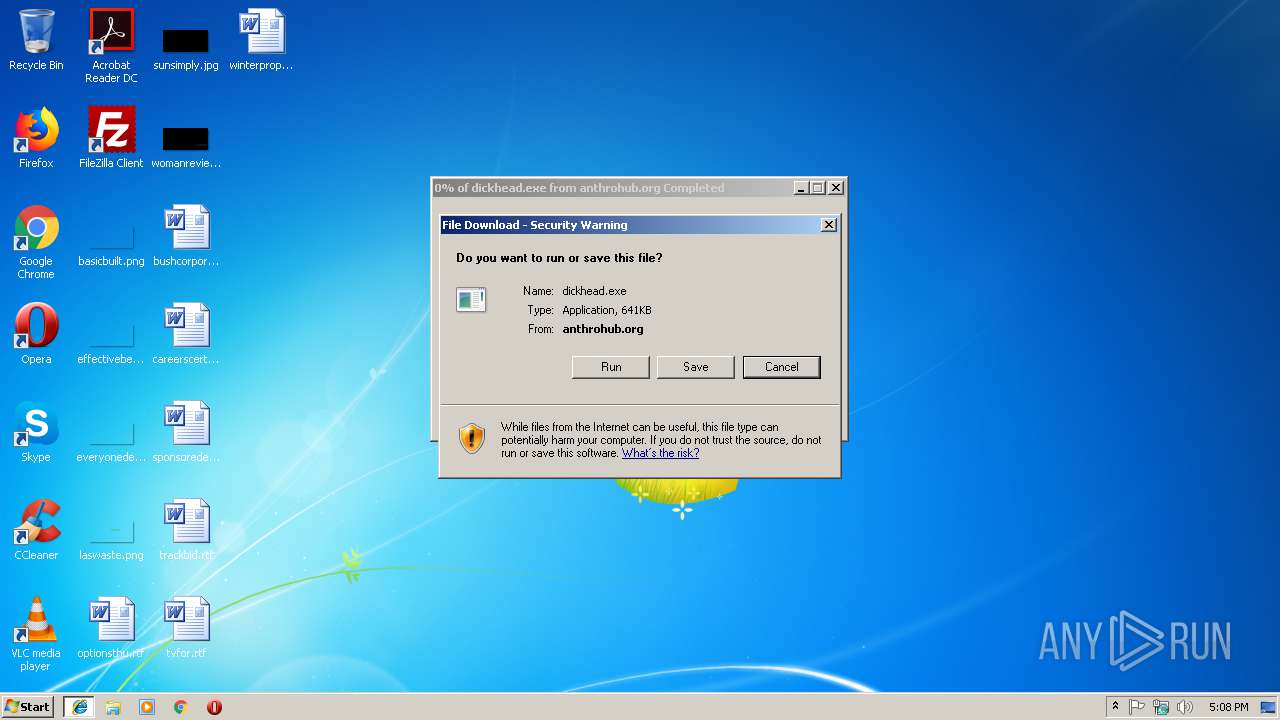
| URL: | http://anthrohub.org/.well-known/dickhead.exe |
| Full analysis: | https://app.any.run/tasks/201c63f9-eff6-41f9-82a6-6adbab6b5e37 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | December 06, 2018, 17:08:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0756EB1BEA92F26BBAD59E952C435E66 |
| SHA1: | 70F8AD3BB77E558BCCB5F5C4919A1316D8198637 |
| SHA256: | 8189CF38C36AC32B3E1D9A5391C3EA4DBD96E1843827EE4F360DEAC9C919EFDB |
| SSDEEP: | 3:N1KflFWQHLWLzTLKH8NbNn:CtFWQCLzTUcZ |
MALICIOUS
Downloads executable files from the Internet
- iexplore.exe (PID: 3204)
AGENTTESLA was detected
- dickhead[1].exe (PID: 3120)
Actions looks like stealing of personal data
- dickhead[1].exe (PID: 3120)
Application was dropped or rewritten from another process
- dickhead[1].exe (PID: 3120)
- dickhead[1].exe (PID: 3044)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2948)
- iexplore.exe (PID: 3204)
Application launched itself
- dickhead[1].exe (PID: 3044)
Checks for external IP
- dickhead[1].exe (PID: 3120)
Cleans NTFS data-stream (Zone Identifier)
- dickhead[1].exe (PID: 3044)
Loads DLL from Mozilla Firefox
- dickhead[1].exe (PID: 3120)
Connects to SMTP port
- dickhead[1].exe (PID: 3120)
Reads Windows Product ID
- dickhead[1].exe (PID: 3120)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2948)
Application launched itself
- iexplore.exe (PID: 2948)
Reads Internet Cache Settings
- iexplore.exe (PID: 3204)
- iexplore.exe (PID: 2948)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3204)
- iexplore.exe (PID: 2948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
34
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2948 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3044 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\dickhead[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\dickhead[1].exe | iexplore.exe | ||||||||||||
User: admin Company: Mandis Companies Inc. Integrity Level: MEDIUM Description: Dynamic Module Exit code: 0 Version: 13.11.7.3 Modules
| |||||||||||||||
| 3120 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\dickhead[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\dickhead[1].exe | dickhead[1].exe | ||||||||||||
User: admin Company: Mandis Companies Inc. Integrity Level: MEDIUM Description: Dynamic Module Exit code: 0 Version: 13.11.7.3 Modules
| |||||||||||||||
| 3204 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2948 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
708
Read events
643
Write events
61
Delete events
4
Modification events
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {9E2BC8D1-F979-11E8-834A-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2948) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C0004000600110008003A008803 | |||
Executable files
2
Suspicious files
1
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2948 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2948 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCF1C54B46AC947AF.TMP | — | |
MD5:— | SHA256:— | |||
| 2948 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF882AE274856F59D8.TMP | — | |
MD5:— | SHA256:— | |||
| 2948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{9E2BC8D1-F979-11E8-834A-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\dickhead[1].exe | executable | |
MD5:— | SHA256:— | |||
| 2948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{9E2BC8D2-F979-11E8-834A-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 2948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\dickhead[1].exe | executable | |
MD5:— | SHA256:— | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012018120620181207\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
4
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3204 | iexplore.exe | GET | 200 | 192.185.16.105:80 | http://anthrohub.org/.well-known/dickhead.exe | US | executable | 641 Kb | malicious |
3120 | dickhead[1].exe | GET | 200 | 216.146.43.70:80 | http://checkip.dyndns.org/ | US | html | 107 b | shared |
2948 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2948 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3204 | iexplore.exe | 192.185.16.105:80 | anthrohub.org | CyrusOne LLC | US | malicious |
3120 | dickhead[1].exe | 208.91.198.143:587 | smtp.cilizltd.com | PDR | US | shared |
3120 | dickhead[1].exe | 216.146.43.70:80 | checkip.dyndns.org | Dynamic Network Services, Inc. | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
anthrohub.org |
| malicious |
checkip.dyndns.org |
| shared |
smtp.cilizltd.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3204 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
3120 | dickhead[1].exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup - checkip.dyndns.org |
3120 | dickhead[1].exe | Potentially Bad Traffic | ET POLICY DynDNS CheckIp External IP Address Server Response |
3120 | dickhead[1].exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3120 | dickhead[1].exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla Exfiltration via SMTP |
3120 | dickhead[1].exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla Exfiltration via SMTP |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
dickhead[1].exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
dickhead[1].exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
dickhead[1].exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
dickhead[1].exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
dickhead[1].exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
dickhead[1].exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
dickhead[1].exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
dickhead[1].exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|