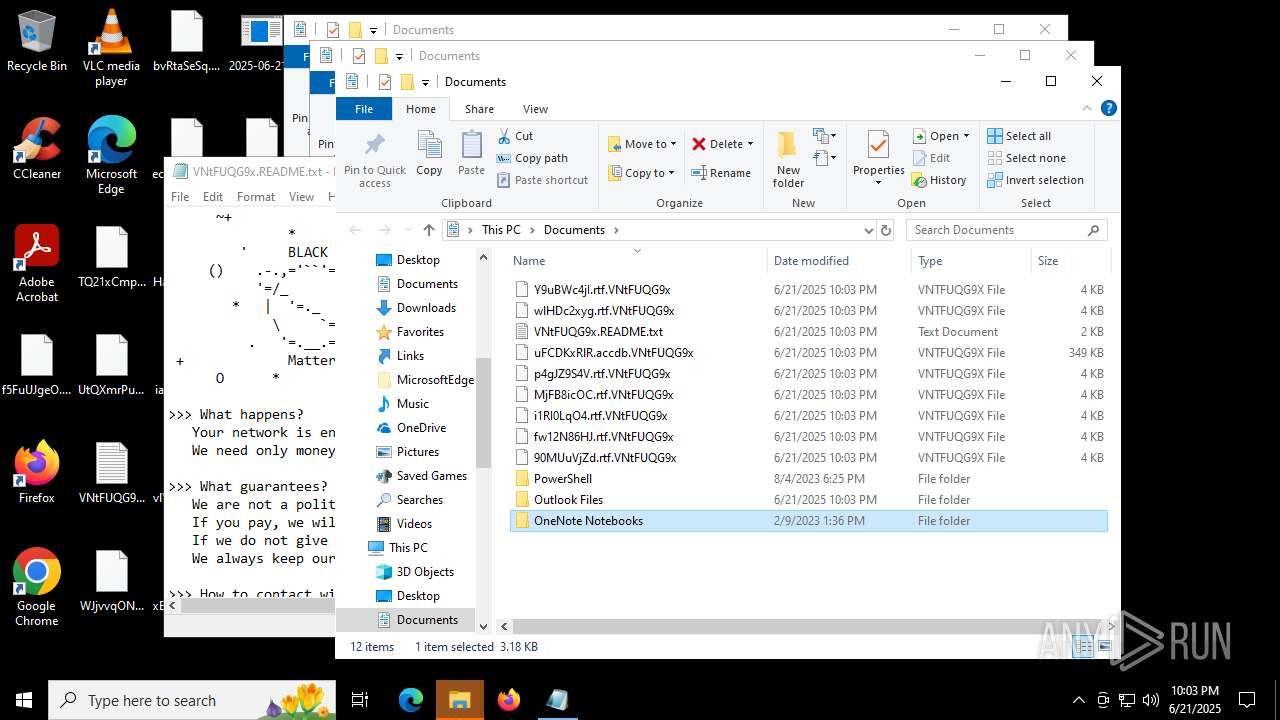
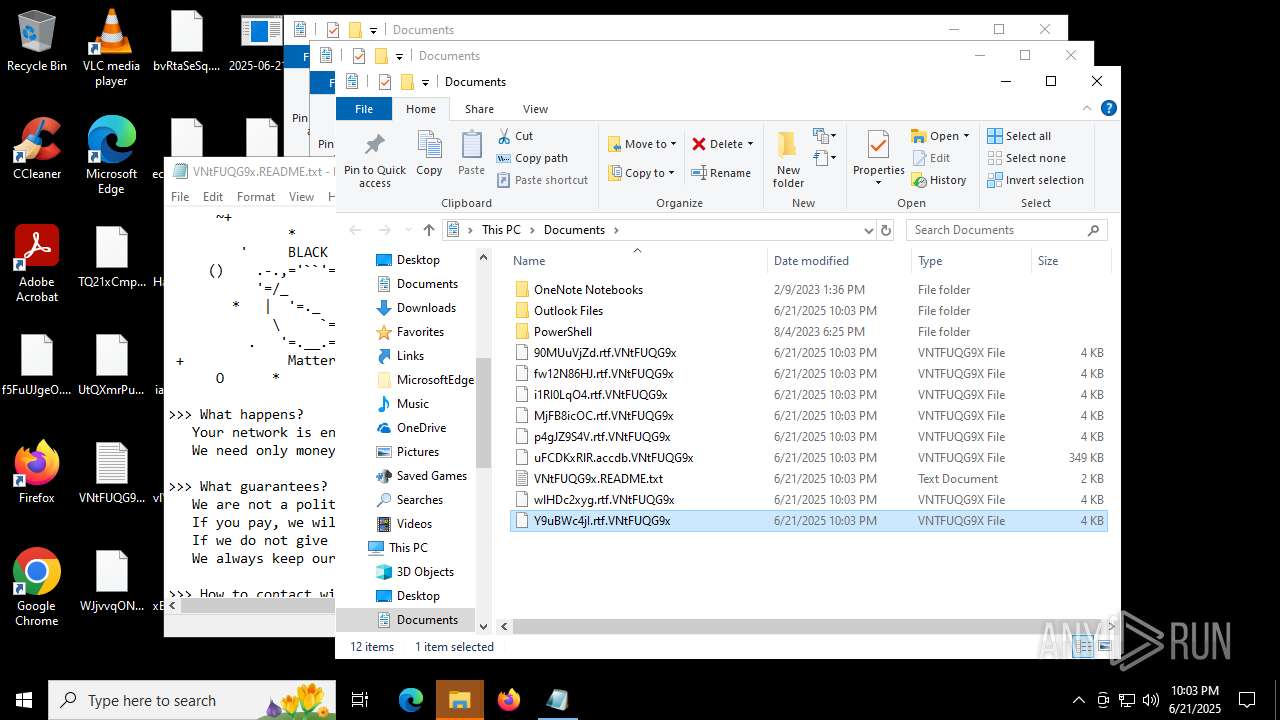
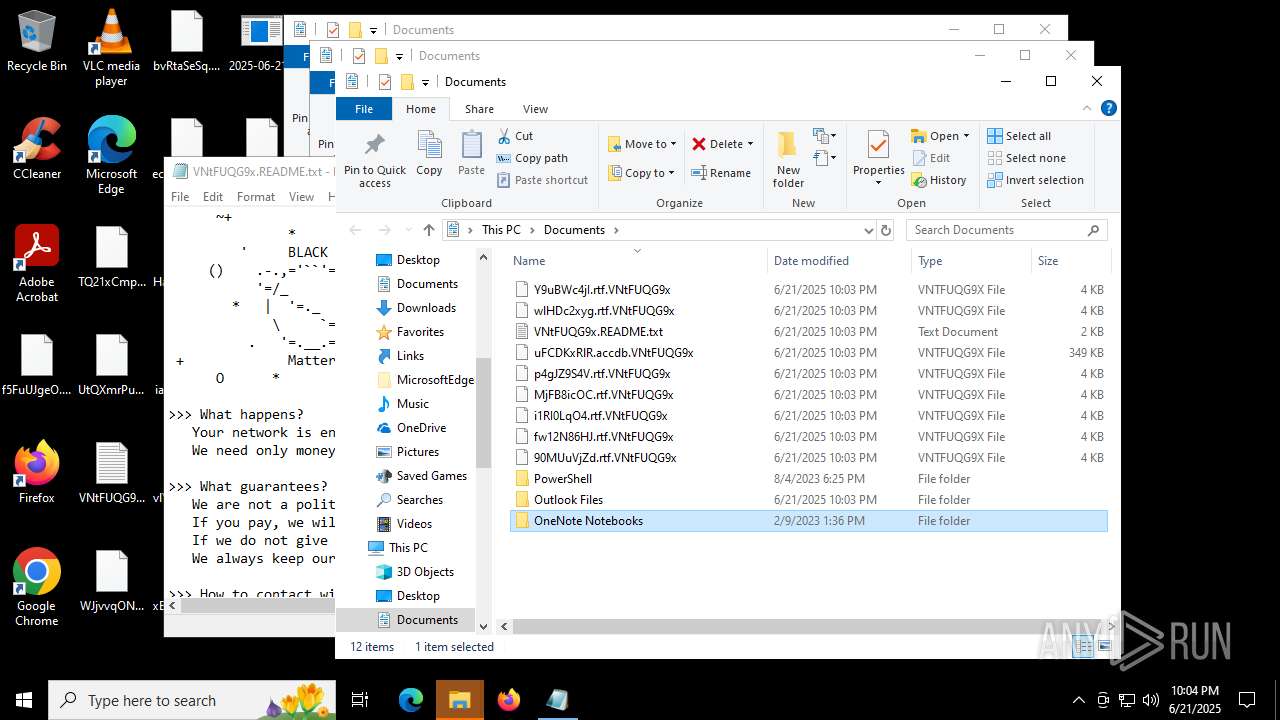
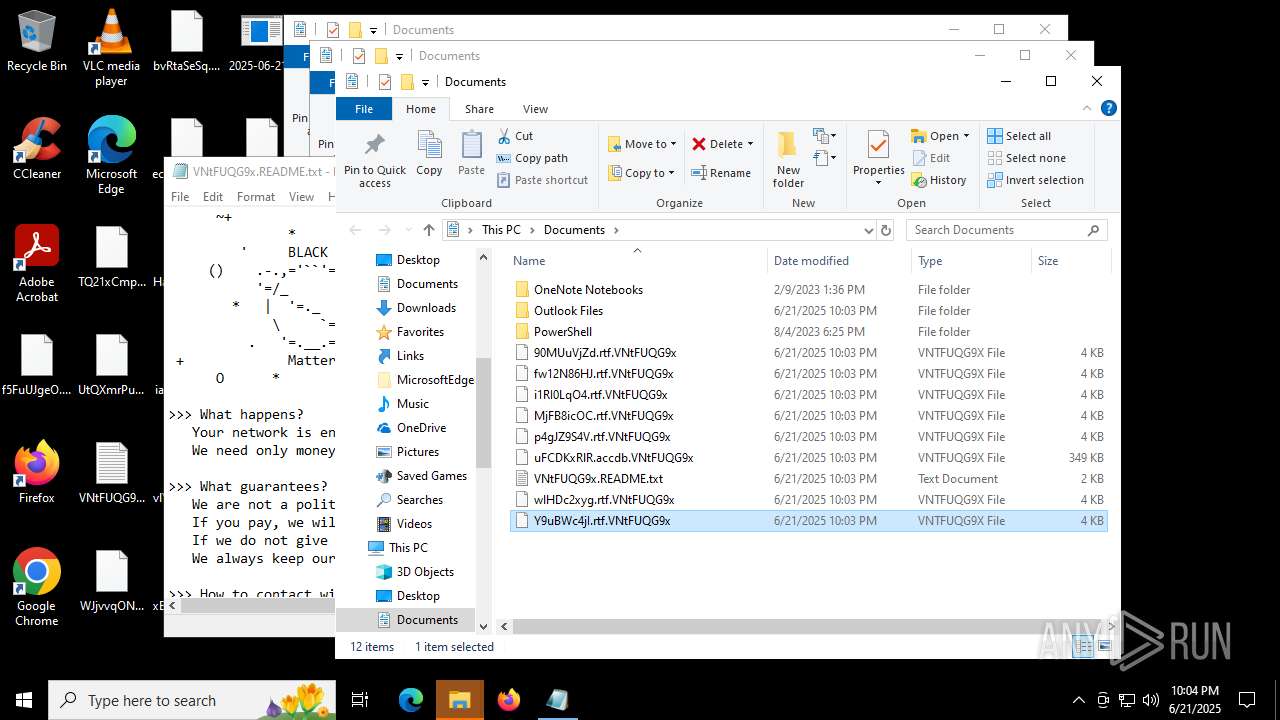
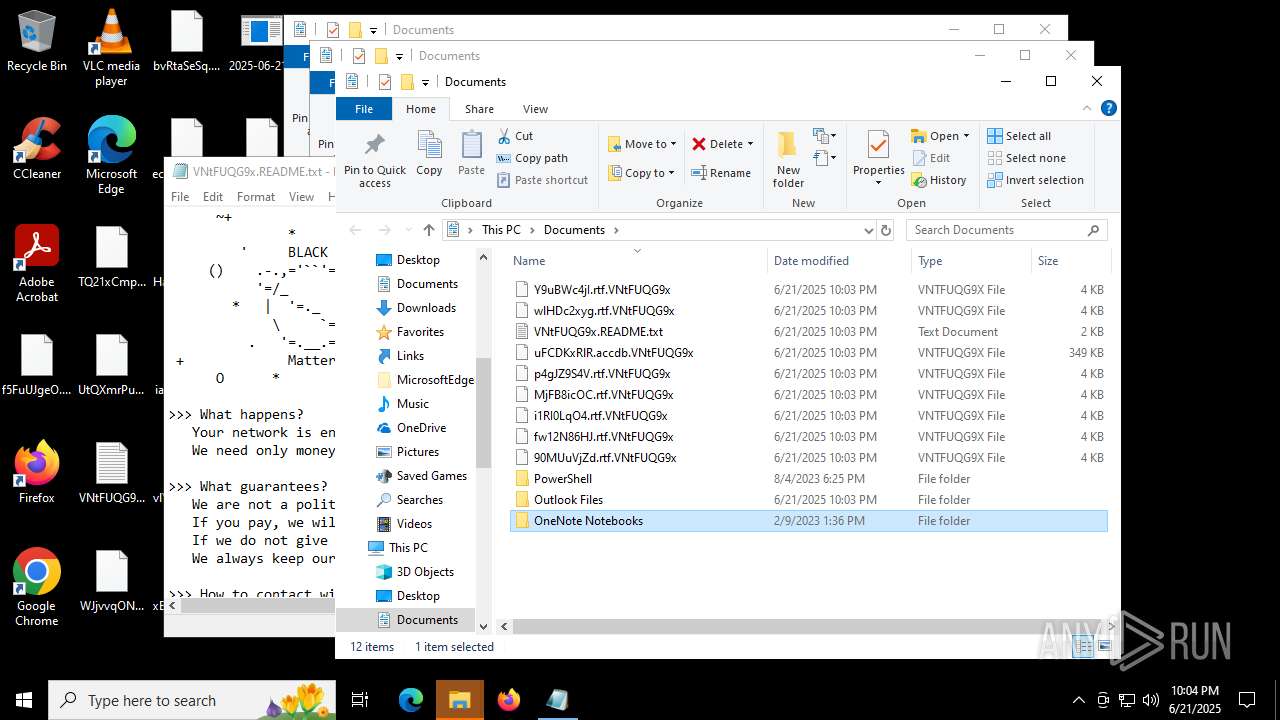
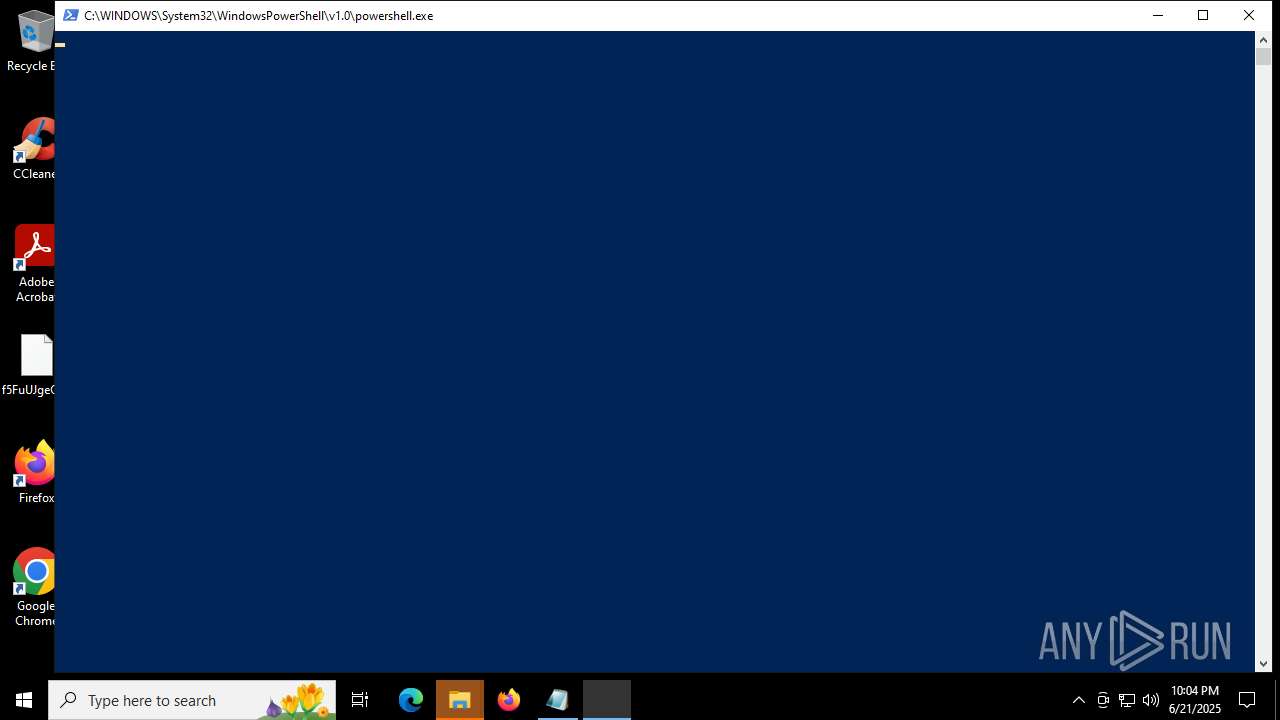
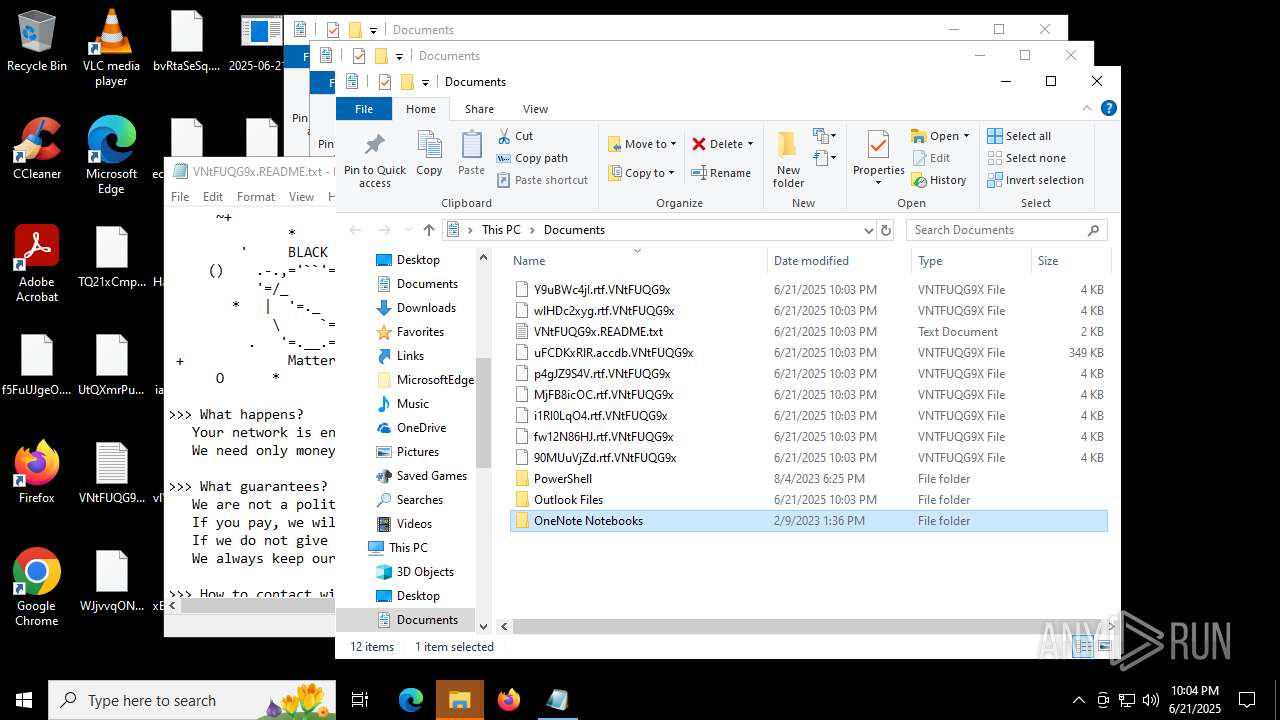
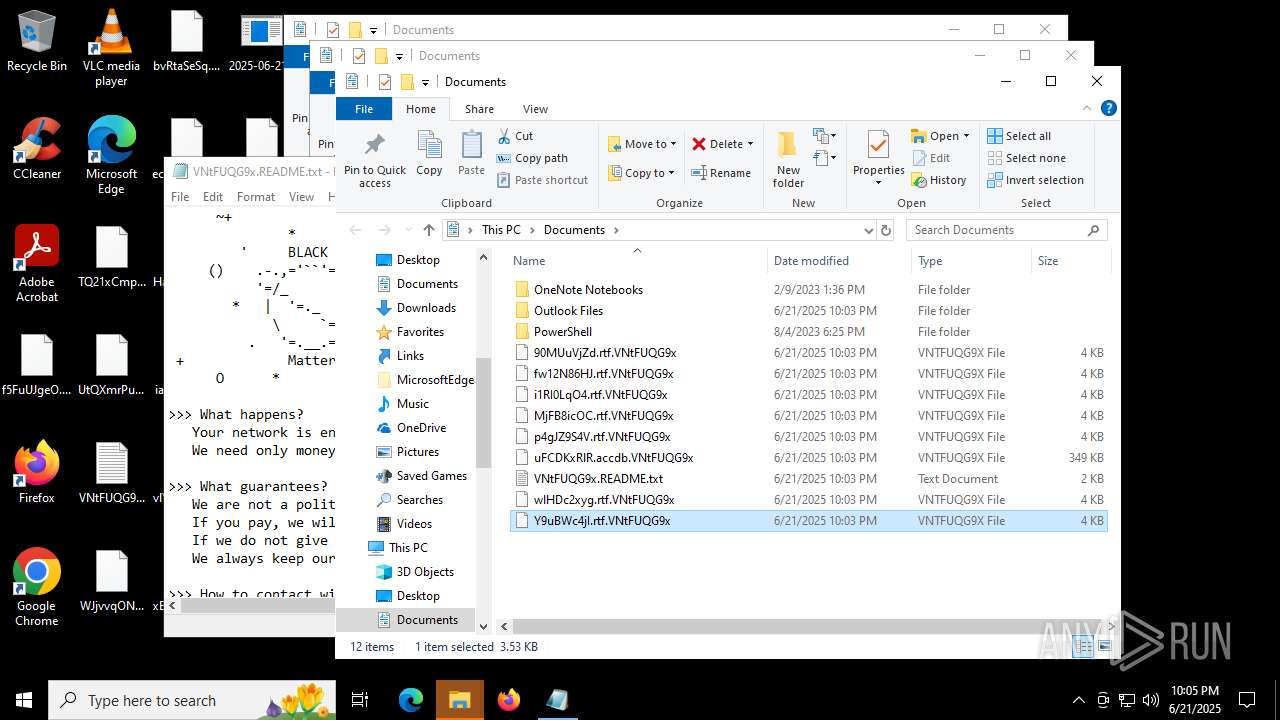
| File name: | 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry |
| Full analysis: | https://app.any.run/tasks/12f7db18-e408-4366-87c4-98d144fa3068 |
| Verdict: | Malicious activity |
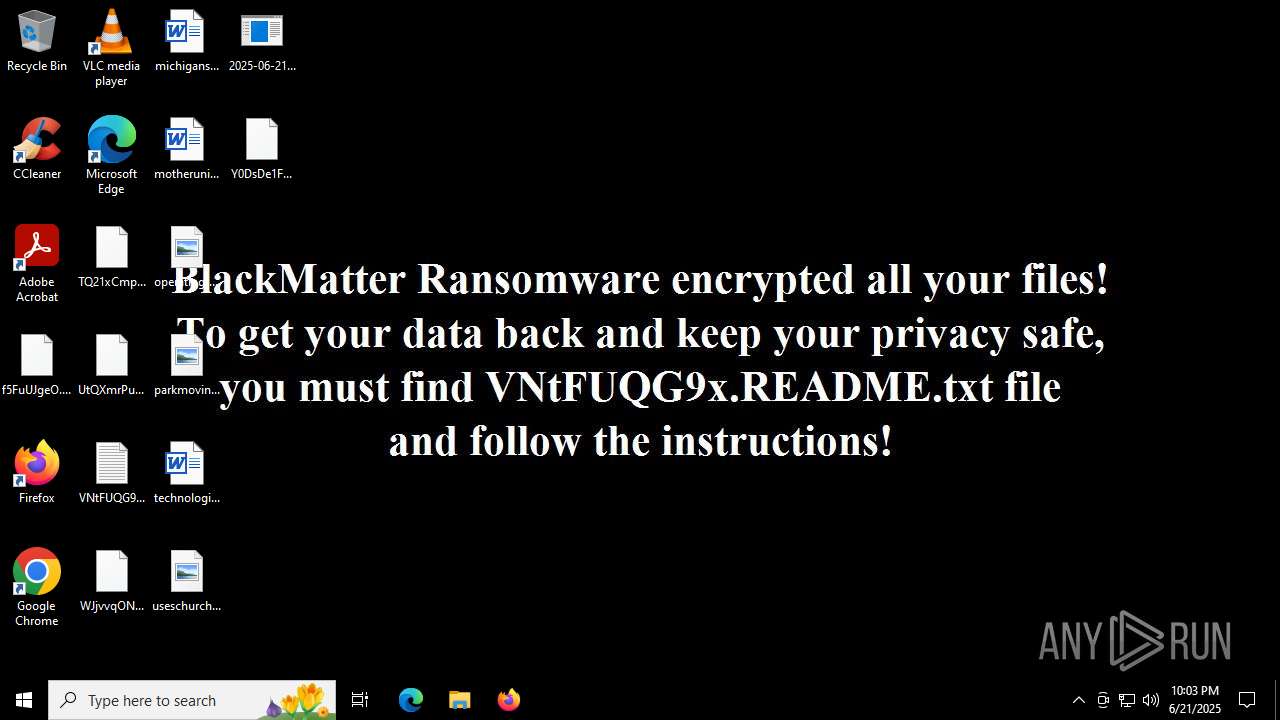
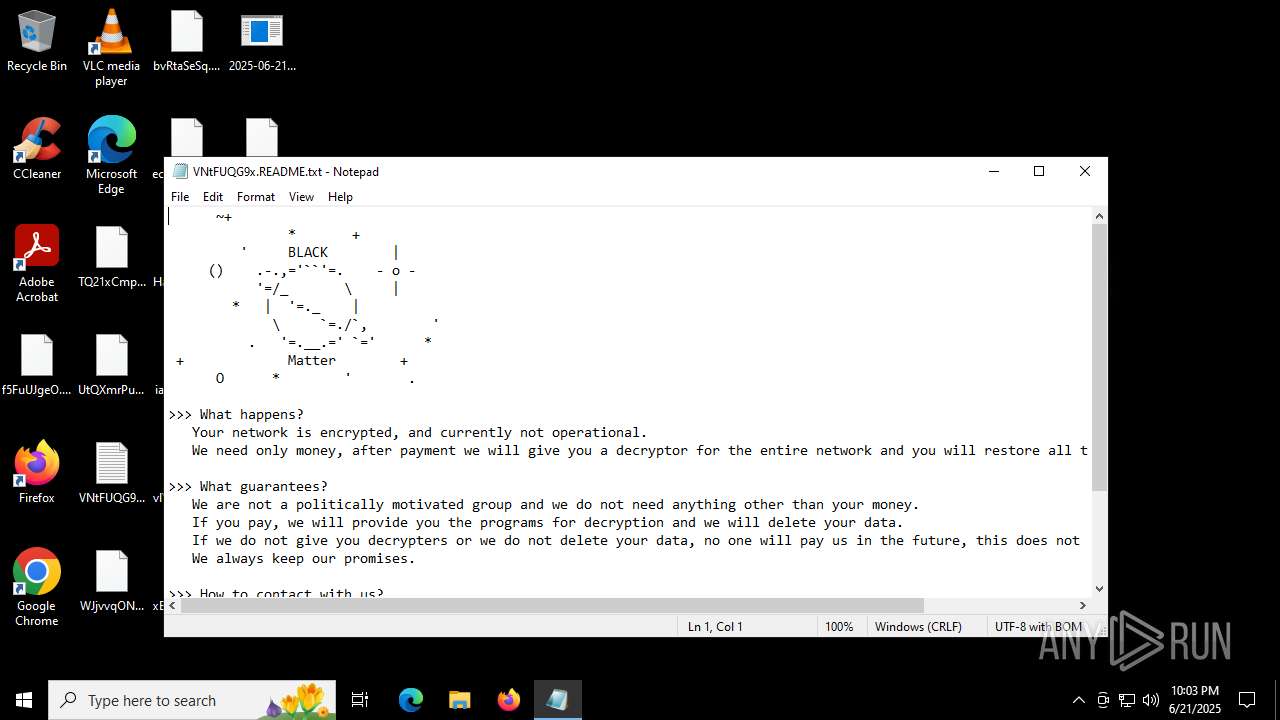
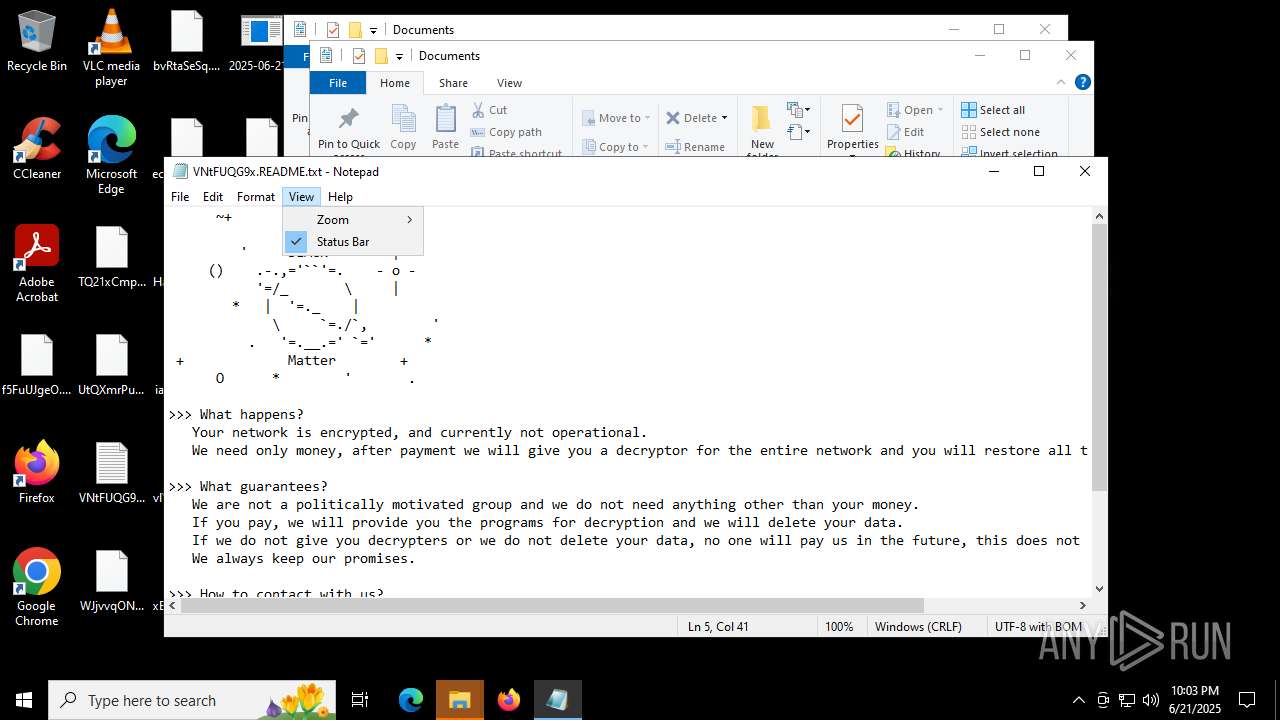
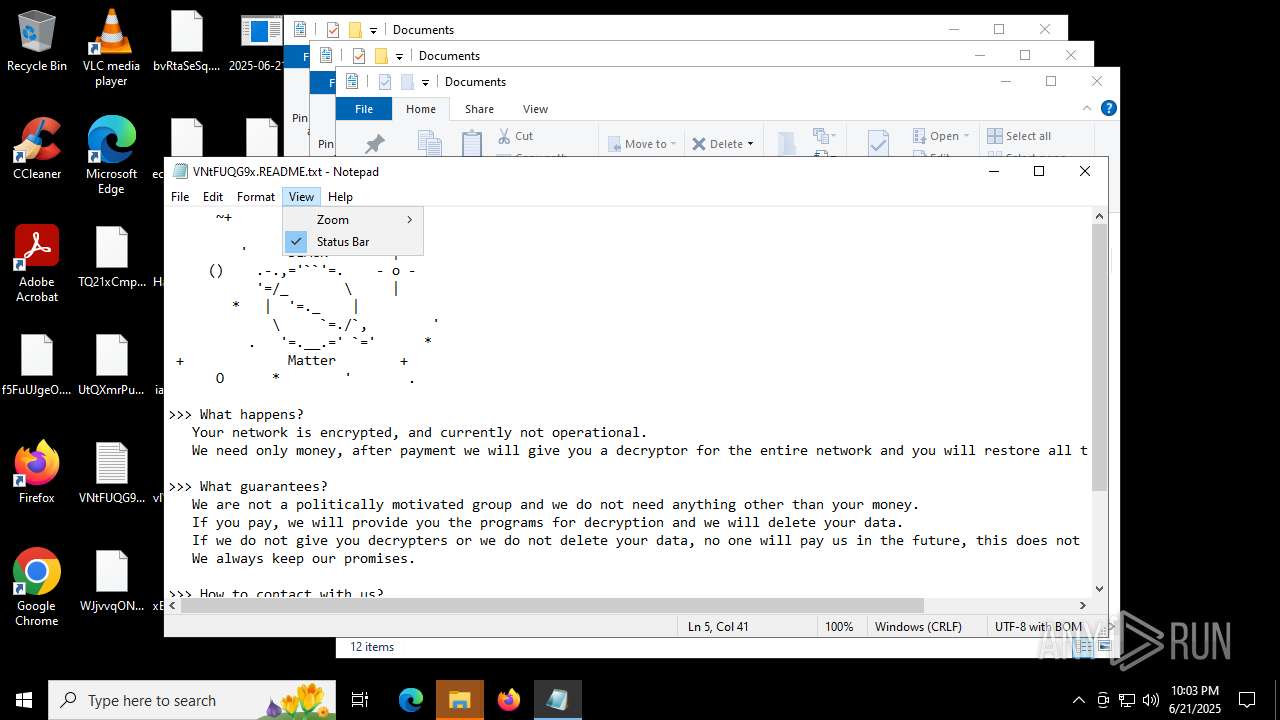
| Threats: | BlackMatter is a ransomware strain operating as a Ransomware-as-a-Service (RaaS), designed to encrypt files, remove recovery options, and extort victims across critical industries. Emerging in 2021, it quickly became a major concern due to its ability to evade defenses, spread across networks, and cause large-scale operational disruption, forcing security teams to act against a highly destructive and persistent threat. |
| Analysis date: | June 21, 2025, 22:02:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 65538E16F1090CFC81C5465A2185FA41 |
| SHA1: | C8C738B726021638C298ED5E93BF720CBBF03399 |
| SHA256: | 82AF319F72C145EC6FF713C64F13307C2A7C098B534F15D59AD0636A1455DD1F |
| SSDEEP: | 1536:l1FO8q31rzaGSX/GrfIjQgP111BoLfiYmZx5AG8Sf9YMXiQeJn:l1FO8q31rzaGSvMqWSf9YMXiZJn |
MALICIOUS
BLACKMATTER mutex has been found
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 1080)
Uses Task Scheduler to autorun other applications
- svchost.exe (PID: 1080)
Deletes shadow copies
- svchost.exe (PID: 1080)
- cmd.exe (PID: 6348)
- cmd.exe (PID: 4816)
Changes the autorun value in the registry
- svchost.exe (PID: 1080)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 5620)
- svchost.exe (PID: 1080)
Bypass User Account Control (Modify registry)
- svchost.exe (PID: 1080)
Starts NET.EXE for service management
- svchost.exe (PID: 1080)
- net.exe (PID: 4544)
- net.exe (PID: 4104)
- net.exe (PID: 6356)
- net.exe (PID: 4860)
- net.exe (PID: 4808)
- net.exe (PID: 6336)
- net.exe (PID: 6960)
- net.exe (PID: 1568)
- net.exe (PID: 5644)
- net.exe (PID: 2192)
- net.exe (PID: 7056)
- net.exe (PID: 6428)
- net.exe (PID: 5644)
- net.exe (PID: 4708)
