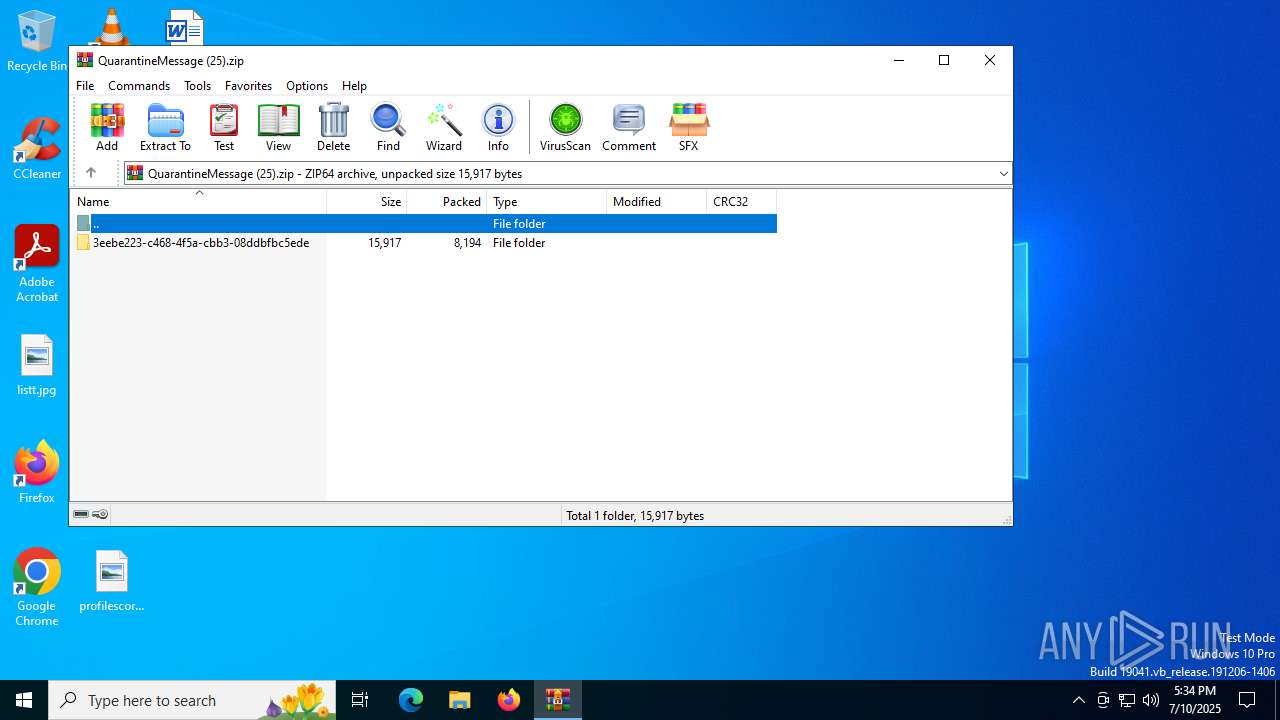
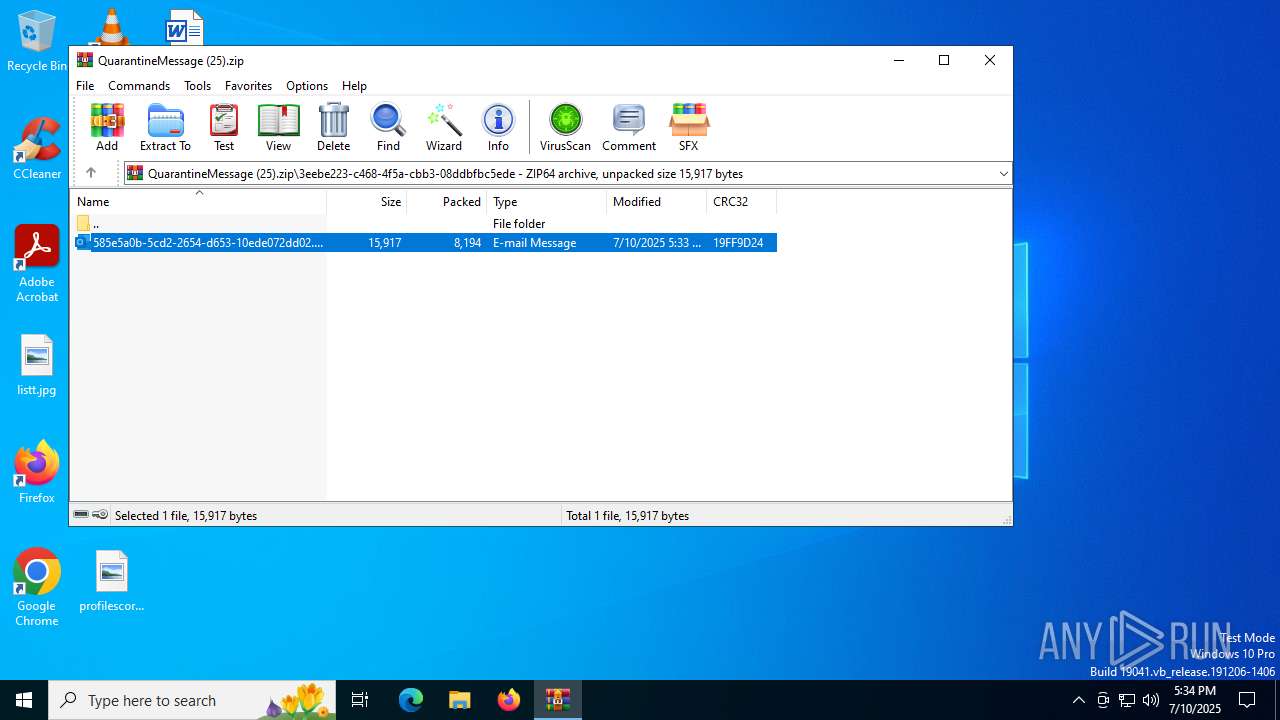
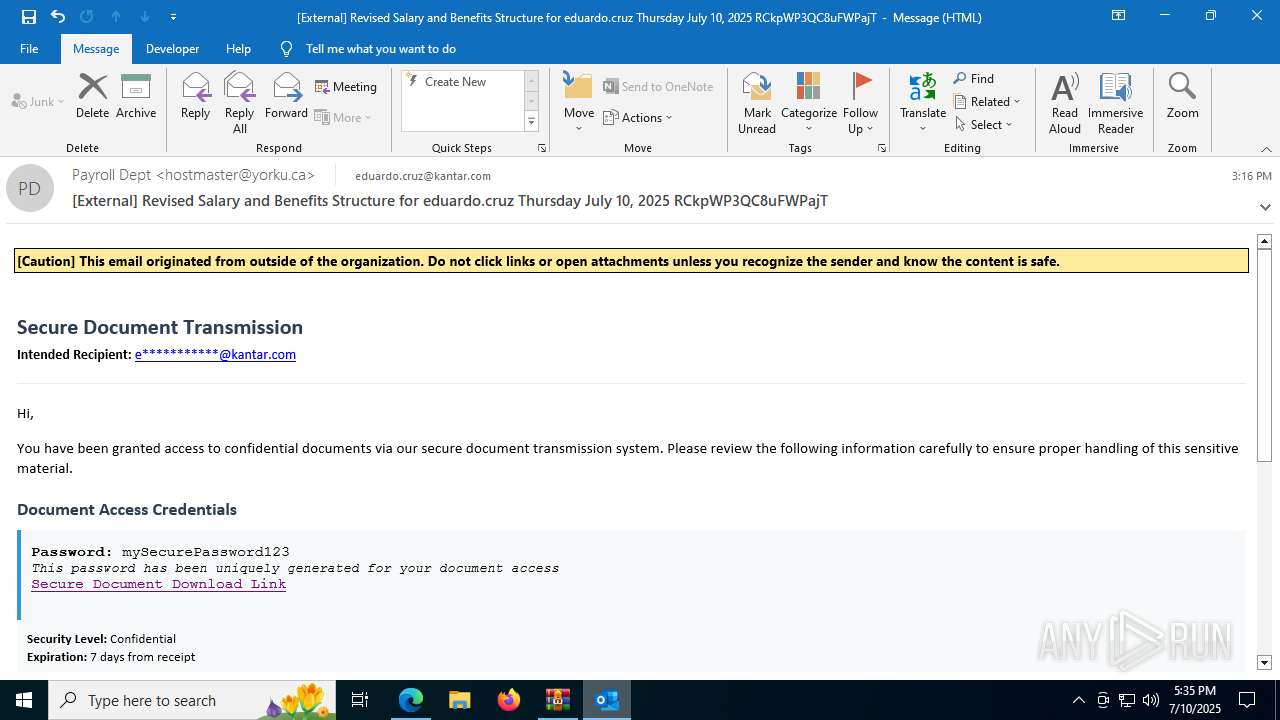
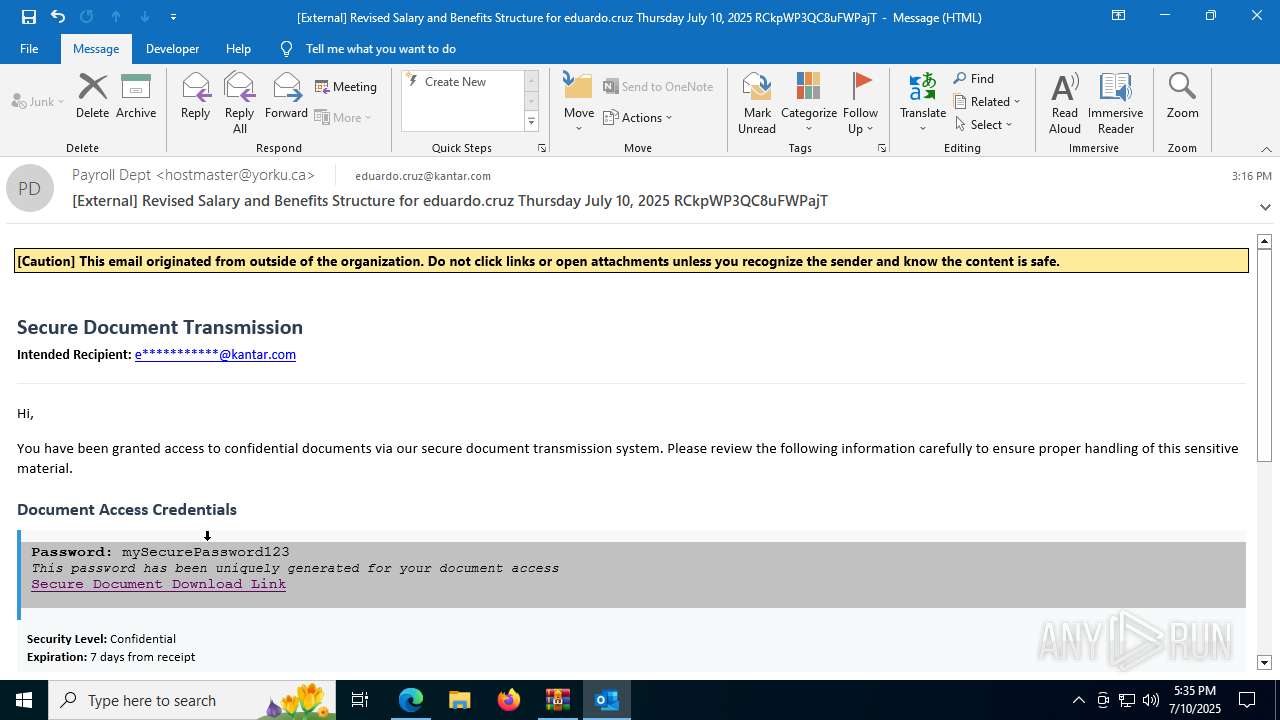
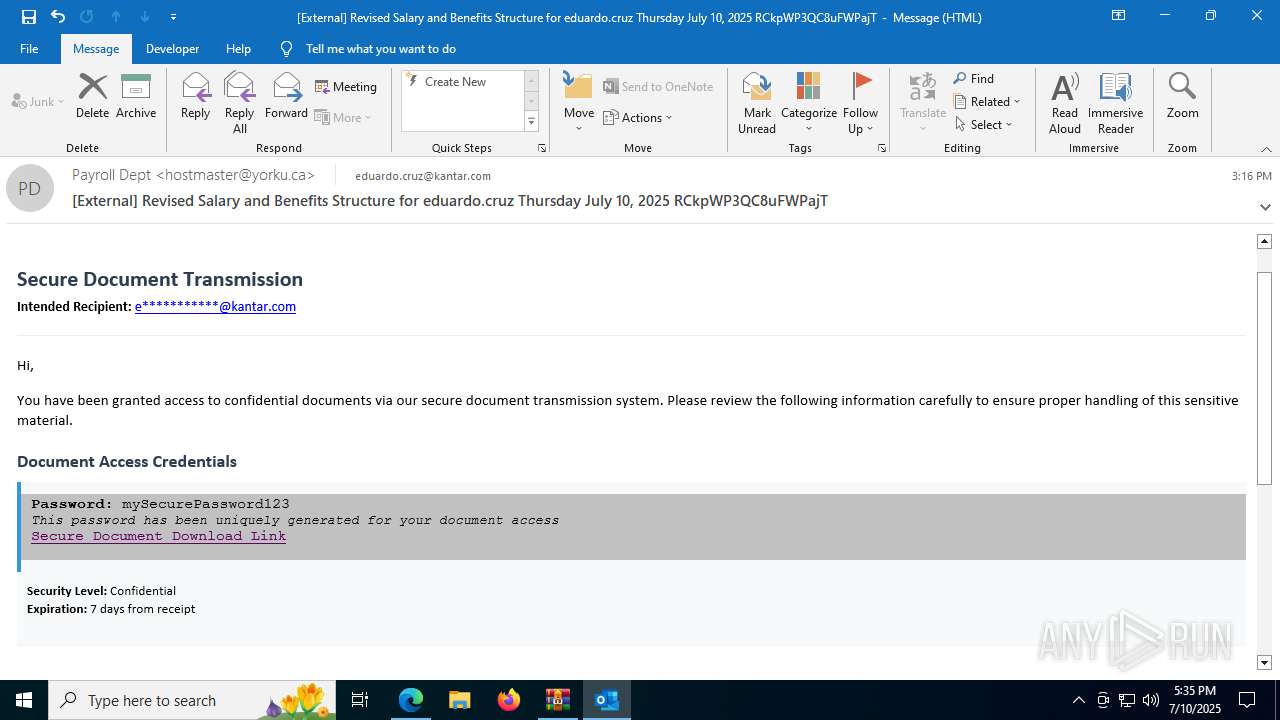
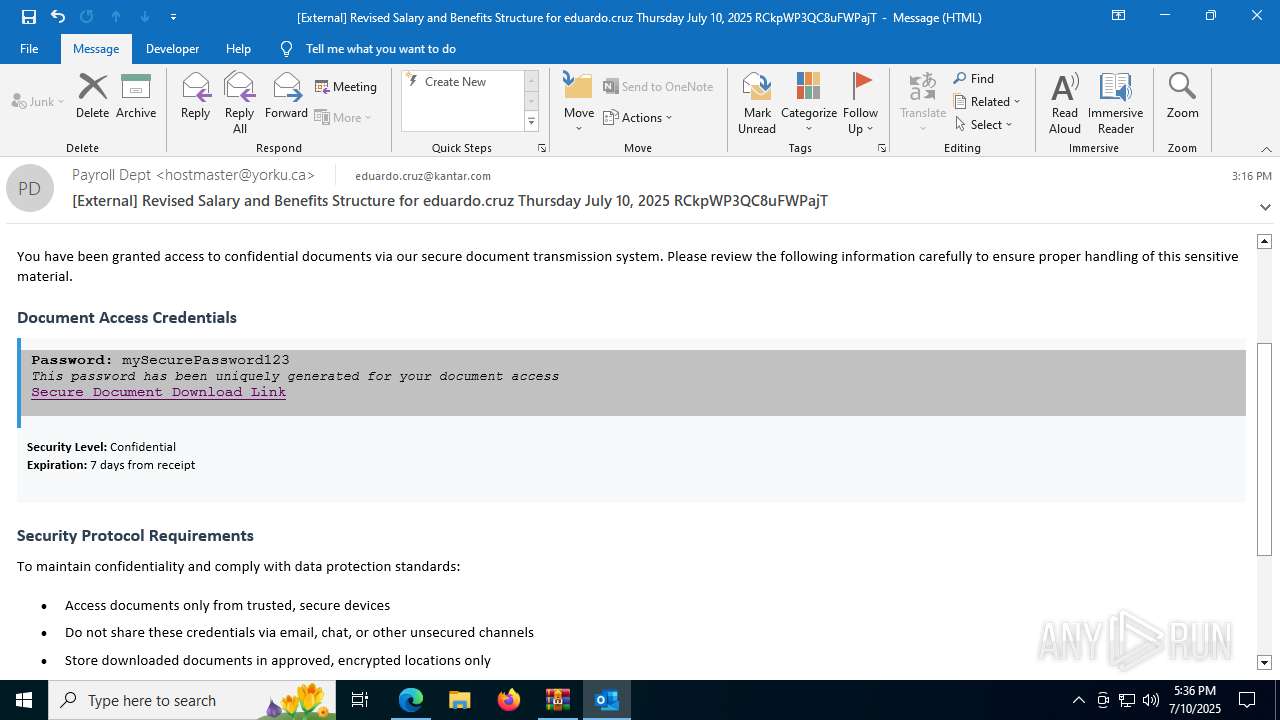
| File name: | QuarantineMessage (25).zip |
| Full analysis: | https://app.any.run/tasks/b0014a40-b09f-41b8-b83c-c9d73cc46a8f |
| Verdict: | Malicious activity |
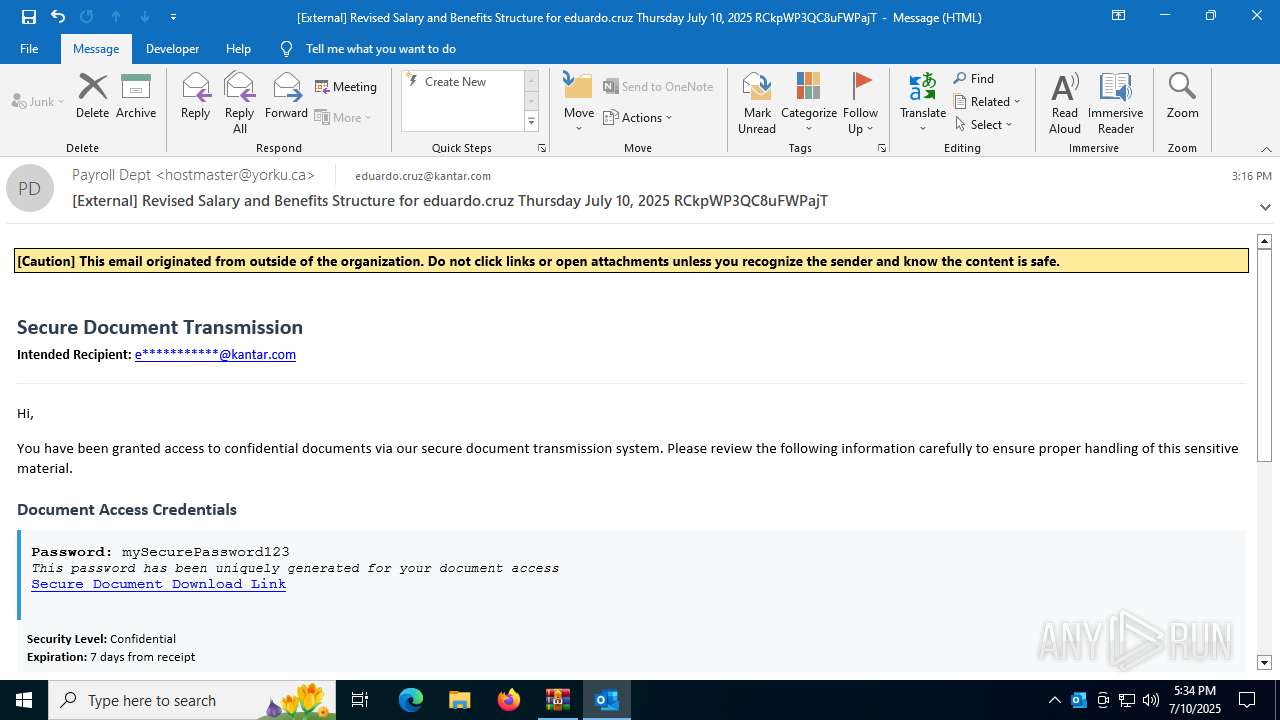
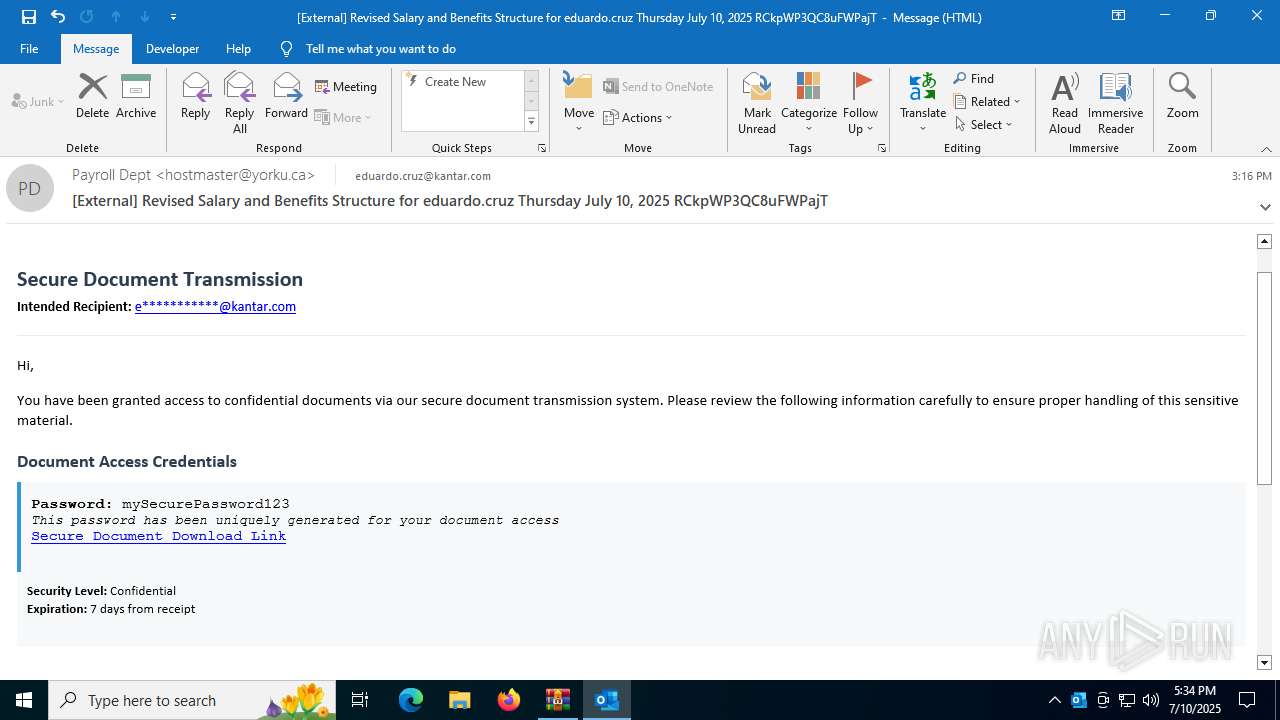
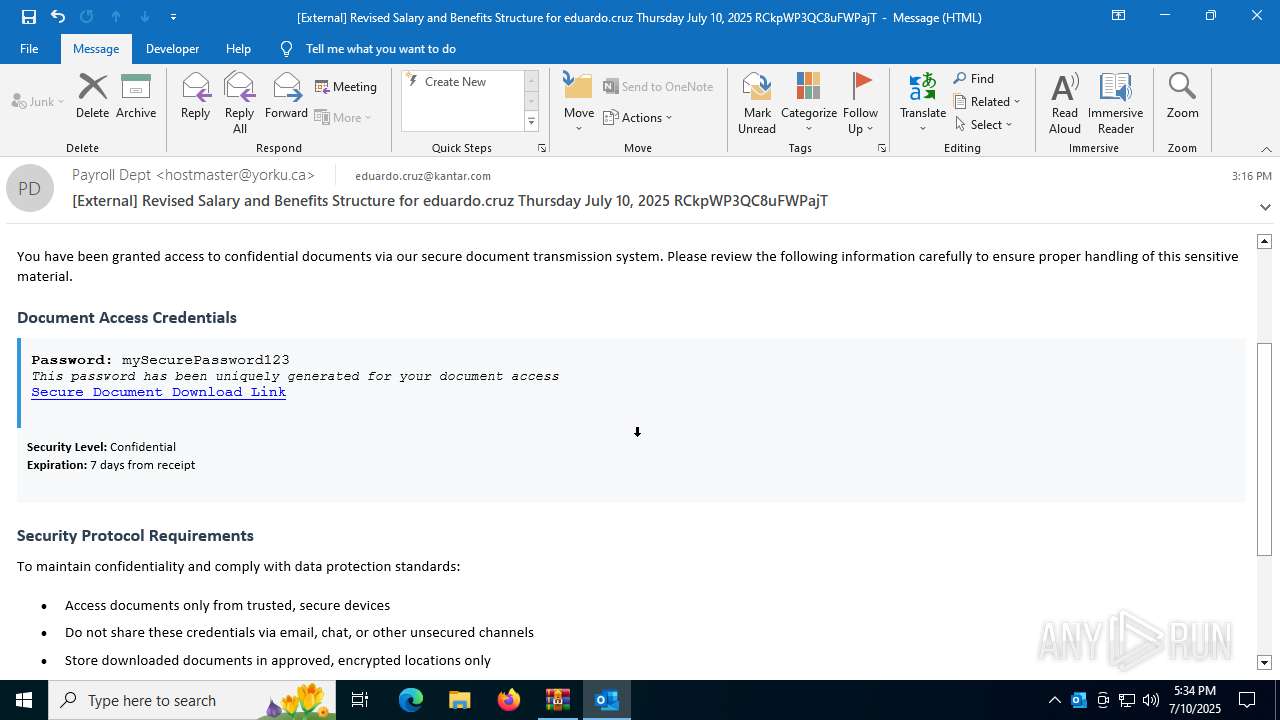
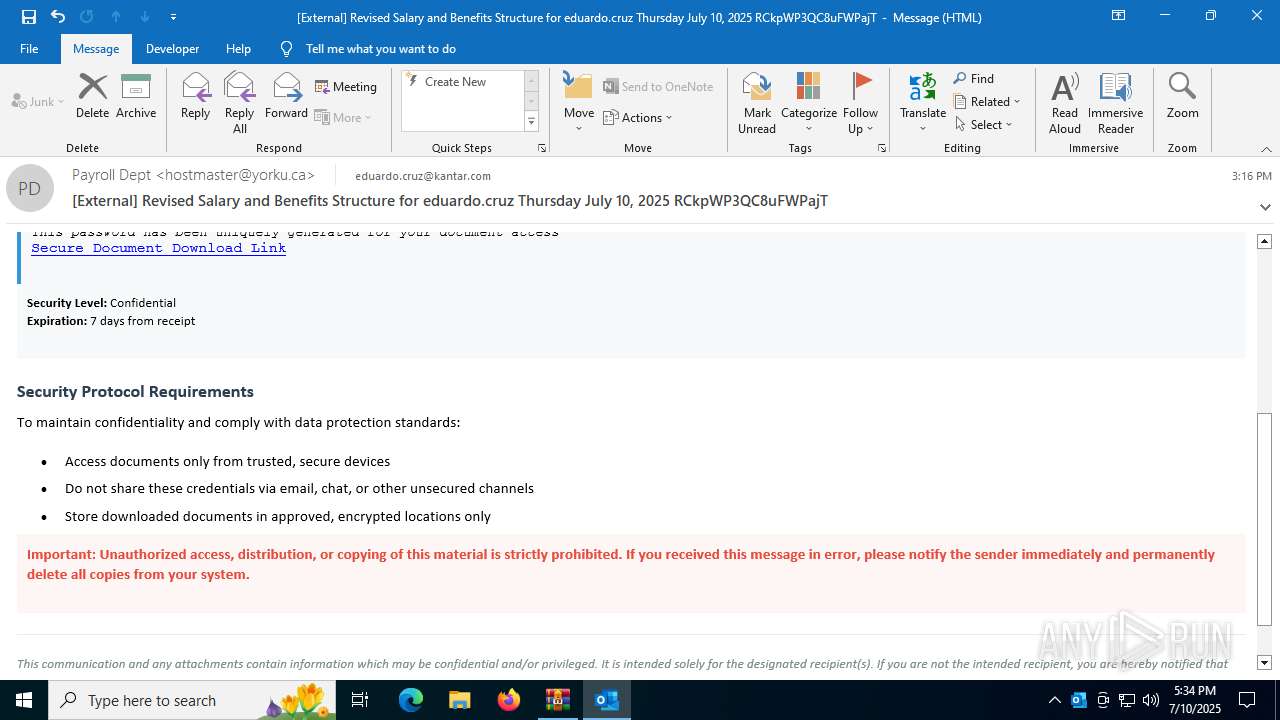
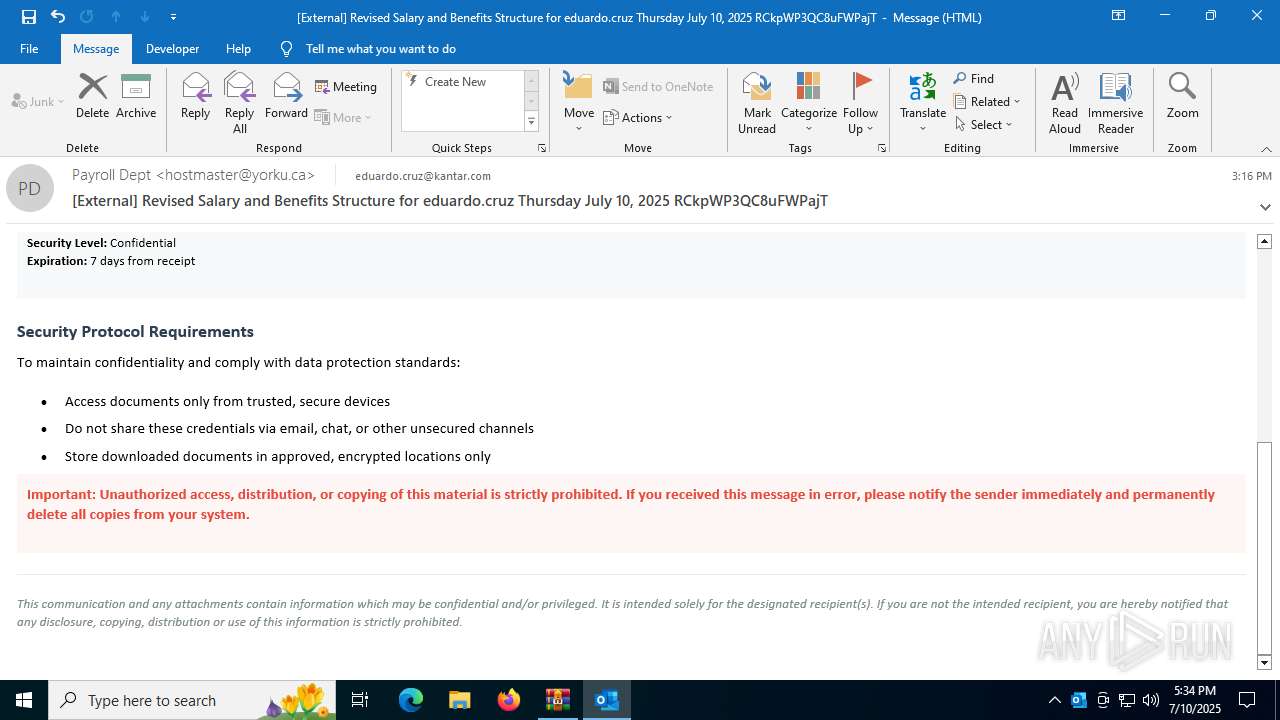
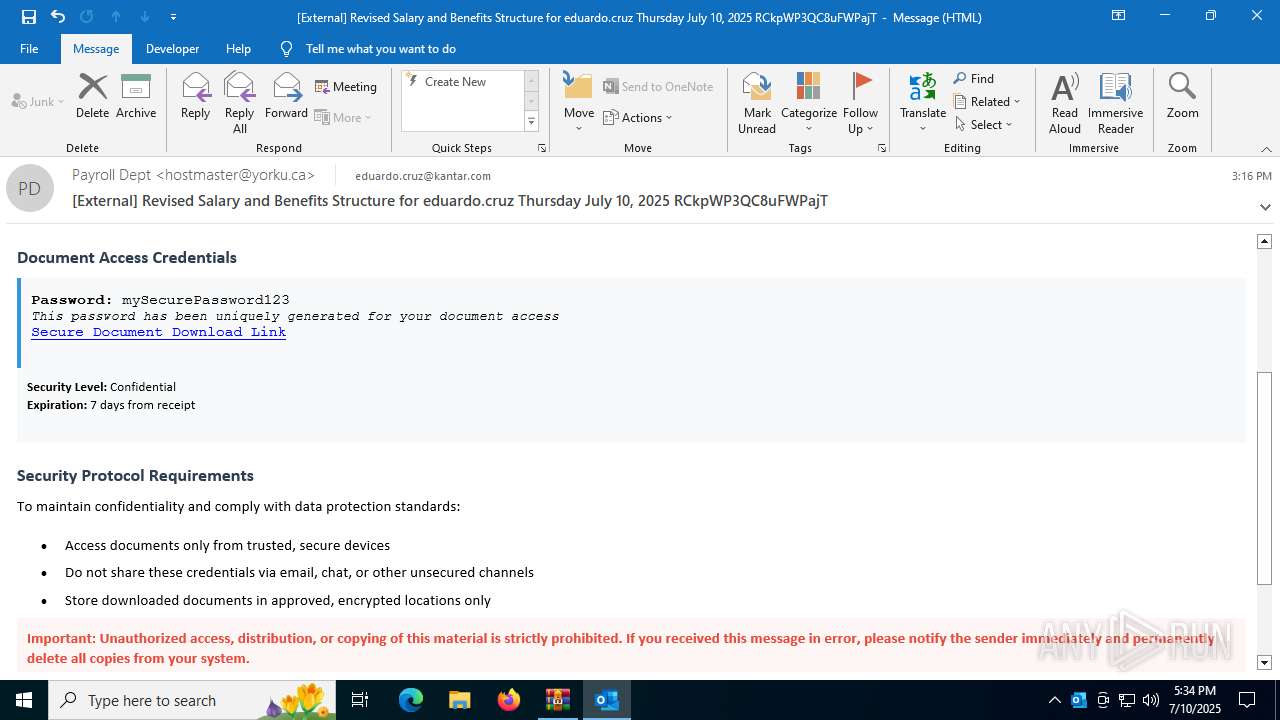
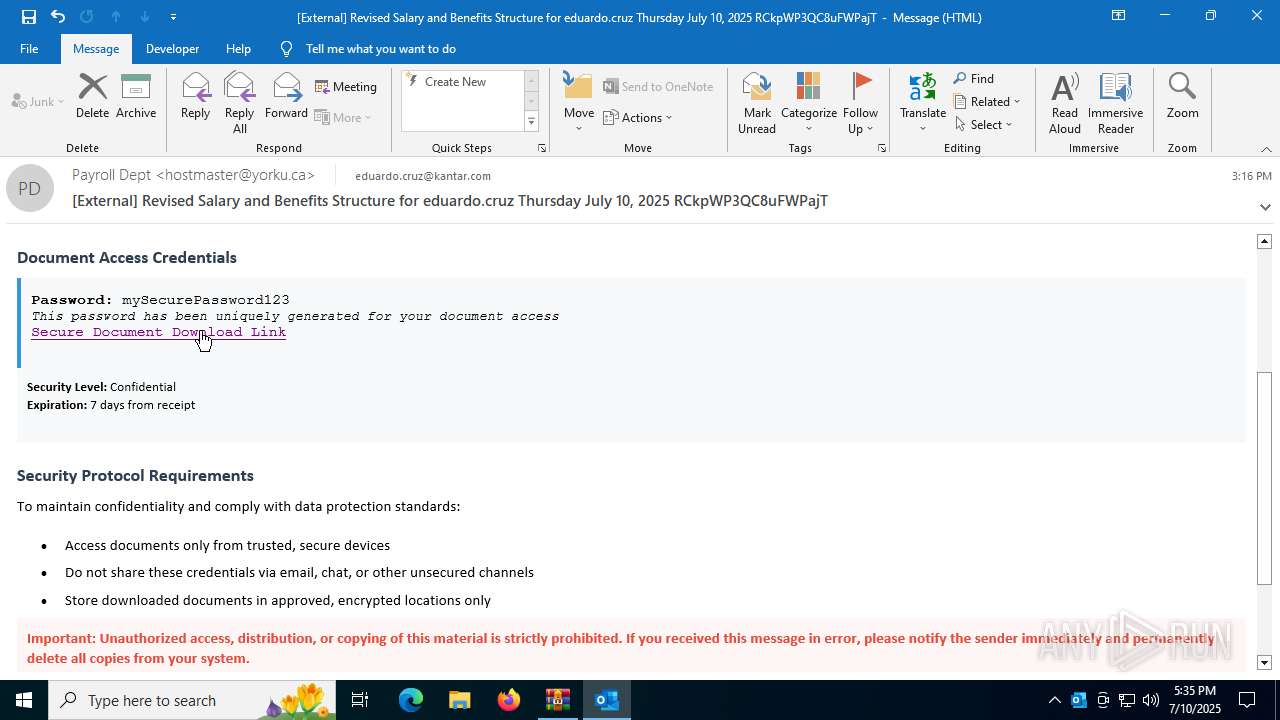
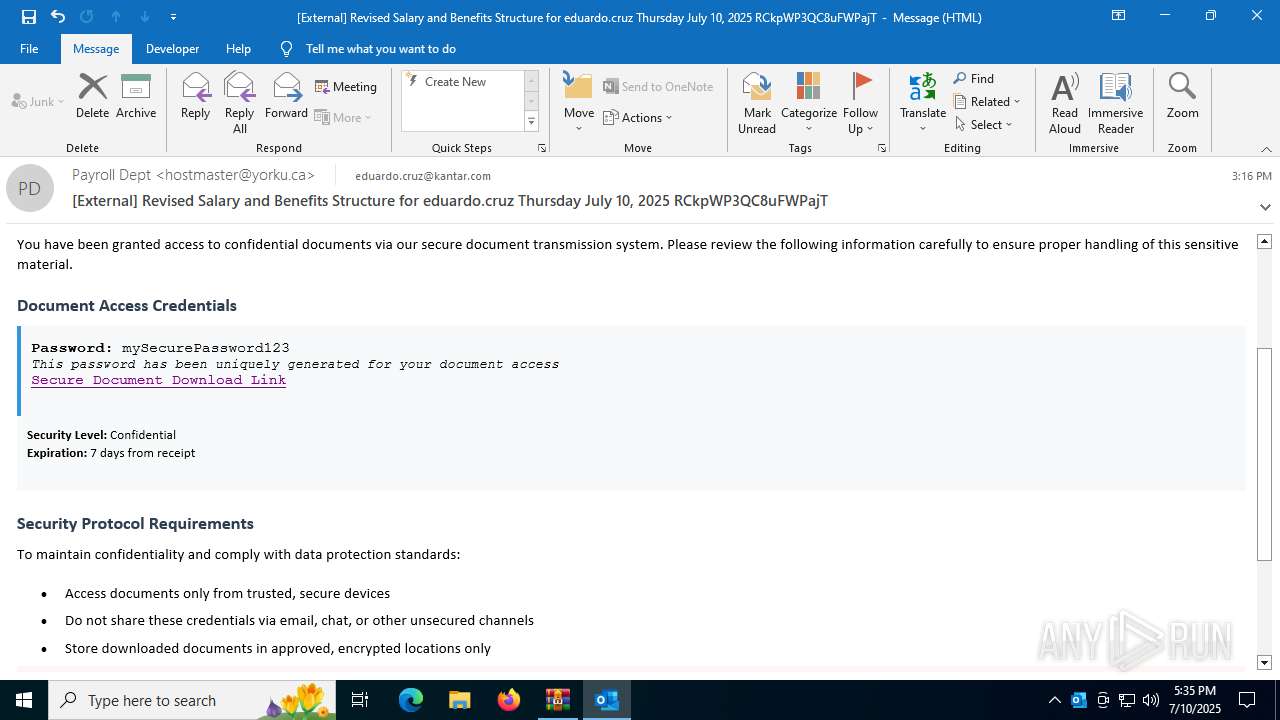
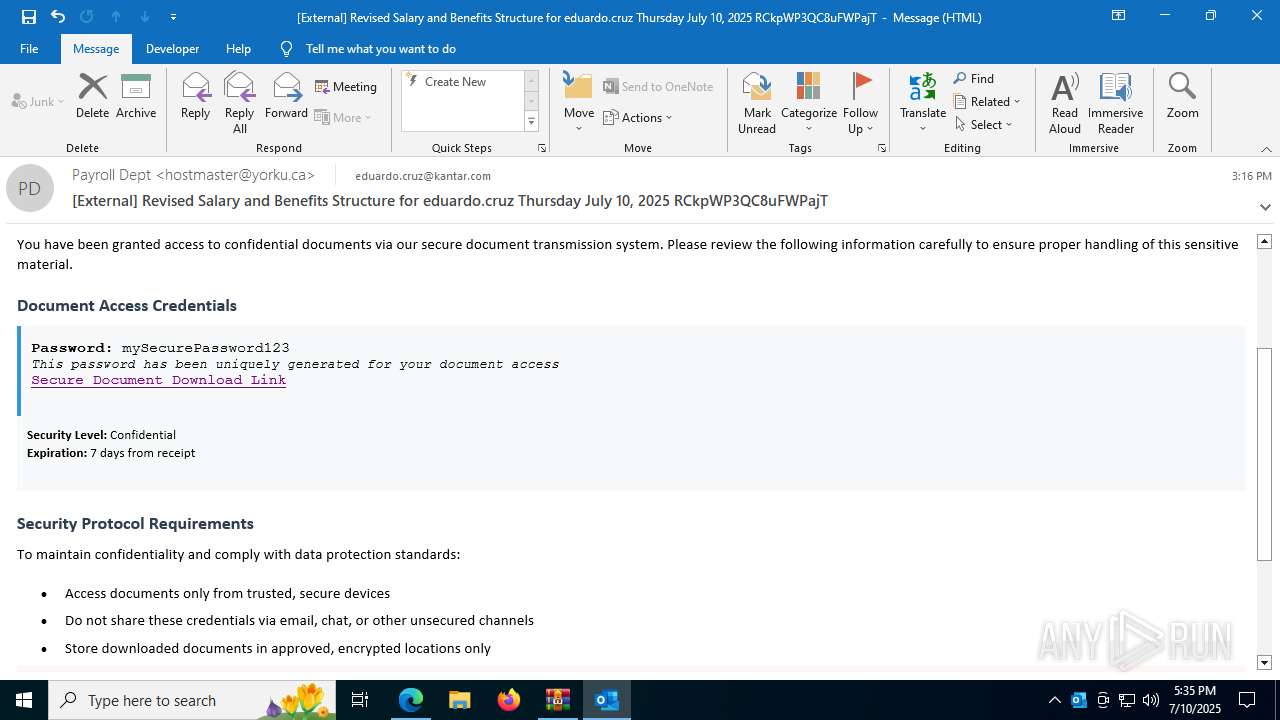
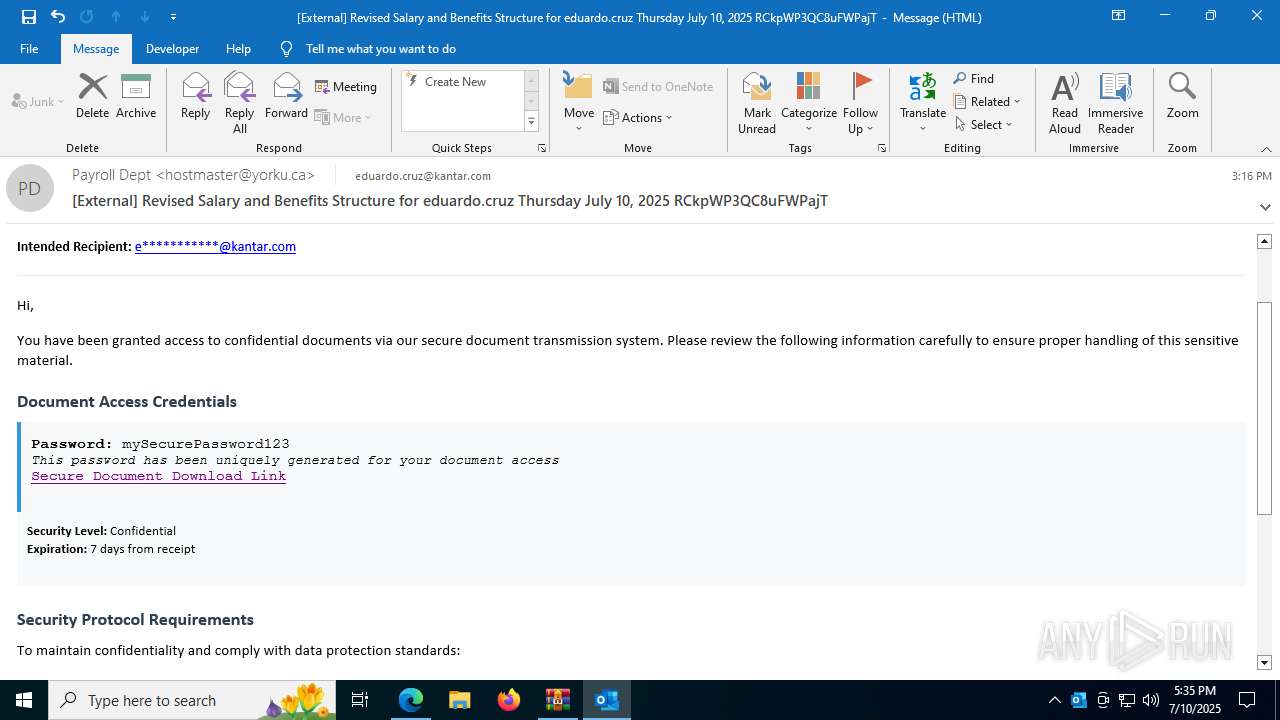
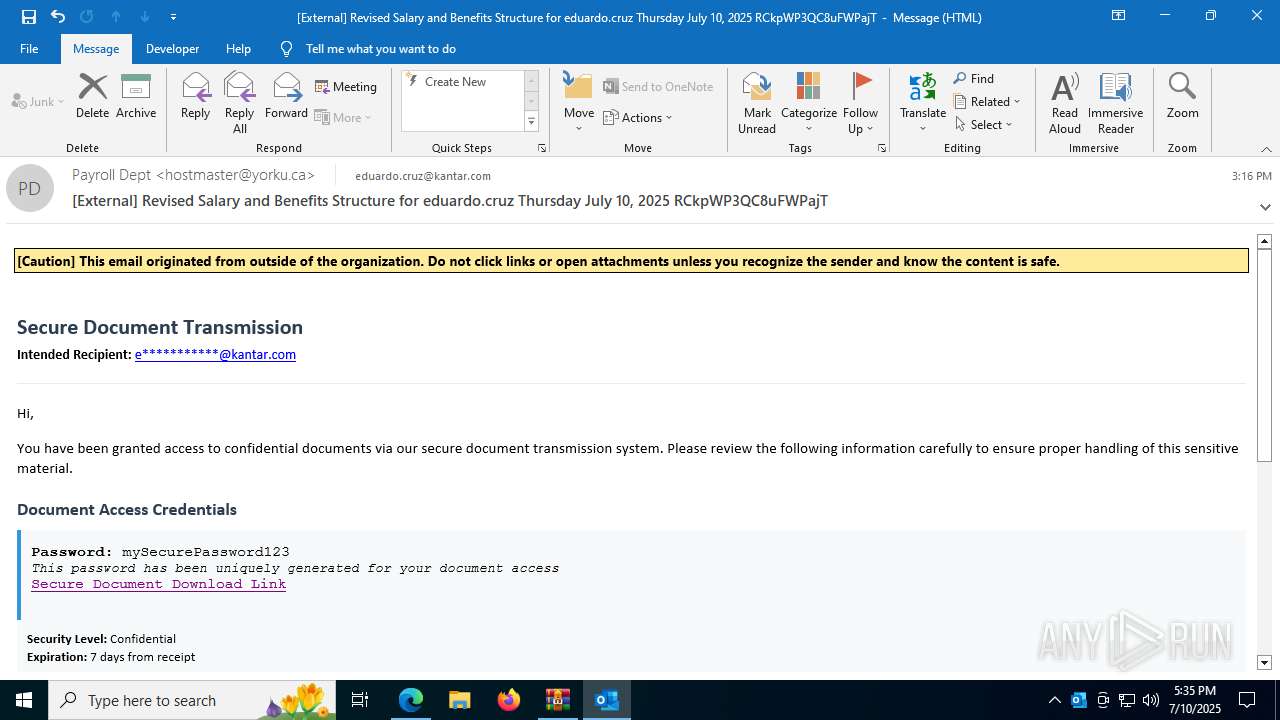
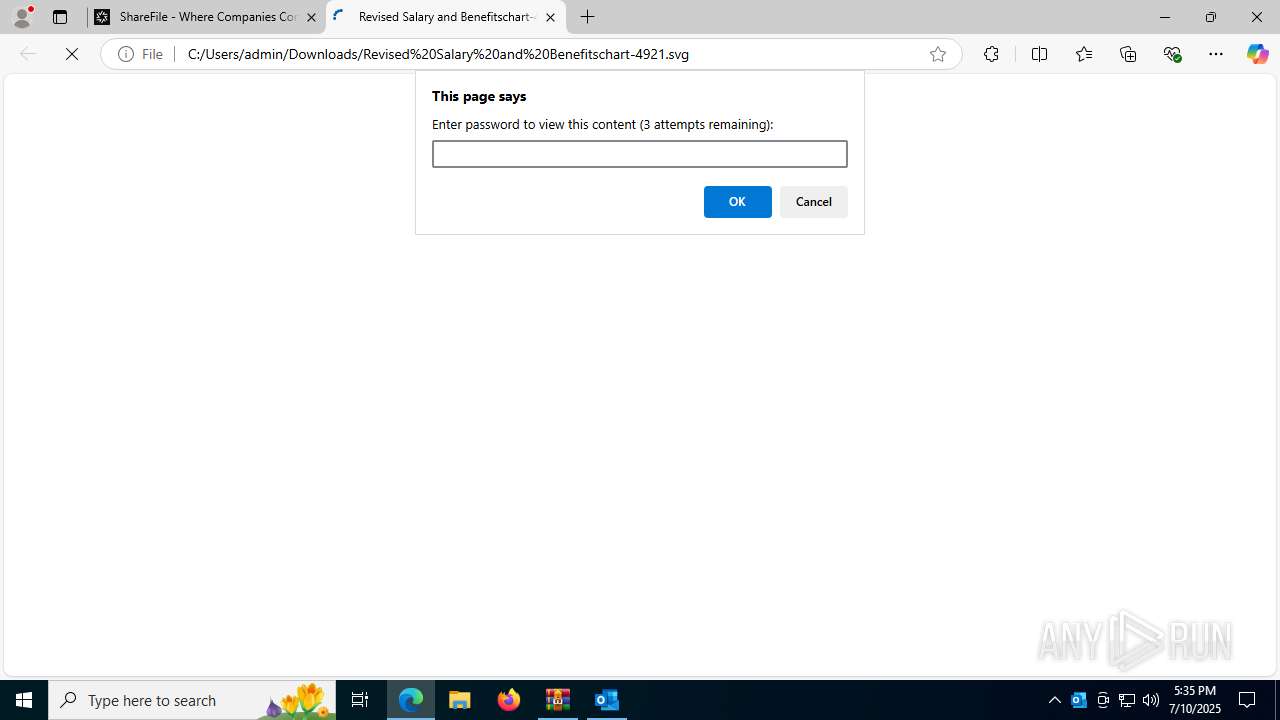
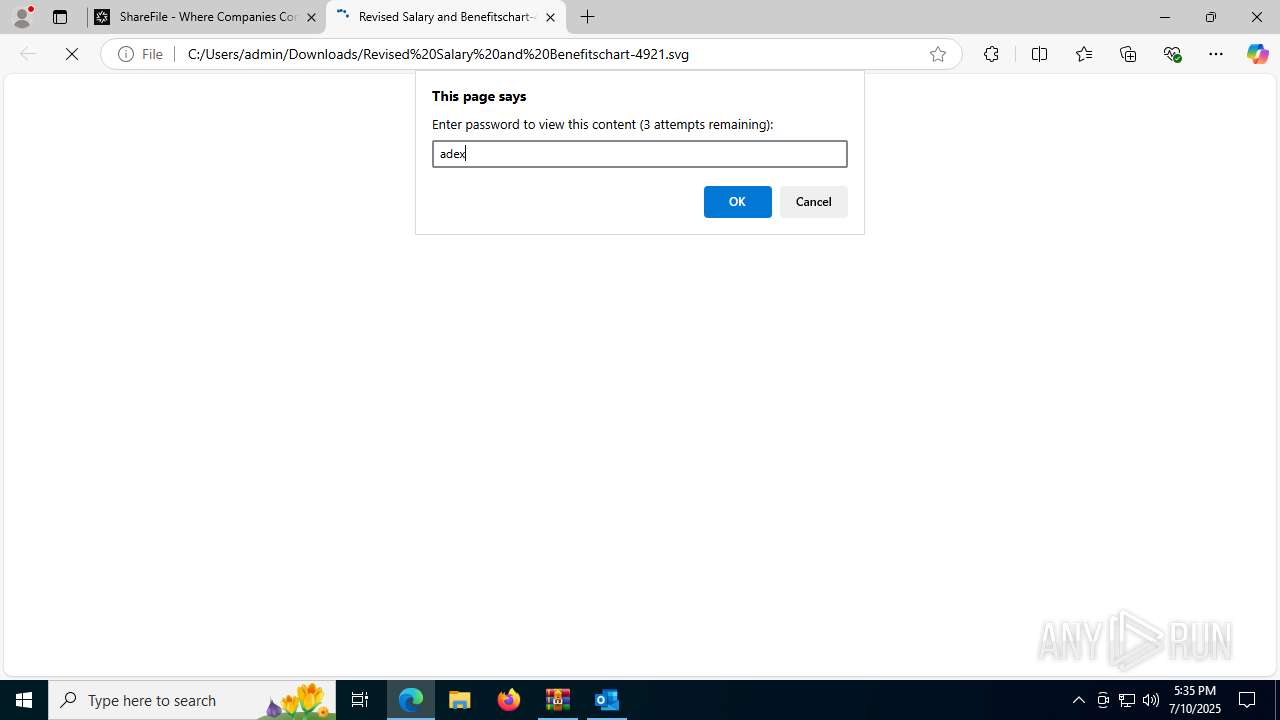
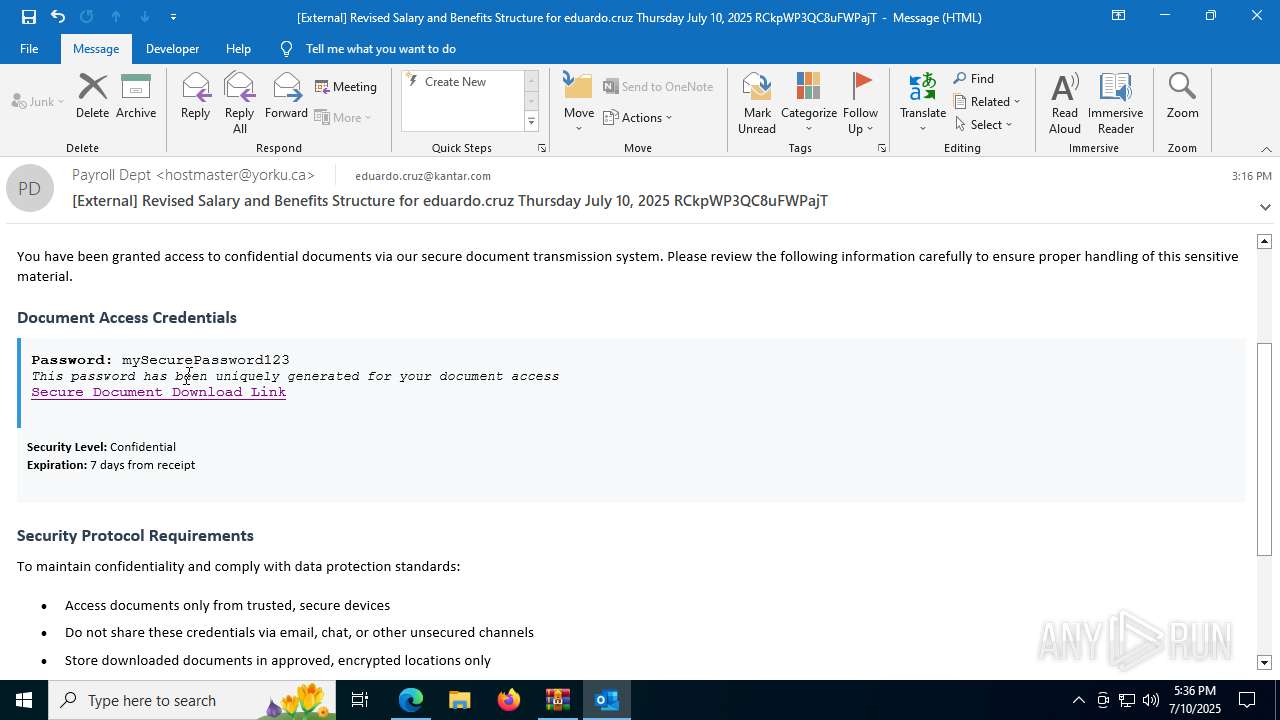
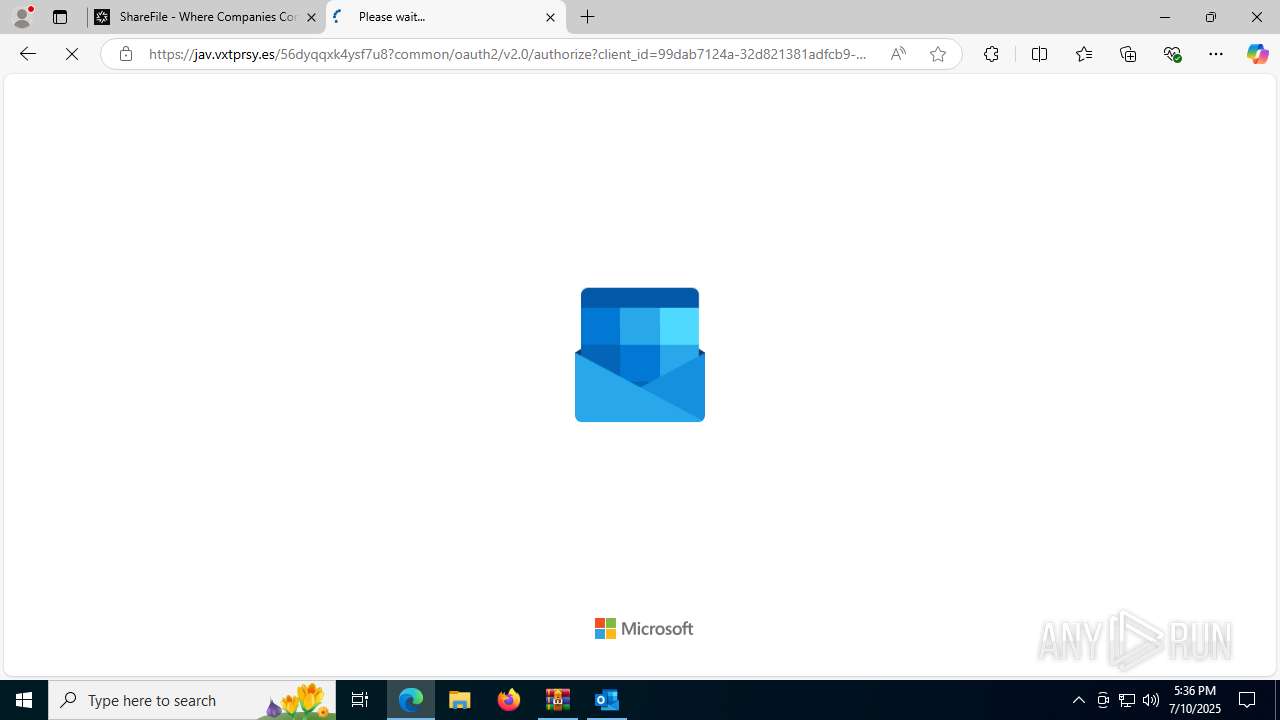
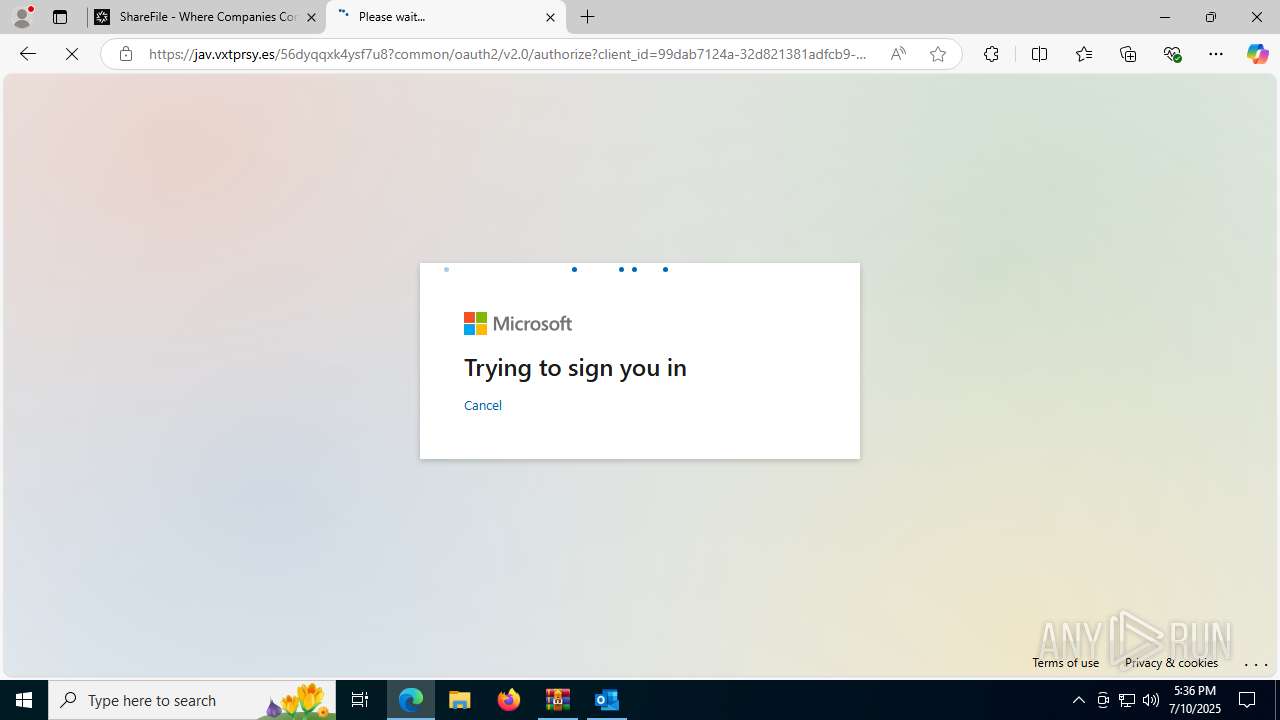
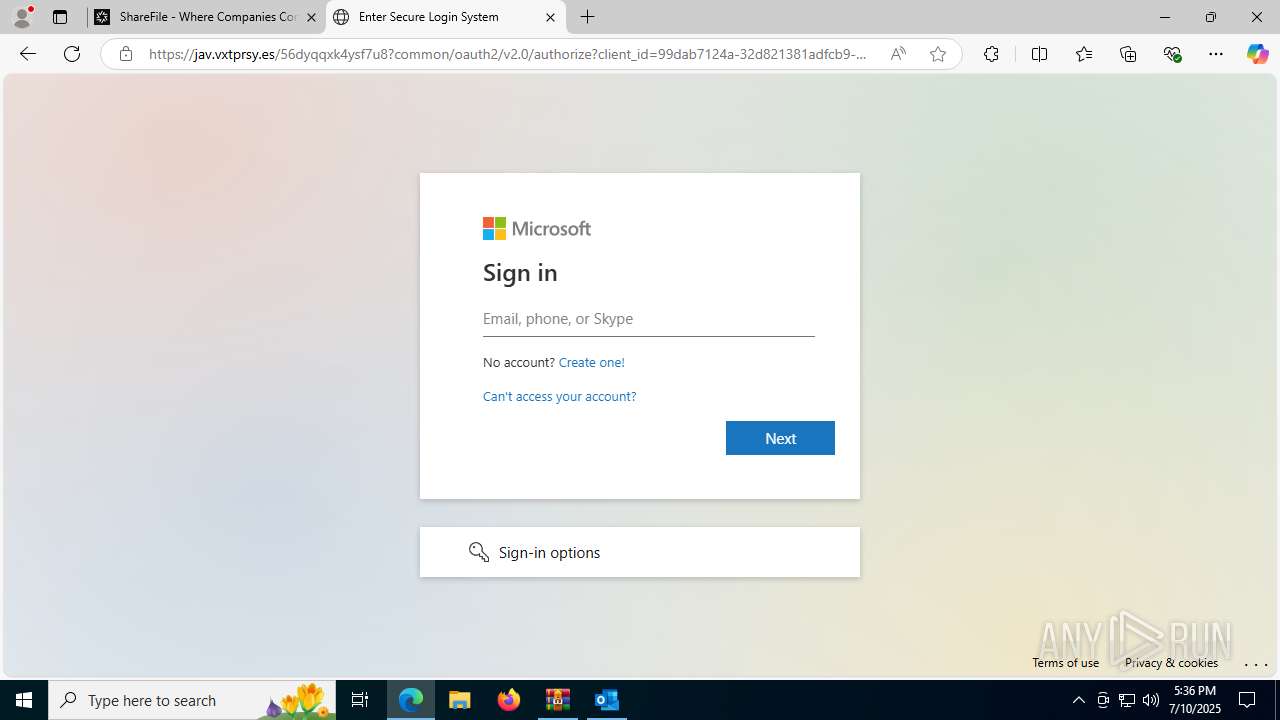
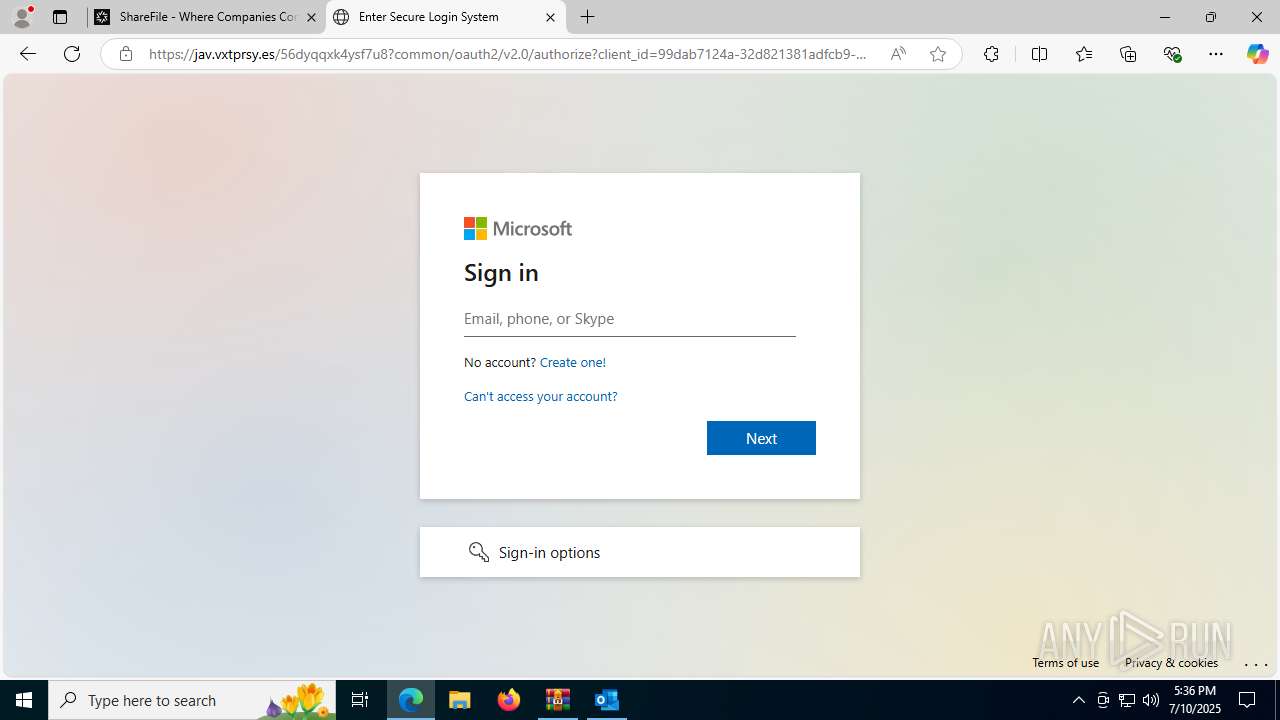
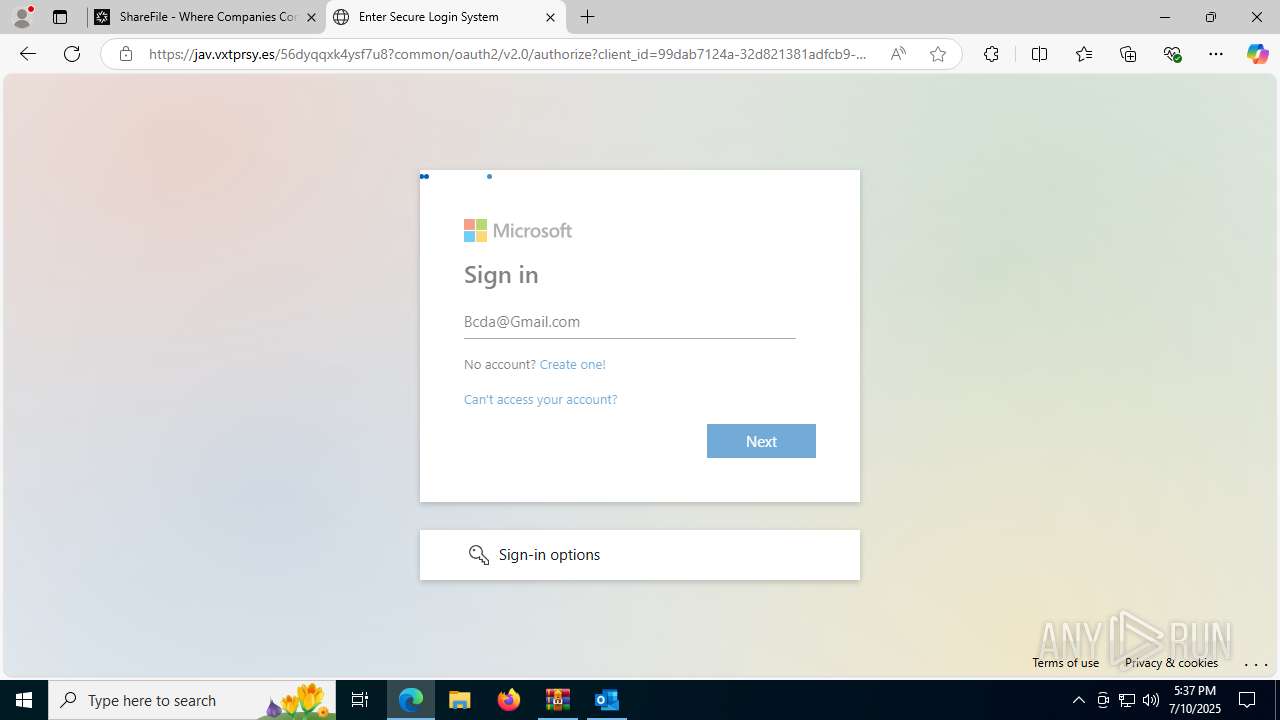
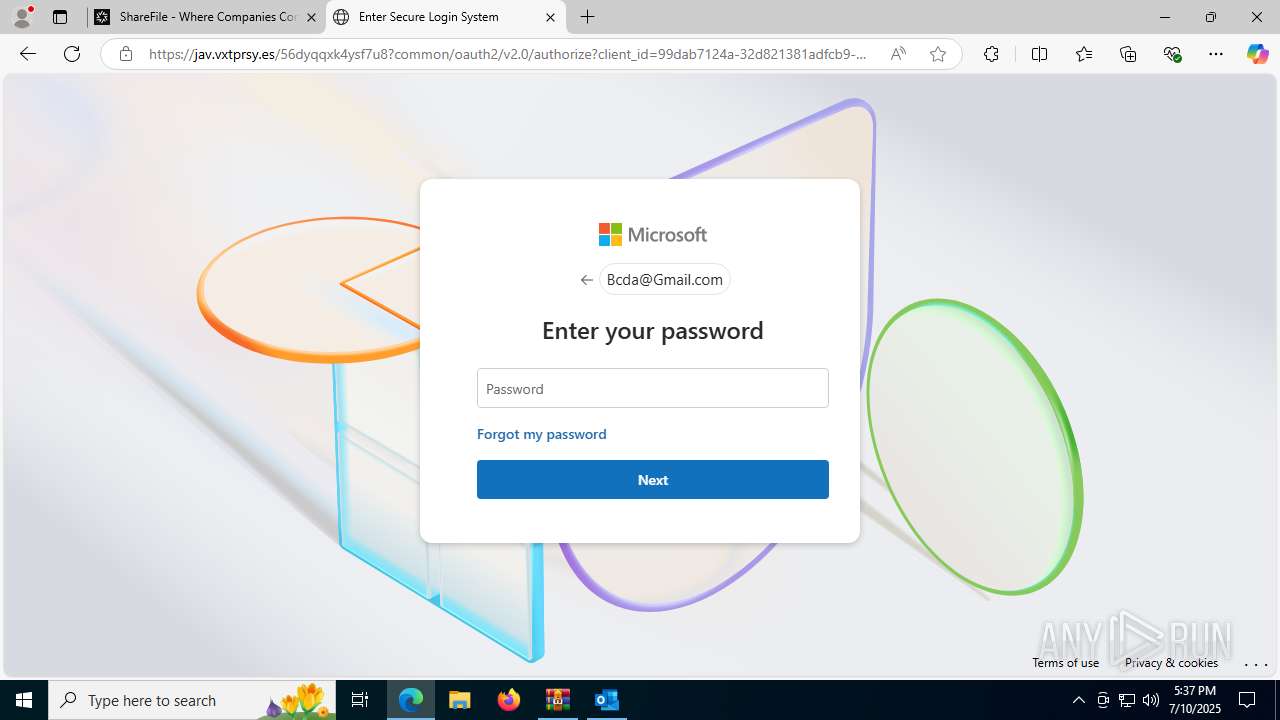
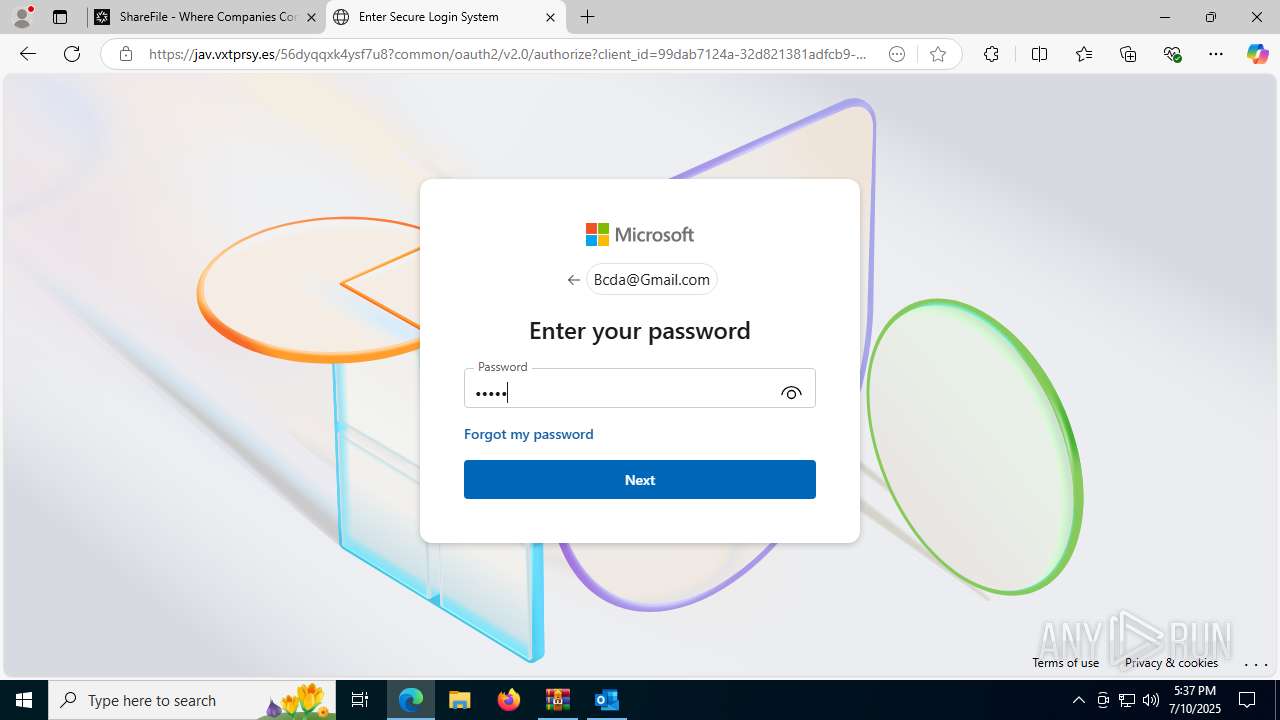
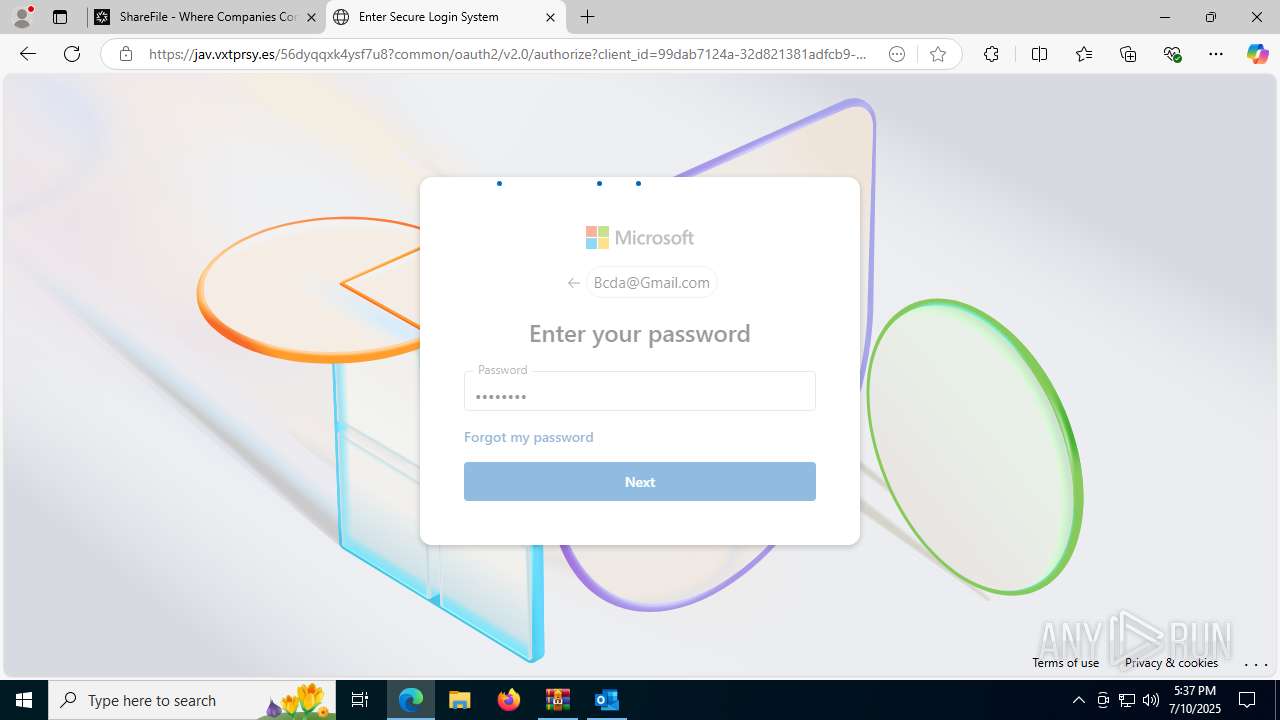
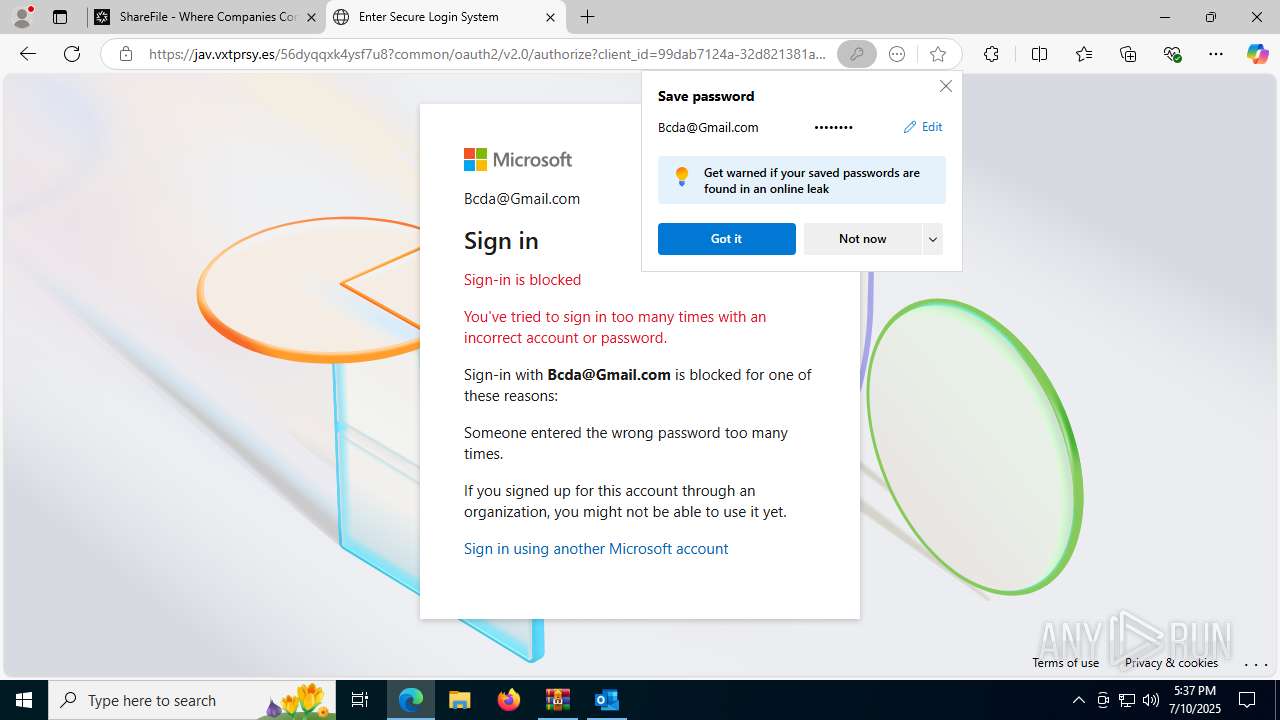
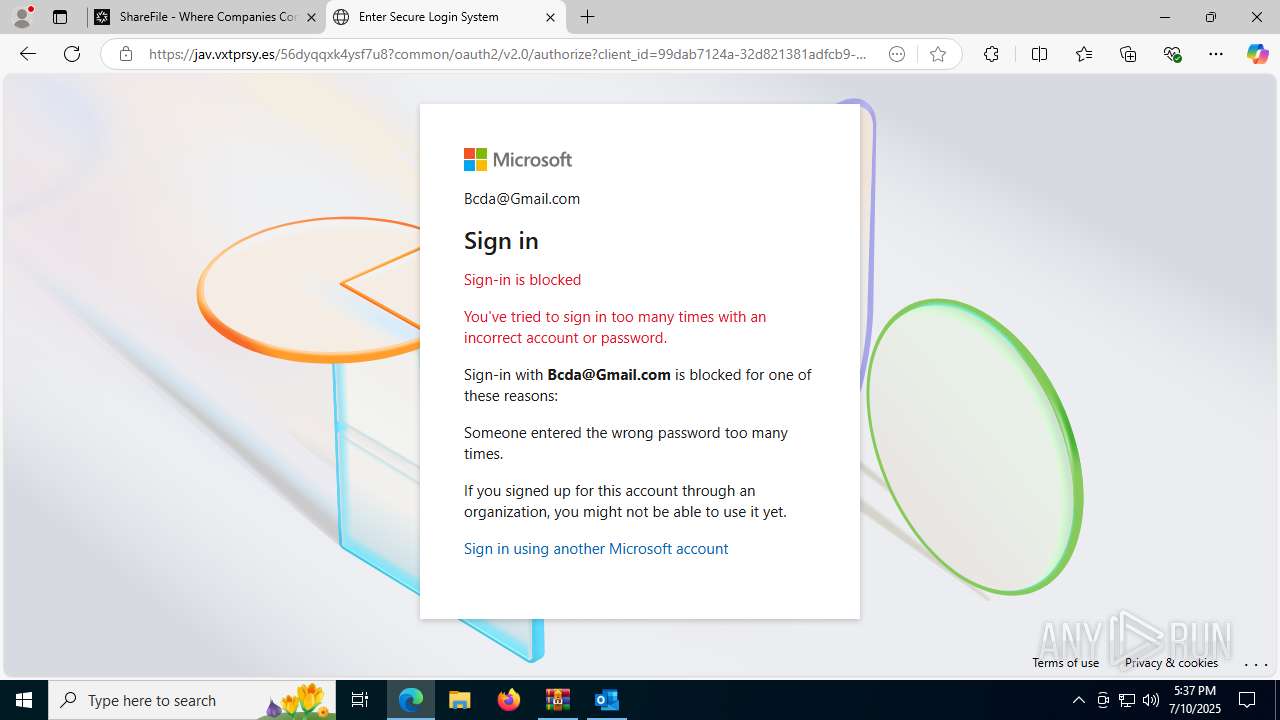
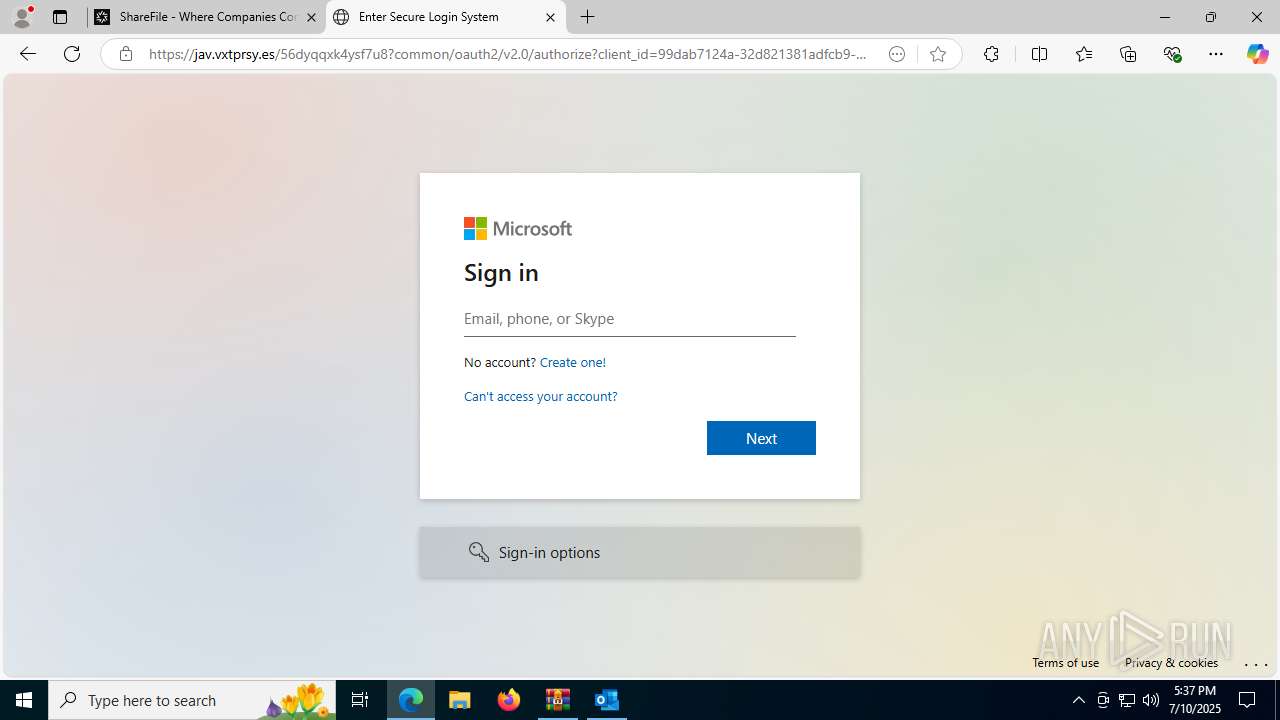
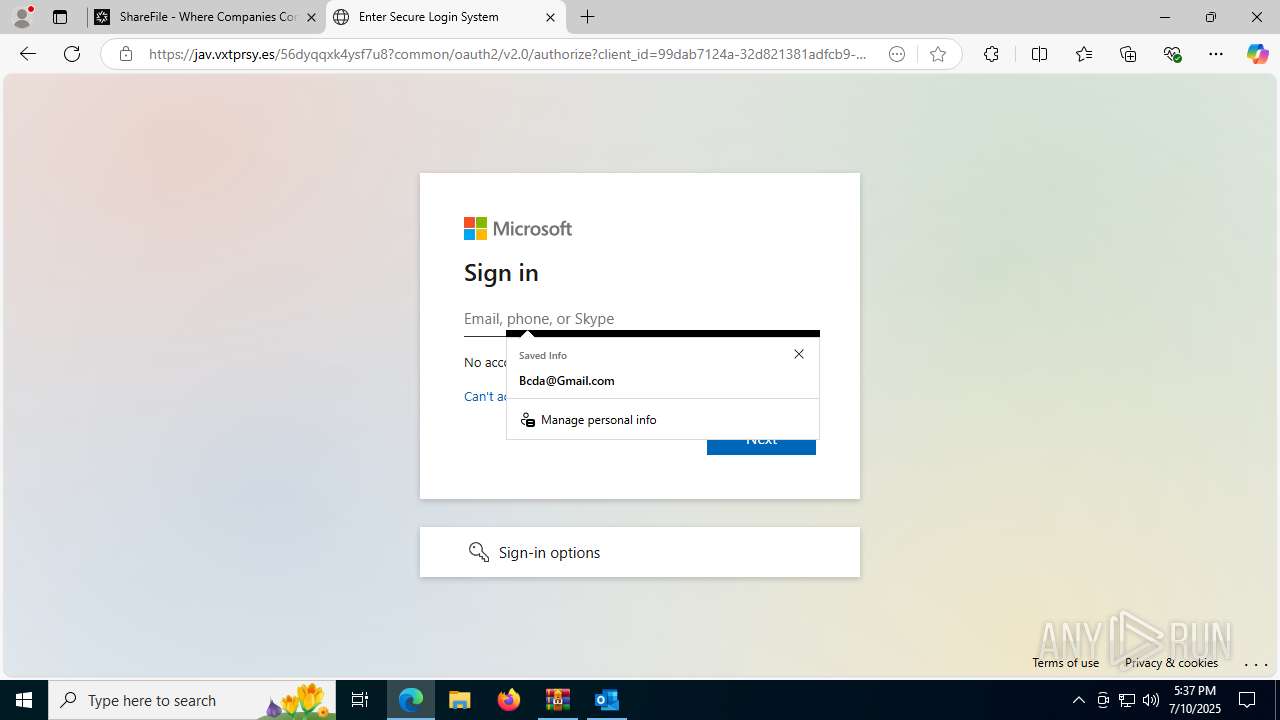
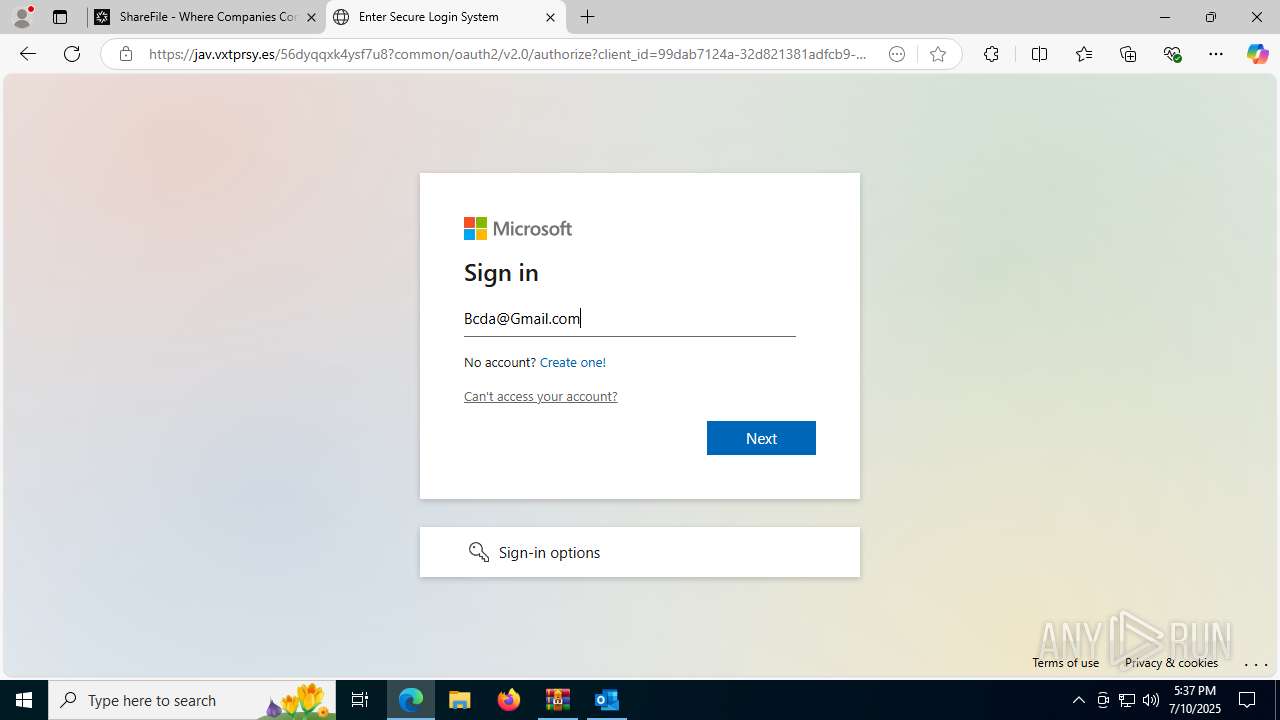
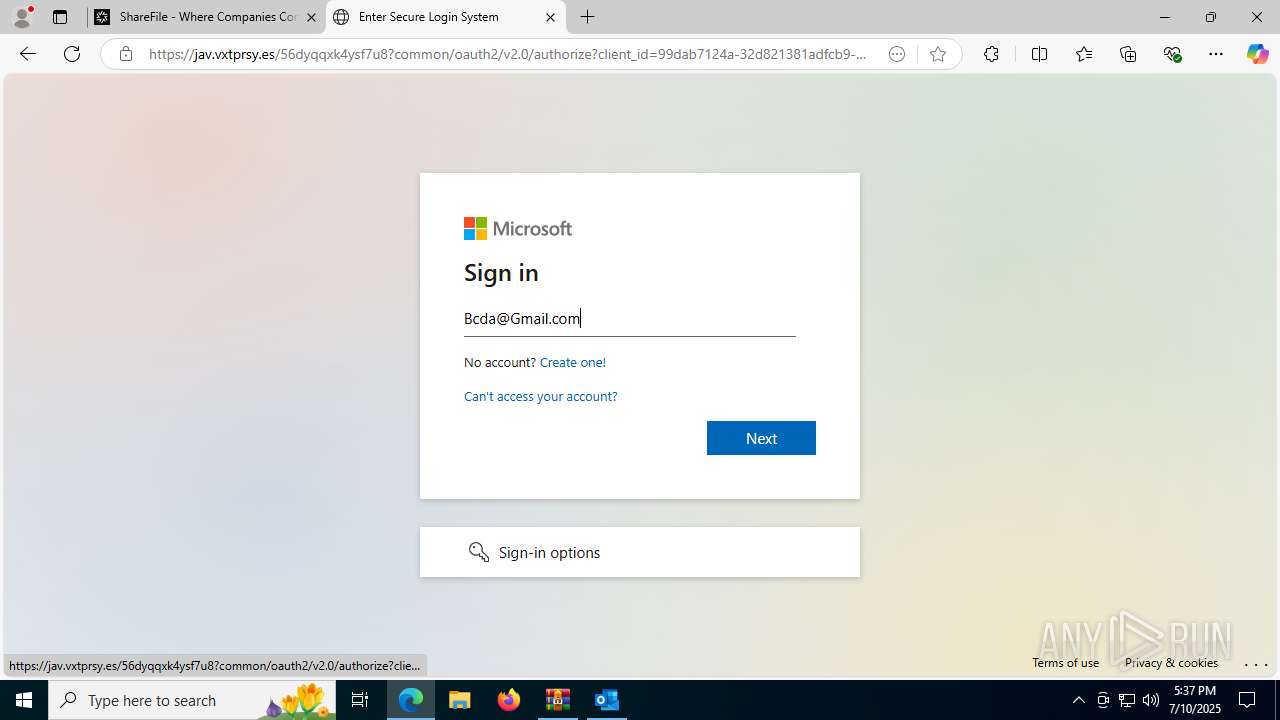
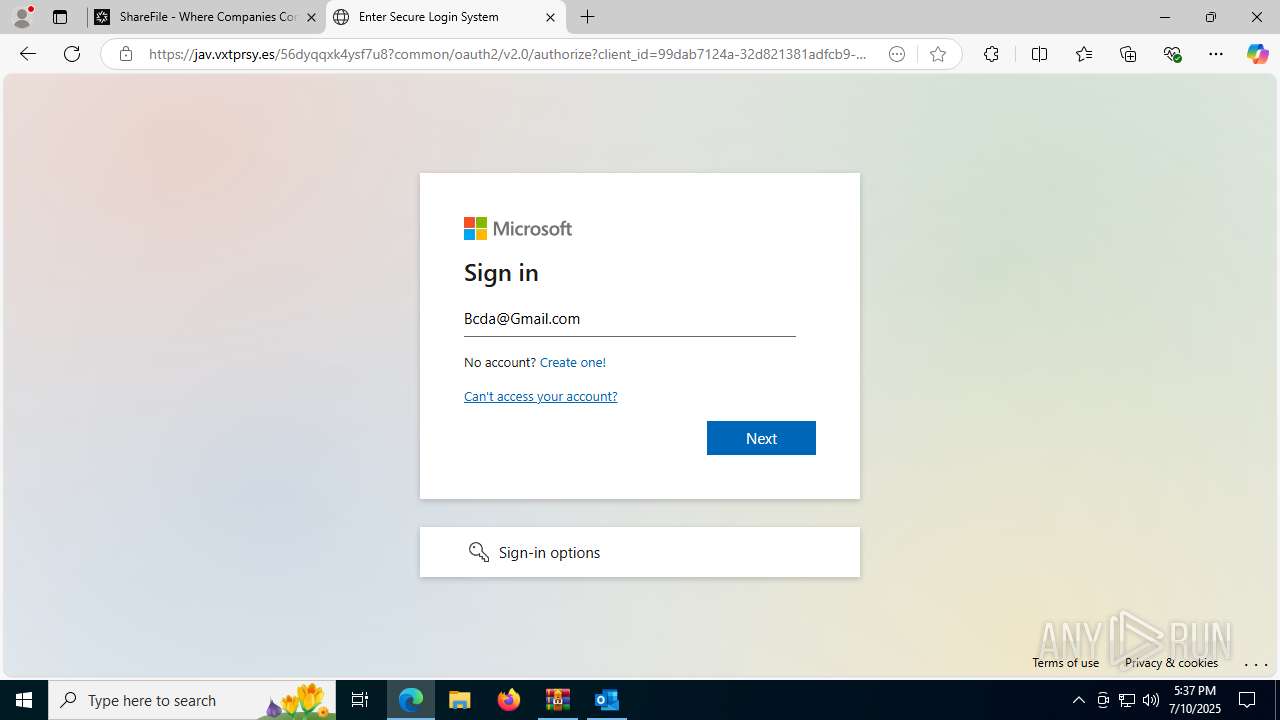
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | July 10, 2025, 17:34:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
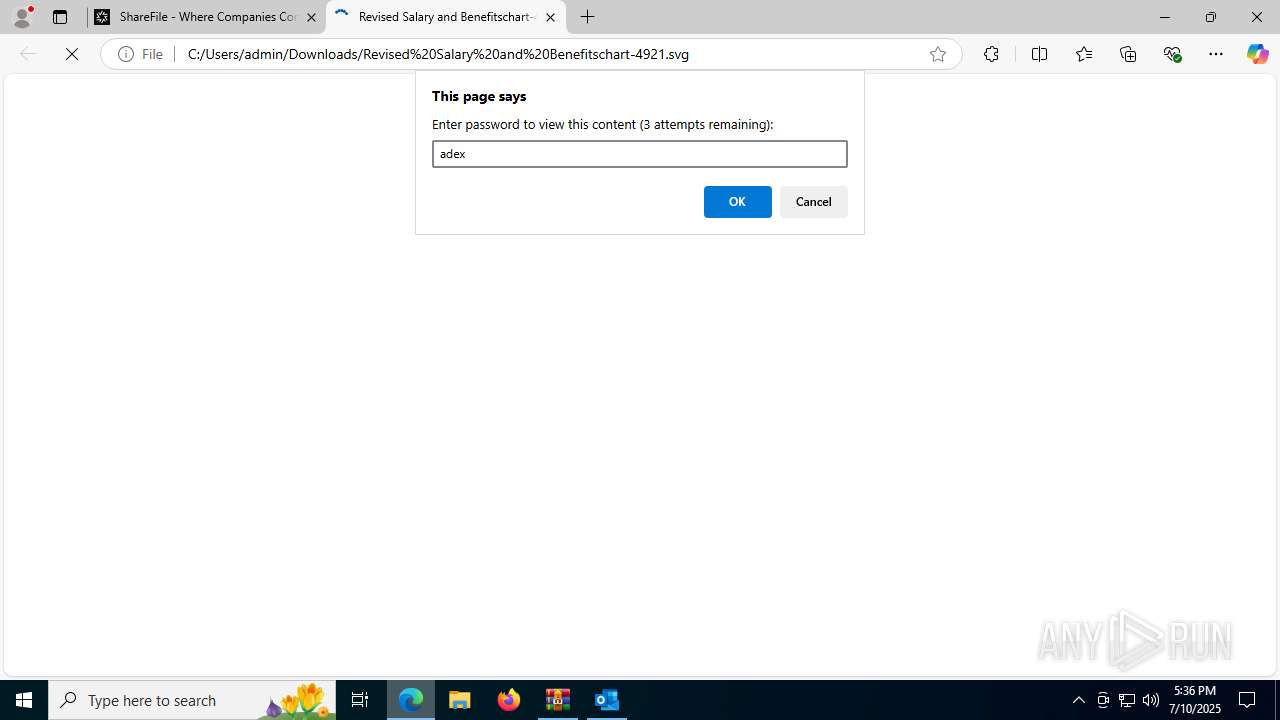
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | F9A88A7A5682463A1A20D98EA1B47C08 |
| SHA1: | 3EDFA520C6FCD66655CDB33163E34EA4B586D0D1 |
| SHA256: | 7F4A7512147AD50B1C64A35D7F96CC49D4F0D95E722CD28C2EEA43A073565930 |
| SSDEEP: | 192:8VAaFte592GDaTT0+5BN1k6KZa9HrFINvzee6vF1ULPlMwbJXhud+:PaqmTp5Rk69rbp4VXEU |
MALICIOUS
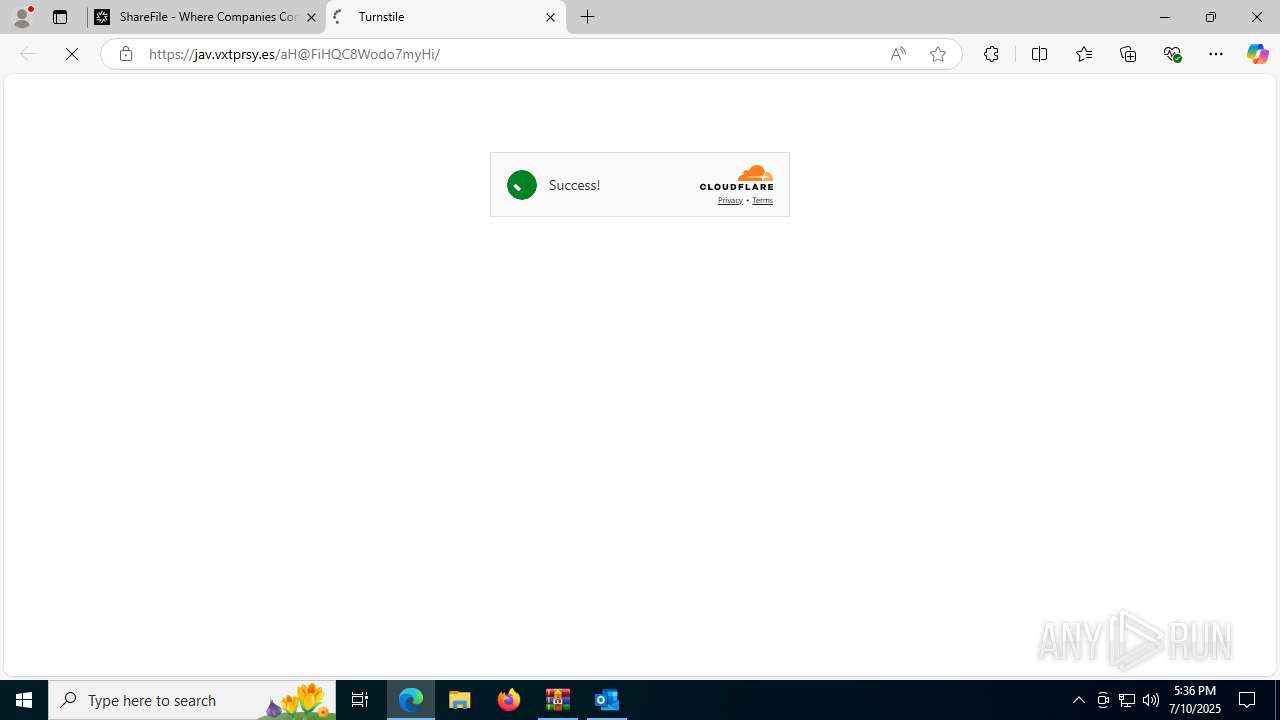
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 1520)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3540)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 3540)
INFO
Checks proxy server information
- slui.exe (PID: 7432)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3540)
Reads Environment values
- identity_helper.exe (PID: 7936)
Application launched itself
- msedge.exe (PID: 2032)
Reads the software policy settings
- slui.exe (PID: 7432)
Checks supported languages
- identity_helper.exe (PID: 7936)
Reads the computer name
- identity_helper.exe (PID: 7936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:10 17:33:20 |
| ZipCRC: | 0x19ff9d24 |
| ZipCompressedSize: | 4294967295 |
| ZipUncompressedSize: | 4294967295 |
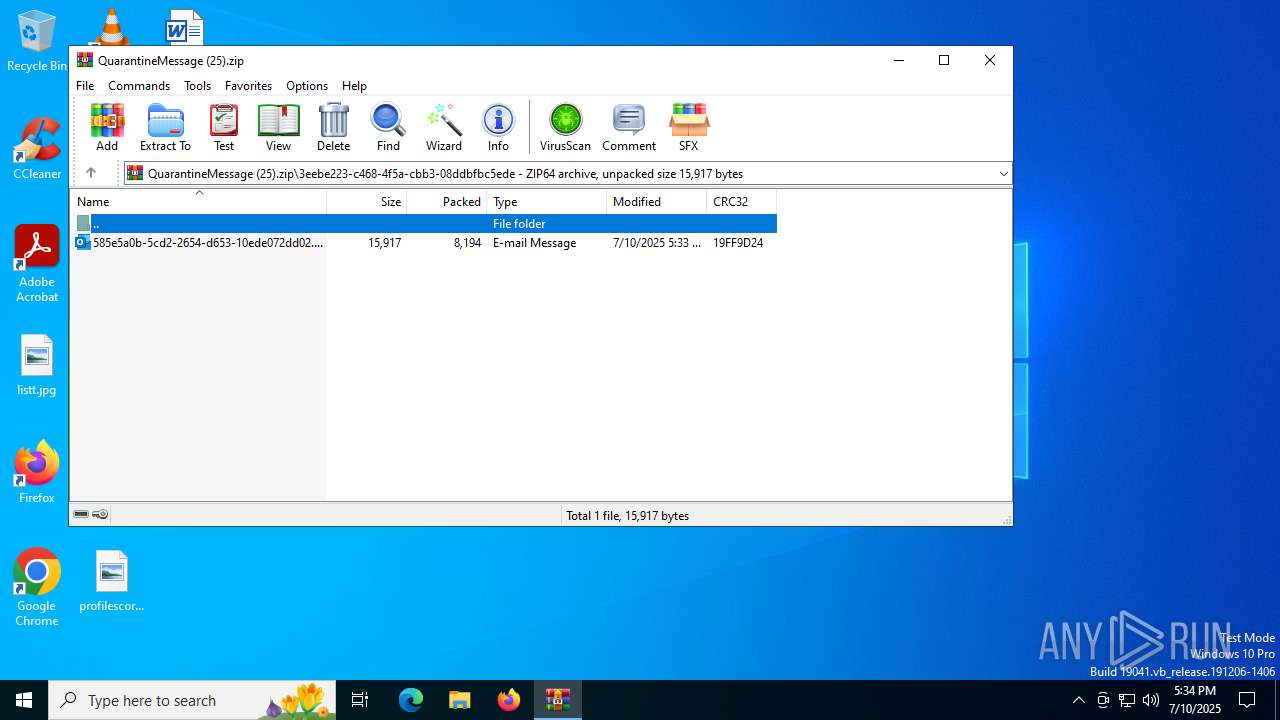
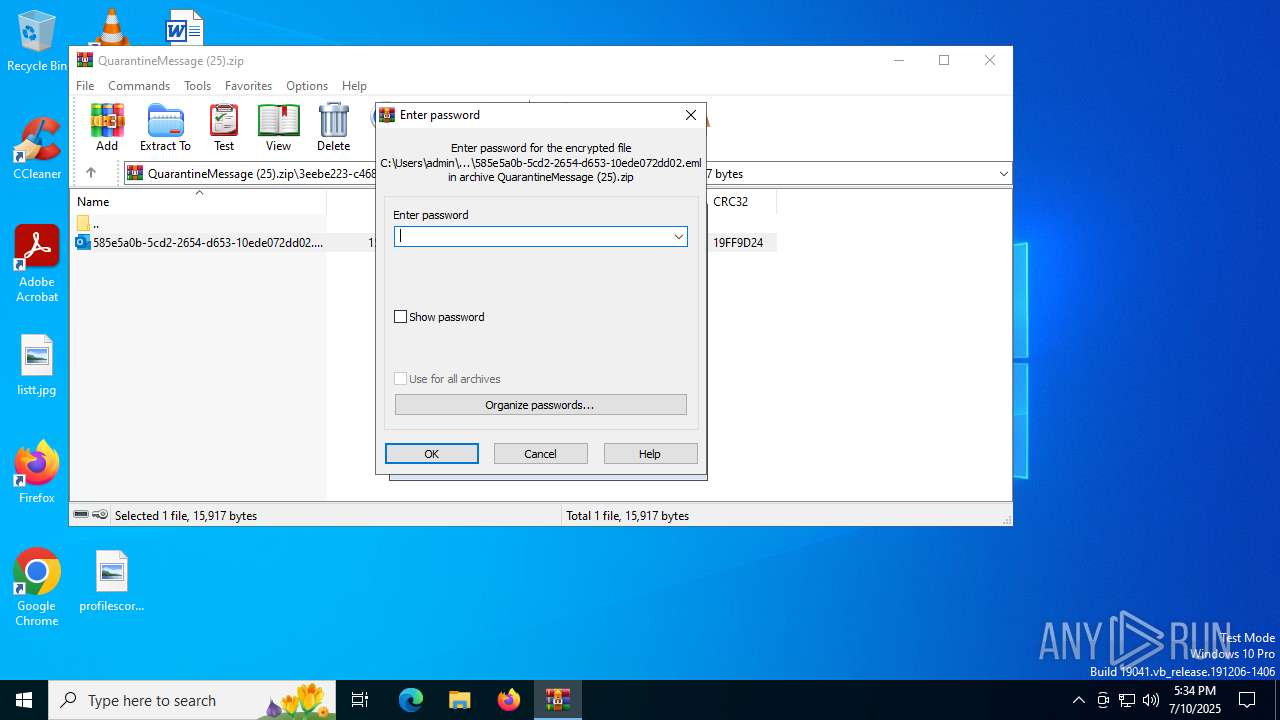
| ZipFileName: | 3eebe223-c468-4f5a-cbb3-08ddbfbc5ede/585e5a0b-5cd2-2654-d653-10ede072dd02.eml |
Total processes
184
Monitored processes
44
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --always-read-main-dll --field-trial-handle=5584,i,12471568069615272374,1379864636791256494,262144 --variations-seed-version --mojo-platform-channel-handle=5600 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 420 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=6904,i,12471568069615272374,1379864636791256494,262144 --variations-seed-version --mojo-platform-channel-handle=6856 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=29 --always-read-main-dll --field-trial-handle=7136,i,12471568069615272374,1379864636791256494,262144 --variations-seed-version --mojo-platform-channel-handle=7164 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2248,i,12471568069615272374,1379864636791256494,262144 --variations-seed-version --mojo-platform-channel-handle=2480 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
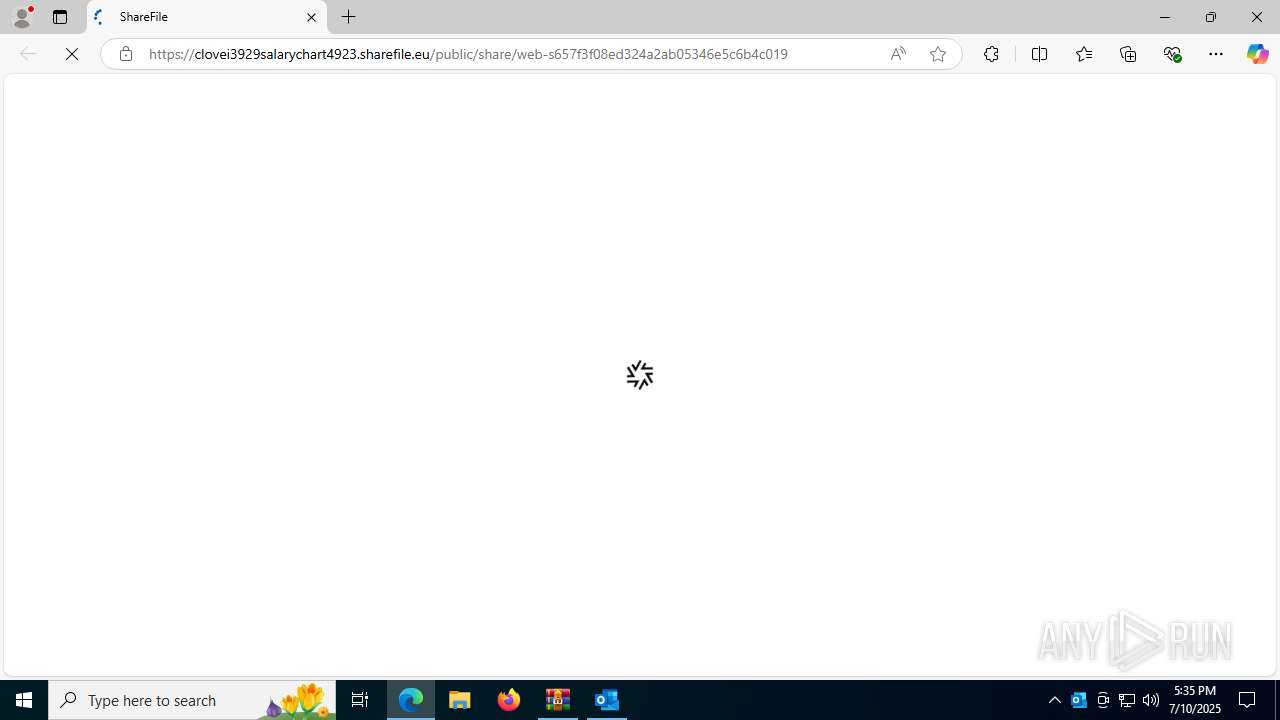
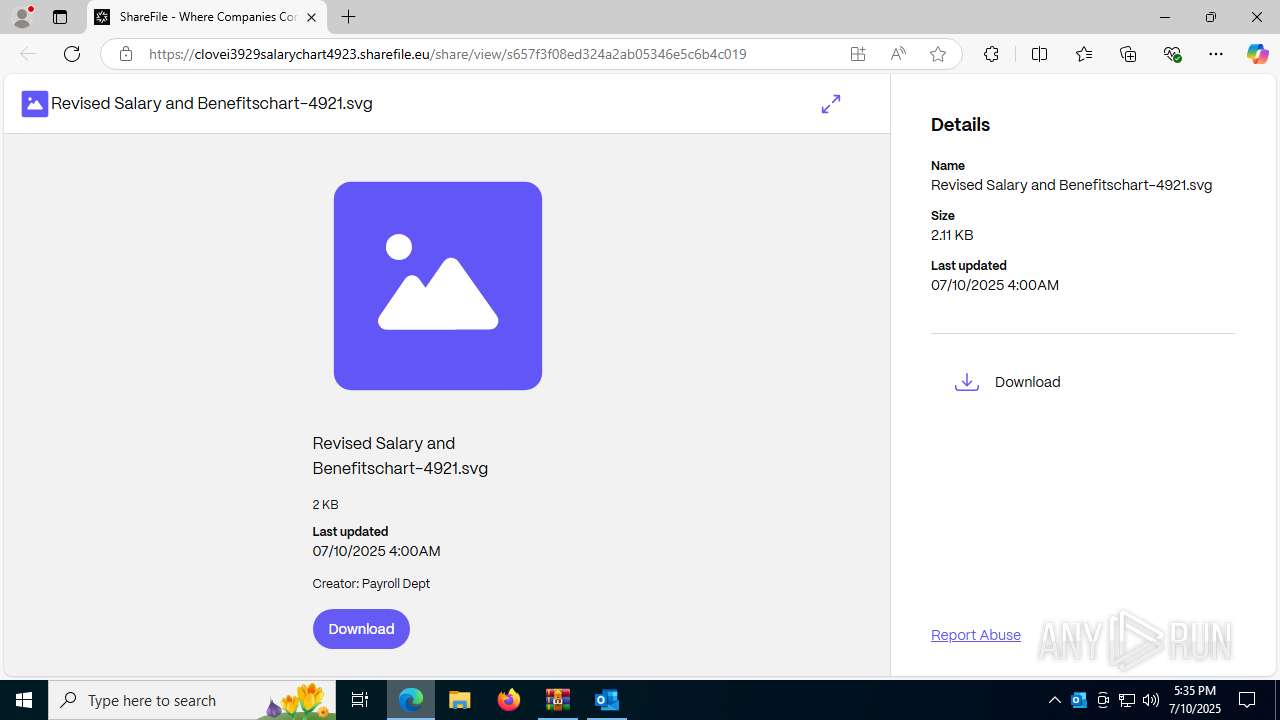
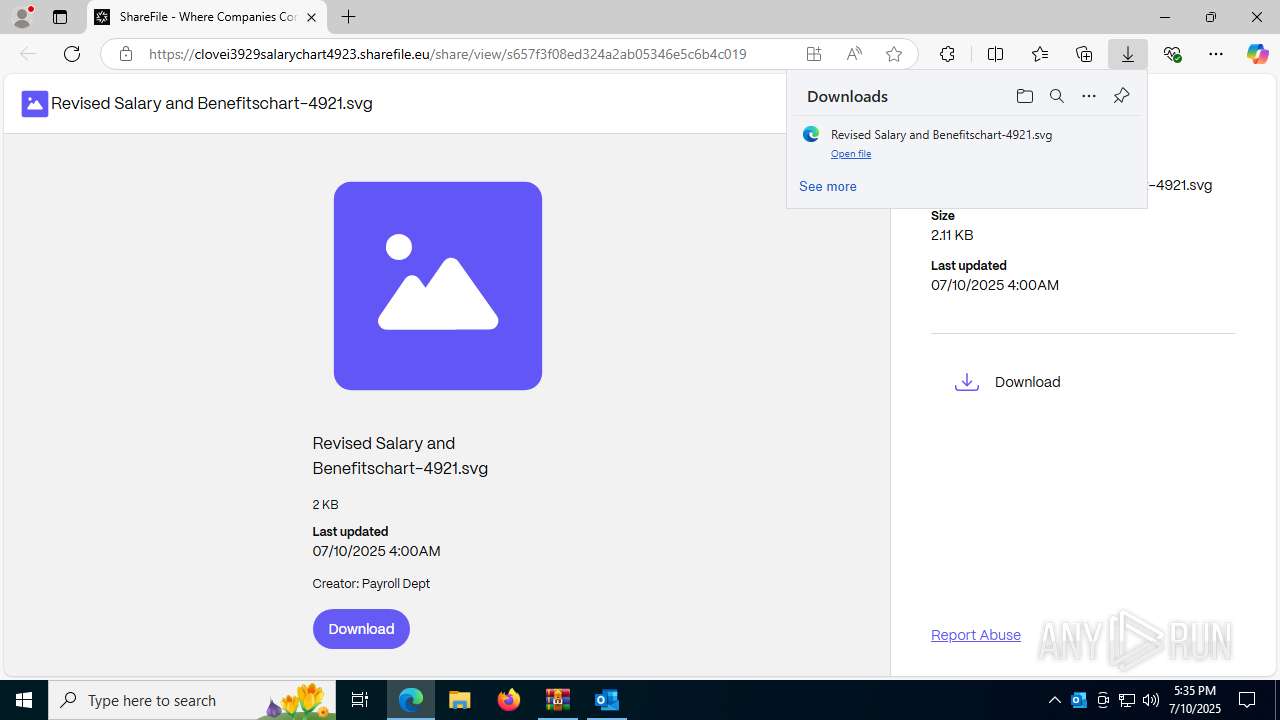
| 2032 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://clovei3929salarychart4923.sharefile.eu/public/share/web-s657f3f08ed324a2ab05346e5c6b4c019 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3540 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\QuarantineMessage (25).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3572 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3624,i,12471568069615272374,1379864636791256494,262144 --variations-seed-version --mojo-platform-channel-handle=3616 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=1452,i,12471568069615272374,1379864636791256494,262144 --variations-seed-version --mojo-platform-channel-handle=5408 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3580,i,12471568069615272374,1379864636791256494,262144 --variations-seed-version --mojo-platform-channel-handle=3644 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5716,i,12471568069615272374,1379864636791256494,262144 --variations-seed-version --mojo-platform-channel-handle=6924 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
19 583
Read events
19 029
Write events
451
Delete events
103
Modification events
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\QuarantineMessage (25).zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.eml\OpenWithProgids |
| Operation: | write | Name: | Outlook.File.eml.15 |
Value: | |||
Executable files
0
Suspicious files
240
Text files
91
Unknown types
60
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5552 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 2032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:EB0AECD0551E36D91C996742D6D5BA9D | SHA256:86A46850BEB77118A25CC1B816E93249F169ADB5794F99A66E08000CE87F7342 | |||
| 2032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:CDDDC745A8C954DC438C931889999BDB | SHA256:3DC9043838386F5363AC96A01477CF3163B5118B80191576A11B32CE9894314C | |||
| 2032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF17d9e5.TMP | — | |
MD5:— | SHA256:— | |||
| 5552 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\mso9328.tmp | image | |
MD5:ED3C1C40B68BA4F40DB15529D5443DEC | SHA256:039FE79B74E6D3D561E32D4AF570E6CA70DB6BB3718395BE2BF278B9E601279A | |||
| 2032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5552 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | der | |
MD5:FBFF52C4A4EE118720EA65A1BA44846D | SHA256:CB9F851D139947A2A35B1012B14623BF0B4476C234CE27C602D3E2453B861013 | |||
| 2032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF17da04.TMP | — | |
MD5:— | SHA256:— | |||
| 2032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2032 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF17da14.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
164
DNS requests
177
Threats
42
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5552 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2148 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1520 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:L7J1CuDHItBlMyvL4Hc_3AJfANaBKJuybU_RwVLPgl8&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4196 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7816 | svchost.exe | HEAD | 200 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1752548479&P2=404&P3=2&P4=iGnO8BOJvteEZCrVvE7rM9uj1ONCdGHpKTqall%2b3HCFRyjtoGzUq7GdAZRts6RsZL%2fXN%2fyK7bYmSwfhk4Ile4Q%3d%3d | unknown | — | — | whitelisted |
4196 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7816 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1752548479&P2=404&P3=2&P4=iGnO8BOJvteEZCrVvE7rM9uj1ONCdGHpKTqall%2b3HCFRyjtoGzUq7GdAZRts6RsZL%2fXN%2fyK7bYmSwfhk4Ile4Q%3d%3d | unknown | — | — | whitelisted |
7816 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1752548479&P2=404&P3=2&P4=iGnO8BOJvteEZCrVvE7rM9uj1ONCdGHpKTqall%2b3HCFRyjtoGzUq7GdAZRts6RsZL%2fXN%2fyK7bYmSwfhk4Ile4Q%3d%3d | unknown | — | — | whitelisted |
7816 | svchost.exe | HEAD | 200 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1752548485&P2=404&P3=2&P4=A4S%2bkA%2bzw1teld%2b3RJcTU7j7lSddRXHRNXrswukNYRSz611zwWZ3fXWH00uQt1IlJx6xLEwwxrwq16DXrTu%2bVQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6980 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2148 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2148 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
1520 | msedge.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1520 | msedge.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1520 | msedge.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
1520 | msedge.exe | Misc activity | ET FILE_SHARING External File Sharing Service in DNS Lookup (sharefile .com) |
1520 | msedge.exe | Misc activity | ET FILE_SHARING External File Sharing Service in DNS Lookup (sharefile .com) |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] JavaScript Obfuscation (ParseInt) |
1520 | msedge.exe | Misc activity | ET FILE_SHARING External File Sharing Service in DNS Lookup (sharefile .com) |
1520 | msedge.exe | Misc activity | ET FILE_SHARING External File Sharing Service in DNS Lookup (sharefile .com) |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] JavaScript Obfuscation (ParseInt) |