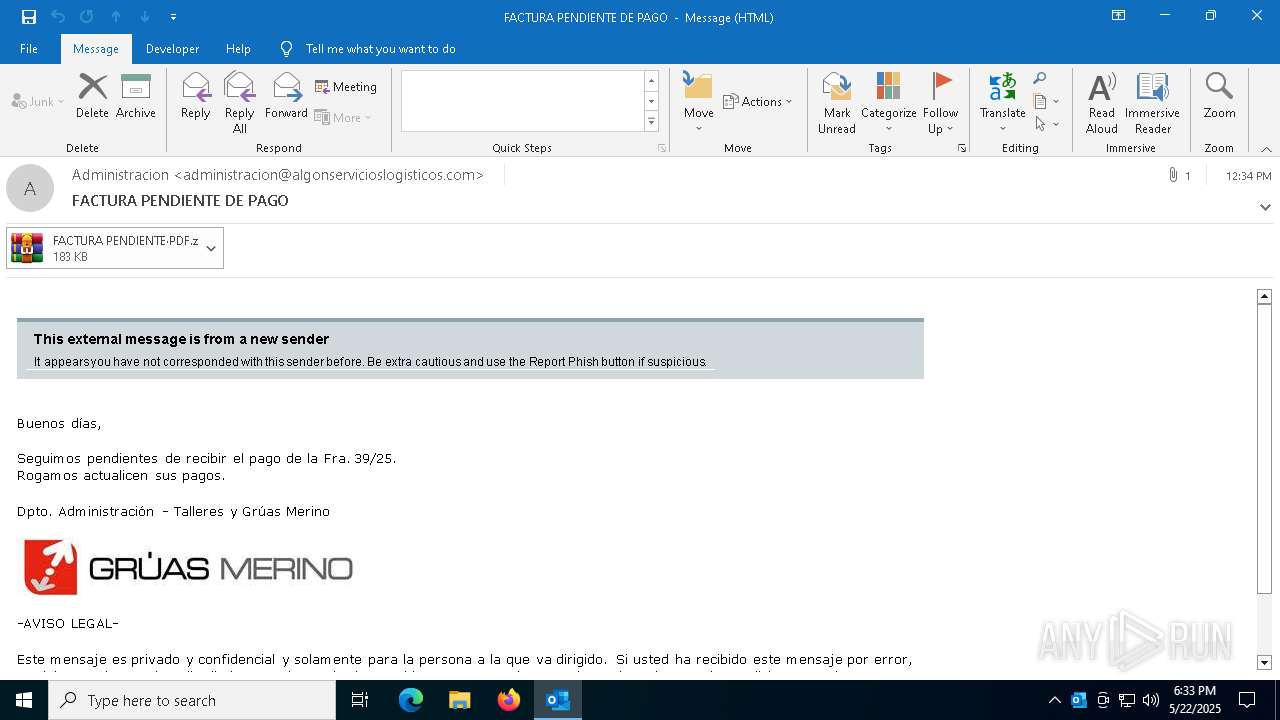
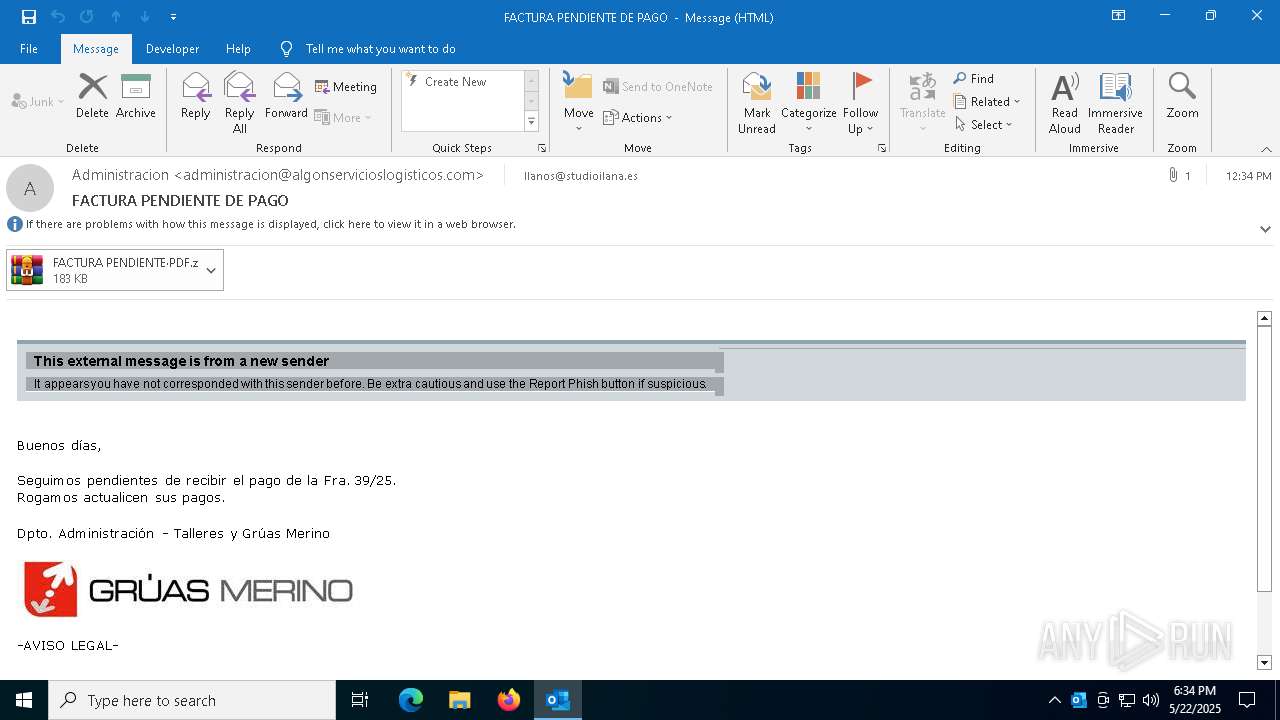
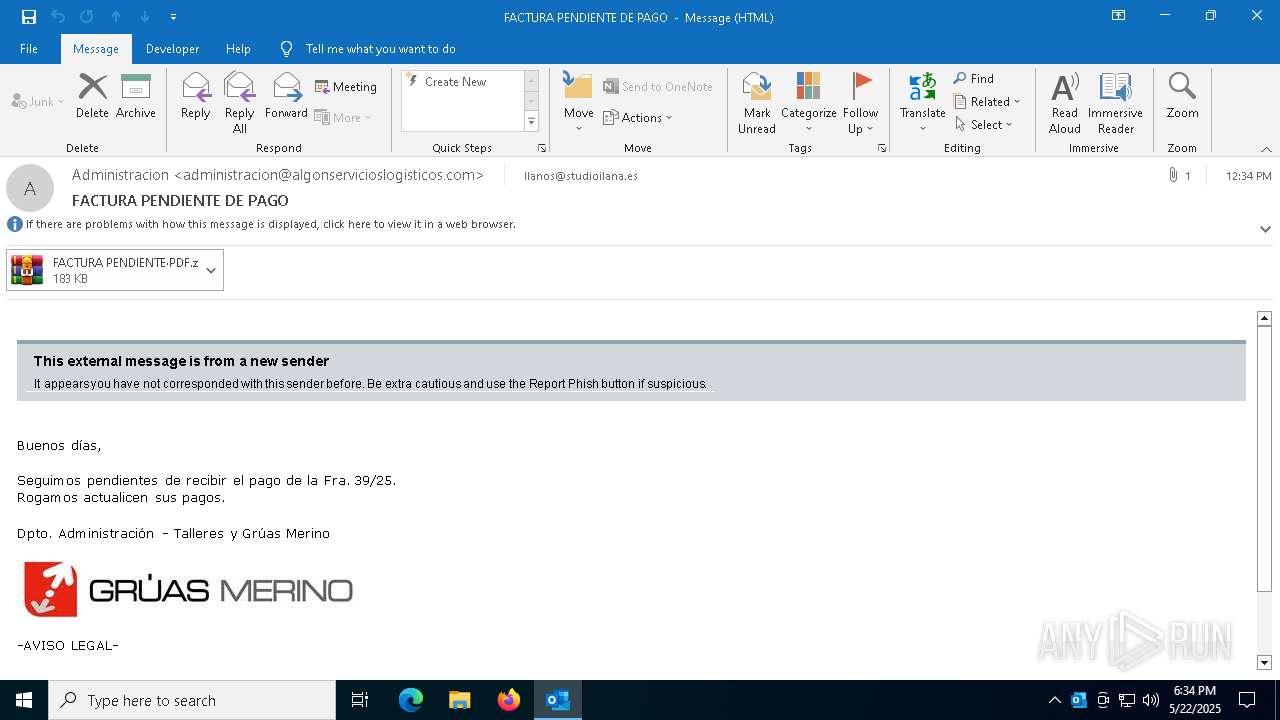
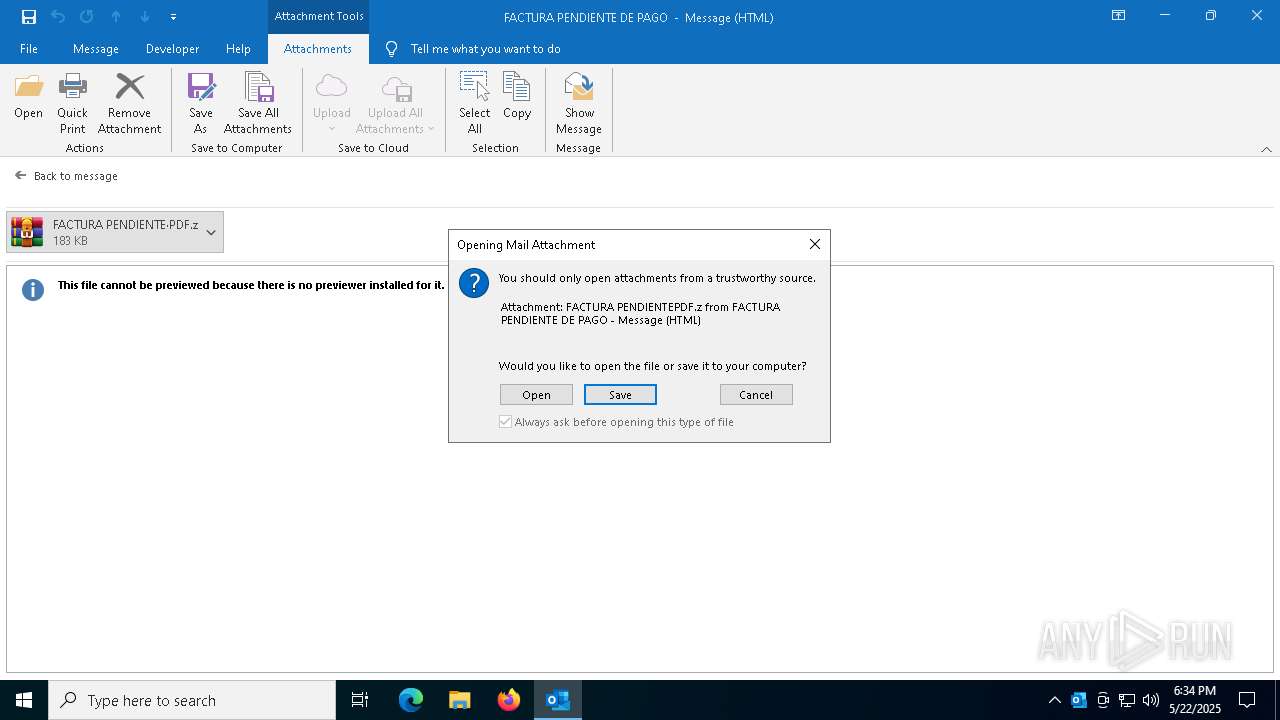
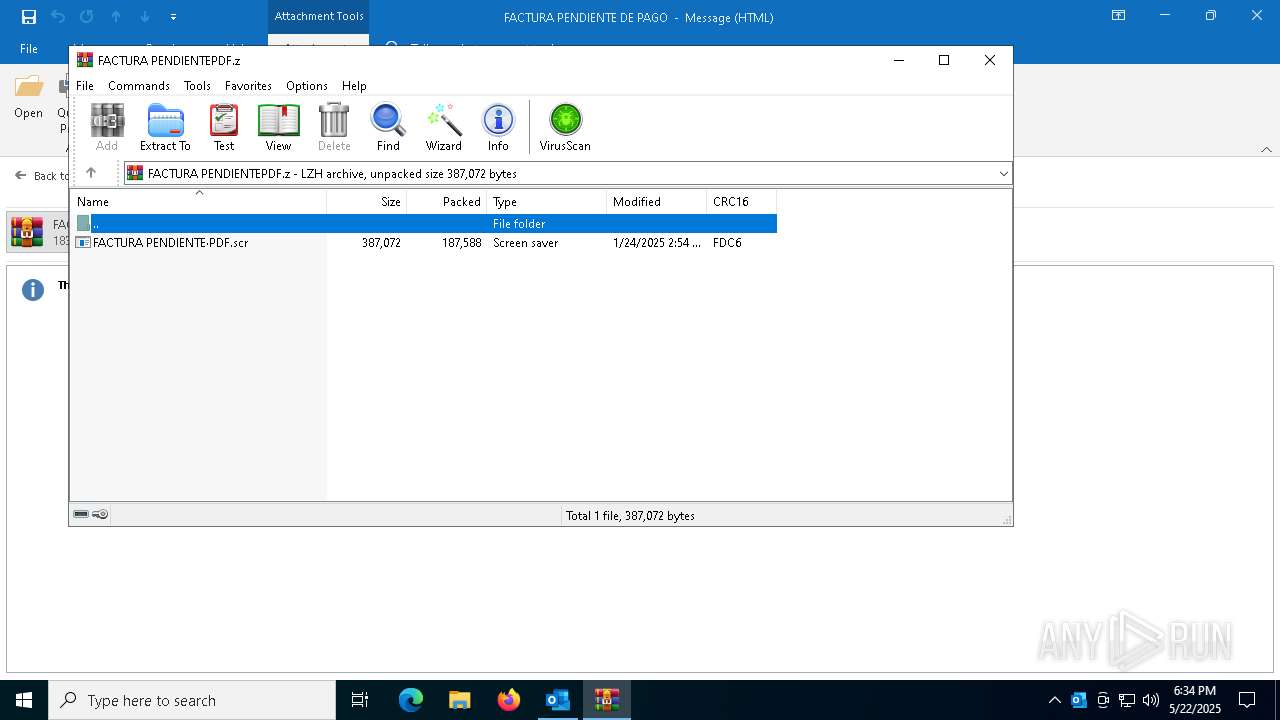
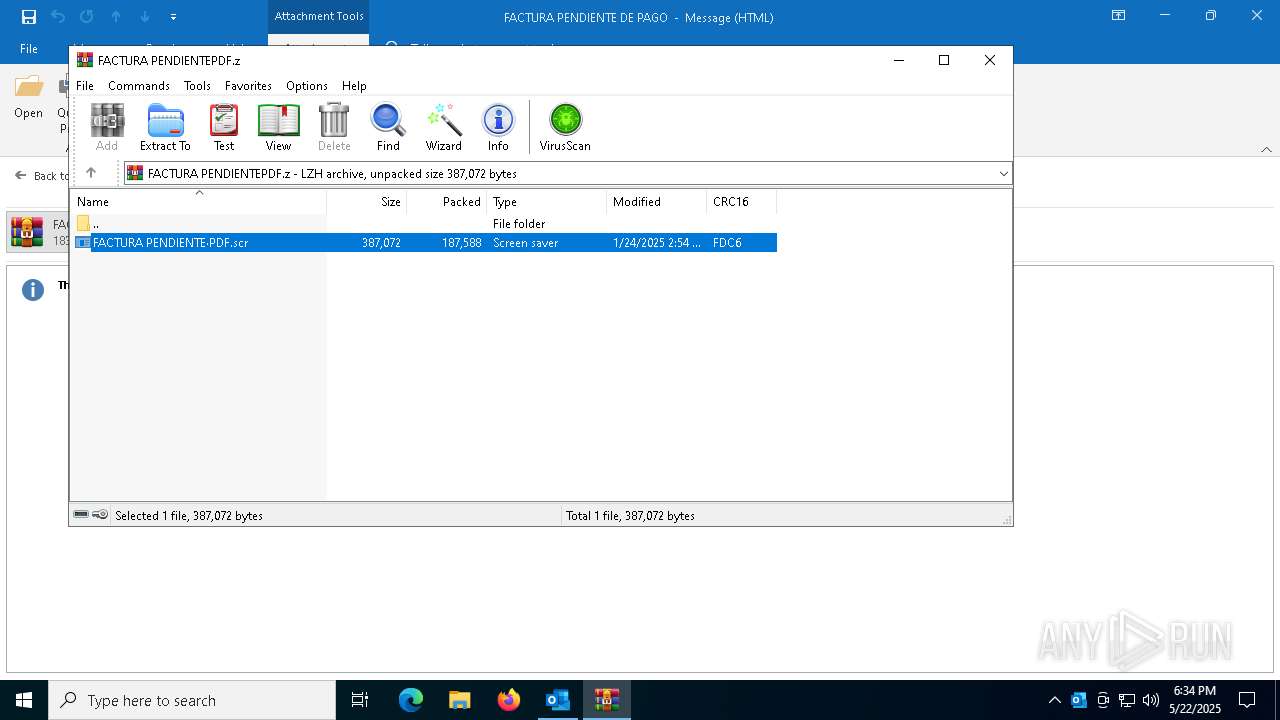
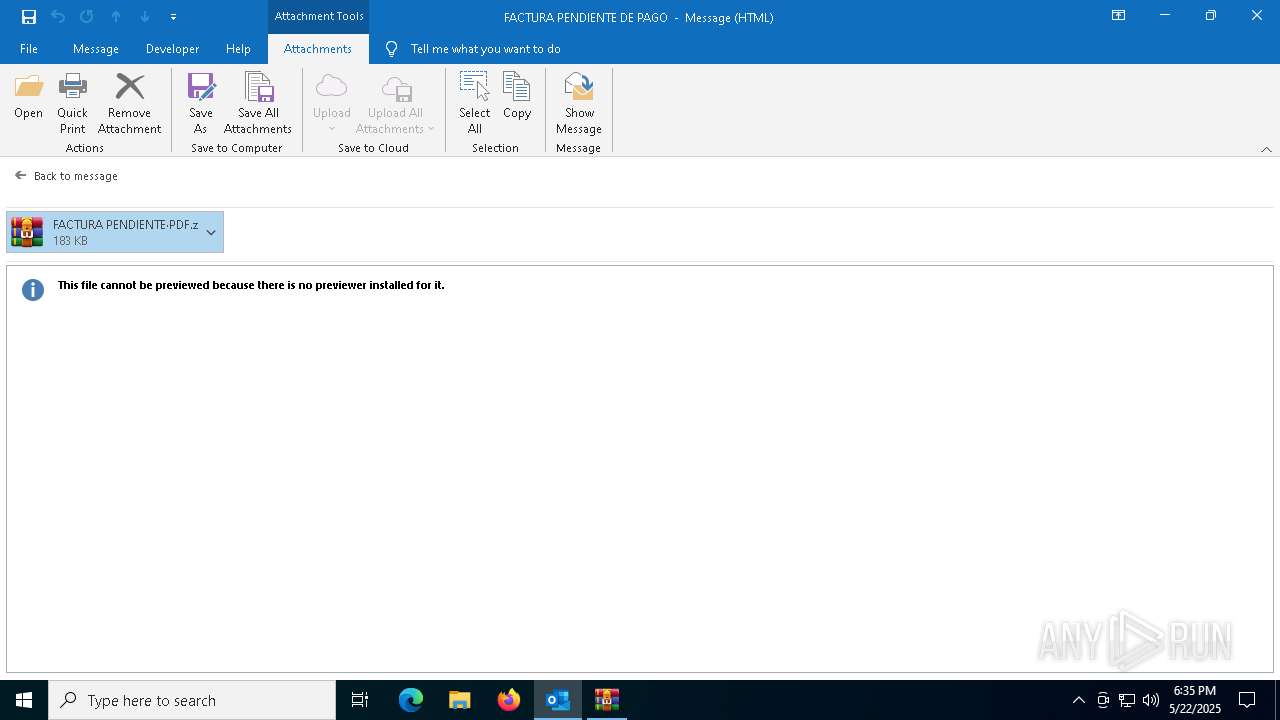
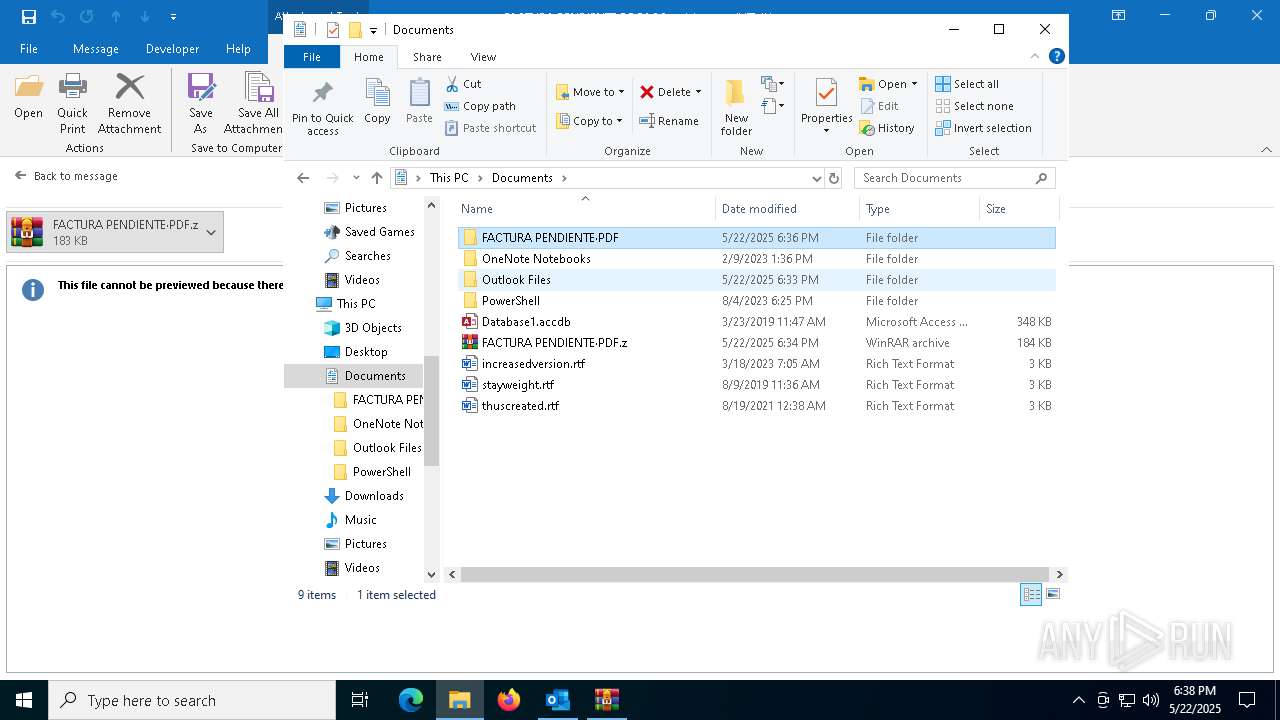
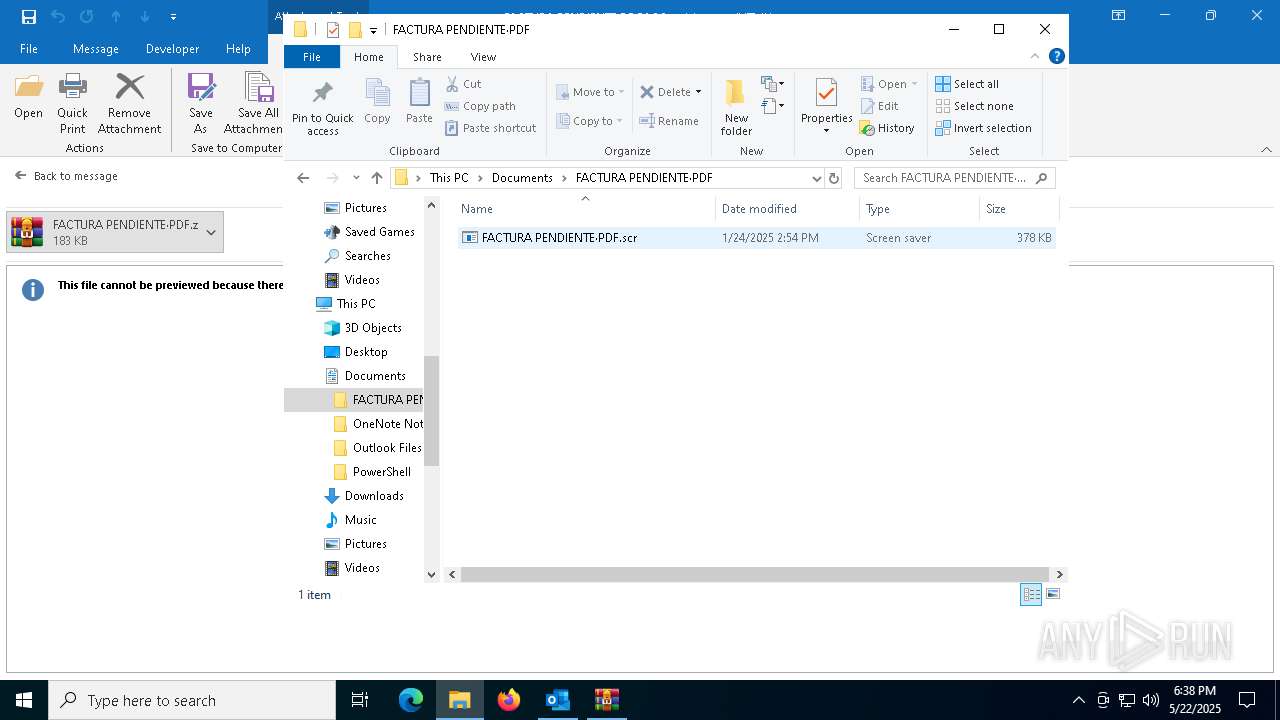
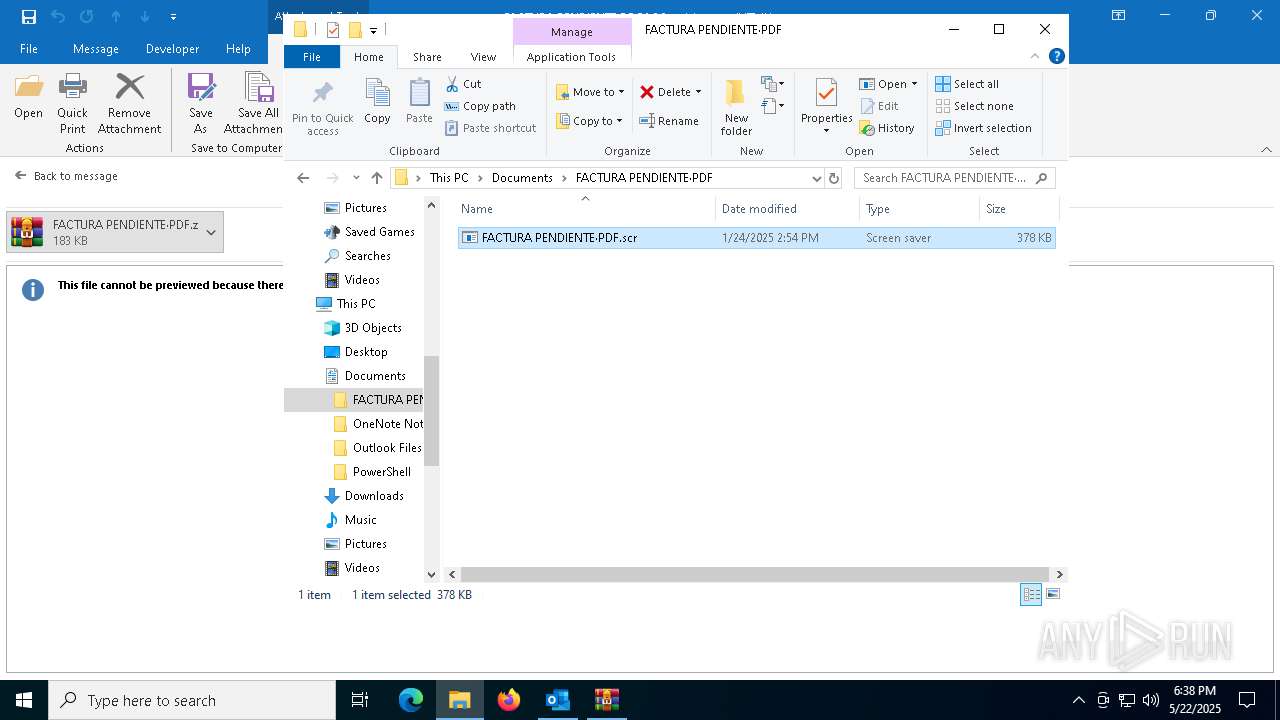
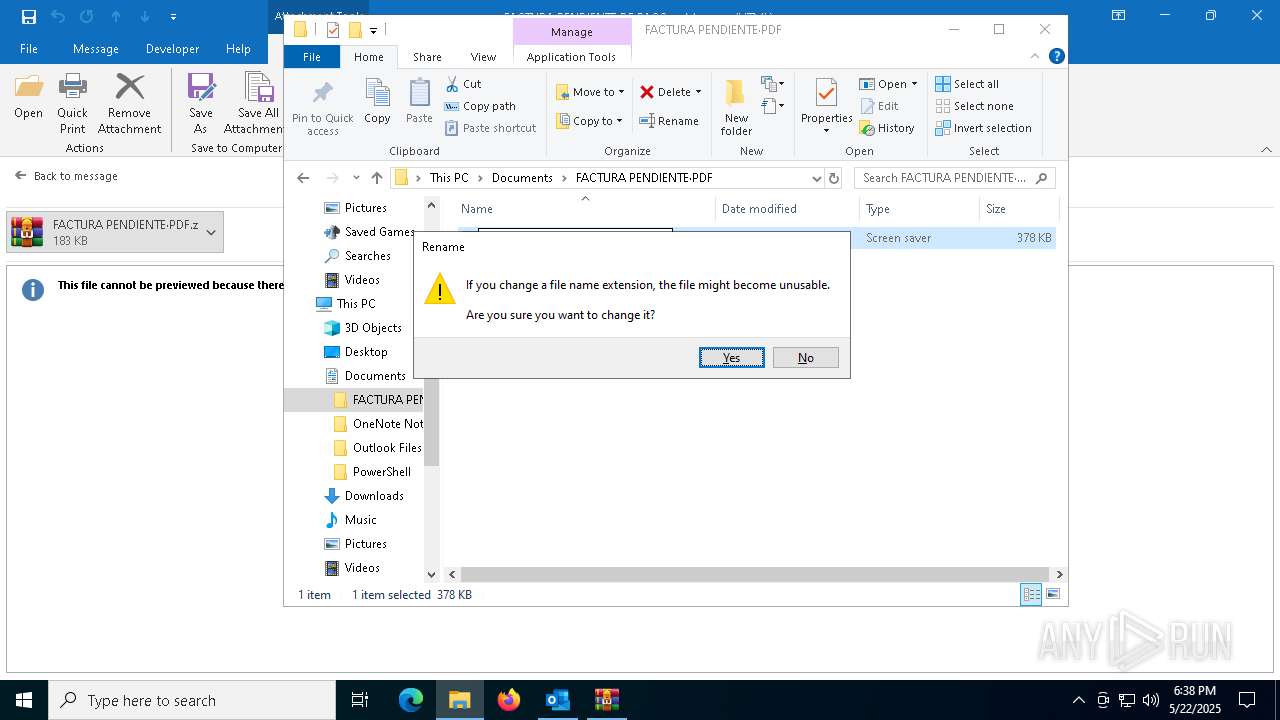
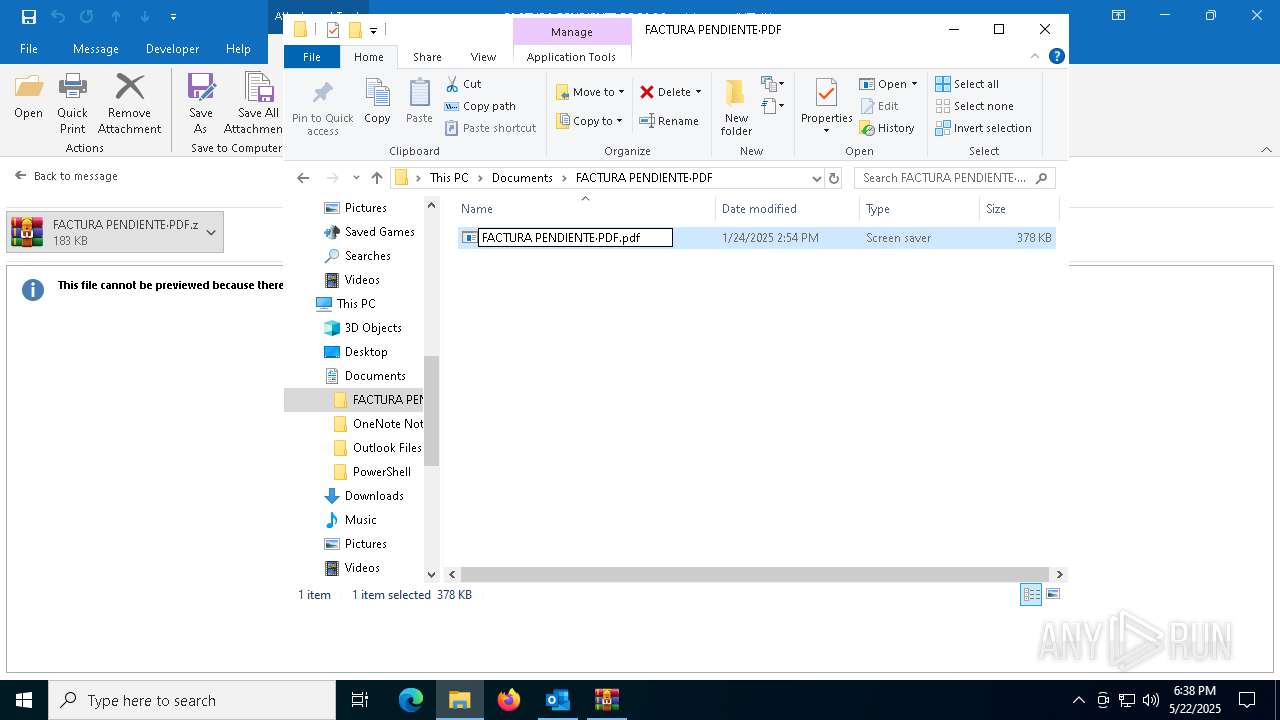
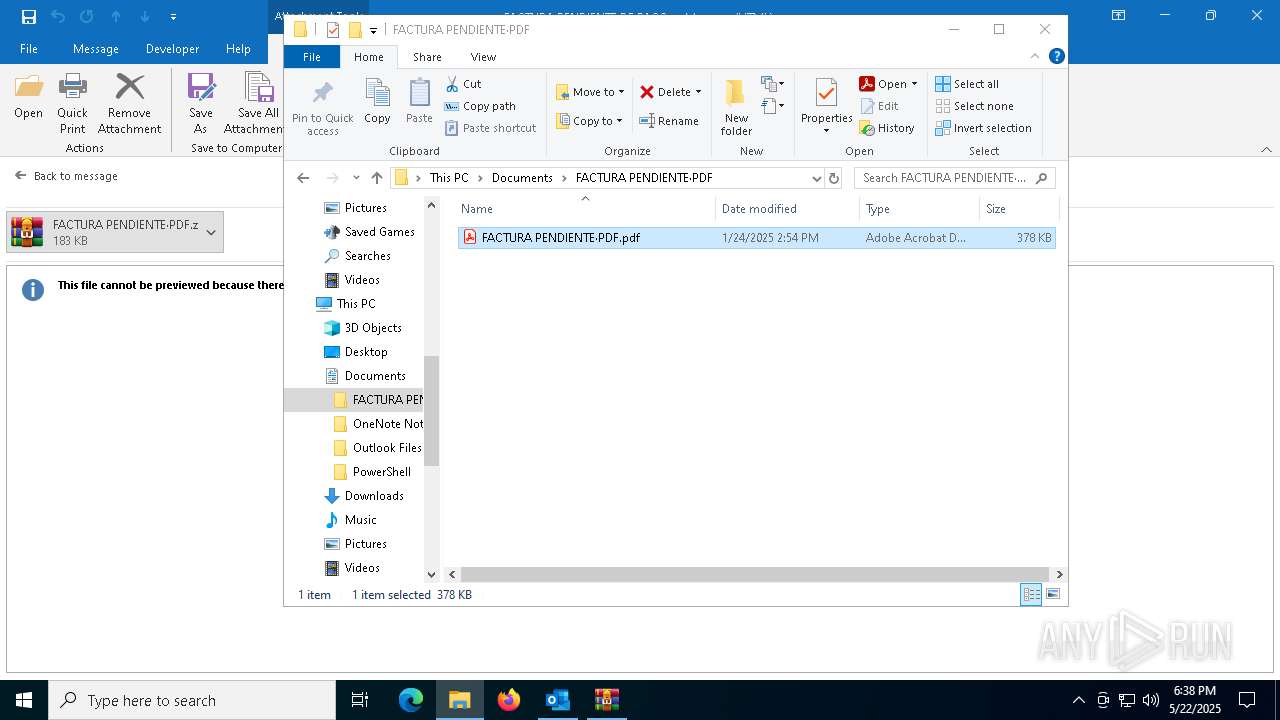
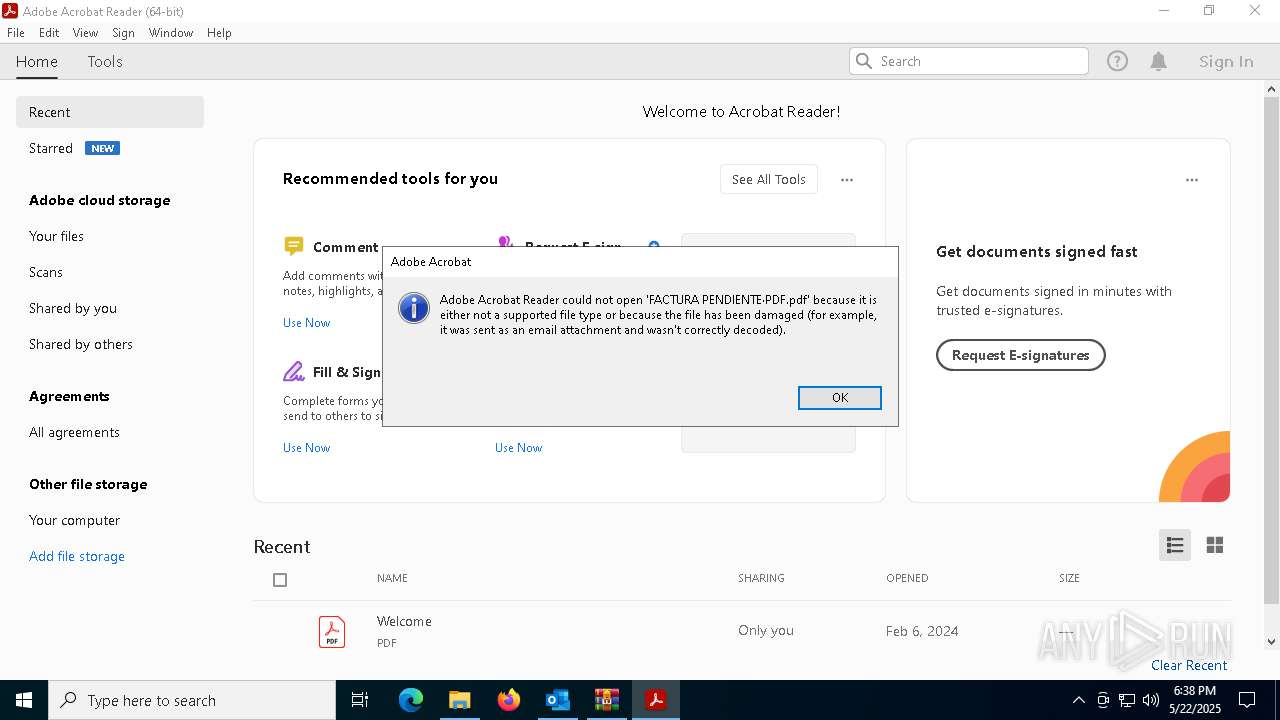
| File name: | 3z2HgNK-44755-07gA97811266A3A1F286bf40064.eml |
| Full analysis: | https://app.any.run/tasks/f9e78b28-eb47-4774-a9b9-ffebfcd3ddbc |
| Verdict: | Malicious activity |
| Threats: | A keylogger is a type of spyware that infects a system and has the ability to record every keystroke made on the device. This lets attackers collect personal information of victims, which may include their online banking credentials, as well as personal conversations. The most widespread vector of attack leading to a keylogger infection begins with a phishing email or link. Keylogging is also often present in remote access trojans as part of an extended set of malicious tools. |
| Analysis date: | May 22, 2025, 18:33:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 81099A3C96E37A883DC0F27A7A6CC4BB |
| SHA1: | CEC926608049C2BDA1C8343802E4718890B0179A |
| SHA256: | 7F30BFF735C51B29C5B0C3593099AF55BD50925542AE185685984FDA3C20C893 |
| SSDEEP: | 6144:ao6YOVClBBeXAuWENUIb5KwtmszOihiVMO/pNYqv4:B80BBeQzEH5KtqOf3/pS |
MALICIOUS
Actions looks like stealing of personal data
- RegAsm.exe (PID: 7304)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 7304)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegAsm.exe (PID: 7304)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 4284)
- RegAsm.exe (PID: 4056)
PURECRYPTER has been detected (YARA)
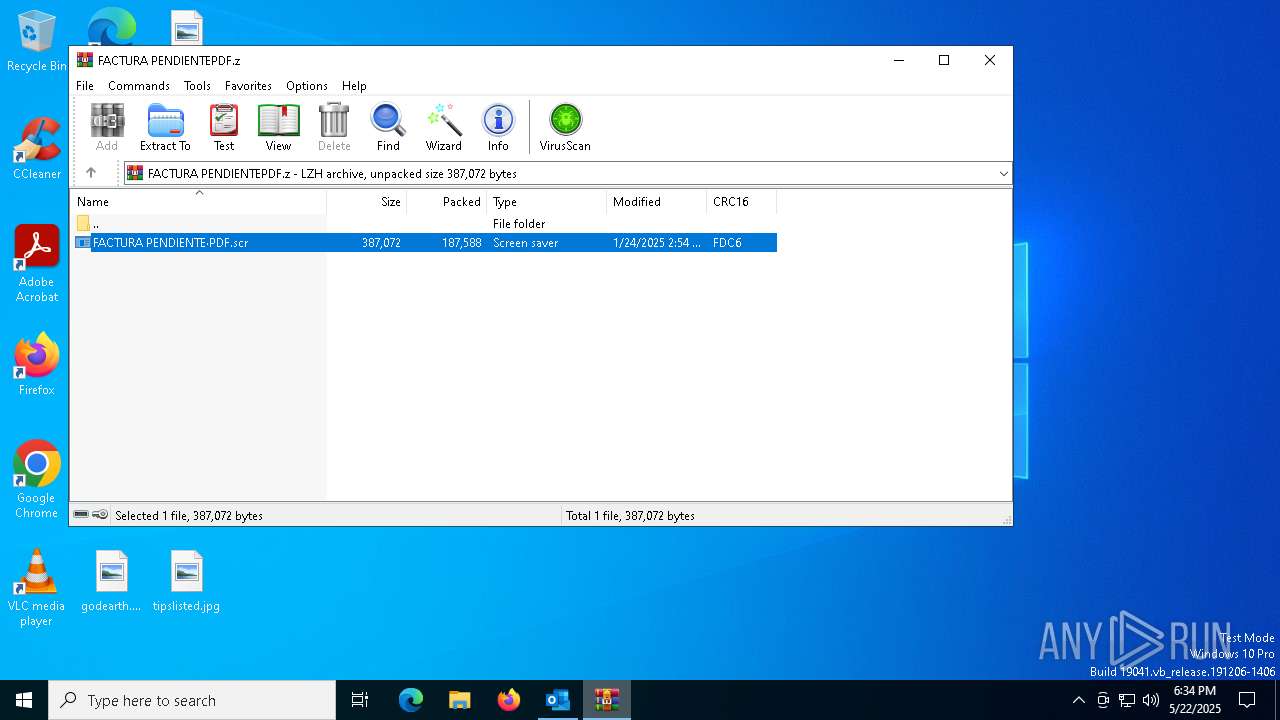
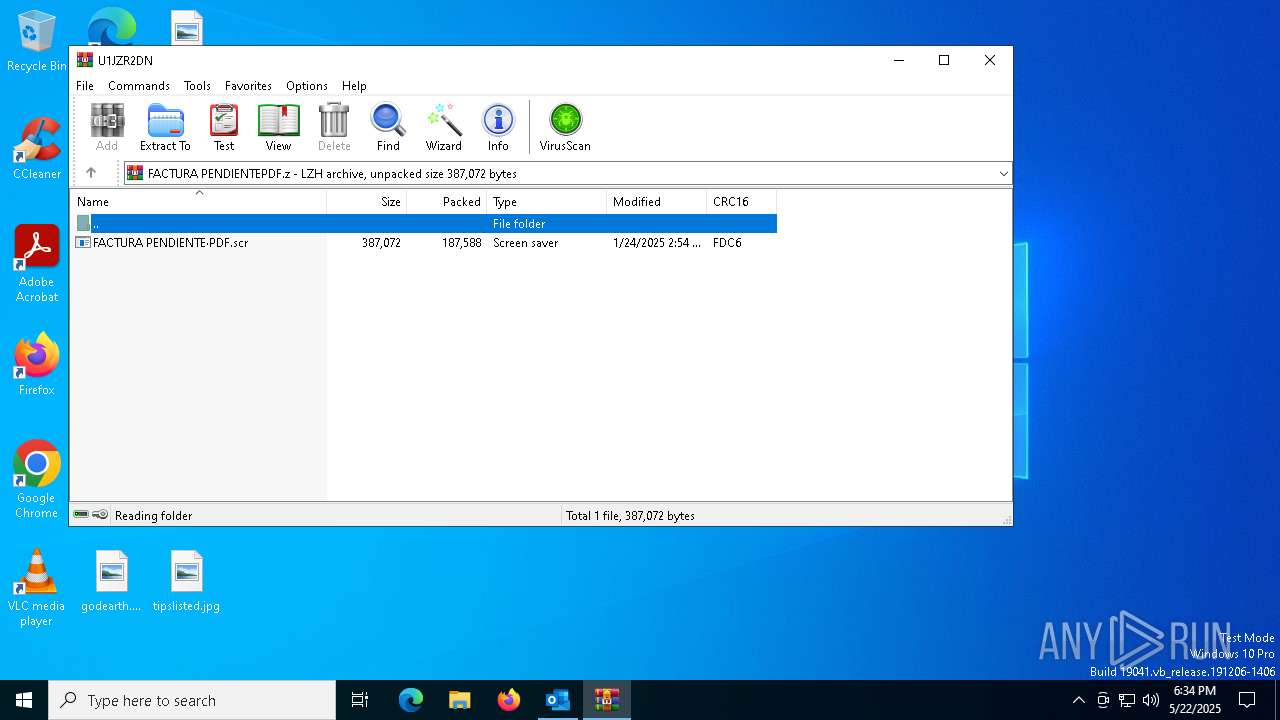
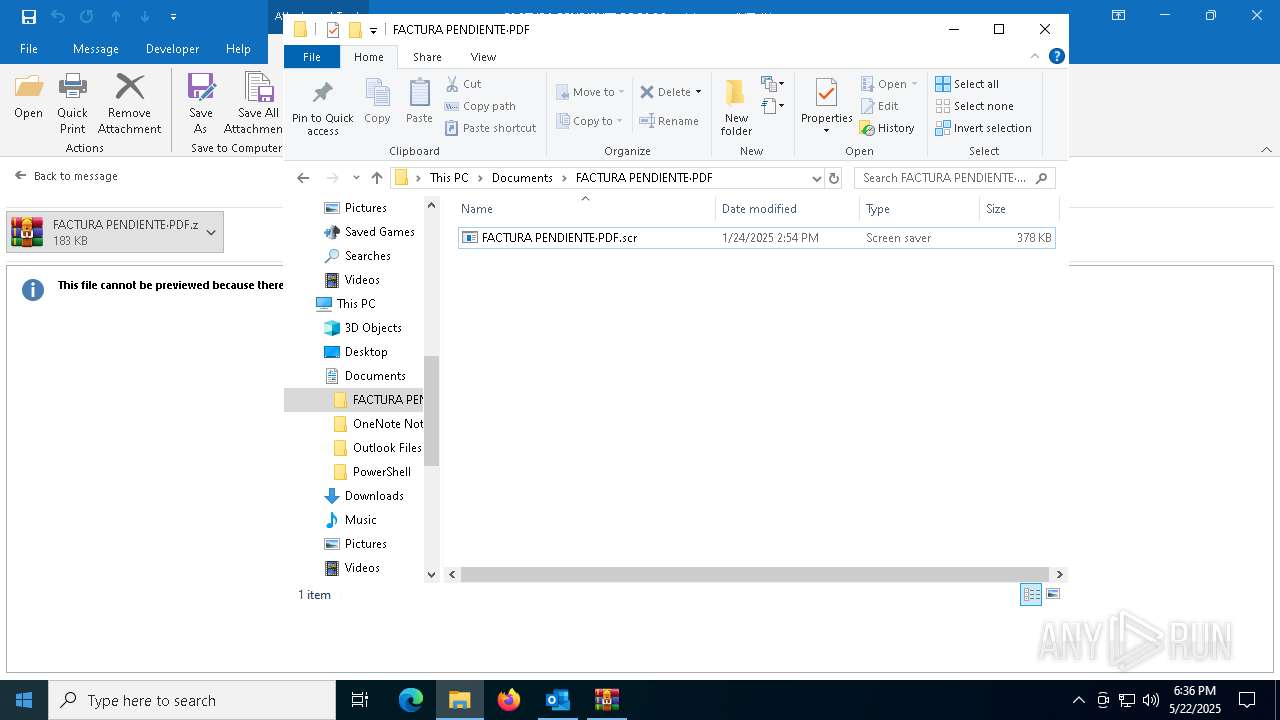
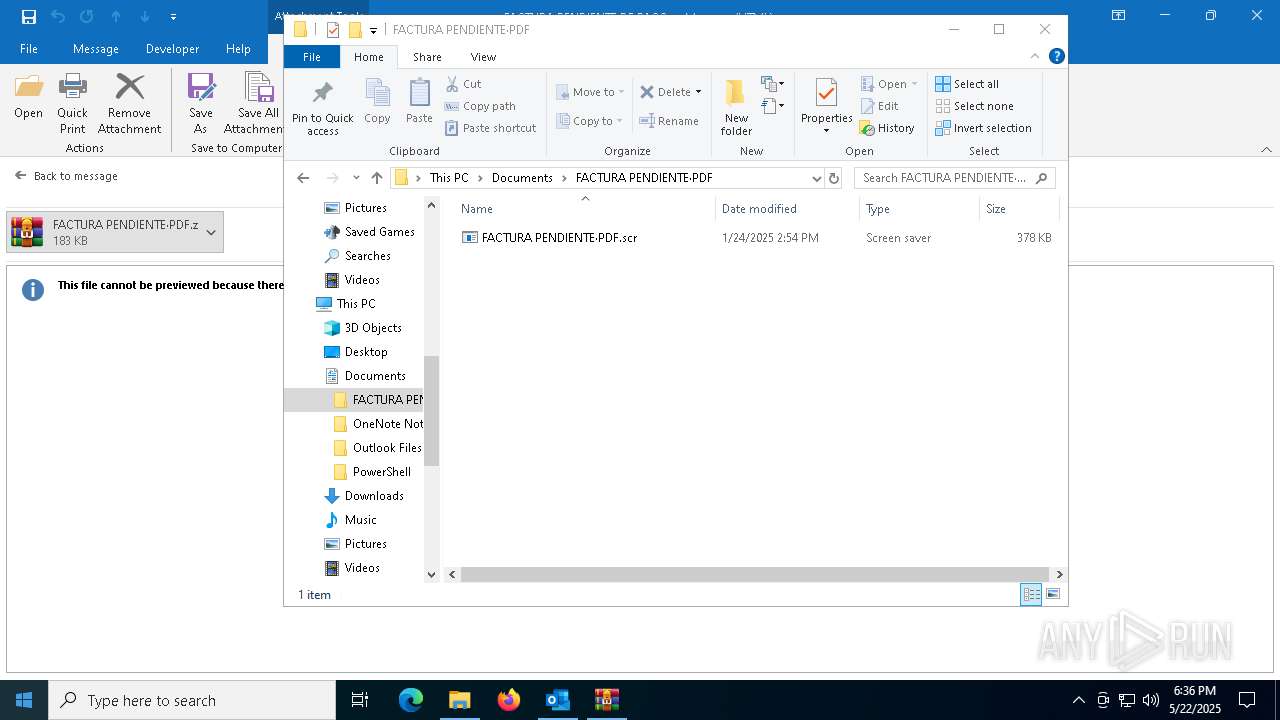
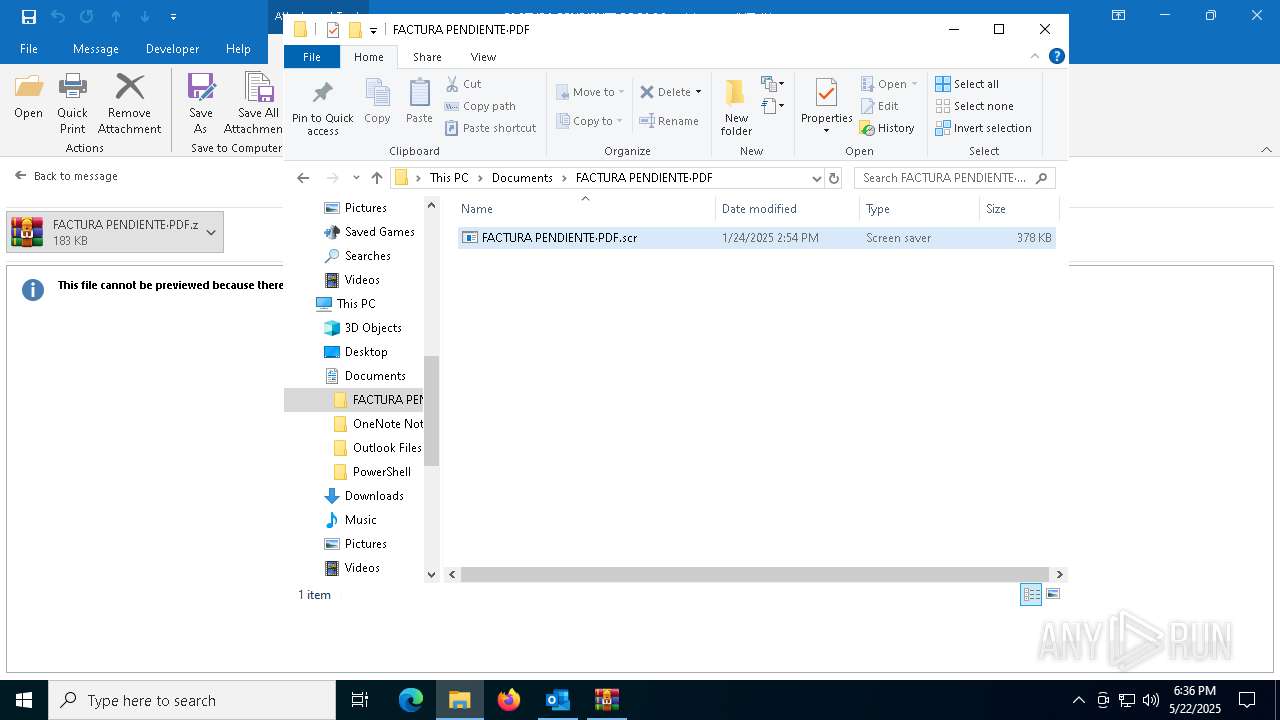
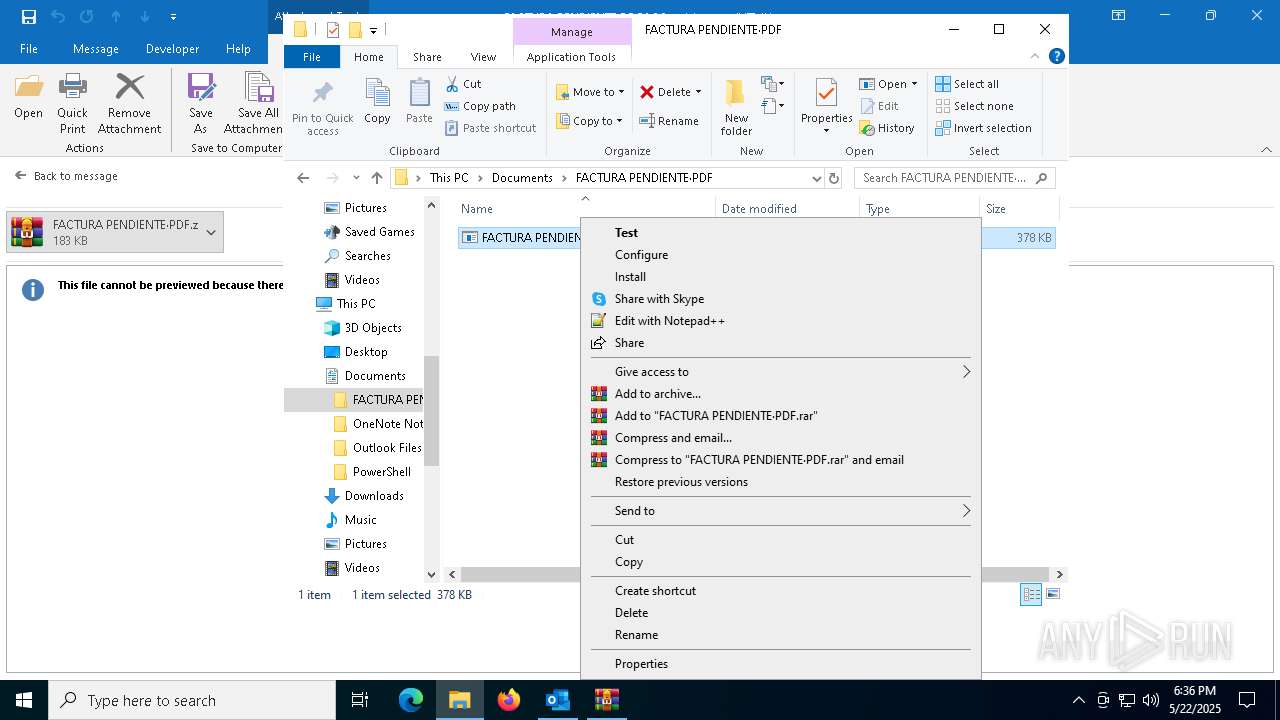
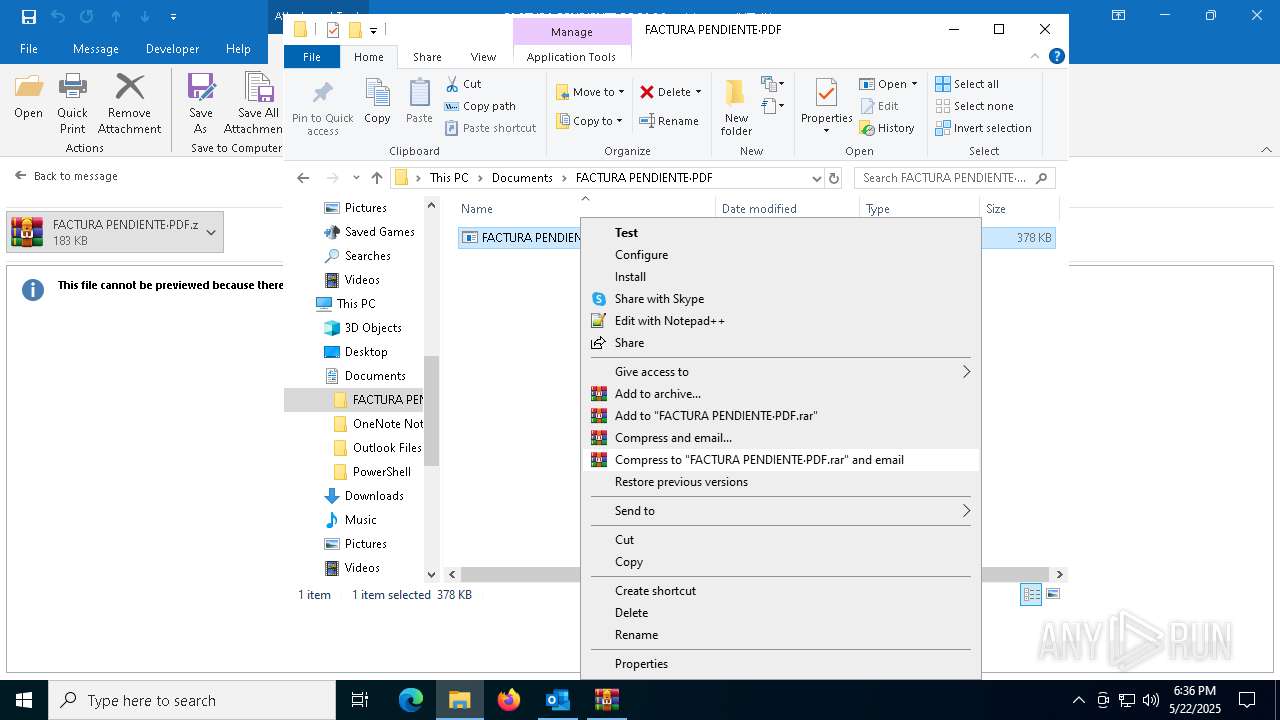
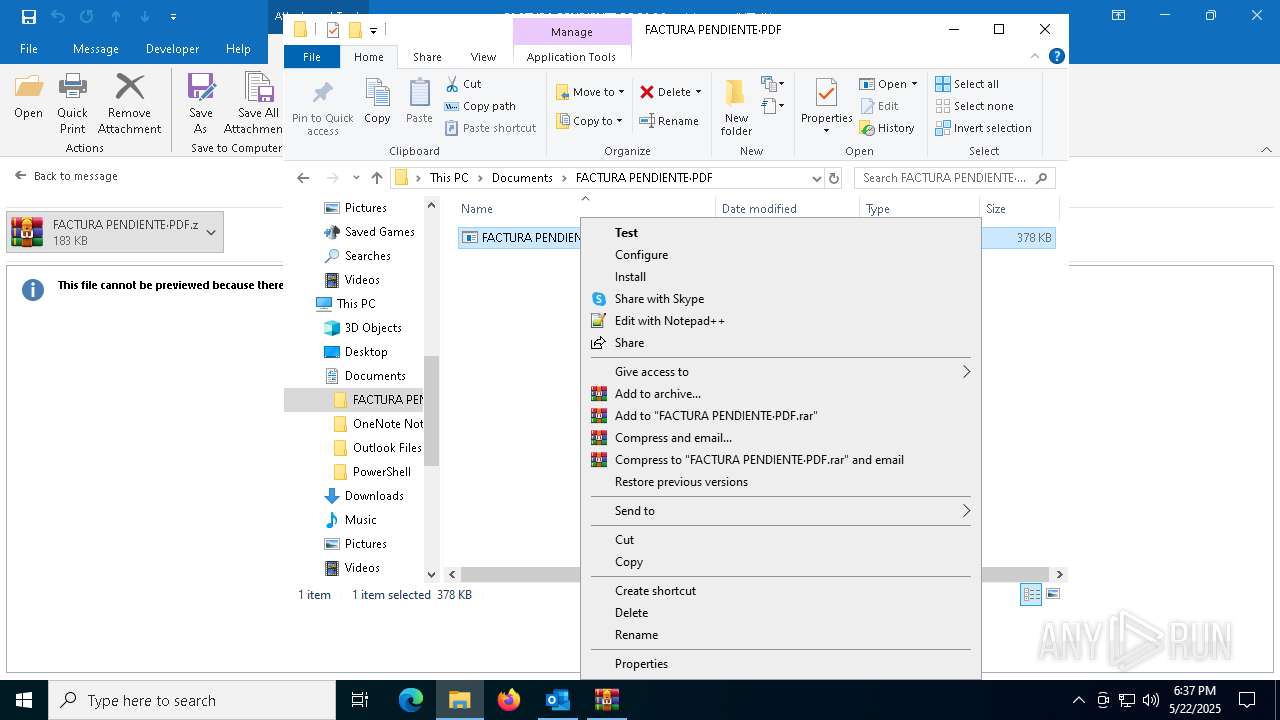
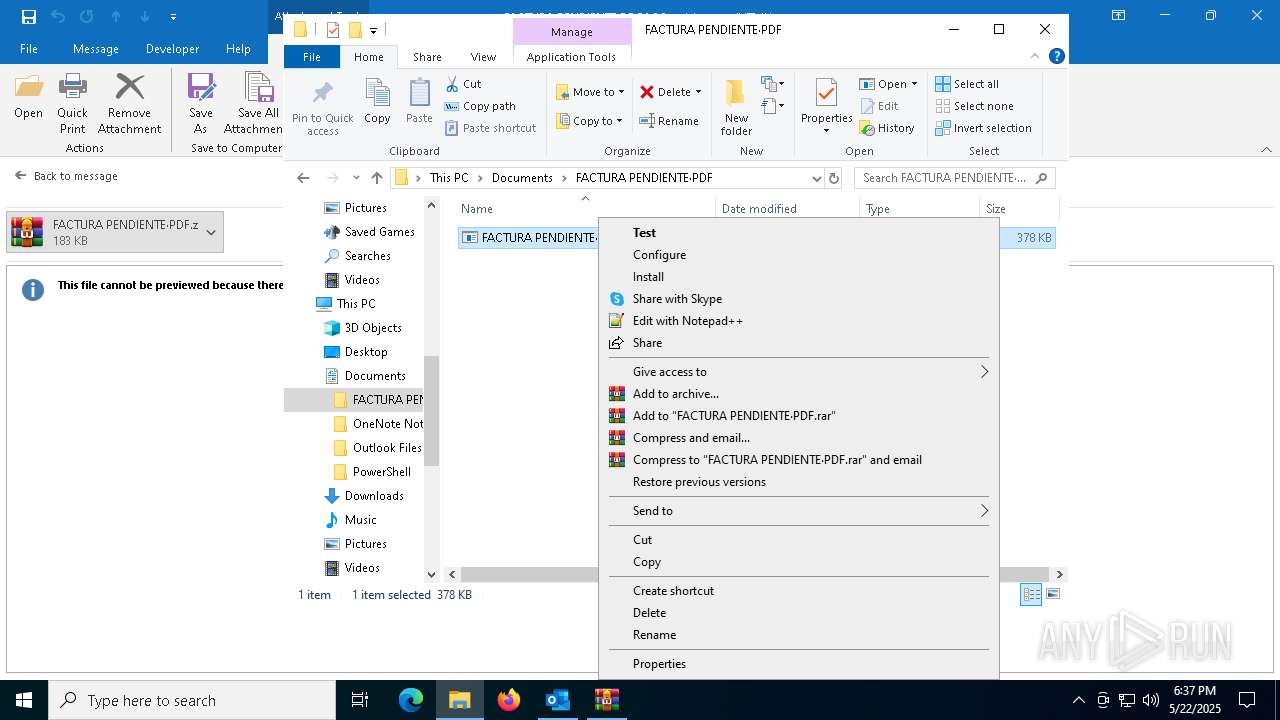
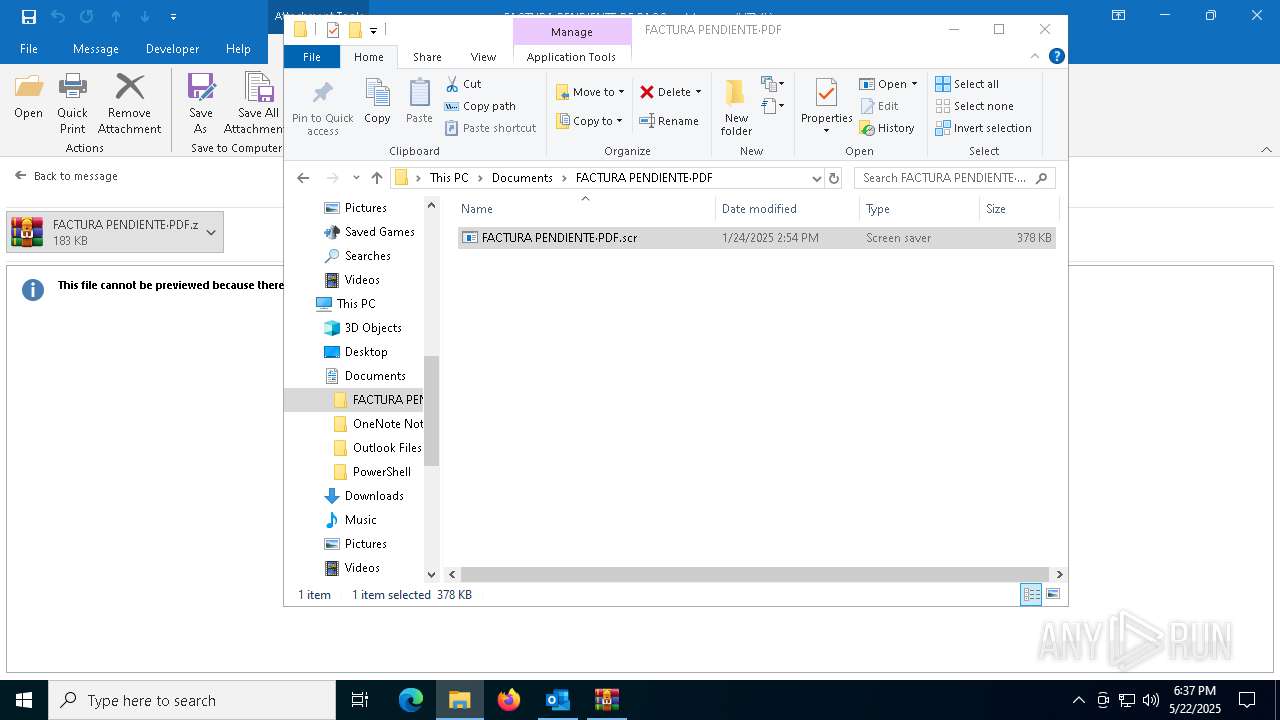
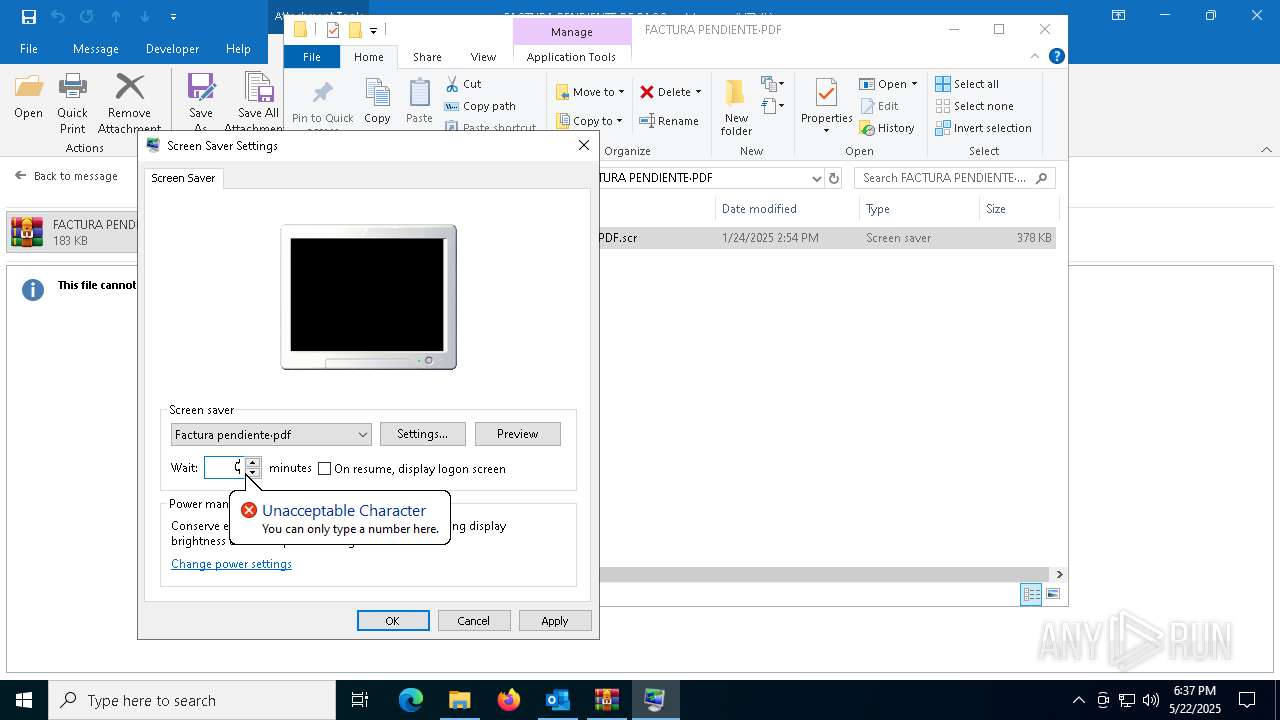
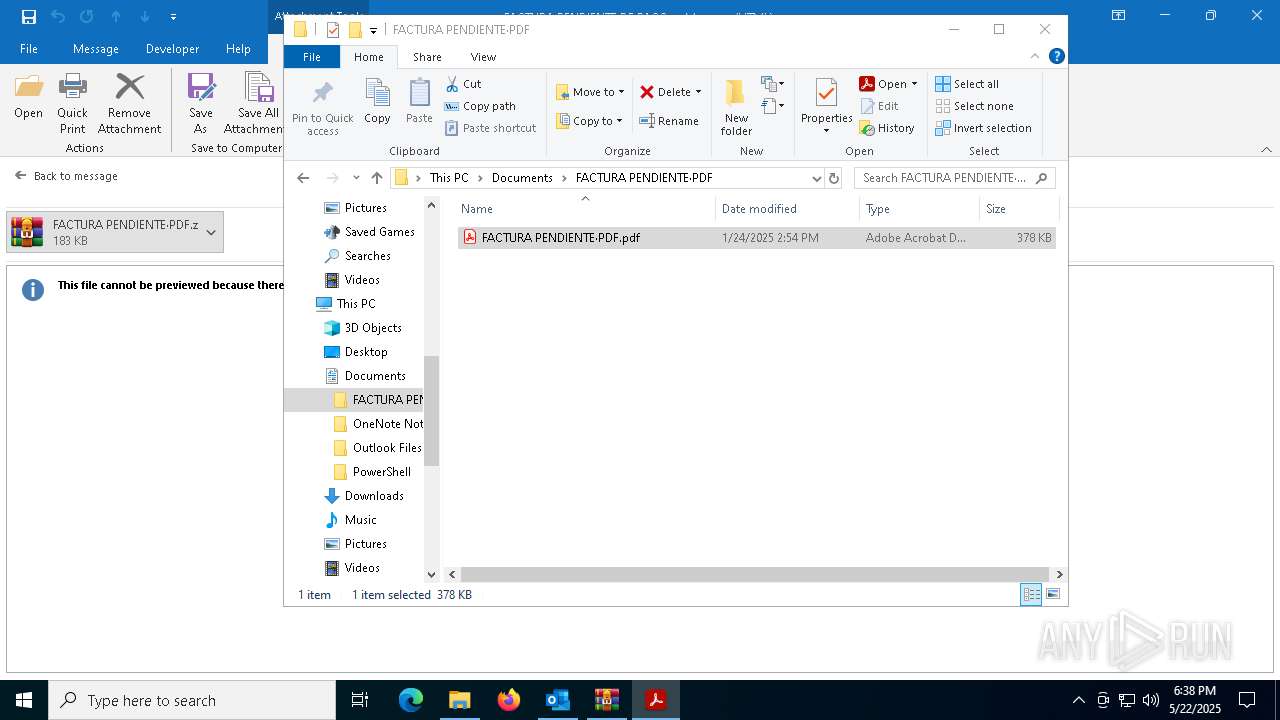
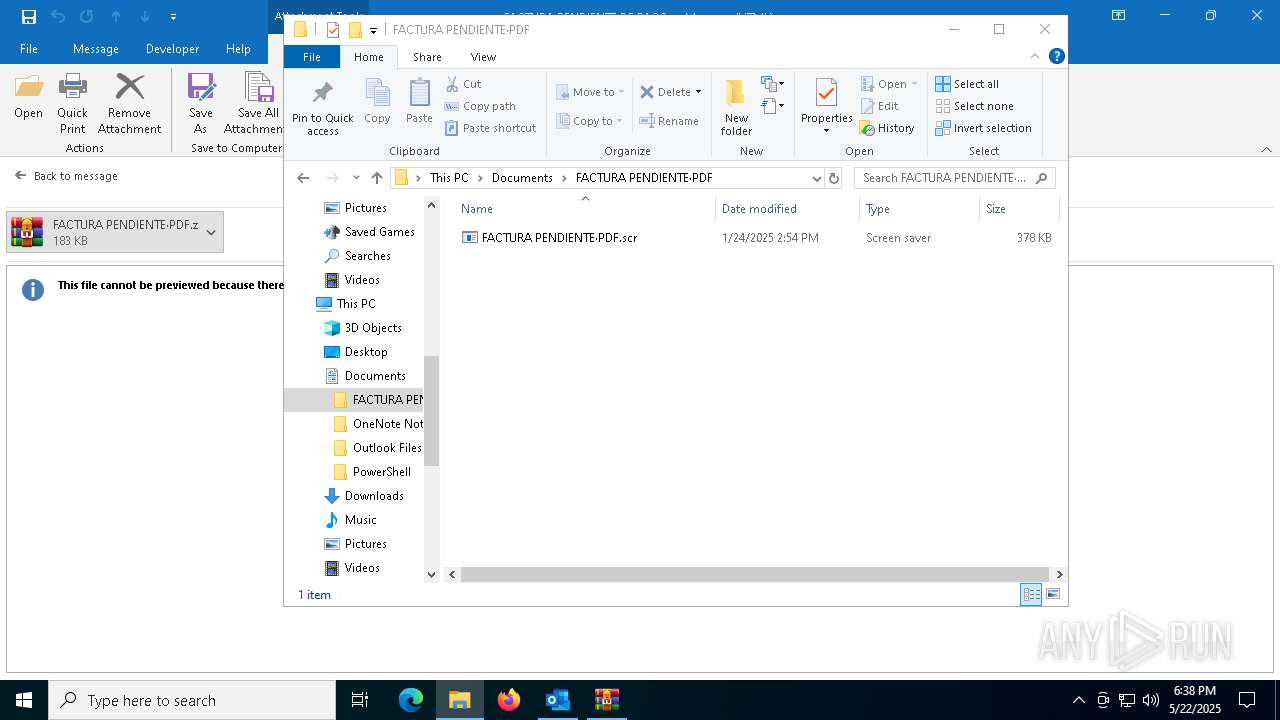
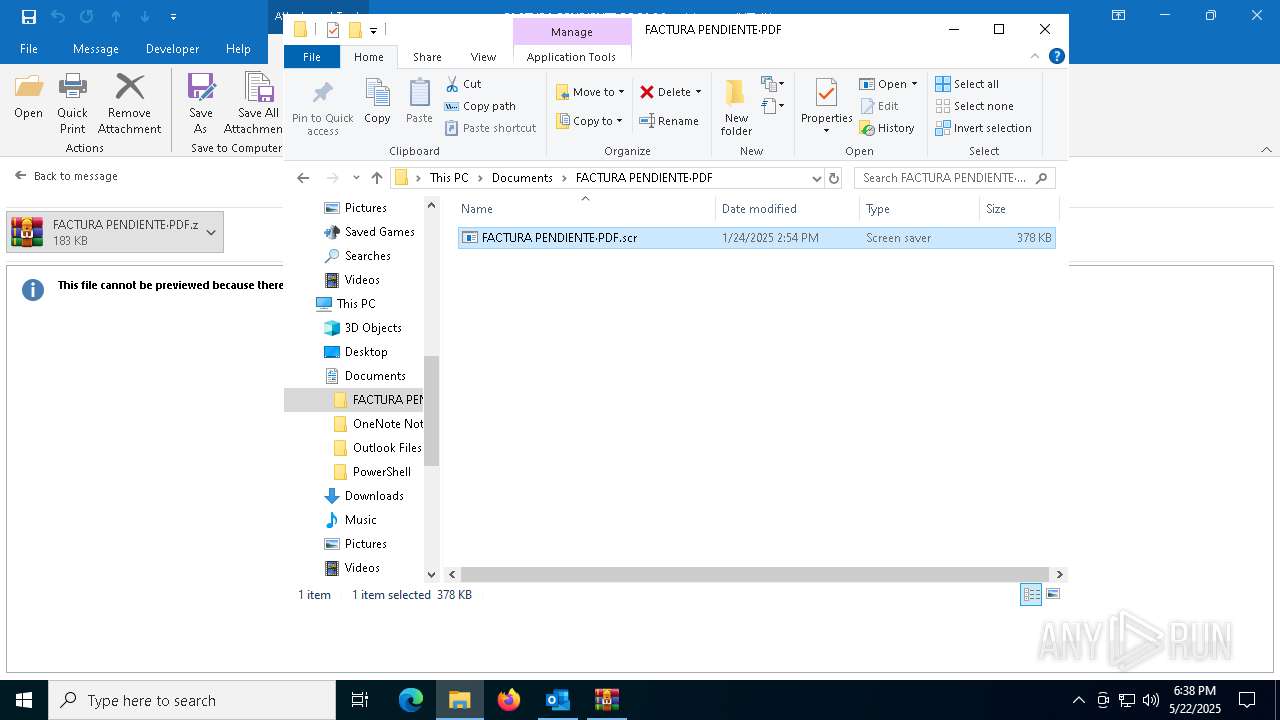
- FACTURA PENDIENTE·PDF.scr (PID: 680)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7212)