- net.exe (PID: 5172)
- net.exe (PID: 5252)
- net.exe (PID: 7020)
- net.exe (PID: 3800)
- net.exe (PID: 1896)
- net.exe (PID: 7080)
- net.exe (PID: 3924)
- net.exe (PID: 4760)
- net.exe (PID: 6104)
- net.exe (PID: 1484)
- net.exe (PID: 2596)
- net.exe (PID: 4764)
- net.exe (PID: 1812)
- net.exe (PID: 4456)
- net.exe (PID: 7040)
- net.exe (PID: 6620)
- net.exe (PID: 4188)
- net.exe (PID: 1964)
- net.exe (PID: 6488)
- net.exe (PID: 6236)
- net.exe (PID: 5644)
- net.exe (PID: 1212)
- net.exe (PID: 6348)
- net.exe (PID: 6620)
- net.exe (PID: 1644)
- net.exe (PID: 6348)
- net.exe (PID: 5764)
- net.exe (PID: 6680)
- net.exe (PID: 4188)
- net.exe (PID: 6980)
- net.exe (PID: 6488)
- net.exe (PID: 1816)
- net.exe (PID: 6292)
- net.exe (PID: 2460)
- net.exe (PID: 2368)
- net.exe (PID: 4800)
- net.exe (PID: 2124)
- net.exe (PID: 3668)
- net.exe (PID: 3668)
- net.exe (PID: 4960)
- net.exe (PID: 768)
- net.exe (PID: 4412)
- net.exe (PID: 984)
- net.exe (PID: 1896)
- net.exe (PID: 3788)
- net.exe (PID: 2512)
- net.exe (PID: 5020)
- net.exe (PID: 1204)
- net.exe (PID: 3652)
- net.exe (PID: 6892)
- net.exe (PID: 6152)
- net.exe (PID: 1132)
- net.exe (PID: 5008)
- net.exe (PID: 2604)
- net.exe (PID: 1512)
- net.exe (PID: 3620)
- net.exe (PID: 6140)
- net.exe (PID: 5552)
- net.exe (PID: 756)
- net.exe (PID: 1200)
- net.exe (PID: 1440)
- net.exe (PID: 4828)
- net.exe (PID: 6756)
- net.exe (PID: 2836)
- net.exe (PID: 2276)
- net.exe (PID: 2664)
- net.exe (PID: 6656)
- net.exe (PID: 6400)
- net.exe (PID: 2760)
- net.exe (PID: 4528)
- net.exe (PID: 4380)
- net.exe (PID: 3388)
- net.exe (PID: 6980)
- net.exe (PID: 6704)
- net.exe (PID: 6472)
- net.exe (PID: 5600)
- net.exe (PID: 2228)
- net.exe (PID: 6320)
- net.exe (PID: 1560)
- net.exe (PID: 5552)
- net.exe (PID: 6836)
- net.exe (PID: 6680)
- net.exe (PID: 7048)
- net.exe (PID: 1096)
- net.exe (PID: 6388)
- net.exe (PID: 1096)
- net.exe (PID: 6012)
- net.exe (PID: 3112)
- net.exe (PID: 6336)
- net.exe (PID: 4312)
- net.exe (PID: 6652)
- net.exe (PID: 1508)
- net.exe (PID: 5824)
- net.exe (PID: 5252)
- net.exe (PID: 4576)
- net.exe (PID: 1096)
- net.exe (PID: 6380)
- net.exe (PID: 5116)
- net.exe (PID: 1880)
- net.exe (PID: 4040)
- net.exe (PID: 7072)
- net.exe (PID: 3732)
- net.exe (PID: 3644)
- net.exe (PID: 4680)
- net.exe (PID: 5552)
- net.exe (PID: 4040)
- net.exe (PID: 2632)
