| File name: | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1 |
| Full analysis: | https://app.any.run/tasks/5b48631b-010e-4679-907c-485cb6be5142 |
| Verdict: | Malicious activity |
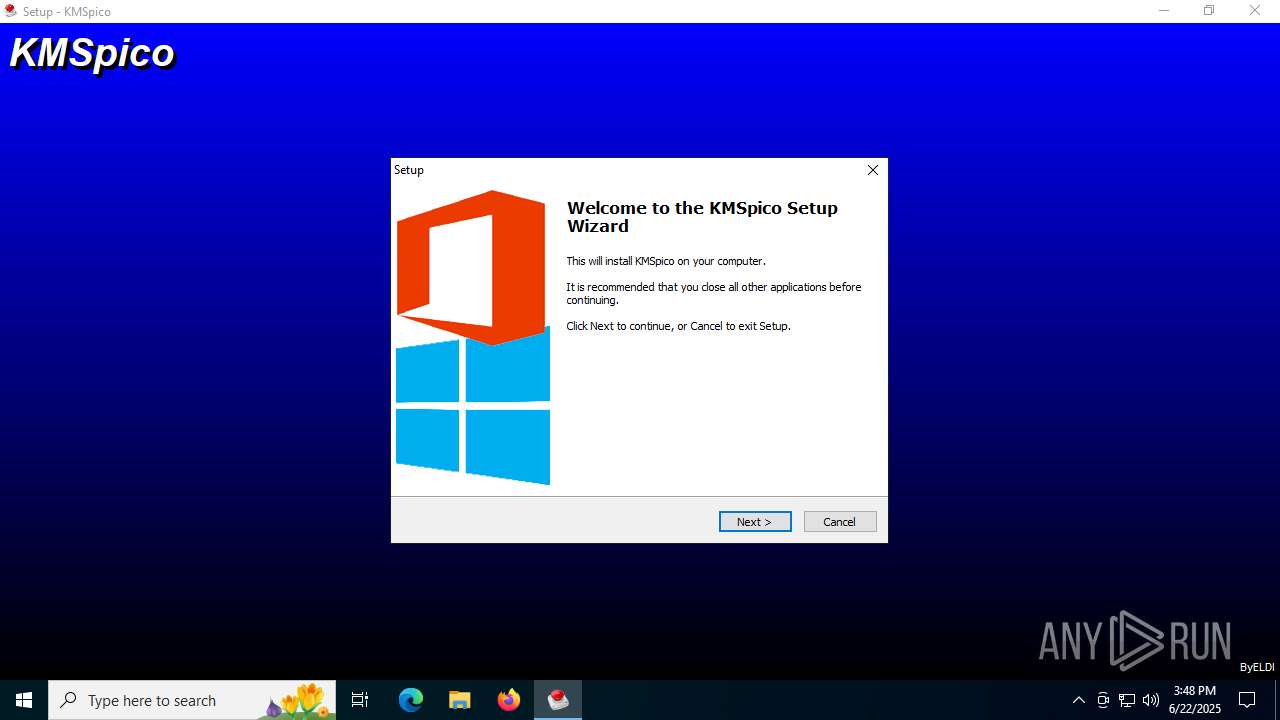
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | June 22, 2025, 15:48:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | DE130915BA884E252290A74787201D68 |
| SHA1: | D27C6EF969FEED767281FA5BCA9197537850E4B4 |
| SHA256: | 826BC445A8F02DFB4D83BF671621C612755A1E8EE8BC4D89BDE48418E83A81E1 |
| SSDEEP: | 98304:H6GavilSmy6ZD/ejjm1+CBviv+0x+ctRYeJ84wr/AYrvy48MnYbY2bz0JqB6yrqG:mhWaE5sV0h77q |
MALICIOUS
GENERIC has been found (auto)
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
Executing a file with an untrusted certificate
- KMSpico.exe (PID: 5080)
- KMSpico.exe (PID: 4040)
- KMSELDI.exe (PID: 3884)
- AutoPico.exe (PID: 316)
- AutoPico.exe (PID: 4312)
LUMMA mutex has been found
- core.exe (PID: 1212)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 5340)
Changes image file execution options
- KMSELDI.exe (PID: 3884)
- AutoPico.exe (PID: 4312)
Actions looks like stealing of personal data
- core.exe (PID: 1212)
Steals credentials from Web Browsers
- core.exe (PID: 1212)
Bypass execution policy to execute commands
- powershell.exe (PID: 6892)
Changes powershell execution policy (Bypass)
- core.exe (PID: 1212)
SUSPICIOUS
Executable content was dropped or overwritten
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.exe (PID: 1668)
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.exe (PID: 4040)
- KMSpico.tmp (PID: 4644)
- KMSELDI.exe (PID: 3884)
- KMSpico.exe (PID: 5080)
Reads the Windows owner or organization settings
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.tmp (PID: 4644)
Reads security settings of Internet Explorer
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.tmp (PID: 1096)
Process drops legitimate windows executable
- KMSpico.tmp (PID: 4644)
Modifies the phishing filter of IE
- KMSpico.tmp (PID: 4644)
Executing commands from ".cmd" file
- KMSpico.tmp (PID: 4644)
Starts CMD.EXE for commands execution
- KMSpico.tmp (PID: 4644)
Creates a new Windows service
- sc.exe (PID: 1324)
Starts SC.EXE for service management
- cmd.exe (PID: 7156)
Searches for installed software
- core.exe (PID: 1212)
Starts POWERSHELL.EXE for commands execution
- core.exe (PID: 1212)
INFO
Checks supported languages
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.exe (PID: 1668)
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.exe (PID: 4040)
- KMSpico.tmp (PID: 4644)
- UninsHs.exe (PID: 1356)
- KMSELDI.exe (PID: 3884)
- SECOH-QAD.exe (PID: 4768)
- AutoPico.exe (PID: 4312)
- KMSpico.tmp (PID: 1096)
- KMSpico.exe (PID: 5080)
- core.exe (PID: 1212)
Create files in a temporary directory
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.exe (PID: 1668)
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.exe (PID: 4040)
- KMSpico.tmp (PID: 4644)
- powershell.exe (PID: 6892)
- KMSpico.exe (PID: 5080)
Reads the computer name
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.tmp (PID: 1096)
- KMSpico.tmp (PID: 4644)
- core.exe (PID: 1212)
- KMSELDI.exe (PID: 3884)
- AutoPico.exe (PID: 4312)
Creates files or folders in the user directory
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
Creates a software uninstall entry
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.tmp (PID: 4644)
The sample compiled with english language support
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.tmp (PID: 4644)
Process checks computer location settings
- rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp (PID: 6360)
- KMSpico.tmp (PID: 1096)
Creates files in the program directory
- KMSpico.tmp (PID: 4644)
- KMSELDI.exe (PID: 3884)
- AutoPico.exe (PID: 4312)
Detects InnoSetup installer (YARA)
- KMSpico.exe (PID: 5080)
- KMSpico.tmp (PID: 1096)
- KMSpico.exe (PID: 4040)
- KMSpico.tmp (PID: 4644)
Reads the machine GUID from the registry
- core.exe (PID: 1212)
- KMSELDI.exe (PID: 3884)
- AutoPico.exe (PID: 4312)
Compiled with Borland Delphi (YARA)
- KMSpico.tmp (PID: 4644)
- KMSpico.tmp (PID: 1096)
Reads the software policy settings
- core.exe (PID: 1212)
- slui.exe (PID: 6260)
- powershell.exe (PID: 6892)
Application launched itself
- chrome.exe (PID: 768)
- chrome.exe (PID: 1932)
- chrome.exe (PID: 5772)
- chrome.exe (PID: 7336)
- msedge.exe (PID: 4088)
- msedge.exe (PID: 6572)
- msedge.exe (PID: 8188)
- msedge.exe (PID: 7312)
- msedge.exe (PID: 7120)
- msedge.exe (PID: 7072)
Launching a file from Task Scheduler
- cmd.exe (PID: 5340)
Manual execution by a user
- AutoPico.exe (PID: 316)
- OpenWith.exe (PID: 5876)
Reads product name
- KMSELDI.exe (PID: 3884)
- AutoPico.exe (PID: 4312)
Reads Environment values
- KMSELDI.exe (PID: 3884)
- AutoPico.exe (PID: 4312)
Reads Microsoft Office registry keys
- KMSELDI.exe (PID: 3884)
- OpenWith.exe (PID: 5876)
- AutoPico.exe (PID: 4312)
Reads security settings of Internet Explorer
- powershell.exe (PID: 6892)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:01:08 15:36:35+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 684032 |
| InitializedDataSize: | 159744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7f98 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | MyApp Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | MyApp |
| ProductVersion: | 1.0 |
Total processes
230
Monitored processes
86
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3800,i,1974324969655375452,1207019464760543659,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3936 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 316 | "C:\Program Files\KMSpico\AutoPico.exe" | C:\Program Files\KMSpico\AutoPico.exe | — | explorer.exe | |||||||||||
User: admin Company: @ByELDI Integrity Level: MEDIUM Description: AutoPico Exit code: 3221226540 Version: 16.1.0.0 Modules
| |||||||||||||||
| 768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | core.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1028 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2224,i,3011946205692960363,6602653786411621175,262144 --variations-seed-version --mojo-platform-channel-handle=2552 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1096 | "C:\Users\admin\AppData\Local\Temp\is-H1C10.tmp\KMSpico.tmp" /SL5="$4038E,2952592,69120,C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe" | C:\Users\admin\AppData\Local\Temp\is-H1C10.tmp\KMSpico.tmp | — | KMSpico.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1212 | "C:\Users\admin\AppData\Roaming\MyApp\core.exe" | C:\Users\admin\AppData\Roaming\MyApp\core.exe | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | ||||||||||||
User: admin Company: CrypticStream Collective Integrity Level: MEDIUM Description: Encodes synced Matrix matrices Version: 2.3.277.3726 Modules
| |||||||||||||||
| 1232 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --edge-skip-compat-layer-relaunch | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1324 | sc create "Service KMSELDI" binPath= "C:\Program Files\KMSpico\Service_KMS.exe" type= own error= normal start= auto DisplayName= "Service KMSELDI" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | "C:\Program Files\KMSpico\UninsHs.exe" /r0=KMSpico,default,C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe | C:\Program Files\KMSpico\UninsHs.exe | — | KMSpico.tmp | |||||||||||
User: admin Company: Han-soft Integrity Level: HIGH Description: Uninstall for InnoSetup by Han-soft Exit code: 0 Version: 2.1.0.283 Modules
| |||||||||||||||
| 1488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=4888,i,1974324969655375452,1207019464760543659,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4868 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
32 237
Read events
32 106
Write events
126
Delete events
5
Modification events
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.4.0 | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Roaming\MyApp | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Roaming\MyApp\ | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: MyApp | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: default | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | DisplayName |
Value: MyApp version 1.0 | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Roaming\MyApp\unins000.exe | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Roaming\MyApp\unins000.exe" | |||
| (PID) Process: | (6360) rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Roaming\MyApp\unins000.exe" /SILENT | |||
Executable files
45
Suspicious files
137
Text files
875
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | C:\Users\admin\AppData\Roaming\MyApp\data\is-SSFRD.tmp | executable | |
MD5:A02164371A50C5FF9FA2870EF6E8CFA3 | SHA256:64C731ADBE1B96CB5765203B1E215093DCF268D020B299445884A4AE62ED2D3A | |||
| 6360 | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | C:\Users\admin\AppData\Roaming\MyApp\is-NDNV9.tmp | executable | |
MD5:4134EC81A9D645602B1FA265F98FBF35 | SHA256:69966257CE41717F2121EA1F03F8BFA1486423ACECFCC977DD9F1E157C911AD4 | |||
| 6360 | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | C:\Users\admin\AppData\Roaming\MyApp\is-V4BC9.tmp | executable | |
MD5:AE3133110DC844B7DD7AE8C73721FF99 | SHA256:08F38DA4533A42D60EAF4DFFE1321EF69E8348BFE1CB400F7CE18C0ABDF1AD3C | |||
| 6360 | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | C:\Users\admin\AppData\Local\Temp\is-8O67T.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1668 | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.exe | C:\Users\admin\AppData\Local\Temp\is-NF9KH.tmp\rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | executable | |
MD5:E4C43138CCB8240276872FD1AEC369BE | SHA256:46BE5E3F28A5E4ED63D66B901D927C25944B4DA36EFFEA9C97FB05994360EDF5 | |||
| 6360 | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | C:\Users\admin\AppData\Roaming\MyApp\core.exe | executable | |
MD5:AE3133110DC844B7DD7AE8C73721FF99 | SHA256:08F38DA4533A42D60EAF4DFFE1321EF69E8348BFE1CB400F7CE18C0ABDF1AD3C | |||
| 6360 | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | C:\Users\admin\AppData\Roaming\MyApp\unins000.dat | binary | |
MD5:CB9A28840BE0F40B5F29D25953FC17B1 | SHA256:72DBAF6F5B844CB0F77BCC4A9E43BA82FF21B8D4A1A3A59E05A179945A0DCDA4 | |||
| 4040 | KMSpico.exe | C:\Users\admin\AppData\Local\Temp\is-JQP9Q.tmp\KMSpico.tmp | executable | |
MD5:1778C1F66FF205875A6435A33229AB3C | SHA256:95C06ACAC4FE4598840E5556F9613D43AA1039C52DAC64536F59E45A70F79DA6 | |||
| 6360 | rl_826bc445a8f02dfb4d83bf671621c612755a1e8ee8bc4d89bde48418e83a81e1.tmp | C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe | executable | |
MD5:A02164371A50C5FF9FA2870EF6E8CFA3 | SHA256:64C731ADBE1B96CB5765203B1E215093DCF268D020B299445884A4AE62ED2D3A | |||
| 4644 | KMSpico.tmp | C:\Program Files\KMSpico\is-345UN.tmp | executable | |
MD5:30C7E8E918403B9247315249A8842CE5 | SHA256:6D4FA6727CA952B7B44FA9F3538D84B64E06C76908C76FADE7846532A7115A49 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
112
TCP/UDP connections
176
DNS requests
142
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1644 | RUXIMICS.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1644 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.132:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.134:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.67:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.140:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1644 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1644 | RUXIMICS.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
aculpr.xyz |
| unknown |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |