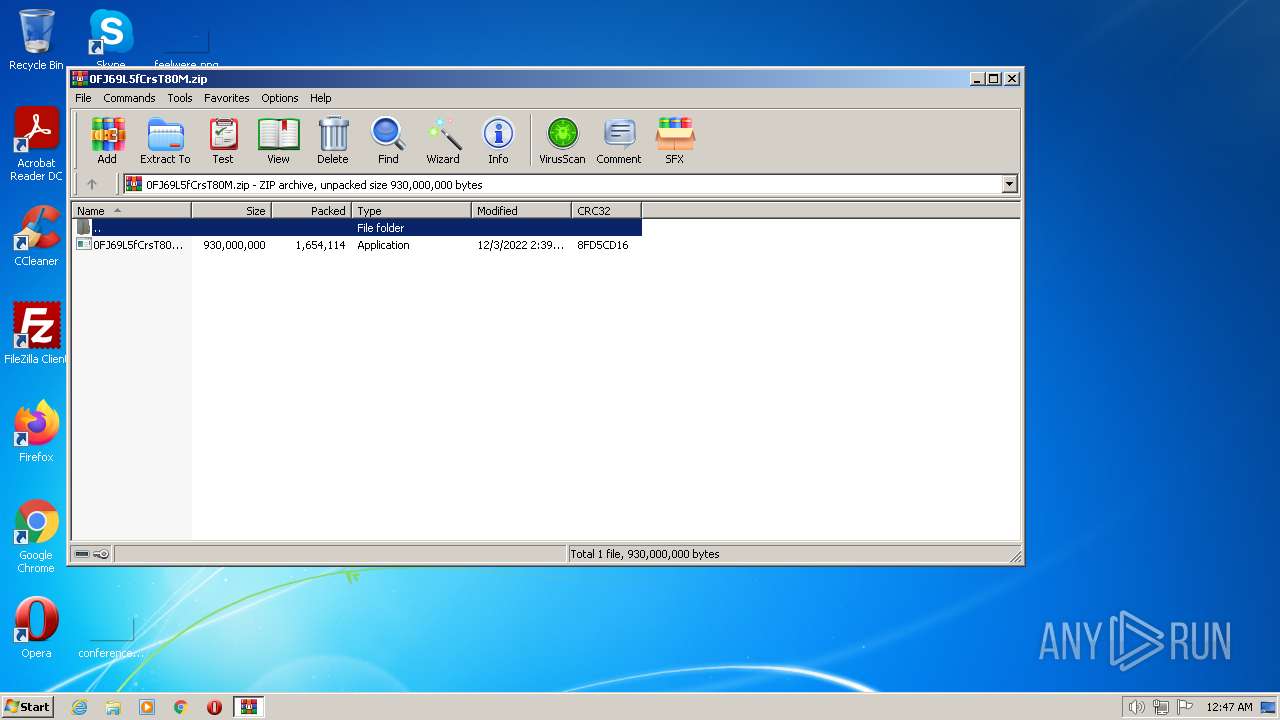
| File name: | 0FJ69L5fCrsT80M.zip |
| Full analysis: | https://app.any.run/tasks/66159012-169f-4edd-bb57-29d138b78e75 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | December 06, 2022, 00:47:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3635B794FD3B3BDA88C7A23DEE6A8543 |
| SHA1: | 35EF70A3DD12ECC6A03B181B3C94DFEC49EB0C28 |
| SHA256: | 81E0AC6719F690B77C048C0D9DEBC47E7DD6649F1A1F3C5690FFD22F954718FA |
| SSDEEP: | 24576:bUxJhXZLrIJyDP7OgTbDPISVXgE+MTXLjP:bU3hpLrLPIq+WXLjP |
MALICIOUS
Connects to the CnC server
- 0FJ69L5fCrsT80M.exe (PID: 2360)
REDLINE was detected
- 0FJ69L5fCrsT80M.exe (PID: 2360)
Steals credentials from Web Browsers
- 0FJ69L5fCrsT80M.exe (PID: 2360)
REDLINE detected by memory dumps
- 0FJ69L5fCrsT80M.exe (PID: 2360)
SUSPICIOUS
Application launched itself
- 0FJ69L5fCrsT80M.exe (PID: 3444)
Reads the Internet Settings
- 0FJ69L5fCrsT80M.exe (PID: 2360)
Reads settings of System Certificates
- 0FJ69L5fCrsT80M.exe (PID: 2360)
Reads browser cookies
- 0FJ69L5fCrsT80M.exe (PID: 2360)
Searches for installed software
- 0FJ69L5fCrsT80M.exe (PID: 2360)
INFO
Manual execution by a user
- 0FJ69L5fCrsT80M.exe (PID: 3444)
Checks supported languages
- 0FJ69L5fCrsT80M.exe (PID: 2360)
- 0FJ69L5fCrsT80M.exe (PID: 3444)
Reads the computer name
- 0FJ69L5fCrsT80M.exe (PID: 3444)
- 0FJ69L5fCrsT80M.exe (PID: 2360)
Reads Environment values
- 0FJ69L5fCrsT80M.exe (PID: 2360)
Reads product name
- 0FJ69L5fCrsT80M.exe (PID: 2360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(2360) 0FJ69L5fCrsT80M.exe
C2 (1)217.160.100.70:80
BotnetNaver
Err_msg
Auth_value766e7b189c56b4df0a5966657eb26e9f
US (181)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Host
Port
:
User
Pass
cookies.sqlite
GetDirectories
Entity12
EnumerateDirectories
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrhKeyyptDeshKeytroyKhKeyey
hKey
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
766e7b189c56b4df0a5966657eb26e9f
Authorization
ns1
UNKNWON
DxgsXg4YLF8PMV0VDzYoGAwIKFsNNihQ
Fh8vXxgqIFA=
Brim
Yandex\YaAddon
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
.
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
1
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
https://api.ip.sb/ip
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
Name
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
The entered value cannot be less than 1 or greater than 20.
#F25D59
Segoe UI
#FFFFFF
#323A3D
Tahoma
#696969
#A0A0A0
−
Marlett
2
#C75050
⨉
#72767F
#FAFAFA
#DE5954
#F46662
#F68F84
#292C3D
#3C3F50
#747881
#2B3043
#7F838C
#AAABB0
Microsoft Sans Serif
Network\
String
Replace
80
81
0.0.0.0
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1756 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\0FJ69L5fCrsT80M.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2360 | "C:\Users\admin\Desktop\0FJ69L5fCrsT80M.exe" | C:\Users\admin\Desktop\0FJ69L5fCrsT80M.exe | 0FJ69L5fCrsT80M.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: proyecto Exit code: 0 Version: 1.0.0.0 Modules
RedLine(PID) Process(2360) 0FJ69L5fCrsT80M.exe C2 (1)217.160.100.70:80 BotnetNaver Err_msg Auth_value766e7b189c56b4df0a5966657eb26e9f US (181) LEnvironmentogiEnvironmentn DatEnvironmenta Environment WSystem.Texteb DatSystem.Texta System.Text CoCryptographyokieCryptographys Cryptography ExtGenericension CooGenerickies Generic OFileInfopeFileInfora GFileInfoX StabFileInfole FileInfo OpLinqera GLinqX Linq ApGenericpDaGenericta\RGenericoamiGenericng\ Network Extension UNKNOWN cFileStreamredFileStreamit_cFileStreamardFileStreams FileStream \ Host Port : User Pass cookies.sqlite GetDirectories Entity12 EnumerateDirectories String.Replace String.Remove bcrFileStream.IOypt.dFileStream.IOll FileStream.IO BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder string.Empty BCruintyptCloseAlgorituinthmProvuintider uint BCrUnmanagedTypeyptDecrUnmanagedTypeypt UnmanagedType BCrhKeyyptDeshKeytroyKhKeyey hKey BCpszPropertyryptGepszPropertytPropepszPropertyrty pszProperty BCEncodingryptSEncodingetPrEncodingoperEncodingty Encoding BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey bMasterKey windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob - {0} net.tcp:// / localhost 766e7b189c56b4df0a5966657eb26e9f Authorization ns1 UNKNWON DxgsXg4YLF8PMV0VDzYoGAwIKFsNNihQ Fh8vXxgqIFA= Brim Yandex\YaAddon asf *wallet* ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu... _ T e l gr am . ex \TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata 1 string.Replace %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl serviceInterface.Extension ProldCharotonVoldCharPN oldChar nSystem.CollectionspvoSystem.Collections* System.Collections ( UNIQUE cstringmstringd string /ProcessC Process Process | " Armenia Azerbaijan Belarus Kazakhstan Kyrgyzstan Moldova Tajikistan Uzbekistan Ukraine Russia https://api.ip.sb/ip SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor System.Windows.Forms roSystem.Linqot\CISystem.LinqMV2 System.Linq SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller AdapterRAM Name SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente System.Management SerialNumber SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId=' System.Text.RegularExpressions ' FileSystem SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId=' System. ExecutablePath [ ] Concat0 MConcatb oConcatr Concat0 Concat SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem Memory {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ The entered value cannot be less than 1 or greater than 20. #F25D59 Segoe UI #FFFFFF #323A3D Tahoma #696969 #A0A0A0 − Marlett 2 #C75050 ⨉ #72767F #FAFAFA #DE5954 #F46662 #F68F84 #292C3D #3C3F50 #747881 #2B3043 #7F838C #AAABB0 Microsoft Sans Serif Network\ String Replace 80 81 0.0.0.0 | |||||||||||||||
| 3444 | "C:\Users\admin\Desktop\0FJ69L5fCrsT80M.exe" | C:\Users\admin\Desktop\0FJ69L5fCrsT80M.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: proyecto Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
5 165
Read events
5 116
Write events
49
Delete events
0
Modification events
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\0FJ69L5fCrsT80M.zip | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
27
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2360 | 0FJ69L5fCrsT80M.exe | 217.160.100.70:80 | — | IONOS SE | DE | malicious |
2360 | 0FJ69L5fCrsT80M.exe | 172.67.75.172:443 | api.ip.sb | CLOUDFLARENET | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ip.sb |
| whitelisted |
Threats
27 ETPRO signatures available at the full report