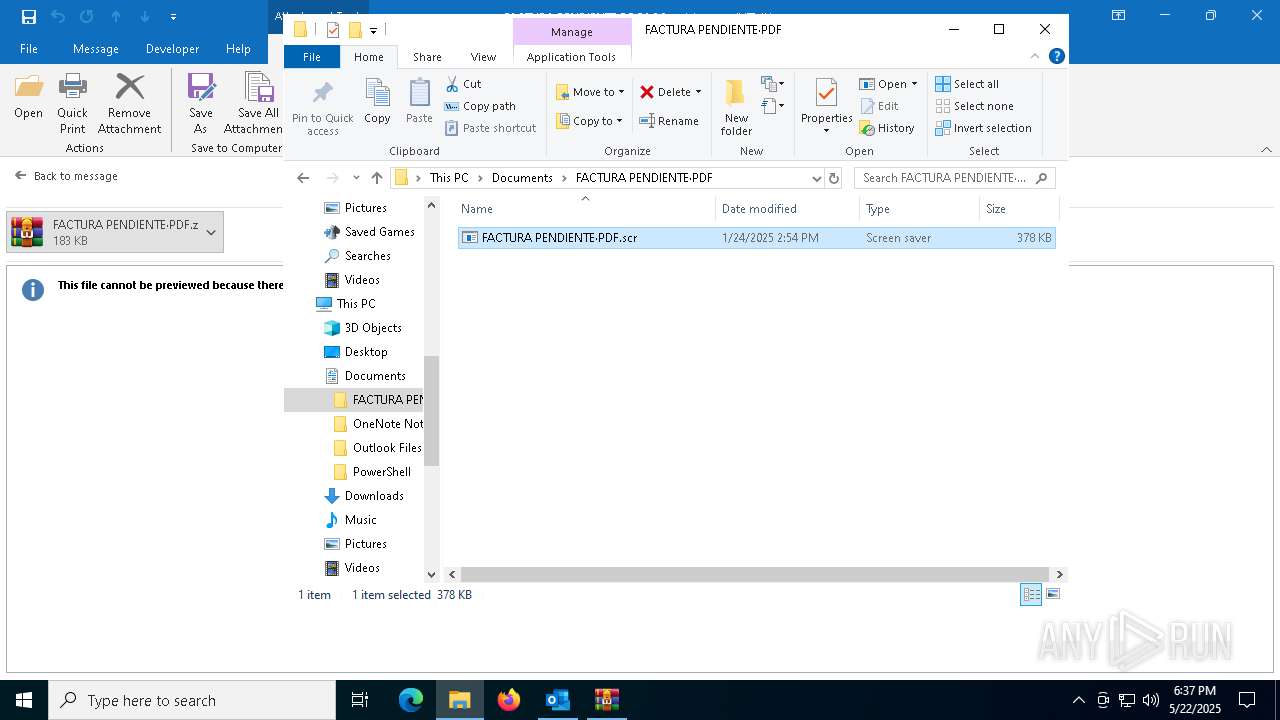
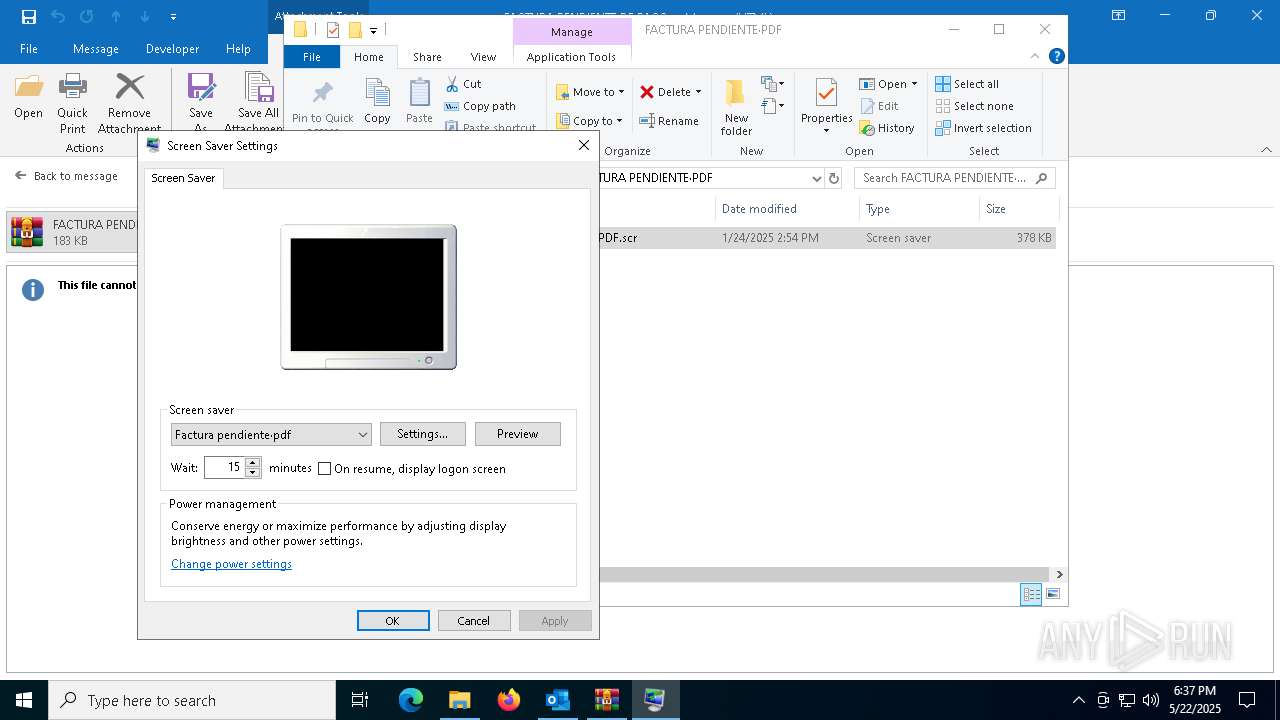
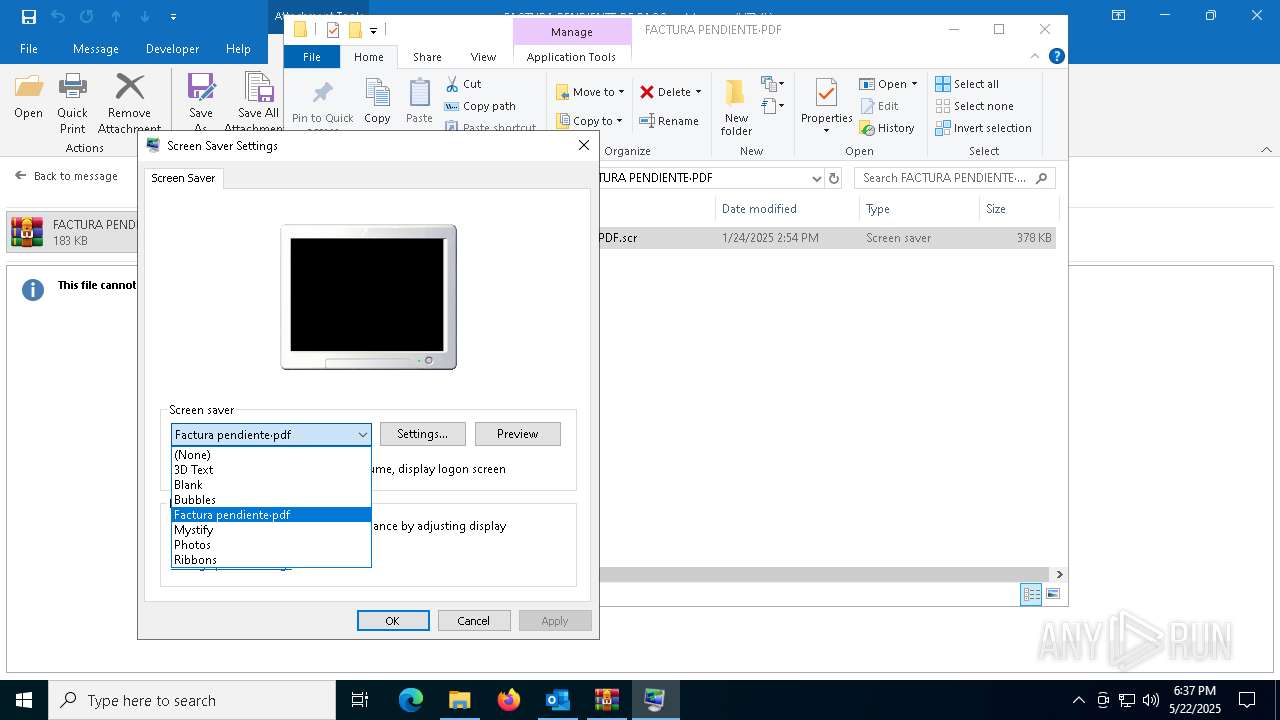
Starts application with an unusual extension
- WinRAR.exe (PID: 7212)
- rundll32.exe (PID: 5596)
Checks for external IP
- svchost.exe (PID: 2196)
- RegAsm.exe (PID: 7304)
- RegAsm.exe (PID: 8000)
- RegAsm.exe (PID: 4284)
- RegAsm.exe (PID: 4056)
The process verifies whether the antivirus software is installed
- RegAsm.exe (PID: 7304)
Connects to SMTP port
- RegAsm.exe (PID: 7304)
- RegAsm.exe (PID: 4284)
- RegAsm.exe (PID: 4056)
- RegAsm.exe (PID: 8000)
INFO
Checks supported languages
- FACTURA PENDIENTE·PDF.scr (PID: 6640)
- RegAsm.exe (PID: 7304)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7212)
- WinRAR.exe (PID: 7284)
Reads the computer name
- FACTURA PENDIENTE·PDF.scr (PID: 6640)
- RegAsm.exe (PID: 7304)
Reads the machine GUID from the registry
- FACTURA PENDIENTE·PDF.scr (PID: 6640)
- RegAsm.exe (PID: 7304)
Disables trace logs
- FACTURA PENDIENTE·PDF.scr (PID: 6640)
- RegAsm.exe (PID: 7304)
Reads the software policy settings
- FACTURA PENDIENTE·PDF.scr (PID: 6640)
- slui.exe (PID: 8020)
- RegAsm.exe (PID: 7304)
- slui.exe (PID: 7812)
Checks proxy server information
- FACTURA PENDIENTE·PDF.scr (PID: 6640)
- RegAsm.exe (PID: 7304)
- slui.exe (PID: 7812)
.NET Reactor protector has been detected
- FACTURA PENDIENTE·PDF.scr (PID: 6640)
- RegAsm.exe (PID: 7304)
- FACTURA PENDIENTE·PDF.scr (PID: 516)
- FACTURA PENDIENTE·PDF.scr (PID: 680)
- RegAsm.exe (PID: 8000)
Manual execution by a user
- rundll32.exe (PID: 5596)
- WinRAR.exe (PID: 7284)
- FACTURA PENDIENTE·PDF.scr (PID: 2616)
- FACTURA PENDIENTE·PDF.scr (PID: 516)
- Acrobat.exe (PID: 5796)
- FACTURA PENDIENTE·PDF.scr (PID: 7964)
Attempting to use file storage service
- FACTURA PENDIENTE·PDF.scr (PID: 2616)
Application launched itself
- Acrobat.exe (PID: 5796)
- AcroCEF.exe (PID: 7928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 3) (100) |
|---|
Total processes
164
Monitored processes
27
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Users\admin\Documents\FACTURA PENDIENTE·PDF\FACTURA PENDIENTE·PDF.scr" /S | C:\Users\admin\Documents\FACTURA PENDIENTE·PDF\FACTURA PENDIENTE·PDF.scr | explorer.exe | ||||||||||||
User: admin Company: 北京九城口岸软件科技有限公司 Integrity Level: MEDIUM Description: 检验检疫电子申报企业端软件 Exit code: 4294967295 Version: 0.0.0.0 Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Documents\FACTURA PENDIENTE·PDF\FACTURA PENDIENTE·PDF.scr" /p 132276 | C:\Users\admin\Documents\FACTURA PENDIENTE·PDF\FACTURA PENDIENTE·PDF.scr | rundll32.exe | ||||||||||||
User: admin Company: 北京九城口岸软件科技有限公司 Integrity Level: MEDIUM Description: 检验检疫电子申报企业端软件 Exit code: 4294967295 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1516 --field-trial-handle=1592,i,652481236269785152,16928186652171026874,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | "C:\Users\admin\Documents\FACTURA PENDIENTE·PDF\FACTURA PENDIENTE·PDF.scr" /S | C:\Users\admin\Documents\FACTURA PENDIENTE·PDF\FACTURA PENDIENTE·PDF.scr | explorer.exe | ||||||||||||
User: admin Company: 北京九城口岸软件科技有限公司 Integrity Level: MEDIUM Description: 检验检疫电子申报企业端软件 Exit code: 4294967295 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3976 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Documents\FACTURA PENDIENTE·PDF\FACTURA PENDIENTE·PDF.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4056 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | FACTURA PENDIENTE·PDF.scr | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4284 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | FACTURA PENDIENTE·PDF.scr | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4920 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5596 | "rundll32.exe" desk.cpl,InstallScreenSaver C:\Users\admin\Documents\FACTURA PENDIENTE·PDF\FACTURA PENDIENTE·PDF.scr | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 300
Read events
33 826
Write events
1 309
Delete events
165
Modification events
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7500 |
| Operation: | write | Name: | 0 |
Value: 0B0E103A447540BD1527408ADF5564B365BCBF23004682DCDFE080E9F2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511CC3AD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (7500) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
2
Suspicious files
17
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7500 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:BC126563D64567484366E720F88DF839 | SHA256:1E57A498FB106656C7F5DA61E966437CCEA6C5B4EC6E513D6BA23D99DB28369A | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:58E61D7A97171A87AD6646CA33F6EE72 | SHA256:3F04B271E7C21354C0D0720FBC2C9067C9C48A9AF2D5BBFD7762D4887B5E4AA4 | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:EFE306A476DA27BCD3B203A60CEBB4E0 | SHA256:BC246245AF79B1D8FC564F31515705793905F9AD5EE99968AF6961A9344506F2 | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:A78C6349A487A6ECCA85EEE161ED4798 | SHA256:395694FE177D519867D4B9ABF867D1468E829B6571554CAFFC89317BC308AACA | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:C0FB66AE92A9C4706198A8508424081A | SHA256:5DD1CBAFA464D8796AA79379E9FEB2F26307FD1A1C38DACD8F780134C4E87988 | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_95958EA845CB6540BF0668BB3287BBCD.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkC054.tmp | binary | |
MD5:12D9549789D795B39464D4726609E404 | SHA256:37AFFBFC012933FB234DC92EE94E88727CEC25293AF5A3EA83ACBB58A42A14DB | |||
| 7500 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:297092526417BD04079B662BC6B04529 | SHA256:CCF5C2A08FCBAD208E4D0021A24E8001D35D3CE621161A0DF71B8DC386CCA564 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
66
DNS requests
35
Threats
39
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8000 | RegAsm.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
8000 | RegAsm.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
8000 | RegAsm.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
7492 | FACTURA PENDIENTE·PDF.scr | GET | 301 | 193.30.119.105:80 | http://3005.filemail.com/api/file/get?filekey=OBaiNgTqiYbcMFZyJxuZTMPAglfd4WEg0LQTO8DIJT3v-NVm88Jwe7gfnds&pk_vid=83aa736e71db521d1747893203c1eb95 | unknown | — | — | malicious |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7500 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
680 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
680 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.158:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7500 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6640 | FACTURA PENDIENTE·PDF.scr | Not Suspicious Traffic | INFO [ANY.RUN] Observed File Sharing Service Download Domain (filemail.com) |
6640 | FACTURA PENDIENTE·PDF.scr | Not Suspicious Traffic | INFO [ANY.RUN] Downloading from a file sharing service is observed |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET DYN_DNS External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
7304 | RegAsm.exe | Misc activity | ET INFO External IP Lookup Service Domain (reallyfreegeoip .org) in TLS SNI |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Address Lookup Domain (reallyfreegeoip .org) |
7304 | RegAsm.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
2196 | svchost.exe | Misc activity | ET INFO External IP Address Lookup Domain in DNS Lookup (reallyfreegeoip .org) |
7304 | RegAsm.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
7304 | RegAsm.exe | Device Retrieving External IP Address Detected | ET INFO 404/Snake/Matiex Keylogger Style External IP Check |
7304 | RegAsm.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |