| File name: | 7f8ec2a28f3657ff6f662953b500088a988f574c9bbfe1a8dc1805cec7c0e2f4.apk |
| Full analysis: | https://app.any.run/tasks/a01337ee-5cdd-4260-88c4-18ccdde1650e |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | April 29, 2025, 22:30:13 |
| OS: | Android 14 |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with AndroidManifest.xml, with APK Signing Block |
| MD5: | D853D2C8BD93EA9F087B1997F56B9DDC |
| SHA1: | A5D05E58603B3E623432B087F4B9366BB3D98120 |
| SHA256: | 7F8EC2A28F3657FF6F662953B500088A988F574C9BBFE1A8DC1805CEC7C0E2F4 |
| SSDEEP: | 98304:/JLRpYMZNd9nsbD+iGetylvurq/5v4no+0ojjiJstrx/pZxcGvYR+LqtnMcgWiPo:8r5U67Op |
MALICIOUS
SPYNOTE has been detected
- app_process64 (PID: 2274)
SUSPICIOUS
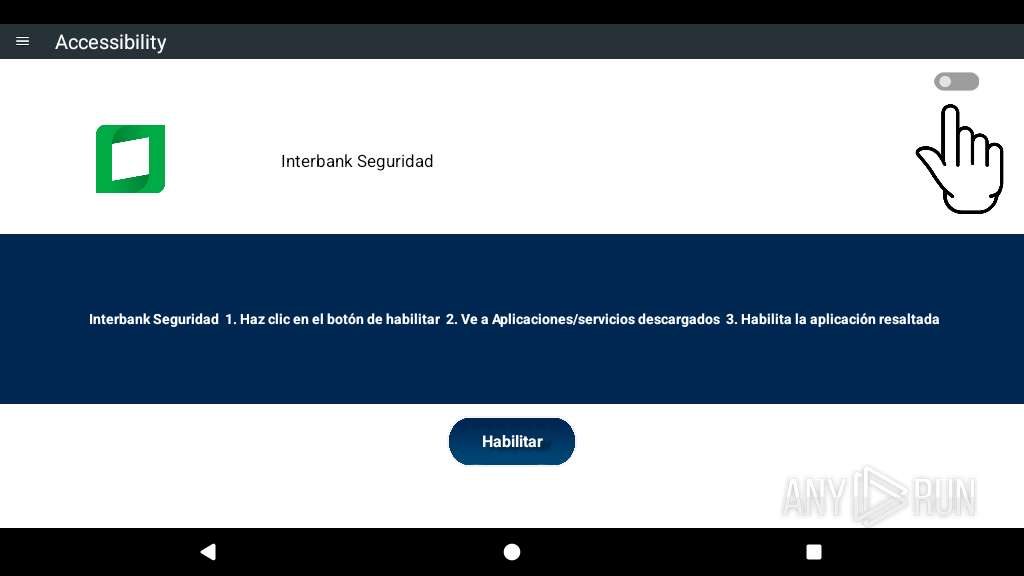
Abuses foreground service for persistence
- app_process64 (PID: 2274)
Retrieves a list of running services
- app_process64 (PID: 2274)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2274)
Launches a new activity
- app_process64 (PID: 2274)
Intercepts events for accessibility services
- app_process64 (PID: 2274)
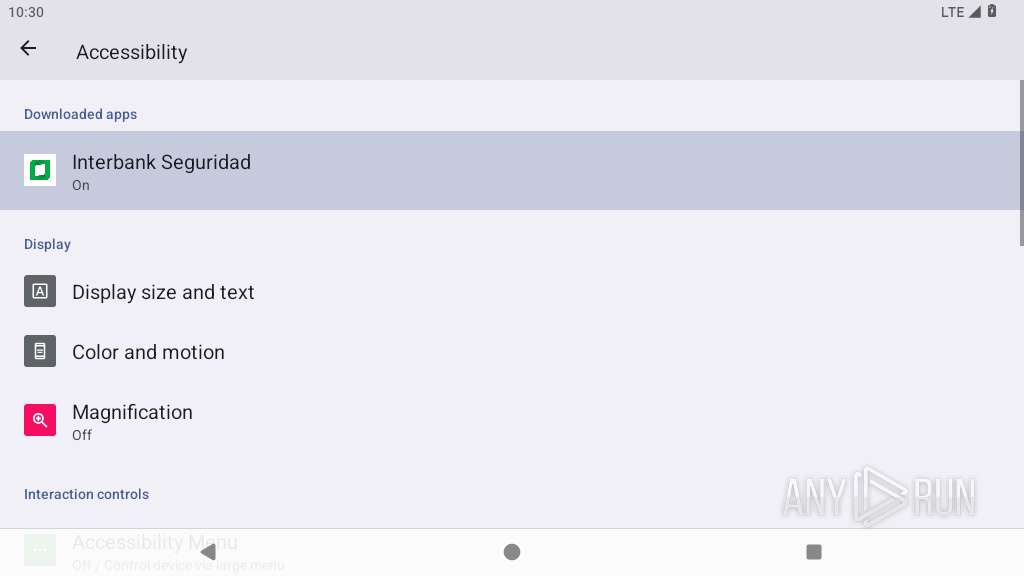
Requests access to accessibility settings
- app_process64 (PID: 2274)
Prevents its uninstallation by user
- app_process64 (PID: 2274)
Overlays content on other applications
- app_process64 (PID: 2274)
Acquires a wake lock to keep the device awake
- app_process64 (PID: 2274)
Creates a WakeLock to manage power state
- app_process64 (PID: 2274)
Accesses external device storage files
- app_process64 (PID: 2274)
Updates the value of a system setting
- app_process64 (PID: 2274)
Checks if the device's lock screen is showing
- app_process64 (PID: 2274)
Leverages accessibility to control apps
- app_process64 (PID: 2274)
Performs UI accessibility actions without user input
- app_process64 (PID: 2274)
Connects to unusual port
- app_process64 (PID: 2274)
INFO
Retrieves the value of a secure system setting
- app_process64 (PID: 2274)
Dynamically registers broadcast event listeners
- app_process64 (PID: 2274)
Creates and writes local files
- app_process64 (PID: 2274)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2274)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zan | | | BlueEyes Animation (77.1) |
|---|---|---|
| .zip | | | ZIP compressed archive (22.8) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Unknown (25887) |
| ZipModifyDate: | 2025:02:24 10:34:50 |
| ZipCRC: | 0xd1835e46 |
| ZipCompressedSize: | 18030 |
| ZipUncompressedSize: | 51516 |
| ZipFileName: | AndroidManifest.xml |
Total processes
127
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2274 | com.elections.leslie | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2333 | com.android.systemui.accessibility.accessibilitymenu | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
31
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2274 | app_process64 | /data/user/0/com.elections.leslie/shared_prefs/com.elections.leslie.xml | xml | |
MD5:— | SHA256:— | |||
| 2274 | app_process64 | /data/user/0/com.elections.leslie/shared_prefs/com.elections.leslie_preferences.xml | xml | |
MD5:— | SHA256:— | |||
| 2274 | app_process64 | /storage/emulated/0/Config/sys/apps/log/log-2025-04-29.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
21
DNS requests
5
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 172.217.18.99:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
445 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.4:123 | time.android.com | — | — | whitelisted |
— | — | 142.250.184.196:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 172.217.18.99:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 64.233.184.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
579 | app_process64 | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
579 | app_process64 | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
579 | app_process64 | 216.239.35.8:123 | time.android.com | — | — | whitelisted |
579 | app_process64 | 216.239.35.4:123 | time.android.com | — | — | whitelisted |
2274 | app_process64 | 173.208.140.135:36057 | — | WII | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
google.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |