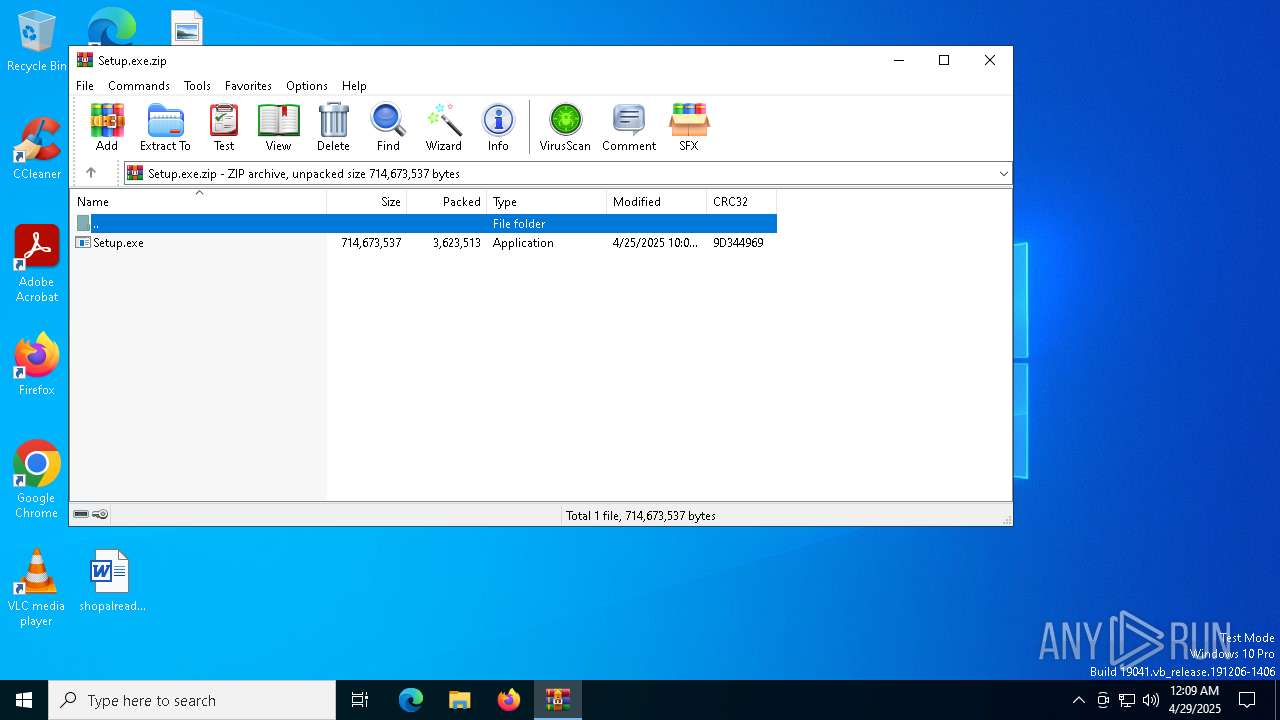
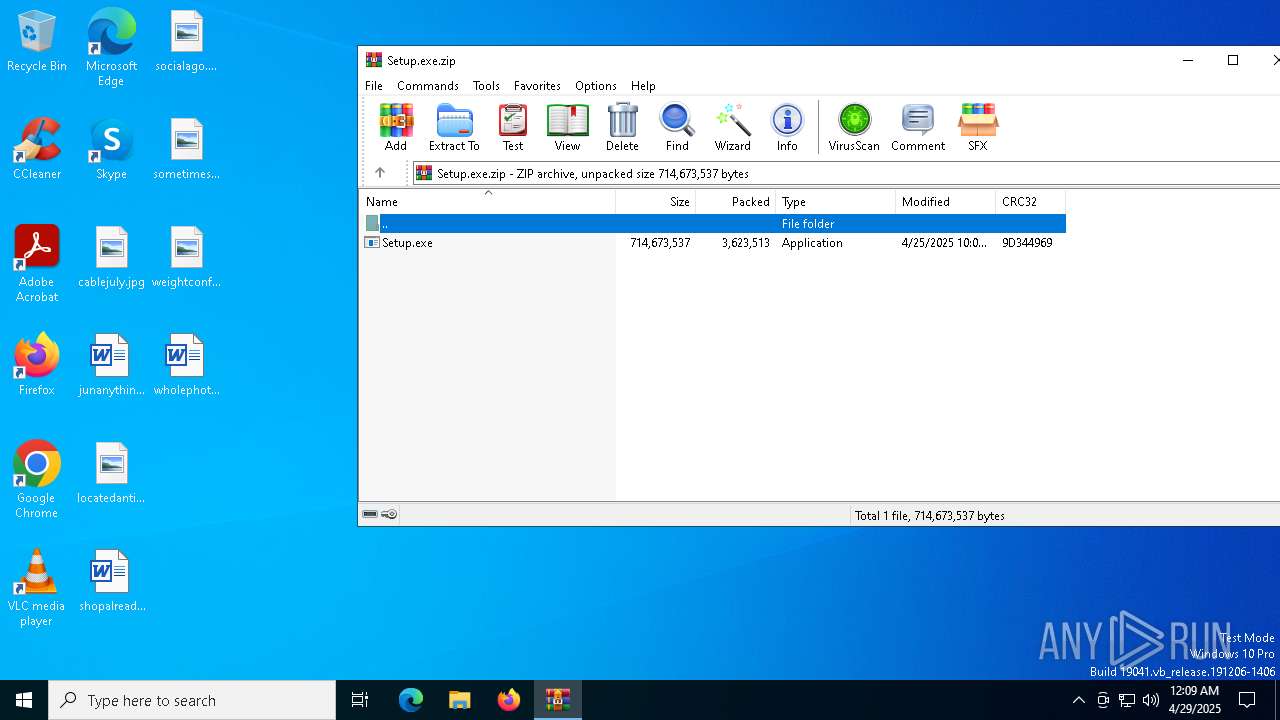
| File name: | Setup.exe.zip |
| Full analysis: | https://app.any.run/tasks/9f4e7ac4-7bb0-4cc9-8c81-cece18bacc27 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 29, 2025, 00:09:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 1B44D6BDB341D0E4441D1EF4D7C7058C |
| SHA1: | 6C913BF5DCAF0BF252BFEA02A538611EB6503CF5 |
| SHA256: | 7F35F29CD541E856E0B04E792D7819C87888DA8D03AA4D9F4222F3A6038B5DFE |
| SSDEEP: | 98304:cxBV980+BXgiA/KyZmzxGoBQO0Ly43xHbkdwpnYF4jB54zgw2ZhwFEHPRYg4+Wt2:2H9BxL0M9 |
MALICIOUS
Executing a file with an untrusted certificate
- Setup.exe (PID: 7832)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
- DN7N5W7KYSCVRJPJLUNALV9XIAP.exe (PID: 8136)
- Safari.exe (PID: 6308)
- asus_framework.exe (PID: 6332)
LUMMA mutex has been found
- Setup.exe (PID: 7832)
Actions looks like stealing of personal data
- Setup.exe (PID: 7832)
Changes the autorun value in the registry
- DN7N5W7KYSCVRJPJLUNALV9XIAP.exe (PID: 8136)
- reg.exe (PID: 7304)
SUSPICIOUS
Searches for installed software
- Setup.exe (PID: 7832)
Executable content was dropped or overwritten
- Setup.exe (PID: 7832)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
- DN7N5W7KYSCVRJPJLUNALV9XIAP.exe (PID: 8136)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6272)
Executes application which crashes
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Starts CMD.EXE for commands execution
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Adds/modifies Windows certificates
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Connects to unusual port
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 1108)
INFO
Compiled with Borland Delphi (YARA)
- Setup.exe (PID: 7832)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Manual execution by a user
- Setup.exe (PID: 7832)
- Safari.exe (PID: 6308)
- asus_framework.exe (PID: 6332)
Detects InnoSetup installer (YARA)
- Setup.exe (PID: 7832)
Reads the software policy settings
- Setup.exe (PID: 7832)
- slui.exe (PID: 7348)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
- slui.exe (PID: 896)
Checks supported languages
- Setup.exe (PID: 7832)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
- DN7N5W7KYSCVRJPJLUNALV9XIAP.exe (PID: 8136)
Reads the computer name
- Setup.exe (PID: 7832)
- DN7N5W7KYSCVRJPJLUNALV9XIAP.exe (PID: 8136)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Create files in a temporary directory
- Setup.exe (PID: 7832)
The sample compiled with english language support
- Setup.exe (PID: 7832)
- DN7N5W7KYSCVRJPJLUNALV9XIAP.exe (PID: 8136)
Creates files in the program directory
- DN7N5W7KYSCVRJPJLUNALV9XIAP.exe (PID: 8136)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Drops encrypted JS script (Microsoft Script Encoder)
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Reads the machine GUID from the registry
- QZDI4YY7FMIR0ZB2.exe (PID: 8112)
Checks proxy server information
- slui.exe (PID: 896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:26 06:05:12 |
| ZipCRC: | 0x9d344969 |
| ZipCompressedSize: | 3623513 |
| ZipUncompressedSize: | 714673537 |
| ZipFileName: | Setup.exe |
Total processes
258
Monitored processes
22
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3272 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8112 -s 580 | C:\Windows\SysWOW64\WerFault.exe | — | QZDI4YY7FMIR0ZB2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
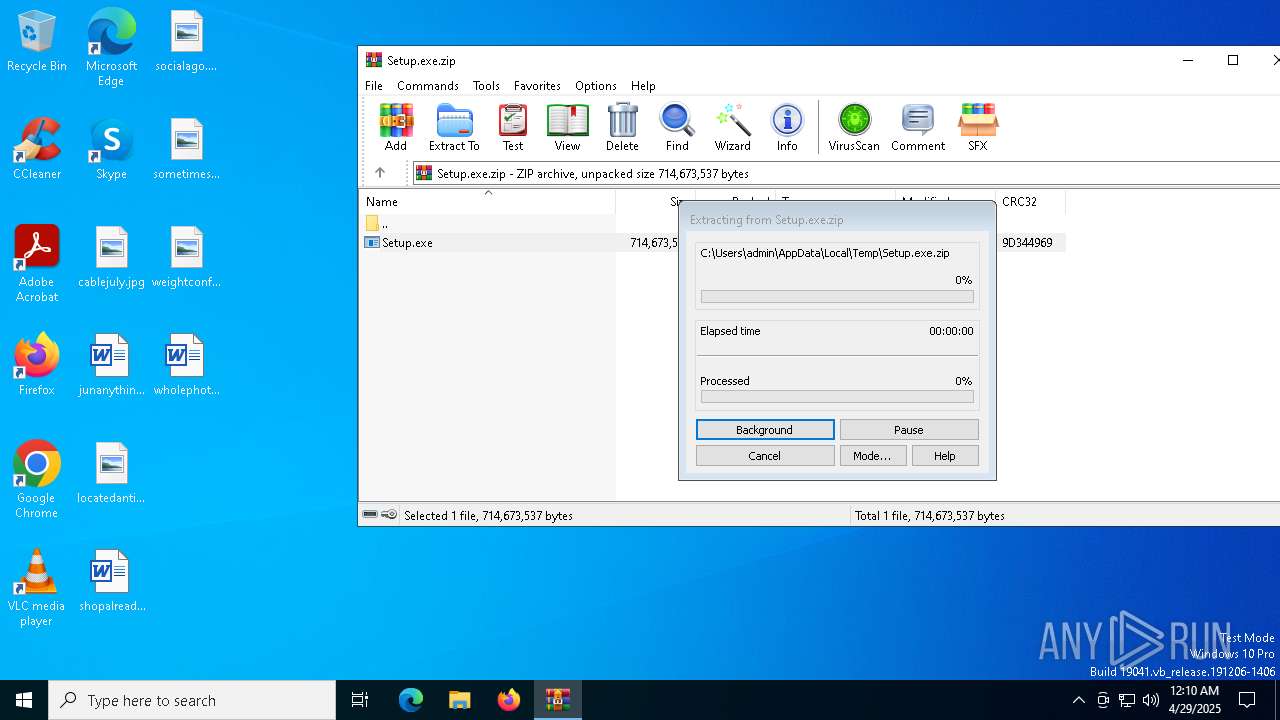
| 4108 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Setup.exe.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5204 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8112 -s 616 | C:\Windows\SysWOW64\WerFault.exe | — | QZDI4YY7FMIR0ZB2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5256 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8112 -s 476 | C:\Windows\SysWOW64\WerFault.exe | — | QZDI4YY7FMIR0ZB2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8112 -s 564 | C:\Windows\SysWOW64\WerFault.exe | — | QZDI4YY7FMIR0ZB2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6108 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8112 -s 1476 | C:\Windows\SysWOW64\WerFault.exe | — | QZDI4YY7FMIR0ZB2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | cmd /c "reg add HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce /v asus_framework /t REG_SZ /d C:\ProgramData\asus_framework.exe /f" | C:\Windows\SysWOW64\cmd.exe | — | QZDI4YY7FMIR0ZB2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6308 | "C:\ProgramData\Safari\Safari.exe" | C:\ProgramData\Safari\Safari.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Version: 14.09 Modules
| |||||||||||||||
Total events
10 311
Read events
10 265
Write events
34
Delete events
12
Modification events
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Setup.exe.zip | |||
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8136) DN7N5W7KYSCVRJPJLUNALV9XIAP.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Autoruns |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (4108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF5E0100002D0000001E05000016020000 | |||
Executable files
4
Suspicious files
44
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4108.21144\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 8112 | QZDI4YY7FMIR0ZB2.exe | C:\ProgramData\asus_framework.exe | executable | |
MD5:2448B111E9296FAB8436D43491763F70 | SHA256:AED18FB2C72B8239C28FB48EBD76B6E89FF3E4E3DD7E8BFFE2582C553C57D880 | |||
| 1108 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 1108 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 1108 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.038.etl | binary | |
MD5:F9485F2BA891697F8B6CF8FB1E7F42C0 | SHA256:69146D4AAEFB8609745B6CA780B48ABC66054AA3CDB8061248CF7B32F3B32617 | |||
| 1108 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 1108 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.042.etl | binary | |
MD5:C1F87CF12DD702D2185E703BA004D216 | SHA256:9D993487866C9538DC19F281A6346E1796E7478C7C164D61437AF6E698C66125 | |||
| 1108 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.046.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 1108 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:89BD161BF7B46C9078937CF832786737 | SHA256:2B83DF5532E9F54ED301C8F82E2CDD489799C8D5222A2D44C97DCB151A96FAA9 | |||
| 1108 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.043.etl | binary | |
MD5:8A2BDE0EAFA7E946196A1B114AB636E9 | SHA256:1C338CBDD9316D7FD8F208341466FEDC554A04D489B3A86C736EC3831A2F2BA2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
62
DNS requests
29
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7908 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7908 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7908 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7908 | SIHClient.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nodepathr.run |
| unknown |
h1.startingshabby.world |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES DNS Query to Commonly Actor Abused Online Service (data-seed-prebsc-2-s1 .binance .org) |
8112 | QZDI4YY7FMIR0ZB2.exe | Misc activity | ET TA_ABUSED_SERVICES Observed Commonly Actor Abused Online Service Domain (data-seed-prebsc-2-s1 .binance .org in TLS SNI) |