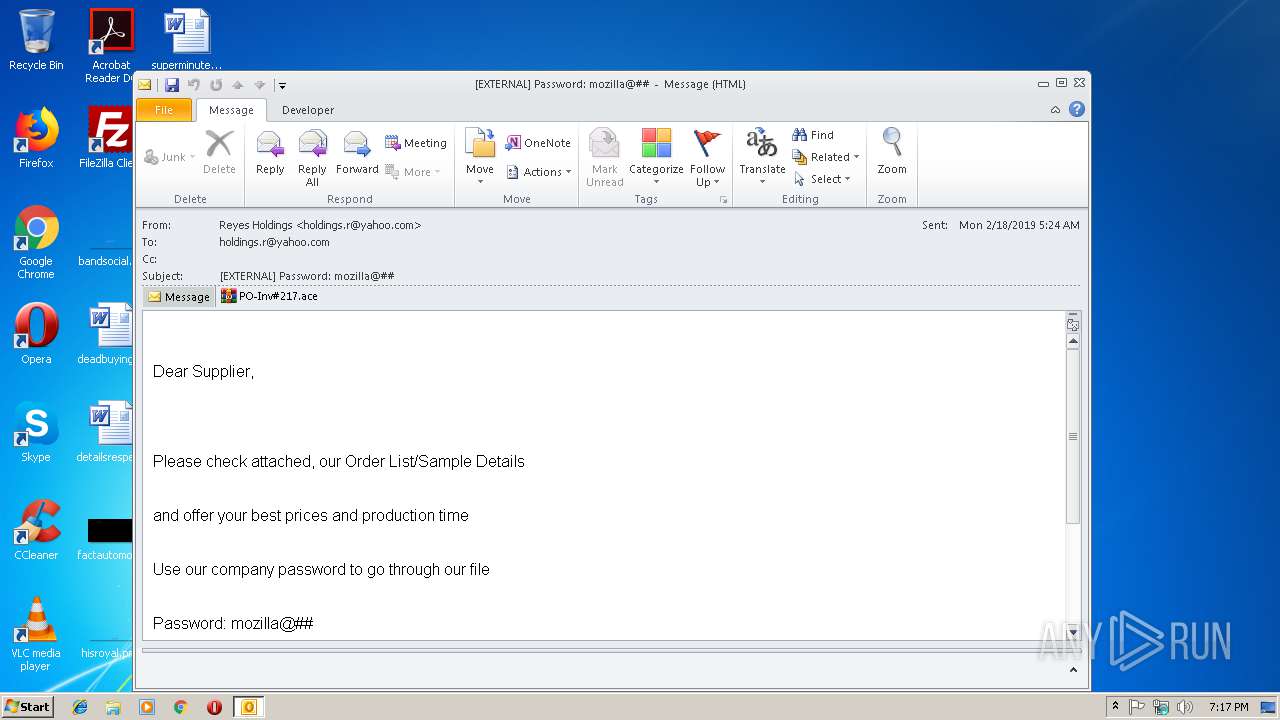
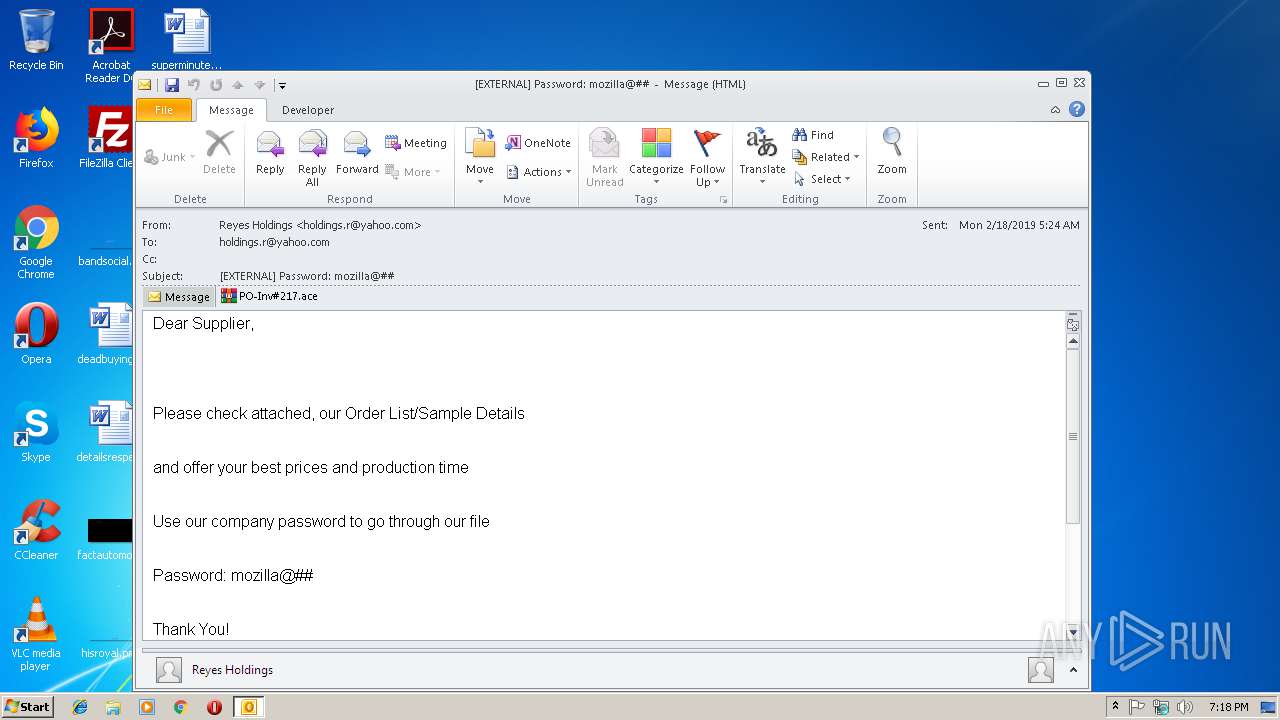
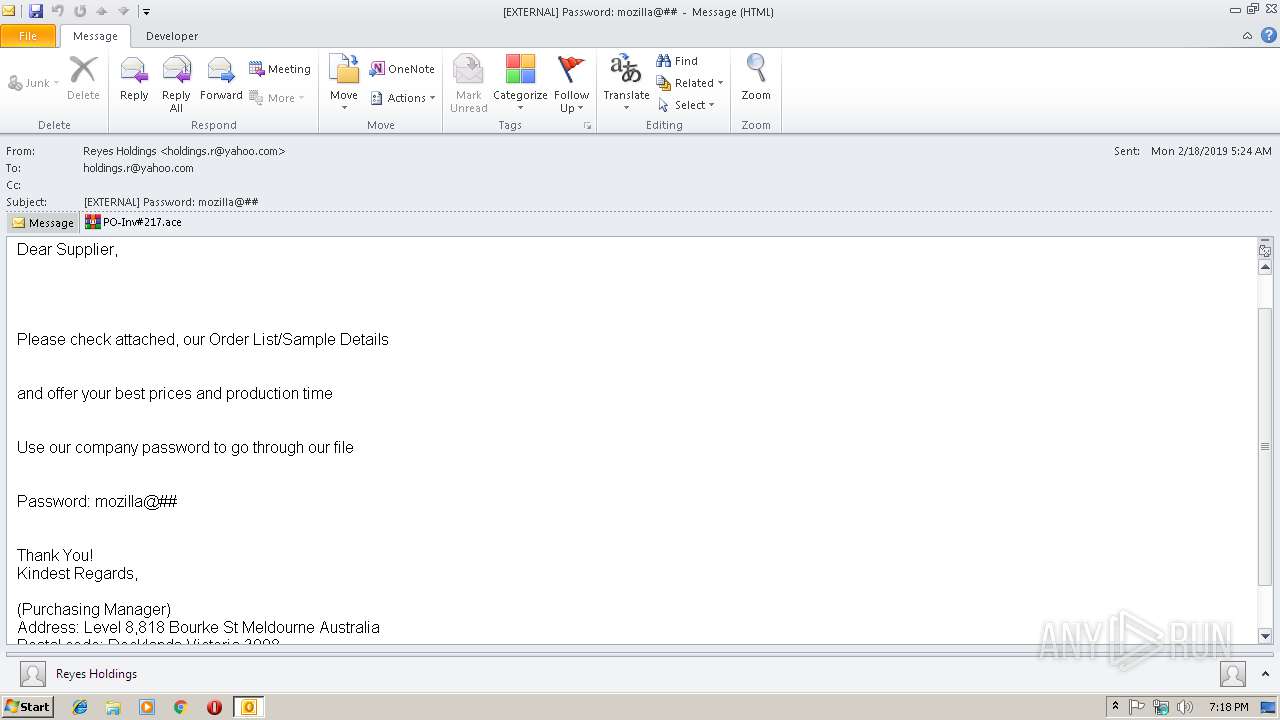
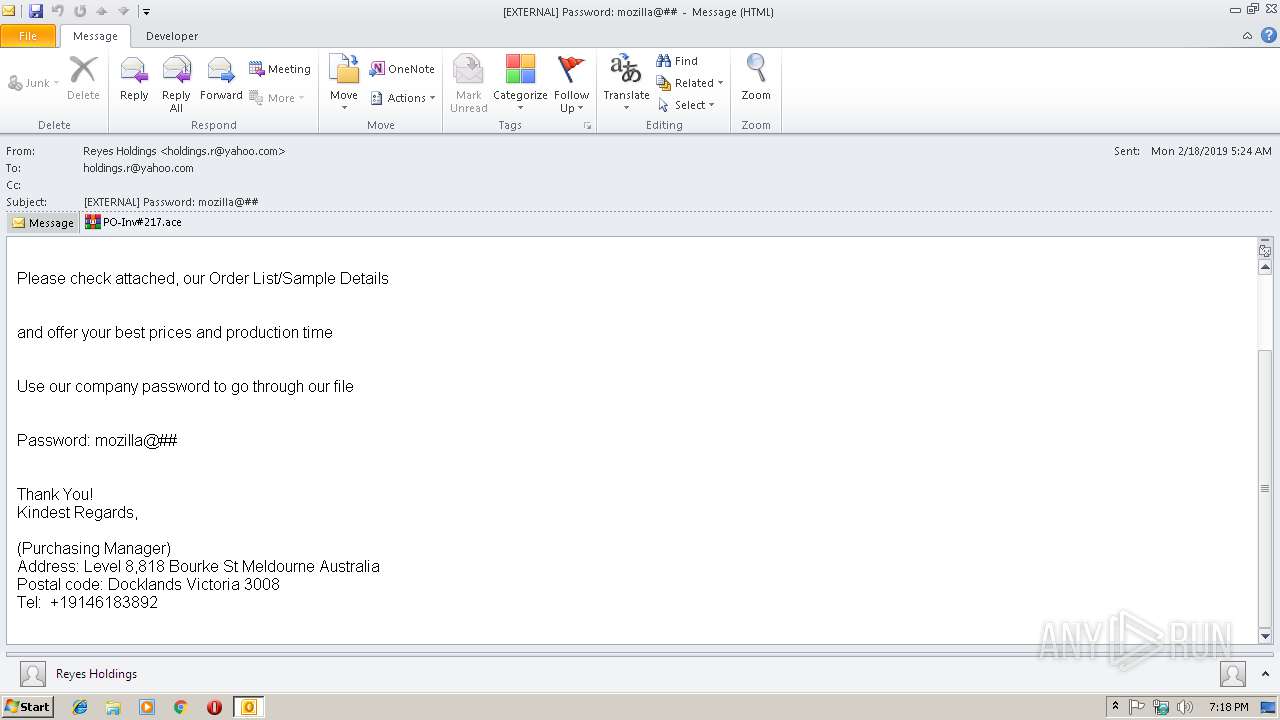
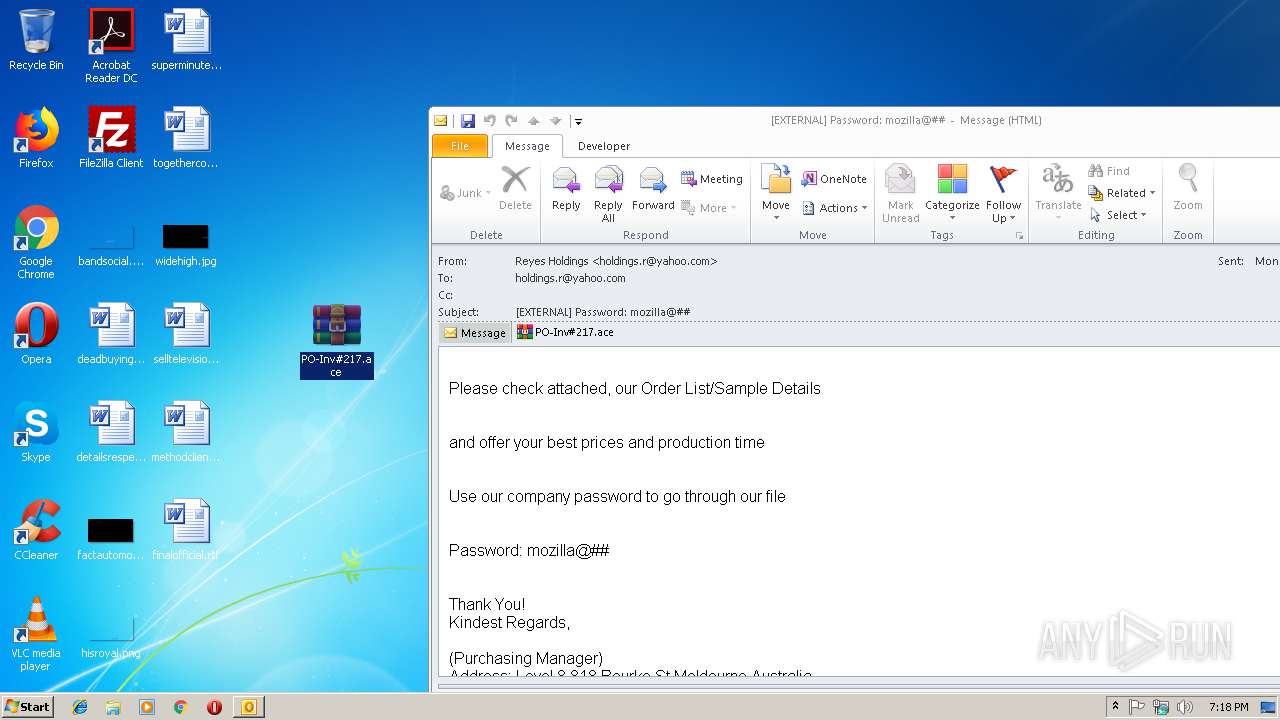
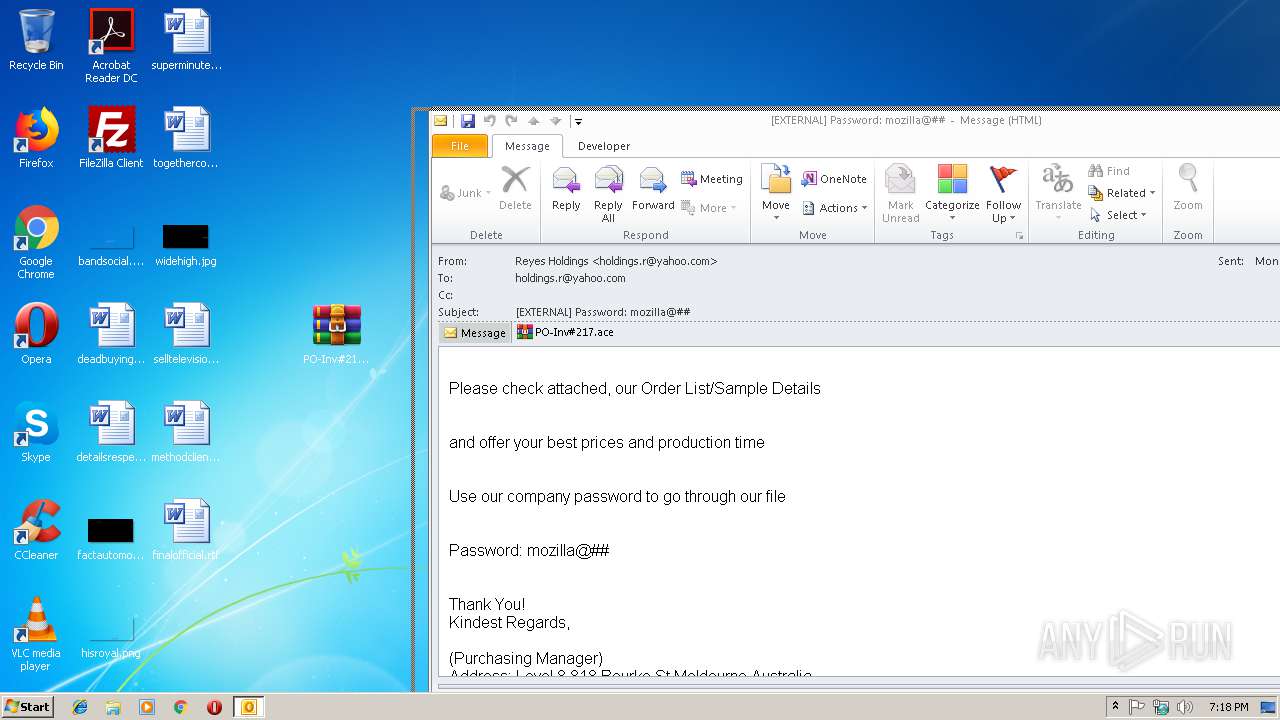
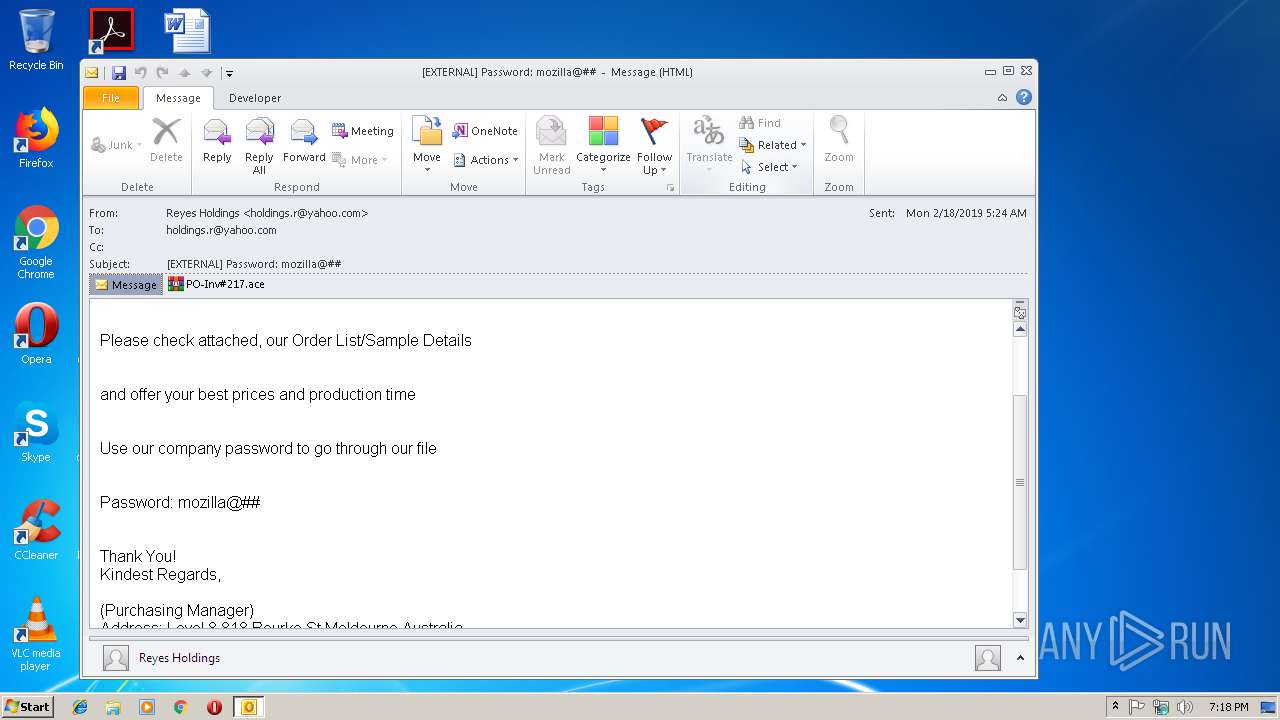
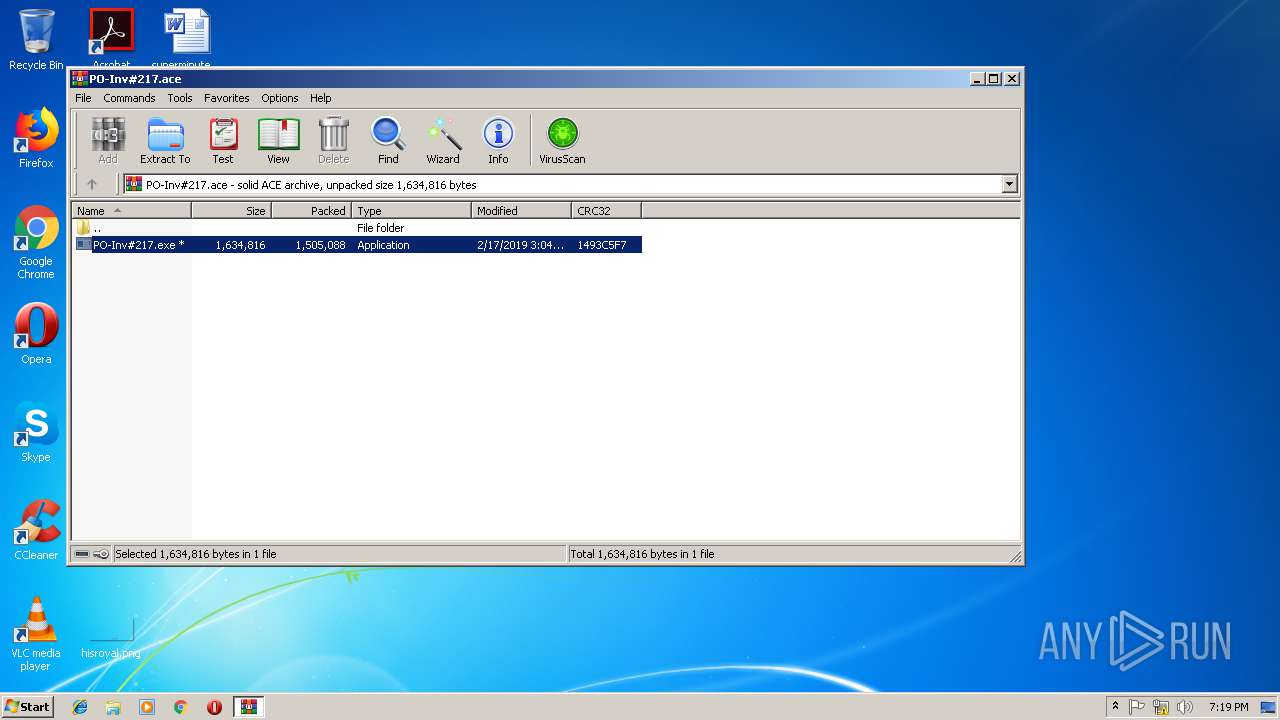
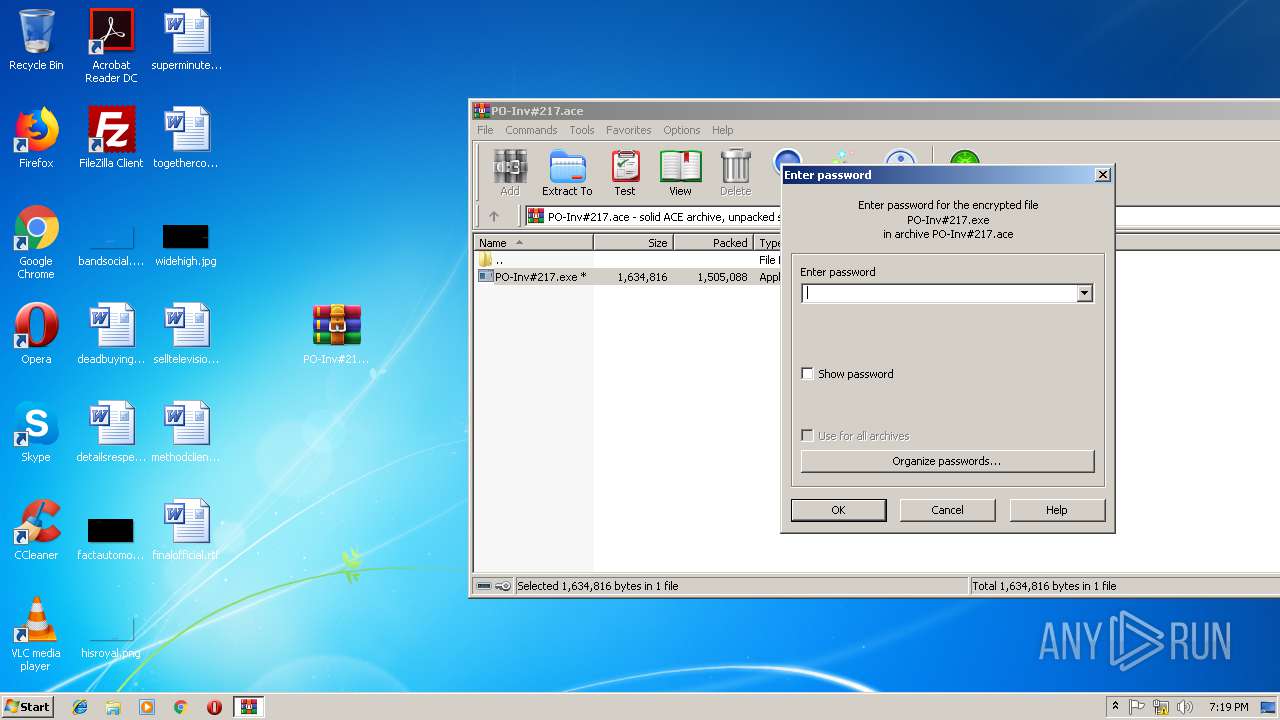
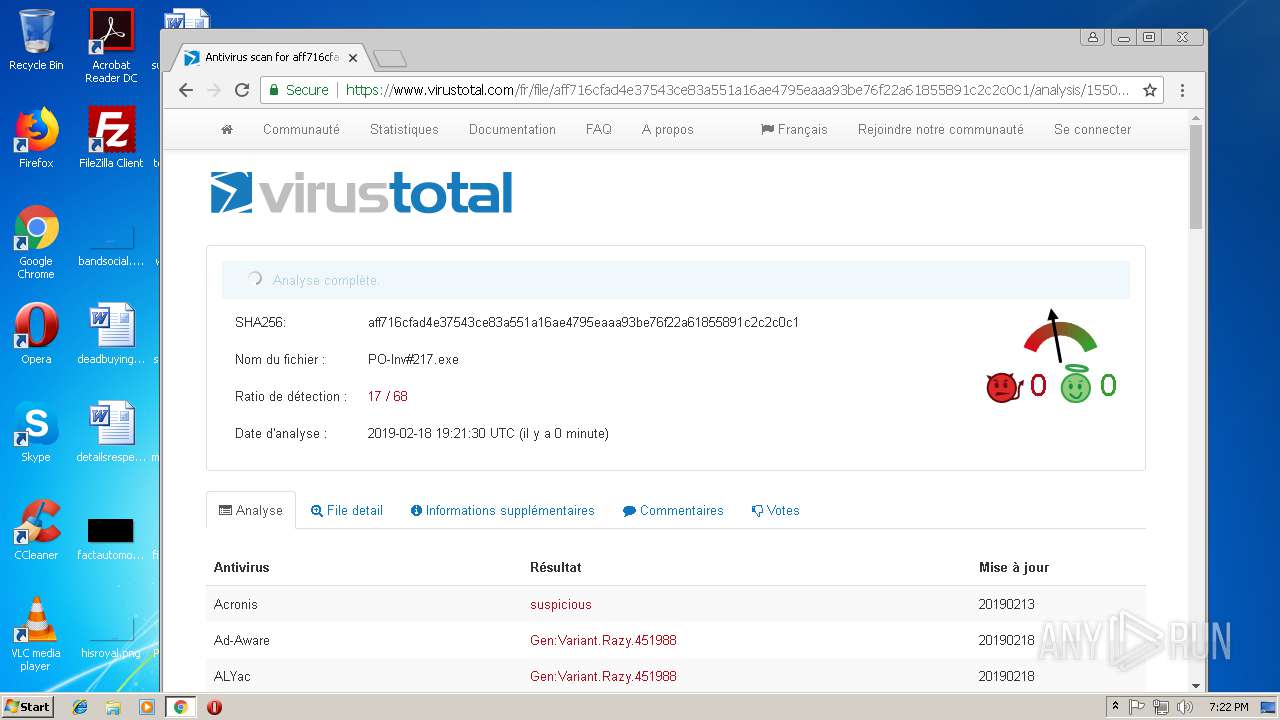
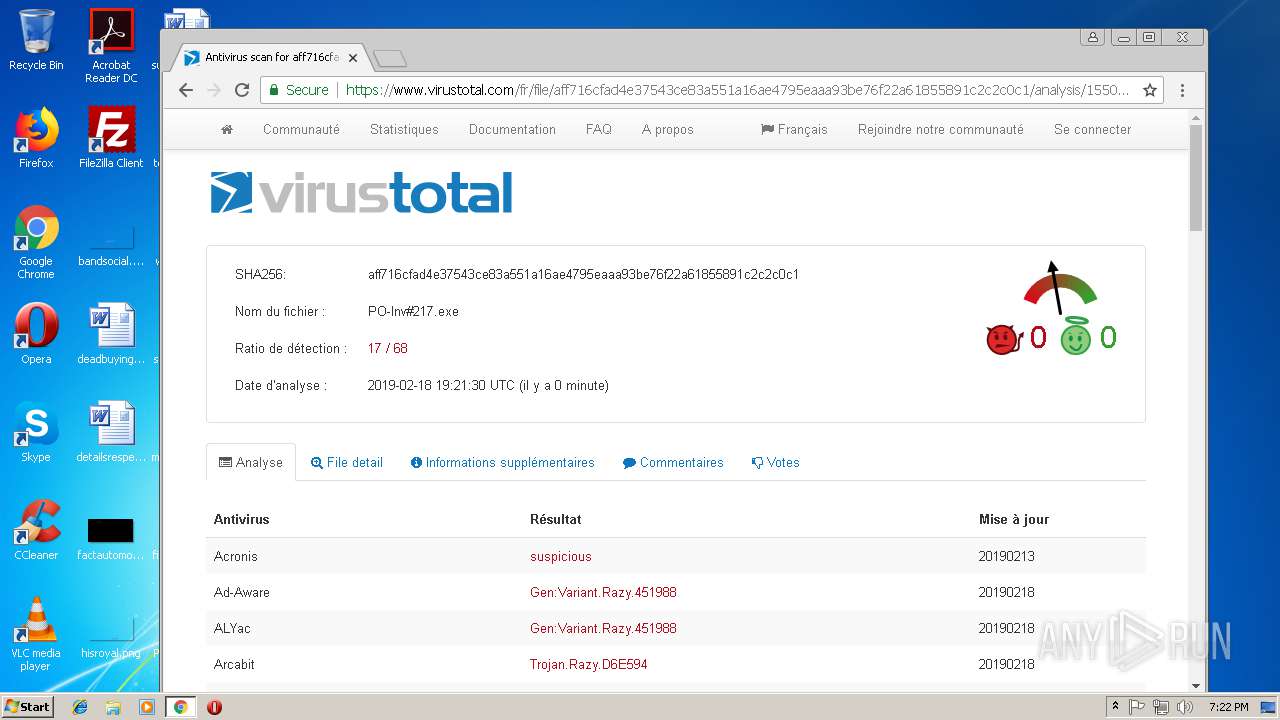
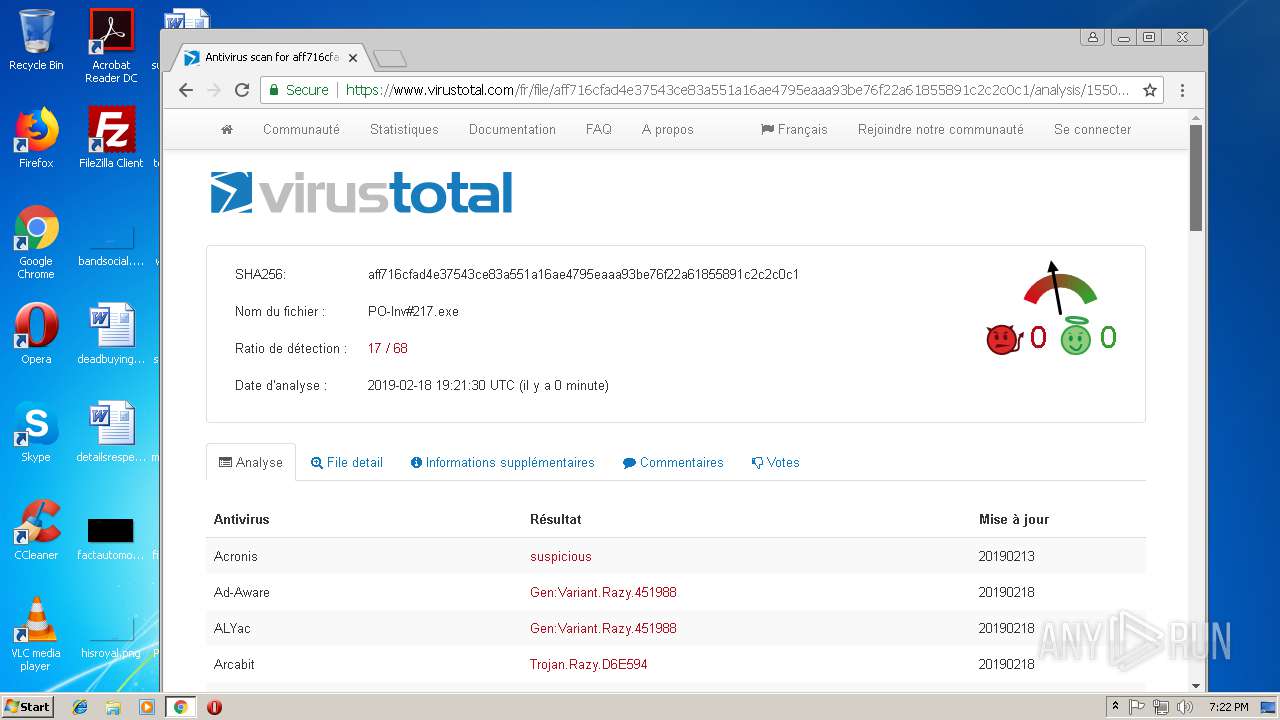
| File name: | EXTERNAL Password mozilla@##.msg |
| Full analysis: | https://app.any.run/tasks/dee97006-2269-465b-a85c-f949b34a13f6 |
| Verdict: | Malicious activity |
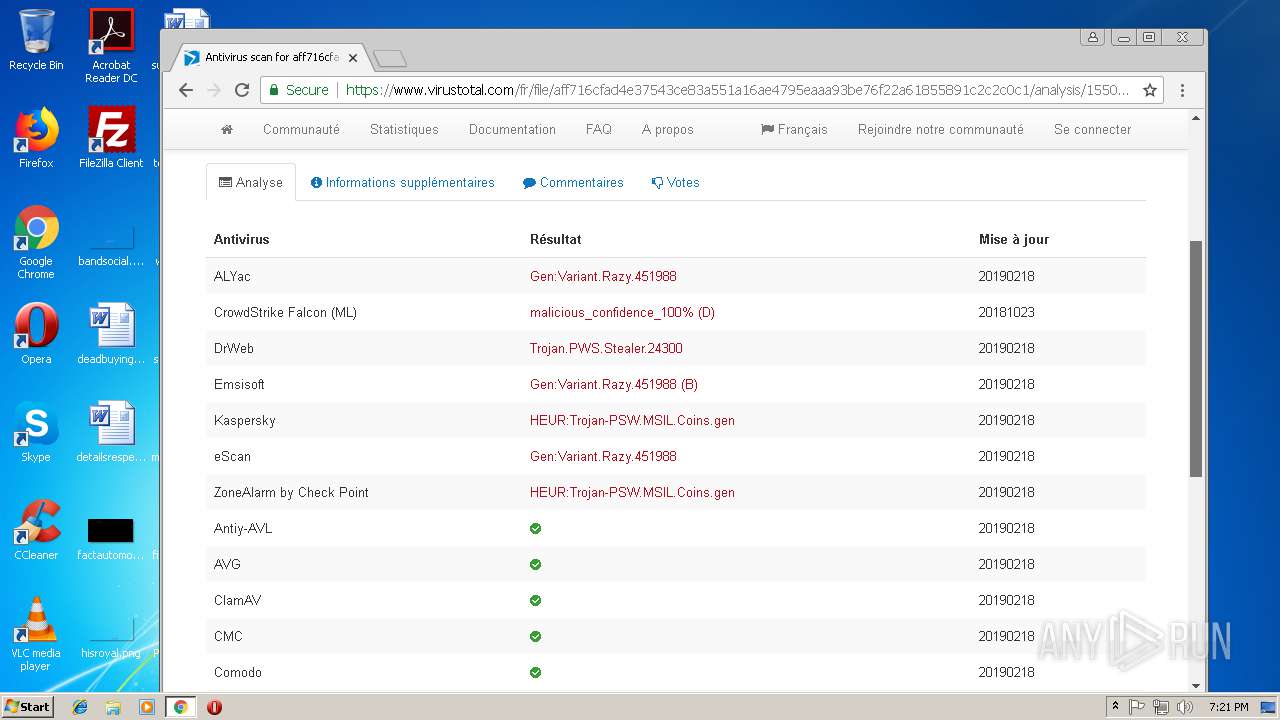
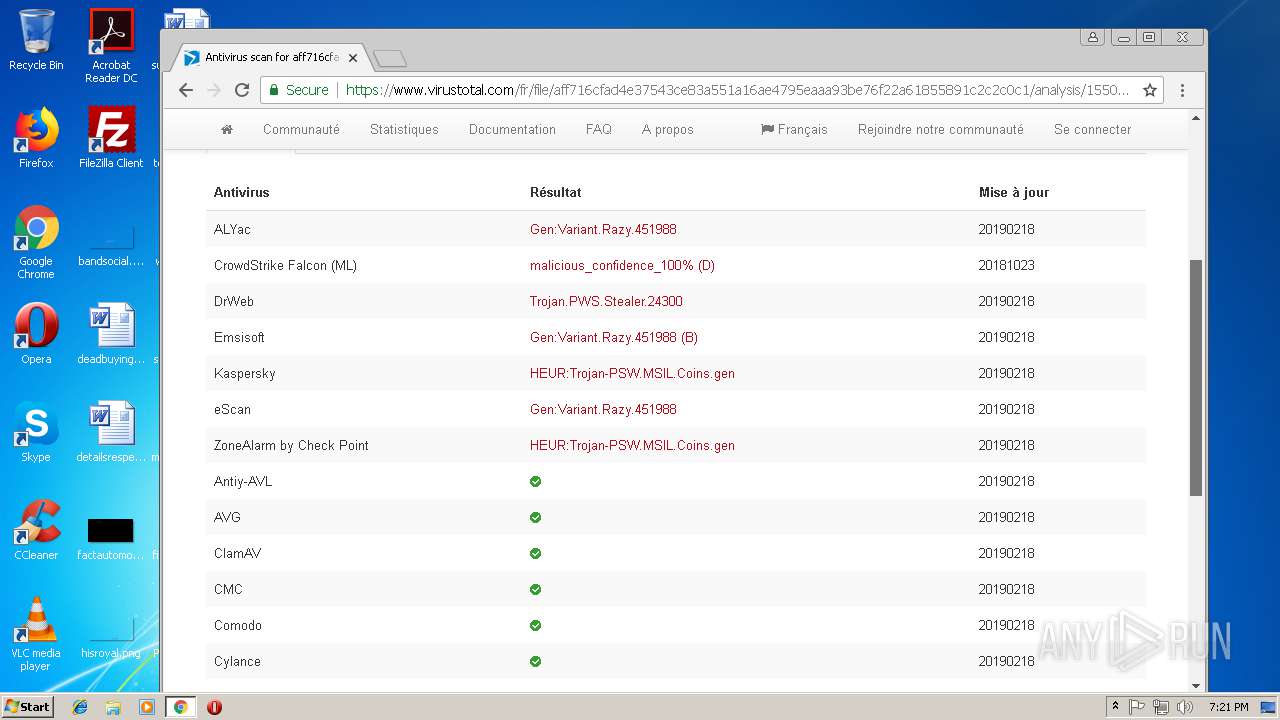
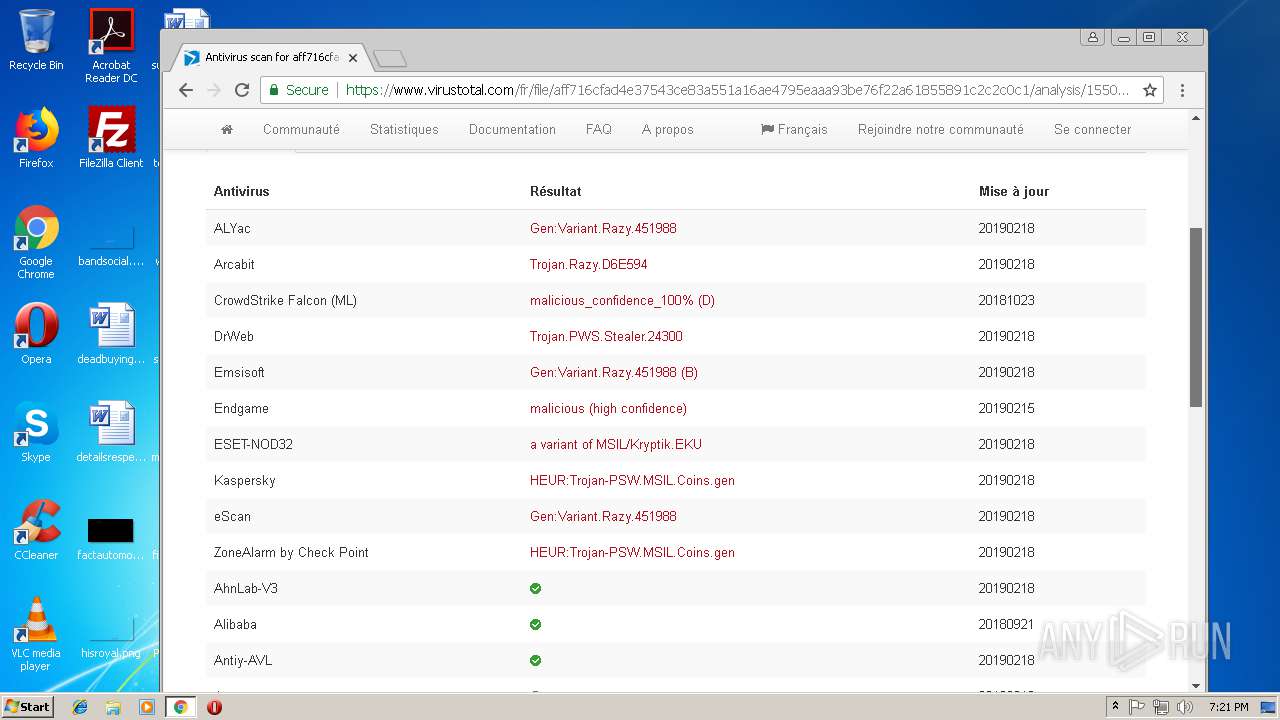
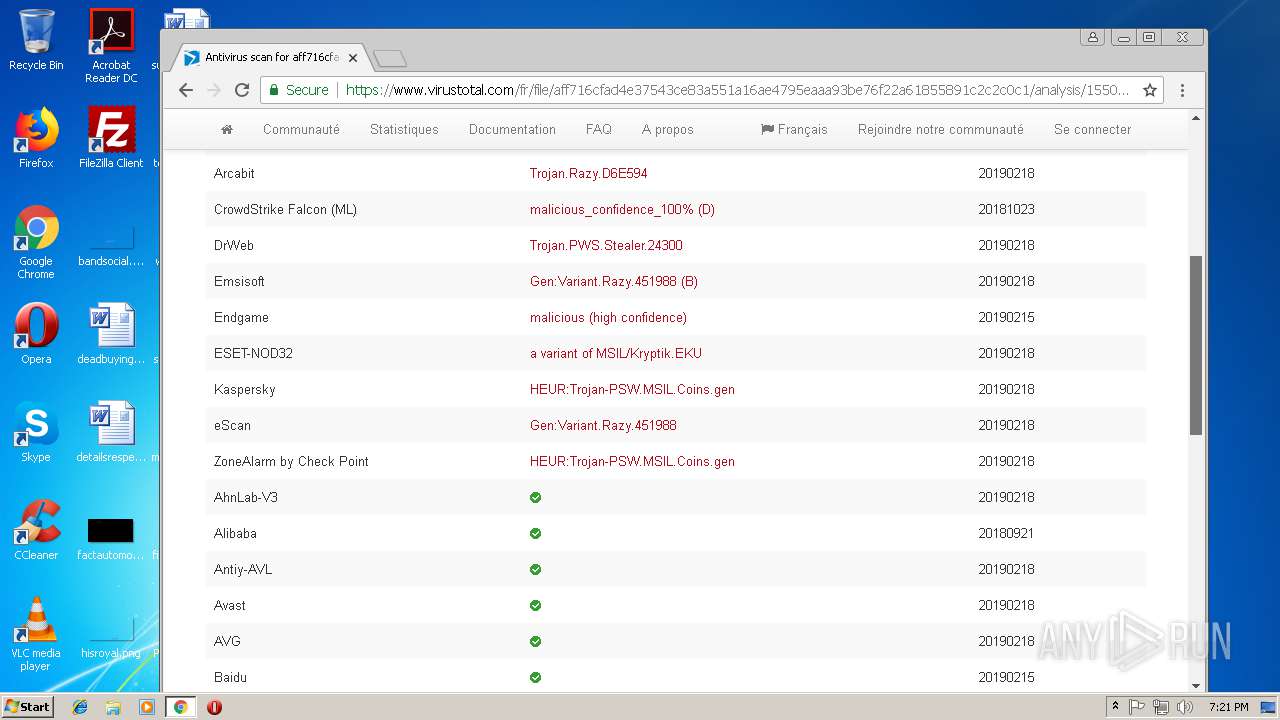
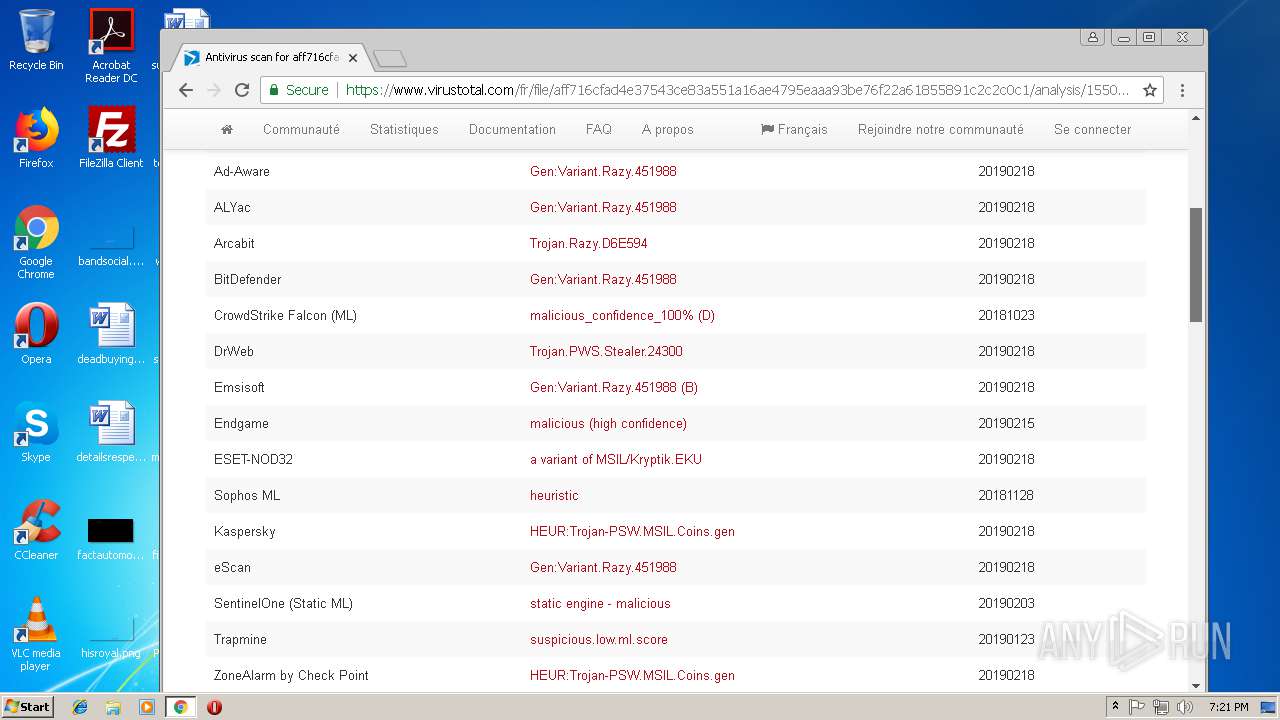
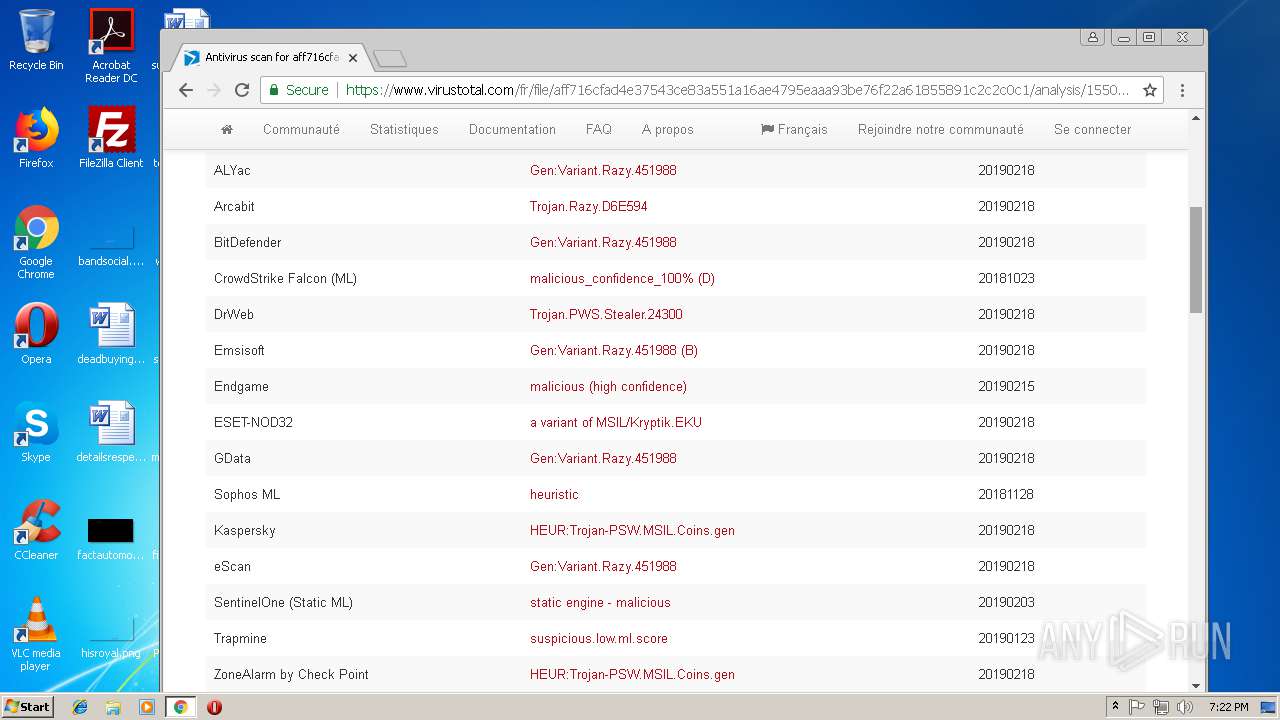
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | February 18, 2019, 19:17:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 30836F08106F2CF25C1624838C4F1387 |
| SHA1: | D5FEFACABA079FE73ED70FECB869901F528601F7 |
| SHA256: | 828D3D232735D493D147395A40A60A7CD5EA004F5A90B089218A93790A22CC8A |
| SSDEEP: | 24576:pyQZ5+348jgTZRfQ5yK4LxJSmdHie5RT3gCn0Y8u+yTu56NXjmD3LadHs+0gF:TiPgvf4Z4L/mo93Vn0Y8356pi7OD |
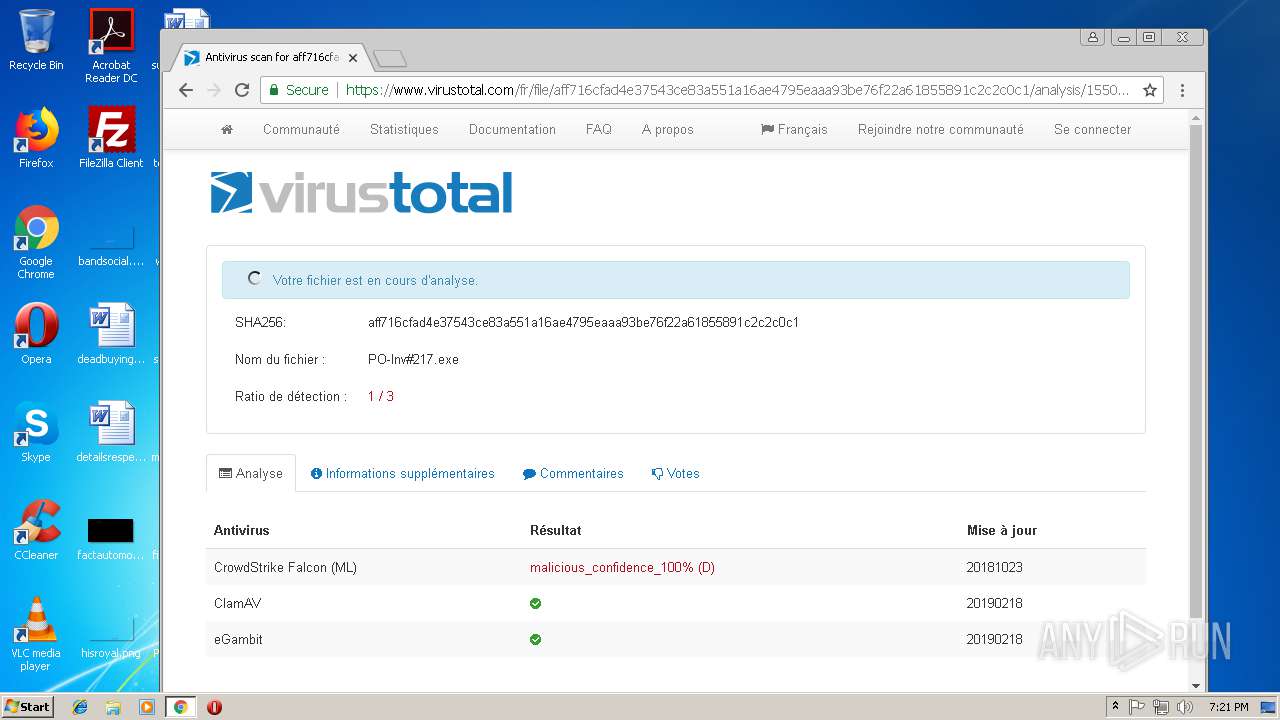
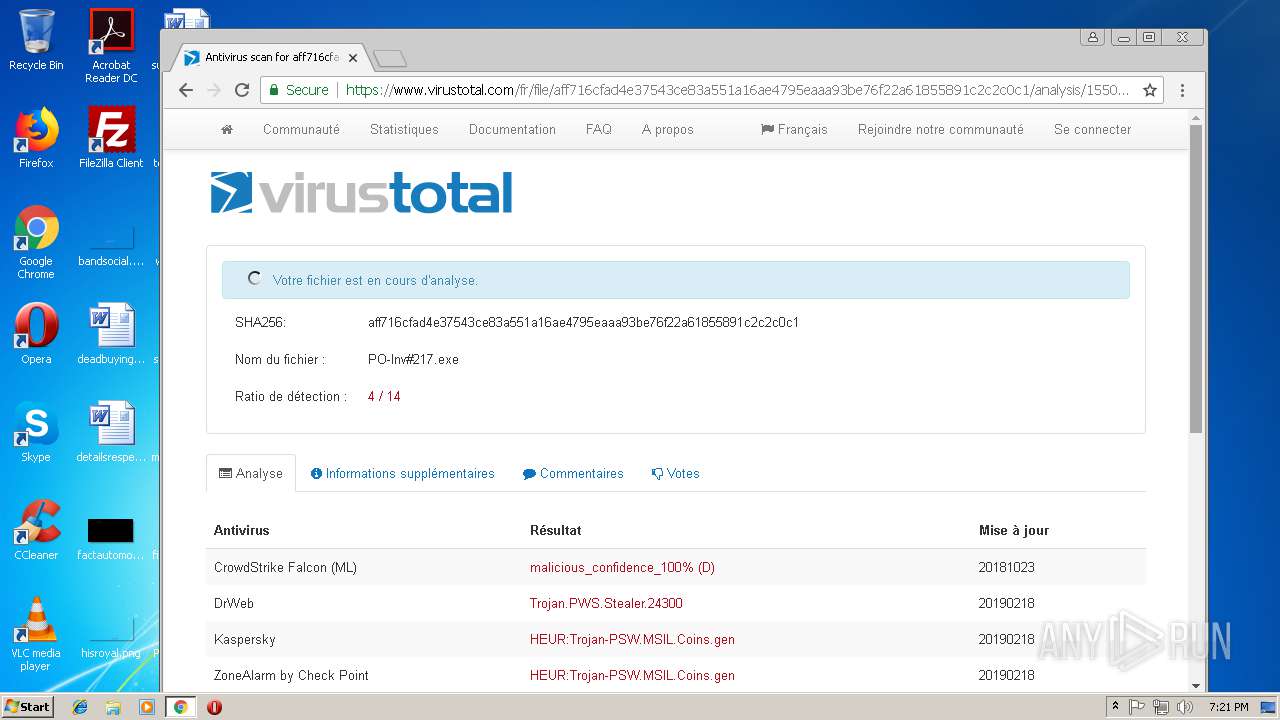
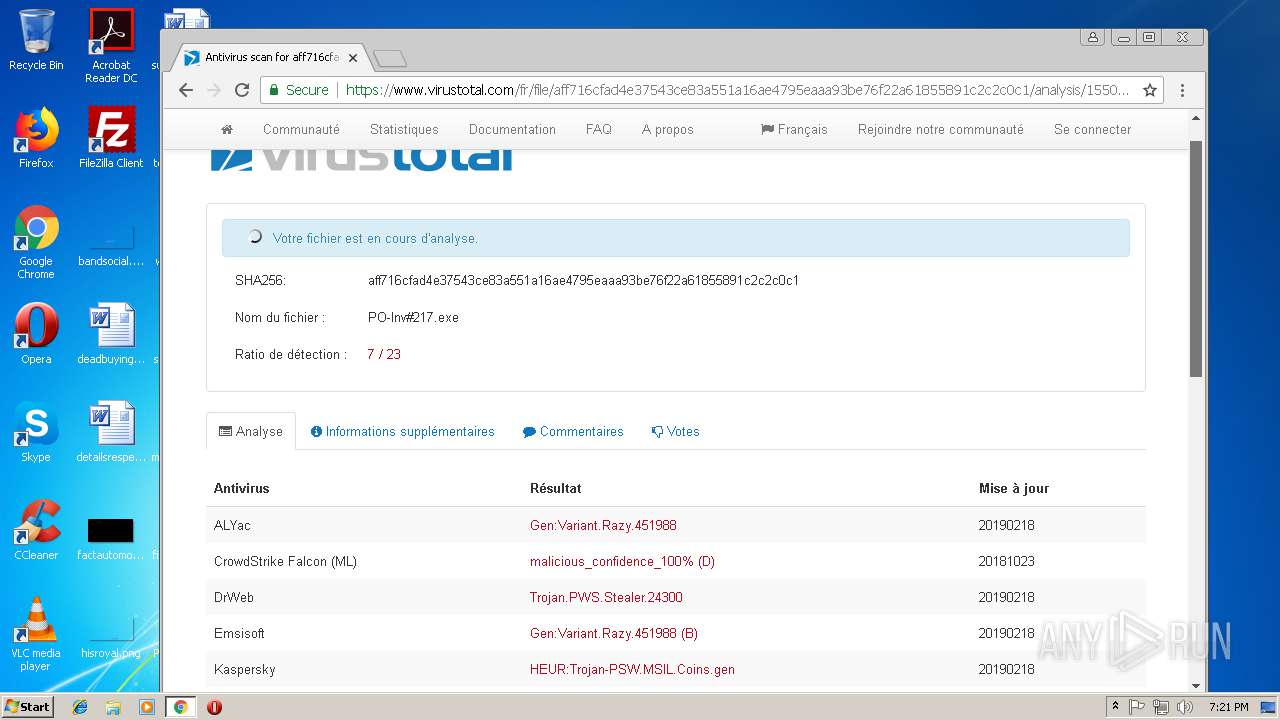
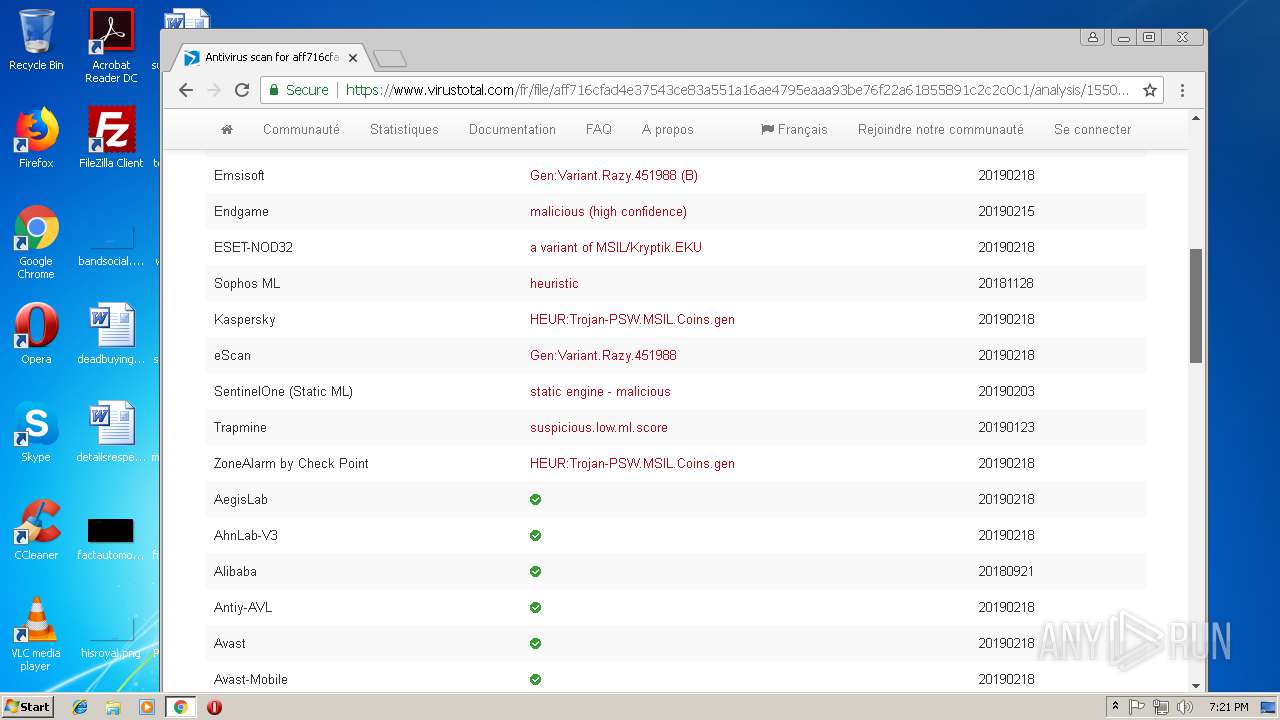
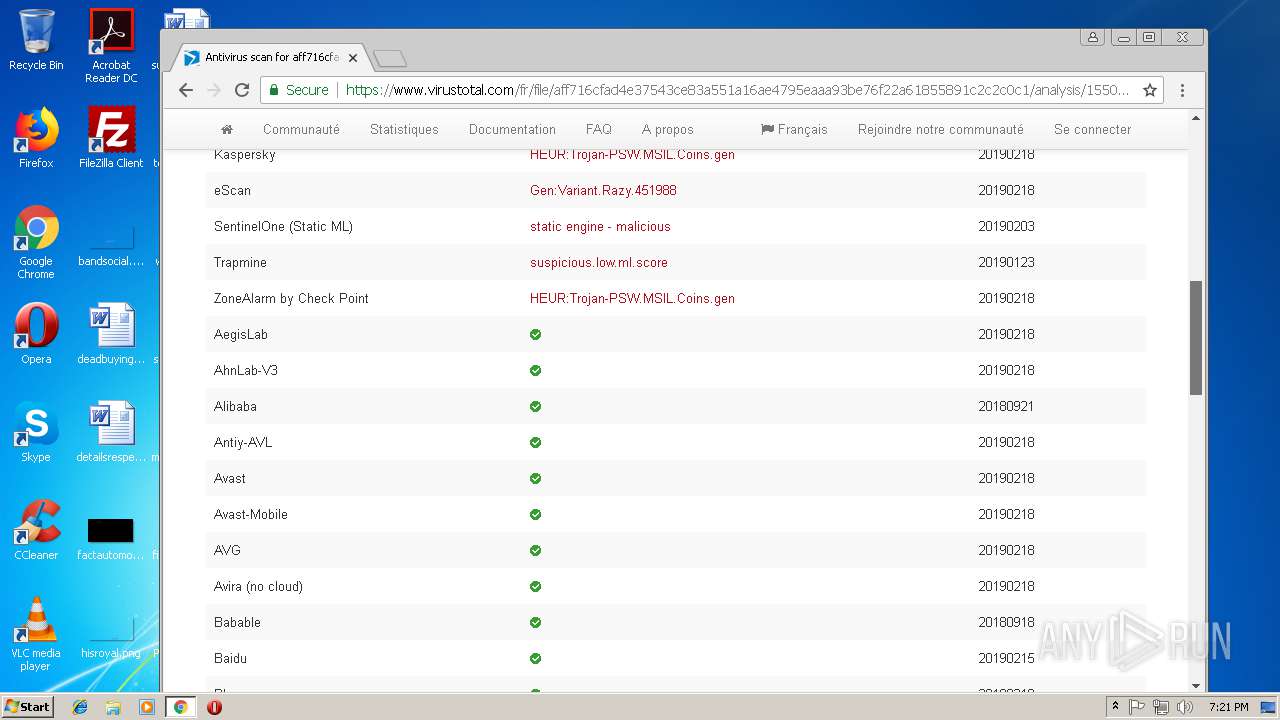
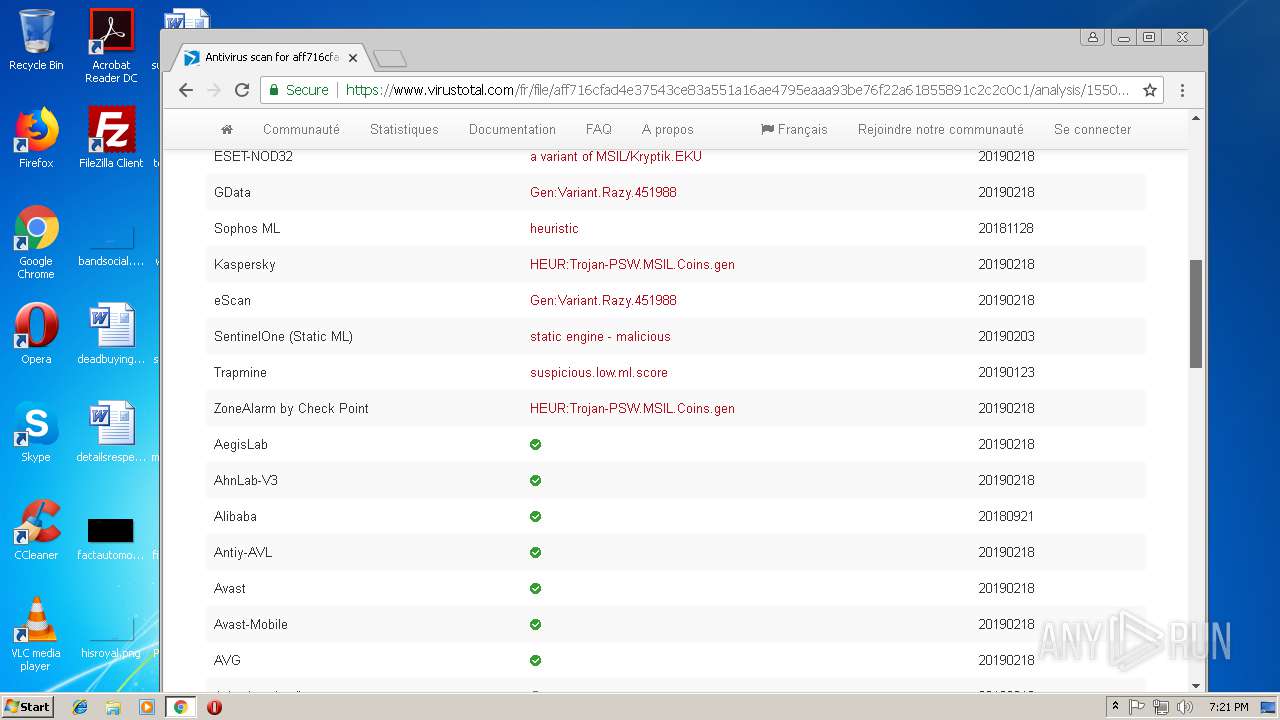
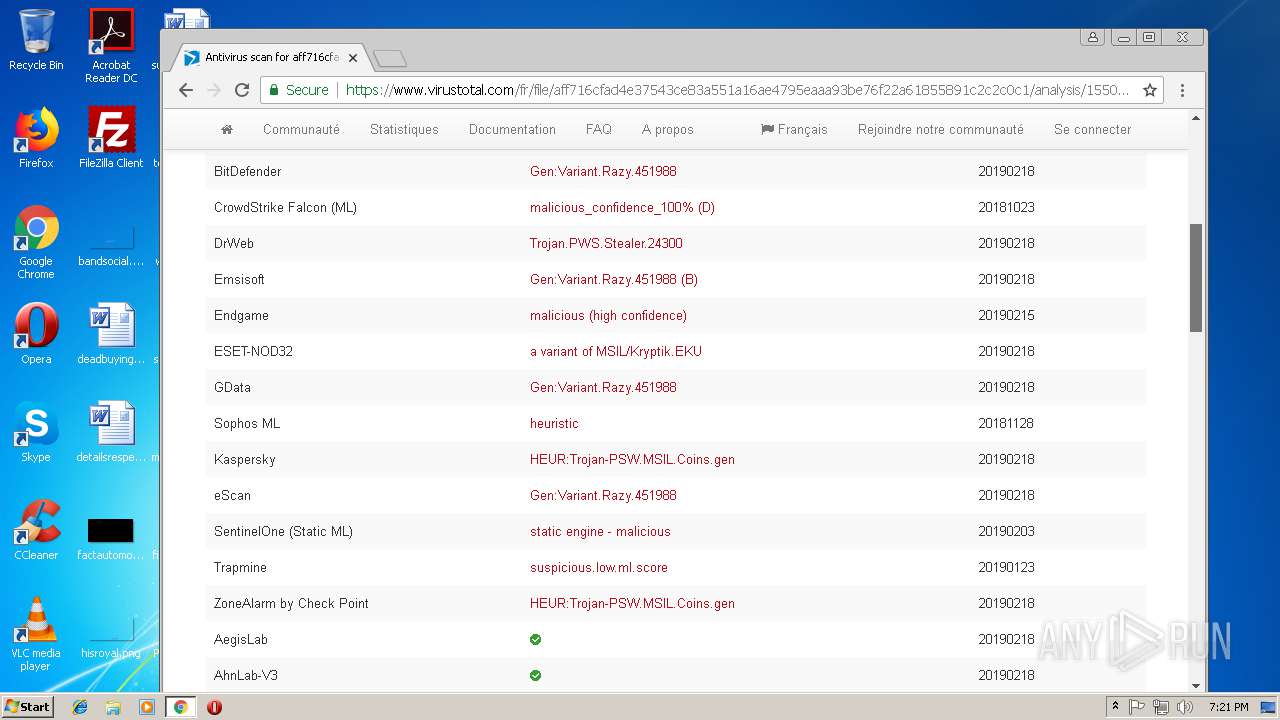
MALICIOUS
Changes the autorun value in the registry
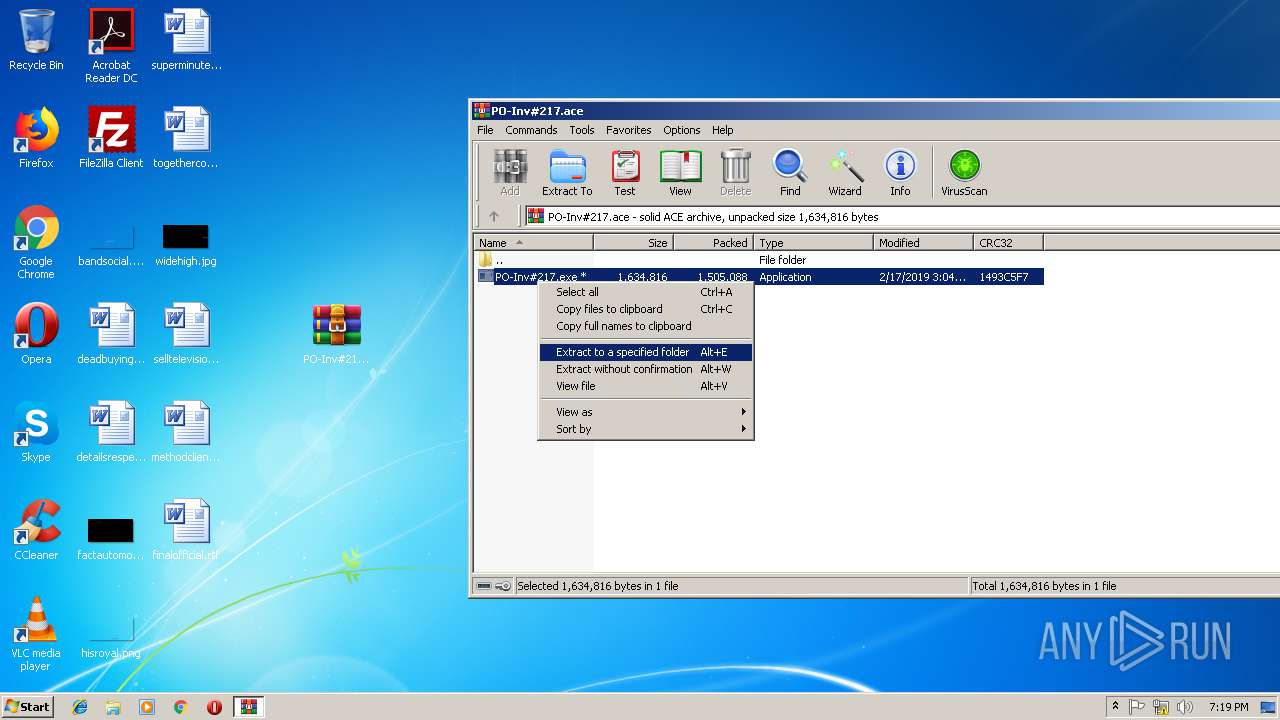
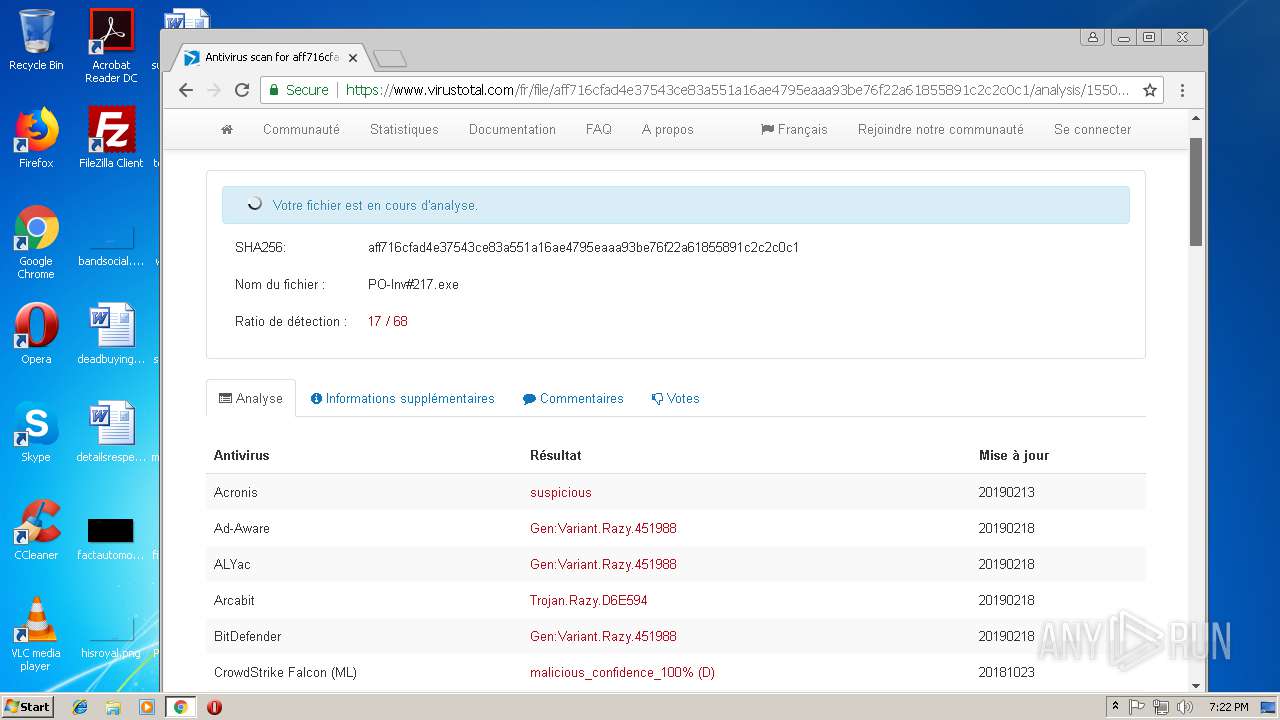
- PO-Inv#217.exe (PID: 3300)
Actions looks like stealing of personal data
- PO-Inv#217.exe (PID: 3300)
Application was dropped or rewritten from another process
- PO-Inv#217.exe (PID: 3300)
AGENTTESLA was detected
- PO-Inv#217.exe (PID: 3300)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3112)
Executable content was dropped or overwritten
- PO-Inv#217.exe (PID: 3300)
- WinRAR.exe (PID: 3036)
- WinRAR.exe (PID: 2640)
Reads Windows Product ID
- PO-Inv#217.exe (PID: 3300)
Creates files in the user directory
- PO-Inv#217.exe (PID: 3300)
- OUTLOOK.EXE (PID: 3112)
Reads Environment values
- PO-Inv#217.exe (PID: 3300)
Loads DLL from Mozilla Firefox
- PO-Inv#217.exe (PID: 3300)
Connects to SMTP port
- PO-Inv#217.exe (PID: 3300)
Checks for external IP
- PO-Inv#217.exe (PID: 3300)
INFO
Reads settings of System Certificates
- PO-Inv#217.exe (PID: 3300)
- chrome.exe (PID: 3024)
Application launched itself
- chrome.exe (PID: 3024)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
55
Monitored processes
17
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=880,11757578864931542103,10159547715694511402,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=E8A557AFEE6E5BD6013DB5F0CAFDBDA6 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=E8A557AFEE6E5BD6013DB5F0CAFDBDA6 --renderer-client-id=8 --mojo-platform-channel-handle=3912 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2364 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=880,11757578864931542103,10159547715694511402,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=3FB8CE445F29F271A9E50F467A0A2733 --mojo-platform-channel-handle=928 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2380 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=880,11757578864931542103,10159547715694511402,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=E3097922E788A5EF2F2FFA2CD1A0E674 --mojo-platform-channel-handle=608 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=880,11757578864931542103,10159547715694511402,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=665A31468EF085292A0FC99A163D6F8D --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=665A31468EF085292A0FC99A163D6F8D --renderer-client-id=6 --mojo-platform-channel-handle=3544 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
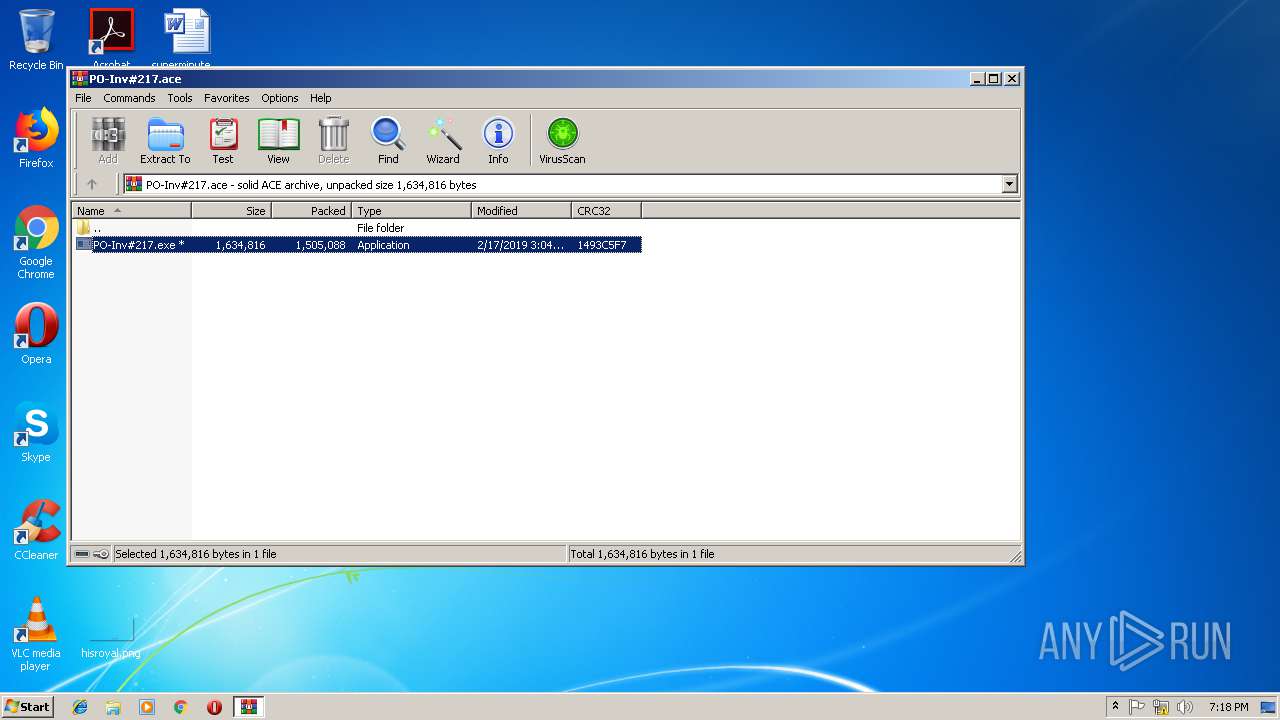
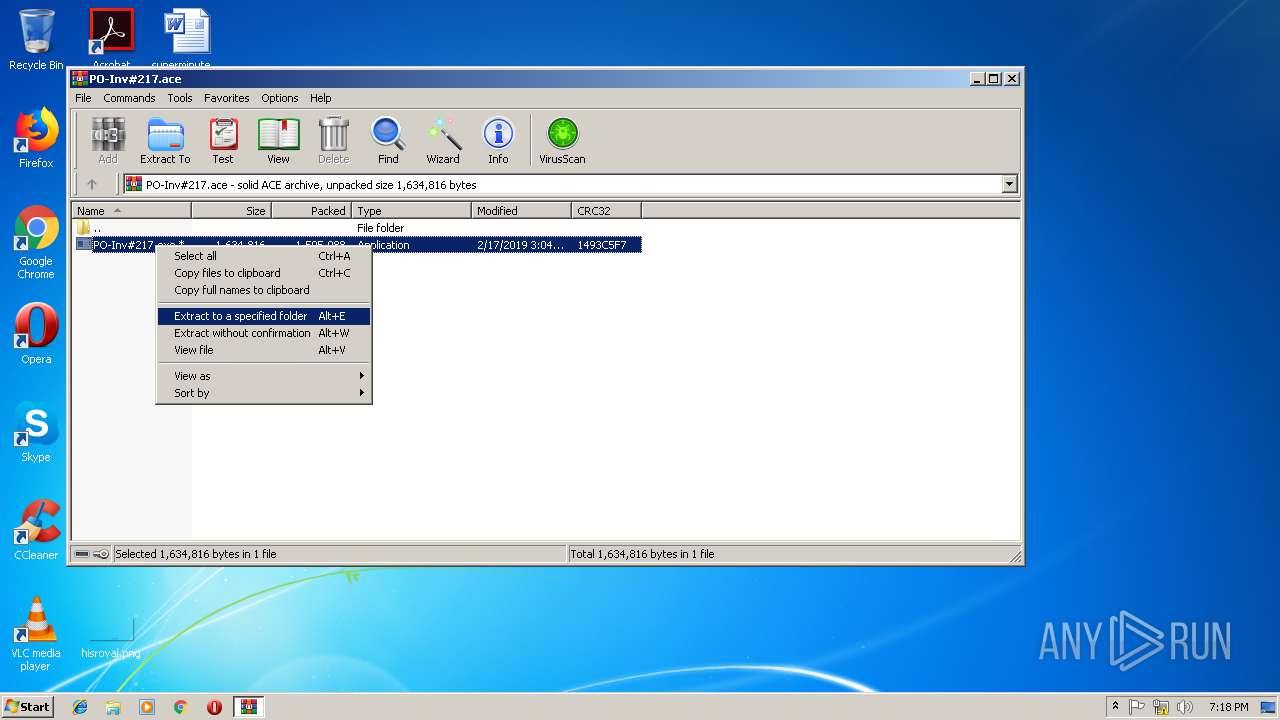
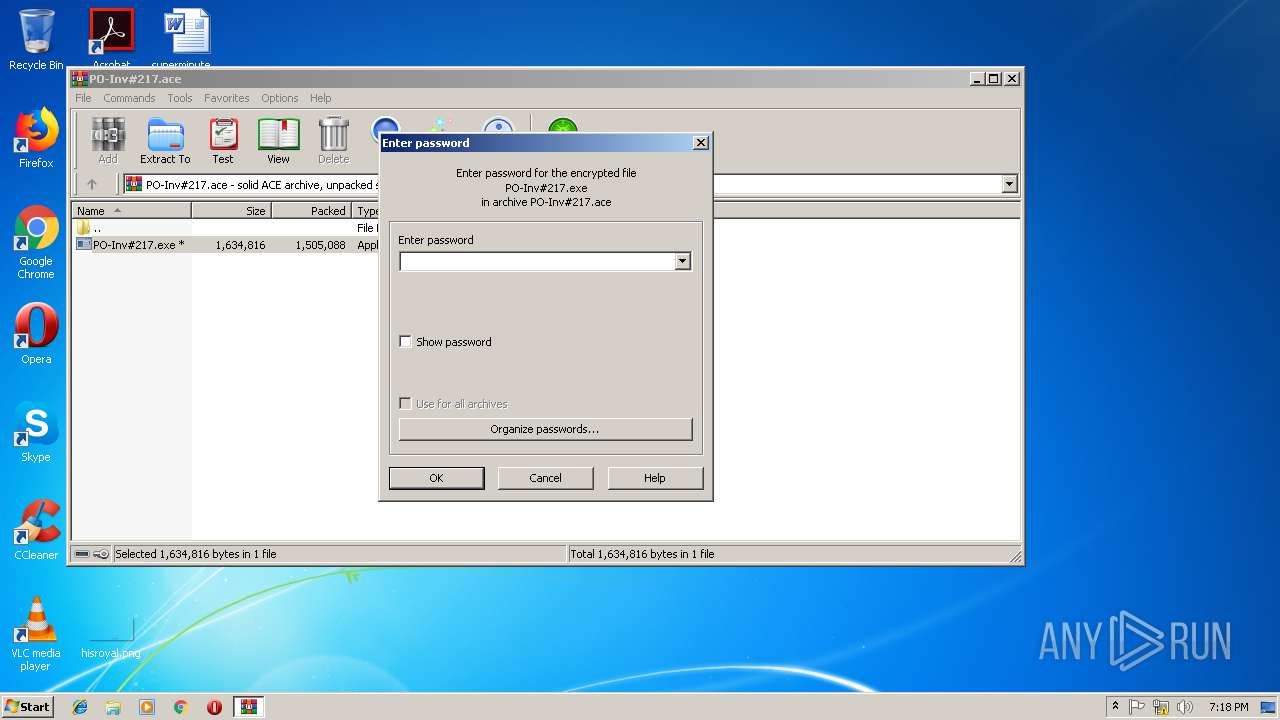
| 2640 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\PO-Inv#217.ace" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=880,11757578864931542103,10159547715694511402,131072 --enable-features=PasswordImport --service-pipe-token=74704B8F787B641688A47B82C519AEF3 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=74704B8F787B641688A47B82C519AEF3 --renderer-client-id=5 --mojo-platform-channel-handle=1920 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=880,11757578864931542103,10159547715694511402,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=AA28300C33E1DF40FB3A591A329FC341 --mojo-platform-channel-handle=3780 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3036 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\PO-Inv#217.ace" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3084 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1796 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
3 193
Read events
2 523
Write events
646
Delete events
24
Modification events
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | "90 |
Value: 22393000280C0000010000000000000000000000 | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 280C000030A276A0BEC7D40100000000 | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219915360 | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3112) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1313996821 | |||
Executable files
3
Suspicious files
70
Text files
103
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3112 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR6D12.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3112 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF46A83B3C59F8FCF4.TMP | — | |
MD5:— | SHA256:— | |||
| 3112 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFE84AAFC75AAA5E09.TMP | — | |
MD5:— | SHA256:— | |||
| 3112 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFEE08277917D58BCC.TMP | — | |
MD5:— | SHA256:— | |||
| 3112 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{46154140-B19E-4073-8CCF-296E8F951119}.tmp | — | |
MD5:— | SHA256:— | |||
| 3112 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3112 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Outlook\NoMail.srs | srs | |
MD5:— | SHA256:— | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PO-Inv#217.exe | executable | |
MD5:— | SHA256:— | |||
| 3300 | PO-Inv#217.exe | C:\Users\admin\AppData\Roaming\pco.exe | executable | |
MD5:— | SHA256:— | |||
| 3112 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\~Outlook Data File - NoMail.pst.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
37
DNS requests
24
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3112 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3300 | PO-Inv#217.exe | GET | 200 | 18.233.42.138:80 | http://checkip.amazonaws.com/ | US | text | 15 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3112 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3300 | PO-Inv#217.exe | 188.125.73.29:587 | smtp.aol.com | — | CH | unknown |
3024 | chrome.exe | 172.217.16.131:443 | www.google.de | Google Inc. | US | whitelisted |
3024 | chrome.exe | 172.217.22.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3024 | chrome.exe | 172.217.22.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3024 | chrome.exe | 172.217.16.142:443 | apis.google.com | Google Inc. | US | whitelisted |
3024 | chrome.exe | 172.217.18.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3024 | chrome.exe | 172.217.16.206:443 | consent.google.com | Google Inc. | US | whitelisted |
3024 | chrome.exe | 216.58.205.226:443 | adservice.google.fr | Google Inc. | US | whitelisted |
3024 | chrome.exe | 216.58.206.20:443 | virustotalcloud.appspot.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
smtp.aol.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3300 | PO-Inv#217.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3300 | PO-Inv#217.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
3300 | PO-Inv#217.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2 ETPRO signatures available at the full report