- net.exe (PID: 5716)
- net.exe (PID: 1880)
- net.exe (PID: 3780)
- net.exe (PID: 3752)
- net.exe (PID: 6420)
- net.exe (PID: 3884)
- net.exe (PID: 6956)
- net.exe (PID: 3788)
- net.exe (PID: 3752)
- net.exe (PID: 4324)
- net.exe (PID: 4828)
- net.exe (PID: 6336)
- net.exe (PID: 2760)
- net.exe (PID: 4560)
- net.exe (PID: 6472)
- net.exe (PID: 4324)
- net.exe (PID: 6472)
Starts NET.EXE to view/change shared resources
- svchost.exe (PID: 1080)
- net.exe (PID: 1512)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 1080)
Changes powershell execution policy (Bypass)
- svchost.exe (PID: 1080)
Bypass execution policy to execute commands
- powershell.exe (PID: 6256)
- powershell.exe (PID: 6104)
Starts SC.EXE for service management
- svchost.exe (PID: 1080)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 2492)
SUSPICIOUS
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2492)
- cmd.exe (PID: 7048)
- cmd.exe (PID: 4664)
- cmd.exe (PID: 4768)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 6224)
- cmd.exe (PID: 4808)
- cmd.exe (PID: 420)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 4892)
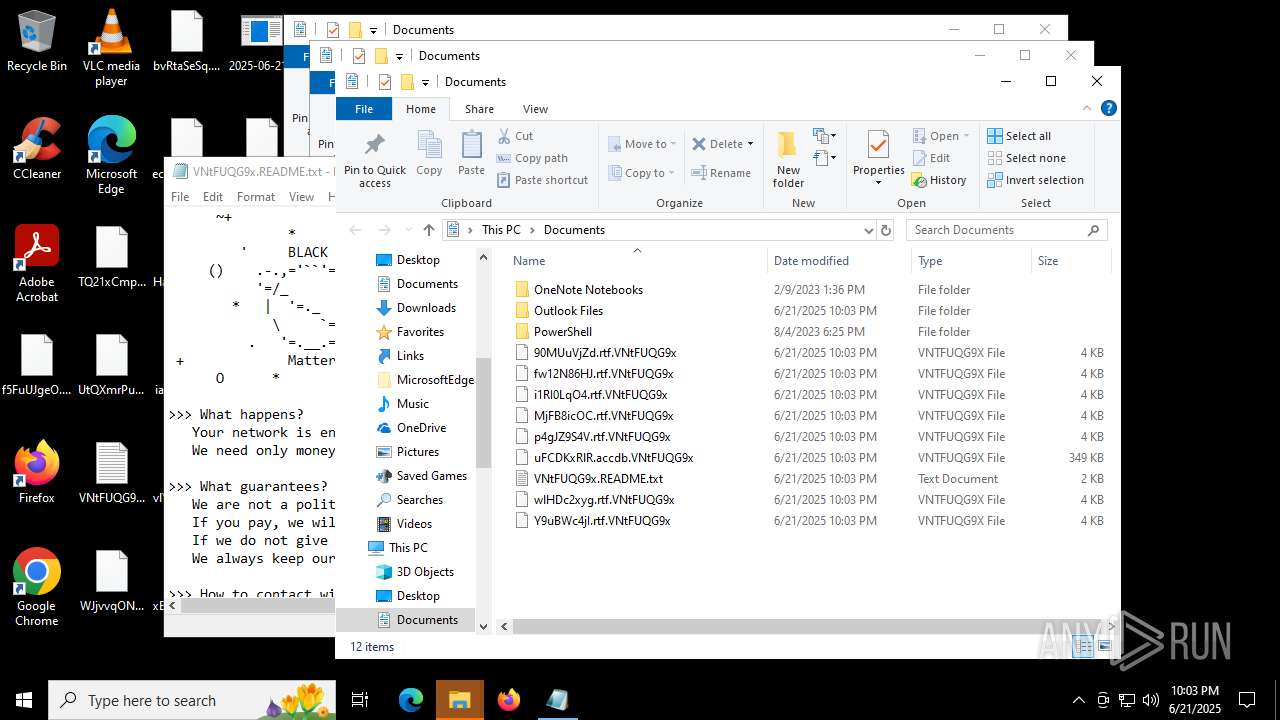
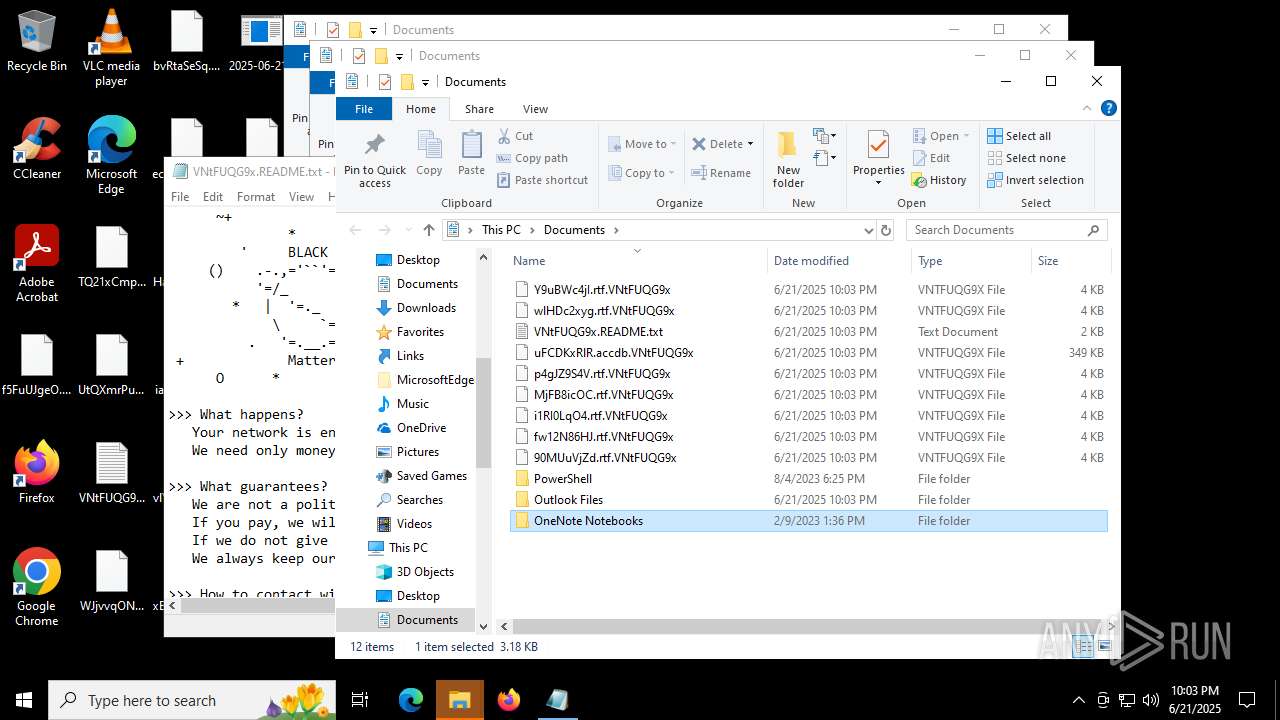
Executable content was dropped or overwritten
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 1080)
The process creates files with name similar to system file names
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
Reads security settings of Internet Explorer
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 1080)
Reads the date of Windows installation
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 1080)
Starts itself from another location
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
Starts CMD.EXE for commands execution
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 1080)
- svchost.exe (PID: 5744)
Executing commands from a ".bat" file
- svchost.exe (PID: 1080)
- svchost.exe (PID: 5744)
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
Changes default file association
- svchost.exe (PID: 1080)
Starts SC.EXE for service management
- svchost.exe (PID: 1080)
Windows service management via SC.EXE
- sc.exe (PID: 1200)
- sc.exe (PID: 856)
- sc.exe (PID: 760)
- sc.exe (PID: 1508)
- sc.exe (PID: 3836)
- sc.exe (PID: 3624)
- sc.exe (PID: 7072)
- sc.exe (PID: 420)
- sc.exe (PID: 4648)
- sc.exe (PID: 6368)
- sc.exe (PID: 3520)
- sc.exe (PID: 3572)
- sc.exe (PID: 4236)
- sc.exe (PID: 3672)
- sc.exe (PID: 3564)
- sc.exe (PID: 4892)
- sc.exe (PID: 3480)
- sc.exe (PID: 3788)
- sc.exe (PID: 6016)
- sc.exe (PID: 6504)
- sc.exe (PID: 2228)
- sc.exe (PID: 4816)
- sc.exe (PID: 1560)
- sc.exe (PID: 6128)
- sc.exe (PID: 6960)
- sc.exe (PID: 1984)
- sc.exe (PID: 1496)
- sc.exe (PID: 6896)
- sc.exe (PID: 6160)
- sc.exe (PID: 2216)
- sc.exe (PID: 1568)
- sc.exe (PID: 1380)
- sc.exe (PID: 1136)
- sc.exe (PID: 5140)
- sc.exe (PID: 5552)
- sc.exe (PID: 1328)
- sc.exe (PID: 2212)
- sc.exe (PID: 3956)
- sc.exe (PID: 5184)
- sc.exe (PID: 2632)
- sc.exe (PID: 4708)
- sc.exe (PID: 6124)
- sc.exe (PID: 5808)
- sc.exe (PID: 6336)
- sc.exe (PID: 2280)
- sc.exe (PID: 5168)
- sc.exe (PID: 4012)
- sc.exe (PID: 6400)
- sc.exe (PID: 3504)
- sc.exe (PID: 1028)
- sc.exe (PID: 3948)
- sc.exe (PID: 3588)
- sc.exe (PID: 1336)
- sc.exe (PID: 3768)
- sc.exe (PID: 6492)
- sc.exe (PID: 6228)
- sc.exe (PID: 7104)
- sc.exe (PID: 2760)
- sc.exe (PID: 984)
- sc.exe (PID: 6796)
- sc.exe (PID: 6256)
- sc.exe (PID: 5600)
- sc.exe (PID: 5564)
- sc.exe (PID: 6472)
- sc.exe (PID: 4768)
- sc.exe (PID: 864)
- sc.exe (PID: 3652)
- sc.exe (PID: 5824)
- sc.exe (PID: 5372)
- sc.exe (PID: 6612)
- sc.exe (PID: 5928)
- sc.exe (PID: 4680)
- sc.exe (PID: 5012)
- sc.exe (PID: 3780)
- sc.exe (PID: 1700)
- sc.exe (PID: 5692)
- sc.exe (PID: 2120)
- sc.exe (PID: 2804)
- sc.exe (PID: 6380)
- sc.exe (PID: 3884)
- sc.exe (PID: 6676)
- sc.exe (PID: 5124)
- sc.exe (PID: 2520)
- sc.exe (PID: 6304)
- sc.exe (PID: 6488)
- sc.exe (PID: 2428)
- sc.exe (PID: 4412)
- sc.exe (PID: 3556)
- sc.exe (PID: 6776)
- sc.exe (PID: 5720)
- sc.exe (PID: 4764)
- sc.exe (PID: 1728)
- sc.exe (PID: 6672)
- sc.exe (PID: 4188)
- sc.exe (PID: 1484)
- sc.exe (PID: 6292)
- sc.exe (PID: 4312)
- sc.exe (PID: 3740)
- sc.exe (PID: 4760)
- sc.exe (PID: 6348)
- sc.exe (PID: 3092)
- sc.exe (PID: 6840)
- sc.exe (PID: 6140)
- sc.exe (PID: 6356)
- sc.exe (PID: 6164)
- sc.exe (PID: 4864)
- sc.exe (PID: 1352)
- sc.exe (PID: 4156)
- sc.exe (PID: 2596)
- sc.exe (PID: 4172)
- sc.exe (PID: 3480)
- sc.exe (PID: 3976)
- sc.exe (PID: 1028)
- sc.exe (PID: 1132)
- sc.exe (PID: 6868)
- sc.exe (PID: 4892)
- sc.exe (PID: 1700)
- sc.exe (PID: 7020)
- sc.exe (PID: 2468)
- sc.exe (PID: 4760)
- sc.exe (PID: 5720)
- sc.exe (PID: 5124)
- sc.exe (PID: 3556)
- sc.exe (PID: 5952)
- sc.exe (PID: 6228)
- sc.exe (PID: 6636)
- sc.exe (PID: 3980)
- sc.exe (PID: 5476)
- sc.exe (PID: 1760)
- sc.exe (PID: 6676)
- sc.exe (PID: 7060)
- sc.exe (PID: 2520)
- sc.exe (PID: 3520)
- sc.exe (PID: 3504)
- sc.exe (PID: 2864)
- sc.exe (PID: 768)
- sc.exe (PID: 6428)
- sc.exe (PID: 1812)
- sc.exe (PID: 5020)
- sc.exe (PID: 6748)
- sc.exe (PID: 1728)
- sc.exe (PID: 3460)
- sc.exe (PID: 1324)
- sc.exe (PID: 6700)
- sc.exe (PID: 3148)
- sc.exe (PID: 5184)
- sc.exe (PID: 6960)
- sc.exe (PID: 1484)
- sc.exe (PID: 3092)
- sc.exe (PID: 1380)
- sc.exe (PID: 4120)
- sc.exe (PID: 6292)
- sc.exe (PID: 6128)
- sc.exe (PID: 4412)
- sc.exe (PID: 7128)
- sc.exe (PID: 5168)
- sc.exe (PID: 1336)
- sc.exe (PID: 4020)
- sc.exe (PID: 5876)
- sc.exe (PID: 2124)
- sc.exe (PID: 2192)
- sc.exe (PID: 6936)
- sc.exe (PID: 4816)
- sc.exe (PID: 6776)
- sc.exe (PID: 2804)
- sc.exe (PID: 6216)
- sc.exe (PID: 3108)
- sc.exe (PID: 480)
- sc.exe (PID: 5368)
- sc.exe (PID: 2668)
- sc.exe (PID: 432)
- sc.exe (PID: 5808)
- sc.exe (PID: 1488)
- sc.exe (PID: 5616)
- sc.exe (PID: 7132)
- sc.exe (PID: 4860)
- sc.exe (PID: 3948)
- sc.exe (PID: 1688)
- sc.exe (PID: 1564)
- sc.exe (PID: 4832)
- sc.exe (PID: 1200)
- sc.exe (PID: 6796)
- sc.exe (PID: 4836)
- sc.exe (PID: 6520)
- sc.exe (PID: 6364)
- sc.exe (PID: 6124)
- sc.exe (PID: 5564)
- sc.exe (PID: 4088)
- sc.exe (PID: 1520)
- sc.exe (PID: 2972)
- sc.exe (PID: 3720)
- sc.exe (PID: 1496)
- sc.exe (PID: 6980)
- sc.exe (PID: 4676)
- sc.exe (PID: 2764)
- sc.exe (PID: 3564)
- sc.exe (PID: 6320)
- sc.exe (PID: 888)
- sc.exe (PID: 6264)
- sc.exe (PID: 1132)
- sc.exe (PID: 5768)
- sc.exe (PID: 6512)
- sc.exe (PID: 5628)
- sc.exe (PID: 2728)
- sc.exe (PID: 2276)
- sc.exe (PID: 2228)
- sc.exe (PID: 6012)
- sc.exe (PID: 5652)
- sc.exe (PID: 2040)
- sc.exe (PID: 6656)
- sc.exe (PID: 5692)
- sc.exe (PID: 2464)
- sc.exe (PID: 6232)
- sc.exe (PID: 7080)
- sc.exe (PID: 7156)
- sc.exe (PID: 6828)
- sc.exe (PID: 1508)
- sc.exe (PID: 6152)
- sc.exe (PID: 1964)
- sc.exe (PID: 5780)
- sc.exe (PID: 3196)
- sc.exe (PID: 6400)
- sc.exe (PID: 4048)
- sc.exe (PID: 1192)
- sc.exe (PID: 7040)
- sc.exe (PID: 4528)
- sc.exe (PID: 5532)
- sc.exe (PID: 3388)
- sc.exe (PID: 864)
- sc.exe (PID: 5468)
- sc.exe (PID: 4960)
- sc.exe (PID: 7120)
- sc.exe (PID: 5744)
- sc.exe (PID: 1180)
- sc.exe (PID: 2216)
- sc.exe (PID: 6164)
- sc.exe (PID: 2836)
- sc.exe (PID: 4796)
- sc.exe (PID: 6832)
- sc.exe (PID: 4052)
- sc.exe (PID: 2800)
- sc.exe (PID: 2664)
- sc.exe (PID: 6492)
- sc.exe (PID: 6380)
- sc.exe (PID: 756)
- sc.exe (PID: 1816)
- sc.exe (PID: 6376)
- sc.exe (PID: 3048)
- sc.exe (PID: 760)
- sc.exe (PID: 304)
- sc.exe (PID: 5060)
- sc.exe (PID: 5008)
- sc.exe (PID: 2512)
- sc.exe (PID: 3788)
- sc.exe (PID: 4708)
- sc.exe (PID: 7072)
- sc.exe (PID: 3924)
- sc.exe (PID: 2604)
- sc.exe (PID: 4544)
- sc.exe (PID: 5172)
- sc.exe (PID: 3944)
- sc.exe (PID: 5716)
- sc.exe (PID: 3740)
- sc.exe (PID: 7104)
- sc.exe (PID: 6348)
- sc.exe (PID: 1868)
- sc.exe (PID: 3780)
- sc.exe (PID: 5928)
- sc.exe (PID: 4380)
- sc.exe (PID: 4104)
- sc.exe (PID: 5032)
- sc.exe (PID: 4236)
- sc.exe (PID: 6368)
- sc.exe (PID: 4196)
- sc.exe (PID: 1388)
- sc.exe (PID: 6192)
- sc.exe (PID: 7164)
- sc.exe (PID: 4112)
- sc.exe (PID: 6200)
- sc.exe (PID: 724)
- sc.exe (PID: 3960)
- sc.exe (PID: 5288)
- sc.exe (PID: 4680)
- sc.exe (PID: 436)
- sc.exe (PID: 7052)
- sc.exe (PID: 4944)
Starts NET.EXE for network exploration
- svchost.exe (PID: 1080)
The process executes Powershell scripts
- svchost.exe (PID: 1080)
Starts POWERSHELL.EXE for commands execution
- svchost.exe (PID: 1080)
Stops a currently running service
- sc.exe (PID: 2148)
- sc.exe (PID: 4444)
- sc.exe (PID: 1644)
- sc.exe (PID: 2076)
- sc.exe (PID: 1872)
INFO
Reads the machine GUID from the registry
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 1080)
- svchost.exe (PID: 5744)
Process checks computer location settings
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 1080)
Creates files or folders in the user directory
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
Checks supported languages
- svchost.exe (PID: 1080)
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 5744)
Reads the computer name
- svchost.exe (PID: 1080)
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
- svchost.exe (PID: 5744)
Create files in a temporary directory
- svchost.exe (PID: 1080)
- svchost.exe (PID: 5744)
- 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe (PID: 1604)
Launching a file from a Registry key
- svchost.exe (PID: 1080)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5764)
- notepad.exe (PID: 6220)
- WMIC.exe (PID: 3676)
Manual execution by a user
- svchost.exe (PID: 5744)
- rundll32.exe (PID: 3488)
- notepad.exe (PID: 6220)
- rundll32.exe (PID: 3876)
- rundll32.exe (PID: 4804)
- powershell.exe (PID: 6104)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 6104)
Checks proxy server information
- slui.exe (PID: 3844)
Reads the software policy settings
- slui.exe (PID: 3844)
Launching a file from Task Scheduler
- svchost.exe (PID: 1080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:06:19 18:26:41+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 74240 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1413e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | LB3.exe |
| LegalCopyright: | |
| OriginalFileName: | LB3.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
1 210
Monitored processes
1 077
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\system32\net1 stop VeeamTransportSvc | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | "sc.exe" config MVArmor start=disabled | C:\Windows\System32\sc.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 316 | C:\WINDOWS\system32\net1 stop VeeamDeploymentService | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | C:\WINDOWS\system32\net1 stop BackupExecRPCService | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | "cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\selfdestruct_RPy5H6T7.bat" | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | "sc.exe" delete sql | C:\Windows\System32\sc.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 281
Read events
27 277
Write events
4
Delete events
0
Modification events
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Update5YoOau |
Value: C:\Users\admin\AppData\Local\svchost.exe | |||
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\Shell\Open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | VNtFUQG9x |
Value: C:\Users\admin\AppData\Local\svchost.exe | |||
Executable files
6
Suspicious files
67
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1604 | 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe | C:\Users\admin\AppData\Local\svchost.exe | executable | |
MD5:65538E16F1090CFC81C5465A2185FA41 | SHA256:82AF319F72C145EC6FF713C64F13307C2A7C098B534F15D59AD0636A1455DD1F | |||
| 1604 | 2025-06-21_65538e16f1090cfc81c5465a2185fa41_destroyer_elex_wannacry.exe | C:\Users\admin\AppData\Local\Temp\selfdestruct_dfmp3yNa.bat | text | |
MD5:5BF575FE0A18AB8CC3F7057E6B992EF8 | SHA256:35B34780DDCA0D6083F525572E74836685DAF253DA1192E7A1B5F00350D706AA | |||
| 5744 | svchost.exe | C:\Users\admin\AppData\Local\Temp\selfdestruct_NUOlAQFz.bat | text | |
MD5:80384AC2A6120ACBE512303AEBC66A1D | SHA256:169674D683BE5127DF6B0817287779B6292835BD97B12785ED9243543B823505 | |||
| 5744 | svchost.exe | C:\Users\admin\AppData\Local\Temp\selfdestruct_fcI8f0xf.bat | text | |
MD5:80384AC2A6120ACBE512303AEBC66A1D | SHA256:169674D683BE5127DF6B0817287779B6292835BD97B12785ED9243543B823505 | |||
| 1080 | svchost.exe | C:\Users\admin\Desktop\WJjvvqONw.jpg.VNtFUQG9x | binary | |
MD5:0A07BB7443FBC6F7A5C1931B7ACADF21 | SHA256:81DE96D505DF7FE410CF3F732CD98195FA4EAB4F0457732E9A12CB0E75A80834 | |||
| 1080 | svchost.exe | C:\Users\admin\AppData\Local\Temp\selfdestruct_rHxJxp07.bat | text | |
MD5:80384AC2A6120ACBE512303AEBC66A1D | SHA256:169674D683BE5127DF6B0817287779B6292835BD97B12785ED9243543B823505 | |||
| 1080 | svchost.exe | C:\Users\admin\Desktop\demandmedical.png | binary | |
MD5:85A69E6C39B25AC5F77D8B7A25A49C05 | SHA256:FCDF19AEF10E69A403FBD136B19B89DDA7932A7FDA722EC8599F31529E41D6B7 | |||
| 1080 | svchost.exe | C:\Users\admin\AppData\Local\Temp\selfdestruct_OHY34y5N.bat | text | |
MD5:80384AC2A6120ACBE512303AEBC66A1D | SHA256:169674D683BE5127DF6B0817287779B6292835BD97B12785ED9243543B823505 | |||
| 1080 | svchost.exe | C:\Users\admin\AppData\Local\Temp\selfdestruct_fajtQ9Sy.bat | text | |
MD5:80384AC2A6120ACBE512303AEBC66A1D | SHA256:169674D683BE5127DF6B0817287779B6292835BD97B12785ED9243543B823505 | |||
| 1080 | svchost.exe | C:\Users\admin\AppData\Local\Temp\selfdestruct_gb9q7FGT.bat | text | |
MD5:80384AC2A6120ACBE512303AEBC66A1D | SHA256:169674D683BE5127DF6B0817287779B6292835BD97B12785ED9243543B823505 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
19
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5116 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5116 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5116 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5116 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wbadmin.exe | Invalid parameter passed to C runtime function.
|
wbadmin.exe | Invalid parameter passed to C runtime function.
|
wbadmin.exe | Invalid parameter passed to C runtime function.
|