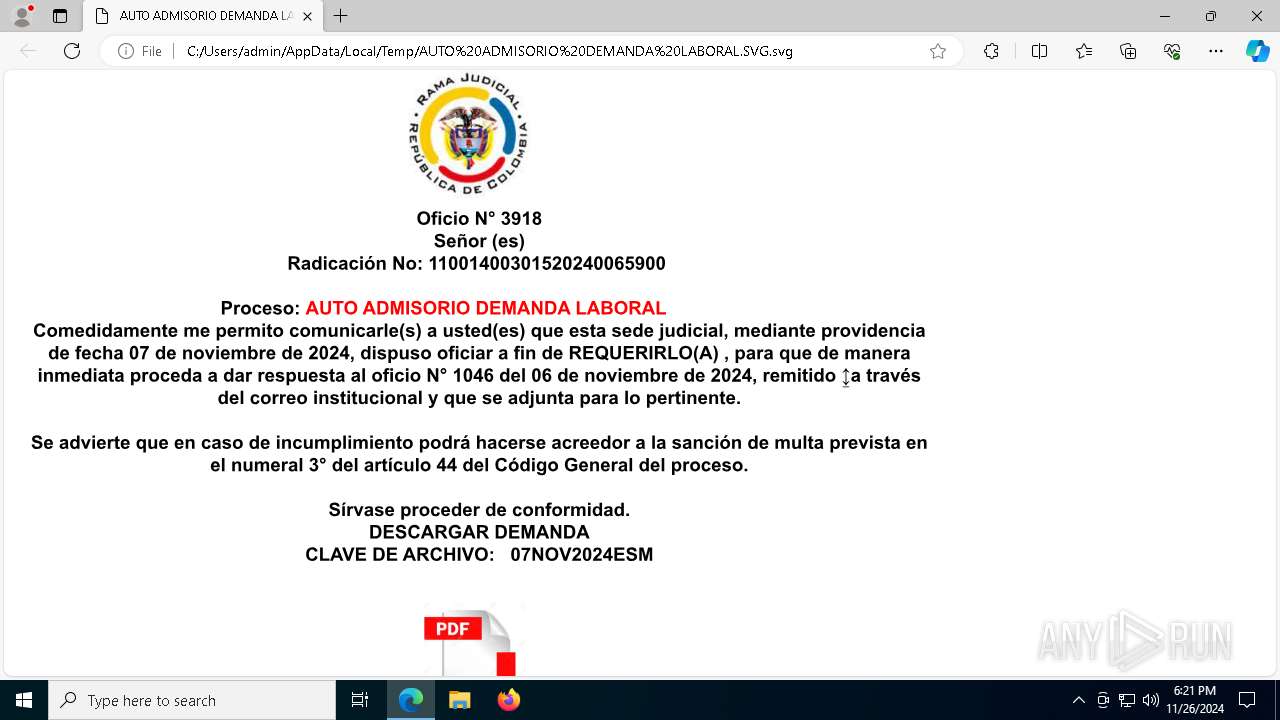
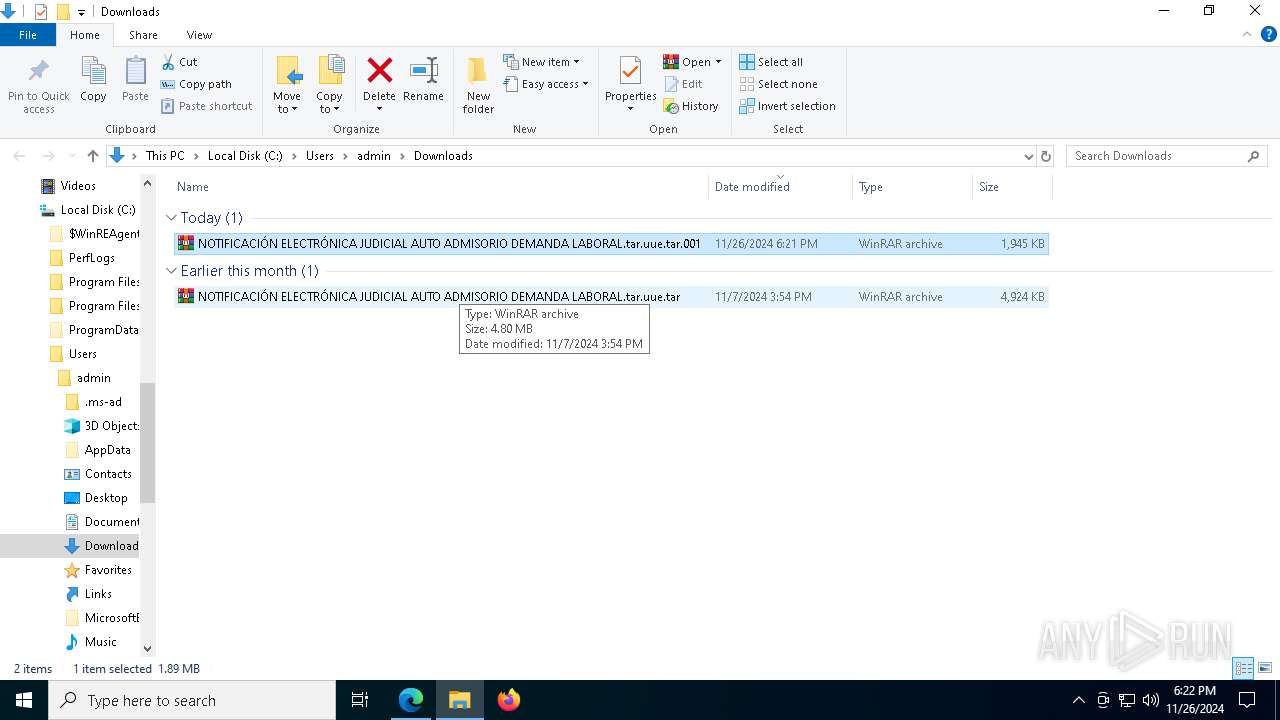
| File name: | AUTO ADMISORIO DEMANDA LABORAL.SVG |
| Full analysis: | https://app.any.run/tasks/7a81a92f-415b-4fda-9fd5-92e3f841e3f7 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | November 26, 2024, 18:21:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/svg+xml |
| File info: | SVG Scalable Vector Graphics image |
| MD5: | 51BB8E20ED473A08553C7DBD575050DE |
| SHA1: | 0C8506C50AA891298D665B7F6927215A2668150C |
| SHA256: | 81CED42E28C0BCC03F07E227D3357BCCF5AE9666979DF6B3AF06E4F315C1A8E7 |
| SSDEEP: | 3072:O7ZHKZA/YokgsUW5eMQATO/iHhokPWm20ftLT719zmdkg+EK/AT9Ic7x8kg36zTD:+HKuZ |
MALICIOUS
Executing a file with an untrusted certificate
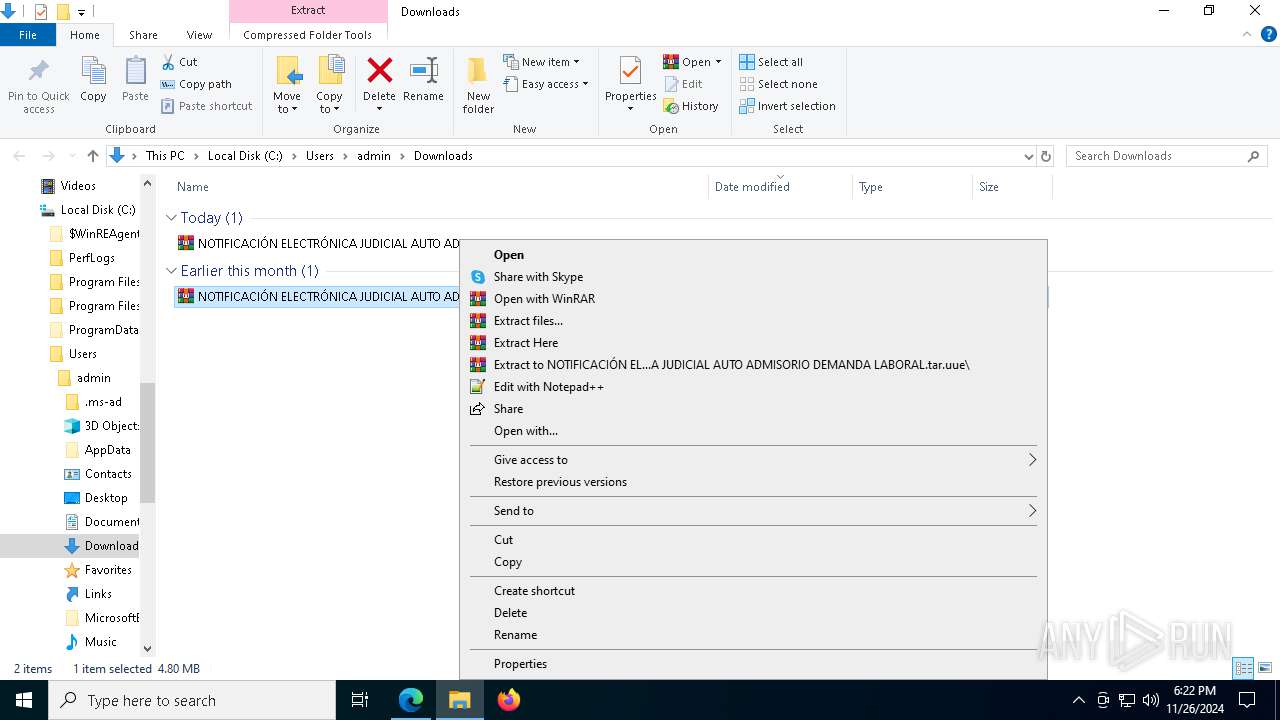
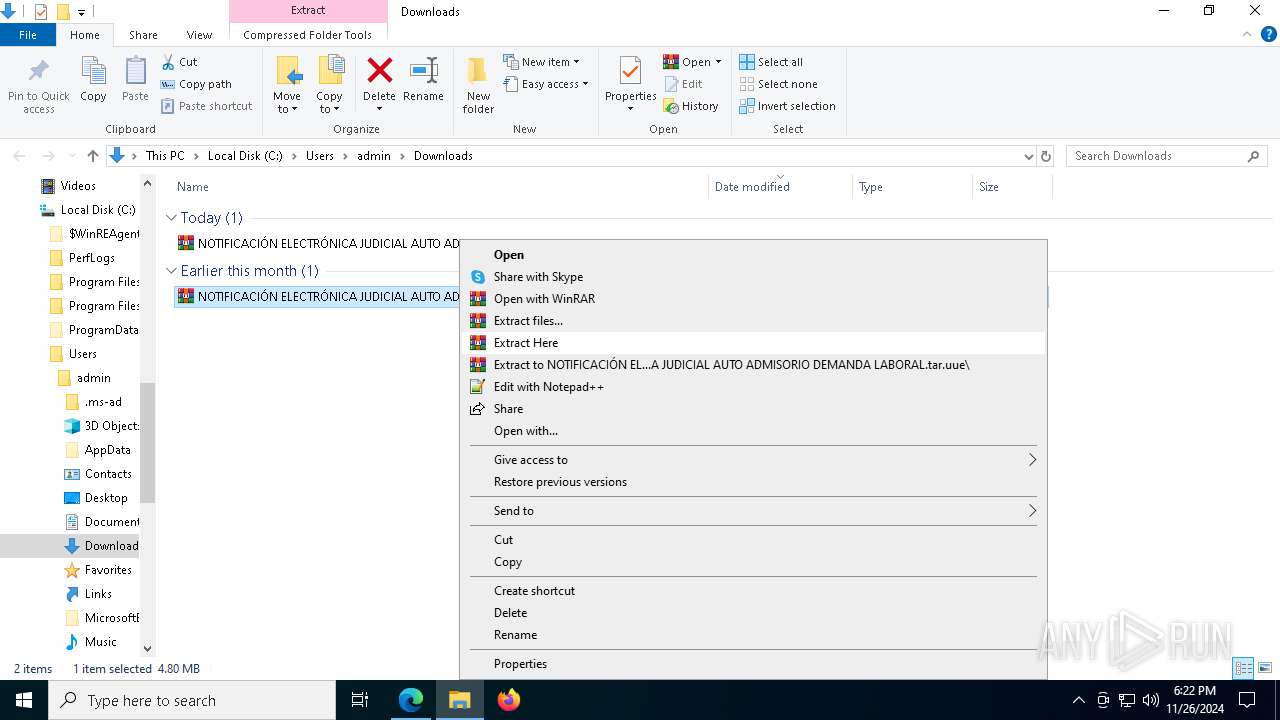
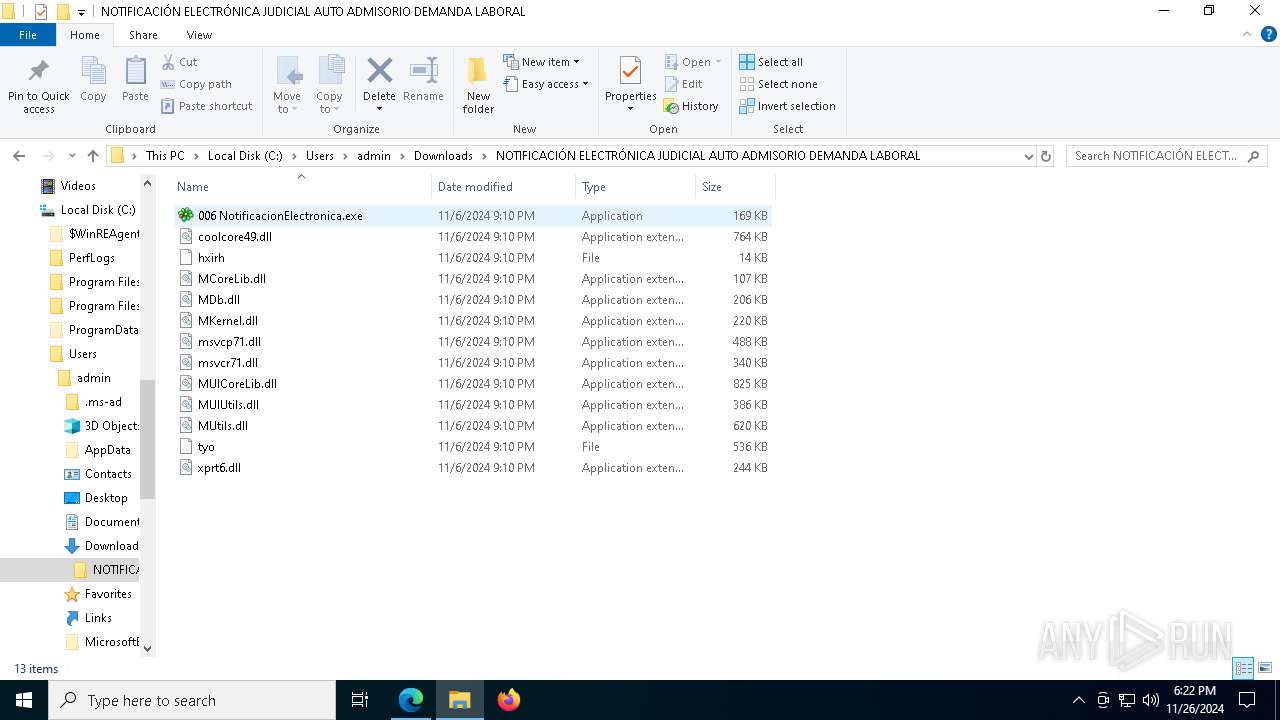
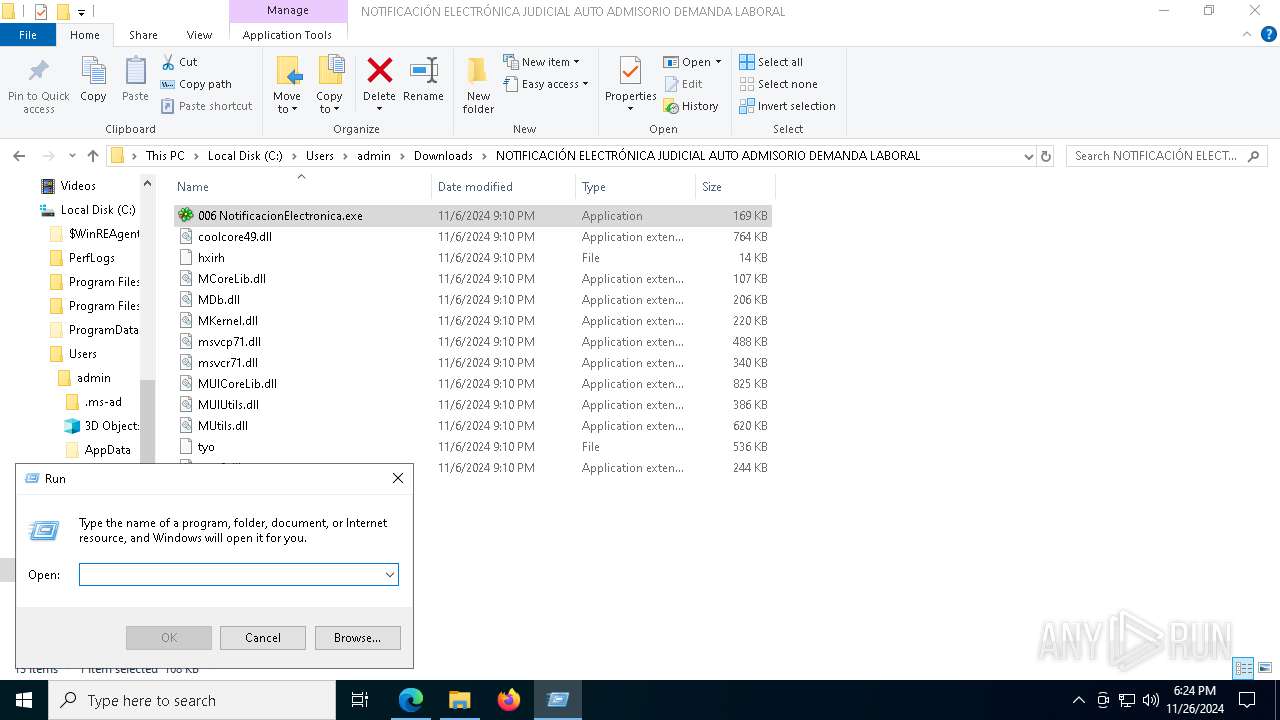
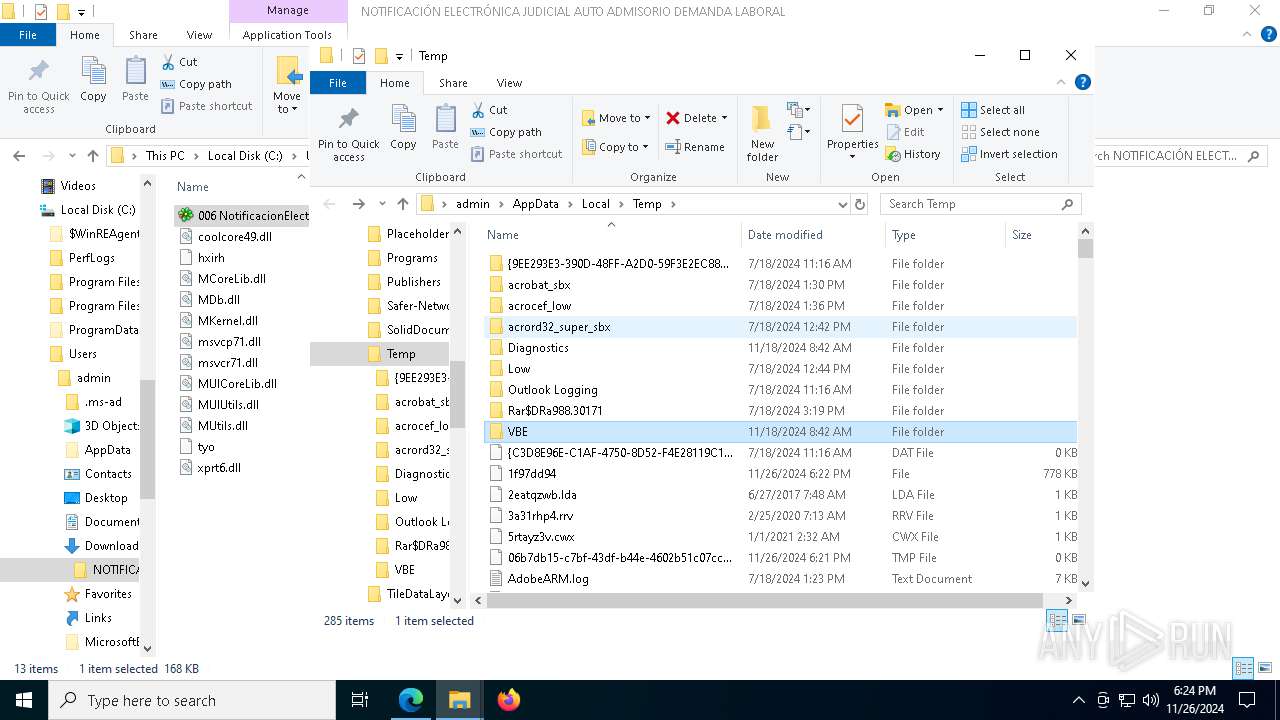
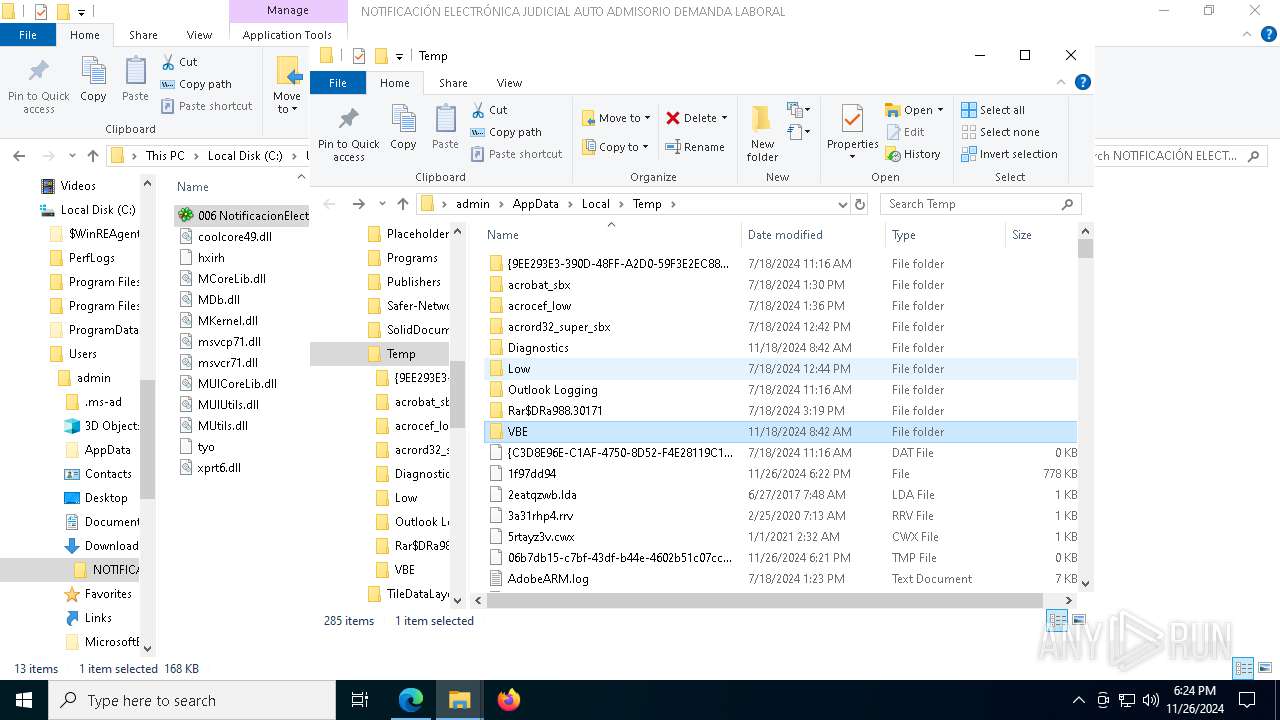
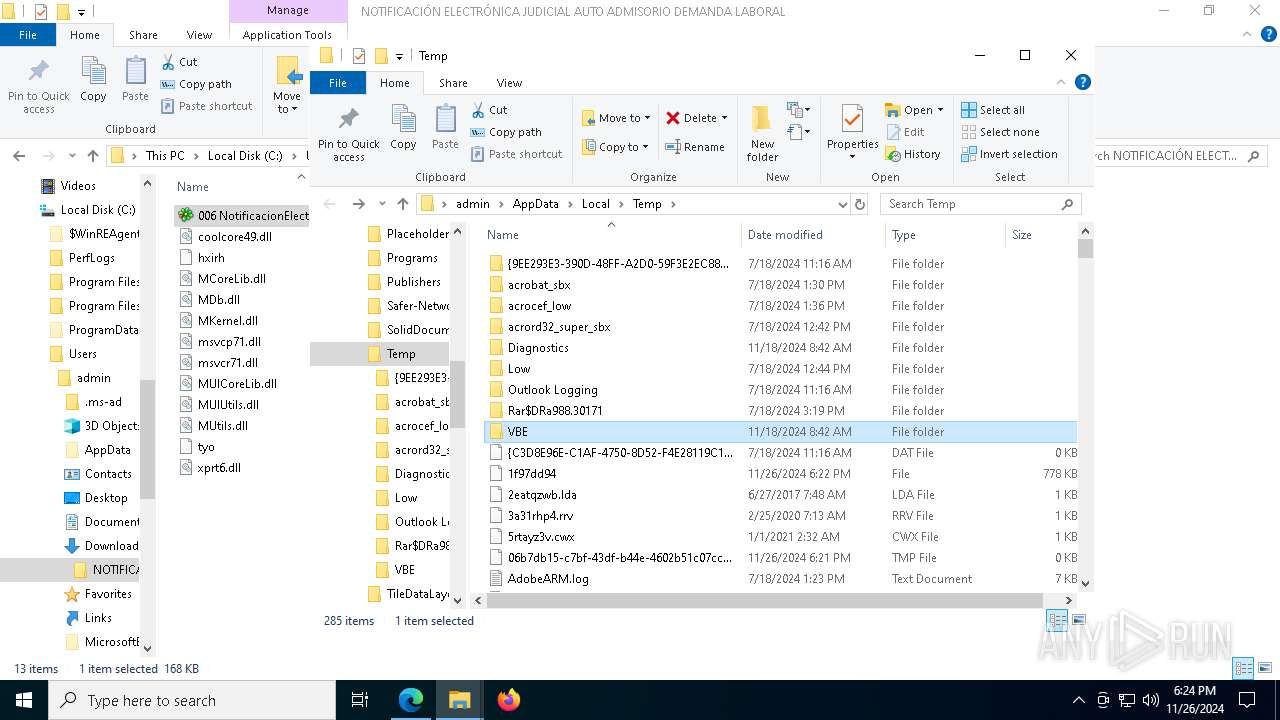
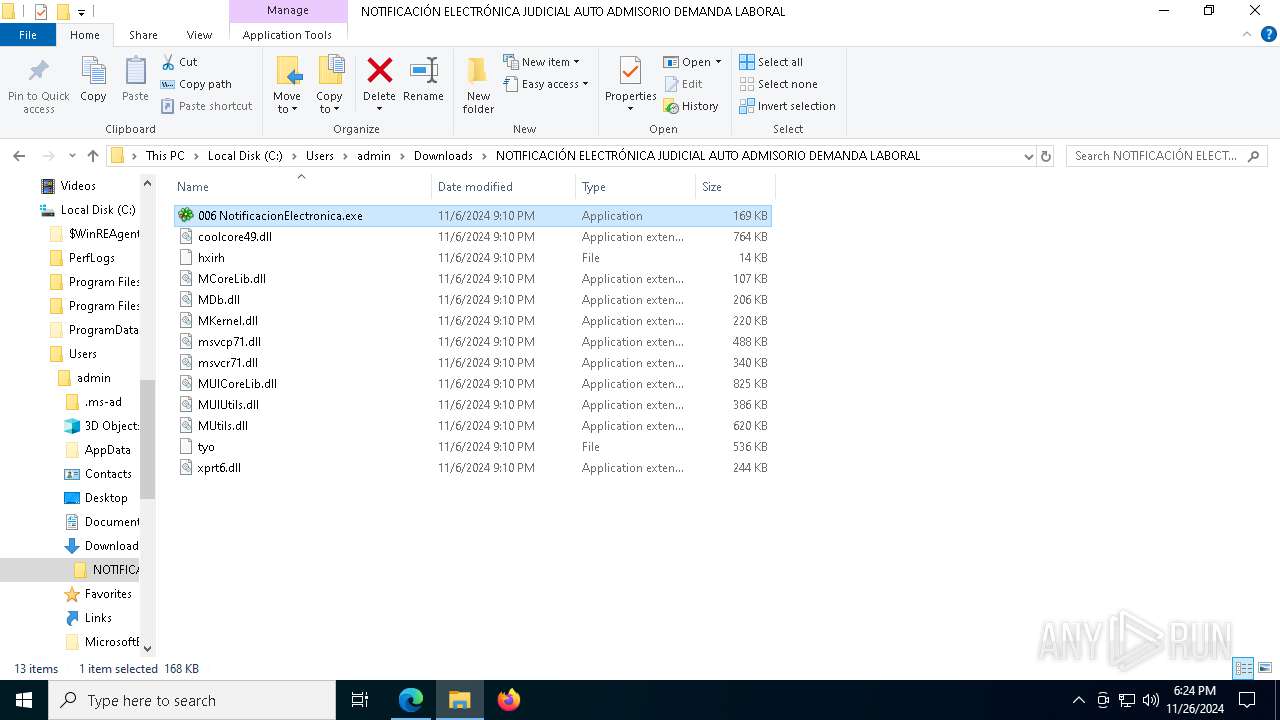
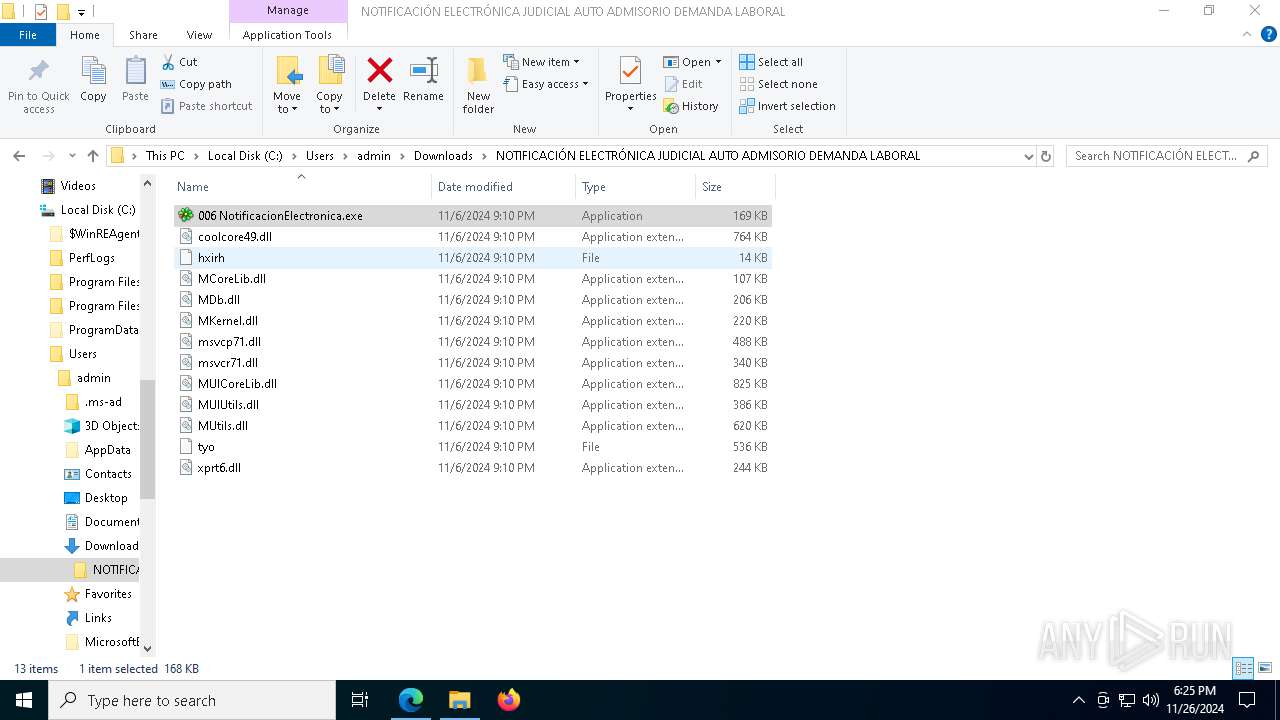
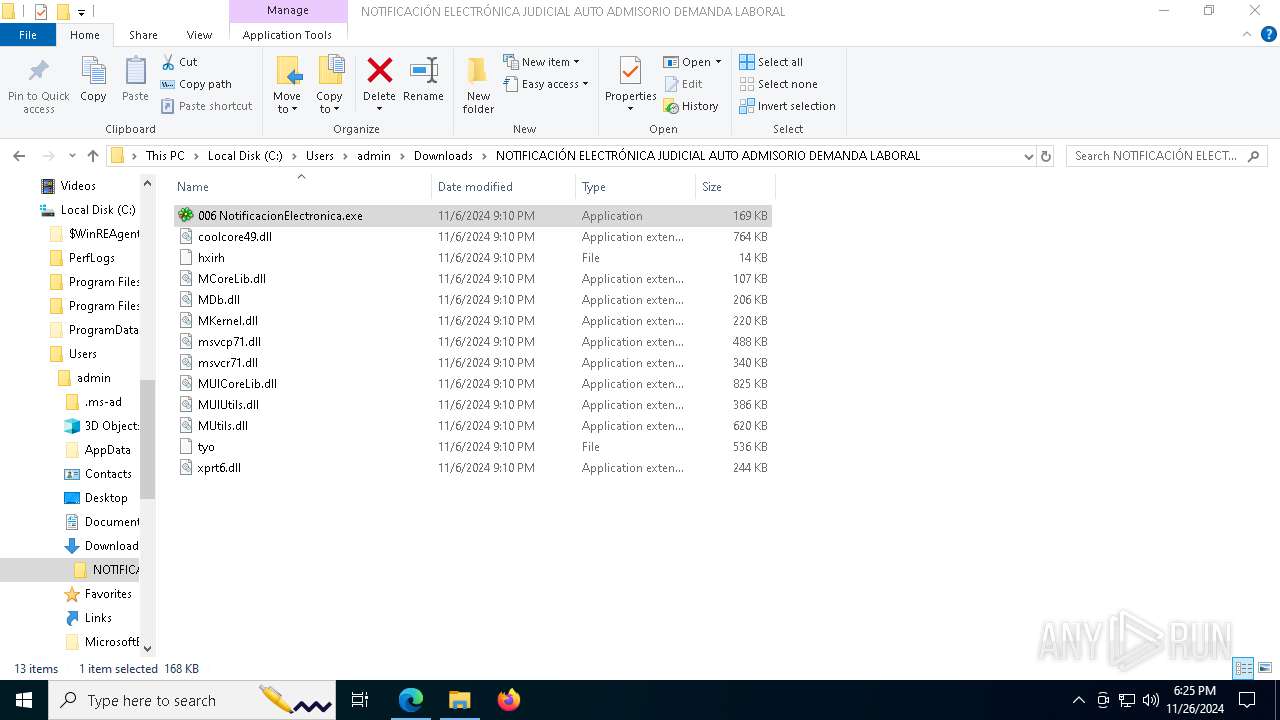
- 006 NotificacionElectronica.exe (PID: 7976)
ASYNCRAT has been detected (MUTEX)
- MSBuild.exe (PID: 4724)
ASYNCRAT has been detected (YARA)
- MSBuild.exe (PID: 4724)
SUSPICIOUS
Executable content was dropped or overwritten
- 006 NotificacionElectronica.exe (PID: 7976)
Starts CMD.EXE for commands execution
- 006 NotificacionElectronica.exe (PID: 7976)
The process drops C-runtime libraries
- 006 NotificacionElectronica.exe (PID: 7976)
Process drops legitimate windows executable
- 006 NotificacionElectronica.exe (PID: 7976)
- WinRAR.exe (PID: 3524)
Connects to unusual port
- MSBuild.exe (PID: 4724)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3524)
Sends debugging messages
- mmc.exe (PID: 7948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .svg | | | Scalable Vector Graphics (var.1) (100) |
|---|
EXIF
SVG
| Fill: | none |
|---|---|
| Stroke: | none |
| Stroke-linecap: | square |
| Stroke-miterlimit: | 10 |
| SVGVersion: | 1.1 |
| Viewbox: | 0.0 0.0 960.0 720.0 |
| Xmlns: | http://www.w3.org/2000/svg |
Total processes
191
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
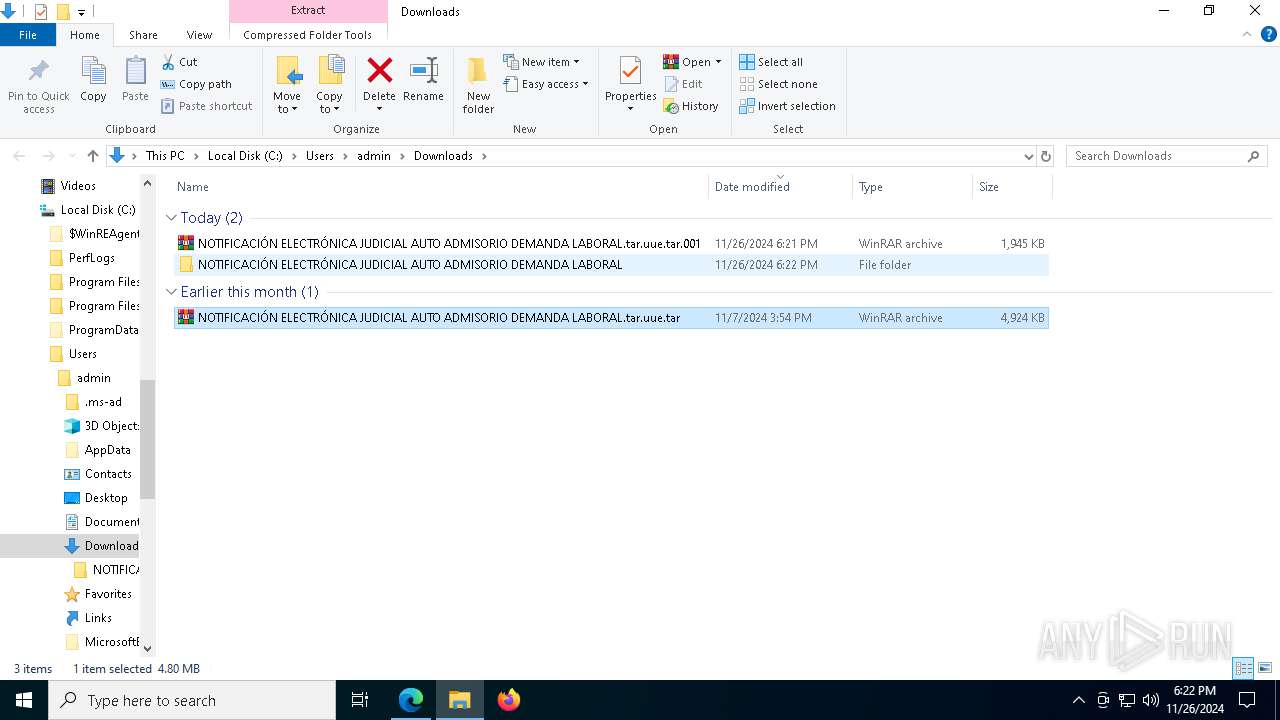
| 3524 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL.tar.uue.tar" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5208 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | 006 NotificacionElectronica.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
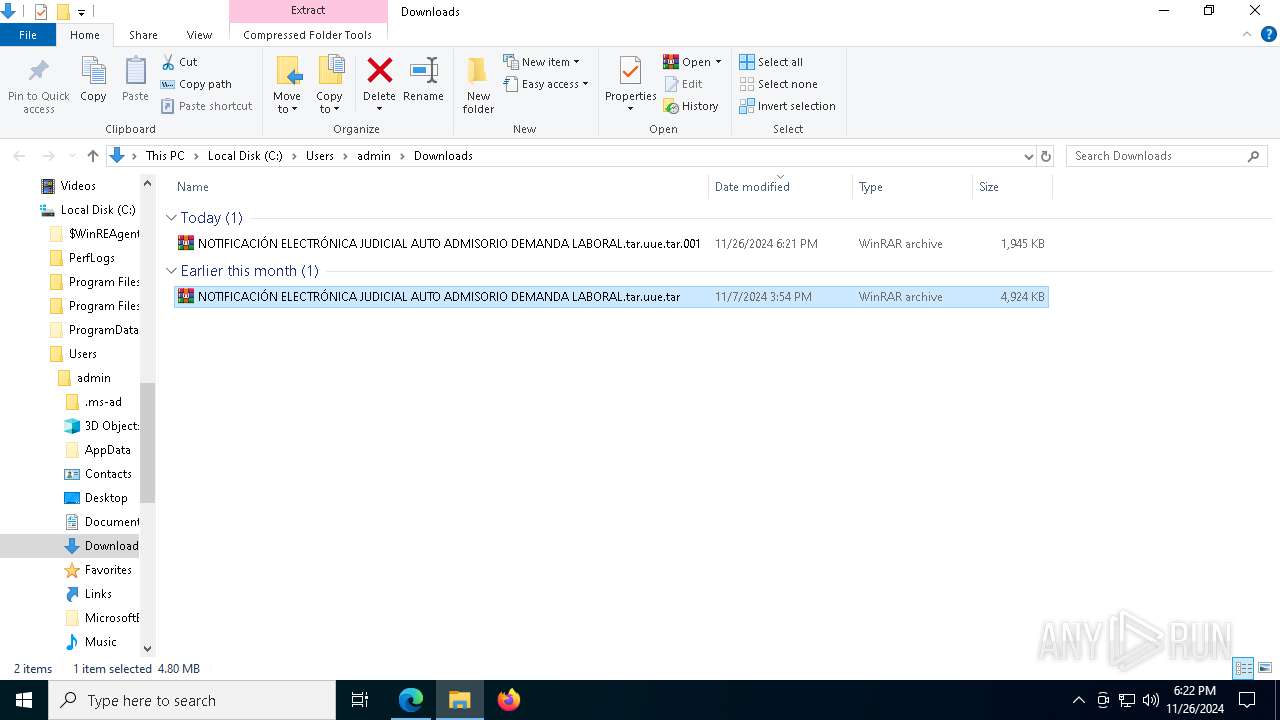
| 6568 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL.tar.uue.tar.001" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
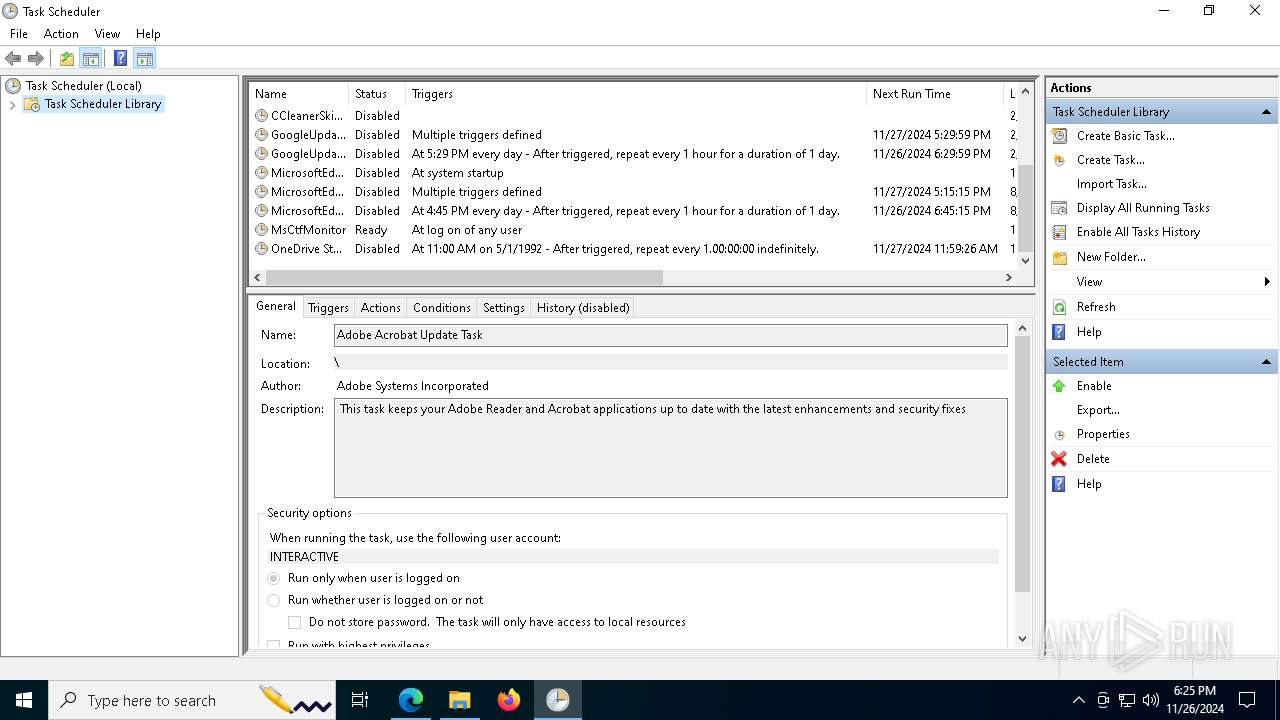
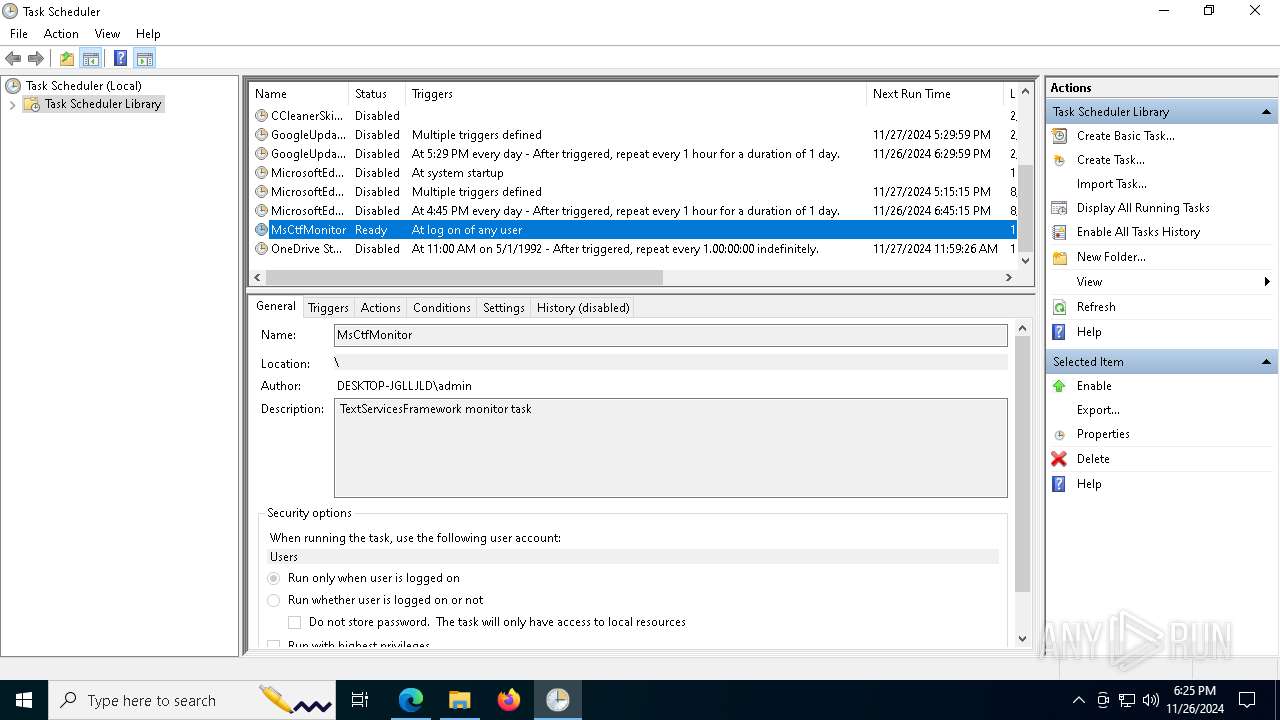
| 7368 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7948 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
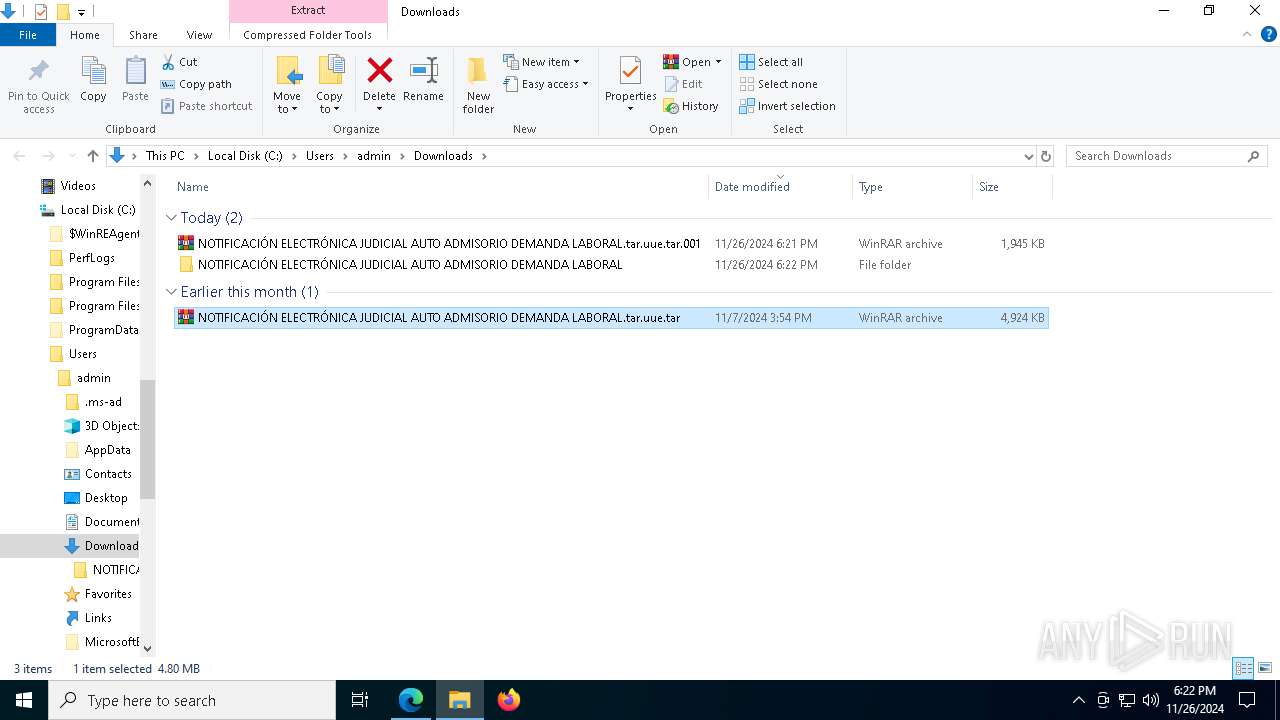
| 7976 | "C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\006 NotificacionElectronica.exe" | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\006 NotificacionElectronica.exe | explorer.exe | ||||||||||||
User: admin Company: ICQ, Inc. Integrity Level: MEDIUM Description: ICQ Library Exit code: 1 Version: 6.5.0.1005 Modules
| |||||||||||||||
Total events
1 927
Read events
1 912
Write events
14
Delete events
1
Modification events
| (PID) Process: | (6568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6568) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7948) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | HelpTopic |
Value: C:\WINDOWS\Help\taskscheduler.chm | |||
Executable files
21
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
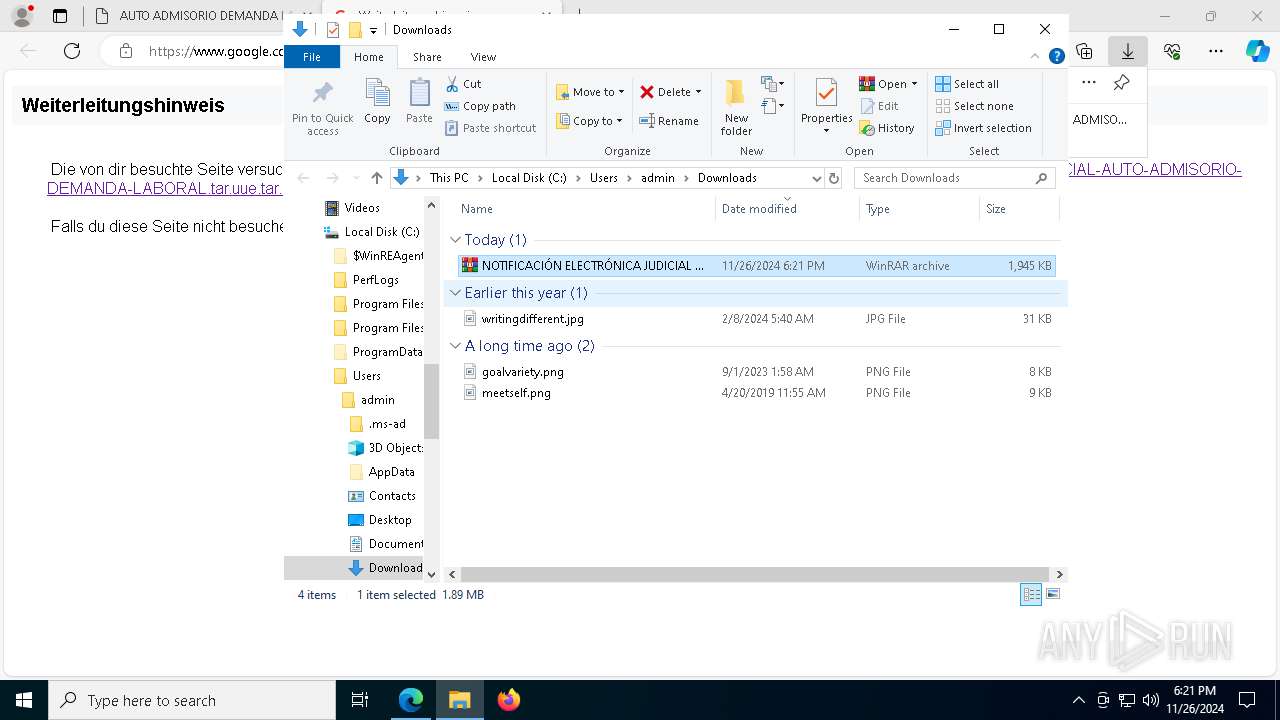
| 6568 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL.tar.uue.tar | — | |
MD5:— | SHA256:— | |||
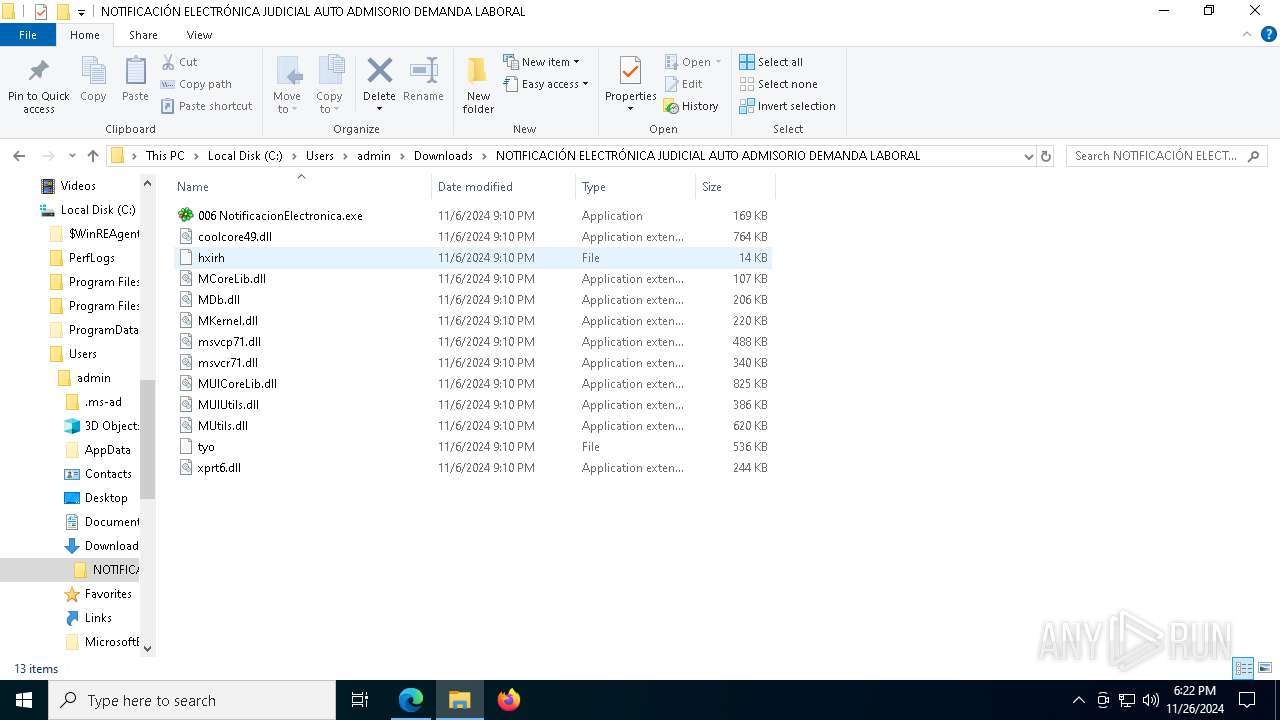
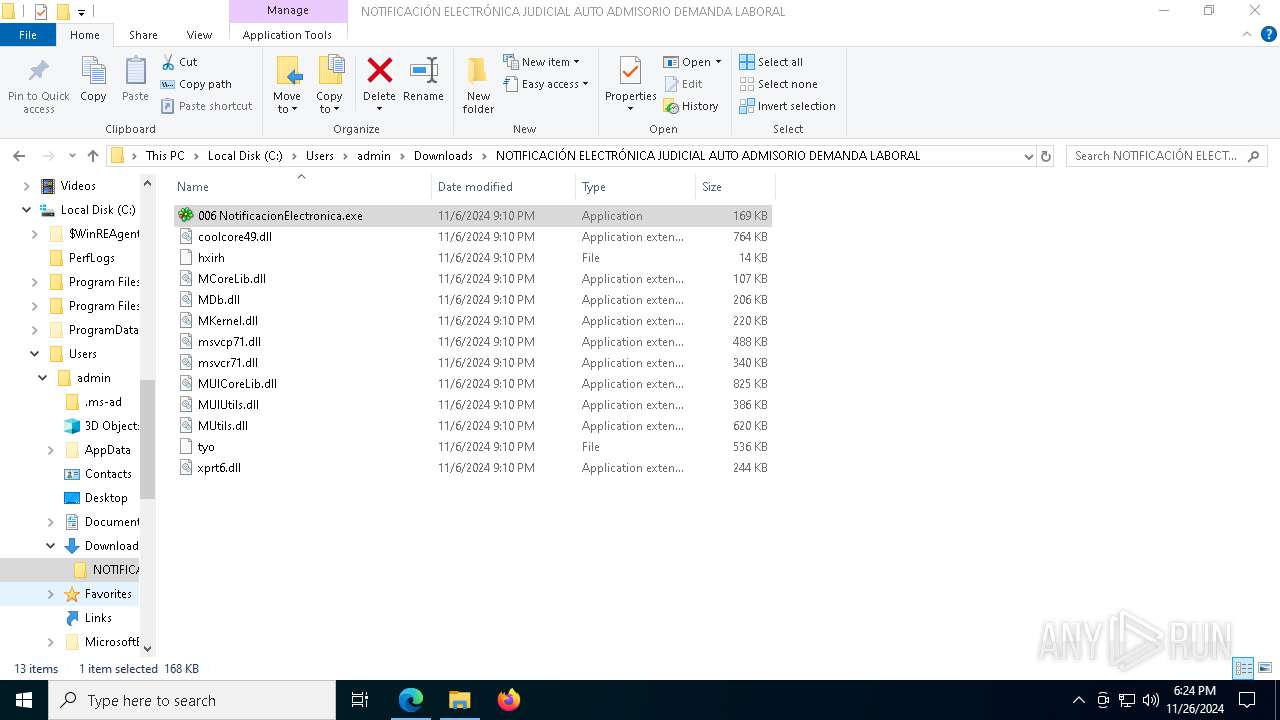
| 3524 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\coolcore49.dll | executable | |
MD5:02DDCE012B021879D5B3E980C48F2D2F | SHA256:4E38D88A59FC49EC56AAFB207777D1987A9711B457514F09FED221DBF640111A | |||
| 3524 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\hxirh | binary | |
MD5:70FC27B068DDE93C2B74BEEC42CD62DA | SHA256:908294A6E49B8B4395708422AE6203A8DA74C7D4E56ABD28F5071EC6BFE1A8A4 | |||
| 3524 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\MUtils.dll | executable | |
MD5:6DA9A492898B66DB78F5C9D3FC7ECC64 | SHA256:50DFC607913A47DD266E27F6533F3F6B8F9FE995582F7662A944149A26B5054C | |||
| 3524 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\msvcp71.dll | executable | |
MD5:561FA2ABB31DFA8FAB762145F81667C2 | SHA256:DF96156F6A548FD6FE5672918DE5AE4509D3C810A57BFFD2A91DE45A3ED5B23B | |||
| 3524 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\msvcr71.dll | executable | |
MD5:86F1895AE8C5E8B17D99ECE768A70732 | SHA256:8094AF5EE310714CAEBCCAEEE7769FFB08048503BA478B879EDFEF5F1A24FEFE | |||
| 3524 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\006 NotificacionElectronica.exe | executable | |
MD5:AEF6452711538D9021F929A2A5F633CF | SHA256:E611A1FFBE9E08A2660BC290A581AA0B54637524AAF6040A70E54F97136CE5AC | |||
| 3524 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\MDb.dll | executable | |
MD5:BE1262B27FF4A4349B337CC95B7746E7 | SHA256:AB47F3A52C1C2A7F1855C48E2D085E87345590B1FB78353C7070C3B6600843FD | |||
| 3524 | WinRAR.exe | C:\Users\admin\Downloads\NOTIFICACIÓN ELECTRÓNICA JUDICIAL AUTO ADMISORIO DEMANDA LABORAL\MKernel.dll | executable | |
MD5:98A71909605B7D088F82D66ABC64D4C2 | SHA256:46410947D60A8B92869AA2CF27B57A94C710047F168AC3BC23879A8461F8686A | |||
| 5208 | cmd.exe | C:\Users\admin\AppData\Local\Temp\hqqxjkrgnm | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
98
DNS requests
72
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6680 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4556 | svchost.exe | HEAD | 200 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1733060243&P2=404&P3=2&P4=KexvhwabL%2frGn53mCz8hPfKKQPglWGykb2TofQgS6atnEoU6aDnKEV4CFLyBBqO%2bpCGW%2bYrLad1R0LwHod9pIw%3d%3d | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4556 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1733060243&P2=404&P3=2&P4=KexvhwabL%2frGn53mCz8hPfKKQPglWGykb2TofQgS6atnEoU6aDnKEV4CFLyBBqO%2bpCGW%2bYrLad1R0LwHod9pIw%3d%3d | unknown | — | — | whitelisted |
4556 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1733060243&P2=404&P3=2&P4=KexvhwabL%2frGn53mCz8hPfKKQPglWGykb2TofQgS6atnEoU6aDnKEV4CFLyBBqO%2bpCGW%2bYrLad1R0LwHod9pIw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6964 | msedge.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
6964 | msedge.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|