| File name: | OctoSniff 3.1.1.0.exe |
| Full analysis: | https://app.any.run/tasks/d6bf63ea-252d-4916-85ec-91d508a54d82 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | August 22, 2020, 21:34:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | F64AD588831FE11544D0CB144CC1A8E7 |
| SHA1: | 156A48D4A250AC47254E3EAEBE0AFC82154F09FF |
| SHA256: | 7F764D1ED13F37F68007ED2B84C5DD1915B537B33E63171FA475C28894C1A81A |
| SSDEEP: | 196608:N9PeX4Gf3EF1EyJGvmeYMFlQHPhJboIk4JK4vUeN1kz0urs:Dcfz7NYtLMIBB1Zurs |
MALICIOUS
Application was dropped or rewritten from another process
- update.exe (PID: 2096)
QUASAR was detected
- update.exe (PID: 2096)
Drops/Copies Quasar RAT executable
- OctoSniff 3.1.1.0.exe (PID: 2780)
SUSPICIOUS
Creates files in the user directory
- OctoSniff 3.1.1.0.exe (PID: 2780)
- update.exe (PID: 2096)
Executable content was dropped or overwritten
- OctoSniff 3.1.1.0.exe (PID: 2780)
Checks for external IP
- update.exe (PID: 2096)
INFO
Manual execution by user
- explorer.exe (PID: 2964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:06:30 18:23:59+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 10556416 |
| InitializedDataSize: | 17408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa1331e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.1.1.0 |
| ProductVersionNumber: | 3.1.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Ip grabber |
| CompanyName: | Octosniff |
| FileDescription: | Octosniff |
| FileVersion: | 3.1.1.0 |
| InternalName: | OctoSniff 3.1.1.0 test.exe |
| LegalCopyright: | Copyright © Octosniff 2015 |
| OriginalFileName: | OctoSniff 3.1.1.0 test.exe |
| ProductName: | Octosniff |
| ProductVersion: | 3.1.1.0 |
| AssemblyVersion: | 3.1.1.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-Jun-2020 16:23:59 |
| Comments: | Ip grabber |
| CompanyName: | Octosniff |
| FileDescription: | Octosniff |
| FileVersion: | 3.1.1.0 |
| InternalName: | OctoSniff 3.1.1.0 test.exe |
| LegalCopyright: | Copyright © Octosniff 2015 |
| OriginalFilename: | OctoSniff 3.1.1.0 test.exe |
| ProductName: | Octosniff |
| ProductVersion: | 3.1.1.0 |
| Assembly Version: | 3.1.1.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 30-Jun-2020 16:23:59 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00A11324 | 0x00A11400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.93739 |
.rsrc | 0x00A14000 | 0x000041C8 | 0x00004200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.9882 |
.reloc | 0x00A1A000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 5.40871 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 5.03363 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 4.62556 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.49203 | 48 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
48
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2096 | "C:\Users\admin\AppData\Roaming\update.exe\update.exe" | C:\Users\admin\AppData\Roaming\update.exe\update.exe | OctoSniff 3.1.1.0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2780 | "C:\Users\admin\AppData\Local\Temp\OctoSniff 3.1.1.0.exe" | C:\Users\admin\AppData\Local\Temp\OctoSniff 3.1.1.0.exe | explorer.exe | ||||||||||||
User: admin Company: Octosniff Integrity Level: MEDIUM Description: Octosniff Exit code: 0 Version: 3.1.1.0 Modules
| |||||||||||||||
| 2964 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
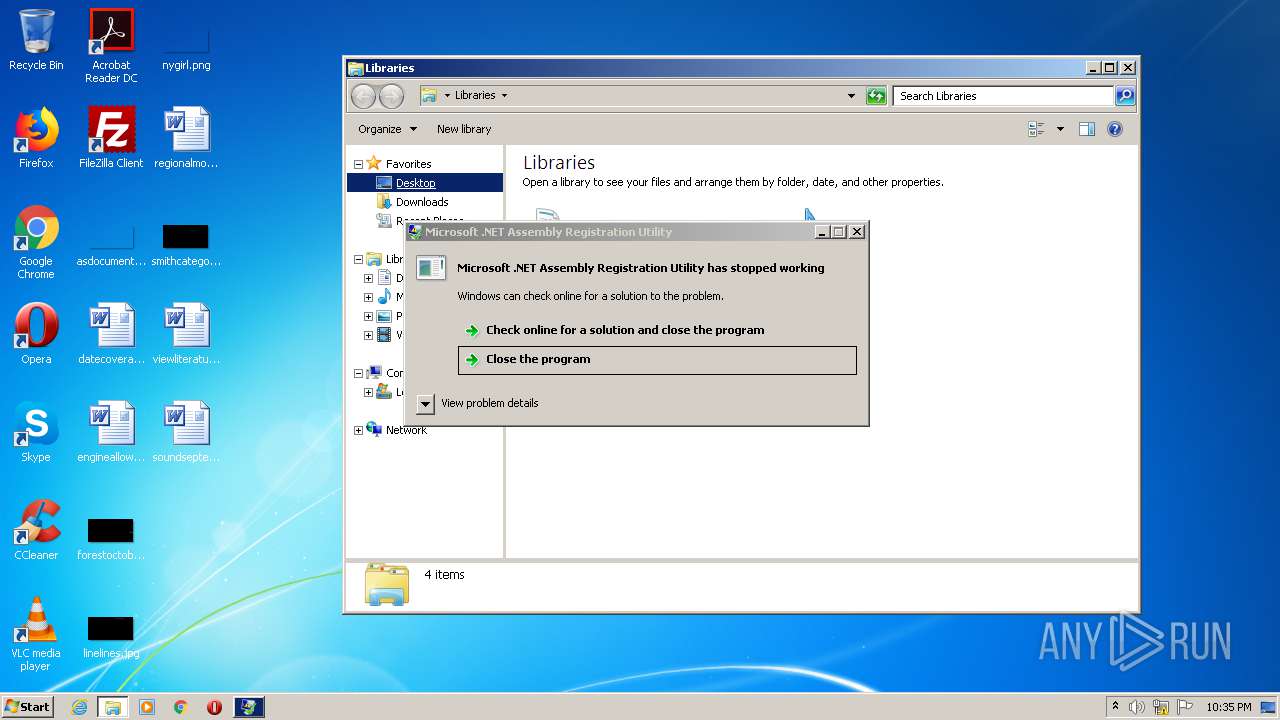
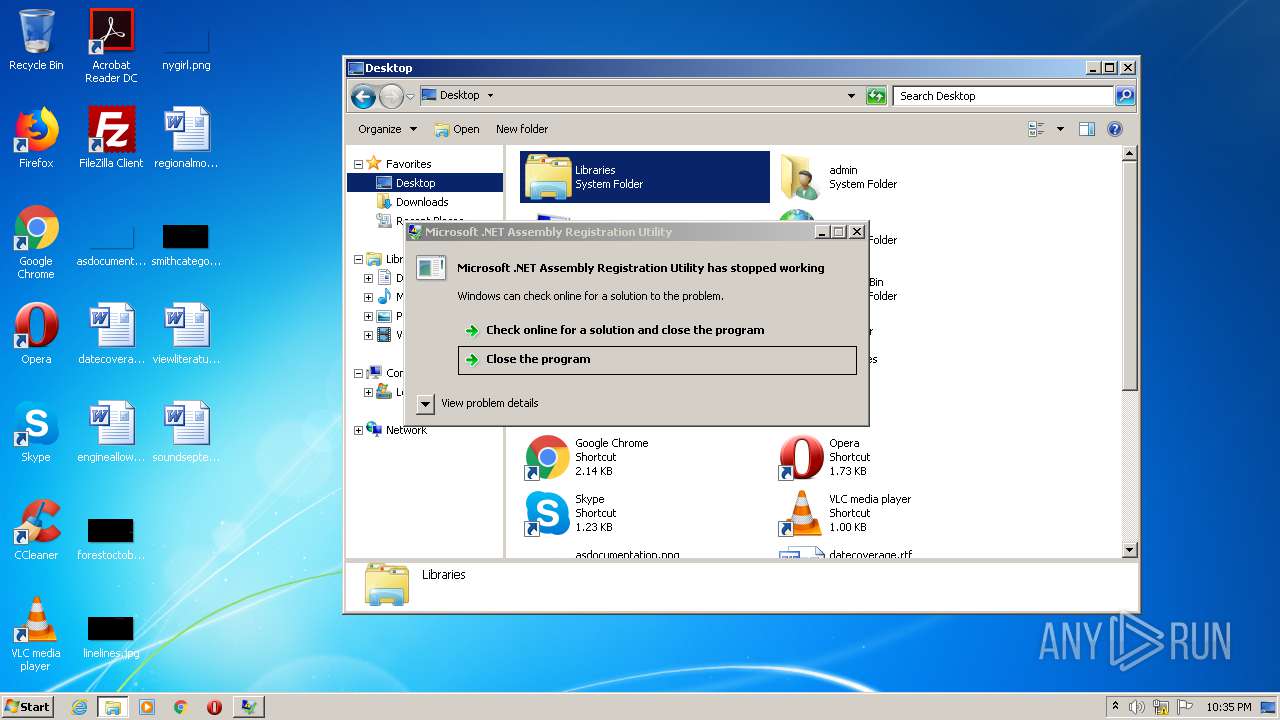
| 3692 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe | OctoSniff 3.1.1.0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 250477278 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
Total events
448
Read events
417
Write events
31
Delete events
0
Modification events
| (PID) Process: | (2780) OctoSniff 3.1.1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2780) OctoSniff 3.1.1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (2780) OctoSniff 3.1.1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
| (PID) Process: | (2780) OctoSniff 3.1.1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dnsapi.dll,-103 |
Value: Domain Name System (DNS) Server Trust | |||
| (PID) Process: | (2780) OctoSniff 3.1.1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-843 |
Value: BitLocker Drive Encryption | |||
| (PID) Process: | (2780) OctoSniff 3.1.1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-844 |
Value: BitLocker Data Recovery Agent | |||
| (PID) Process: | (2780) OctoSniff 3.1.1.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2780) OctoSniff 3.1.1.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2096) update.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\update_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2096) update.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\update_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
1
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2780 | OctoSniff 3.1.1.0.exe | C:\Users\admin\AppData\Roaming\update.exe\update.exe | executable | |
MD5:— | SHA256:— | |||
| 2096 | update.exe | C:\Users\admin\AppData\Roaming\Logs\08-22-2020 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
2
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3652 | WerFault.exe | GET | — | 51.143.111.81:80 | http://watson.microsoft.com/StageOne/regasm_exe/4_7_3062_0/5cc41133/KERNELBASE_dll/6_1_7601_17932/503275ba/0eedfade/0000d3cf.htm?LCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=DELL&SPN=DELL&BV=DELL&MID=3ADE2C42-4AB9-49B7-B142-BE9AEEA69063 | US | — | — | whitelisted |
2096 | update.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 267 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2096 | update.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
— | — | 77.247.127.250:6601 | — | — | — | unknown |
3652 | WerFault.exe | 51.143.111.81:80 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2096 | update.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2096 | update.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2096 | update.exe | A Network Trojan was detected | REMOTE [PTsecurity] Quasar.RAT IP Lookup |
3652 | WerFault.exe | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |
3652 | WerFault.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
1 ETPRO signatures available at the full report