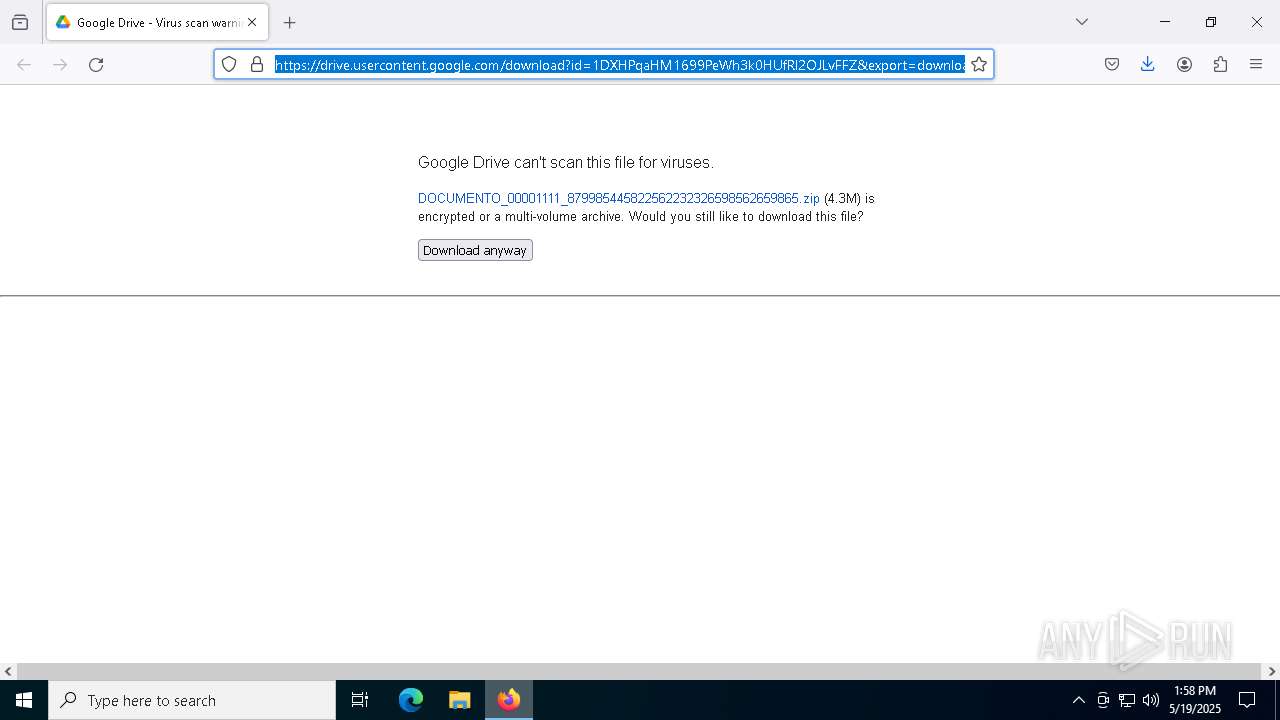
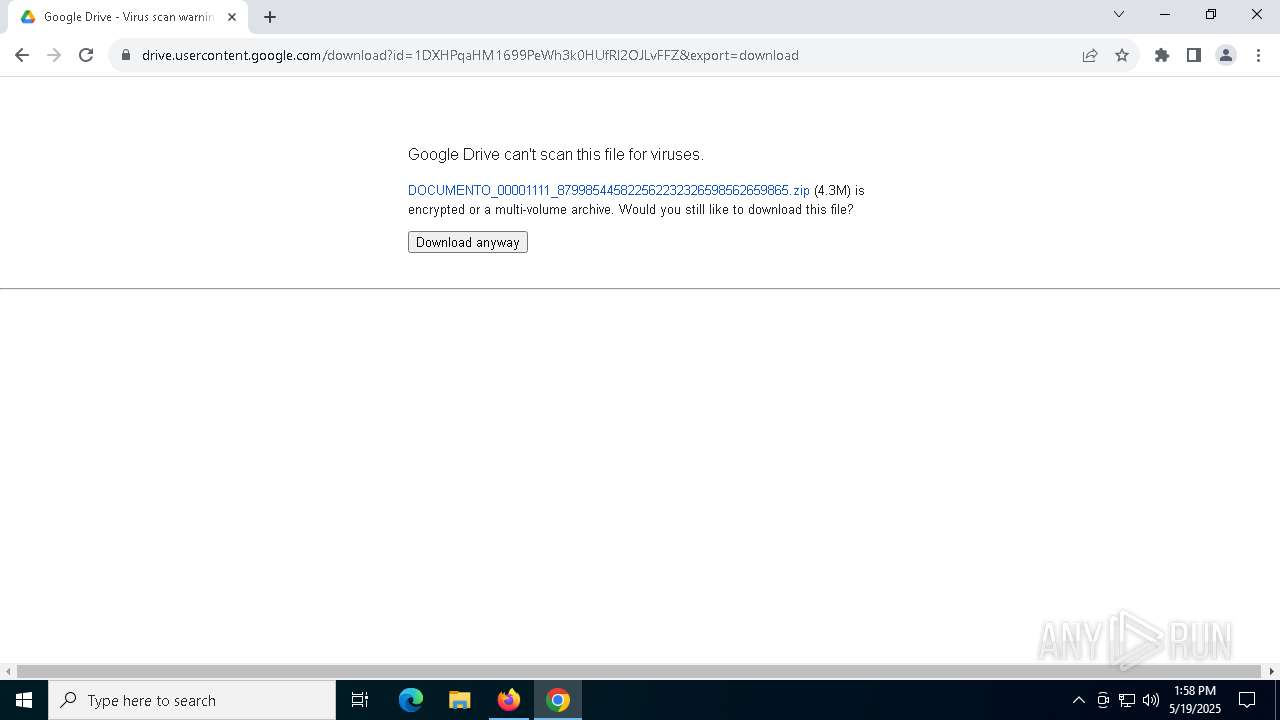
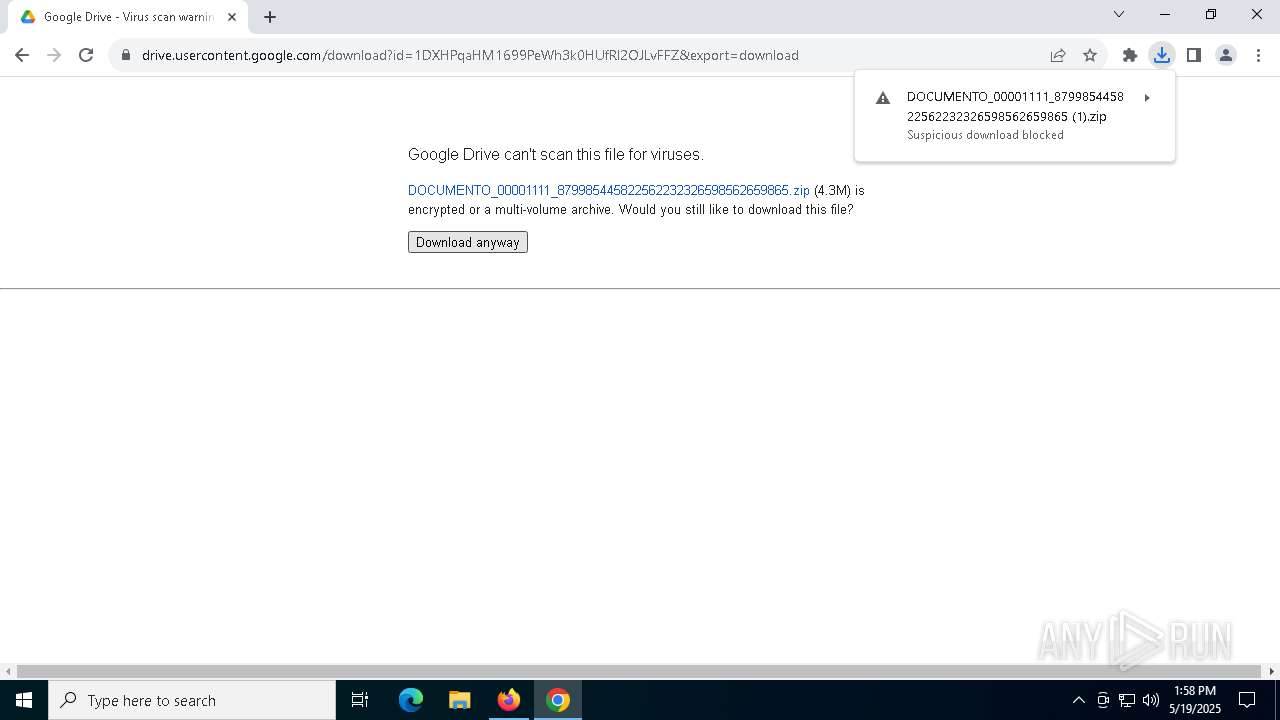
| URL: | https://docs.google.com/uc?export=download&id=1DXHPqaHM1699PeWh3k0HUfRl2OJLvFFZ |
| Full analysis: | https://app.any.run/tasks/148629e6-32c2-4711-a2c9-e87c75b7817f |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 19, 2025, 13:57:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 82D9EDCCE08D04158A0B7715E16FEB0A |
| SHA1: | 8AA799B69EBF6A9A331ED35965566DF75F887600 |
| SHA256: | 8073679E0D9AD8F89D90383780C47126065ADBD7C6BFED59BC5CDF4EFE54C800 |
| SSDEEP: | 3:N8SP3u2NAaBrC2hNUEoKc8WOQD5EpvDn:2Sm2BB+2hNveHO8EV |
MALICIOUS
Executing a file with an untrusted certificate
- Logic_Pilot32.exe (PID: 8876)
- ThreadAggre.exe (PID: 9076)
- Logic_Pilot32.exe (PID: 9192)
- Logic_Pilot32.exe (PID: 9212)
- XPFix.exe (PID: 7220)
- ThreadAggre.exe (PID: 4112)
- Logic_Pilot32.exe (PID: 8900)
- XPFix.exe (PID: 1324)
ASYNCRAT has been detected (SURICATA)
- ThreadAggre.exe (PID: 9076)
SUSPICIOUS
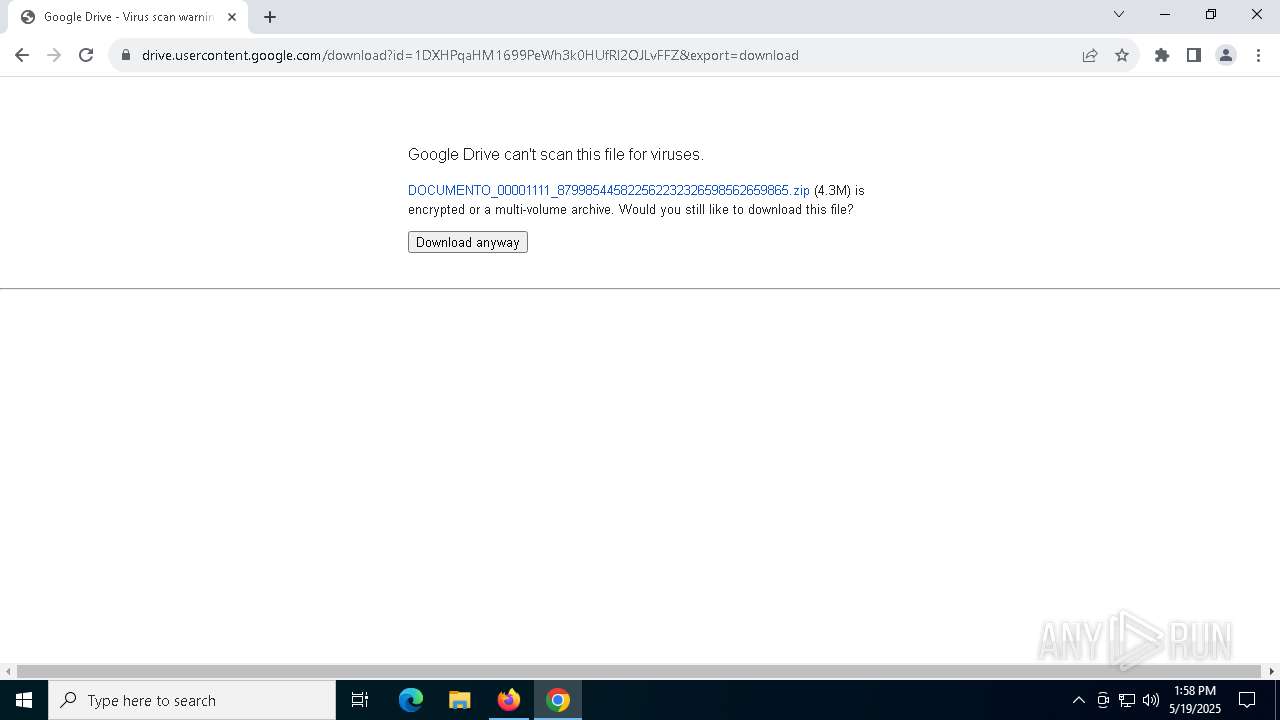
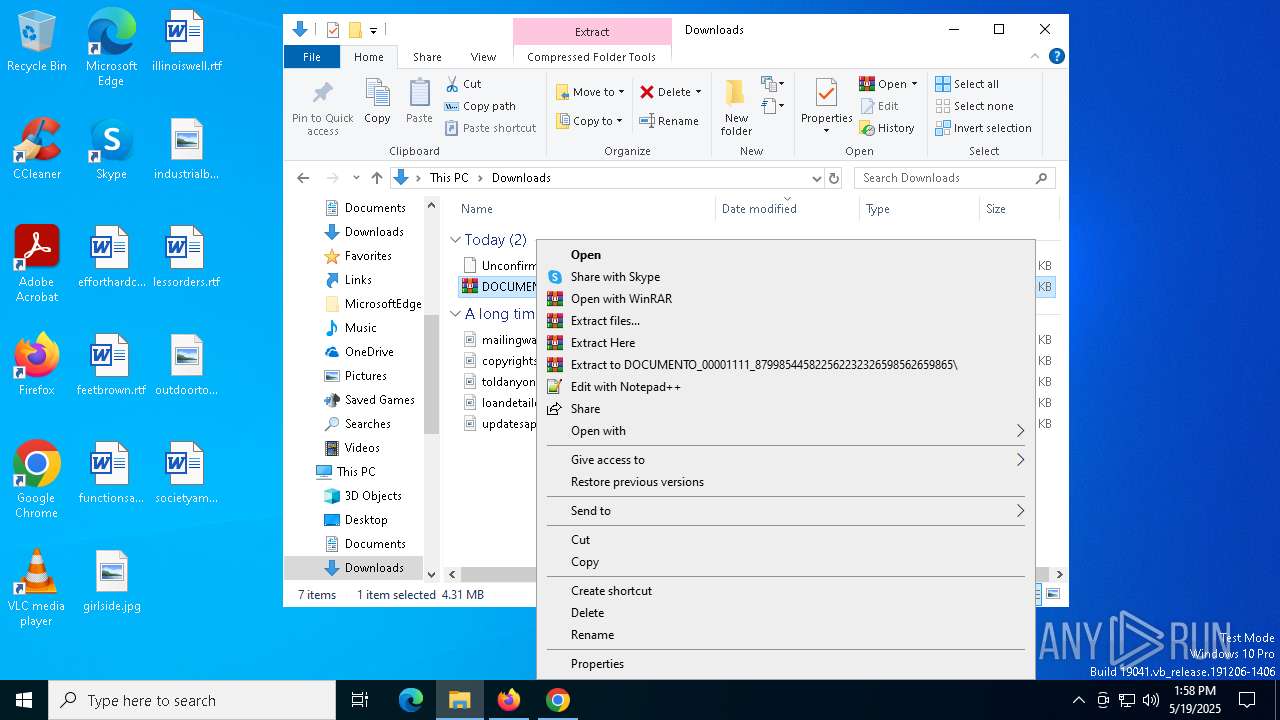
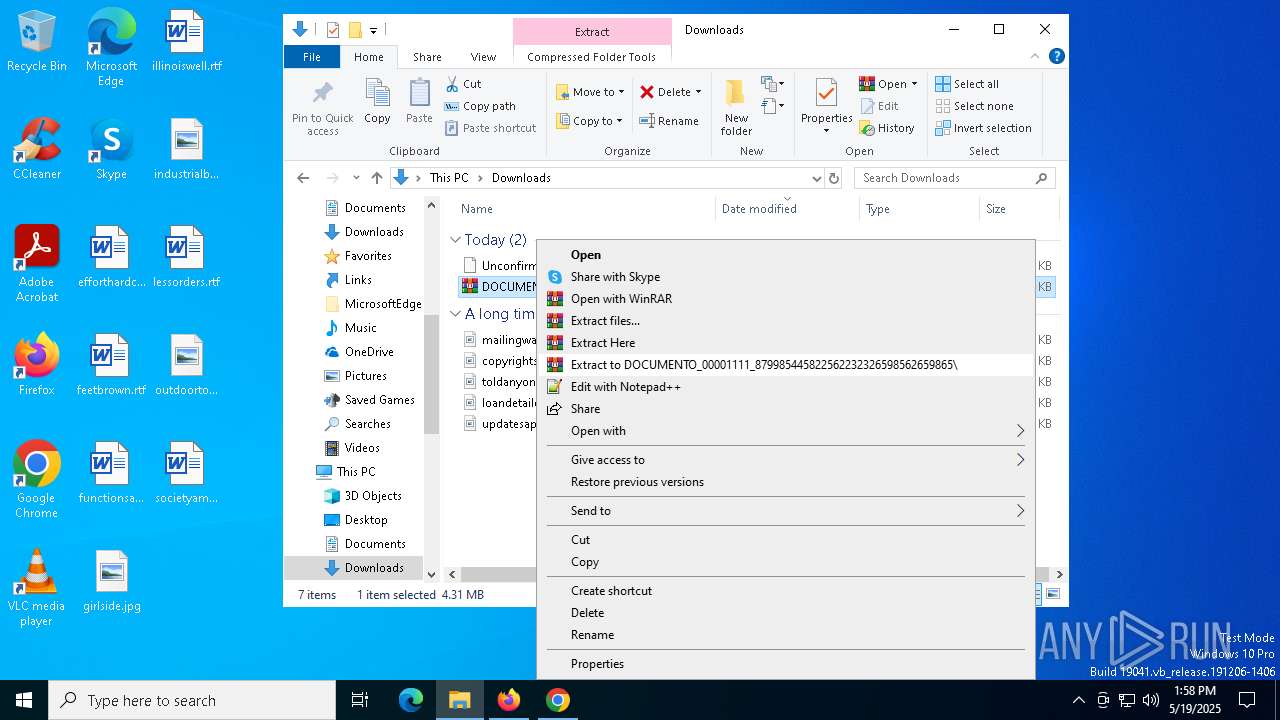
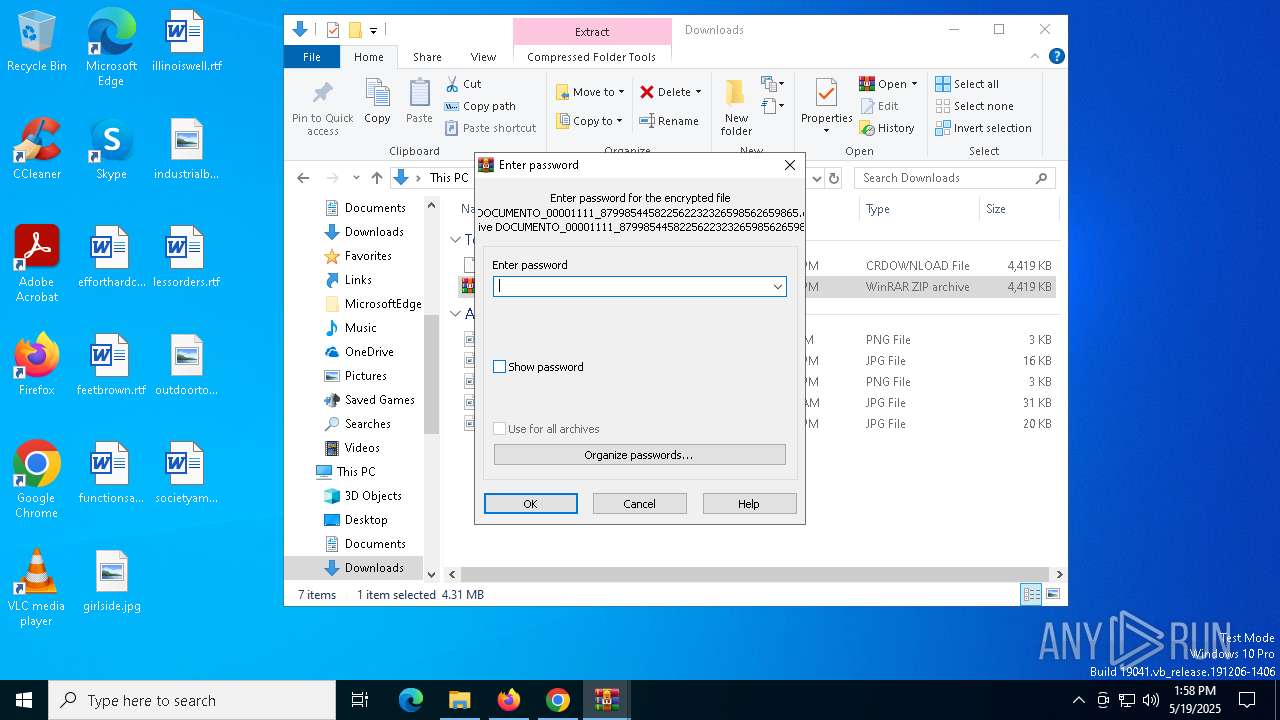
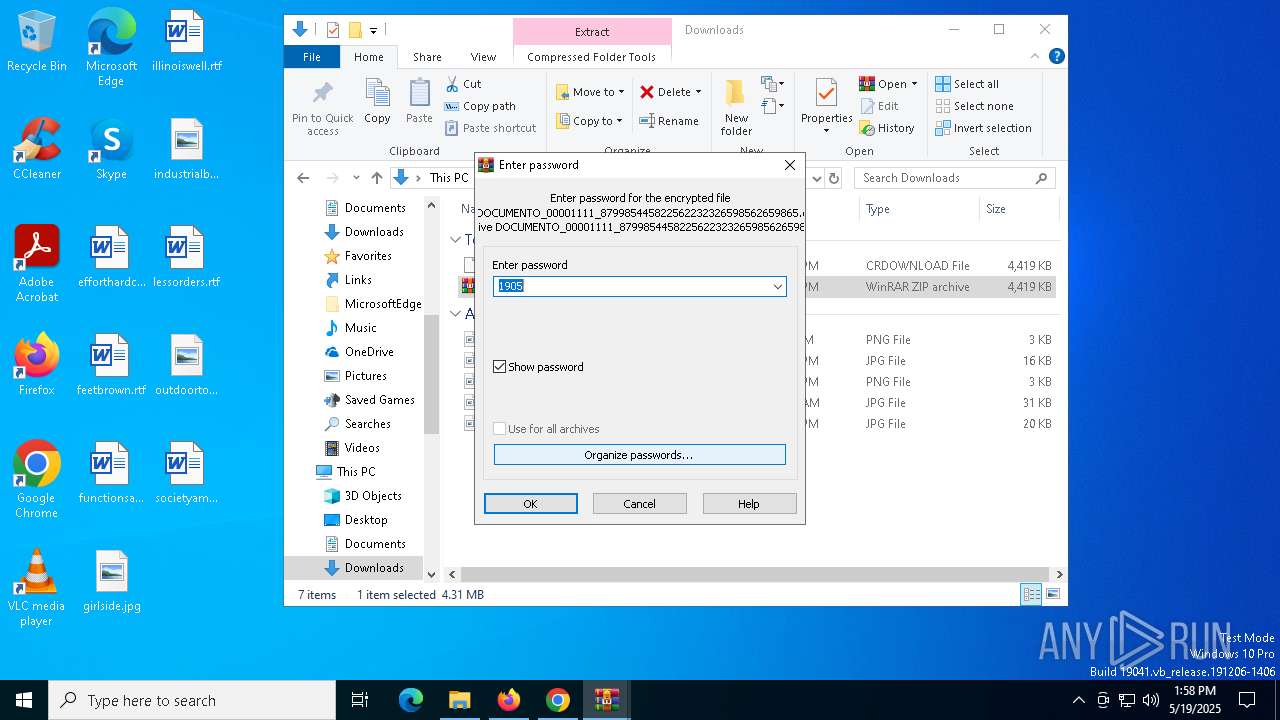
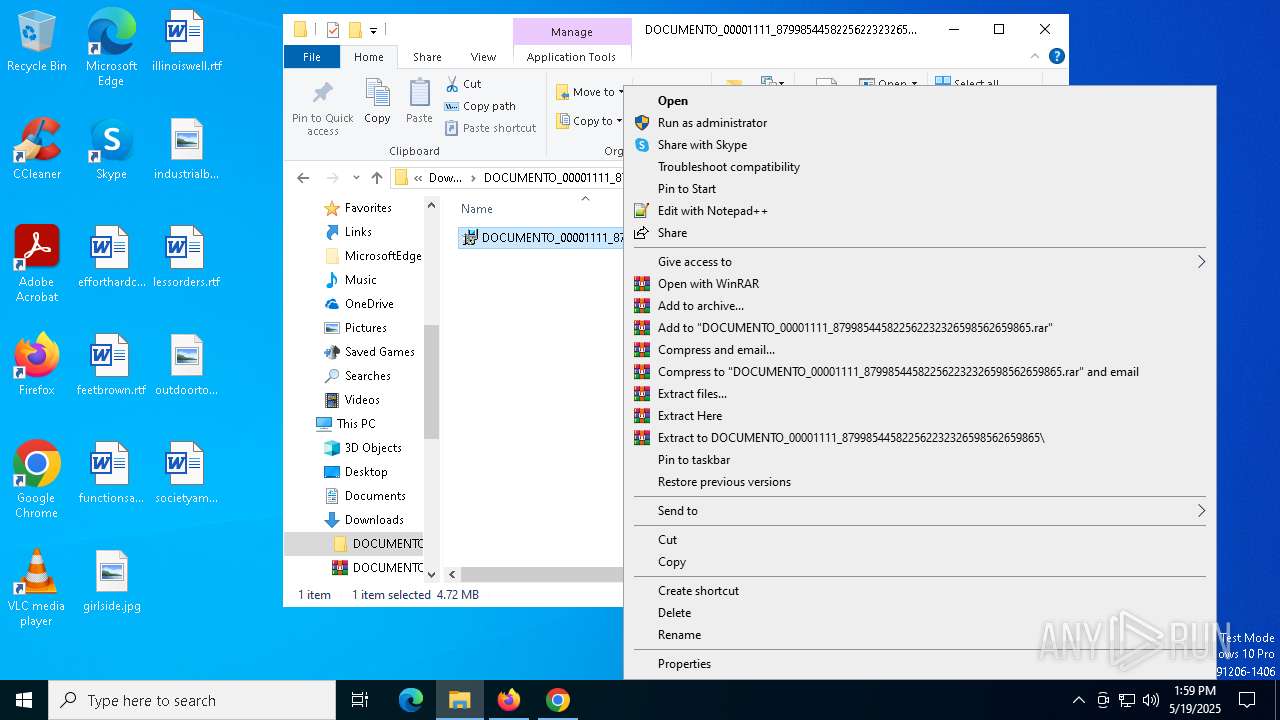
Executable content was dropped or overwritten
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 8824)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 8848)
- Logic_Pilot32.exe (PID: 8876)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 9136)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 9164)
- Logic_Pilot32.exe (PID: 8900)
Process drops legitimate windows executable
- Logic_Pilot32.exe (PID: 8876)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 8848)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 9164)
Starts itself from another location
- Logic_Pilot32.exe (PID: 8876)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 8824)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 9136)
- Logic_Pilot32.exe (PID: 9192)
The process drops C-runtime libraries
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 8848)
- Logic_Pilot32.exe (PID: 8876)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 9164)
Connects to unusual port
- ThreadAggre.exe (PID: 9076)
Contacting a server suspected of hosting an CnC
- ThreadAggre.exe (PID: 9076)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8764)
- chrome.exe (PID: 8404)
Manual execution by a user
- chrome.exe (PID: 2984)
- WinRAR.exe (PID: 8764)
- WinRAR.exe (PID: 8660)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 8824)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 9136)
The sample compiled with english language support
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 8824)
- Logic_Pilot32.exe (PID: 8876)
- WinRAR.exe (PID: 8764)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 8848)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 9136)
- chrome.exe (PID: 8404)
- DOCUMENTO_00001111_879985445822562232326598562659865.exe (PID: 9164)
Reads the software policy settings
- slui.exe (PID: 7804)
Application launched itself
- chrome.exe (PID: 2984)
- firefox.exe (PID: 2136)
- firefox.exe (PID: 5064)
The sample compiled with chinese language support
- Logic_Pilot32.exe (PID: 8900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
182
Monitored processes
49
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3344 --field-trial-handle=1916,i,5247509347867027431,15790353594837646374,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2288 --field-trial-handle=1916,i,5247509347867027431,15790353594837646374,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4724 --field-trial-handle=1916,i,5247509347867027431,15790353594837646374,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1004 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5840 --field-trial-handle=1916,i,5247509347867027431,15790353594837646374,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2724 -childID 1 -isForBrowser -prefsHandle 2732 -prefMapHandle 2644 -prefsLen 26911 -prefMapSize 244583 -jsInitHandle 1384 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {0a0364ad-bf72-42ad-920d-7a64c3fe4587} 5064 "\\.\pipe\gecko-crash-server-pipe.5064" 22670cd7f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\AppData\Roaming\authchrome_XWv4\XPFix.exe" "C:\Users\admin\AppData\Roaming\authchrome_XWv4\XPFix.exe" /update | C:\Users\admin\AppData\Roaming\authchrome_XWv4\XPFix.exe | — | Logic_Pilot32.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: HIGH Description: 360安全卫士 安全防护中心模块 Exit code: 0 Version: 1, 0, 0, 1013 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://docs.google.com/uc?export=download&id=1DXHPqaHM1699PeWh3k0HUfRl2OJLvFFZ" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4880 --field-trial-handle=1916,i,5247509347867027431,15790353594837646374,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
27 543
Read events
27 486
Write events
50
Delete events
7
Modification events
| (PID) Process: | (5064) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | ahfgeienlihckogmohjhadlkjgocpleb |
Value: 3B08F722C14555E595AF269F140EE426CE8DEBAD90D03EE9FF33B95CB34233F6 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | bjbddleefiddlmdfdfbgodgacjjldihj |
Value: 5CFE6AD362B9AABBD07085580BC6C063CF1C79A0B22ECB6BCBA21EECA68BA07F | |||
Executable files
28
Suspicious files
255
Text files
50
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5064 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:D8D651E72A6EE3379A96730DD83A638D | SHA256:C584E21CEEC9BF26ADFCDC0CE6F841017B24038E0A97DE28354370852BF3E6DB | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:1F300FBDF213D378A68D12334B5EF72D | SHA256:26E6D7DB286F37A5622B09BC1669973EF4AE5A98694DAA90B883F16CADFE4F71 | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5064 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
97
DNS requests
141
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5064 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
5064 | firefox.exe | POST | 200 | 184.24.77.45:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5064 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
5064 | firefox.exe | POST | 200 | 184.24.77.45:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5064 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | firefox.exe | 142.250.186.142:443 | docs.google.com | GOOGLE | US | whitelisted |
5064 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
5064 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
5064 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
docs.google.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
content-signature-chains.prod.autograph.services.mozaws.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.dynuddns .com Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.dynuddns .com Domain |
9076 | ThreadAggre.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 31 |
9076 | ThreadAggre.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
9076 | ThreadAggre.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT) |
9076 | ThreadAggre.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |